Input Validation and Bypass Testing of Web Applications
Input Validation and Bypass Testing of Web Applications Jeff Offutt www. cs. gmu. edu/~offutt/ SWE 432 Design and Implementation of Software for the Web

Deploying software • Bundled : Pre-installed on computer • Shrink-wrap : Bought and installed by end-users • Contract : Purchaser pays developer to develop and install, usually for a fixed price • Embedded : Installed on a hardware device, usually with no direct communication with user • Web : Executed across the Internet through HTTP 14 June 2021 © Offutt 2

Problem parameters HTTP is a stateless protocol • – Each request is independent of previous requests Servers have little information about where a request comes from Web site software is extremely loosely coupled • • – – – 14 June 2021 Coupled through the Internet – separated by space Coupled to diverse hardware devices Written in diverse software languages © Offutt 3
Validating inputs Input validation Deciding if input values can be processed by the software • How should a program recognize invalid inputs ? • What should a program do with invalid inputs ? • It is easy to write input validators – but also easy to make mistakes ! 14 June 2021 © Offutt 4
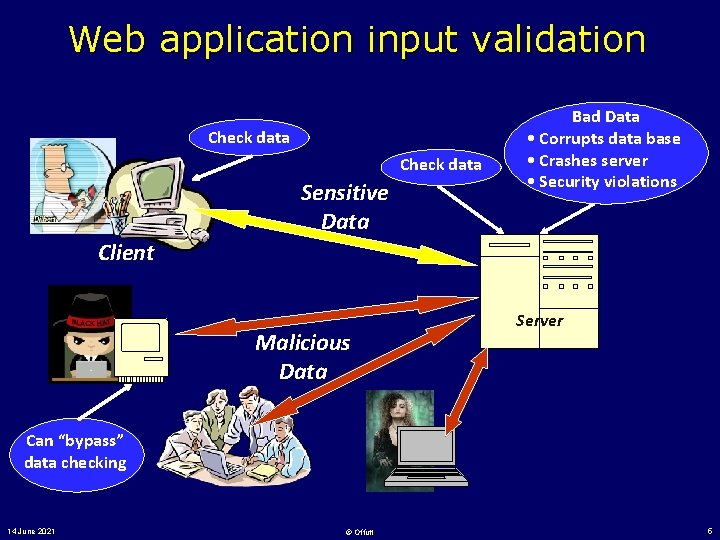
Web application input validation Check data Sensitive Data Bad Data • Corrupts data base • Crashes server • Security violations Client Malicious Data Server Can “bypass” data checking 14 June 2021 © Offutt 5
Validating inputs Input validation Deciding if input values can be processed by the software • How should a program recognize invalid inputs ? • What should a program do with invalid inputs ? • It is easy to write input validators – but also easy to make mistakes ! 14 June 2021 © Offutt 6
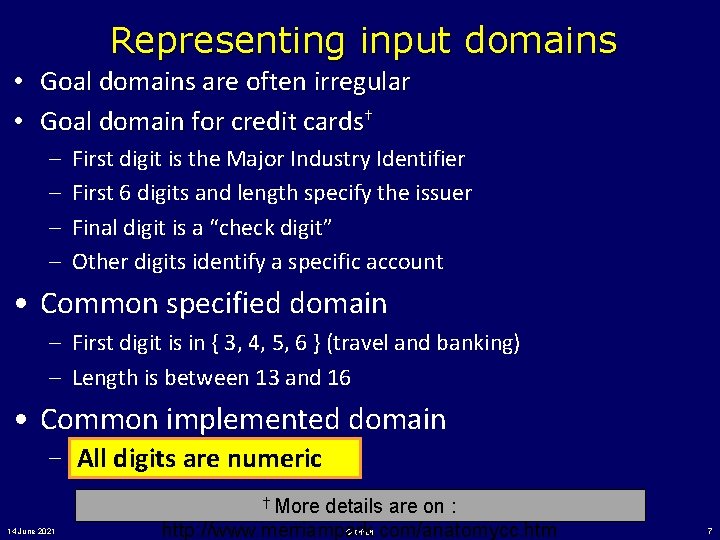
Representing input domains • Goal domains are often irregular • Goal domain for credit cards† – – First digit is the Major Industry Identifier First 6 digits and length specify the issuer Final digit is a “check digit” Other digits identify a specific account • Common specified domain – First digit is in { 3, 4, 5, 6 } (travel and banking) – Length is between 13 and 16 • Common implemented domain – All areare numeric Alldigits numeric † More 14 June 2021 details are on : http: //www. merriampark. com/anatomycc. htm © Offutt 7
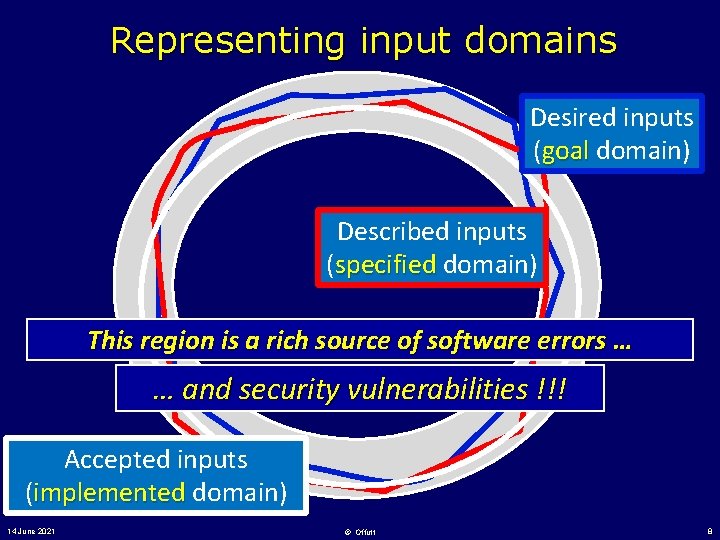
Representing input domains Desired inputs (goal domain) Described inputs (specified domain) This region is a rich source of software errors … … and security vulnerabilities !!! Accepted inputs (implemented domain) 14 June 2021 © Offutt 8
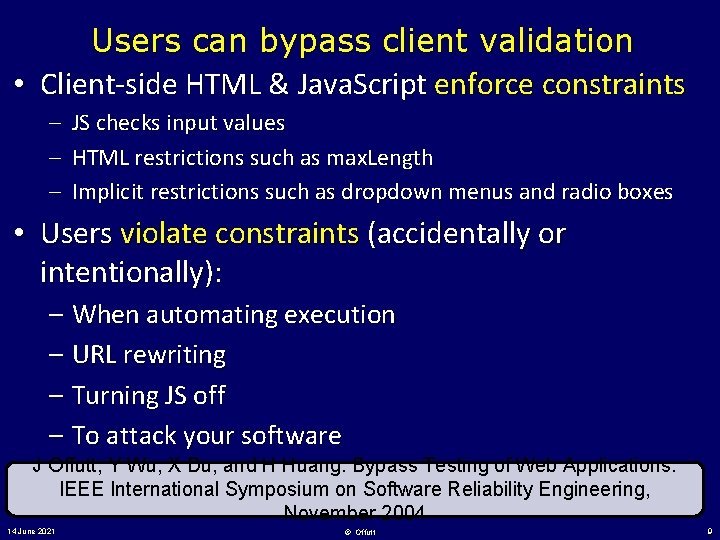
Users can bypass client validation • Client-side HTML & Java. Script enforce constraints – – – JS checks input values HTML restrictions such as max. Length Implicit restrictions such as dropdown menus and radio boxes • Users violate constraints (accidentally or intentionally): – When automating execution – URL rewriting – Turning JS off – To attack your software J Offutt, Y Wu, X Du, and H Huang. Bypass Testing of Web Applications. IEEE International Symposium on Software Reliability Engineering, November 2004 14 June 2021 © Offutt 9
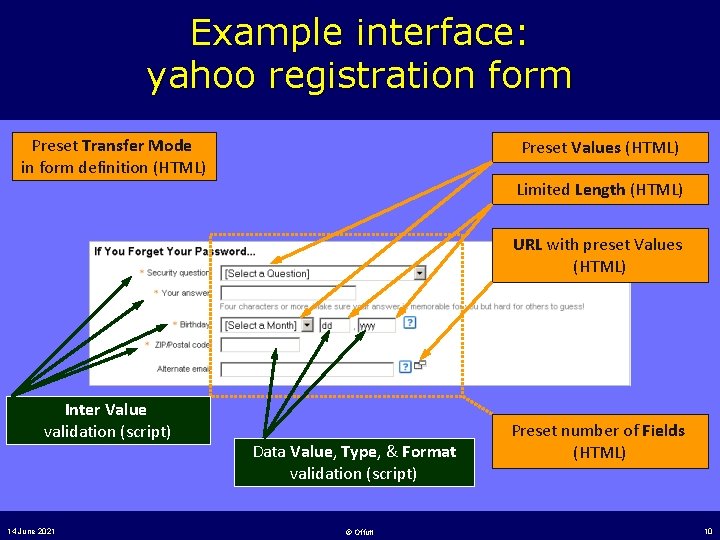
Example interface: yahoo registration form Preset Transfer Mode in form definition (HTML) Preset Values (HTML) Limited Length (HTML) URL with preset Values (HTML) Inter Value validation (script) 14 June 2021 Data Value, Type, & Format validation (script) © Offutt Preset number of Fields (HTML) 10
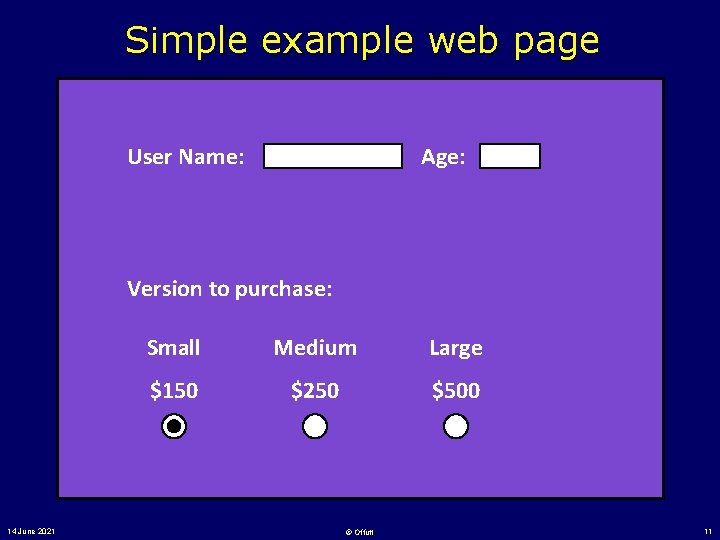
Simple example web page User Name: Age: Version to purchase: 14 June 2021 Small Medium Large $150 $250 $500 © Offutt 11
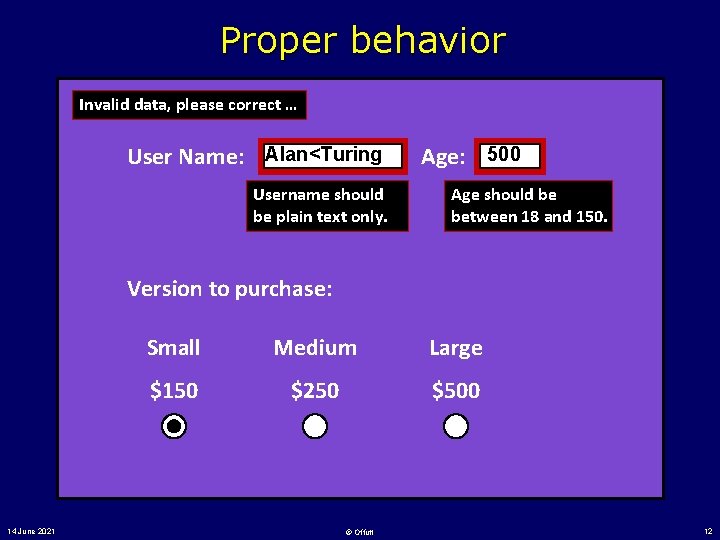
Proper behavior Invalid data, please correct … User Name: Alan<Turing Username should be plain text only. Age: 500 Age should be between 18 and 150. Version to purchase: 14 June 2021 Small Medium Large $150 $250 $500 © Offutt 12

Abbreviated HTML <form> <input type=“text” name=“username” size=20> <input type=“text” name=“age” size=3 maxlength=3> <p> Version to purchase: Constraints … <input type=“radio” name=“version” value=“ 150” Checked> <input type=“radio” name=“version” value=“ 250”> <input type=“radio” name=“version” value=“ 500”> <input type="submit" on. Click="return check. Info(this. form)"> <input type=“hidden” is. Logged. In=“no”> </form> 14 June 2021 © Offutt 13
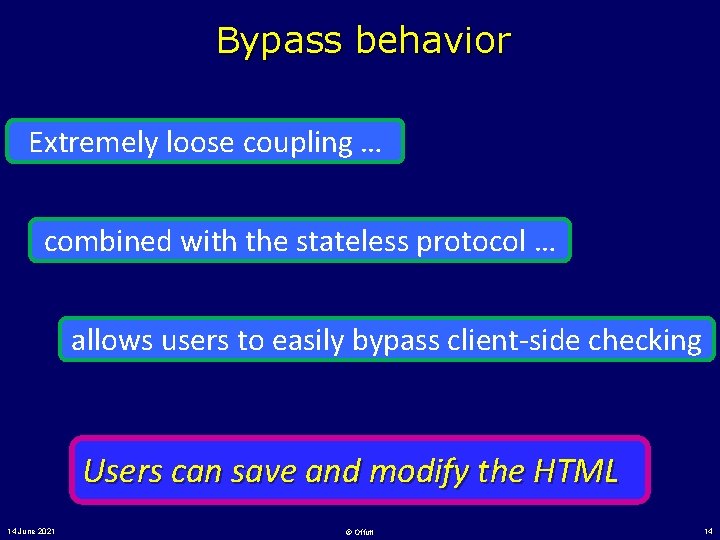
Bypass behavior Extremely loose coupling … combined with the stateless protocol … allows users to easily bypass client-side checking Users can save and modify the HTML 14 June 2021 © Offutt 14

Saved & modified HTML <form> <input type=“text” name=“username” size=20> <input type=“text” name=“age” size=3 maxlength=3> <p> Version to purchase: … Allows an input with arbitrary age, no checking, cost=$25 … ‘<‘ can crash an XML parser <input type=“radio” name=“version” value=“ 150” Checked> Text fields can have SQL statements <input type=“radio” name=“version” value=“ 250”> <input type=“radio” name=“version” value=“ 500”> 25 <input type="submit" on. Click="return check. Info(this. form)"> yes <input type=“hidden” is. Logged. In=“no”> </form> 14 June 2021 © Offutt 15

In-class exercise 1 Saved and modified HTML Open the HTML file: https: //cs. gmu. edu/~offutt/classes/432/in. Class/calculate. html 1. Save it to your computer: i. <ctrl>-u in your browser ii. Copy and paste to your local computer 2. Open the HTML file in your computer 3. Identify elements that could be “bypassed” 14 June 2021 © Offutt 16
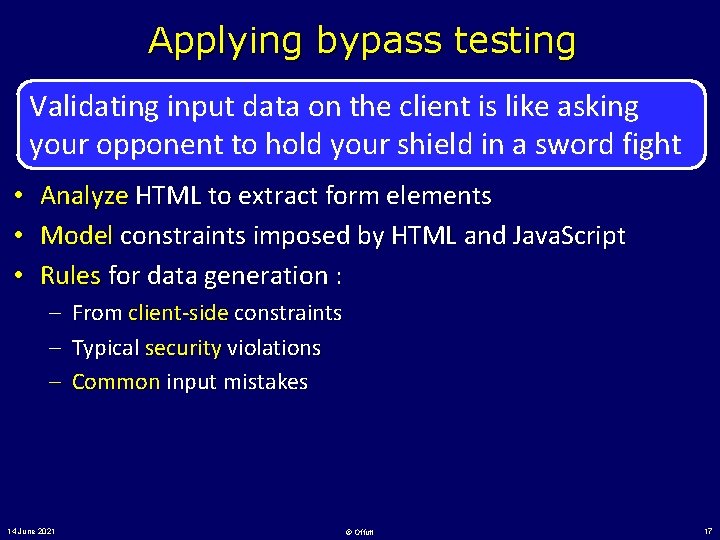
Applying bypass testing Validating input data on the client is like asking your opponent to hold your shield in a sword fight • • • Analyze HTML to extract form elements Model constraints imposed by HTML and Java. Script Rules for data generation : – From client-side constraints – Typical security violations – Common input mistakes 14 June 2021 © Offutt 17
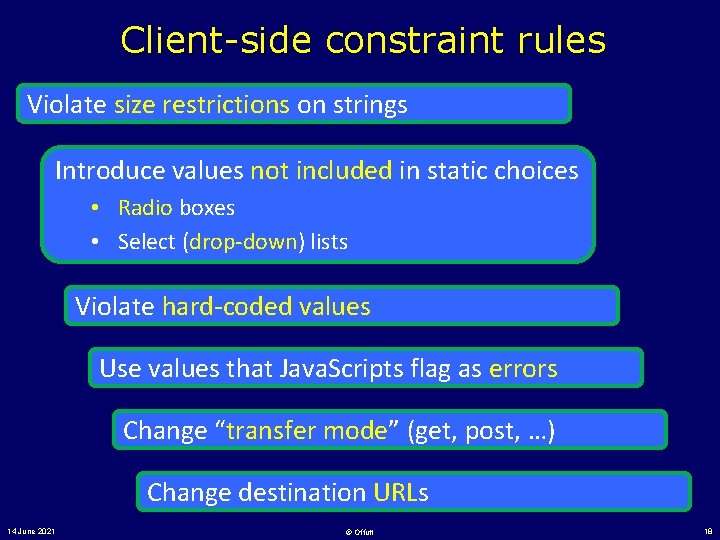
Client-side constraint rules Violate size restrictions on strings Introduce values not included in static choices • Radio boxes • Select (drop-down) lists Violate hard-coded values Use values that Java. Scripts flag as errors Change “transfer mode” (get, post, …) Change destination URLs 14 June 2021 © Offutt 18
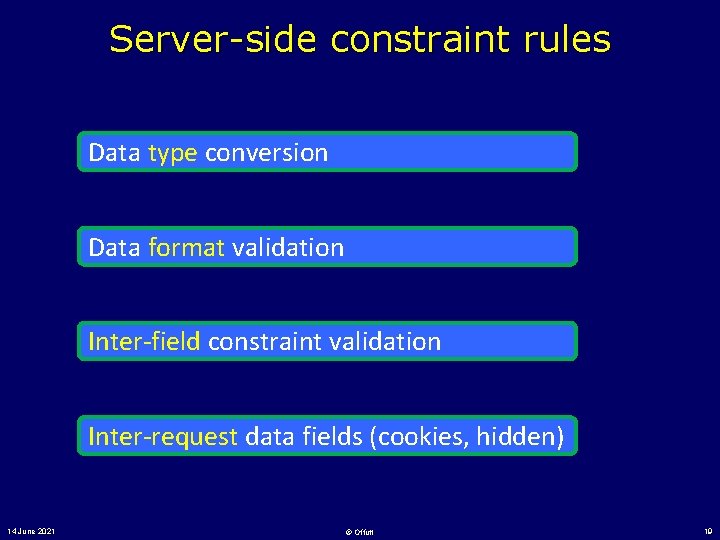
Server-side constraint rules Data type conversion Data format validation Inter-field constraint validation Inter-request data fields (cookies, hidden) 14 June 2021 © Offutt 19

Example security violation rules Potential Illegal Character Empty String Commas Single and double quotes Tag symbols Directory paths Strings starting with forward slash Strings starting with a period Ampersands Control character Characters with high bit set Script symbols 14 June 2021 © Offutt Symbol , ’ or ” Tag symbols < and >. . / /. & NIL, newline 254 and 255 <javascript> or <vbscript> 20
This helps hackers! Application: photosprintshop. Web Error: java. lang. Illegal. State. Exception exception Reason: java. lang. Illegal. State. Exception: An Exception occurred while generating the Exception page 'WOException. Page'. This is most likely due to an error in WOException. Page itself. Below are the logs of first the Exception in WOException. Page, second the Exception in Application that triggered everything. com. webobjects. foundation. NSForward. Exception [com. webobjects. jdbcadaptor. JDBCAdaptor. Exception] date. Information of type java. lang. String is not a valid Date type. You must use java. sql. Timestamp, java. sql. Date, or java. sql. Time: <Session> failed instantiation. Exception raised : com. webobjects. jdbcadaptor. JDBCAdaptor. Exception: date. Information of type java. lang. String is not a valid Date type. You must use java. sql. Timestamp, java. sql. Date, or java. sql. Time Original Exception: 14 June 2021 © Offutt 21

In-class exercise 2 What can happen? Run this program: https: //cs. gmu. edu: 8443/offutt/jsp/gradecalculate. jsp Look at the source (<ctrl>-u) and identify client-side validation rules 14 June 2021 © Offutt 22
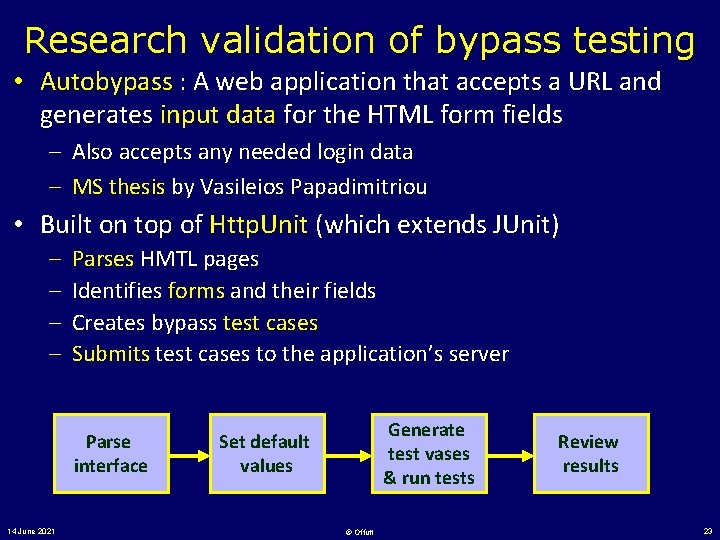
Research validation of bypass testing • Autobypass : A web application that accepts a URL and generates input data for the HTML form fields – Also accepts any needed login data – MS thesis by Vasileios Papadimitriou • Built on top of Http. Unit (which extends JUnit) – – Parses HMTL pages Identifies forms and their fields Creates bypass test cases Submits test cases to the application’s server Parse interface 14 June 2021 Generate test vases & run tests Set default values © Offutt Review results 23
Results on Cyber. Chair Web-based conference management • – – www. cyberchair. org Used by major conferences: ICSE , ICST, ISSRE, ICSM, … Bypass testing found 5 types of faults • 1. 2. 3. 4. 5. 14 June 2021 Submission without authentication Unsafe use of hidden form fields Disclosing information (program crashes) Lack of validation of file type Allows papers of negative length © Offutt 24
Auto. Bypass needs test values • Challenge: – How to automatically provide effective test values? – We need values in the application domain are needed – Enumeration of all possible test values is inefficient • Possible solutions – – Random values (ineffective – lots of junk) Automatically generated values (very hard) Taking values from session log files (feasible but incomplete) Tester input (feasible) • Auto. Bypass uses an input domain created by parsing the interface and tester input 14 June 2021 © Offutt 25

Classifying output responses • (V) Valid Responses : invalid inputs are adequately processed by the server (V 1) Server acknowledges the invalid request and provides an explicit message regarding the violation (V 2) Server produces a generic error message (V 3) Server apparently ignores the invalid request and produces an appropriate response (V 4) Server apparently ignores the request completely • (F) Faults & Failures : invalid inputs that cause abnormal server behavior (typically caught by web server when application fails to handle the error) • (E) Exposure : invalid input is not recognized by the server and abnormal software behavior is exposed to the users 14 June 2021 © Offutt 26

Real-world exp. subjects atutor. ca Atalker demo. joomla. or Poll, Users php. My. Admin Main page, Set Theme, SQL Query, DB Stats brainbench. com nytimes. com Us-markets mutex. gmu. edu Login form yahoo. com Notepad, Composer, Search reminder, Weather Search barnesandnoble. com bankofamerica. com ATM locator, Site search comcast. com Service availability ecost. com Detail submit, Shopping cart control google. com Froogle, Language tools Cart manager, Pure black-box pageflakes. com Book search/resultstesting Submit Request Info, New user Registration means amazon. com myspace. com no source. Item wellsfargolife. com dispatch, (or permission) needed Events & Music Search 14 June 2021 Handle buy © Offutt Quote search 27
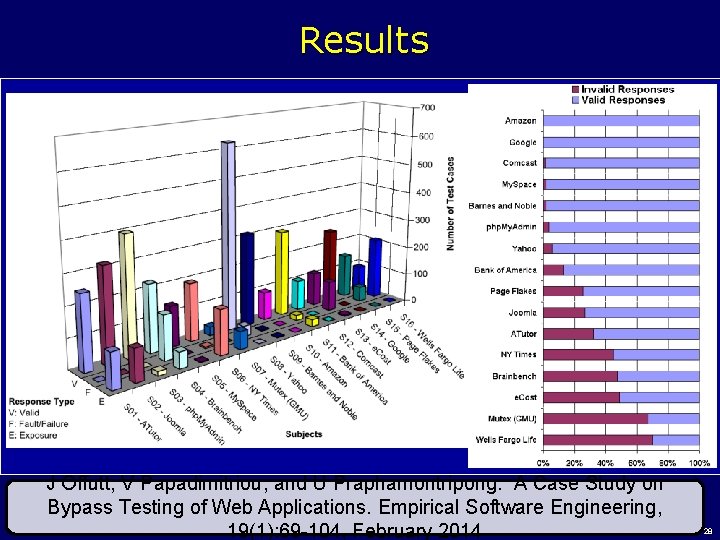
Results v J Offutt, V Papadimitriou, and U Praphamontripong. A Case Study on Bypass Testing of Web Applications. Empirical Software Engineering, 19(1): 69 -104, February 2014 14 June 2021 © Offutt 28
In-class exercise 3 Construct bypass tests for grade. Calculate Encode your tests using URL rewriting Example valid test, 2 courses course. Count=2 course. Name 1=C 1 course. Name 2=C 2 course. Grade 1=A course. Grade 2=B course. Credit 1=3 course. Credit 2=3 Expected output: GPA=3. 5 https: //cs. gmu. edu: 8443/offutt/jsp/gradecalculate. jsp? course. Count= 2&course. Name 1=xx&course. Grade 1=A&course. Credit 1=3&course. Nam e 2=yy&course. Grade 2=B&course. Credit 2=3 14 June 2021 © Offutt 29

Industrial case study • Inventions from scientists are slow to move into industrial practice • We investigated whether the obstacles are : – – – Technical difficulties of applying to industrial use Social barriers Business constraints • Applied bypass testing through the research arm of a software company 14 June 2021 © Offutt 30
Avaya’s NPP technology • NPP : Notification Preference Portal – Used to notify users of events – NPP is a highly user interactive web application • Javascript is used on the client to : – – – • • Validate inputs Dynamically modify screen by manipulating DOM Encode input data into XML before sending to the server This study was part of system testing Encoded values into XML, fed to NPP with Html. Unit 14 June 2021 © Offutt 31
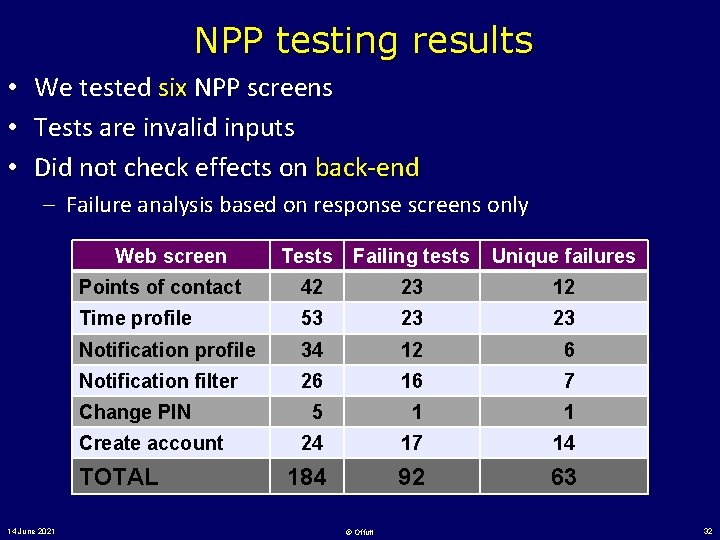
NPP testing results • • • We tested six NPP screens Tests are invalid inputs Did not check effects on back-end – Failure analysis based on response screens only Web screen Tests Failing tests Unique failures Points of contact 42 23 12 Time profile 53 23 23 Notification profile 34 12 6 Notification filter 26 16 7 5 1 1 24 17 14 184 92 63 Change PIN Create account TOTAL 14 June 2021 © Offutt 32

Types of faults • Invalid data saved into the database – These lead to more visible failures later – Example : An invalid password was accepted, but the account could not subsequently be used – Example : Messages could not be sent to invalid contacts • Exposure errors (security issue) – Internal exception message sent in the response screen • No response at all – A software component probably failed – Database or web server sometimes crashed 14 June 2021 © Offutt 33
Summary of Avaya study • Bypass testing worked very well in an industrial context – There is no technical obstacle to adoption • Even generating tests by hand was cheaper – There is no valid business barrier • Most problems are unlikely with non-malicious users and a correct implementation – But client-side validation is notoriously error-prone We concluded the primary obstacle is social The project lead was very defensive Offutt, Wang, and Ordille. An Industrial Case Study of Bypass Testing on Web Applications. 1 st International Conference on Software Testing, April 2008 14 June 2021 © Offutt 34

My bypass testing playmates Ye Wu Vasileios Papadimitriou Joann J. Ordille Xiaochen Du Qingxian Wang Upsorn Praphamontripong Huang 14 June 2021 © Offutt 35

In-class exercise 4 Reflect on research to practice The research literature is full of ideas that have never been used in practice List at least 3 and no more than 10 reasons why research ideas may not be used Write one sentence for each reason 14 June 2021 © Offutt 36

Google’s motto Debugging sucks Testing rocks 14 June 2021 © Offutt 37
- Slides: 37