Information Technology at Emory Network Registration and Intrusion










- Slides: 52

Information Technology at Emory Network Registration and Intrusion Prevention Services Implementation at Emory University Jay D. Flanagan Security Professionals Conference April 2005 Copyright Jay D. Flanagan, 2005. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author.

Information Technology at Emory Information Technology Division Technical Services

Information Technology at Emory Information Technology Division Technical Services

Information Technology at Emory Security at Emory • In 2000 it was determined that more and better security was needed to protect the Emory environment • In 2001 a Security Initiatives Project was proposed and funded – Over 1 million dollars was set aside for the initiatives – Initial projects included: • • Firewalls Virus Scanning Vulnerability Scanning Web Content Security Information Technology Division Technical Services

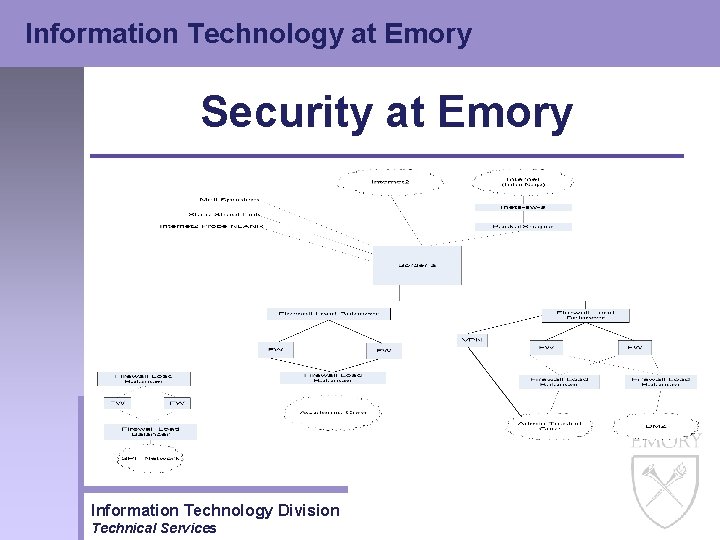
Information Technology at Emory Security at Emory • Firewalls – Firewall protection is the cornerstone of the security project – Firewall protection has been implemented at the Emory border gateway to the internet, for the School of Public Health (SPH), for Resnet and for our Administrative Trusted Core (The Administrative Trusted Core protects those services that are considered confidential and restricted) Information Technology Division Technical Services

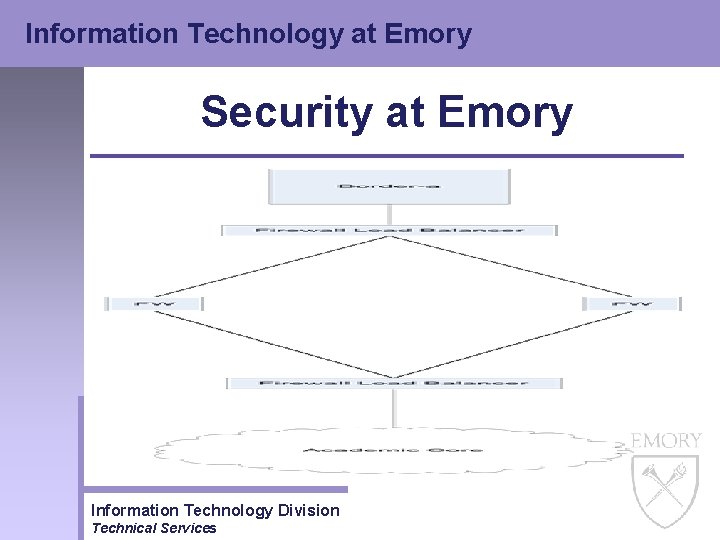
Information Technology at Emory Security at Emory • Border Gateway Firewall – Implemented in the Fall of 2001 – Specific rules set up to protect the Emory Academic network – Rules stop specific vulnerabilities that could adversely affect machines and their ability to work Information Technology Division Technical Services

Information Technology at Emory Security at Emory Information Technology Division Technical Services

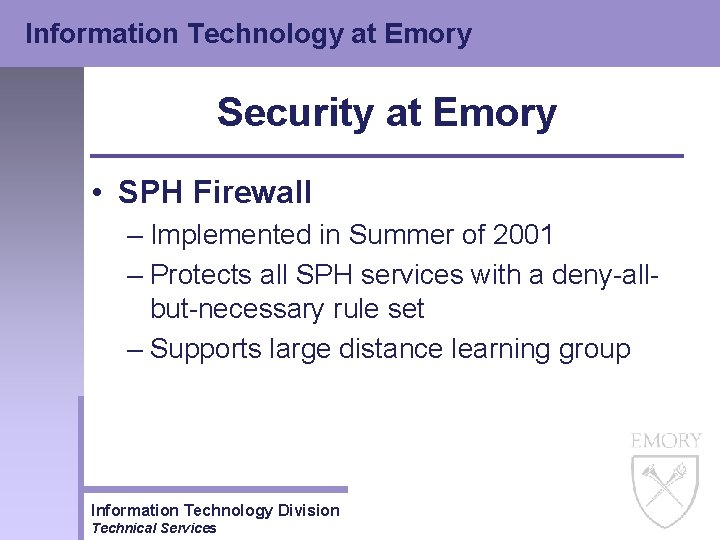
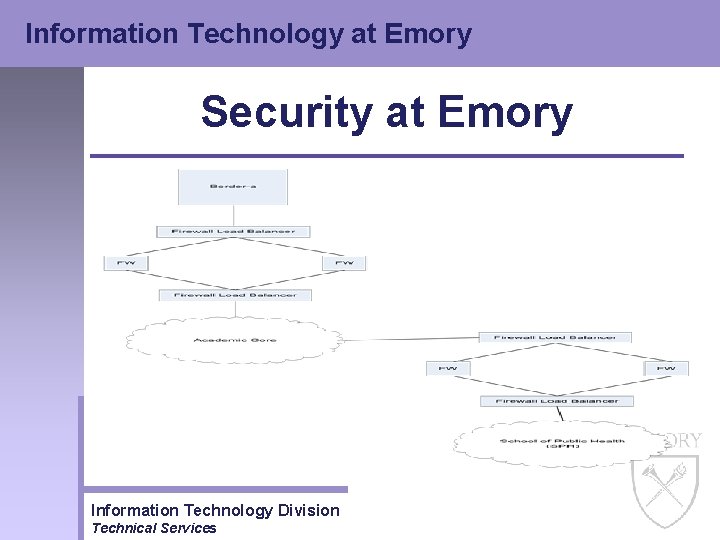
Information Technology at Emory Security at Emory • SPH Firewall – Implemented in Summer of 2001 – Protects all SPH services with a deny-allbut-necessary rule set – Supports large distance learning group Information Technology Division Technical Services

Information Technology at Emory Security at Emory Information Technology Division Technical Services

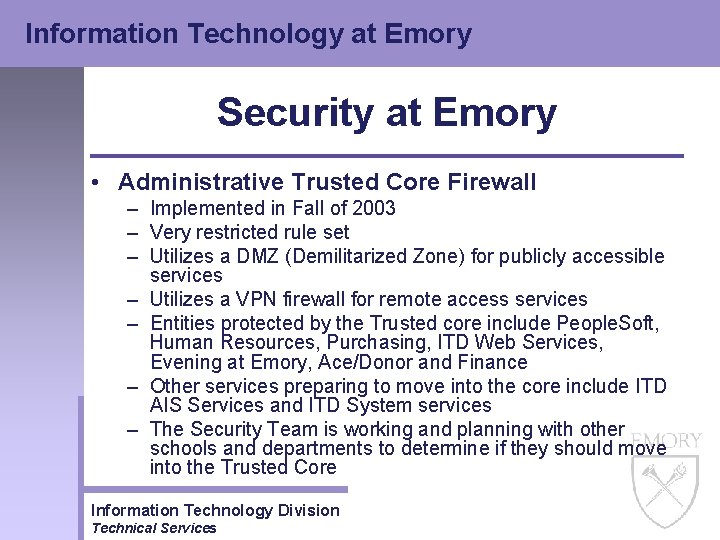
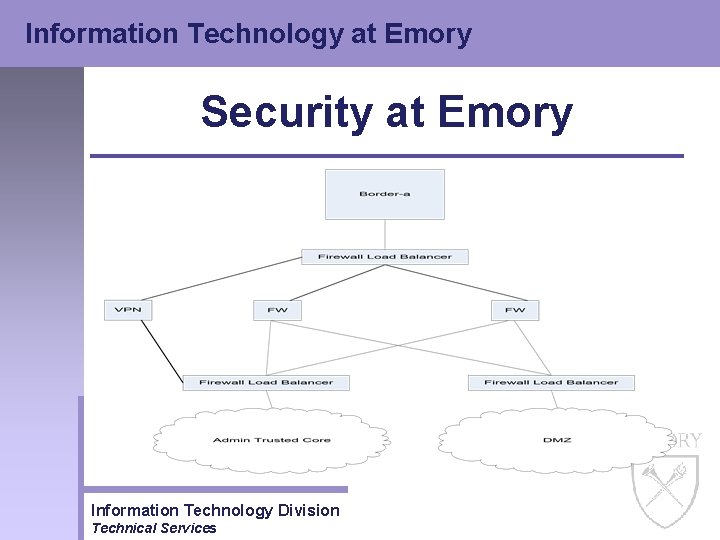
Information Technology at Emory Security at Emory • Administrative Trusted Core Firewall – Implemented in Fall of 2003 – Very restricted rule set – Utilizes a DMZ (Demilitarized Zone) for publicly accessible services – Utilizes a VPN firewall for remote access services – Entities protected by the Trusted core include People. Soft, Human Resources, Purchasing, ITD Web Services, Evening at Emory, Ace/Donor and Finance – Other services preparing to move into the core include ITD AIS Services and ITD System services – The Security Team is working and planning with other schools and departments to determine if they should move into the Trusted Core Information Technology Division Technical Services

Information Technology at Emory Security at Emory Information Technology Division Technical Services

Information Technology at Emory Security at Emory Information Technology Division Technical Services

Information Technology at Emory Information Technology Division Technical Services

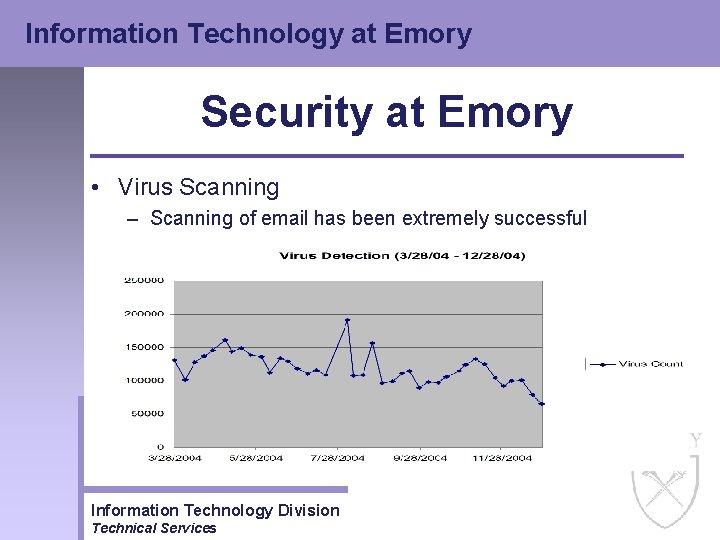
Information Technology at Emory Security at Emory • Email Virus Scanning – Went production in January of 2003 – Service has been a huge success – All inbound and outbound, including internal outbound email is scanned – Hundreds of thousands of email born viruses blocked by email virus scanners Information Technology Division Technical Services

Information Technology at Emory Security at Emory • Virus Scanning – Scanning of email has been extremely successful Information Technology Division Technical Services

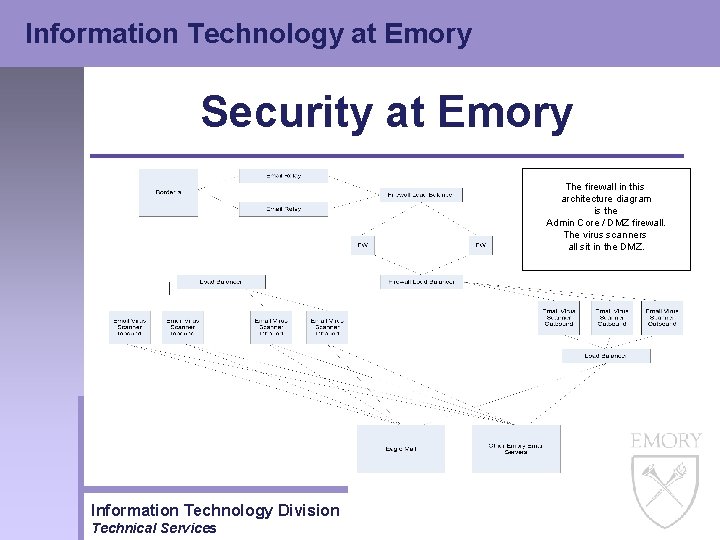
Information Technology at Emory Security at Emory The firewall in this architecture diagram is the Admin Core / DMZ firewall. The virus scanners all sit in the DMZ. Information Technology Division Technical Services

Information Technology at Emory Security at Emory • Desktop Virus Scanning – New desktop antivirus software from Symantec implemented in Summer of 2003 – Pushed out to all users on campus via Emory on Line (EOL) CD – Set up managed AV services for ITD in Fall of 2004 • Working with other schools and departments on campus to set up the managed service • Other schools and departments using the managed service include Emory College, Theology, Campus Life and Bio. Chemistry Information Technology Division Technical Services

Information Technology at Emory Information Technology Division Technical Services

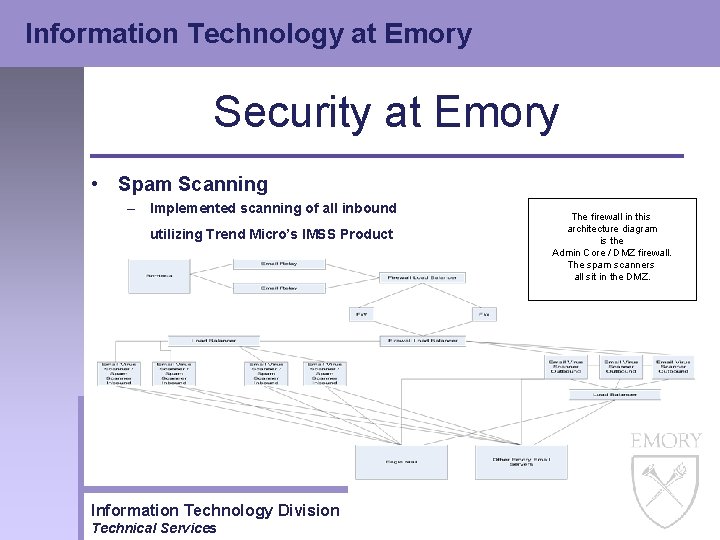
Information Technology at Emory Security at Emory • Spam Scanning Service – A huge problem for Emory email users – Implemented centralized spam scanning in 2003 • Scanned all incoming email to Emory’s central mail service, Eagle Mail – Other campus email servers added to this service in late 2003 and 2004 • Including Learnlink, Listserv, Nursing, Cell Biology, Spinal, Housing, Physics, Physiology, Bimcore, Math. CS, Facilities, SPH, Law School and Biology Information Technology Division Technical Services

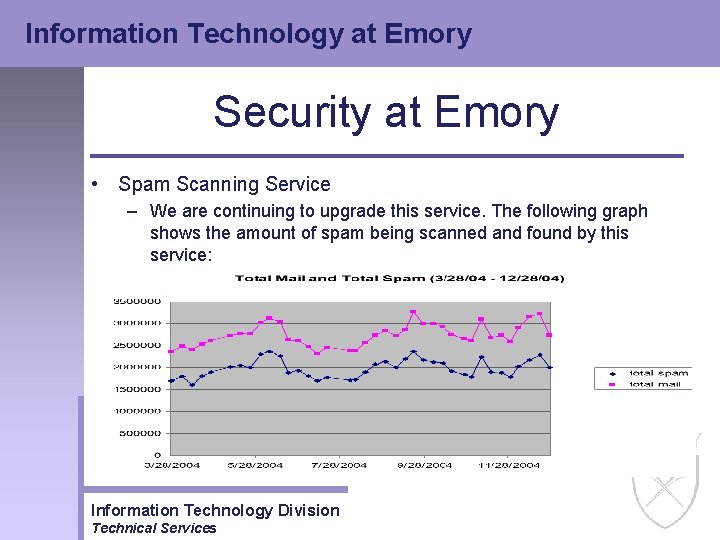
Information Technology at Emory Security at Emory • Spam Scanning Service – We are continuing to upgrade this service. The following graph shows the amount of spam being scanned and found by this service: Information Technology Division Technical Services

Information Technology at Emory Security at Emory • Spam Scanning – Implemented scanning of all inbound utilizing Trend Micro’s IMSS Product Information Technology Division Technical Services email The firewall in this architecture diagram is the Admin Core / DMZ firewall. The spam scanners all sit in the DMZ.

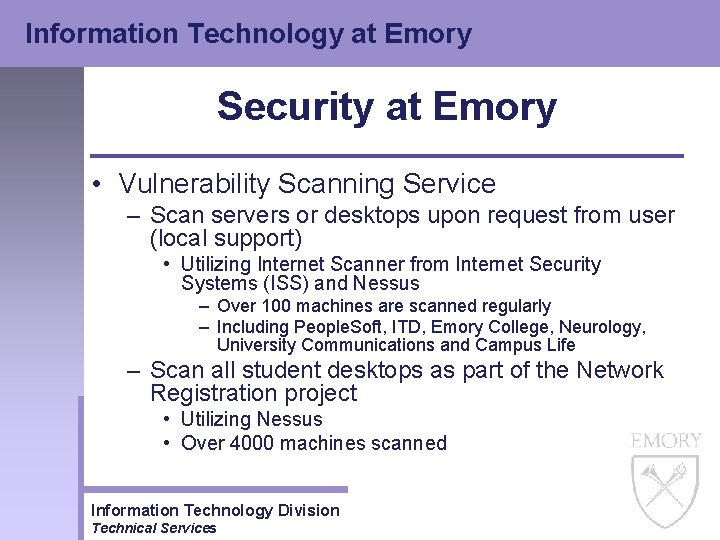
Information Technology at Emory Security at Emory • Vulnerability Scanning Service – Scan servers or desktops upon request from user (local support) • Utilizing Internet Scanner from Internet Security Systems (ISS) and Nessus – Over 100 machines are scanned regularly – Including People. Soft, ITD, Emory College, Neurology, University Communications and Campus Life – Scan all student desktops as part of the Network Registration project • Utilizing Nessus • Over 4000 machines scanned Information Technology Division Technical Services

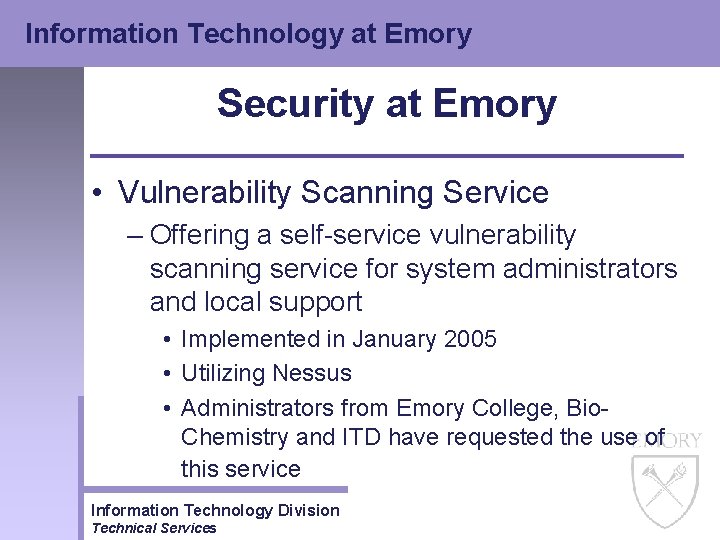
Information Technology at Emory Security at Emory • Vulnerability Scanning Service – Offering a self-service vulnerability scanning service for system administrators and local support • Implemented in January 2005 • Utilizing Nessus • Administrators from Emory College, Bio. Chemistry and ITD have requested the use of this service Information Technology Division Technical Services

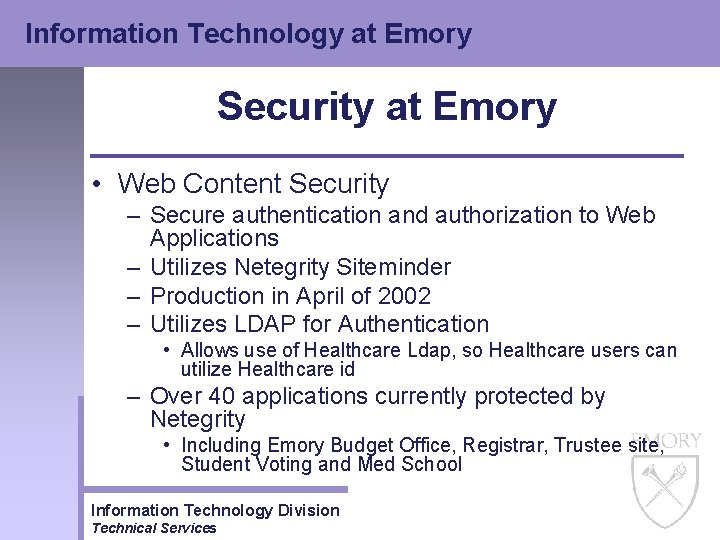
Information Technology at Emory Security at Emory • Web Content Security – Secure authentication and authorization to Web Applications – Utilizes Netegrity Siteminder – Production in April of 2002 – Utilizes LDAP for Authentication • Allows use of Healthcare Ldap, so Healthcare users can utilize Healthcare id – Over 40 applications currently protected by Netegrity • Including Emory Budget Office, Registrar, Trustee site, Student Voting and Med School Information Technology Division Technical Services

Information Technology at Emory Not Enough? • In the Fall of 2003, Emory was hit by the Blaster and Welchia viruses/worms like many other Universities – Thousands of machines were infected – Many were never completely cleaned • In the Spring of 2004, Emory was hit by a rash of DDo. S attacks which took down the academic network – Almost 60% of the attacks were initiated by machines on our Resnet network Information Technology Division Technical Services

Information Technology at Emory Information Technology Division Technical Services

Information Technology at Emory More needed to be done • Even with the many new security initiatives in place, infections, compromises and outages were occurring – Caused major disruptions to Emory operations • During registration at beginning of school year • During finals at end of the school year • New options needed to be found and implemented – Network Redesign – Network Registration – Intrusion Prevention Information Technology Division Technical Services

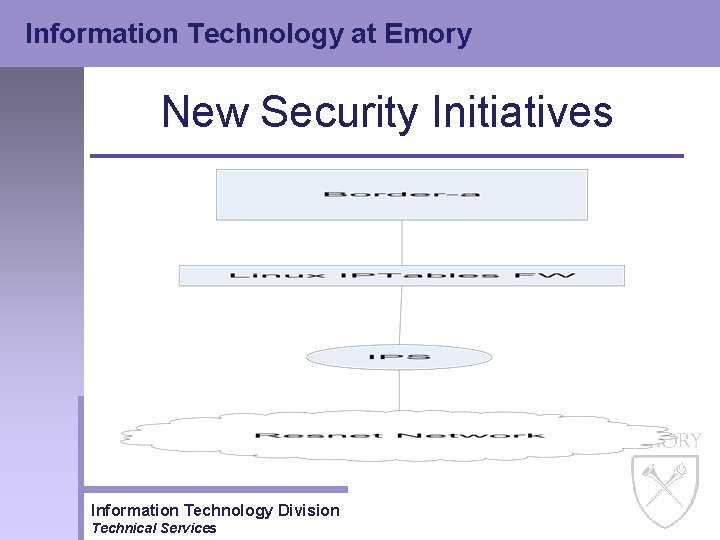
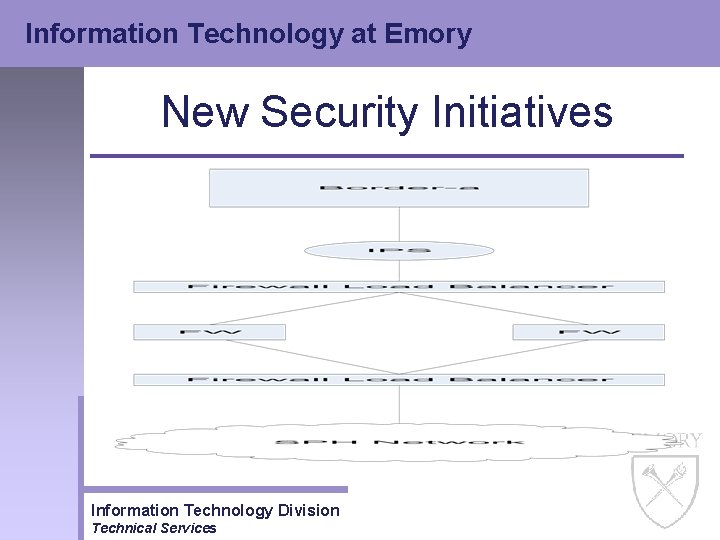
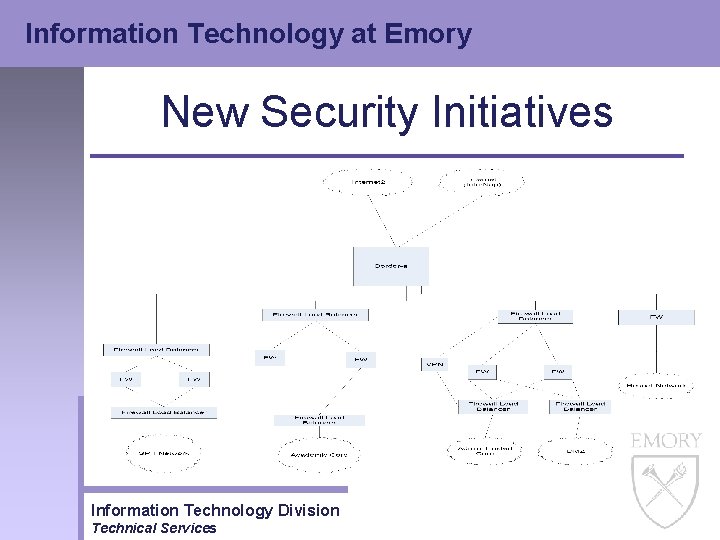
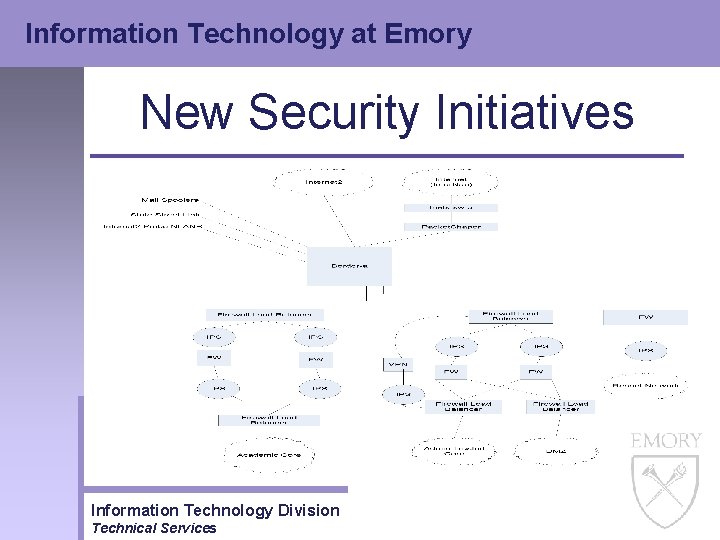
Information Technology at Emory New Security Initiatives • Network Redesign – Resnet Network • Over 60% of the DDo. S attacks in the spring of 2004 were from our Resnet network • Copyright violations were increasing, with over 70% from our Resnet network • How to prevent these attacks and violations from occurring while at the same time protecting the Resnet network? – Move the Resnet network outside the Academic Core firewall – Implement IPS / IDS – Implement Firewall Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

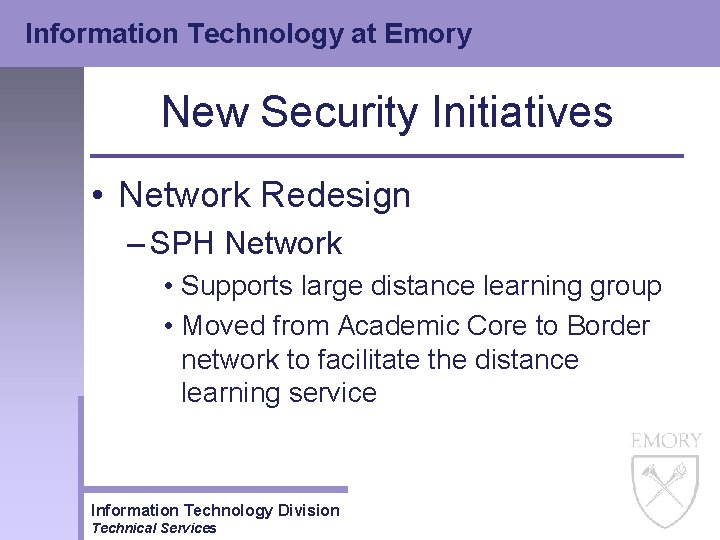
Information Technology at Emory New Security Initiatives • Network Redesign – SPH Network • Supports large distance learning group • Moved from Academic Core to Border network to facilitate the distance learning service Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

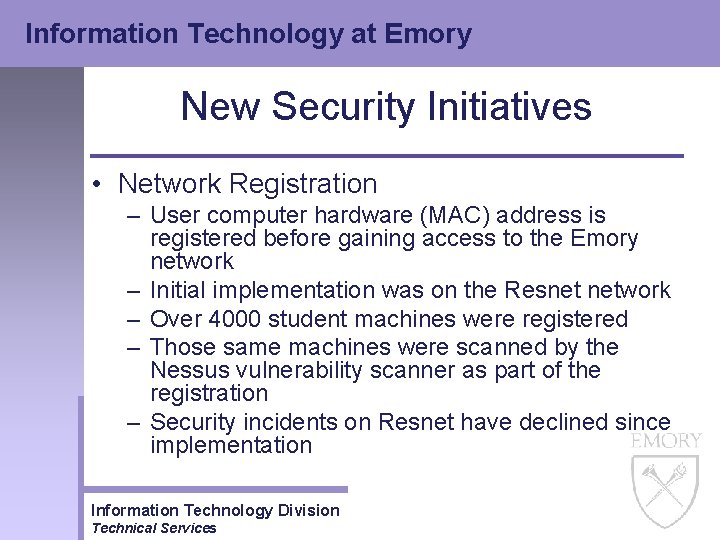
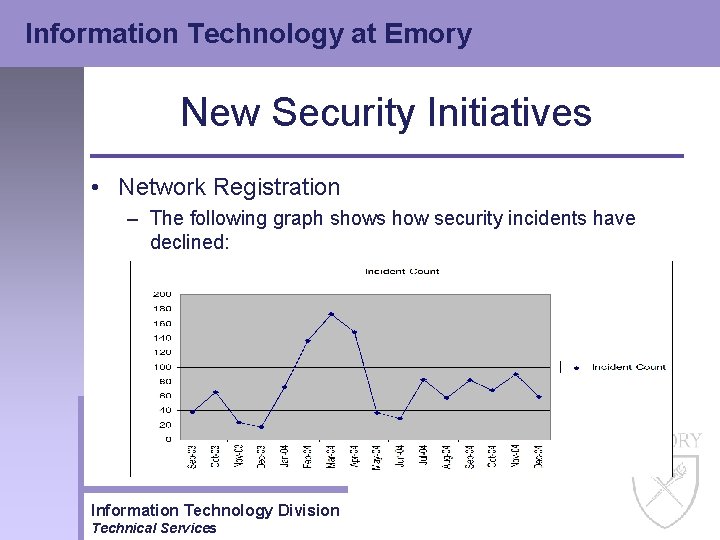
Information Technology at Emory New Security Initiatives • Network Registration – User computer hardware (MAC) address is registered before gaining access to the Emory network – Initial implementation was on the Resnet network – Over 4000 student machines were registered – Those same machines were scanned by the Nessus vulnerability scanner as part of the registration – Security incidents on Resnet have declined since implementation Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives • Network Registration – The following graph shows how security incidents have declined: Information Technology Division Technical Services

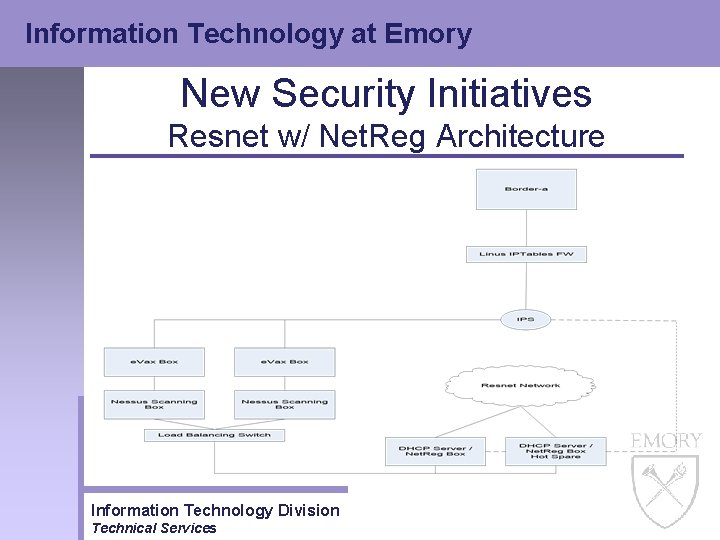
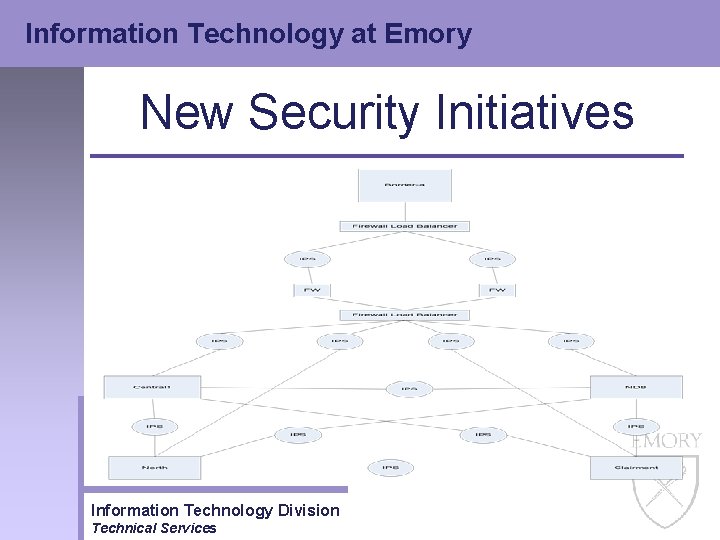
Information Technology at Emory New Security Initiatives Resnet w/ Net. Reg Architecture Information Technology Division Technical Services

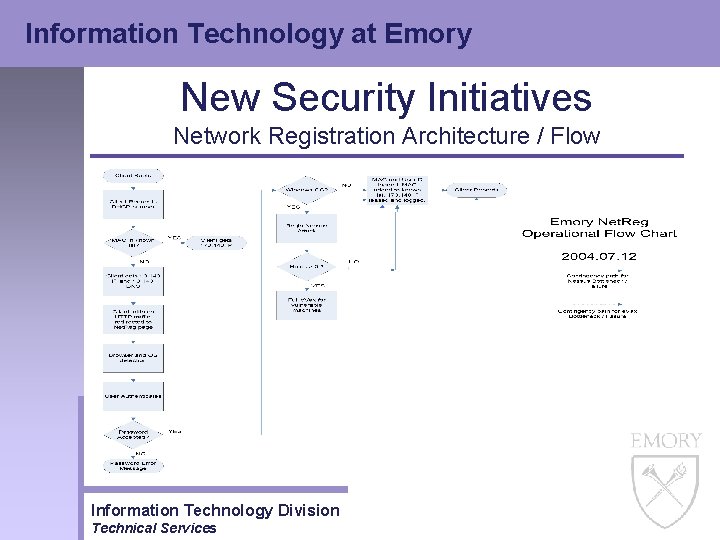
Information Technology at Emory New Security Initiatives Network Registration Architecture / Flow Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives • Network Registration – Phase 2 – The 2 nd phase of Network Registration implements this service to other portions of the Emory campus • Initially: – Library – Oxford • Other schools and departments indicating interest include: – Law School – School of Public Health Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives • Network Registration – Phase 2 – Implementing at these other entities has different requirements – Specifically guest access requirements – With these new requirements, an evaluation was done of vendor products, including Perfigo’s Clean Machine and Bradford’s Campus Manager Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives • Network Registration – Phase 2 – Implementing network registration in places like Oxford and the Library will give us an excellent indication of how it will roll out to the entire campus. – Phase 2 part 1 of the project would implement network registration at Oxford and the Library – Phase 2 part 2 would move the rest of the campus Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives • Intrusion Detection / Prevention – Original proposal implemented Intrusion Detection • Manual intervention necessary for all alerts • Resource intensive • Large number of false positives – Decided to evaluate Intrusion Prevention • Alerts like intrusion detection • Automatically blocks hacks and attacks without manual intervention • Less resources necessary to mange multiple boxes • Non-existent false positives Information Technology Division Technical Services

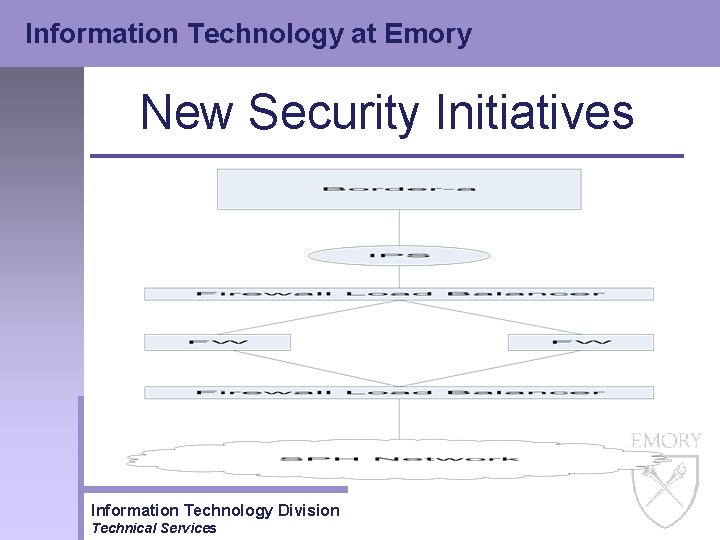
Information Technology at Emory New Security Initiatives • Intrusion Prevention – Implemented two IPS boxes in July of 2004 • Interfaces for Resnet, Administrative Trusted Core and border network firewalls Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives • Intrusion Prevention – Implemented four more IPS boxes in October of 2004 • Interfaces for entire Academic Core and SPH Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

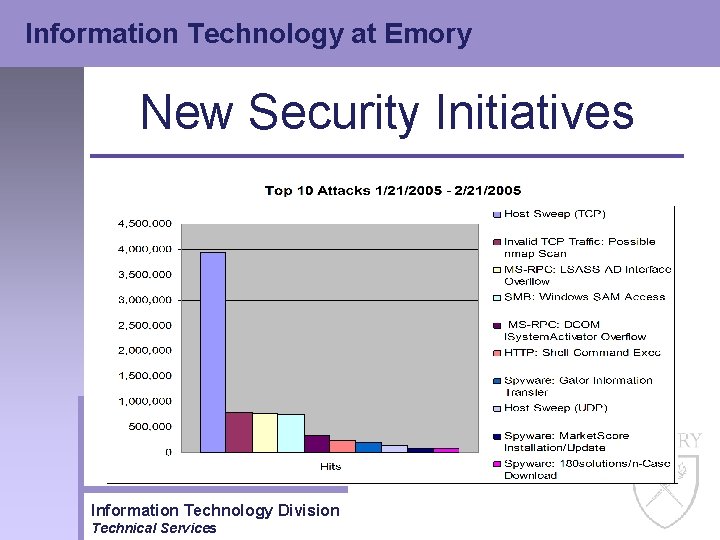
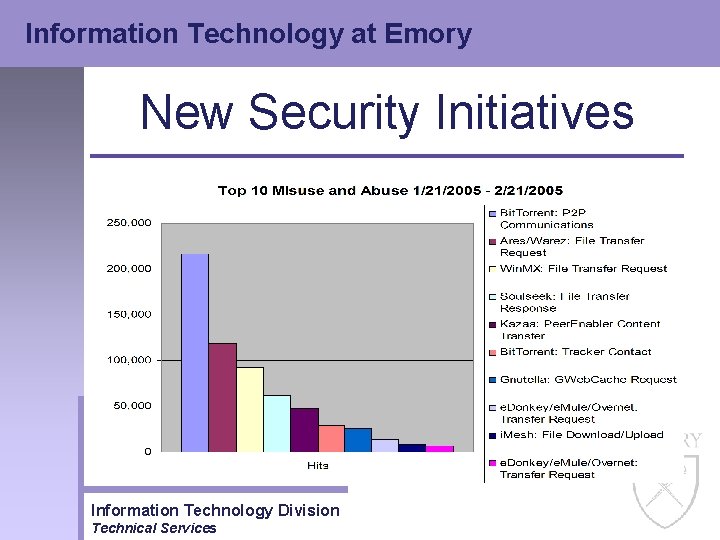
Information Technology at Emory New Security Initiatives • Intrusion Prevention – The IPS implementation has been extremely successful • Literally millions of hacks, attacks and compromises have been blocked by this service • The graphs on the following two slides shows our success Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

Information Technology at Emory New Security Initiatives Information Technology Division Technical Services

Information Technology at Emory Summary • We have come a long way in securing the Emory network • Work still remains • The steps outlined here will help in making Emory more secure by being aggressive and proactive in our vigilance against hacks, attacks, compromises and viruses Information Technology Division Technical Services

Information Technology at Emory Information Technology Division Technical Services

Information Technology at Emory Contact Information • Jay D. Flanagan – Security Team Lead – jflanag@emory. edu • Security. Team-L@listserv. emory. edu • http: //security. it. emory. edu Information Technology Division Technical Services

Information Technology at Emory Questions ? Information Technology Division Technical Services