Information Technology Asset Management ITAM Software License Management



















- Slides: 42

Information Technology Asset Management (ITAM) Software License Management (SLM) Introduction August 2018

Webinar Information Audio dial-in number: 1 -866 -783 -7350 Participant code: 6928919# URL: https: //conference. apps. mil/webconf/esiwebinar § Teleconference audio will be muted for all participants § Please submit any questions or comments via the webinar chat § Questions will be addressed at the end, time permitting 1

Do. D ESI Team Introductions Floyd Groce | DON CIO IT Strategic Jim Cecil| IT Management Consultant, Leads the DON CIO Enterprise Licensing and strategic sourcing efforts for IT hardware, software and services. One of the Do. D points of contact for OMB Federal Strategic Sourcing Initiative (FSSI) Smart. BUY software licensing initiative. Previously, held an unlimited contracting officer warrant for IT contracting. Enterprise IT asset management, portfolio management, strategic sourcing, and program management consultant with over 20 years of experience in managing and implementing commercial and custom information technology. Supports Do. D CIO in IT Asset Management and Enterprise Software Licensing and Procurement. Sourcing Lead, Do. D ESI Co-Chair Do. D CIO 2

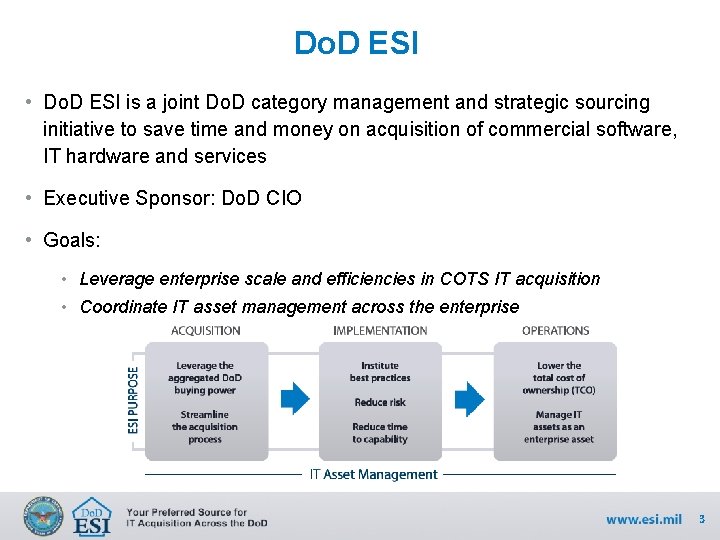
Do. D ESI • Do. D ESI is a joint Do. D category management and strategic sourcing initiative to save time and money on acquisition of commercial software, IT hardware and services • Executive Sponsor: Do. D CIO • Goals: • Leverage enterprise scale and efficiencies in COTS IT acquisition • Coordinate IT asset management across the enterprise 3

Agenda • The need for Software License Management (SLM) • IT Asset Management (ITAM) • SLM framework • Do. D approach • Federal and Do. D SLM policy and resources 4

The need for Software License Management (SLM) 5

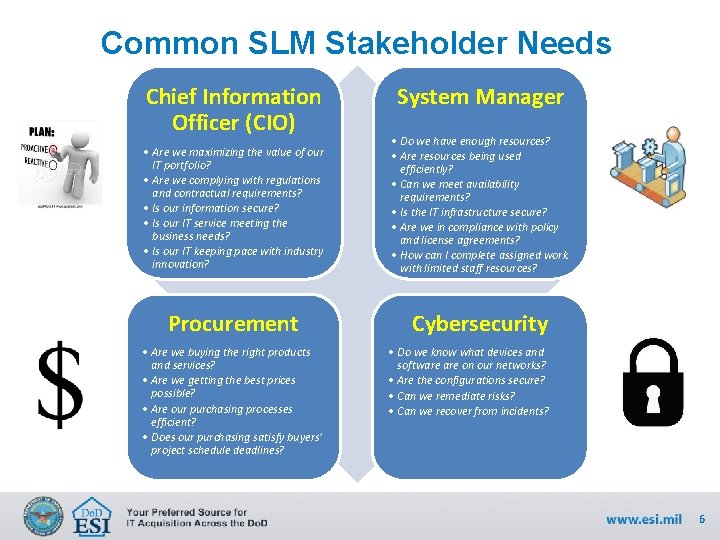
Common SLM Stakeholder Needs Chief Information Officer (CIO) System Manager • Are we maximizing the value of our IT portfolio? • Are we complying with regulations and contractual requirements? • Is our information secure? • Is our IT service meeting the business needs? • Is our IT keeping pace with industry innovation? • Do we have enough resources? • Are resources being used efficiently? • Can we meet availability requirements? • Is the IT infrastructure secure? • Are we in compliance with policy and license agreements? • How can I complete assigned work with limited staff resources? Procurement Cybersecurity • Are we buying the right products and services? • Are we getting the best prices possible? • Are our purchasing processes efficient? • Does our purchasing satisfy buyers’ project schedule deadlines? • Do we know what devices and software on our networks? • Are the configurations secure? • Can we remediate risks? • Can we recover from incidents? 6

Do. D SLM Requirements • FY 17 NDAA Section 1653: Cybersecurity Comply to Connect & License Management – Forbids purchasing software costing more than $5 M unless automated inventory reporting tools are in place – Do. D CIO 10 July 2018 Memorandum reiterates software inventory requirement • DODI 5000. 76 (2017): Management and Accounting of Internal Use Software – Requires property accountability for “Internal Use Software” and bulk license purchases • MEGABYTE Act of 2016 & OMB Policy M-16 -1 – Directs Federal CIOs to implement enterprise software license management capabilities – Requires agencies to maintain enterprise-wide license inventory reports • FY 15 NDAA / Federal IT Acquisition Reform Act (FITARA) – Directs OMB to implement government-wide software licensing solutions • FY 14 NDAA Section 935: Software License Inventory Reporting – Requires automated software license inventory reporting process • RMF: Cybersecurity information security continuous monitoring (ISCM) – NIST Risk Management Framework (RMF) & NIST SP 800 -137 – Requires visibility into all IT assets on Do. D networks to assess and remediate vulnerabilities 7

SLM Challenges 8

What is a “software license”*? 9

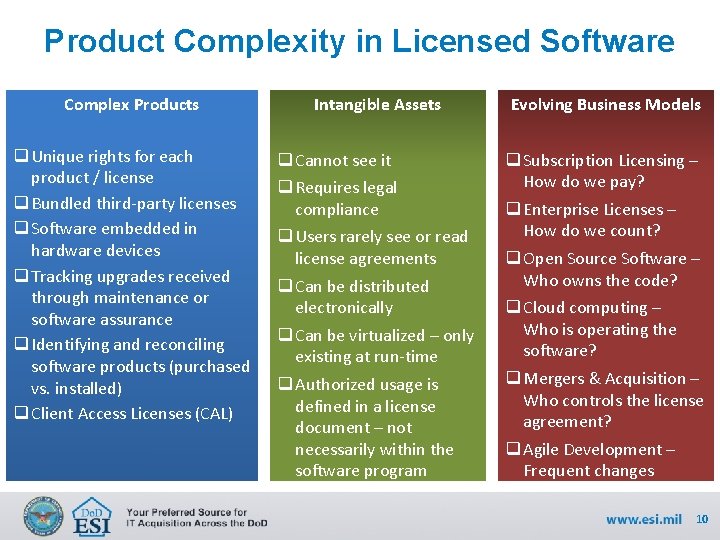
Product Complexity in Licensed Software Complex Products Intangible Assets Evolving Business Models q Unique rights for each product / license q Bundled third-party licenses q Software embedded in hardware devices q Tracking upgrades received through maintenance or software assurance q Identifying and reconciling software products (purchased vs. installed) q Client Access Licenses (CAL) q Cannot see it q Requires legal compliance q Users rarely see or read license agreements q Can be distributed electronically q Can be virtualized – only existing at run-time q Authorized usage is defined in a license document – not necessarily within the software program q Subscription Licensing – How do we pay? q Enterprise Licenses – How do we count? q Open Source Software – Who owns the code? q Cloud computing – Who is operating the software? q Mergers & Acquisition – Who controls the license agreement? q Agile Development – Frequent changes 10

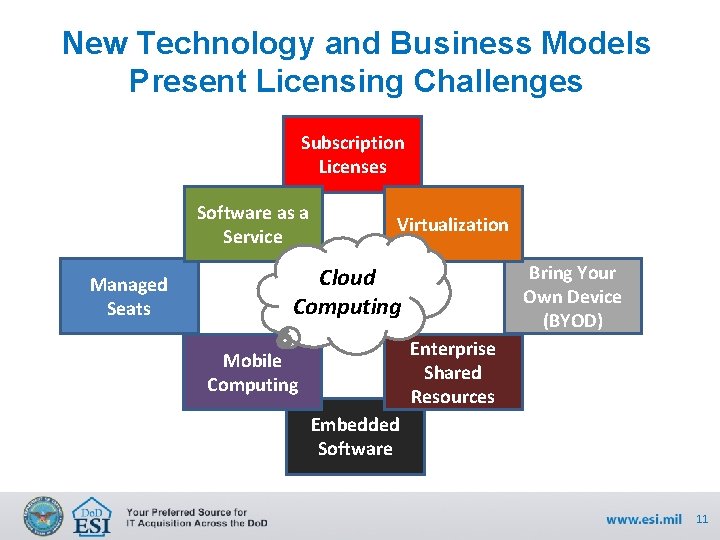
New Technology and Business Models Present Licensing Challenges Subscription Licenses Software as a Service Managed Seats Virtualization Bring Your Own Device (BYOD) Cloud Computing Enterprise Shared Resources Mobile Computing Embedded Software 11

IT Asset Management (ITAM) & SLM 12

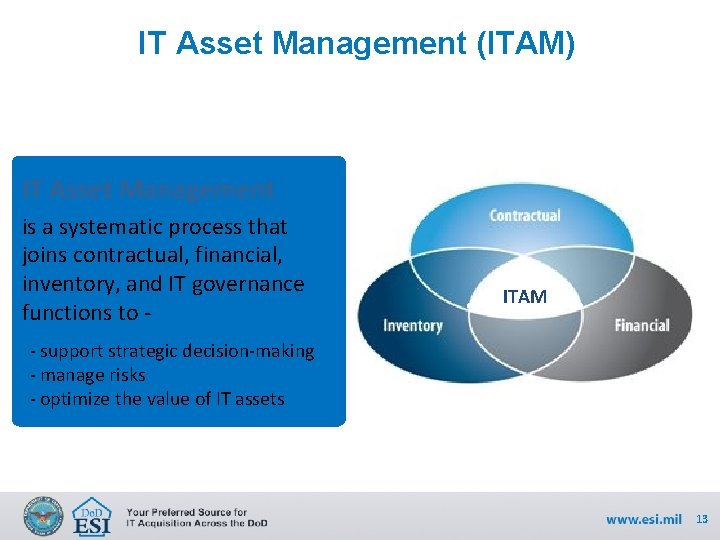
IT Asset Management (ITAM) IT Asset Management is a systematic process that joins contractual, financial, inventory, and IT governance functions to - ITAM - support strategic decision-making - manage risks - optimize the value of IT assets 13

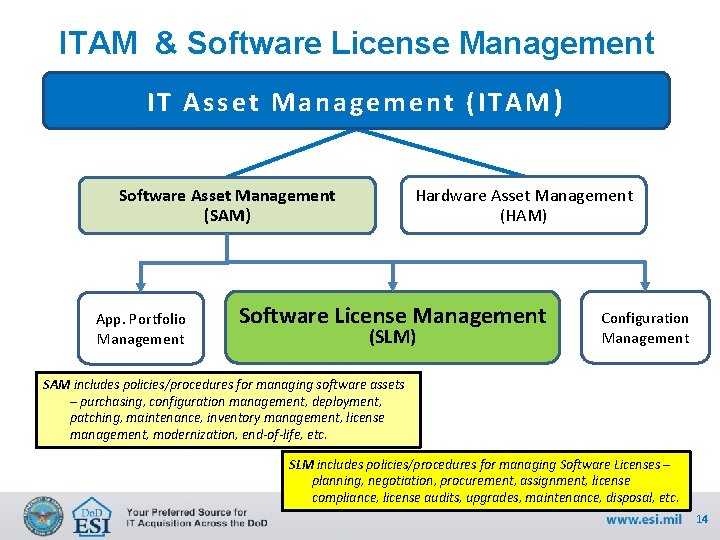
ITAM & Software License Management IT Asset Management (ITAM) Hardware Asset Management (HAM) Software Asset Management (SAM) App. Portfolio Management Software License Management (SLM) Configuration Management SAM includes policies/procedures for managing software assets – purchasing, configuration management, deployment, patching, maintenance, inventory management, license management, modernization, end-of-life, etc. SLM includes policies/procedures for managing Software Licenses – planning, negotiation, procurement, assignment, license compliance, license audits, upgrades, maintenance, disposal, etc. 14

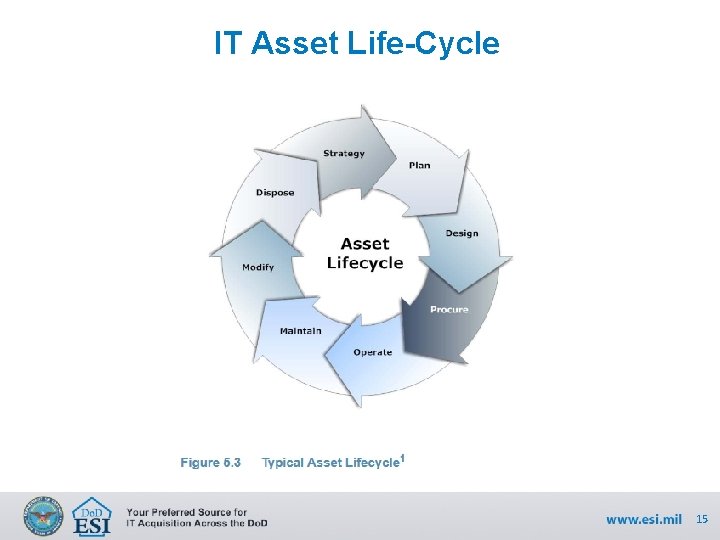
IT Asset Life-Cycle 15

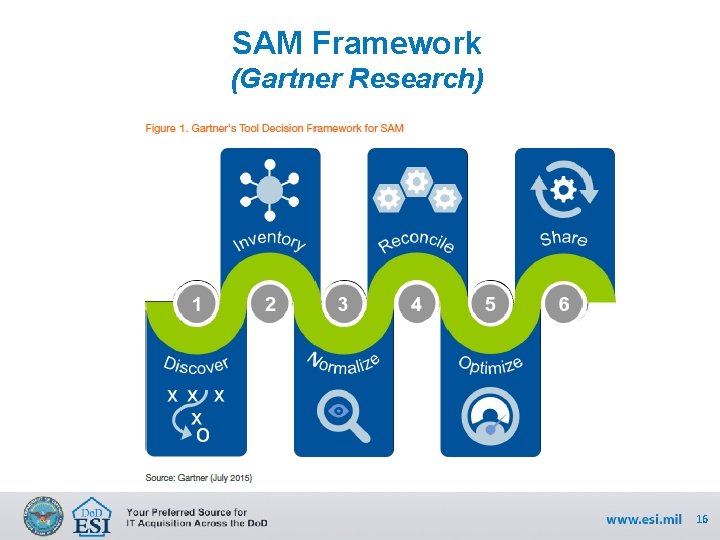
SAM Framework (Gartner Research) 16

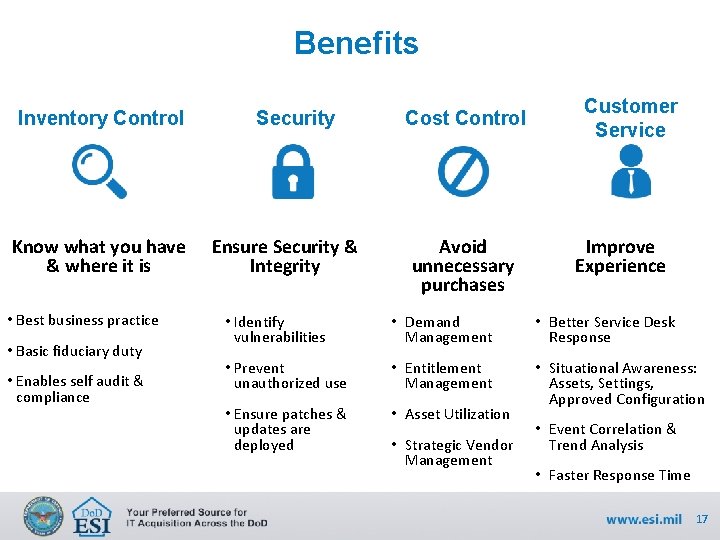
Benefits Inventory Control Know what you have & where it is • Best business practice • Basic fiduciary duty • Enables self audit & compliance Security Ensure Security & Integrity Cost Control Avoid unnecessary purchases Customer Service Improve Experience • Identify vulnerabilities • Demand Management • Better Service Desk Response • Prevent unauthorized use • Entitlement Management • Ensure patches & updates are deployed • Asset Utilization • Situational Awareness: Assets, Settings, Approved Configuration • Strategic Vendor Management • Event Correlation & Trend Analysis • Faster Response Time 17

SLM Solution Elements 18

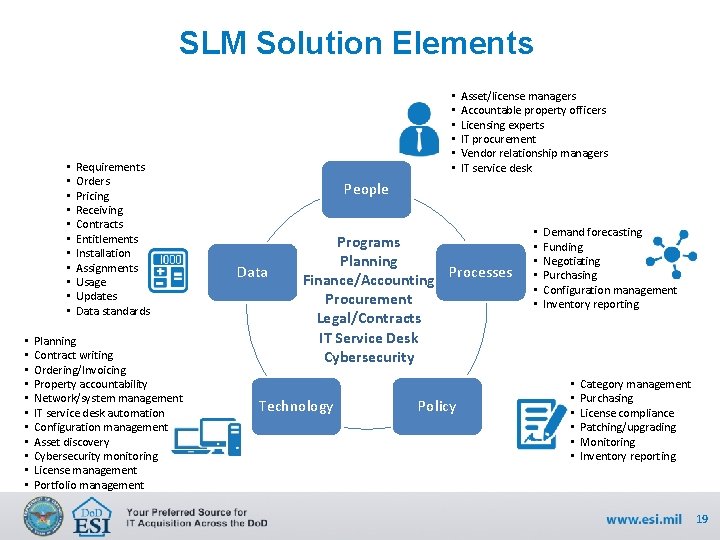
SLM Solution Elements • • • • • • Requirements Orders Pricing Receiving Contracts Entitlements Installation Assignments Usage Updates Data standards Planning Contract writing Ordering/Invoicing Property accountability Network/system management IT service desk automation Configuration management Asset discovery Cybersecurity monitoring License management Portfolio management • • • Asset/license managers Accountable property officers Licensing experts IT procurement Vendor relationship managers IT service desk People Data Programs Planning Finance/Accounting Processes Procurement Legal/Contracts IT Service Desk Cybersecurity Technology Policy • • • Demand forecasting Funding Negotiating Purchasing Configuration management Inventory reporting • • • Category management Purchasing License compliance Patching/upgrading Monitoring Inventory reporting 19

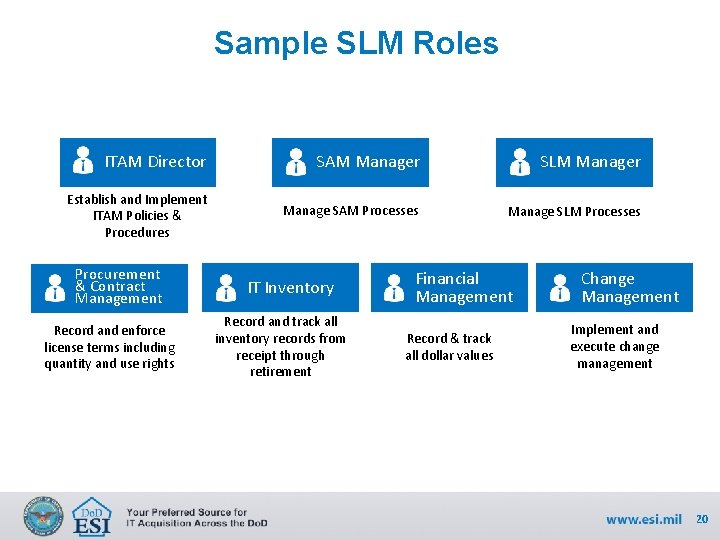
Sample SLM Roles ITAM Director SAM Manager SLM Manager Establish and Implement ITAM Policies & Procedures Manage SAM Processes Manage SLM Processes Procurement & Contract Management Record and enforce license terms including quantity and use rights IT Inventory Record and track all inventory records from receipt through retirement Financial Management Record & track all dollar values Change Management Implement and execute change management 20

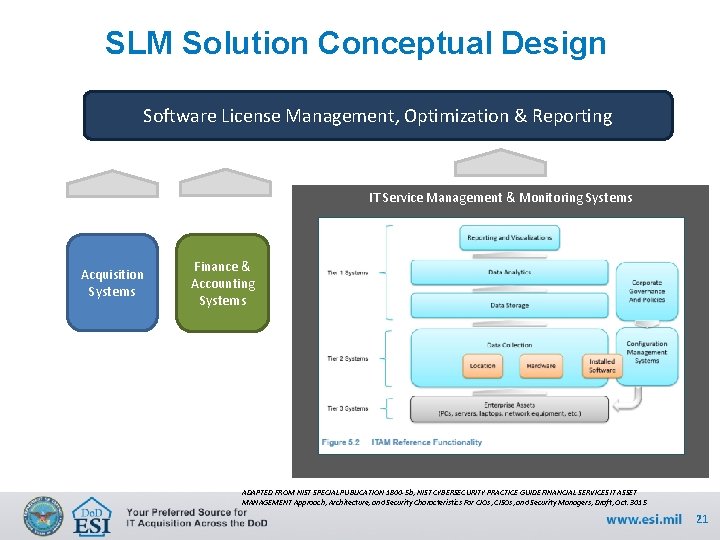
SLM Solution Conceptual Design Software License Management, Optimization & Reporting IT Service Management & Monitoring Systems Acquisition Systems Finance & Accounting Systems ADAPTED FROM NIST SPECIAL PUBLICATION 1800 -5 b, NIST CYBERSECURITY PRACTICE GUIDE FINANCIAL SERVICES IT ASSET MANAGEMENT Approach, Architecture, and Security Characteristics For CIOs, CISOs, and Security Managers, Draft, Oct. 3015 21

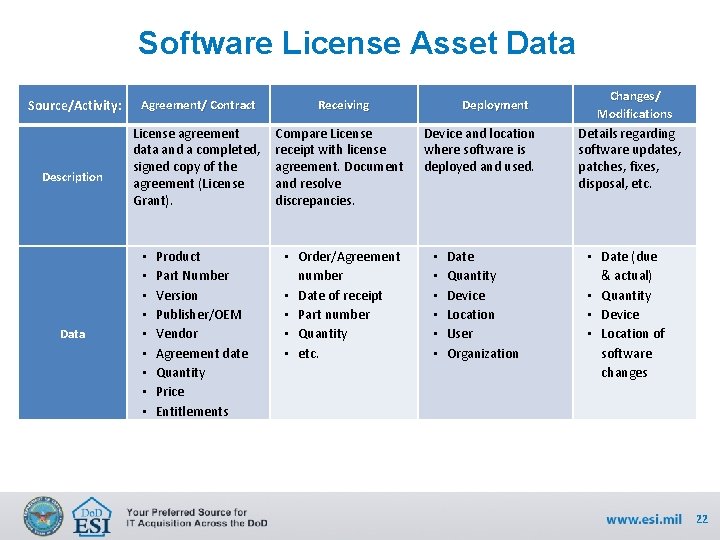
Software License Asset Data Source/Activity: Description Data Agreement/ Contract License agreement data and a completed, signed copy of the agreement (License Grant). • • • Product Part Number Version Publisher/OEM Vendor Agreement date Quantity Price Entitlements Receiving Compare License receipt with license agreement. Document and resolve discrepancies. • Order/Agreement number • Date of receipt • Part number • Quantity • etc. Deployment Changes/ Modifications Device and location where software is deployed and used. Details regarding software updates, patches, fixes, disposal, etc. Date Quantity Device Location User Organization • Date (due & actual) • Quantity • Device • Location of software changes • • • 22

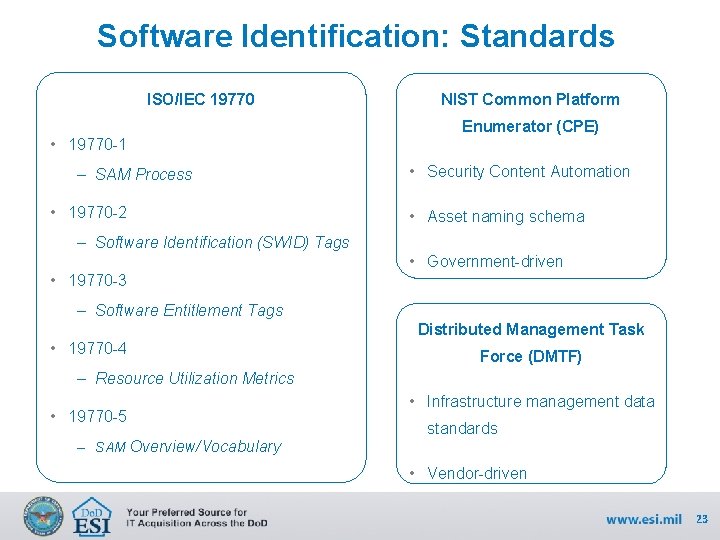
Software Identification: Standards ISO/IEC 19770 • 19770 -1 – SAM Process • 19770 -2 NIST Common Platform Enumerator (CPE) • Security Content Automation • Asset naming schema – Software Identification (SWID) Tags • Government-driven • 19770 -3 – Software Entitlement Tags Distributed Management Task • 19770 -4 Force (DMTF) – Resource Utilization Metrics • 19770 -5 • Infrastructure management data standards – SAM Overview/Vocabulary • Vendor-driven 23

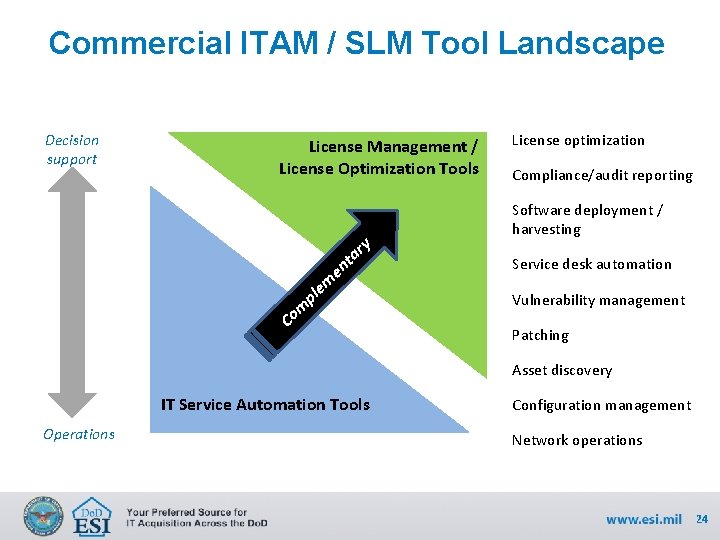
Commercial ITAM / SLM Tool Landscape Decision support License Management / License Optimization Tools y r ta en m e pl om C License optimization Compliance/audit reporting Software deployment / harvesting Service desk automation Vulnerability management Patching Asset discovery IT Service Automation Tools Operations Configuration management Network operations 24

Do. D Way Ahead 25

Do. D Software License Inventory Reporting Plan Requirement • FY 14 NDAA Sec. 935: Plan for an enterprise-wide automated software license inventory reporting process. • Goal: To optimize the acquisition and use of software licenses. • Approach: Leverage acquisition, finance and cybersecurity continuous monitoring systems Implementation Strategy • Build on existing efforts to collect and report SLM data -– Financial data & audit trail: Leverage Financial Improvement and Audit Readiness (FIAR) Internal Use Software (IUS) policy, guidance, business systems, and reporting processes – License inventory status: Leverage Cybersecurity Information Security Continuous Monitoring (ISCM) [Asset Management, Configuration Management, License Management] – Analysis & Reporting: Implement reports and dashboards in ISCM reporting environment – License Optimization: Leverage the Do. D Enterprise Software Initiative (Do. D ESI) • • IT Category Management Strategic Vendor Management (SVM) Enterprise licenses Enterprise purchasing vehicles 26

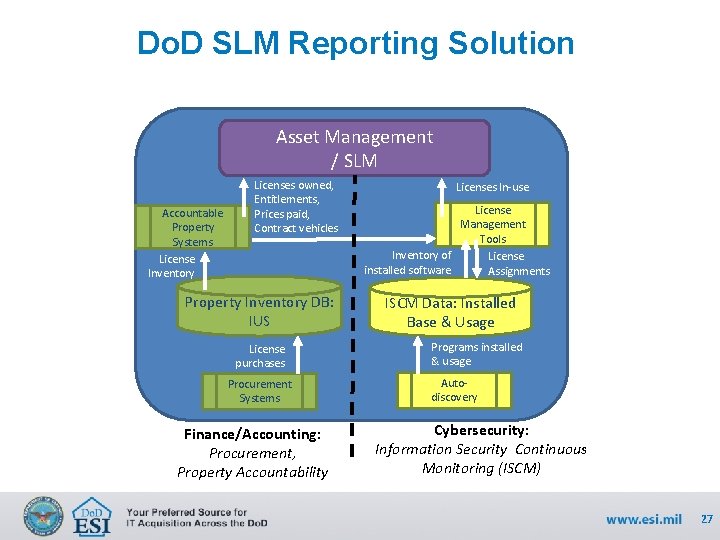
Do. D SLM Reporting Solution Asset Management / SLM Accountable Property Systems License Inventory Licenses owned, Entitlements, Prices paid, Contract vehicles Property Inventory DB: IUS License purchases Procurement Systems Finance/Accounting: Procurement, Property Accountability Licenses In-use License Management Tools Inventory of License installed software Assignments ISCM Data: Installed Base & Usage Programs installed & usage Autodiscovery Cybersecurity: Information Security Continuous Monitoring (ISCM) 27

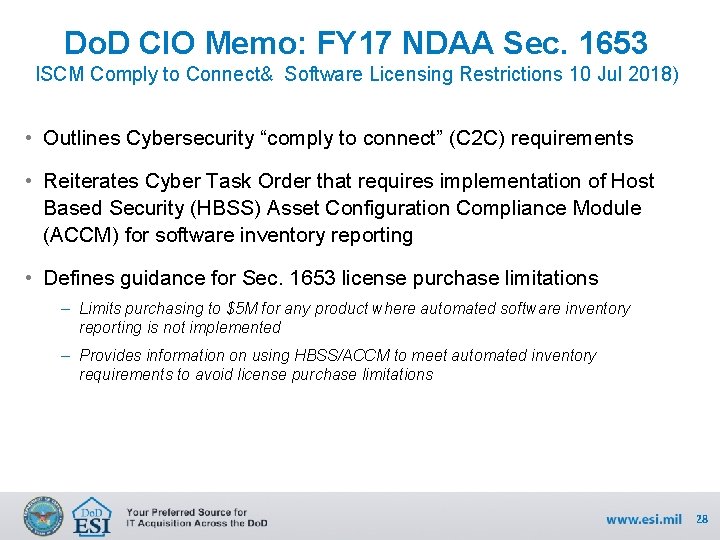
Do. D CIO Memo: FY 17 NDAA Sec. 1653 ISCM Comply to Connect& Software Licensing Restrictions 10 Jul 2018) • Outlines Cybersecurity “comply to connect” (C 2 C) requirements • Reiterates Cyber Task Order that requires implementation of Host Based Security (HBSS) Asset Configuration Compliance Module (ACCM) for software inventory reporting • Defines guidance for Sec. 1653 license purchase limitations – Limits purchasing to $5 M for any product where automated software inventory reporting is not implemented – Provides information on using HBSS/ACCM to meet automated inventory requirements to avoid license purchase limitations 28

Accounting for Internal Use Software (IUS) • Reconvened IUS Account Working Group in May • Clarifying guidance for implementation of DODI 5000. 76 for Management and Accountability of IUS • Developing use cases for accounting for software licenses • Identifying Do. D Component property accountability systems for IUS • Facilitating requirements definition for IUS management and reporting enhancements for the Defense Property Accountability System (DPAS) 29

Implementation Status • ISCM Organizational Software Inventory Report – Phase 1 base software inventory report was implemented in the Cybersecurity Continuous Monitoring Risk Scoring (CMRS) dashboard system in April 2018 – CMRS inventory report shows counts for installed software inventory, by Component – Planned enhancements include software usage metrics • IUS asset inventory – IUS management function implemented in the Defense Property Accountability System (DPAS) in May 2018 – Planned enhancements include inventory reporting • Integration & License Management – Initiating planning for: • • ISCM software identification Procurement data standards for software purchasing APSR & ISCM data integration License management and optimization solutions 30

Federal & Do. D Guidance 31

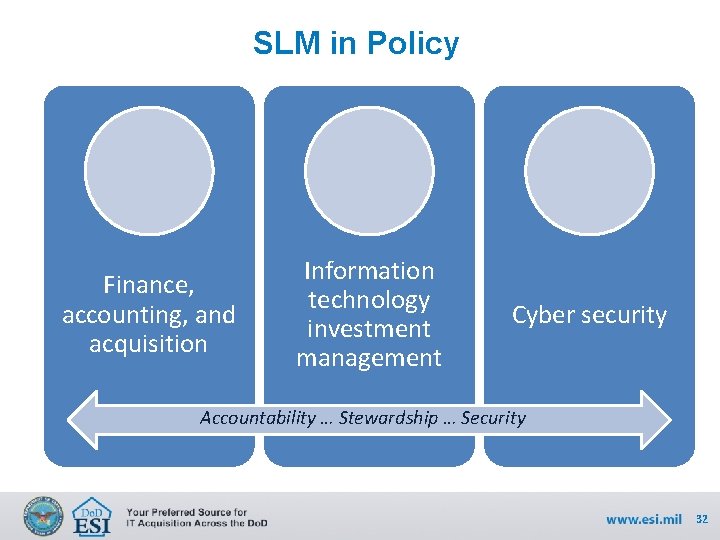
SLM in Policy Finance, accounting, and acquisition Information technology investment management Cyber security Accountability … Stewardship … Security 32

Federal SLM Government Policy & Guidance: Foundation 1. 2. 3. 4. Federal Policy & Guidance Reference Description Clinger-Cohen Act (1996) / USC Title 40 CIO Act / USC Title 10 Do. D CIO Designed to improve the way the federal government acquires, uses and disposes IT. Title 10 defines additional responsibilities for Do. D & MILDEP CIOs. Executive Order 13103 – Computer Software Piracy (December 1998) Prevent and combat computer software piracy by U. S. Government Agencies. Establish procedures to ensure that the agency has present on its computers and uses only computer software not in violation of applicable copyright laws, including: (1) installed software inventories of the software on its computers; (2) authorization software inventories; and (3) adequate recordkeeping systems. Executive Order 13589 – Promoting Efficient Spending (November 2011) Sec. 4. IT Devices. Assess current device inventories and usage…ensure that they are not paying for unused or underutilized IT equipment, installed software, or services…consider agency-wide IT solutions for desktop services, email, and collaboration tools. NIST Information Security Continuous Monitoring (SP 800 -137) SP 800 -137: (Asset Management) Maintain inventory of software and hardware within the organization. (License Management) Track license compliance, monitor usage status, and manage the software asset life cycle. 33

Federal SLM Policy & Guidance: Current Priorities Federal Policy & Guidance Reference Description 5. GAO-14 -413 Federal Software Licenses: Better Management Needed to Achieve Significant Savings Government-Wide May 2014 report that recommends adoption of leading practices for software license management across the Federal government 6. Federal IT Acquisition Reform Act (FITARA) / FY 15 NDAA Includes provisions that require the federal government to: inventory all IT and develop a federal strategic sourcing initiative for the use of government-wide software user license agreements. FITARA was included NDAA FY 15. OMB Category Management Policy 161: Improving the Acquisition and Management of Common IT: Software Licensing (June 2016) Implements FITARA provisions for commercial software licenses. Requires agency CIOs to establish comprehensive software license management policy to: compile agency-wide license inventory; analyze inventory data to ensure compliance, consolidate redundant applications, and identify cost-savings opportunities; increase use of government-wide “best in class” purchasing agreement to reduce duplicative contract vehicles; ensure appropriate personnel have received adequate training in SLM; and, collect and report metrics on cost savings. MEGABYTE Act (Making Electronic Government Accountable By Yielding Tangible Efficiencies, Public Law 114 -210, July 2016) Requires OMB to issue a directive on the management of software licenses, requiring executive agency CIOs to develop comprehensive SLM policy that requires: establish a comprehensive license inventory using automated discovery and inventory tools; regularly track and maintain software licenses; analyze software usage to make cost-effective decisions; provide SLM training; establish SLM goals and objectives; and, consider the software license management life cycle phases to implement effective decision making and incorporate existing standards, processes, and metrics. 7. 8. 34

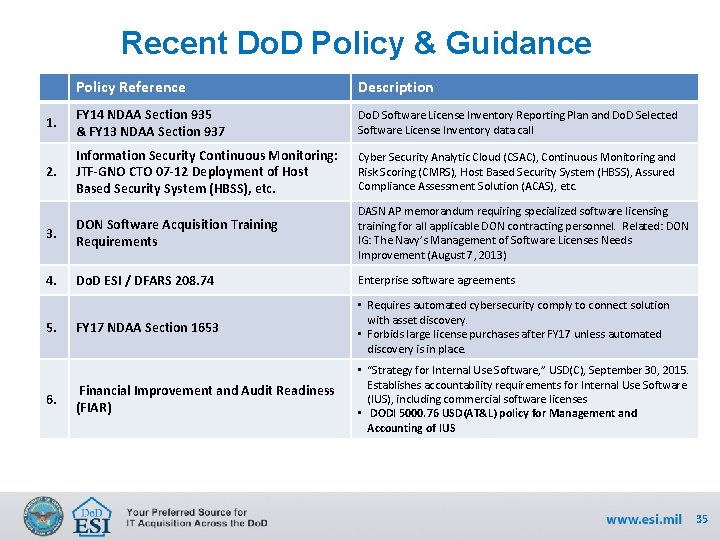
Recent Do. D Policy & Guidance Policy Reference Description 1. FY 14 NDAA Section 935 & FY 13 NDAA Section 937 Do. D Software License Inventory Reporting Plan and Do. D Selected Software License Inventory data call 2. Information Security Continuous Monitoring: JTF-GNO CTO 07 -12 Deployment of Host Based Security System (HBSS), etc. Cyber Security Analytic Cloud (CSAC), Continuous Monitoring and Risk Scoring (CMRS), Host Based Security System (HBSS), Assured Compliance Assessment Solution (ACAS), etc. 3. DON Software Acquisition Training Requirements DASN AP memorandum requiring specialized software licensing training for all applicable DON contracting personnel. Related: DON IG: The Navy’s Management of Software Licenses Needs Improvement (August 7, 2013) 4. Do. D ESI / DFARS 208. 74 Enterprise software agreements FY 17 NDAA Section 1653 • Requires automated cybersecurity comply to connect solution with asset discovery. • Forbids large license purchases after FY 17 unless automated discovery is in place. Financial Improvement and Audit Readiness (FIAR) • “Strategy for Internal Use Software, ” USD(C), September 30, 2015. Establishes accountability requirements for Internal Use Software (IUS), including commercial software licenses • DODI 5000. 76 USD(AT&L) policy for Management and Accounting of IUS 5. 6. 35

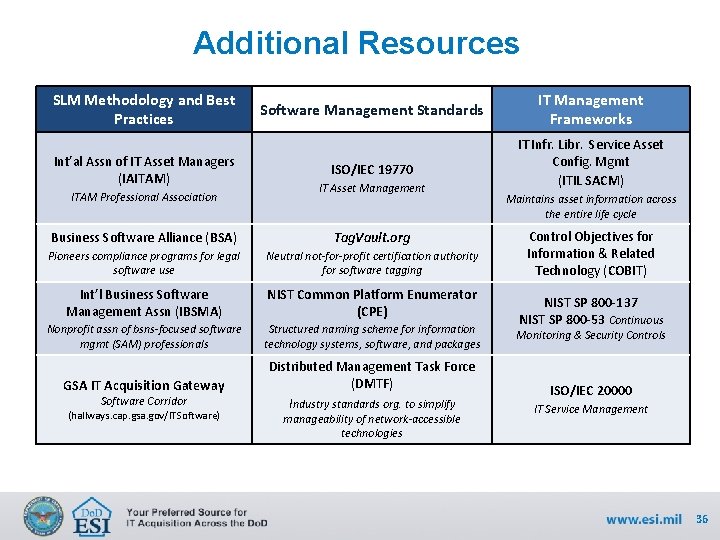
Additional Resources SLM Methodology and Best Practices Int’al Assn of IT Asset Managers (IAITAM) ITAM Professional Association Software Management Standards ISO/IEC 19770 IT Asset Management IT Management Frameworks IT Infr. Libr. Service Asset Config. Mgmt (ITIL SACM) Maintains asset information across the entire life cycle Control Objectives for Information & Related Technology (COBIT) Business Software Alliance (BSA) Tag. Vault. org Pioneers compliance programs for legal software use Neutral not-for-profit certification authority for software tagging Int’l Business Software Management Assn (IBSMA) NIST Common Platform Enumerator (CPE) Nonprofit assn of bsns-focused software mgmt (SAM) professionals Structured naming scheme for information technology systems, software, and packages Monitoring & Security Controls GSA IT Acquisition Gateway Distributed Management Task Force (DMTF) Industry standards org. to simplify ISO/IEC 20000 Software Corridor (hallways. cap. gsa. gov/ITSoftware) manageability of network-accessible technologies NIST SP 800 -137 NIST SP 800 -53 Continuous IT Service Management 36

Questions? Please submit your questions via webinar chat or use “Ask an Expert” function on www. ESI. mil. Briefing slides are posted to www. ESI. mil for download. Visit www. ESI. mil For additional IT acquisition resources and training information 37

BACKUP 38

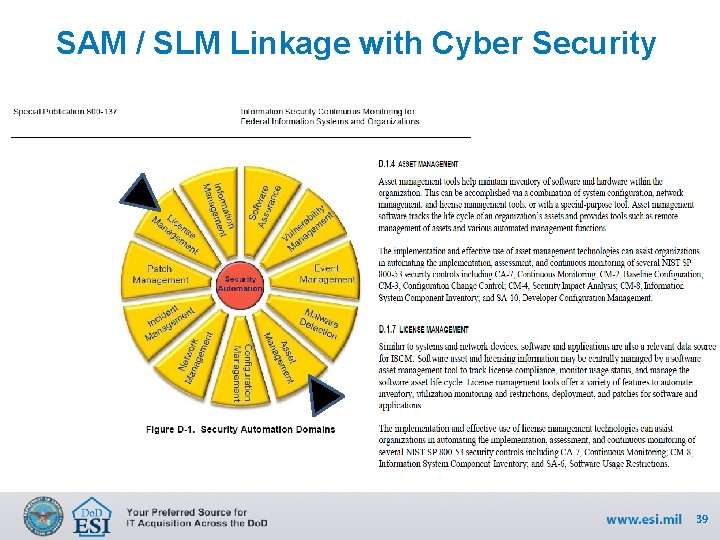
SAM / SLM Linkage with Cyber Security 39

Software License Management (SLM) A mechanism for systematically ensuring compliance with system vendor and independent software vendor (ISV) software licenses — for example, maximum users, maximum nodes and maximum MIPS. (Gartner IT Glossary, May 7, 2015) 40

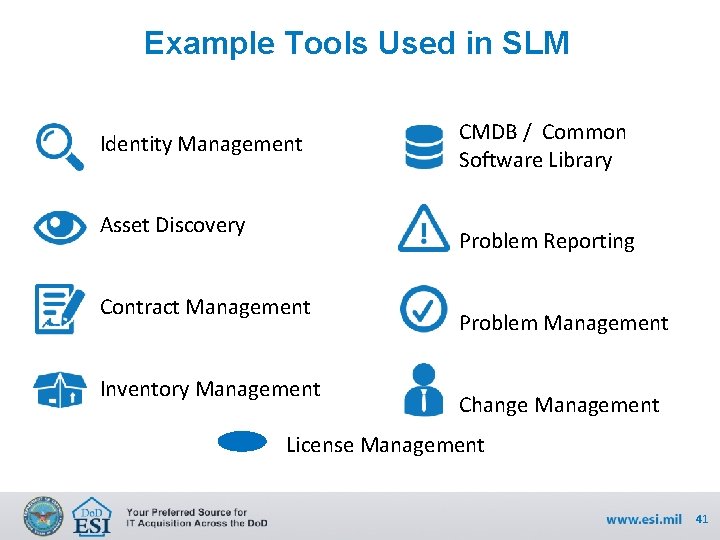
Example Tools Used in SLM Identity Management Asset Discovery CMDB / Common Software Library Problem Reporting Contract Management Inventory Management Problem Management Change Management License Management 41