Information System IS Audit Concept Process and Implementation





















- Slides: 65

Information System (IS) Audit. Concept Process and Implementation Developing a Risk-based Audit Plan Roshan Regmi IT/MIS Department Nepal Underhill Bank Limited Kathy October 2009 Vice-President, Risk and Internal Audit December 2005

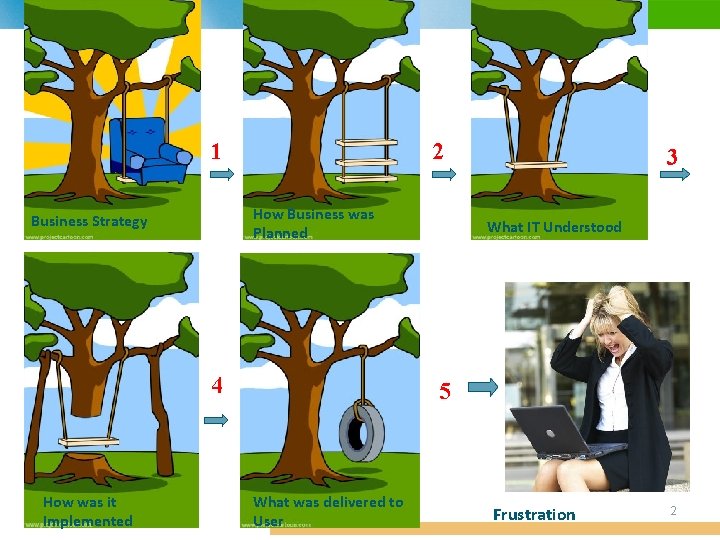
1 2 How Business was Planned Business Strategy 4 How was it Implemented 3 What IT Understood 5 What was delivered to User Frustration 2

Outline n Snapshots n Information System Fundamentals n Core Banking System Basics n IS Audit Responsibilities n COSO Framework n COSO ERM Framework n Risk Based IS Audit and Examples n Co. BIT Framework n Using Co. BIT in IS Audit

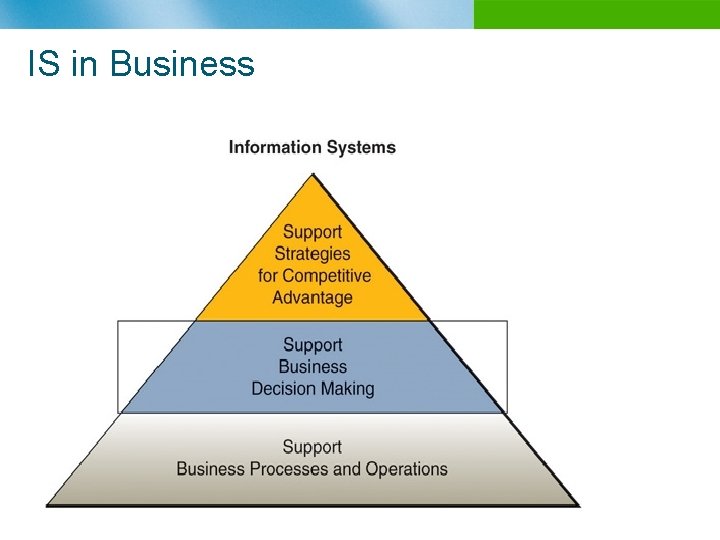
IS in Business

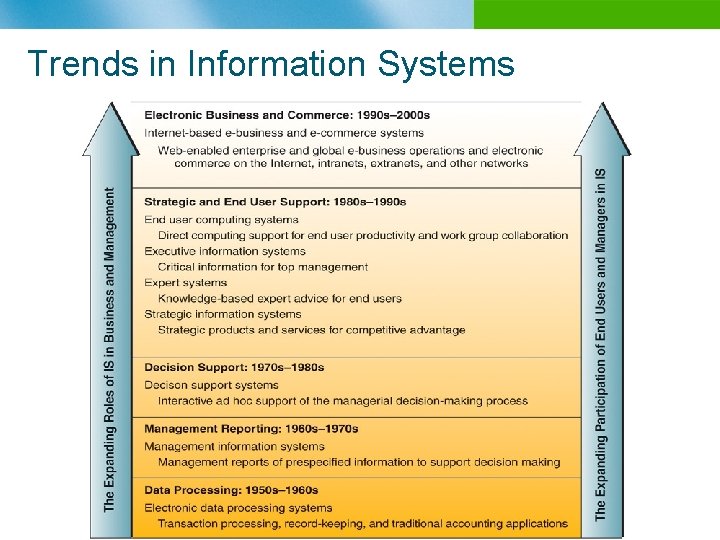
Trends in Information Systems

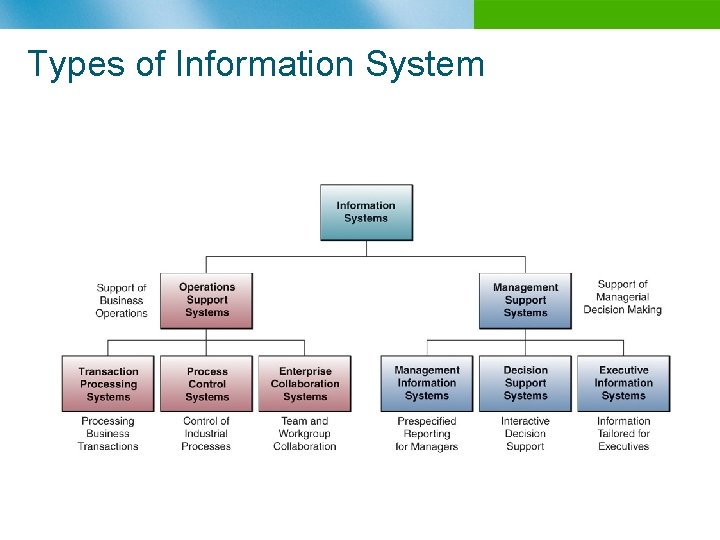
Types of Information System

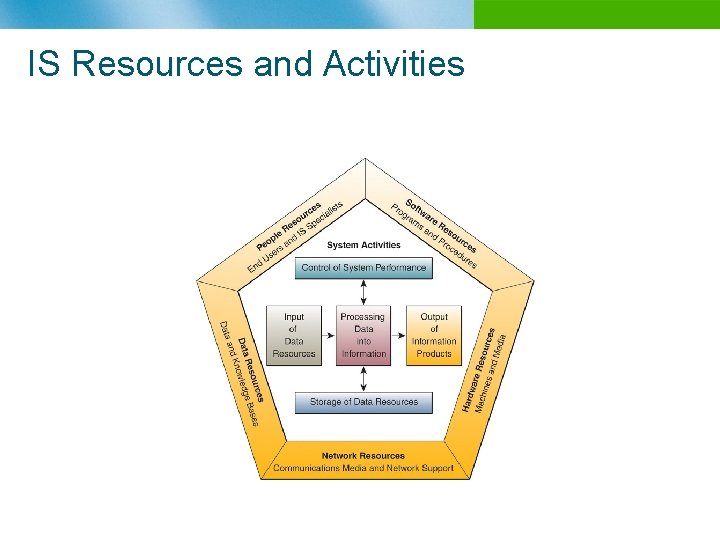
IS Resources and Activities

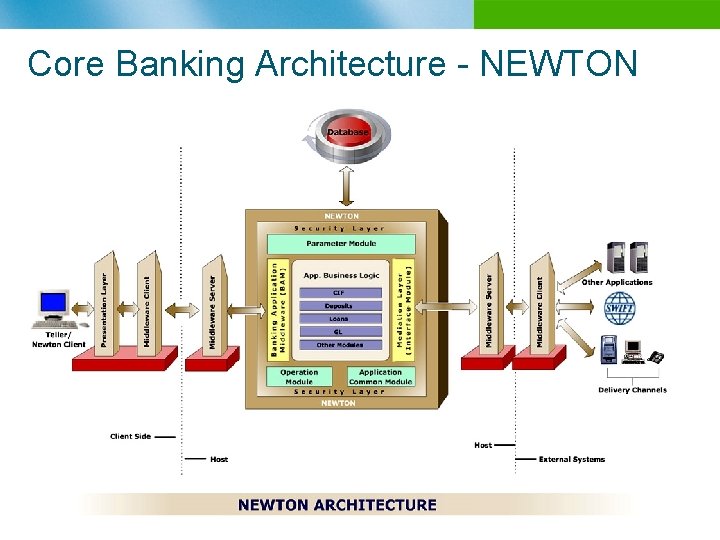
Core Banking Architecture - NEWTON

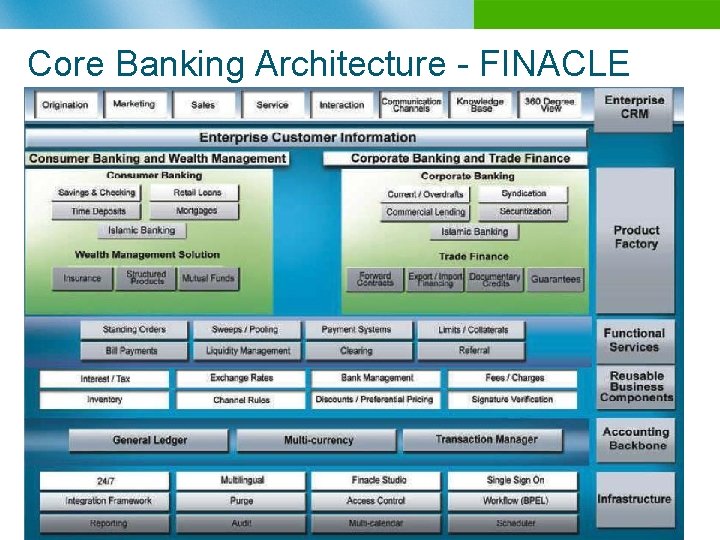
Core Banking Architecture - FINACLE

Information System Audit “the process of collecting and evaluating evidence to determine whether acomputer system (information system) safeguards assets, maintains data integrity, achieves organizational goals effectively and consumes resources efficiently “ q Purpose of IS Audit q Will the organization's computerized systems be available for the business at all times when required? (Availability) q Will the information in the systems be disclosed only to authorized users? (Confidentiality) q Will the information provided by the system always be accurate, reliable, and timely? (Integrity).

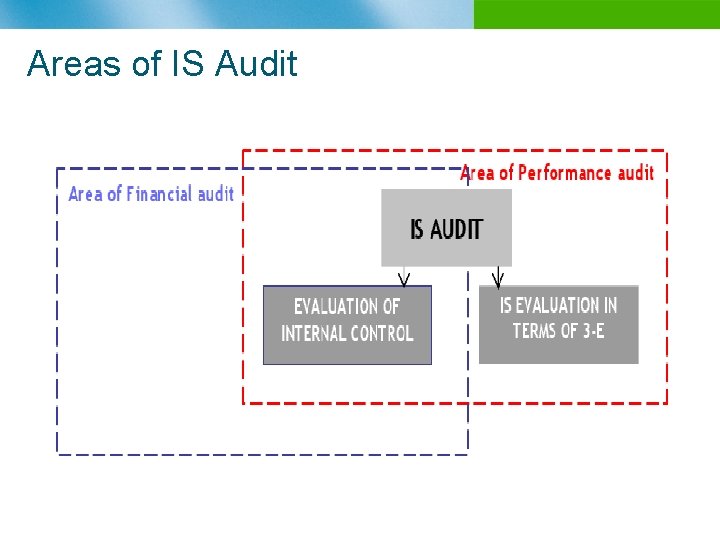
Areas of IS Audit

Spectrum of IS Audit n Systems and Applications: An audit to verify that systems and applications are appropriate, are efficient, and are adequately controlled to ensure valid, reliable, timely, and secure input, processing, and output at all levels of a system's activity n Information Processing Facilities: An audit to verify that the processing facility is controlled to ensure timely, accurate, and efficient processing of applications under normal and potentially disruptive conditions n Systems Development: An audit to verify that the systems under development meet the objectives of the organization, and to ensure that the systems are developed in accordance with generally accepted standards for systems development n Management of IT and Enterprise Architecture: An audit to verify that IT management has developed an organizational structure and procedures to ensure a controlled and efficient environment for information processing n Client/Server, Telecommunications, Intranets, and Extranets: An audit to verify that controls are in place on the client (computer receiving services), server, and on the network connecting the clients and servers

IS Audit Responsibilities Audit Roles Strategic risk assurance Participate in oversight committee for the risk and management process Test management’s mitigation policy Business n n n n Test/verify assumptions behind key decisions Risks Product line expansion Acquisitions/JV/Dive stiture Threats to company reputation Shift in market competitive dynamics n n n New Capabilities Transfer strategic risks into auditable risk activities Link strategic direction to risk priorities Identify and incorporate external conditions into audit plans

IS Audit Responsibilities Audit Roles Operational Identify risk trends and communicate to n n n n management Facilitate continuous improvement of controls Recommend improvements on the adequacy and effectiveness of management’s risk processes Identify gaps in management’s plans to achieve goals Risks Ineffective risk management system Supply chain and outsourcing management Customer contact quality n n n New Capabilities Risk management experience Understand company’s corporate values and goals Understand company’s IT infrastructure

IS Audit Responsibilities Audit Roles Financial Perform proactive, risk-based audit of management processes Reporting Drive self-service tool usage for management testing and Evaluate effectiveness of controls encompassing reliability and integrity of Regulatory financial information based upon risk Compliance assessments n n n Risks Inaccurate financial statements Noncompliance with laws, regulations, contracts Integrity of financial information n n New Capabilities Maintain self-service tools Continuous monitoring/auditin g

COSO Framework Issued in 1992 by the Committee of Sponsoring Organization of the Treadway Commission (COSO) Framework has long served as a blueprint for establishing/Evaluate internal controls that promote efficiency, minimize risks, help ensure the reliability of financial statements, and comply with laws and regulations.

COSO – Key Components of Internal Control Environment - Integrity and Ethical Values - Commitment to Competence - BOD and Audit Committee - Management’s Philosophy and Operating Style - Organizational Structure - Assignment of Authority and Responsibility - Human Resource Policies and Procedures. Control Activities - Policies and Procedures - Security (Application and Network) - Application Change Management - Business Continuity / Backups - Outsourcing Risk Assessment - Company-wide Objectives - Process-level Objectives - Risk Identification and Analysis - Managing Change. Information and Communication - Quality of Information - Effectiveness of Communication. Monitoring - On-going Monitoring - Separate Evaluations - Reporting Deficiencies

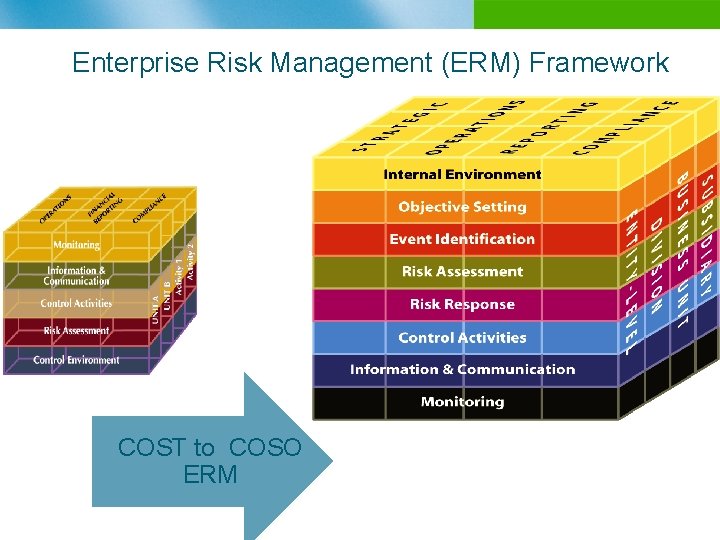
Enterprise Risk Management (ERM) Framework COST to COSO ERM

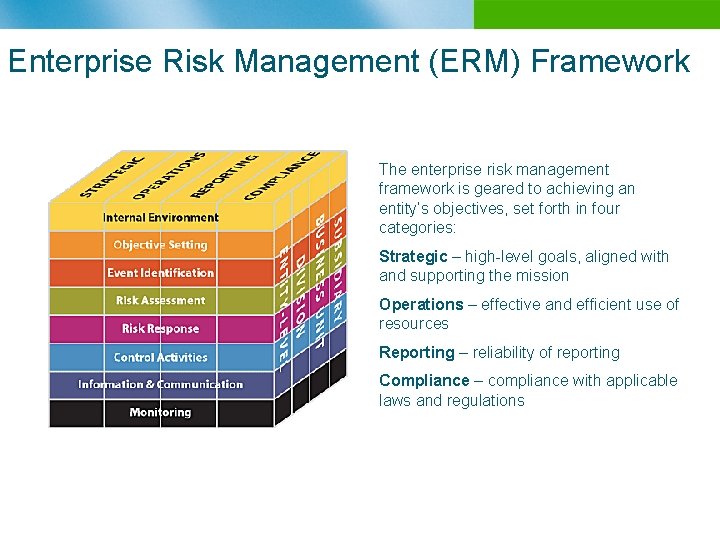
Enterprise Risk Management (ERM) Framework The enterprise risk management framework is geared to achieving an entity’s objectives, set forth in four categories: Strategic – high-level goals, aligned with and supporting the mission Operations – effective and efficient use of resources Reporting – reliability of reporting Compliance – compliance with applicable laws and regulations

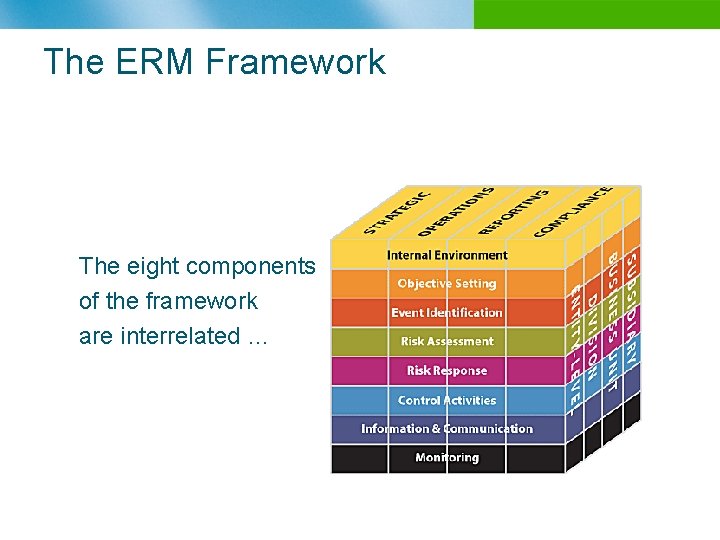
The ERM Framework The eight components of the framework are interrelated …

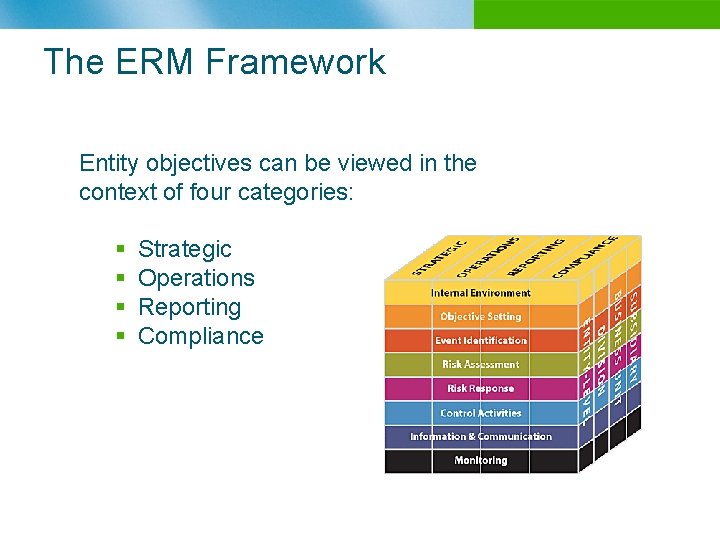
The ERM Framework Entity objectives can be viewed in the context of four categories: § § Strategic Operations Reporting Compliance

In a riskier World! n Global village – moving to a unified economy n Borderless world – a quiver of new threats n Mergers and Acquisitions – order of the day n Unprecedented dependence and pace of IT and networks used by business n Increasing potential of cyber crime n IT Operational failures n Outsourcing – an accepted way n Stringent Regulatory Compulsions n Demanding customers – online real time customers n Ethics climate!

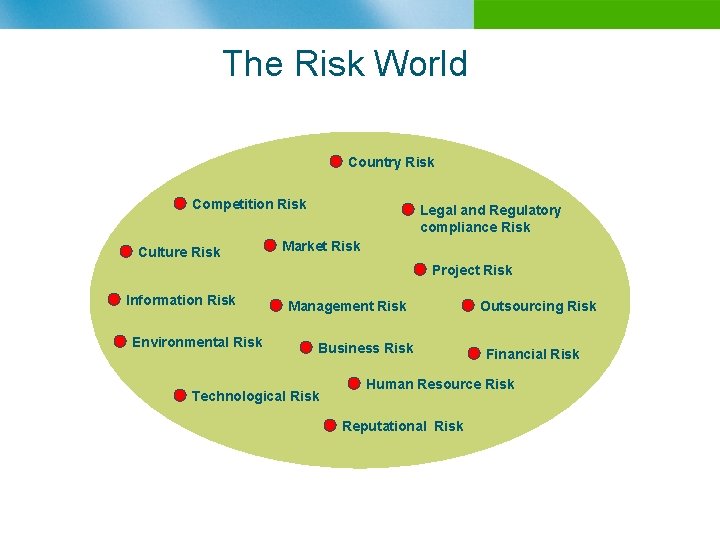
The Risk World Country Risk Competition Risk Culture Risk Legal and Regulatory compliance Risk Market Risk Project Risk Information Risk Environmental Risk Management Risk Business Risk Technological Risk Outsourcing Risk Financial Risk Human Resource Risk Reputational Risk

Using Risk Management to determine IS areas to be audited: n n Enables management to effectively allocate limited IS audit resources Provides reasonable assurance that relevant information has been obtained from all levels of management, including the board of directors and functional area management. Generally, the information includes areas that will assist management in effectively discharging their responsibilities and provides reasonable assurance that the IS audit activities are directed to high business risk areas and will add value to management. Establishes a basis for effectively managing the IS audit function Provides a summary of how the individual review subject is related to the overall organization as well as to the business plans

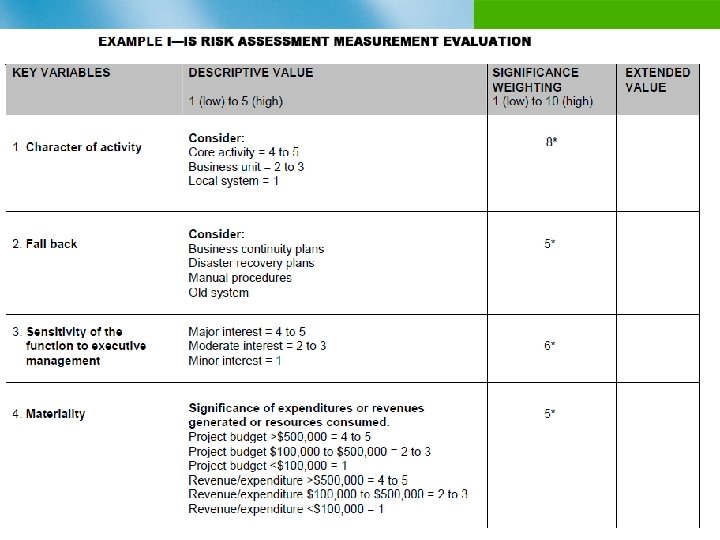
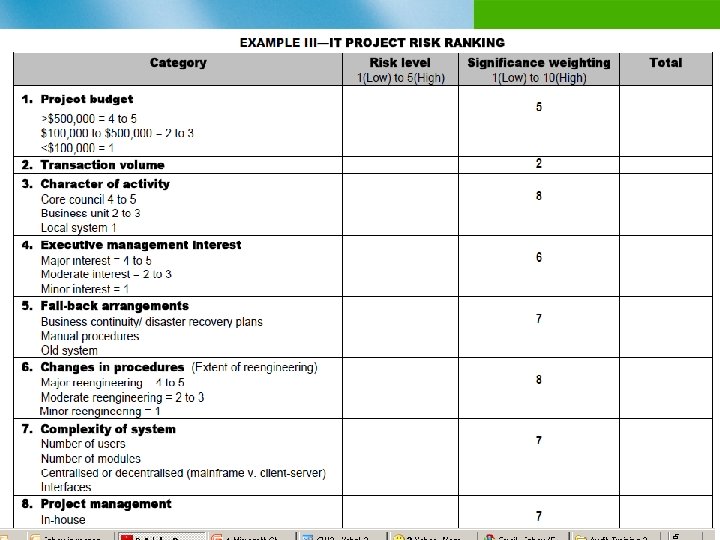
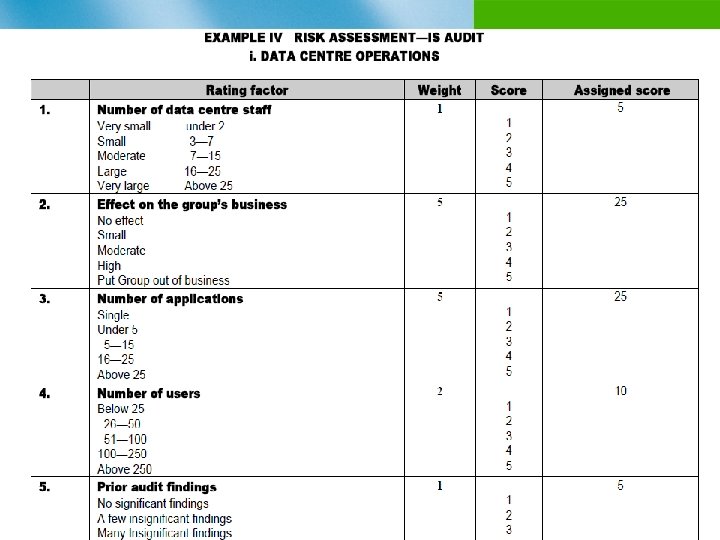
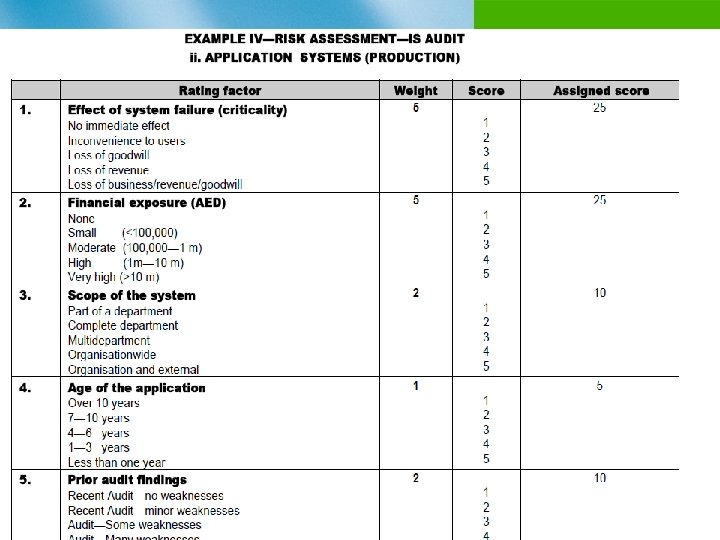
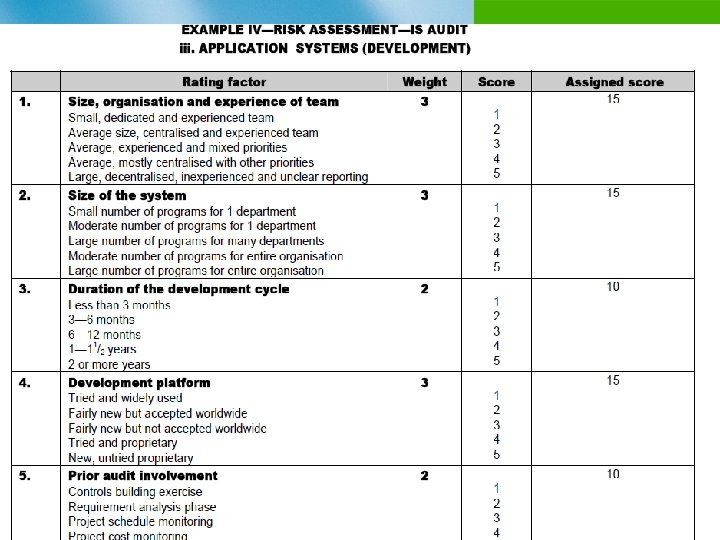
Example of an Organizational Risk Assessment Process n Identify risk factors and give them weights n Identify objectives/assets/auditable activities n Analyze the risks by considering their likelihood and consequence n Assign ratings to the risks n Review with audit client/management n Use rankings to develop audit priorities


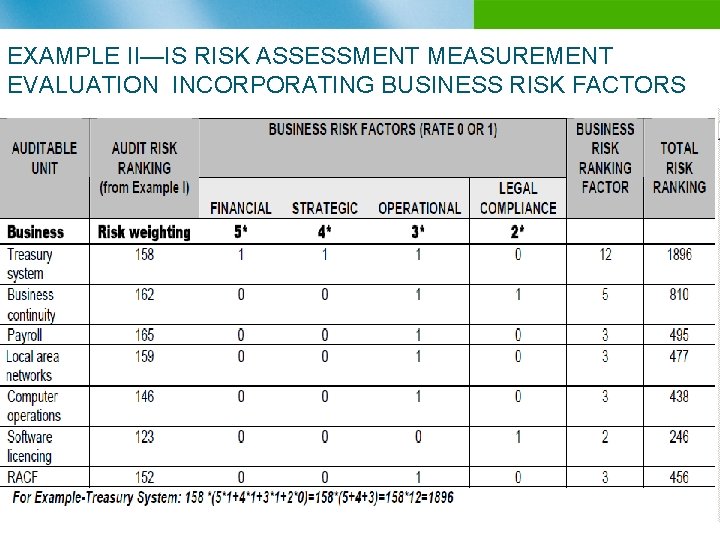
EXAMPLE II—IS RISK ASSESSMENT MEASUREMENT EVALUATION INCORPORATING BUSINESS RISK FACTORS n B


IS Risk Assessment of Auditable Units n Data centre operations n Application systems (production) n Application systems (development) n IS procurement (manpower and material) n Software package acquisition n Other IS functions



New n B

New n B

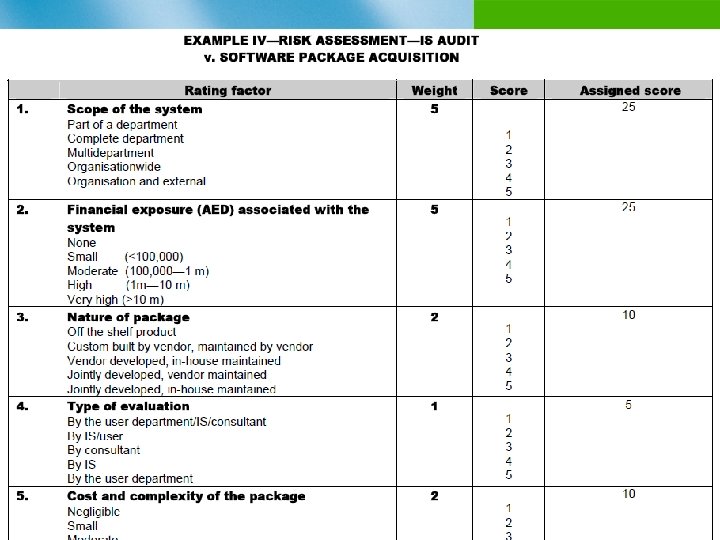
Case Study: Software Acquisition Implementation Details n n n A company has received an approval to install software to improve its services in the competitive market RFP has been developed, approved and gone for tendering process In the process of selecting a vendor based on competitive bidding 2 envelop system is adopted to ensure fairness and transparency Specifics Perceived Benefits n Enhanced services n Competitive n Better MIS reporting and Asset/Liability position Size of systems Deployment n Centralised systems n Possibility of decentralised systems n Application controls and auditing n Leased lines, Wireless IEEE 802. 11 b and VSAT Connectivity

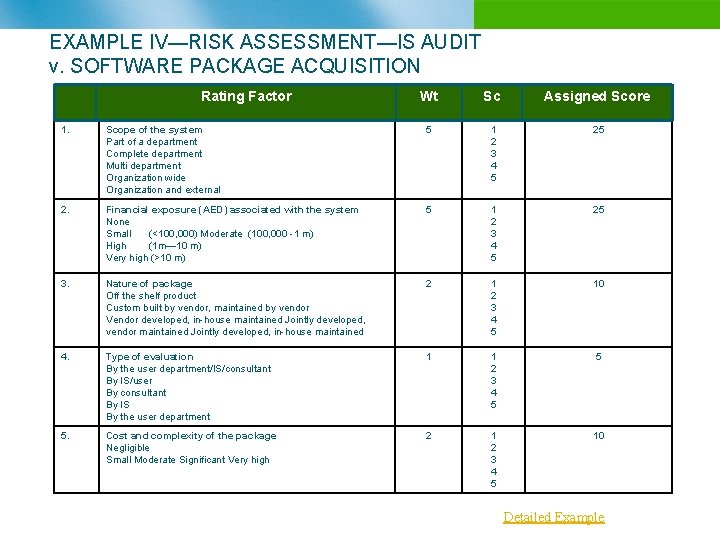
EXAMPLE IV—RISK ASSESSMENT—IS AUDIT v. SOFTWARE PACKAGE ACQUISITION Rating Factor factor Rating Weight Wt Score Sc Assigned score Assigned 1. Scope of the system Part of a department Complete department Multi department Organization wide Organization and external 5 1 2 3 4 5 25 2. Financial exposure (AED) associated with the system None Small (<100, 000) Moderate (100, 000 -1 m) High (1 m— 10 m) Very high (>10 m) 5 1 2 3 4 5 25 3. Nature of package Off the shelf product Custom built by vendor, maintained by vendor Vendor developed, in-house maintained Jointly developed, vendor maintained Jointly developed, in-house maintained 2 1 2 3 4 5 10 4. Type of evaluation By the user department/IS/consultant By IS/user By consultant By IS By the user department 1 1 2 3 4 5 5 5. Cost and complexity of the package Negligible Small Moderate Significant Very high 2 1 2 3 4 5 10 Detailed Example Score

Co. BIT Framework n n Control Objectives for Information and related Technology (COBIT) is a set of best practices (framework) for information technology (IT) management created by the Information Systems Audit and Control Association (ISACA), and the IT Governance Institute (ITGI) in 1996. COBIT provides managers, auditors, and IT users with a set of generally accepted measures, indicators, processes and best practices to assist them in maximizing the benefits derived through the use of information technology and developing appropriate IT governance and control in a company

Co. BIT Background n “Generally applicable and accepted international standard of good practice for IT control” C OB I T n Control OBjectives for Information and Related Technology “An authoritative, up-to-date, international set of generally accepted Information Technology Control Objectives for day-to-day use by business managers and auditors. ”

Co. BIT’s Scope and Objectives n n COBIT® 4. 0 was developed and by the IT Governance Institute (www. itgi. org) and was released in December, 2005 COBIT® has evolved into an IT governance / control framework: n n A toolkit of “best practices” for IT control representing the consensus of experts IT Governance focus Linkage with business requirements (bridges the gap between control requirements, technical issues, and business risks). Management – process owner – orientation (accountability) n Measurement and maturity driven n Generic focus – applicable to multiple environments n Organizes IT activities into a generally accepted process model (in alignment with ITIL, ISO, and other relevant ‘best practices’) n Identifies the major IT resources to be leveraged n Defines control objectives and associated assurance guidelines

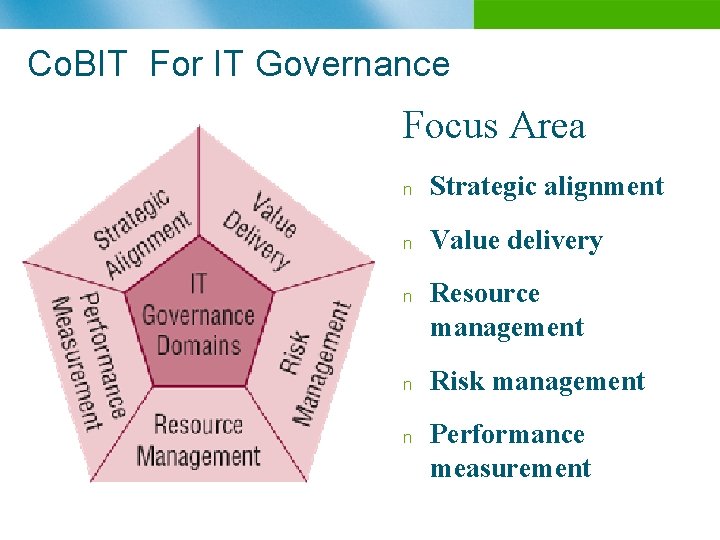
Co. BIT For IT Governance Focus Area n Strategic alignment n Value delivery n n n Resource management Risk management Performance measurement

Co. BIT As A Framework n n n Enables the auditor to review specific IT processes against COBIT’s Control Objectives to determine where controls are sufficient or advise management where processes need to be improved. Helps process owners answer questions - “Is what I’m doing adequate and in line with best practices? If not, what should I be doing and where should I focus my efforts? ” COBIT® is a framework and is NOT exhaustive or definitive. The scope and breadth of a COBIT® implementation varies from organization to organization. COBIT® prescribes “what” best practices should be in place. An effective implementation requires that COBIT® be supplemented with other sources of best practice that prescribe the “how” for IT governance and controlled process execution.

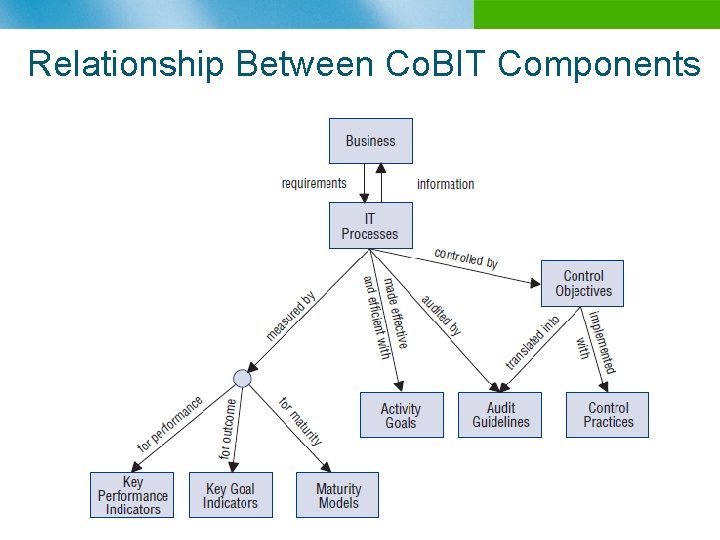
Relationship Between Co. BIT Components n B

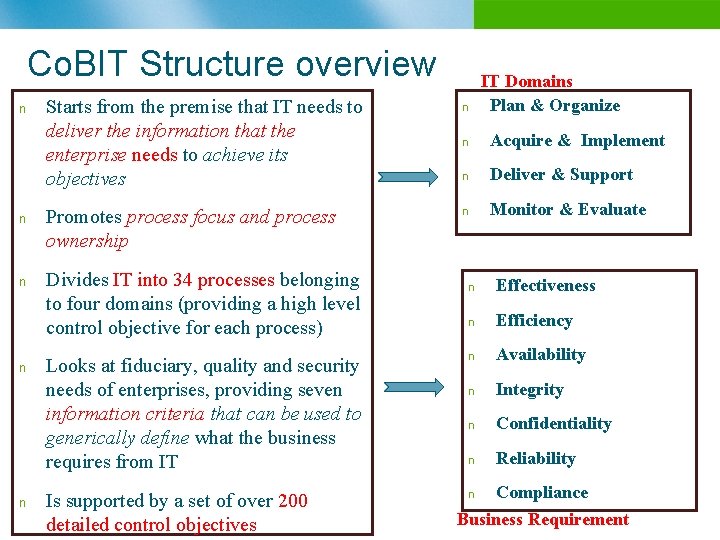
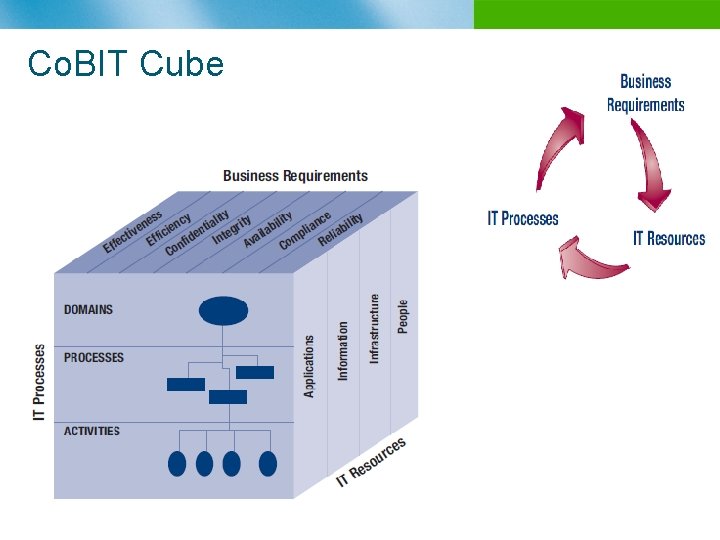
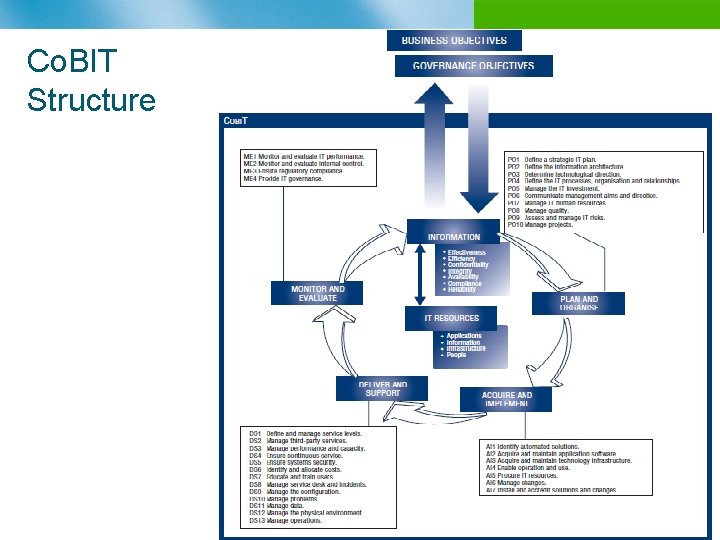
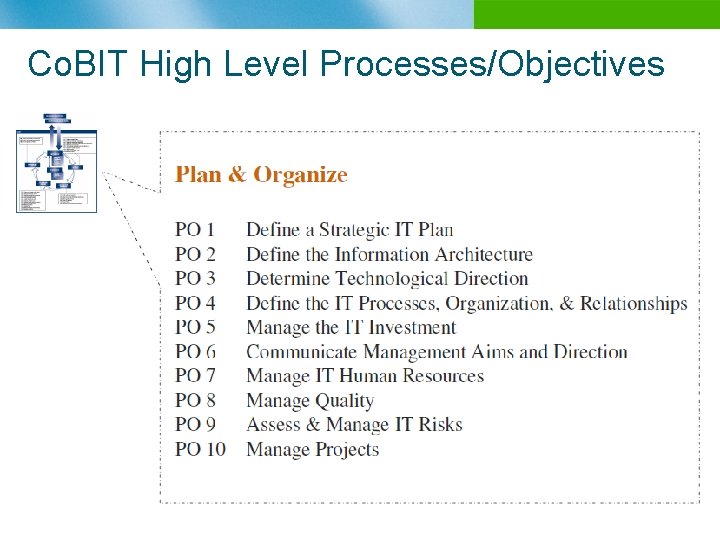
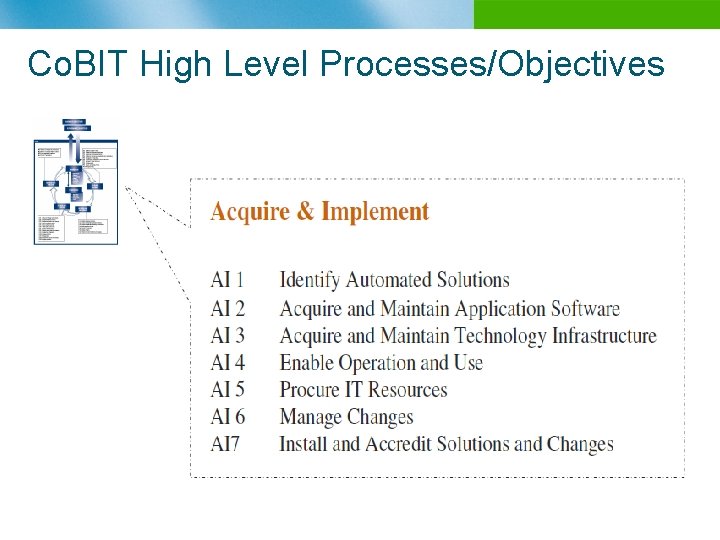
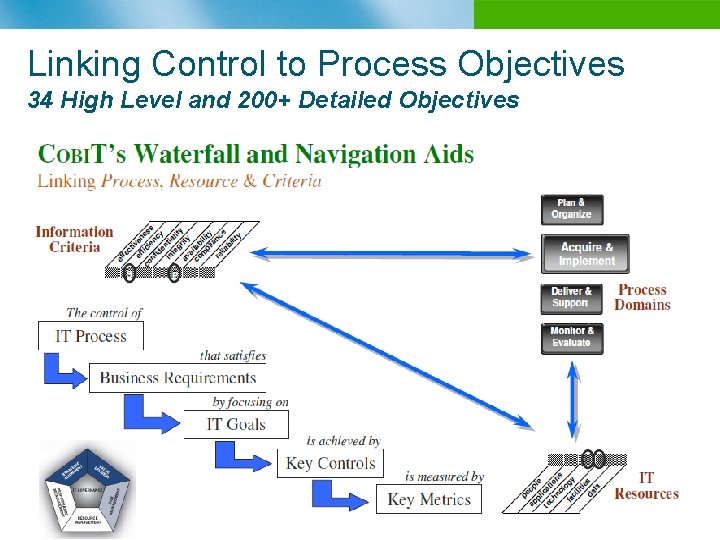
Co. BIT Structure overview n n n Starts from the premise that IT needs to deliver the information that the enterprise needs to achieve its objectives Promotes process focus and process ownership Divides IT into 34 processes belonging to four domains (providing a high level control objective for each process) Looks at fiduciary, quality and security needs of enterprises, providing seven information criteria that can be used to generically define what the business requires from IT Is supported by a set of over 200 detailed control objectives n IT Domains Plan & Organize n Acquire & Implement n Deliver & Support n Monitor & Evaluate n Effectiveness n Efficiency n Availability n Integrity n Confidentiality n Reliability Compliance Business Requirement n

Co. BIT Cube n B

Co. BIT Structure

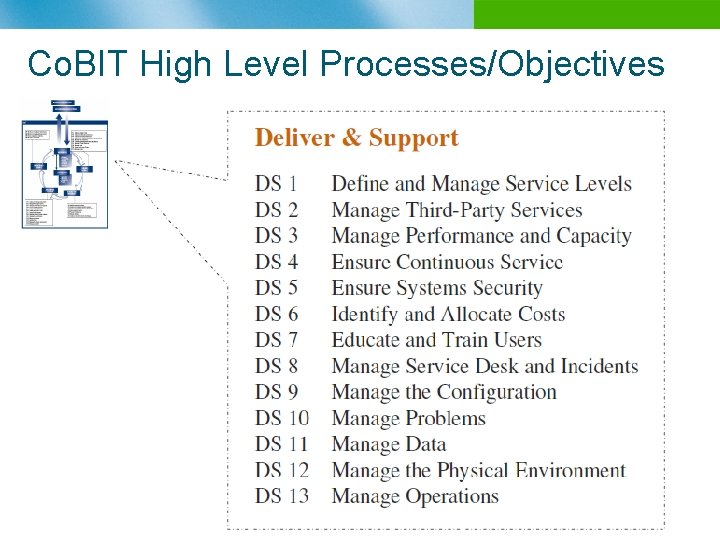
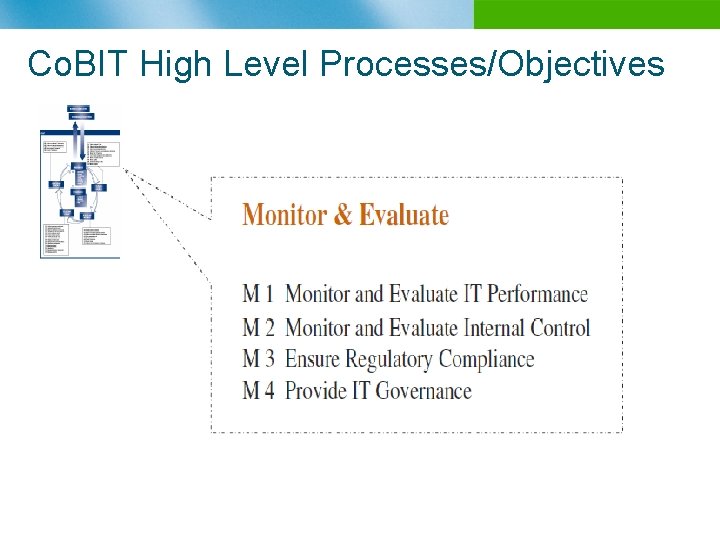
Co. BIT High Level Processes/Objectives n B

Co. BIT High Level Processes/Objectives n B

Co. BIT High Level Processes/Objectives n B

Co. BIT High Level Processes/Objectives n B

Linking Control to Process Objectives 34 High Level and 200+ Detailed Objectives

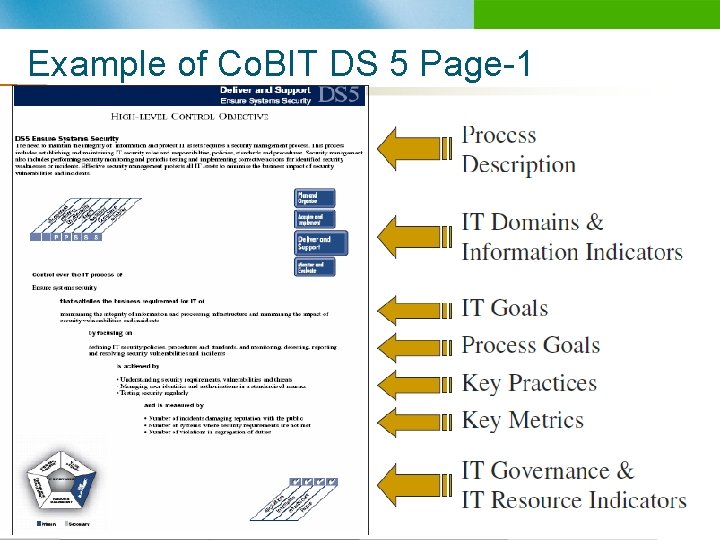
Example of Co. BIT DS 5 Page-1 n B

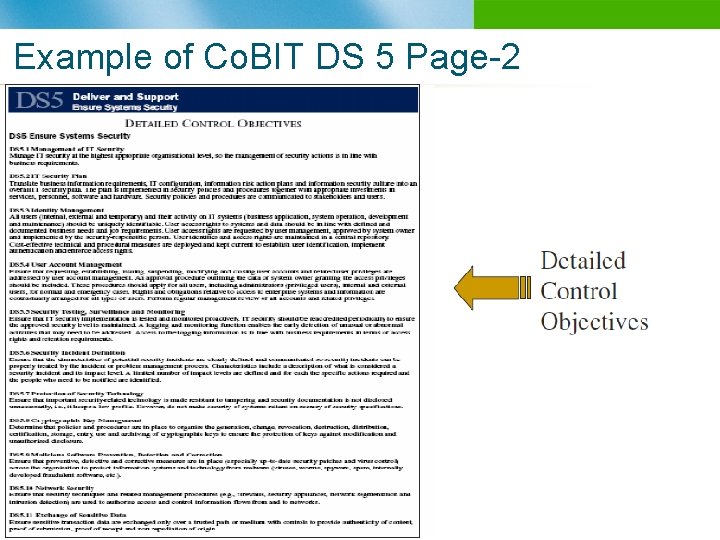
Example of Co. BIT DS 5 Page-2 n B

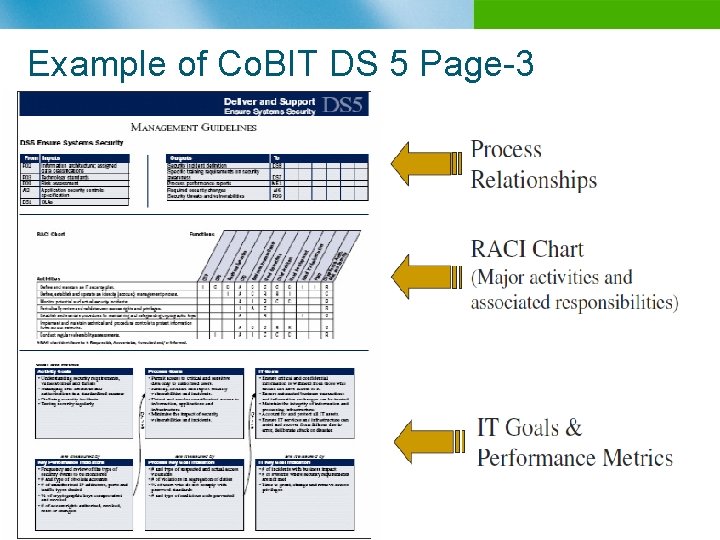
Example of Co. BIT DS 5 Page-3 n B

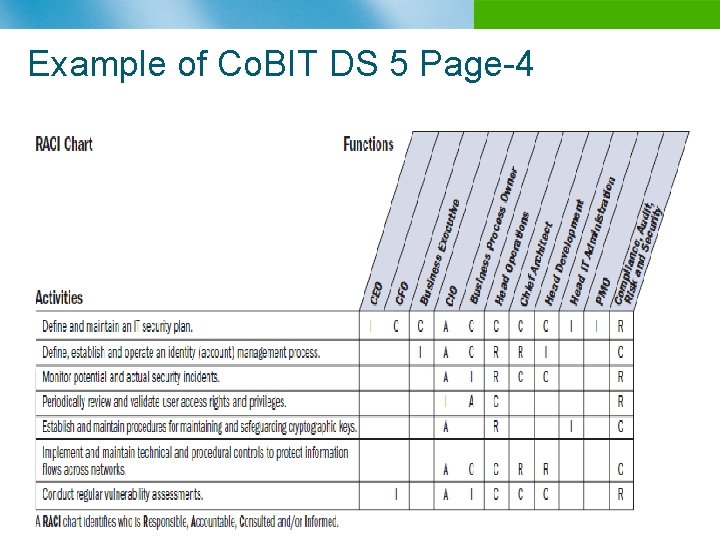
Example of Co. BIT DS 5 Page-4 n B

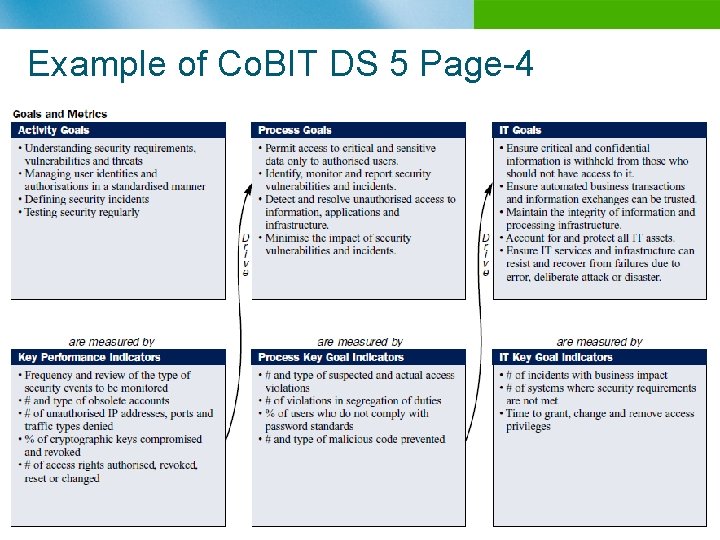
Example of Co. BIT DS 5 Page-4 n B

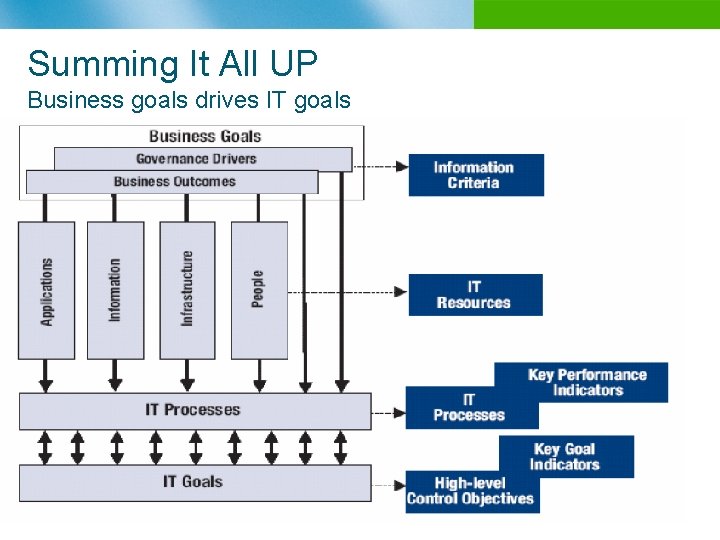
Summing It All UP Business goals drives IT goals n B

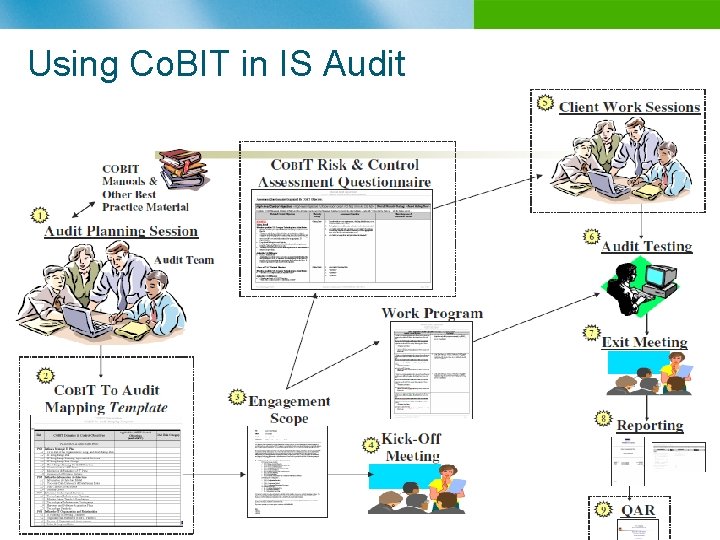
Using Co. BIT in IS Audit n B

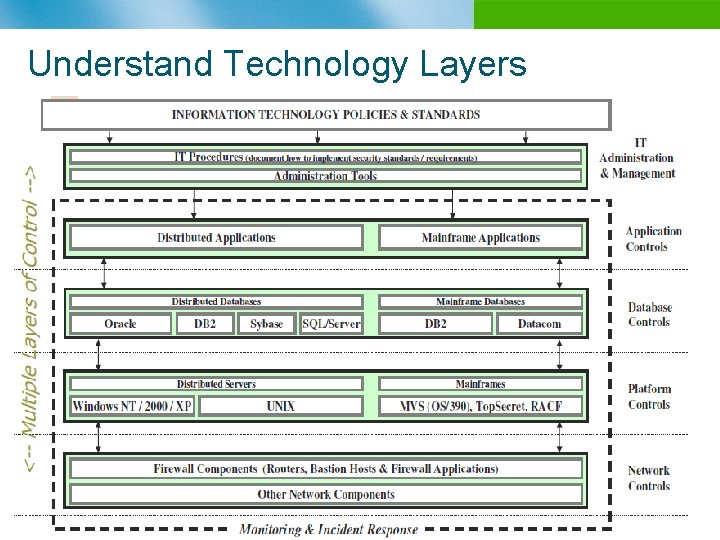
Understand Technology Layers n B

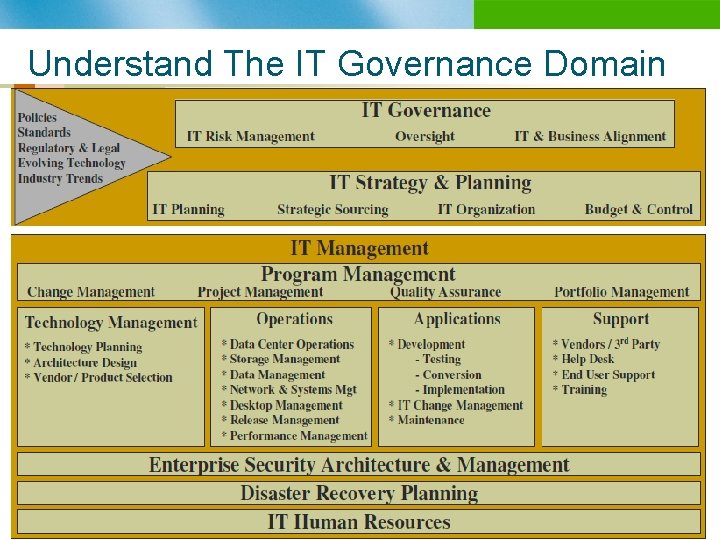
Understand The IT Governance Domain n B

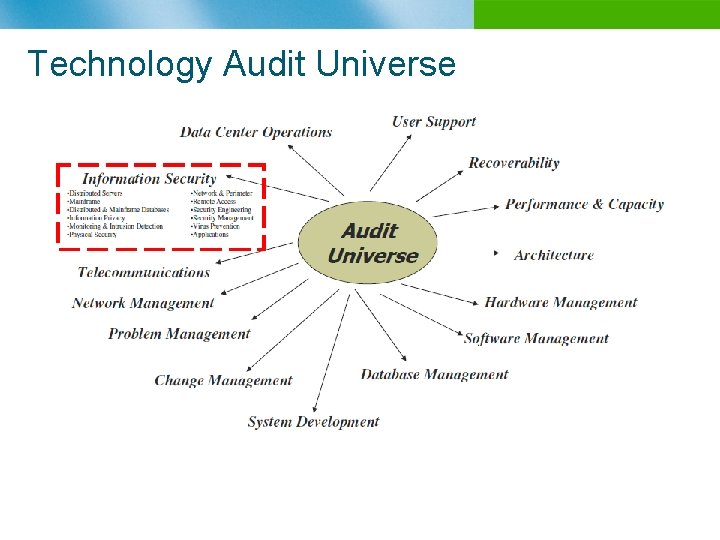
Technology Audit Universe n B

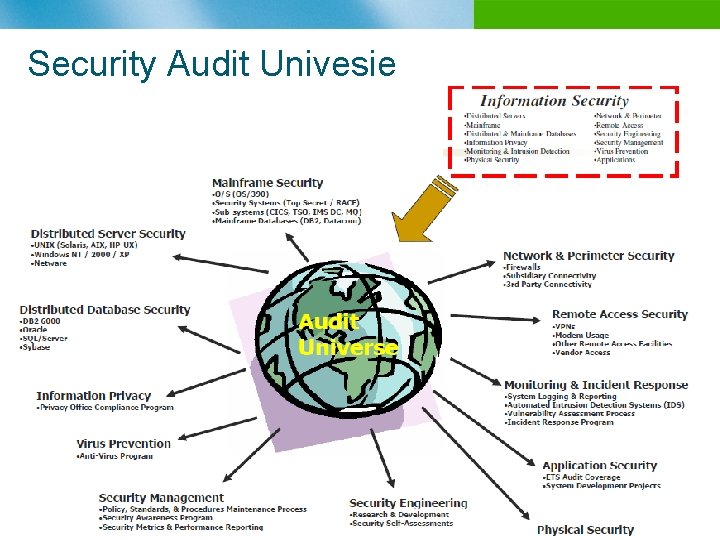
Security Audit Univesie n B

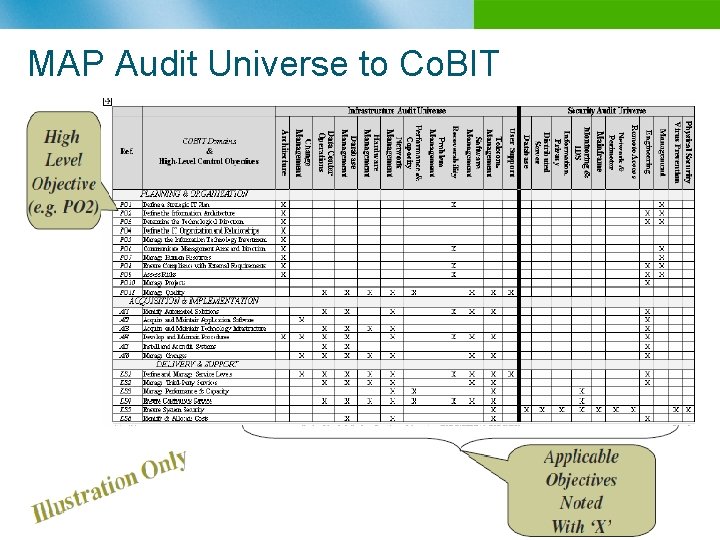
MAP Audit Universe to Co. BIT n B

Using Co. BIT to Tie It All Together n B

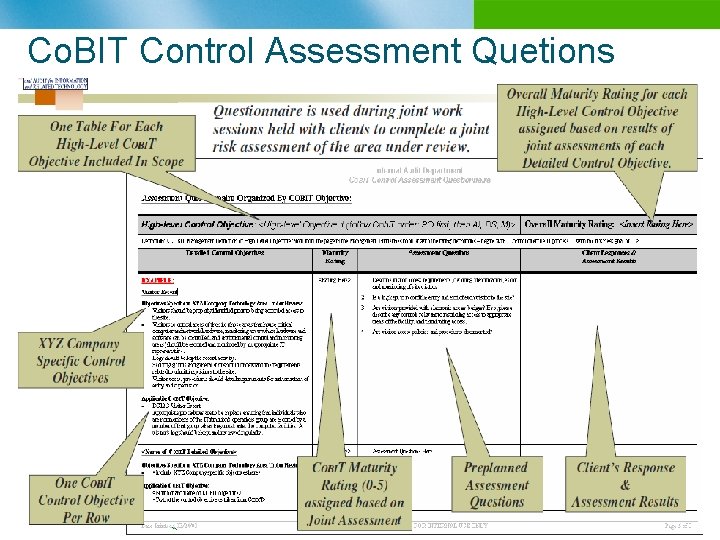
Co. BIT Control Assessment Quetions

Co. BIT’s Audit Report Template n Sample Audit Report

Questions!