Information System Audit Essential of IS Audit for








- Slides: 29

Information System Audit Essential of IS Audit for IT Engineer UP-ITTC October. 2010 1

Summary Information system Audit (IS Audit), is needed long experience and lot of skill and knowledge about both Audit and Information Technology. Because of this, This training course and text book include summary of knowledge and skill that IS Auditor needs and especially detail skill and knowledge about IS Audit processes and methods for IT engineers who want to become IS Auditor or conduct audit tasks. Acknowledgments Content of this training and text book is based on Certified Information Systems Auditor (CISA) and Japan Information Technology Engineers Examination-. System Auditor Examination Content of this training and text book is copyrighted to JICA (Japan International Cooperation Agency) and UP-ITTC(UP Information Technology Training Center), and developed by Go Ota, PADECO Co. , Ltd. and UPITTC Expected Trainees IS Audit is needed wide area of IT skill and knowledge, the training expects the trainees have , at least, passed FE exam or have had same level of IT experience (at least 5 five years, desirable more than 10 years) and knowledge. 2

U How to become IS Auditor & Task and role of IS Auditor 3

U What is Audit? What is IS Audit? “An official examination of accounts to see that they are in order” – The Oxford Dictionary An INDEPENDENT assessment of / opinion on how well (badly) the financial statements were prepared IS audit: - A review of the controls within an entity's technology infrastructure - Official examination of IT related processes to see that they are in order 4

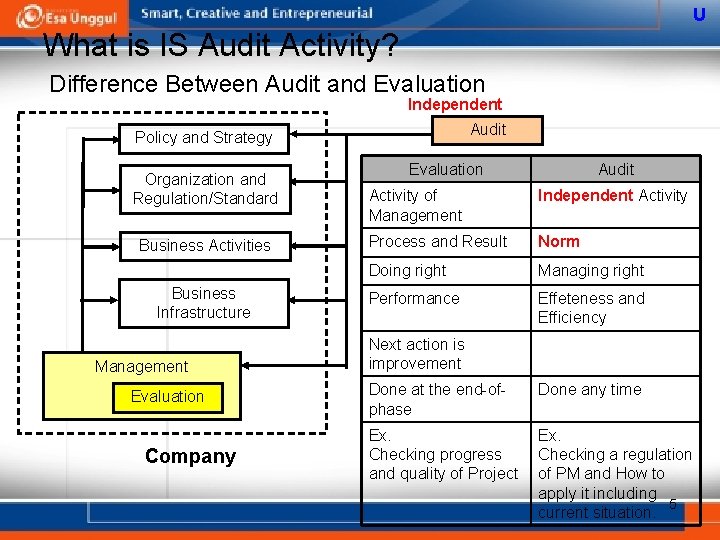
U What is IS Audit Activity? Difference Between Audit and Evaluation Independent Audit Policy and Strategy Organization and Regulation/Standard Business Activities Business Infrastructure Management Evaluation Company Evaluation Audit Activity of Management Independent Activity Process and Result Norm Doing right Managing right Performance Effeteness and Efficiency Next action is improvement Done at the end-ofphase Done any time Ex. Checking progress and quality of Project Ex. Checking a regulation of PM and How to apply it including 5 current situation.

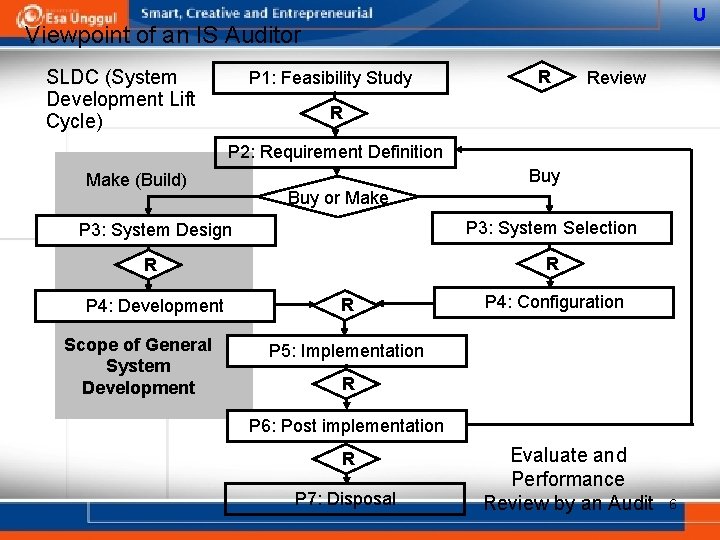
U Viewpoint of an IS Auditor SLDC (System Development Lift Cycle) P 1: Feasibility Study R Review R P 2: Requirement Definition Make (Build) Buy or Make P 3: System Design P 3: System Selection R R P 4: Development Scope of General System Development R P 4: Configuration P 5: Implementation R P 6: Post implementation R P 7: Disposal Evaluate and Performance Review by an Audit 6

U Why IS Audit is needed? Social Background Information System has been becoming a main function for business. • Supporting business activity • Keeping business information • Main interface to customer Innovation of ICT gave information system major role in business Problem of business management • Inappropriate IT system to business strategy • Bug investment for IT system and unclear ROI Problem of security/ risk management • Computer virus/ illegal Access • System trouble and Backup of disaster Effective and Efficient inter management and operation for Information system should be needed Independent Information System Audit 7

U Why IS Audit is needed? Legal Background (1) After major corporate and accounting scandals including those affecting Enron, Tyco International, Adelphia, Peregrine Systems and World. Com, the 'Public Company Accounting Reform and Investor Protection Act' and 'Corporate and Auditing Accountability and Responsibility Act' and commonly called Sarbanes–Oxley, Sarbox or SOX, is a United States federal law enacted on July 30, 2002 • Directs SEC to enact rules protecting shareholders & the economy • Honesty in financial reporting • Responsibility at the Top • Demonstrate Compliance by Audits The most contentious aspect of SOX is Section 404, which requires management and the external auditor to report on the adequacy of the company's internal control over financial reporting Internal Control must use Information System now. To evaluate internal control should needs audit for Information system 8

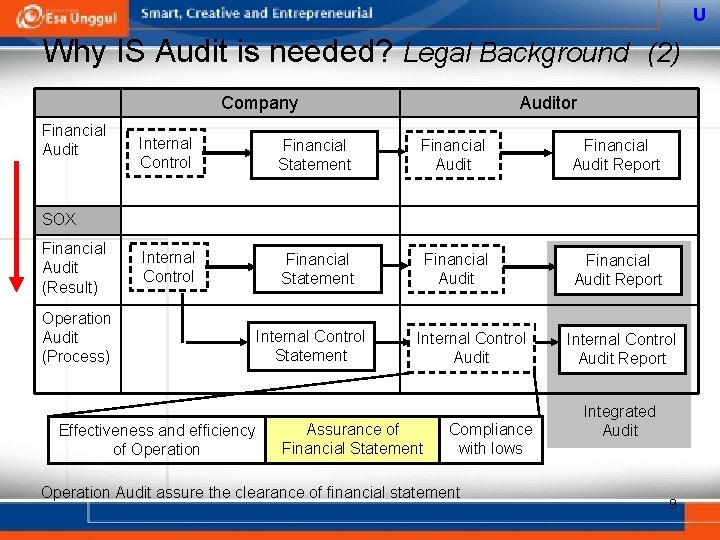
U Why IS Audit is needed? Legal Background (2) Company Financial Auditor Internal Control Financial Statement Financial Audit Report SOX Financial Audit (Result) Operation Audit (Process) Effectiveness and efficiency of Operation Internal Control Statement Internal Control Audit Assurance of Financial Statement Compliance with lows Operation Audit assure the clearance of financial statement Internal Control Audit Report Integrated Audit 9

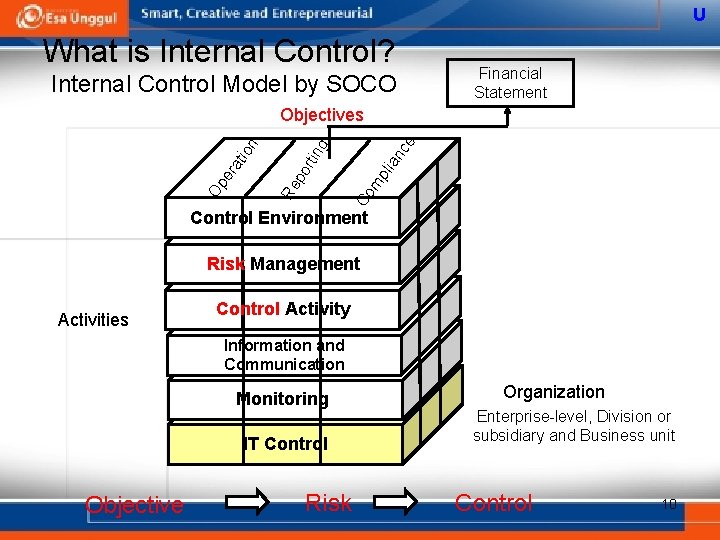
U What is Internal Control? Internal Control Model by SOCO Financial Statement ce g pli an rt i n Co m po Re Op er at ion Objectives Control Environment Risk Management Activities Control Activity Information and Communication Monitoring IT Control Objective Risk Organization Enterprise-level, Division or subsidiary and Business unit Control 10

U Activities of Internal Control Environment The tone for the organization, influencing the control consciousness of its people. It is the foundation for all other components of internal control. Risk Management The identification and analysis of relevant risks to the achievement of objectives, forming a basis for how the risks should be managed Control Activity The policies and procedures that help ensure management directives are carried out. Consists of 2 aspects: Policy of what should be and Procedures to accomplish policy Information and Communication Support the identification, capture, and exchange of information in a form and time frame that enable people to carry out their responsibilities Monitoring Assess the quality of internal control performance over time. IT Control Procedure or policy that provides a reasonable assurance that the information technology (IT) used by an organization 11

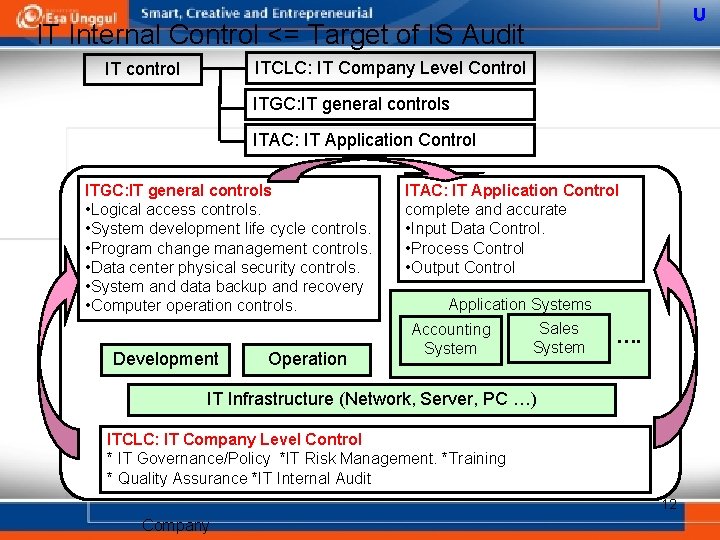
U IT Internal Control <= Target of IS Audit ITCLC: IT Company Level Control IT control ITGC: IT general controls ITAC: IT Application Control ITGC: IT general controls • Logical access controls. • System development life cycle controls. • Program change management controls. • Data center physical security controls. • System and data backup and recovery • Computer operation controls. Development Operation ITAC: IT Application Control complete and accurate • Input Data Control. • Process Control • Output Control Application Systems Sales Accounting System …. IT Infrastructure (Network, Server, PC …) ITCLC: IT Company Level Control * IT Governance/Policy *IT Risk Management. *Training * Quality Assurance *IT Internal Audit 12 Company

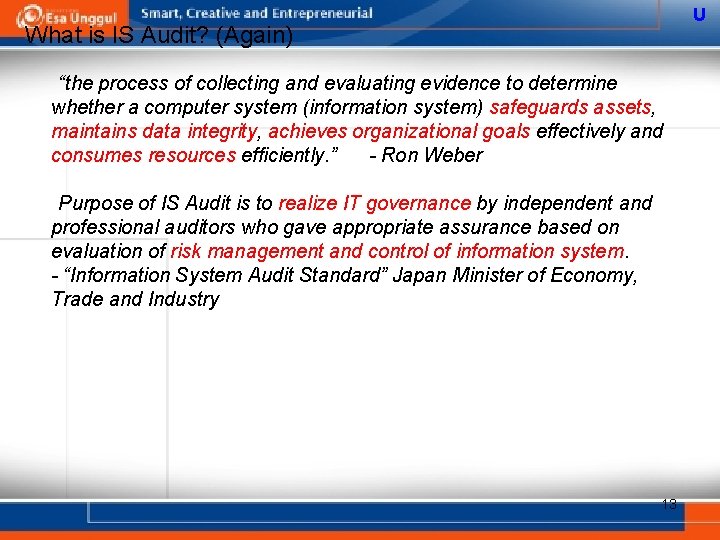
U What is IS Audit? (Again) “the process of collecting and evaluating evidence to determine whether a computer system (information system) safeguards assets, maintains data integrity, achieves organizational goals effectively and consumes resources efficiently. ” - Ron Weber Purpose of IS Audit is to realize IT governance by independent and professional auditors who gave appropriate assurance based on evaluation of risk management and control of information system. - “Information System Audit Standard” Japan Minister of Economy, Trade and Industry 13

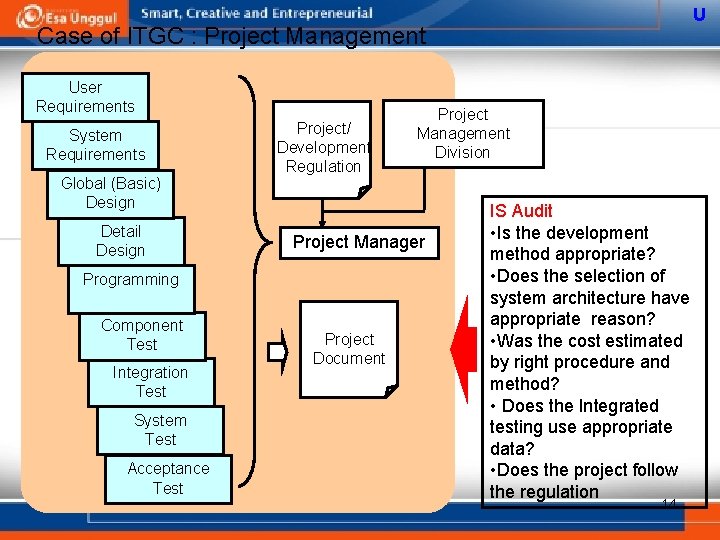
U Case of ITGC : Project Management User Requirements System Requirements Global (Basic) Design Detail Design Project/ Development Regulation Project Manager Programming Component Test Integration Test System Test Acceptance Test Project Management Division Project Document IS Audit • Is the development method appropriate? • Does the selection of system architecture have appropriate reason? • Was the cost estimated by right procedure and method? • Does the Integrated testing use appropriate data? • Does the project follow the regulation 14

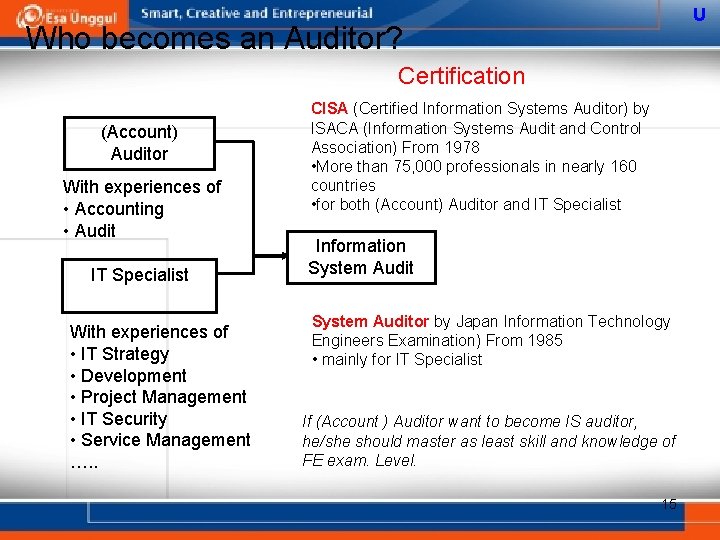
U Who becomes an Auditor? Certification (Account) Auditor With experiences of • Accounting • Audit IT Specialist With experiences of • IT Strategy • Development • Project Management • IT Security • Service Management …. . CISA (Certified Information Systems Auditor) by ISACA (Information Systems Audit and Control Association) From 1978 • More than 75, 000 professionals in nearly 160 countries • for both (Account) Auditor and IT Specialist Information System Auditor by Japan Information Technology Engineers Examination) From 1985 • mainly for IT Specialist If (Account ) Auditor want to become IS auditor, he/she should master as least skill and knowledge of FE exam. Level. 15

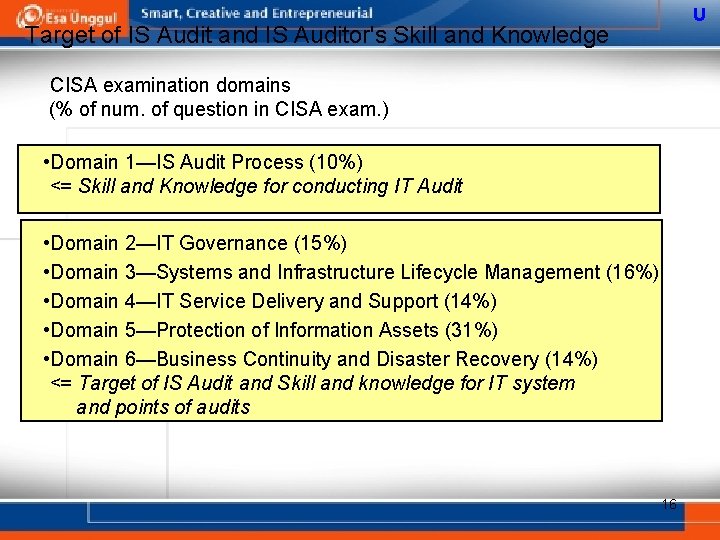
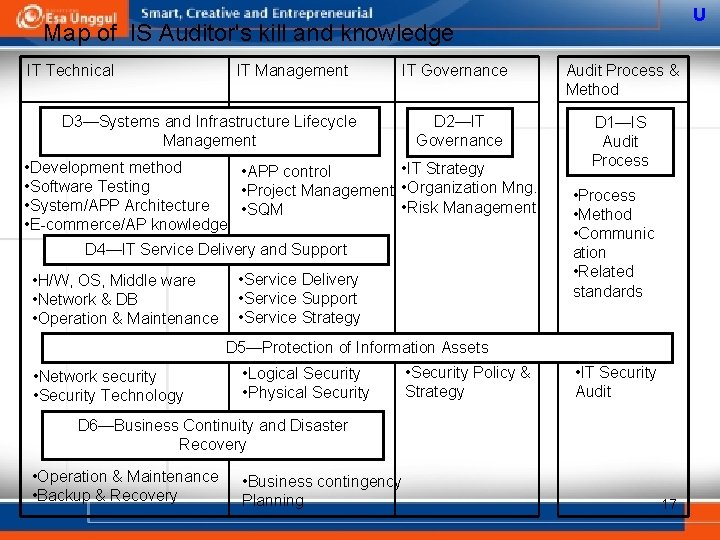
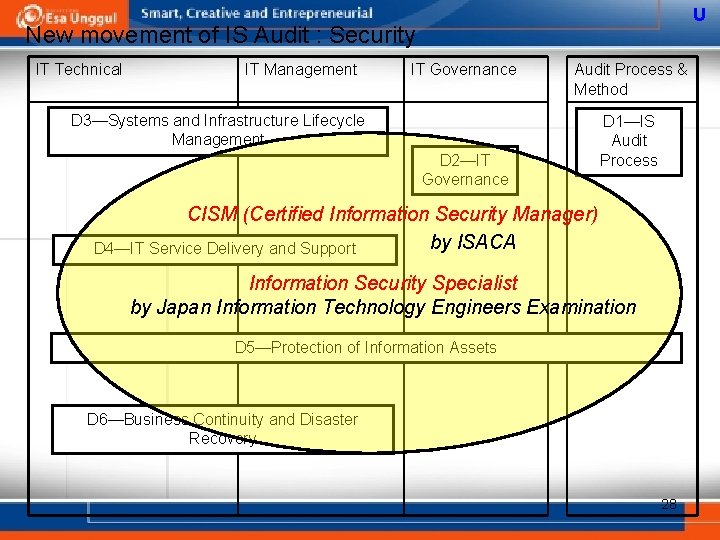
U Target of IS Audit and IS Auditor's Skill and Knowledge CISA examination domains (% of num. of question in CISA exam. ) • Domain 1—IS Audit Process (10%) <= Skill and Knowledge for conducting IT Audit • Domain 2—IT Governance (15%) • Domain 3—Systems and Infrastructure Lifecycle Management (16%) • Domain 4—IT Service Delivery and Support (14%) • Domain 5—Protection of Information Assets (31%) • Domain 6—Business Continuity and Disaster Recovery (14%) <= Target of IS Audit and Skill and knowledge for IT system and points of audits 16

U Map of IS Auditor's kill and knowledge IT Technical IT Management IT Governance Audit Process & Method D 2—IT Governance D 1—IS Audit Process D 3—Systems and Infrastructure Lifecycle Management • Development method • IT Strategy • APP control • Software Testing • Project Management • Organization Mng. • System/APP Architecture • Risk Management • SQM • E-commerce/AP knowledge D 4—IT Service Delivery and Support • H/W, OS, Middle ware • Network & DB • Operation & Maintenance • Service Delivery • Service Support • Service Strategy • Process • Method • Communic ation • Related standards D 5—Protection of Information Assets • Network security • Security Technology • Logical Security • Physical Security • Security Policy & Strategy • IT Security Audit D 6—Business Continuity and Disaster Recovery • Operation & Maintenance • Backup & Recovery • Business contingency Planning 17

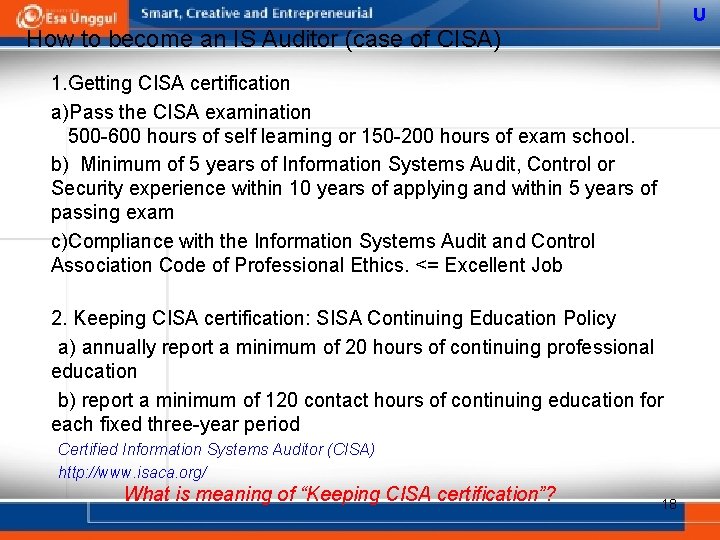
U How to become an IS Auditor (case of CISA) 1. Getting CISA certification a)Pass the CISA examination 500 -600 hours of self learning or 150 -200 hours of exam school. b) Minimum of 5 years of Information Systems Audit, Control or Security experience within 10 years of applying and within 5 years of passing exam c)Compliance with the Information Systems Audit and Control Association Code of Professional Ethics. <= Excellent Job 2. Keeping CISA certification: SISA Continuing Education Policy a) annually report a minimum of 20 hours of continuing professional education b) report a minimum of 120 contact hours of continuing education for each fixed three-year period Certified Information Systems Auditor (CISA) http: //www. isaca. org/ What is meaning of “Keeping CISA certification”? 18

U Professional Ethics (ISACA Code) • Support the implementation of, and encourage compliance with, appropriate standards, procedures and controls for information systems. • Perform their duties with objectivity, due diligence and professional care, in accordance with professional standards and best practices. • Serve in the interest of stakeholders in a lawful and honest manner, while maintaining high standards of conduct and character, and not engage in acts discreditable to the profession. • Maintain the privacy and confidentiality of information obtained in the course of their duties unless disclosure is required by legal authority. Such information shall not be used for personal benefit or released to inappropriate parties. • Maintain competency in their respective fields and agree to undertake only those activities, which they can reasonably expect to complete with professional competence. • Inform appropriate parties of the results of work performed; revealing all significant facts known to them. • Support the professional education of stakeholders in enhancing their understanding of information systems security and control. 19

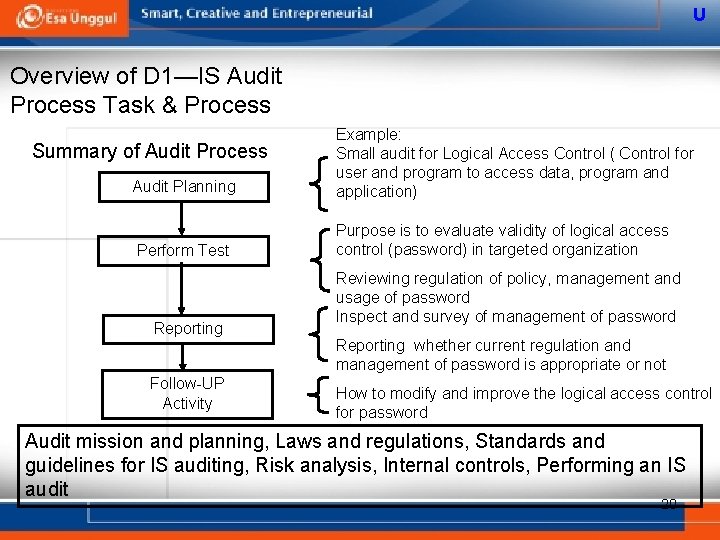
U Overview of D 1—IS Audit Process Task & Process Audit Planning Example: Small audit for Logical Access Control ( Control for user and program to access data, program and application) Perform Test Purpose is to evaluate validity of logical access control (password) in targeted organization Summary of Audit Process Reporting Follow-UP Activity Reviewing regulation of policy, management and usage of password Inspect and survey of management of password Reporting whether current regulation and management of password is appropriate or not How to modify and improve the logical access control for password Audit mission and planning, Laws and regulations, Standards and guidelines for IS auditing, Risk analysis, Internal controls, Performing an IS audit 20

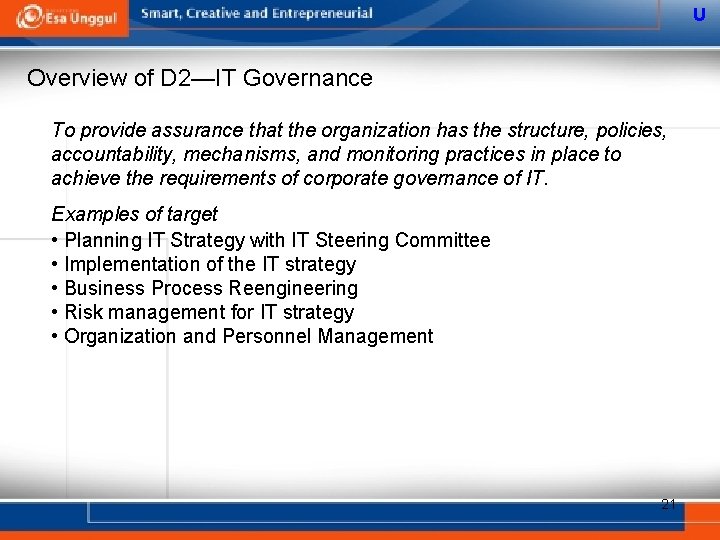
U Overview of D 2—IT Governance To provide assurance that the organization has the structure, policies, accountability, mechanisms, and monitoring practices in place to achieve the requirements of corporate governance of IT. Examples of target • Planning IT Strategy with IT Steering Committee • Implementation of the IT strategy • Business Process Reengineering • Risk management for IT strategy • Organization and Personnel Management 21

U Overview of D 3—Systems and Infrastructure Lifecycle Management To provide assurance that the management practices for the development/acquisition, testing, implementation, maintenance, and disposal of systems and infrastructure will meet the organization’s objectives. Examples of target • Application development process and regulation including needs analysis, including cost estimation and • Quality Management • Validation of computer & system architecture for Application • Application control • Management of outsourcing and vender 22

U Overview of D 4—IT Service Delivery and Support To provide assurance that the IT service management practices will ensure the delivery of the level of services required to meet the organization’s objectives. Example of Target • Service level Agreement • Validation of Hardware and software • Validation of network infrastructure • Monitoring of Information System/Infrastructure • Capacity and Configuration Management • Configuration Management of software • Regulation of operation and maintenance • Help (Service) Desk and Incident/Problem management 23

U Overview of D 5—Protection of Information Assets To provide assurance that the security architecture (policies, standards, procedures, and controls) ensures the confidentiality, integrity, and availability of information assets. Examples of Target • Policy and regulation of IT Security including risk management • Validation of logical access control such as password and authentication • Validation of physical access control with security technology and devices • Validation of security of network infrastructure • Validation of encryption system • Validation of environmental control against fire, power break down and … 24

U Overview of D 6—Business Continuity and Disaster Recovery To provide assurance that in the event of a disruption the business continuity and disaster recovery processes will ensure the timely resumption of IT services while minimizing the business impact Examples of Target • Business Impact Analysis (BIA) and Disaster Recovery Planning (DRP) • Validation of backup and recovery against disasters • Validation of means for continuity against disasters 25

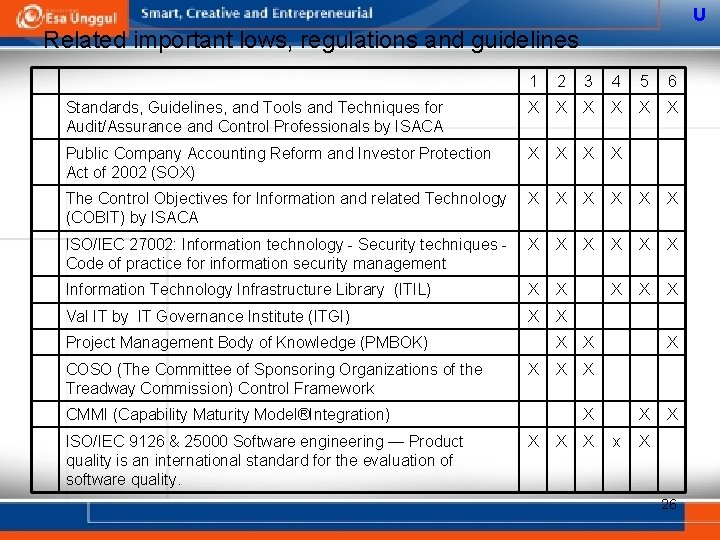
U Related important lows, regulations and guidelines 1 2 3 4 5 6 Standards, Guidelines, and Tools and Techniques for Audit/Assurance and Control Professionals by ISACA X X X Public Company Accounting Reform and Investor Protection Act of 2002 (SOX) X X The Control Objectives for Information and related Technology (COBIT) by ISACA X X X ISO/IEC 27002: Information technology - Security techniques Code of practice for information security management X X X Information Technology Infrastructure Library (ITIL) X X X Val IT by IT Governance Institute (ITGI) X X Project Management Body of Knowledge (PMBOK) COSO (The Committee of Sponsoring Organizations of the Treadway Commission) Control Framework X X X CMMI (Capability Maturity Model®Integration) ISO/IEC 9126 & 25000 Software engineering — Product quality is an international standard for the evaluation of software quality. X X X x X X 26

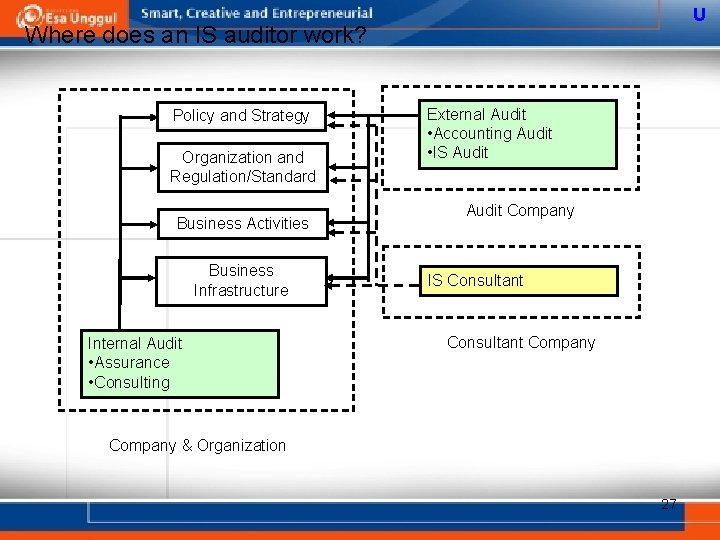
U Where does an IS auditor work? Policy and Strategy Organization and Regulation/Standard Business Activities Business Infrastructure Internal Audit • Assurance • Consulting External Audit • Accounting Audit • IS Audit Company IS Consultant Company & Organization 27

U New movement of IS Audit : Security IT Technical IT Management IT Governance Audit Process & Method D 3—Systems and Infrastructure Lifecycle Management D 2—IT Governance D 1—IS Audit Process CISM (Certified Information Security Manager) by ISACA D 4—IT Service Delivery and Support Information Security Specialist by Japan Information Technology Engineers Examination D 5—Protection of Information Assets D 6—Business Continuity and Disaster Recovery 28

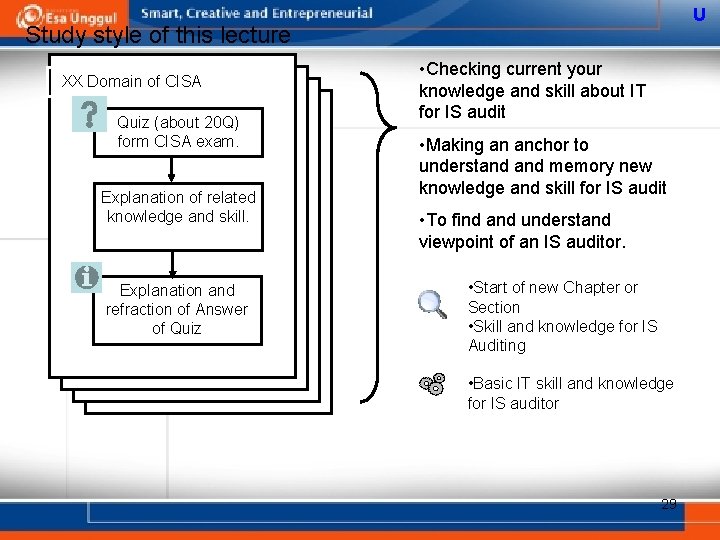
U Study style of this lecture XX Domain of CISA Quiz (about 20 Q) form CISA exam. Explanation of related knowledge and skill. Explanation and refraction of Answer of Quiz • Checking current your knowledge and skill about IT for IS audit • Making an anchor to understand memory new knowledge and skill for IS audit • To find and understand viewpoint of an IS auditor. • Start of new Chapter or Section • Skill and knowledge for IS Auditing • Basic IT skill and knowledge for IS auditor 29