Information Social Access Mapping Who is doing what










- Slides: 18

Information Social Access Mapping: Who is doing what with data? Dan Jennings March 2016 Veritas Partner Technical Account Manager +44 (0)7590 003199 Veritas Technologies LLC Office: +44 (0)7590 003199 Email address: dan. jennings@veritas. com

Information Ownership Identification Including Inferred Ownership 2

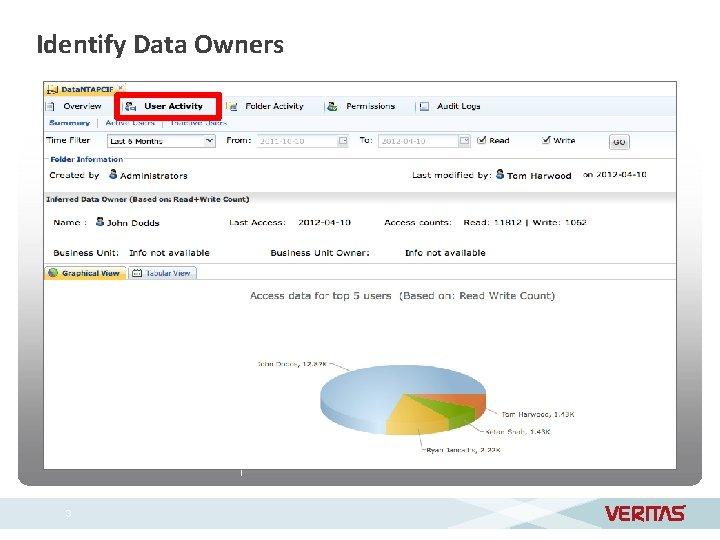
Identify Data Owners 3

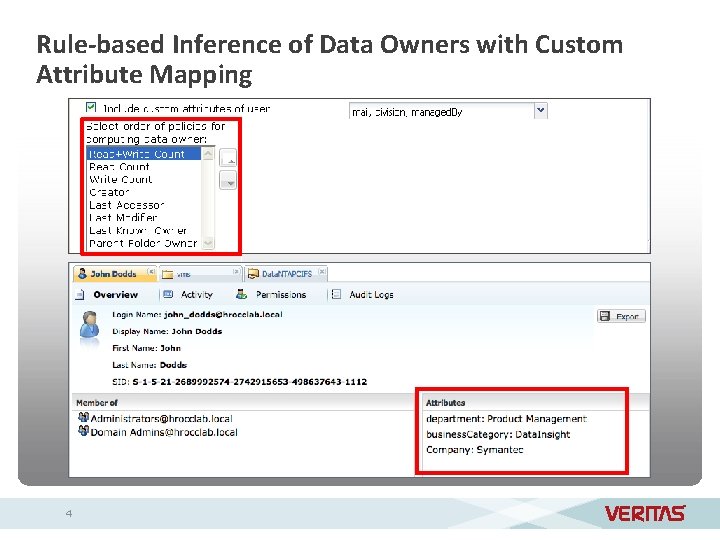
Rule-based Inference of Data Owners with Custom Attribute Mapping 4

Tracking Users 5

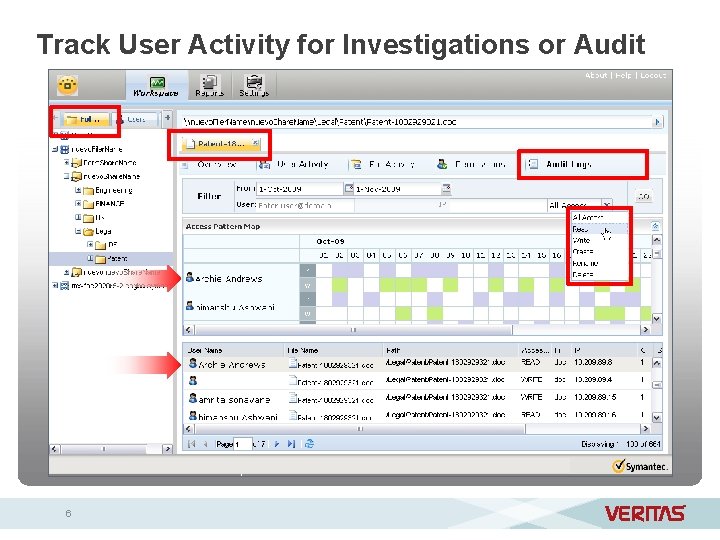
Track User Activity for Investigations or Audit 6

Archiving Integration 7 Copyright © 2015 Symantec Corporation

Archive Orphan Folders Symantec Propietary and Confidential SYMC CONFIDENTIAL

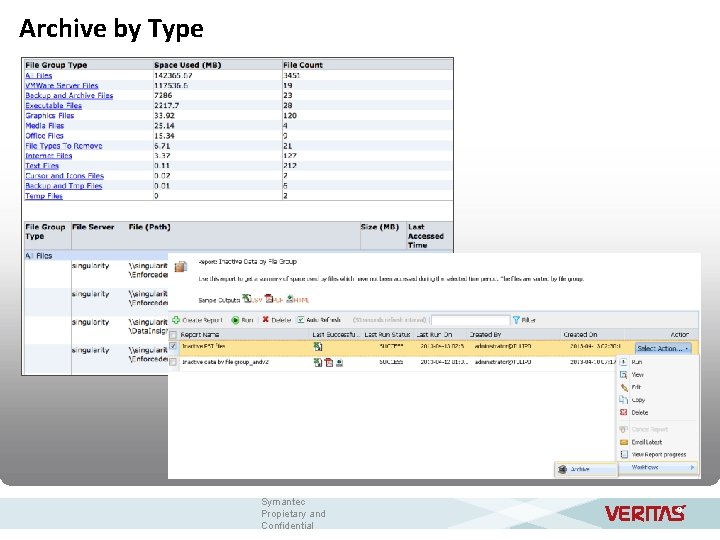
Archive by Type Symantec Propietary and Confidential 9

Archive Custodian Data Symantec Propietary and Confidential 10

Archive for Retention Symantec Propietary and Confidential 11

Data Loss Prevention Integration 12 Copyright © 2015 Symantec Corporation

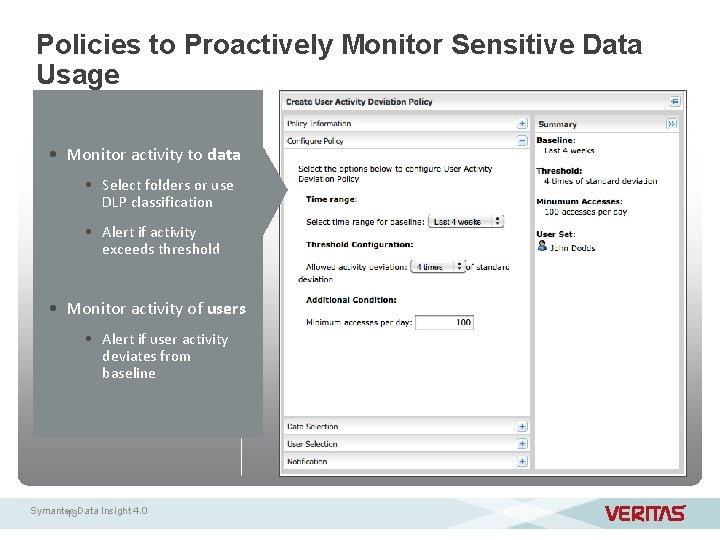
Policies to Proactively Monitor Sensitive Data Usage • Monitor activity to data • Select folders or use DLP classification • Alert if activity exceeds threshold • Monitor activity of users • Alert if user activity deviates from baseline Symantec 13 Data Insight 4. 0

Social Network Map: Secure Collaboration • Detect outliers among users • Reduce risk from excessive access permissions 14

Data Loss Prevention View: Incident and Data Owner Data Insight John Smith 15 Symantec Data Insight 4. 0

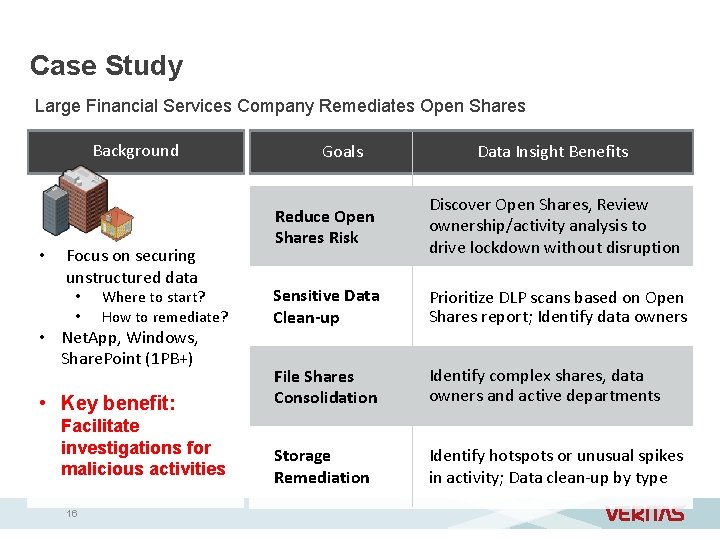
Case Study Large Financial Services Company Remediates Open Shares Background • Focus on securing unstructured data • • Where to start? How to remediate? • Net. App, Windows, Share. Point (1 PB+) • Key benefit: Facilitate investigations for malicious activities 16 Goals Data Insight Benefits Reduce Open Shares Risk Discover Open Shares, Review ownership/activity analysis to drive lockdown without disruption Sensitive Data Clean-up Prioritize DLP scans based on Open Shares report; Identify data owners File Shares Consolidation Identify complex shares, data owners and active departments Storage Remediation Identify hotspots or unusual spikes in activity; Data clean-up by type

Thank you! Dan Jennings +44 (0)7590 003199 dan. jennings@veritas. com Copyright © 2015 Symantec Corporation. All rights reserved. Veritas and the Veritas Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice.

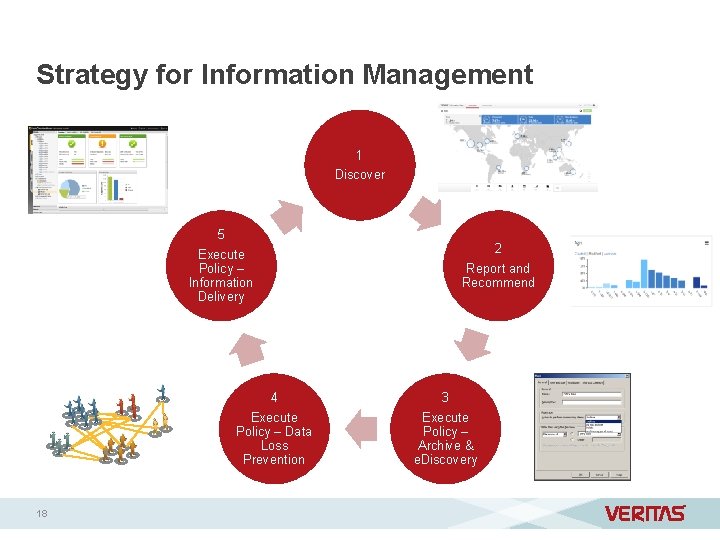
Strategy for Information Management 1 Discover 5 Execute Policy – Information Delivery 4 Execute Policy – Data Loss Prevention 18 2 Report and Recommend 3 Execute Policy – Archive & e. Discovery