Information Security Program The WVU Information Security Program




























- Slides: 45

Information Security Program The WVU Information Security Program ~~~~~ If You Build It, They Will Use It May 17, 2004 Educause/Internet 2 Security Professionals Workshop 1

Information Security Program Introductions ● Sue Ann Lipinski Management Auditor, Internal Audit ● Tim Marton Director, Information Systems ● Mark Six Manager, Systems Administration May 17, 2004 Educause/Internet 2 Security Professionals Workshop 2

Information Security Program Abstract WVU is building an institution-wide information security program to ensure the continued confidentiality, integrity & availability of mission critical information resources. This presentation discusses our incremental implementation approach, including the development of policies / standards / procedures, as well as efforts to include this program in current & future informationrelated activities & projects. May 17, 2004 Educause/Internet 2 Security Professionals Workshop 3

Information Security Program Some WVU Facts ● Founded in 1867 in Morgantown, WV ● Land Grant Institution ● 13 colleges & schools, offering 170 bachelor’s, masters, doctoral & professional degree programs ● Medical Center ● Doctoral Research Extensive Classification ● Spread over 3 Morgantown & 3 regional campuses ● Enrollment of approximately 31, 800 ● Faculty/Staff of 6, 487 May 17, 2004 Educause/Internet 2 Security Professionals Workshop 4

Information Security Program Agenda ● Evolution of WVU’s Program ● Insight into Current Program ● Where Are We Going Next ● Words to the Wise May 17, 2004 Educause/Internet 2 Security Professionals Workshop 5

Information Security Program Evolution of WVU’s Program ● Drivers – Internal & External ● Champions Promoted, Promoted … ● Defined Information Security for WVU ● Developed / Updated Policies / Standards – On-going ● Identified Information Security Program Elements May 17, 2004 Educause/Internet 2 Security Professionals Workshop 6

Information Security Program Why? Why Now? ● Internal Drivers − Recognized Need to Protect Information Resources − Impact of an Incident ● External Drivers − − − Gramm-Leach-Bliley Act (GLB) Health Insurance Portability & Accountability Act (HIPAA) Family Education Rights & Privacy Act (FERPA) The Privacy Act West Virginia Code 18 -2 -5 f – Use of Student SSNs ● Demonstrate Due Diligence − Higher Education in the Headlines May 17, 2004 Educause/Internet 2 Security Professionals Workshop 7

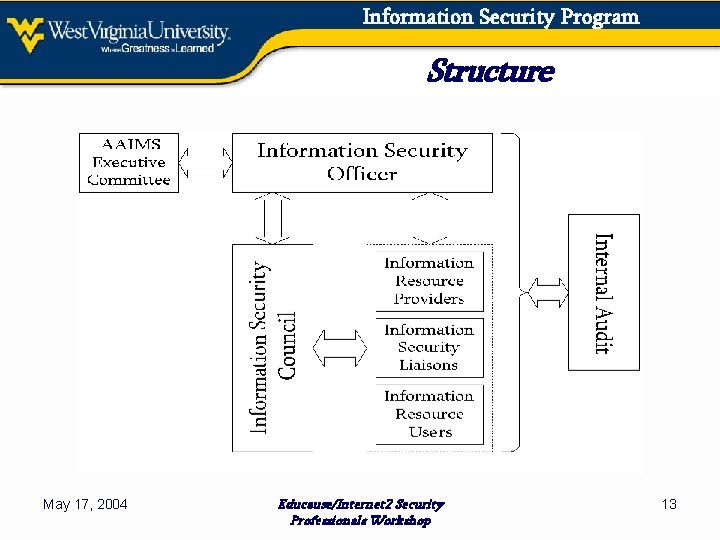
Information Security Program WVU’s Security Policy ● Information Resources as Vital Assets ● Definition / Purpose of Information Security ● Elements of WVU’s Program ● Structure, Composition & Responsibilities May 17, 2004 Educause/Internet 2 Security Professionals Workshop 8

Information Security Program WVU Information Resources ● WVU relies on numerous, diverse information resources to support the mission critical operations of administration, education, research & service. ● If these information resources were unavailable, unreliable or disclosed in an inappropriate manner, the University could suffer damage to its reputation & incur serious financial & operational losses. ● Accordingly, WVU acknowledges that information resources are vital assets requiring protection commensurate with their value. May 17, 2004 Educause/Internet 2 Security Professionals Workshop 9

Information Security Program Definition & Purpose ● The protection of information resources from unauthorized access, modification, destruction or harm ● The establishment of controls & measures to minimize the risk of loss or damage to information resources ● Inform users (students, staff and faculty) of essential requirements for protecting various assets including people hardware, software resources & data assets ● Provide a baseline from which to acquire, configure & audit computer systems & networks for compliance with the policy May 17, 2004 Educause/Internet 2 Security Professionals Workshop 10

Information Security Program Three Tenets ● Confidentiality … addresses the protection of private, sensitive or trusted information resources from unauthorized access or disclosure ● Integrity … refers to the accuracy, completeness & consistency of information resources ● Availability … ensures reliable & timely access to information resources by appropriate personnel May 17, 2004 Educause/Internet 2 Security Professionals Workshop 11

Information Security Program Elements of WVU’s Program ● ● ● ● Defined Structure w/ Central Point of Coordination Risk Assessment & Management Policies & Standards / Policy Management Communication & Education Compliance Reporting & Enforcement Procurement Oversight for Service Providers Security-related Projects May 17, 2004 Educause/Internet 2 Security Professionals Workshop 12

Information Security Program Structure May 17, 2004 Educause/Internet 2 Security Professionals Workshop 13

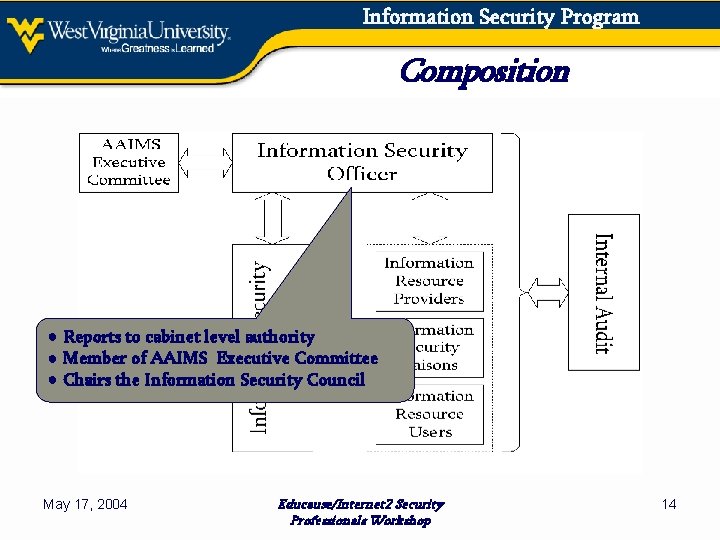
Information Security Program Composition ● Reports to cabinet level authority ● Member of AAIMS Executive Committee ● Chairs the Information Security Council May 17, 2004 Educause/Internet 2 Security Professionals Workshop 14

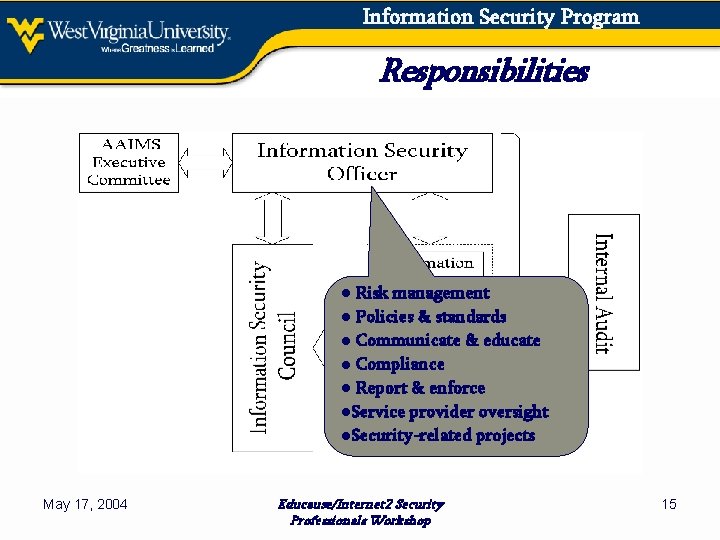
Information Security Program Responsibilities ● Risk management ● Policies & standards ● Communicate & educate ● Compliance ● Report & enforce ●Service provider oversight ●Security-related projects May 17, 2004 Educause/Internet 2 Security Professionals Workshop 15

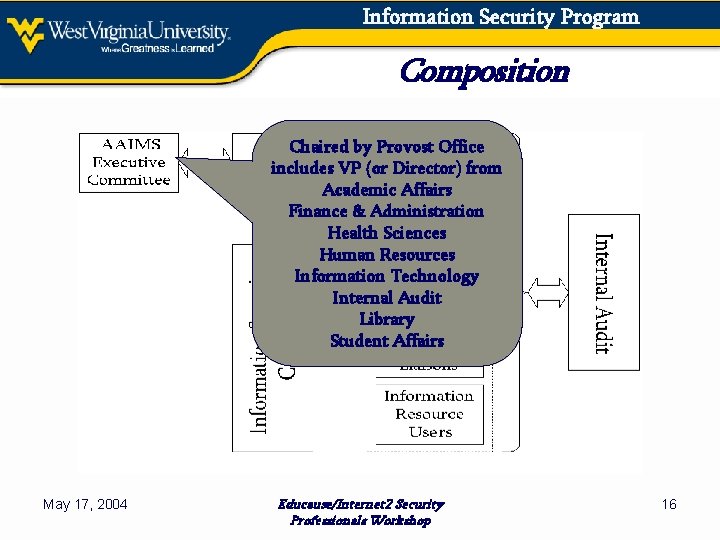
Information Security Program Composition Chaired by Provost Office includes VP (or Director) from Academic Affairs Finance & Administration Health Sciences Human Resources Information Technology Internal Audit Library Student Affairs May 17, 2004 Educause/Internet 2 Security Professionals Workshop 16

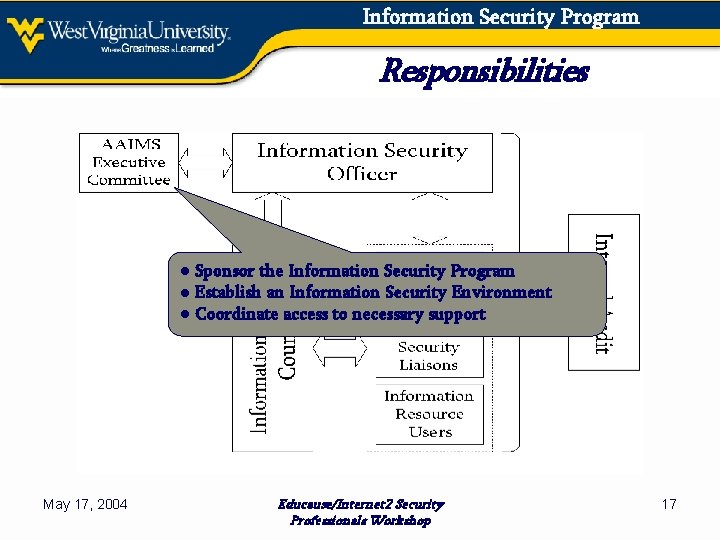
Information Security Program Responsibilities ● Sponsor the Information Security Program ● Establish an Information Security Environment ● Coordinate access to necessary support May 17, 2004 Educause/Internet 2 Security Professionals Workshop 17

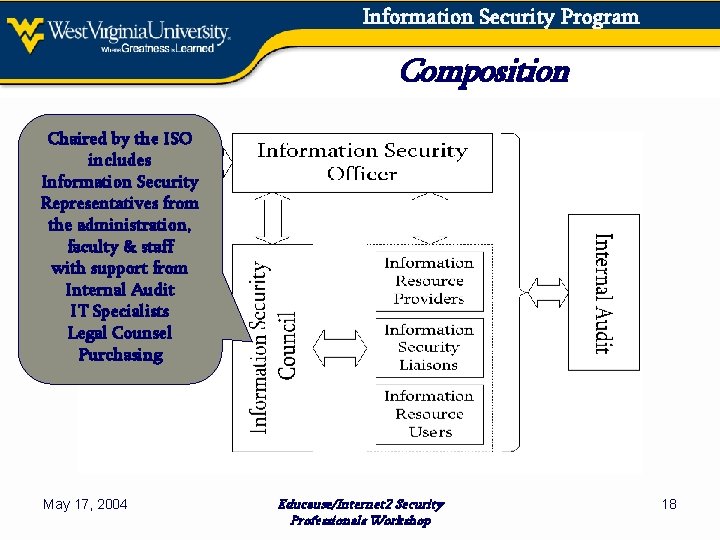
Information Security Program Composition Chaired by the ISO includes Information Security Representatives from the administration, faculty & staff with support from Internal Audit IT Specialists Legal Counsel Purchasing May 17, 2004 Educause/Internet 2 Security Professionals Workshop 18

Information Security Program ISC Charter ● Serve as senior management sponsors of the WVU Information Security Program ● Provide management & coordination of a University-wide information security program ● Review & revise information security policies, standards and procedures ● Establish & maintain a comprehensive risk management program ● Establish & maintain an information security compliance program ● Recommend & sponsor information security awareness, communication & education programs ● Provide a forum to discuss & assess pending regulations & requirements ● Perform periodic reviews of information security incidents / violations ● Govern contractual relationships with vendors, consultants & other 3 rd parties May 17, 2004 Educause/Internet 2 Security Professionals Workshop 19

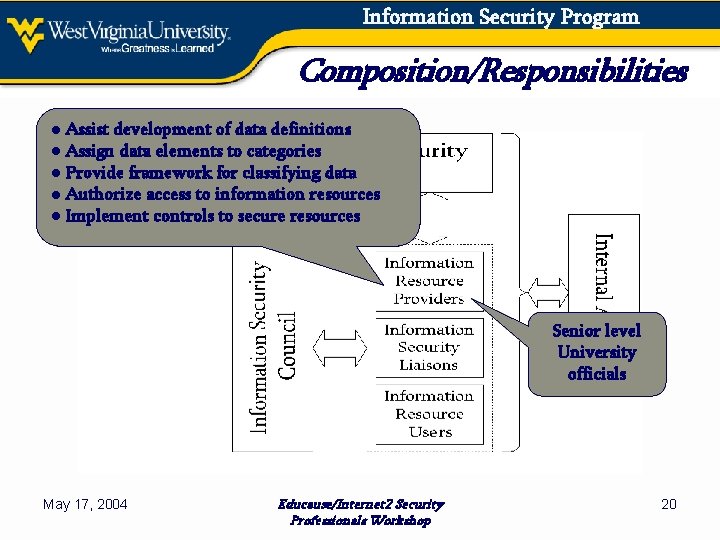
Information Security Program Composition/Responsibilities ● Assist development of data definitions ● Assign data elements to categories ● Provide framework for classifying data ● Authorize access to information resources ● Implement controls to secure resources Senior level University officials May 17, 2004 Educause/Internet 2 Security Professionals Workshop 20

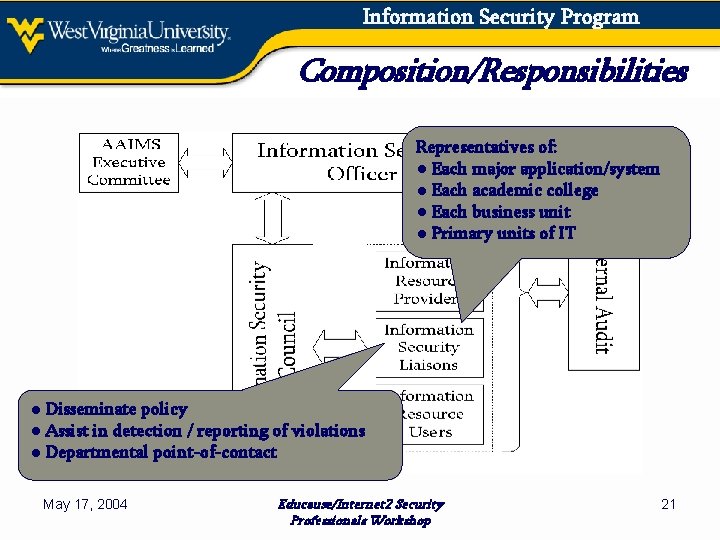
Information Security Program Composition/Responsibilities Representatives of: ● Each major application/system ● Each academic college ● Each business unit ● Primary units of IT ● Disseminate policy ● Assist in detection / reporting of violations ● Departmental point-of-contact May 17, 2004 Educause/Internet 2 Security Professionals Workshop 21

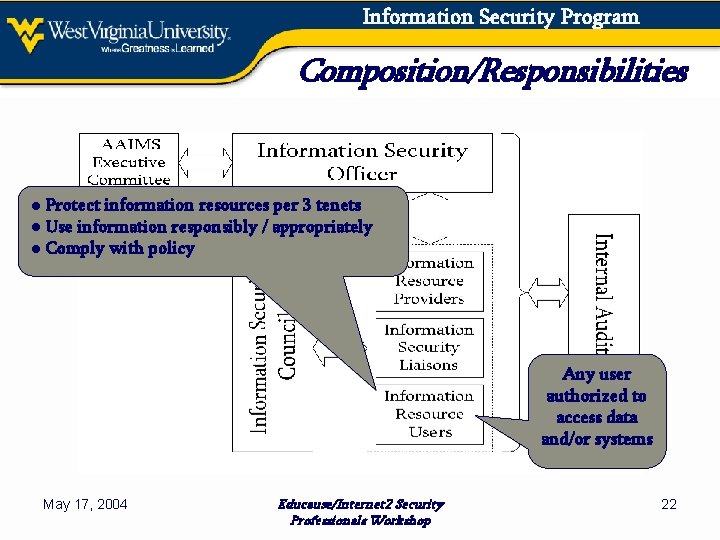
Information Security Program Composition/Responsibilities ● Protect information resources per 3 tenets ● Use information responsibly / appropriately ● Comply with policy Any user authorized to access data and/or systems May 17, 2004 Educause/Internet 2 Security Professionals Workshop 22

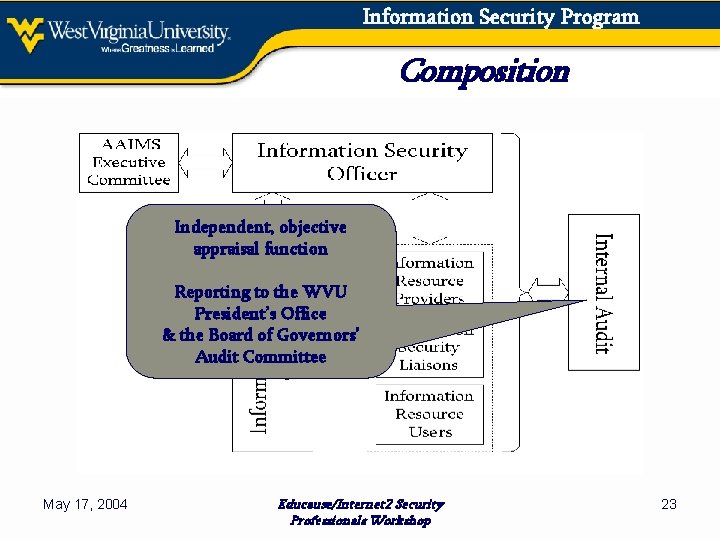
Information Security Program Composition Independent, objective appraisal function Reporting to the WVU President’s Office & the Board of Governors’ Audit Committee May 17, 2004 Educause/Internet 2 Security Professionals Workshop 23

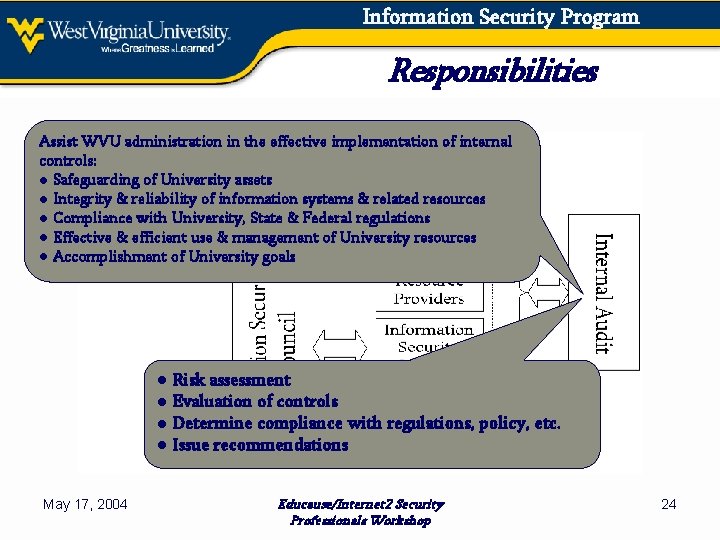
Information Security Program Responsibilities Assist WVU administration in the effective implementation of internal controls: ● Safeguarding of University assets ● Integrity & reliability of information systems & related resources ● Compliance with University, State & Federal regulations ● Effective & efficient use & management of University resources ● Accomplishment of University goals ● Risk assessment ● Evaluation of controls ● Determine compliance with regulations, policy, etc. ● Issue recommendations May 17, 2004 Educause/Internet 2 Security Professionals Workshop 24

Information Security Program Risk Management ● Identify & Classify Resources ● Identify Threats & Vulnerabilities ● Determine & Prioritize Risks ● Determine Response: − Prevent, Mitigate or Accept ● Risk Assessment: − Periodic: ISO & ISC − Independent: Internal Audit May 17, 2004 Educause/Internet 2 Security Professionals Workshop 25

Information Security Program Policies/Standards ● Contain senior management directives to create an information security program, establish its goals & measures, & assign responsibilities; define an organization’s information security philosophy ● Mandatory activities, rules, measures of minimal performance or achievement, designed to provide support & structure; intended for universal application throughout the organization; used to implement the general policies/standards May 17, 2004 Educause/Internet 2 Security Professionals Workshop 26

Information Security Program Policies/Standards (cont’d) ● Recently Developed / Updated − − − − Acceptable (Appropriate) Use Anti-Spam, Anti-Virus Data Center Access e-Commerce Management Electronic Mail End-User Accountability Network Security ● Under Development − Data Ownership / Classification / Security − Security Awareness / Education − Security Incident Reporting / Response May 17, 2004 Educause/Internet 2 Security Professionals Workshop 27

Information Security Program Policy Management ● Posted on the ISO Web Site ● Formal Protocol for Policy Evolution ● Policy Waivers May 17, 2004 Educause/Internet 2 Security Professionals Workshop 28

Information Security Program Communication & Education ● Student, Faculty & Employee Orientation ● e-News – Tips for the Day ● Web Site − Simple but informative − Intranet version debuted April 2004 − Internet version @ http: //oit. wvu. edu/iso ● Posters ● Classes and/or Mini-Workshops – Planning May 17, 2004 Educause/Internet 2 Security Professionals Workshop 29

Information Security Program May 17, 2004 Educause/Internet 2 Security Professionals Workshop 30

Information Security Program Compliance Program ● Measures to Prevent & Detect ● Response to Compromise or Violations ● Continually Evaluate Regulations, Policies & Standards ● ISC plus Management, Providers & Users ● Internal Audit − Critical role in evaluation of compliance & recommendation of measures to help ensure compliance May 17, 2004 Educause/Internet 2 Security Professionals Workshop 31

Information Security Program Reporting & Enforcement ● Vanity e-Mail Account − Information_Security@mail. wvu. edu − For submitting “general” inquiries or reporting potential violations or concerns ● Developing Formal Reporting / Response Protocol ● Information Security Liaisons ● ISC “Action Team” − Fore-runner to an incident response team ● Consequences for Non-compliance May 17, 2004 Educause/Internet 2 Security Professionals Workshop 32

Information Security Program Procurement Oversight ● Service Providers Held to Same Standard as Staff ● Confidential Information [Contract] Addendum − − Definitions of covered data & information Acknowledgement of required access Safeguard standards Reporting ● Audit Standards for Service Provider Contracts May 17, 2004 Educause/Internet 2 Security Professionals Workshop 33

Information Security Program Security-related Efforts ● Business Continuity Plan − Disaster Recovery Plan – In Place − Business Resumption Plan – In Planning ● e-Commerce Review Committee ● Ethics & Confidentiality Notice / Certification − University-wide coverage – Replacement under Review − Departmental / project specific – Some in Place ● SSN Replacement ● Identity Management / Central Authentication May 17, 2004 Educause/Internet 2 Security Professionals Workshop 34

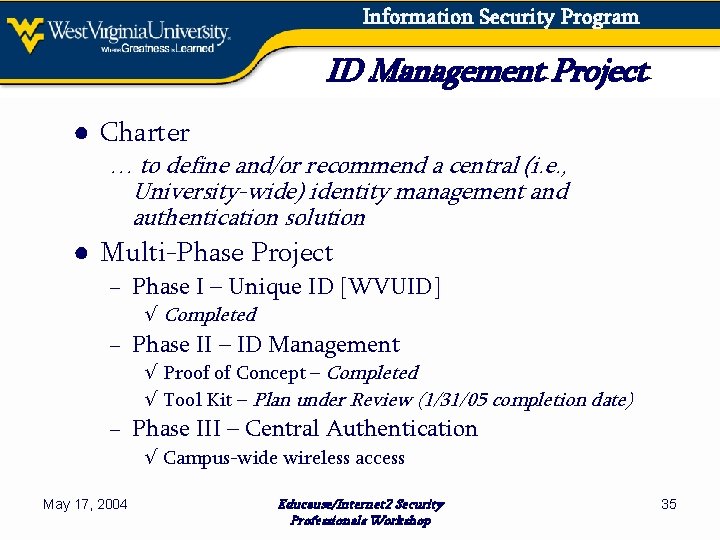
Information Security Program ID Management Project ● Charter … to define and/or recommend a central (i. e. , University-wide) identity management and authentication solution ● Multi-Phase Project − Phase I – Unique ID [WVUID] √ Completed − Phase II – ID Management √ Proof of Concept – Completed √ Tool Kit – Plan under Review (1/31/05 completion date) − Phase III – Central Authentication √ Campus-wide wireless access May 17, 2004 Educause/Internet 2 Security Professionals Workshop 35

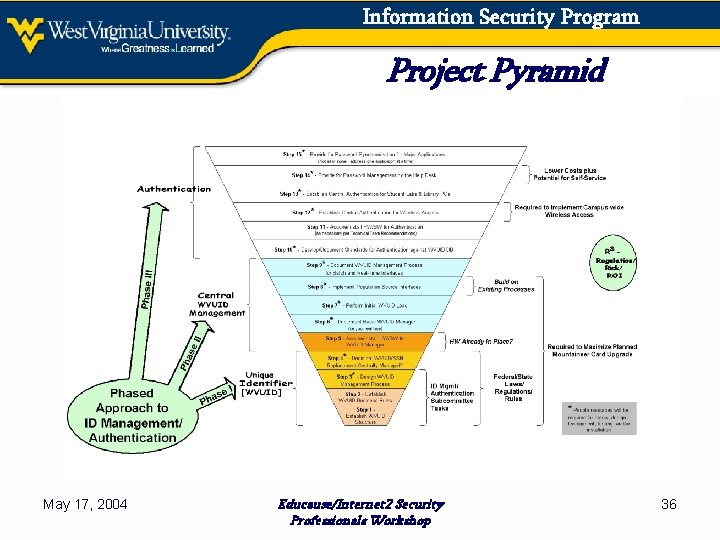
Information Security Program Project Pyramid May 17, 2004 Educause/Internet 2 Security Professionals Workshop 36

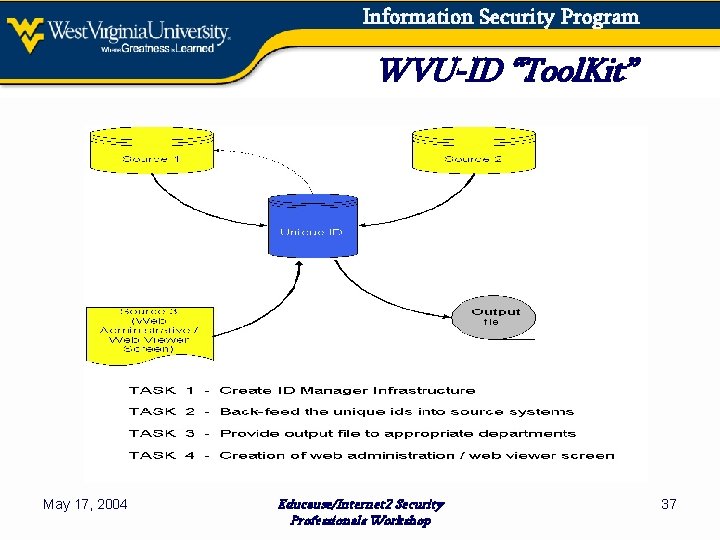
Information Security Program WVU-ID “Tool. Kit” May 17, 2004 Educause/Internet 2 Security Professionals Workshop 37

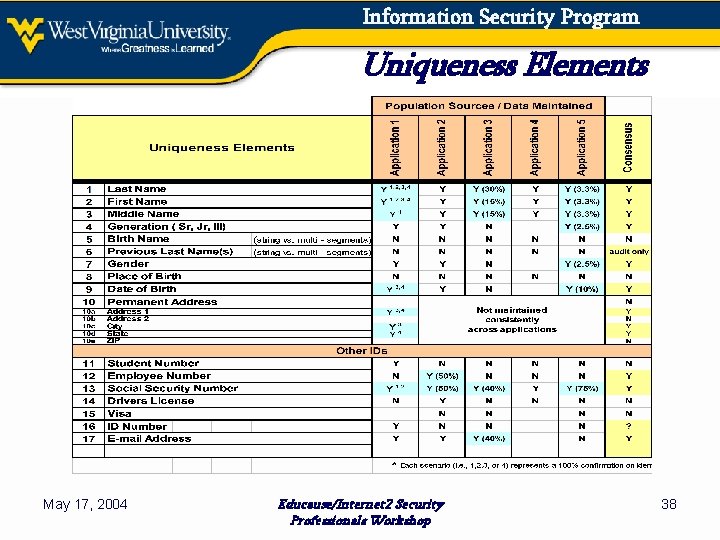
Information Security Program Uniqueness Elements May 17, 2004 Educause/Internet 2 Security Professionals Workshop 38

Information Security Program Where Are We Going Next ● Establish the Information Security Office(r) ● Develop Risk Assessment “Plan of Attack” − Job of the Information Security Council − Initial Focus on Electronic Resources − Risk Assessment Algorithms ● ● ● Classify Information Resources Continue to Address the Use of SSN at WVU Complete the ID Management / Authentication Project Continue to Spread the Word Continue to Review Current Policies / Procedures Implement Compliance, Reporting & Enforcement May 17, 2004 Educause/Internet 2 Security Professionals Workshop 39

Information Security Program A Word To The Wise ● Terminology − Information Security vs. Computer Security ● Cost & Benefits − Determine risk algorithms early in the process ● Consider Current Security Environment − Whenever possible, use existing elements − Can have reasonable plan by connecting dots May 17, 2004 Educause/Internet 2 Security Professionals Workshop 40

Information Security Program A Word To The Wise (cont’d) ● If Policy is Too Relaxed or Non-Existent − Little or no enforcement ● If Policy is Too Strict − Nobody pays attention to it (“hope I don’t get caught!”) − Too complicated, too cumbersome ● Flexibility / Adaptability is Key − Should be independent of specific HW/SW − Policy update mechanisms should be clearly spelled out May 17, 2004 Educause/Internet 2 Security Professionals Workshop 41

Information Security Program Resource Examples ● Federal / State laws, regulations, statutes − WV State Information Security Policy Guidelines ● Other Colleges & Universities ● “Information Security Policies Made Easy” − by Charles Wood ● Information Systems Audit & Control (ISACA) ● CERT, NIST, NSA, SANS, … May 17, 2004 Educause/Internet 2 Security Professionals Workshop 42

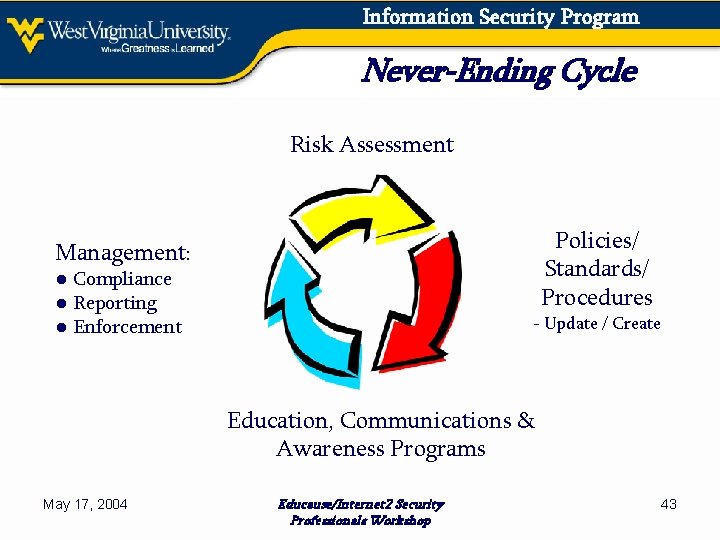
Information Security Program Never-Ending Cycle Risk Assessment Policies/ Standards/ Procedures Management: ● Compliance ● Reporting ● Enforcement - Update / Create Education, Communications & Awareness Programs May 17, 2004 Educause/Internet 2 Security Professionals Workshop 43

Information Security Program Questions and/or Comments May 17, 2004 Educause/Internet 2 Security Professionals Workshop 44

Information Security Program Contacts ● http: //oit. wvu. edu/iso ● Information_Security@mail. wvu. edu ● Sue. Ann. Lipinski@mail. wvu. edu ● RTMarton@mail. wvu. edu ● Mark. Six@mail. wvu. edu May 17, 2004 Educause/Internet 2 Security Professionals Workshop 45