Information Security Occupations and Certifications Dr Cheryl Hinds


























- Slides: 32

Information Security Occupations and Certifications Dr. Cheryl Hinds (Computer Science Department) & Dr. Robert Perkins (Sociology)

Overview Introduction Job Roles Certifications

Introduction In order to maintain a secure work environment the Security Department must be staffed with an appropriate mix of skilled and screened personnel.

General Requirements for Info. Sec

General Requirements When hiring security professionals at all levels organizations frequently look for individuals who: Understand how organizations are structured and operated Recognize that management cannot handle security with technology alone. Work well with people in general, including users, and having strong written and verbal communication skills Acknowledge the role of policy in guiding security efforts

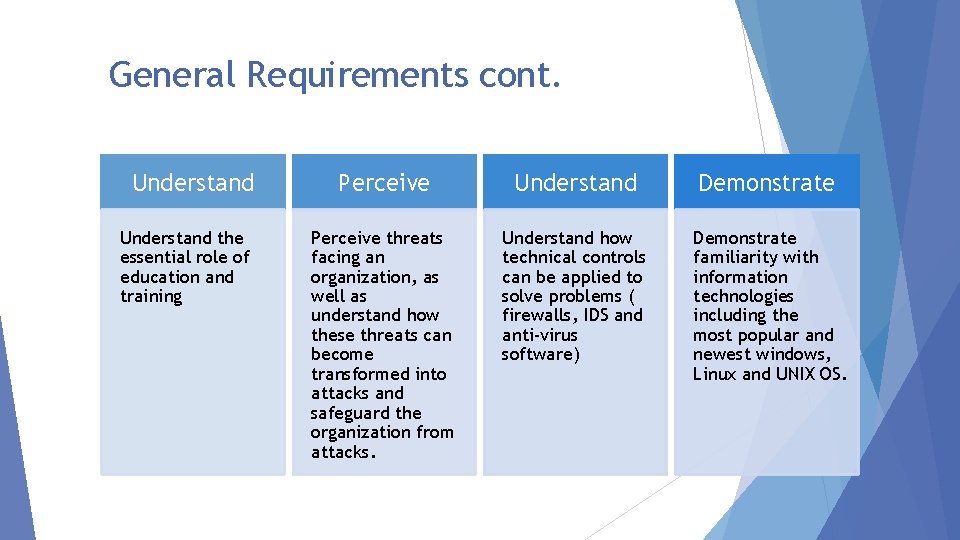
General Requirements cont. Understand the essential role of education and training Perceive Understand Demonstrate Perceive threats facing an organization, as well as understand how these threats can become transformed into attacks and safeguard the organization from attacks. Understand how technical controls can be applied to solve problems ( firewalls, IDS and anti-virus software) Demonstrate familiarity with information technologies including the most popular and newest windows, Linux and UNIX OS.

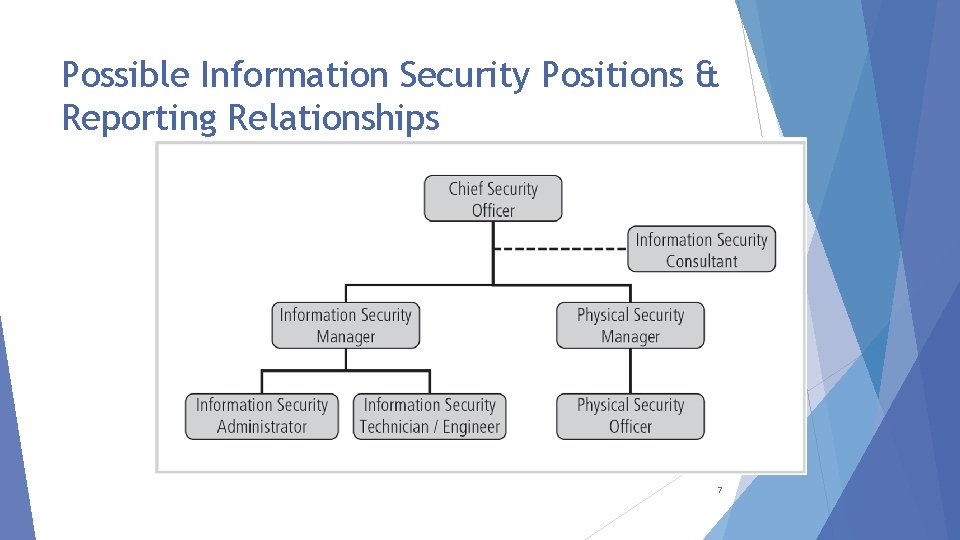
Possible Information Security Positions & Reporting Relationships 7

Chief Information Officer(CIO)

01 02 Chief information Officer(CIO) is an executive level position that oversees the organizations computing technology and staves to create efficiency in the processing and access of an organizations information. The Chief information Security officer(CISO) reports to the Chief information Officer(CIO), unless the organization employs a Chief Security office(CSO), who over sees both. What is a CIO

Chief Information Security Officer (CISO)

CISO Occupation CISO is considered to be the Top Inf. Security position in the organization. He/she frequently reports to the Chief information officer(CIO). CISO are business mangers first and Technologists second. They are conversant in all areas of Info. Sec including technology planning and policy. They develop Info. Sec budgets based on available funding and make decisions about purchasing, project and technology implementation and recruiting hiring and fire security staff. CISO is the spokesperson fo the secuity team and is responsible for the overall security program.

Qualification for CISO The most common certifications include The most common qualification for CISO included working as a security manager as well as Experience in planning, policy and budgets. • Certified information Systems Security Professional (CISSP) • Certified information Security Manager (CISM). • A Bachelors degree is almost always required • Graduated degree in business technology or another related field.

Security Manger

Security Manager Occupation A security manager is accountable for the day to day operation of all or part of the Info. Sec program. They accomplish objectives identified by the CISO and resolve issues identified by technicians. They are often assigned specific managerial duties by the CISO including policy development, risk assessment, contingency planning and operational and tactical planning for security function. Maintain current and appropriate body of knowledge necessary to perform the management functions

Security Manger Qualification and position requirements. It is not uncommon for a Security Manger to have the same Certifications as a CISO which is a CISSP or CISM. Must have experience in traditional business activities including budgeting, project management, personnel management. Must be able to draft middle-level and lower-level policies as well as standards and guidelines

Security Technician

A Security Technician is a technically qualified individual who may: configure firewalls configure intrusion detection prevention systems implement security software diagnoses and troubleshoot problems coordinate with systems and network administrators to ensure that security technical control are properly implemented. Security Technician occupation

Security Technician Qualifications and Position requirements. Organizations prefer experts, certified, proficient technicians. (Security Technicians are likely to be IT Technicians who have adopted a different Career Path) This job requires some level of experience with a particular hardware and software package. Comp. TIA certifications such as: Security + and other Comp. TIA certs. Experience using Technology is required.

Information Security Professional Certifications

The Certified information systems Security Professional(CISSP) certification isconsidered to be the most prestigious certification for Security managers and CISO. To sit for the CISSP exam the candidate must Have at least five years of direct, fulltime Security professional work experience in two or more of 10 domains or four years of direct Security work experience in two or more domains and a 4 year college degree. CISSP consist of 250 multiple choice questions and must be completed within 6 hours

What does the exam cover? This exam covers 10 Domains of Info. Sec knowledge: Access control Business continuity and disaster recovery planning Cryptography Info. Sec governance and risk management Legal, regulations, investigation, compliance Operation security Physical security Security architecture and design Software development security Telecommunication and network security.

Since it is difficult to master all 10 domains and the qualifications for a CISSP certification many security professionals seek less rigorous certifications such as the Systems Security Certified Practitioner (SSCP). SSCP focuses on practices, roles and responsibilities as defined by experts from major Info. Sec industries The SSCP exam consist of 125 multiple choice questions Must finish within 3 hours. SSCP

What does this Exam cover? This exam covers 7 domains: Access control Security operations and administration Risk identification, monitoring, and analysis Incident response and recovery Cryptography Network and communications Security Systems and application Security

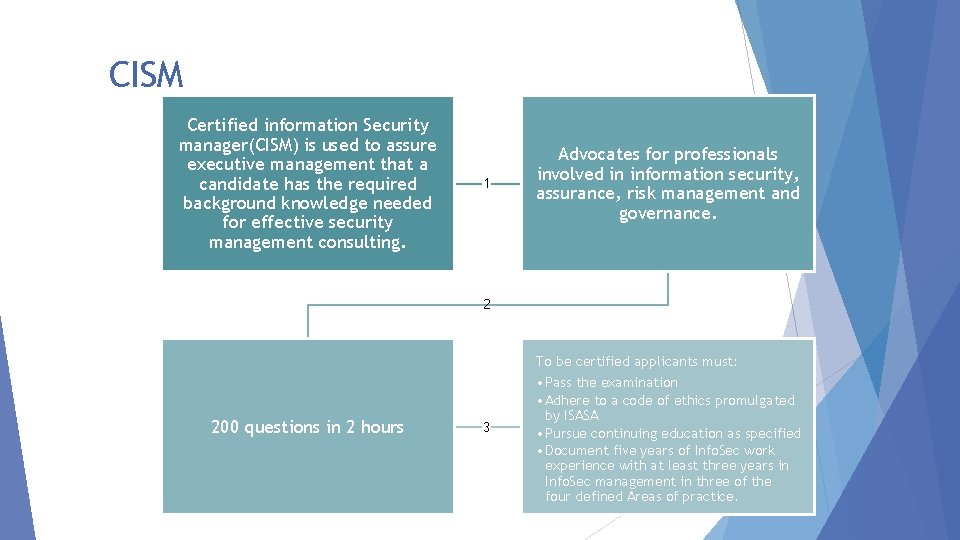
CISM Certified information Security manager(CISM) is used to assure executive management that a candidate has the required background knowledge needed for effective security management consulting. 1 Advocates for professionals involved in information security, assurance, risk management and governance. 2 To be certified applicants must: 200 questions in 2 hours 3 • Pass the examination • Adhere to a code of ethics promulgated by ISASA • Pursue continuing education as specified • Document five years of Info. Sec work experience with at least three years in Info. Sec management in three of the four defined Areas of practice.

What does this Exam consist of? Information security governce (24 percent) Information Risk Management and Compliance (33 percent) Information Security Program Development and Management (25 percent) Information security incident management(18 percent)

Comp. TIA certifications -CASP The Comp. TIA Advanced security practitioner is the organization’s newest Mastery-Level Certification. This Exam Covers the Technical knowledge and skills required to conceptualize, design, and engineer secure solutions across complex enterprise environment. The multiple choice exam certification requires 10 years experience in IT with a minimum of 5 years of Technical, hands-on, security experience. It consist of 80 questions and must be completed in 2 hours.

What does this Exam consist of? This exam consist of 5 domains: Enterprise security(30 percent) Risk management and incident response (20 percent) Research and Analysis (18 percent) Integration of computing, communications, and business disciplines (16 percent) Technical integration of enterprise components (16 percent)

Security + certification is designed to test for basic security knowledge of mastery of a person who has two years on the job networking experience, with an emphasis on security. This exam covers industry-wide topics, including communication security, infrastructure security, cryptography, access control, authentication, external attacks and operation and organization security. 90 questions (Multiple choice, Multiple response, Fill in the blank, Drag and drop, Exhibits, and Performance-based Questions) Time limit is 90 minutes Comp. TIA – Security +

What does this exam consist of? The security + exam consist of 6 domains: Network security(20 percent) Compliance and operational security(18 percent) Threats and vulnerabilities (20 percent) Application, data, and host security(15 Percent) Access control an identity management(15 percent) Cryptography(12 percent)

Certification Costs Certifications cost money, and the more preferred certifications can be expensive Given the nature of the knowledge needed to pass the examinations, most experienced professionals find it difficult to do well without at least some review Certifications are designed to recognize experts in their respective fields, and the cost of certification deters those who might otherwise take the exam just to see if they can pass Most examinations require between two and three years of work experience, and they are often structured to reward candidates who have significant hands-on experience 30

Information Security Career Paths 31
