INFORMATION SECURITY MANAGEMENT LECTURE 5 DEVELOPING THE SECURITY
























- Slides: 31

INFORMATION SECURITY MANAGEMENT LECTURE 5: DEVELOPING THE SECURITY PROGRAM You got to be careful if you don’t know where you’re going, because you might not get there. – Yogi Berra

Introduction: Information Security Program The overall combination of technical, operational and procedural measures, and management structures implemented to provide for the confidentiality, integrity and availability of information based on business requirements and risk analysis 1 Ex. Federal Government Security Ex. University of Washington 1 ISACA, CISM® Review Manual 2008, USA, 2007, p. 34

Organizing for Security • Variables involved in structuring an information security program:

Does Size Matter? : Approaches to Programs • Larger Organization • Medium Sized Organization • Small Business

Security: Very Large Organizations Security budgets often grow faster than IT budgets Even with a large budget, the average amount spent on security per user is still smaller than any other type of organization

Security: Large Organizations Security approach has often matured, integrating planning and policy into the organization’s culture One approach separates functions into four areas: – Non-technology business units outside of IT – IT groups outside of information security area – Information Security Dept. (customer service) – Information Security Dept. (compliance)

Security: Large Organizations (cont’d. ) • The CISO has responsibility for information security functions • The deployment of full-time security personnel depends on: – – Sensitivity of the information to be protected Industry regulations General profitability Budgetary Constraints

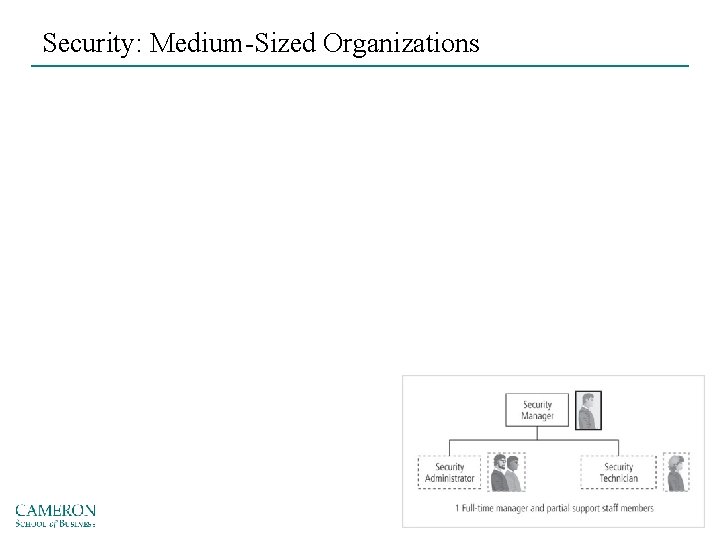
Security: Medium-Sized Organizations

Security: Small Organizations

Components of the Security Program • Organization’s information security needs – Unique to the culture, size, and budget of the organization • Determining what level the information security program operates on depends on the organization’s strategic plan http: //www. isaca. org/Journal/Past-Issues/2009/Volume-5/Pages/JOnline-Information-Security-Program-Establishing-It-the-Right-Way-for-Continued-Success. aspx

Critical Elements of the Security Program • • • Senior management commitment to information security initiatives Management understanding of information security issues Information security planning prior to implementation of new technologies Integration between business and information security Alignment of information security with the organization’s objectives Executive and line management ownership and accountability for implementing, monitoring and reporting on information security Additionally: • Appropriate employee SETA on asset protection • Consistent enforcement of Info. Sec policies/standards • Ability to cost-justify security http: //www. isaca. org/Knowledge-Center/Research/Documents/Critical-Elements-of-Information-Security-Program-Success_res_Eng_0105. pdf

Information Security Roles and Titles • Types of information security positions – Those that define – Those that build – Those that administer • A typical organization has a number of individuals with information security responsibilities

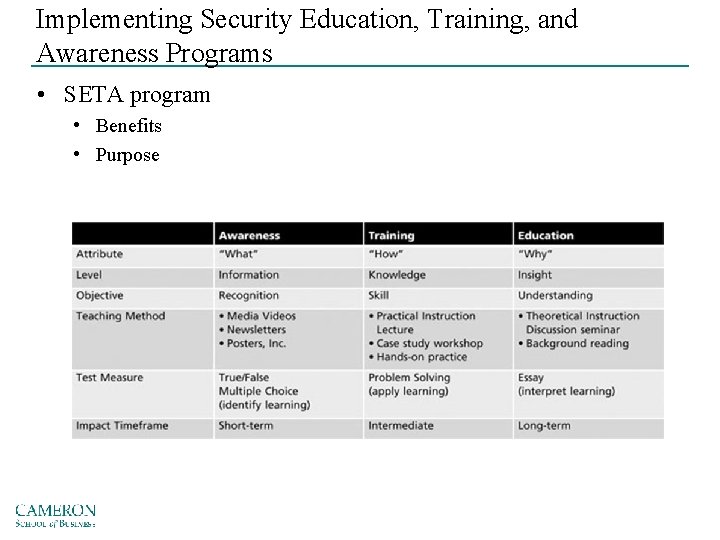
Implementing Security Education, Training, and Awareness Programs • SETA program • Benefits • Purpose

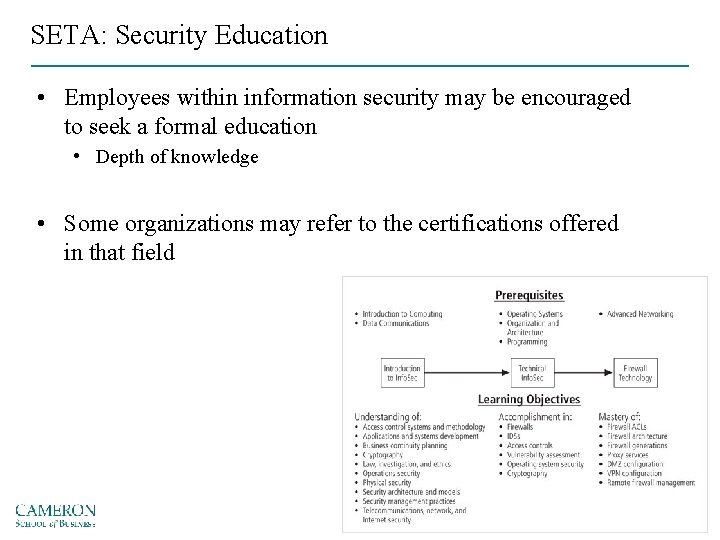
SETA: Security Education • Employees within information security may be encouraged to seek a formal education • Depth of knowledge • Some organizations may refer to the certifications offered in that field

SETA: Security Education Developing Education Program • Once the knowledge areas are identified, common knowledge areas are aggregated into teaching domains • Course design – Should enable a student to obtain the required knowledge and skills upon completion of the program – Identify the prerequisite knowledge for each class

SETA: Security Training • Involves providing detailed information and hands-on instruction • Management can either develop customized training or outsource • Customizing training for users: • Functional Background • Skill Level

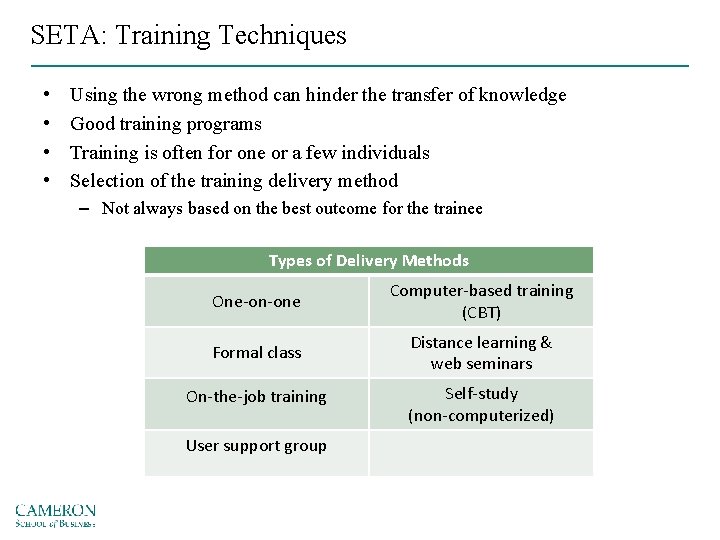
SETA: Training Techniques • • Using the wrong method can hinder the transfer of knowledge Good training programs Training is often for one or a few individuals Selection of the training delivery method – Not always based on the best outcome for the trainee Types of Delivery Methods One-on-one Computer-based training (CBT) Formal class Distance learning & web seminars On-the-job training Self-study (non-computerized) User support group

SETA: Security Awareness • Less frequently implemented, but most effective security methods • Security awareness programs: – Set the stage for training by changing organizational attitudes to realize the importance of security and the adverse consequences of its failure – Remind users of the procedures to be followed

SETA: Security Awareness (cont’d. ) • Best practices: – – – – – Focus on people Refrain from using technical jargon Use every available venue Define learning objectives, state them clearly, and provide sufficient detail and coverage Keep things light Don’t overload the users Help users understand their roles in Info. Sec Take advantage of in-house communications media Make the awareness program formal • Plan and document all actions Provide good information early, rather than perfect information late

SETA: Security Awareness (cont’d. ) • Commandments of information security awareness training – – – Information security is a people issue Speak their language If they cannot see it, they will not learn it Make your point, support it, and conclude it Always let the recipients know how the behavior that you request will affect them – Formalize your training methodology – Always be timely

SETA: Security Awareness (cont’d. ) • Designed to modify any employee behavior that endangers the security of the organization’s information • Effective programs make employees accountable for their actions • Dissemination and enforcement of policy become easier • Demonstrating due care and due diligence can help indemnify the institution against lawsuits

SETA: Security Awareness (cont’d. ) • Awareness can take on different forms for particular audiences • A security awareness program can use many methods to deliver its message • Recognize that people tend to practice a tuning out process (acclimation)

SETA: Security Awareness (cont’d. ) • Many security awareness components are available at little or no cost – Others can be very expensive • Examples of security awareness components – Videos – Another One – Posters and banners – Lectures and conferences – Computer-based training

Case Discussion: Safety Approach to IS Communications • Security Communications • Mental Models • Risk Perception • Risk Compensation

Security Awareness (cont’d. ) • Organizations can establish Web pages or sites dedicated to promoting information security awareness • Tips on creating and maintaining an educational Web site (cont’d. ) – – Keep page loading time to a minimum Seek feedback Assume nothing and check everything Spend time promoting your site

Case: Making Info. Sec User Friendly • User mentality • Approach to information assets • Loss of information • Improving the current model/approach to Info. Sec

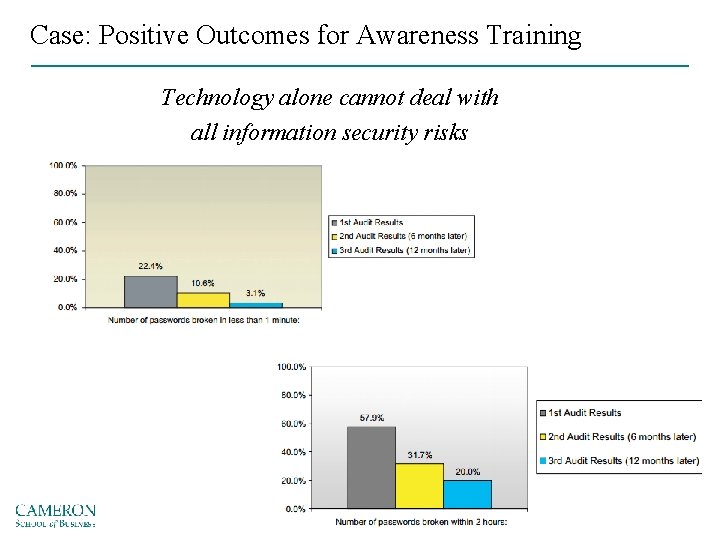
Case: Positive Outcomes for Awareness Training Technology alone cannot deal with all information security risks

Discussion Topics Discuss the advantages and disadvantages of nesting the information security role within the information technology (IT) part of the organization. Discuss posters, trinkets, and Web sites as information security awareness methods. What are some advantages and disadvantages of each method? Which do you think is the best method and why?

Useful Resources • Building an SETA program • Microsoft Security Awareness

Summary • • • Organizing for security Placing information security within an organization Components of the security program Information security roles and titles Implementing security education, training, and awareness programs

Reminders • Next Week • Security Management Models • Demo Project – Start to brainstorm • Term Paper • Need topic by next week