Information Security Investments in Organizations How its actually

- Slides: 3

Information Security Investment's in Organizations – How it's actually been done? Daniel Dor & Prof. Yuval Elovici Ben-Gurion University of the Negev Abstract Method According to Creswell (2009), grounded theory is “a qualitative strategy of inquiry in which the researcher derives a general, abstract theory of process, action, or interaction grounded in the views of participants in a study. ” (p. 13 & 229) this process involves using multiple stages of data collection and the refinement and interrelationships of categories of information. In this research, we’ve used a Contextual Analysis software (Machine Learning and Human Input capabilities) combined with Grounded Theory, in order to find correlations between different Categories in the information security investments process, and different concepts within this process. Our research displays connected categories and concepts that appear in the Information security Investments decision process in several SMB’s. Introduction Propositions In Grounded Theory, researchers using an iterative coding process, in which they review the data collected, code it, analyze it, understand the concepts and categories that appear in it, and using those concepts and categories in order to formulate a theory. We’ve conducted several interviews with CISOs and CIOs that making decisions regarding Information Security Investment. In those interviews, the subjects told us how the IS Investments process of decision making is being done. We enhanced the subjects results with data that we gained from the Literature. The data was extracted using a Contextual Analysis software, in which we’ve used Machine Learning to “learn” the Literature, and then we’ve tried to see correlations between concepts and categories that found during the interviews. The research is still in progress, but a draft of 14 thorys’ propositions is already for discussion. (P 1) External Environments of Business is associated with organizational cyber security education and awareness, the need for Information security compliance and the understanding of Information security threats landscape. (P 2) Organizational Structure or Behavior is associated with Prioritization and budgeting, Organizational cyber security education and awareness, Risk Management, Decision makers and Doctrine and or organizational policy. (P 3) Identification of the cyber threat landscape is associated with Prioritization and budgeting, Organizational cyber security education and awareness, Information security threats, Decision makers, and with Doctrine and or organizational policy. (P 4) Current cyber security situation in the organization is associated with Quality, Applying information security capabilities, Information security threats, Risk Management, Decision variable and with Doctrine and or organizational policy. (P 5) Organizations cyber security gap analysis is associated with Information security threats, Risk Management and Decision makers. (P 6) Detection of required capabilities is associated with Strategy, Prioritization and budgeting, Information security compliance, Information security threats, Risk Management, Decision makers, Competitive Advantage, and with Customer expectations. (P 7) Detection of alternatives is associated with Prioritization and budgeting, Applying information security capabilities, Information security threats, and with Start-ups. (P 8) Inspection of alternatives is associated with Constraints, Information security compliance, Risk Management, Decision makers and with Decision variable. (P 9) Picking a portfolio of projects is associated with Prioritization and budgeting, Organizational cyber security education and awareness, Risk Management and with Decision makers. (P 10) Proof of Concept is associated with Decision makers and with Decision variable. (P 11) Decision andor execution is associated with Risk Management, Decision makers and with Decision variable. (P 12) Project's initiation is associated with Prioritization and budgeting, Decision makers and whit Projects concept. (P 13) Project's Planning is associated with Projects concept (P 14) Project's execution and Implementation is associated with Constraints, Organizational cyber security education and awareness, Risk Management, Projects and with Quality References Creswell, J. W. (2009). Research Design: Qualitative, Quantitative, and Mixed Approaches. TO, CA: Sage. Posey, C. , Roberts, T. L. , Lowry, P. B. , & Hightower, R. T. (2014). Bridging the divide: A qualitative comparison of information security thought patterns between information security professionals and ordinary organizational insiders. Information & Management, 51(5), 551 -567. Vannoy, S. A. and Salam, A. F. (2010). Managerial Interpretations of the Role of Information Systems in Competitive Actions and Firm Performance: A grounded theory investigation, ISR 21(3): 496– 515.

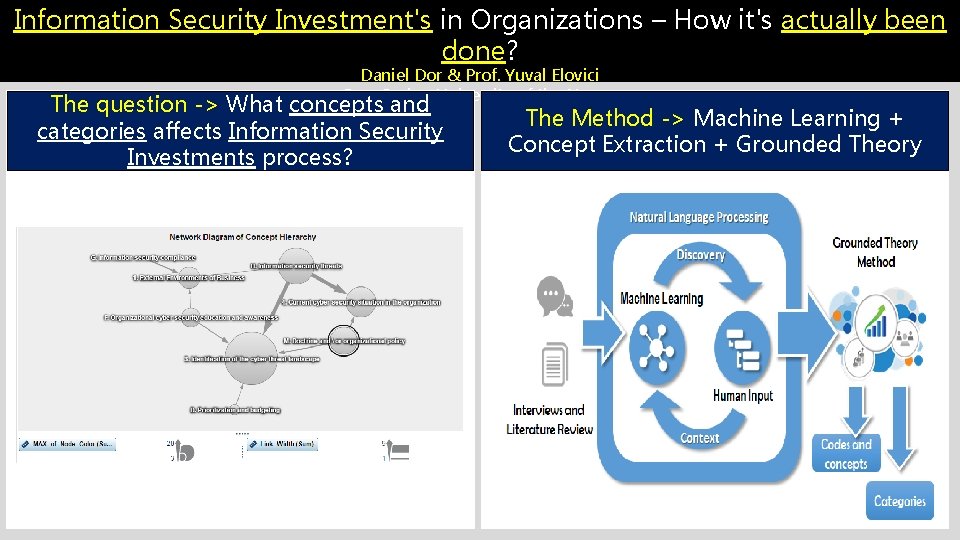
Information Security Investment's in Organizations – How it's actually been done? Daniel Dor & Prof. Yuval Elovici Ben-Gurion University of the Negev The question -> What concepts and categories affects Information Security Investments process? The Method -> Machine Learning + Concept Extraction + Grounded Theory

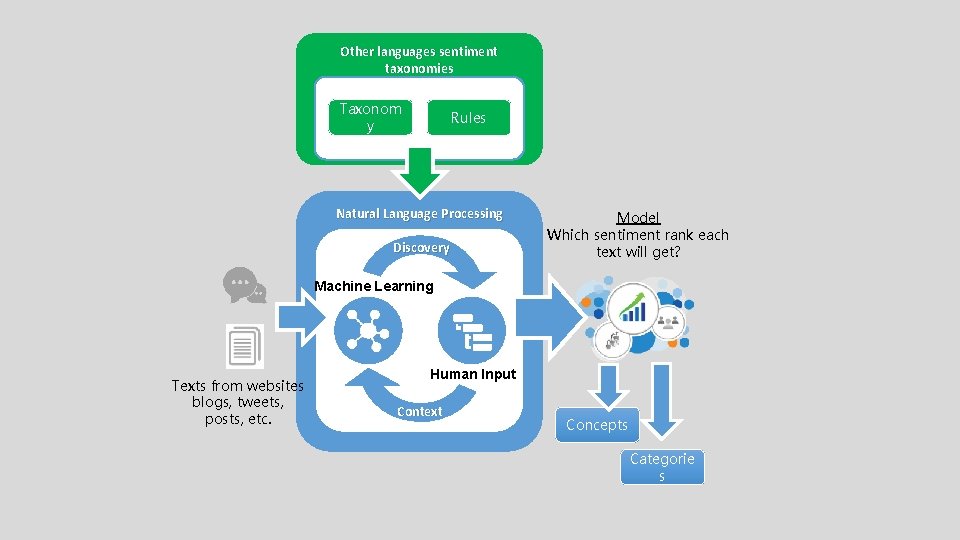
Other languages sentiment taxonomies Taxonom y Rules Natural Language Processing Discovery Model Which sentiment rank each text will get? Machine Learning H JL Texts from websites blogs, tweets, posts, etc. Human Input Context Concepts Categorie s