Information Security for Sensors Overwhelming Random Sequences and






![Comparison With Previous Schemes Paper Length of initial secret Ding-Rabin [1] k log n Comparison With Previous Schemes Paper Length of initial secret Ding-Rabin [1] k log n](https://slidetodoc.com/presentation_image_h2/2a6c85bf84c5cb9485d85ba45301bf86/image-18.jpg)





















- Slides: 41

Information Security for Sensors Overwhelming Random Sequences and Permutations Presented by Shlomi Dolev (joint work with Niv Gilboa, Marina Kopeetsky, Giuseppe Persiano, and Paul G. Spirakis)

General Outline • • • Introduction and Motivation Problem Statement Permutation Revealing Protocol PRP Permutation Encrypted Protocol PEP Improving Key Exchange Algorithms Conclusions

Bounded Storage Model • Introduced by Maurer (‘ 92) • Model – Adversary has bounded storage capacity – A source of random bits broadcasts more traffic than adversary can store • Task: Key exchange • Information Theoretic security – No computational assumptions

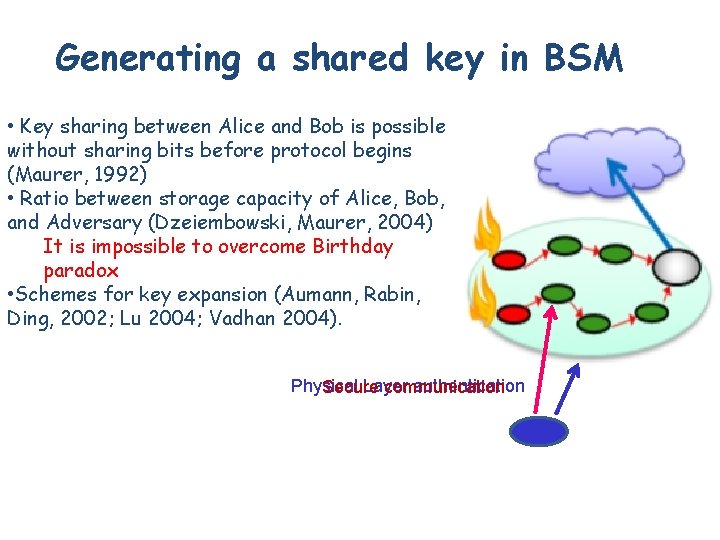
Generating a shared key in BSM • Key sharing between Alice and Bob is possible without sharing bits before protocol begins (Maurer, 1992) • Ratio between storage capacity of Alice, Bob, and Adversary (Dzeiembowski, Maurer, 2004) It is impossible to overcome Birthday paradox • Schemes for key expansion (Aumann, Rabin, Ding, 2002; Lu 2004; Vadhan 2004). Physical Layer authentication Secure communication

Our Contribution • Information Theoretic Secure key exchange schemes for BSM – Permutation Revealing Protocol PRP – Permutation Encrypted Protocol PEP • Especially suitable for resource constrained & wireless environment – Simple – to implement and to run – Efficient – Uses typical physical implementation • Traffic is sent in frames • Random source works in parallel over several channels

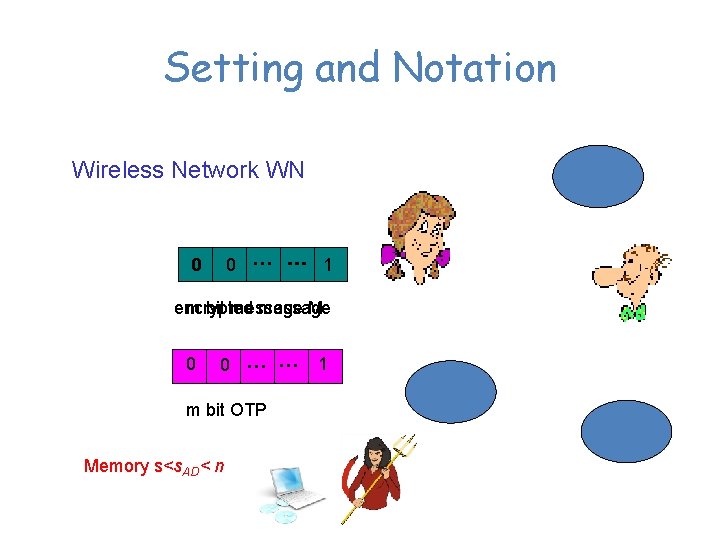
Setting and Notation Wireless Network WN … 1 0 … … 1 0 encrypted m bit message M 0 0 … … m bit OTP Memory s<s. AD< n 1 S

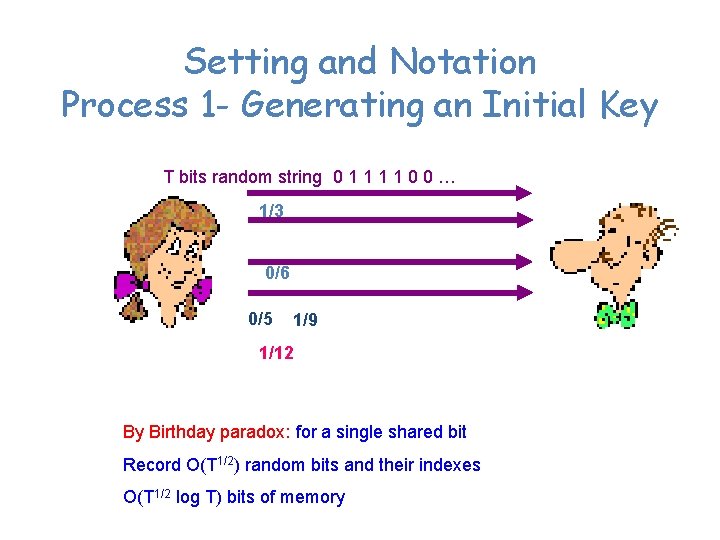
Setting and Notation Process 1 - Generating an Initial Key T bits random string 0 1 1 0 0 … 1/3 0/6 0/5 1/9 1/12 By Birthday paradox: for a single shared bit Record O(T 1/2) random bits and their indexes O(T 1/2 log T) bits of memory

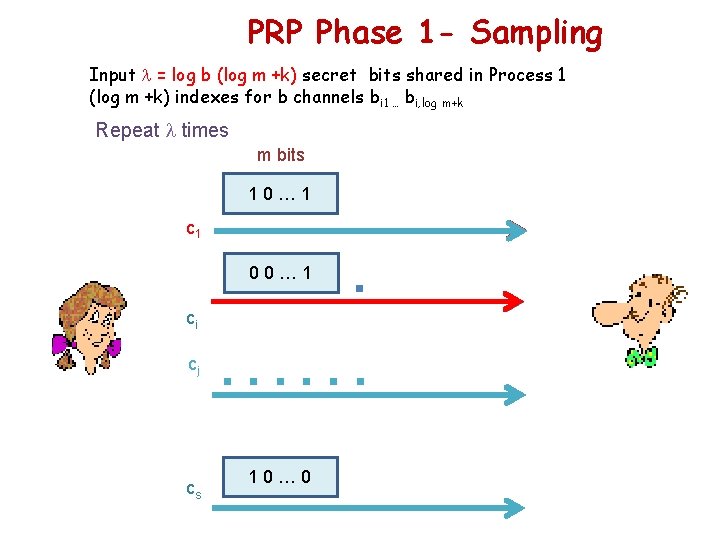
PRP Phase 1 - Sampling Input = log b (log m +k) secret bits shared in Process 1 (log m +k) indexes for b channels bi 1 … bi, log m+k Repeat times m bits 10… 1 c 1 . . . 00… 1 ci cj cs . . . 10… 0

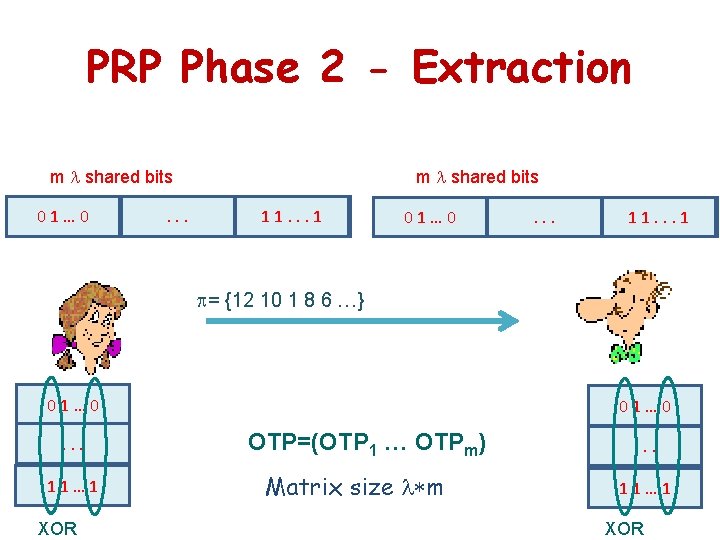
PRP Phase 2 - Extraction m shared bits … 01 10 01 … . …. . m shared bits 1 10. …. . 11 … 01 10 01 … . …. . 1 1 10. … = {12 10 1 8 6 …} 01… 0. . . 11… 1 XOR 01… 0 OTP=(OTP 1 … OTPm) Matrix size m . . . 11… 1 XOR

PRP Theorem 1 Assume, that Ad is computationally unbounded, but its storage is limited to s. AD bits, s. AD < L/2, where L=min(T, bm ). Assume further that Ad is limited to storing bits of the random string and does not store a function of these bits. Then PRP outputs an OTP of m bits that Alice and Bob share, and the probability that Ad determines even a single bit of the OTP correctly is less than 1/2+2 -k.

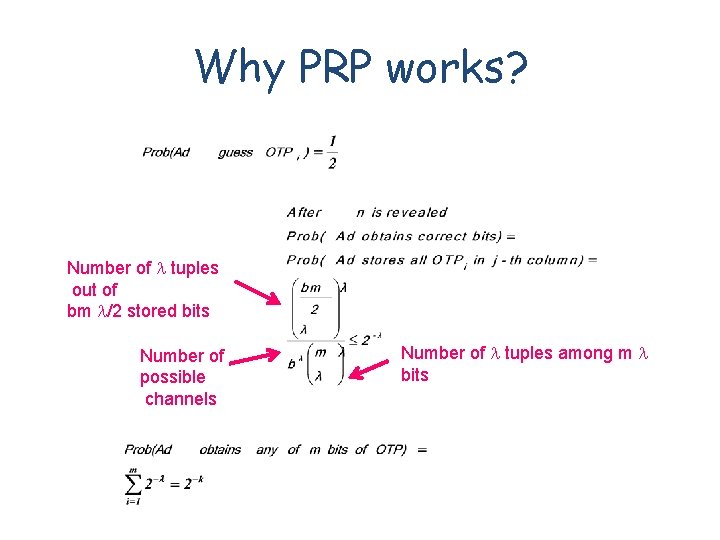
Why PRP works? Number of tuples out of bm /2 stored bits Number of possible channels Number of tuples among m bits

Permutation Encrypted Protocol PEP Motivation: OTP in PRP is not reusable and it is valid for a single encryption.

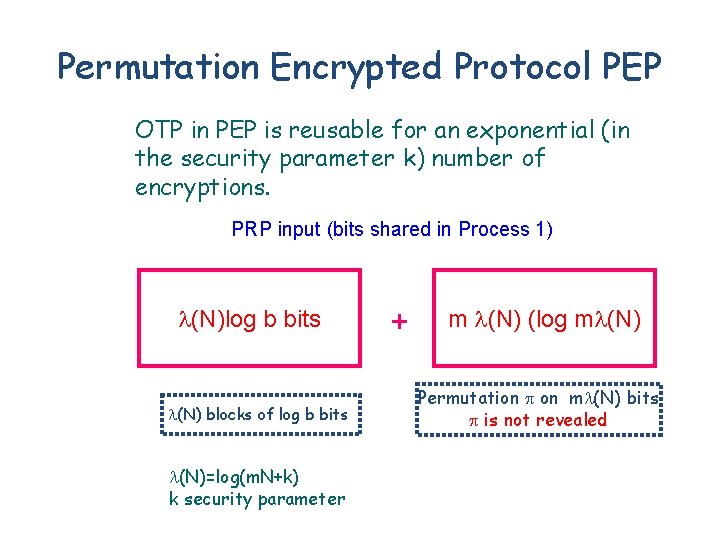
Permutation Encrypted Protocol PEP OTP in PEP is reusable for an exponential (in the security parameter k) number of encryptions. PRP input (bits shared in Process 1) (N)log b bits (N) blocks of log b bits (N)=log(m. N+k) k security parameter + m (N) (log m (N) Permutation on m (N) bits is not revealed

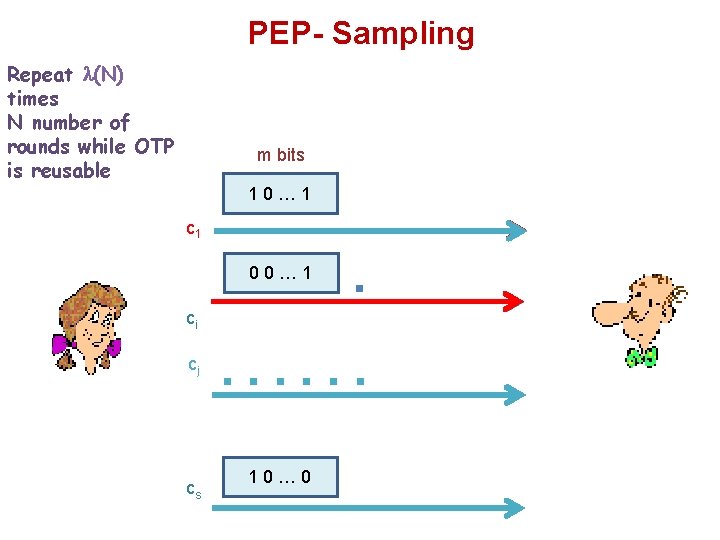
PEP- Sampling Repeat (N) times N number of rounds while OTP is reusable m bits 10… 1 c 1 . . . 00… 1 ci cj cs . . . 10… 0

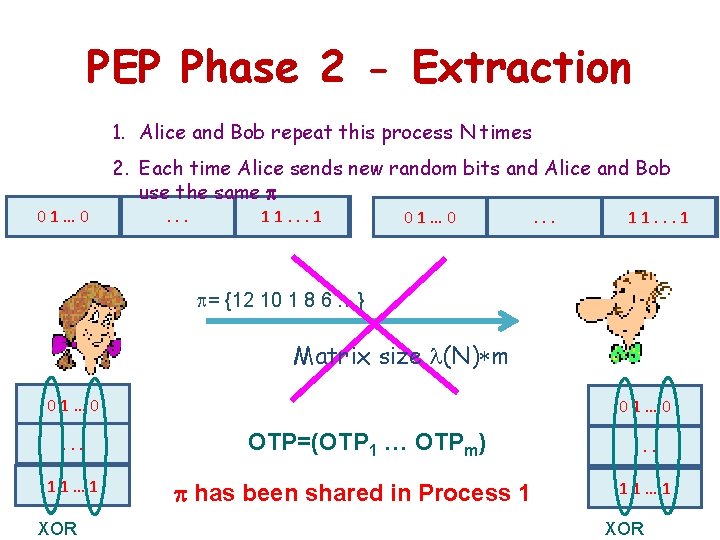
PEP Phase 2 - Extraction 1. Alice and Bob repeat this process N times … 01 10 01 … 2. Each time Alice sends new random bits and Alice and Bob use the same . …. . 1 10. …. . 11 … 01 10 01 … . …. . 1 1 10. … = {12 10 1 8 6 …} Matrix size (N) m 01… 0. . . 11… 1 XOR 01… 0 OTP=(OTP 1 … OTPm) has been shared in Process 1 . . . 11… 1 XOR

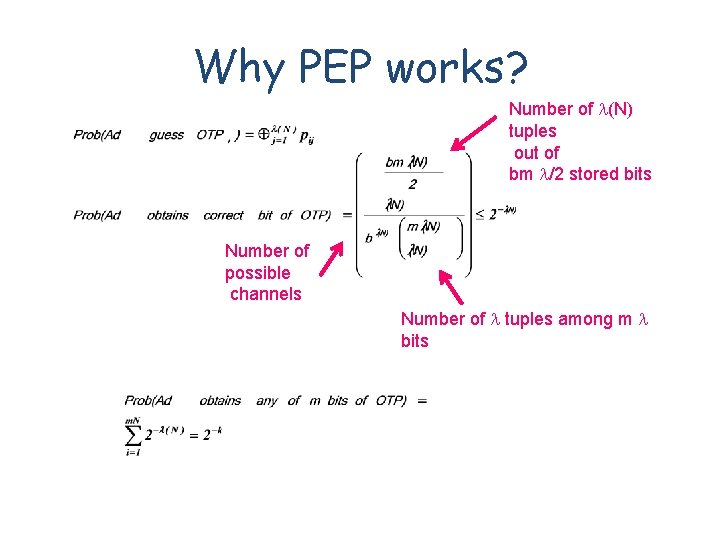
Why PEP works? Number of (N) tuples out of bm /2 stored bits Number of possible channels Number of tuples among m bits

Comparison With Previous Schemes • Efficiency measure- expansion factor – Unified “Sample and Extract Approach” (Lu and Vadhan) • High computationally complexity
![Comparison With Previous Schemes Paper Length of initial secret DingRabin 1 k log n Comparison With Previous Schemes Paper Length of initial secret Ding-Rabin [1] k log n](https://slidetodoc.com/presentation_image_h2/2a6c85bf84c5cb9485d85ba45301bf86/image-18.jpg)
Comparison With Previous Schemes Paper Length of initial secret Ding-Rabin [1] k log n Dziembowski-Maurer [2] k log n Lu [3] (k+log n)2 /log n Vadhan [4] k+log n Our work Log b(k+log m) k> log b: our expansion factor is better [1], [2] k> log b log n: our expansion factor is better than [3] b=2: our expansion factor is better by constant factor than [4]

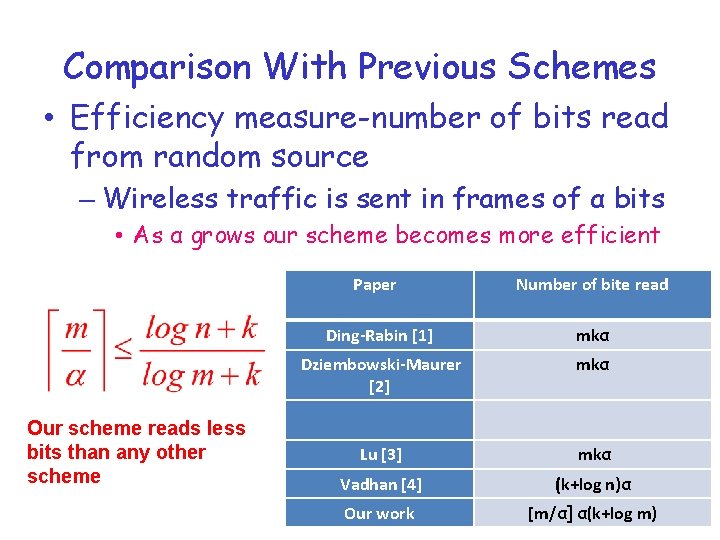
Comparison With Previous Schemes • Efficiency measure-number of bits read from random source – Wireless traffic is sent in frames of α bits • As α grows our scheme becomes more efficient Our scheme reads less bits than any other scheme Paper Number of bite read Ding-Rabin [1] mkα Dziembowski-Maurer [2] mkα Lu [3] mkα Vadhan [4] (k+log n)α Our work [m/α] α(k+log m)

Improving Key Exchange Algorithms

Conclusions • A new technique – Defining sections of random sequences, rather then bits – Random permutation of the bits among the concatenation of the chosen sections • PRP and PEP fit multi-frequency wireless communication – Choice subset of frequencies implies exponentially growing security parameter • Establishing short secret from scratch.



















