Information Security Cybercrime status and way forward writing

Information Security & Cybercrime status and way forward (writing on the wall) Sherif El-Kassas CTO Secure. Misr December 20, 2011/12/20 1

Outline • Information Security Overview • Technology and Trust (local perspective) • Way forward: – Societal directions – R&D directions 2011/12/20 2

Cybercrime 2011/12/20 3
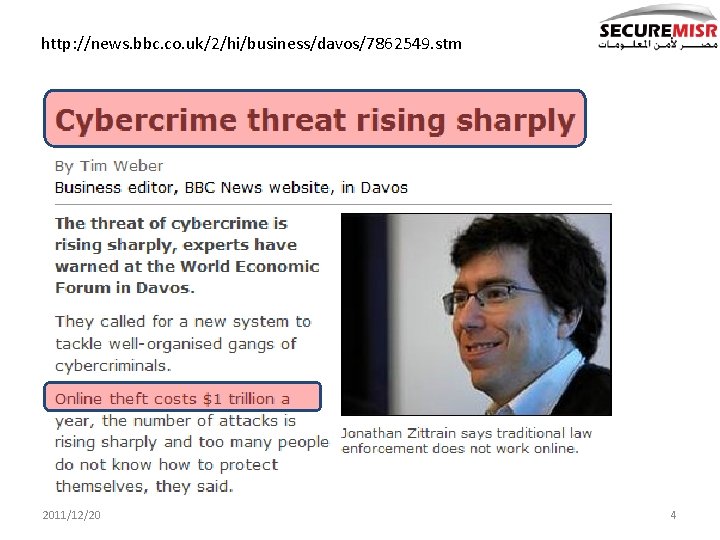
http: //news. bbc. co. uk/2/hi/business/davos/7862549. stm 2011/12/20 4
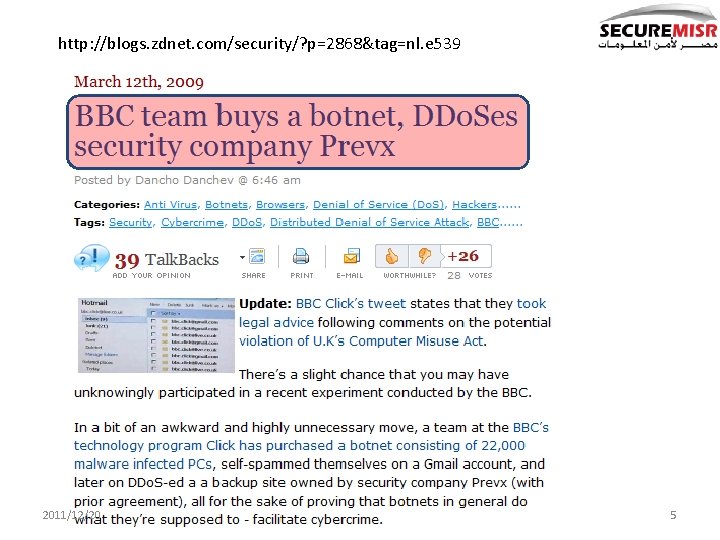
http: //blogs. zdnet. com/security/? p=2868&tag=nl. e 539 2011/12/20 5
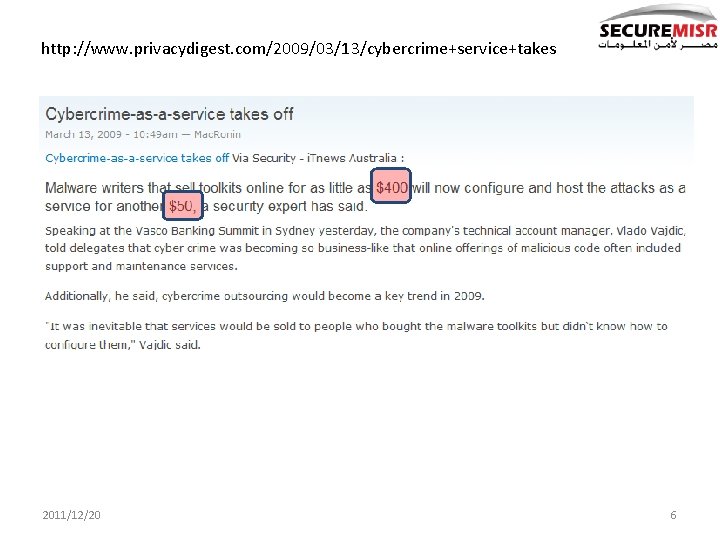
http: //www. privacydigest. com/2009/03/13/cybercrime+service+takes 2011/12/20 6

Information Security News Our Region 2011/12/20 7
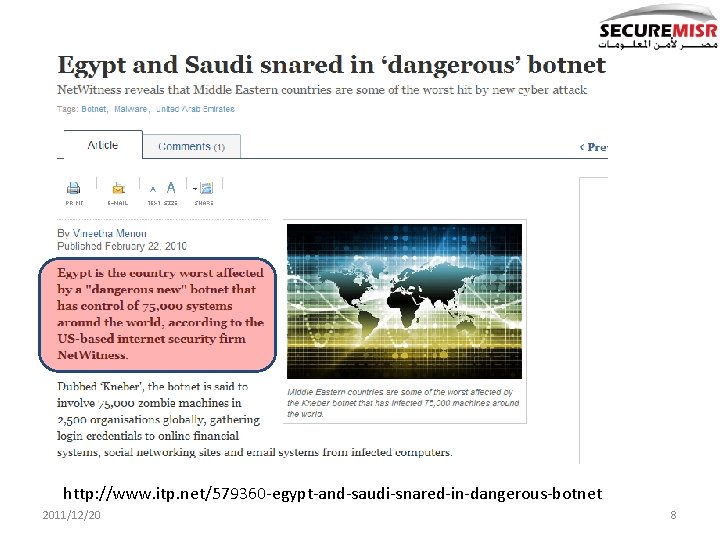
http: //www. itp. net/579360 -egypt-and-saudi-snared-in-dangerous-botnet 2011/12/20 8
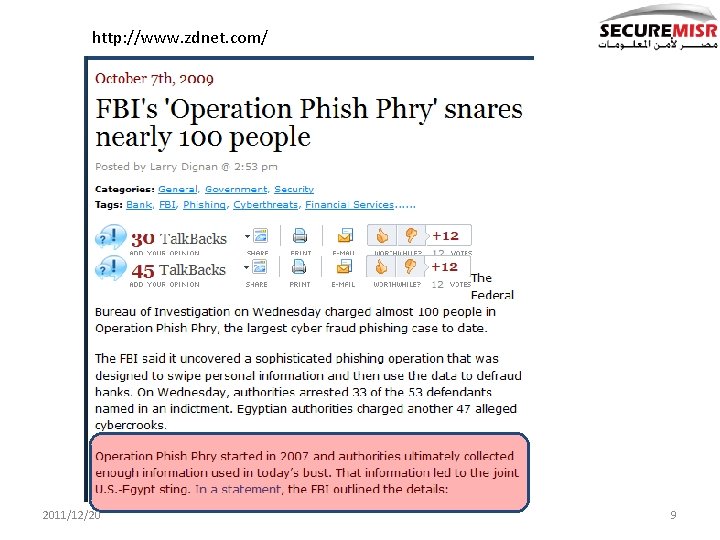
http: //www. zdnet. com/ 2011/12/20 9
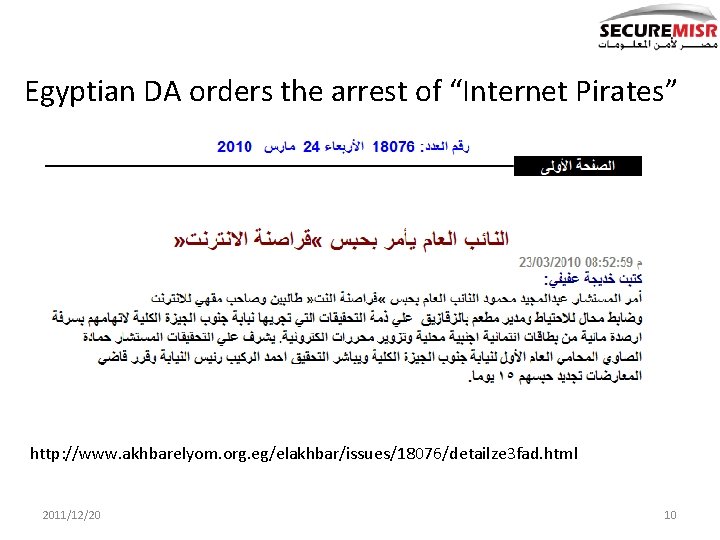
Egyptian DA orders the arrest of “Internet Pirates” http: //www. akhbarelyom. org. eg/elakhbar/issues/18076/detailze 3 fad. html 2011/12/20 10
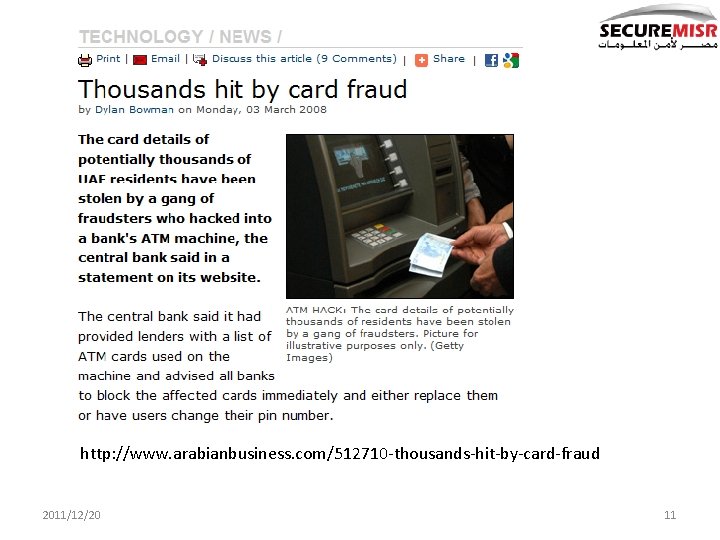
http: //www. arabianbusiness. com/512710 -thousands-hit-by-card-fraud 2011/12/20 11

Security Trends & News in the region Countries Generating Most Online fraud Nir Kshetri, “The Simple Economics of Cybercrimes, ” IEEE Security & Privacy, January/February 2006 2011/12/20 12

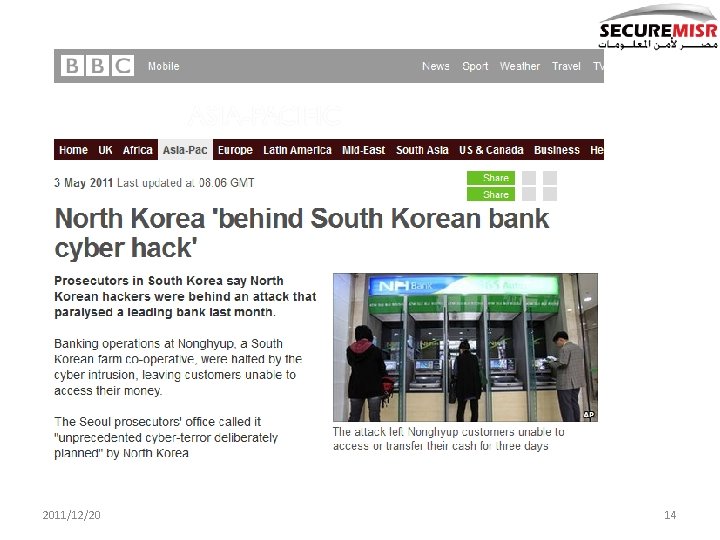
Elsewhere 2011/12/20 13
2011/12/20 14
http: //www. almasryalyoum. com/node/481121 2011/12/20 15
2011/12/20 16
2011/12/20 http: //www. wired. com/threatlevel/2010/07/atmsjackpotted/ 17
2011/12/20 18
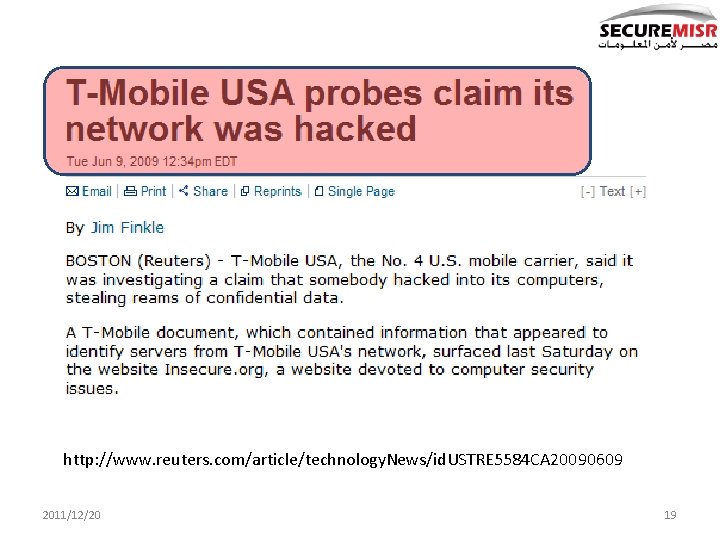
http: //www. reuters. com/article/technology. News/id. USTRE 5584 CA 20090609 2011/12/20 19
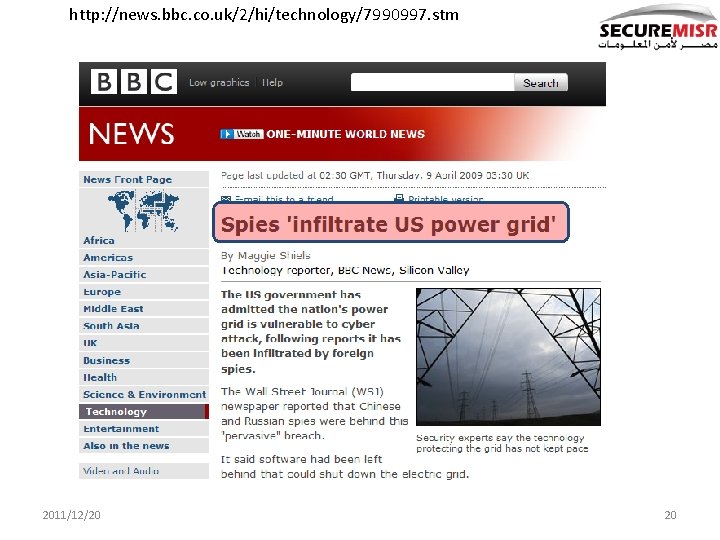
http: //news. bbc. co. uk/2/hi/technology/7990997. stm 2011/12/20 20
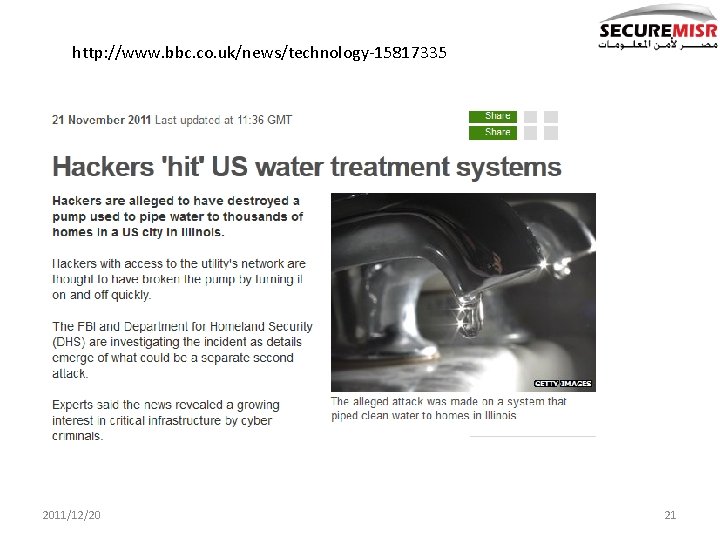
http: //www. bbc. co. uk/news/technology-15817335 2011/12/20 21
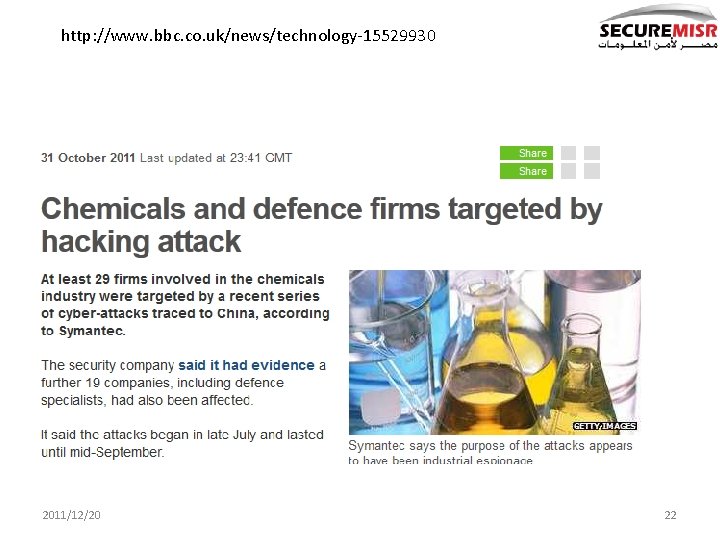
http: //www. bbc. co. uk/news/technology-15529930 2011/12/20 22
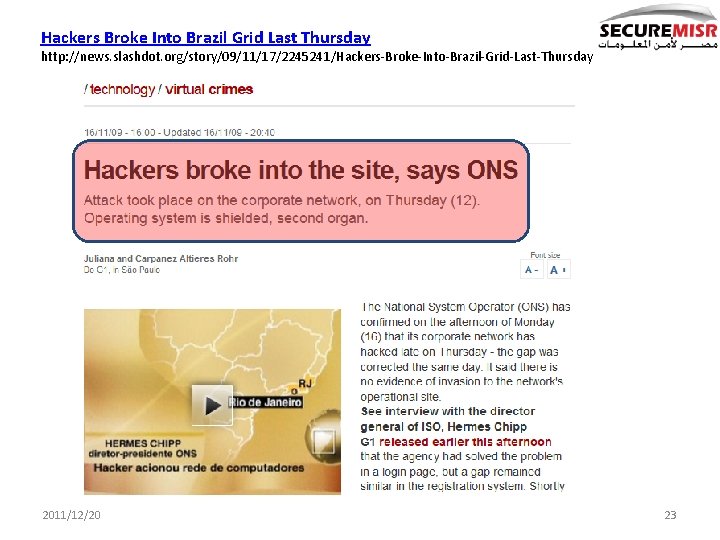
Hackers Broke Into Brazil Grid Last Thursday http: //news. slashdot. org/story/09/11/17/2245241/Hackers-Broke-Into-Brazil-Grid-Last-Thursday 2011/12/20 23
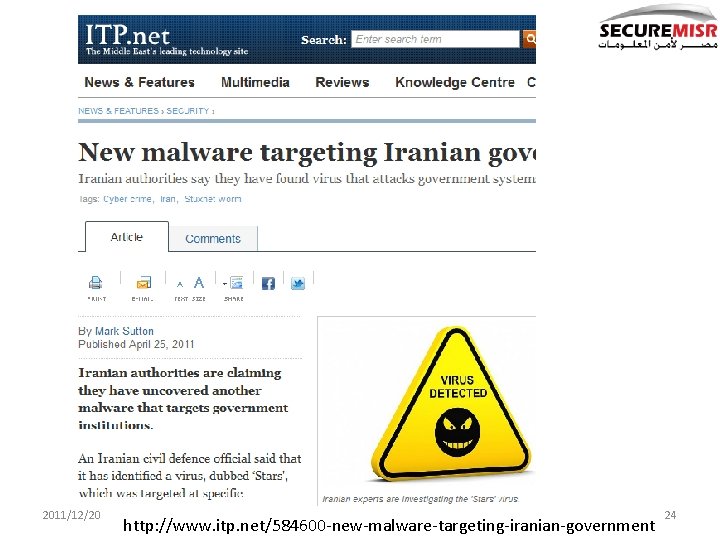
2011/12/20 http: //www. itp. net/584600 -new-malware-targeting-iranian-government 24
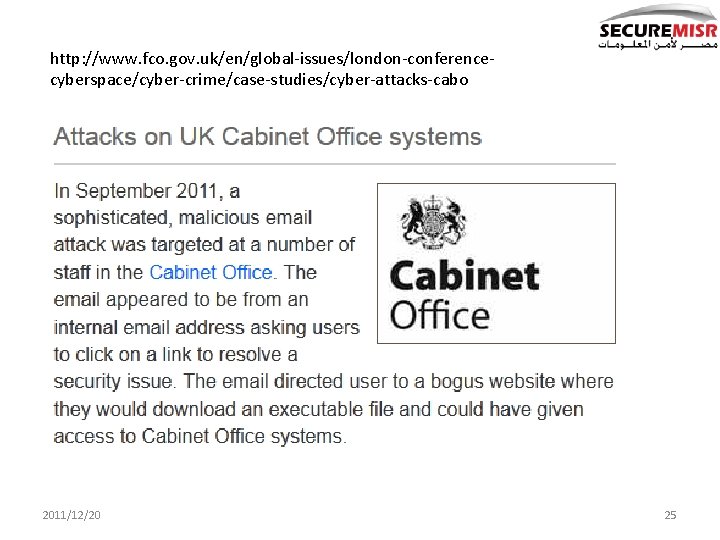
http: //www. fco. gov. uk/en/global-issues/london-conferencecyberspace/cyber-crime/case-studies/cyber-attacks-cabo 2011/12/20 25

“on trusting trust” a local perspective 2011/12/20 26

Conspiracy Theories! 2011/12/20 27
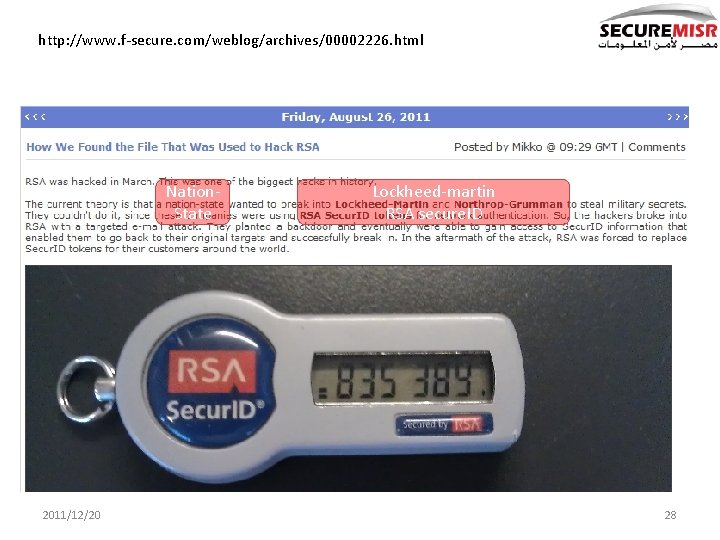
http: //www. f-secure. com/weblog/archives/00002226. html Nation. State 2011/12/20 Lockheed-martin RSA secure. ID 28
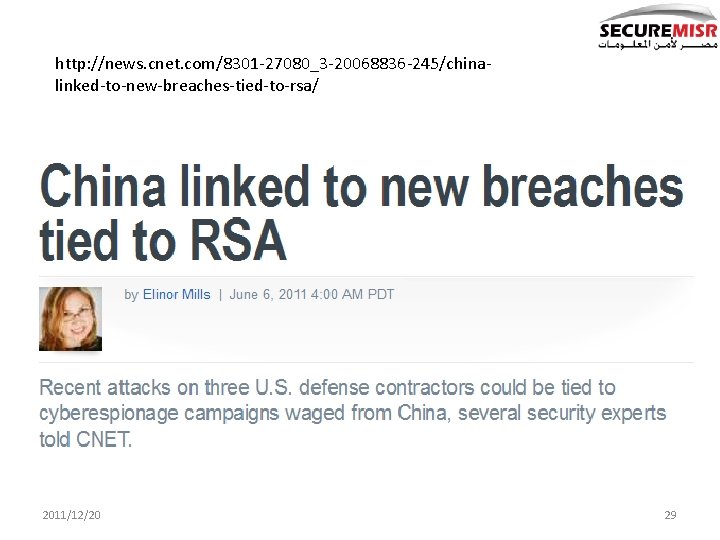
http: //news. cnet. com/8301 -27080_3 -20068836 -245/chinalinked-to-new-breaches-tied-to-rsa/ 2011/12/20 29
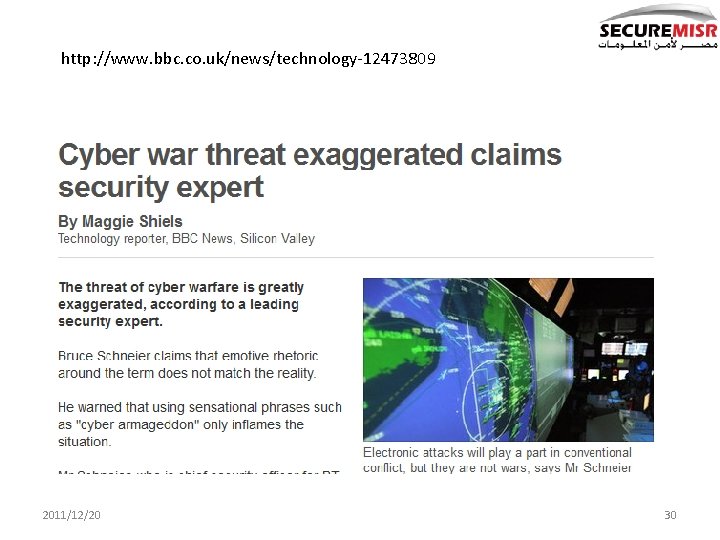
http: //www. bbc. co. uk/news/technology-12473809 2011/12/20 30
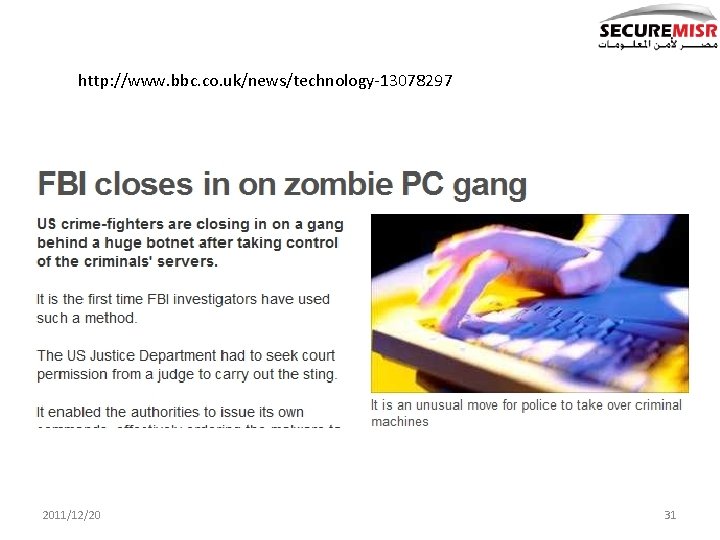
http: //www. bbc. co. uk/news/technology-13078297 2011/12/20 31
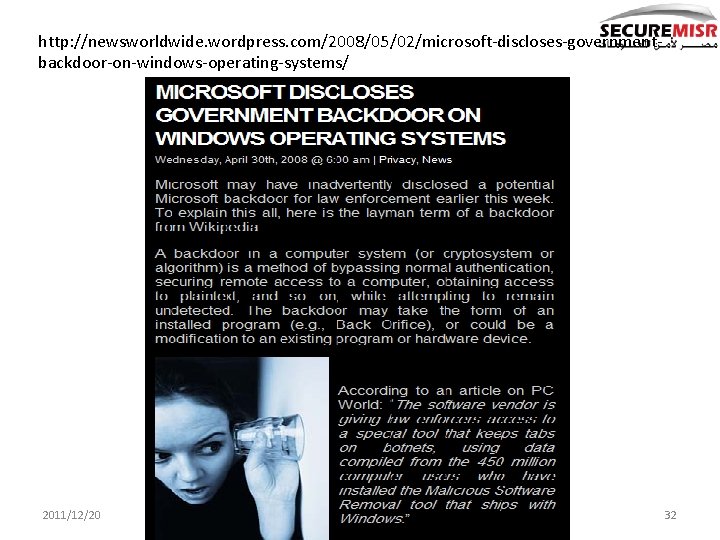
http: //newsworldwide. wordpress. com/2008/05/02/microsoft-discloses-governmentbackdoor-on-windows-operating-systems/ 2011/12/20 32
http: //vincentarnold. com/blog/chinesebackdoors-hidden-in-router-firmware/ 2011/12/20 33
www. spectrum. ieee. org/may 08/6171 2011/12/20 34

2011/12/20 http: //www. iwm. org. uk/online/enigma/eni-intro. htm 35
People! 2011/12/20 36
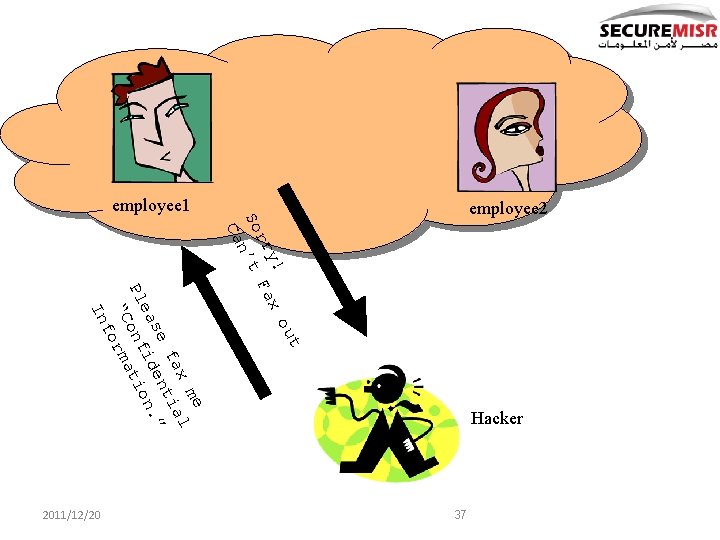
t ou y! Fax rr So n’t Ca Hacker me l x fa tia se iden n. ” ea Pl onf tio “C orma f In 37 2011/12/20 employee 2 employee 1
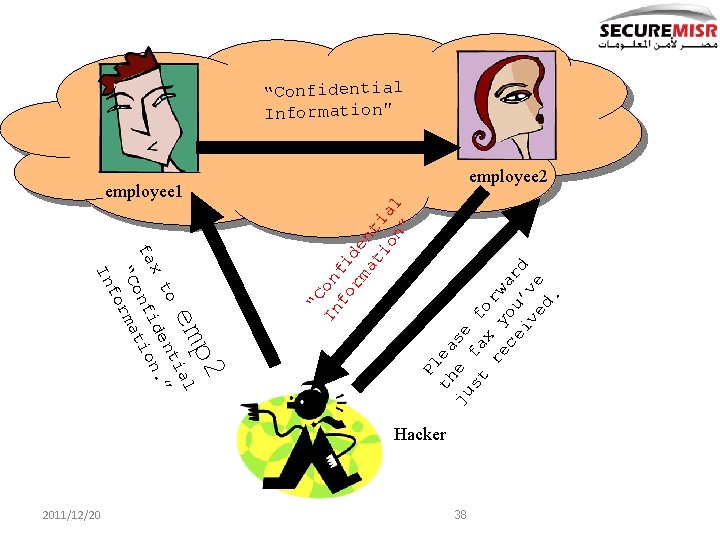
p 2 em l ia to dent. ” x n fa onfi tio “C rma fo In 2011/12/20 Pl th ea ju e se st fa f o re x y rw ce ou ar iv ’v d ed e. “C In on fo fi rm de at nt io ia n” l “Confidential Information” employee 1 employee 2 Hacker 38

Seeking answers 2011/12/20 39

Some Perspective 2011/12/20 40
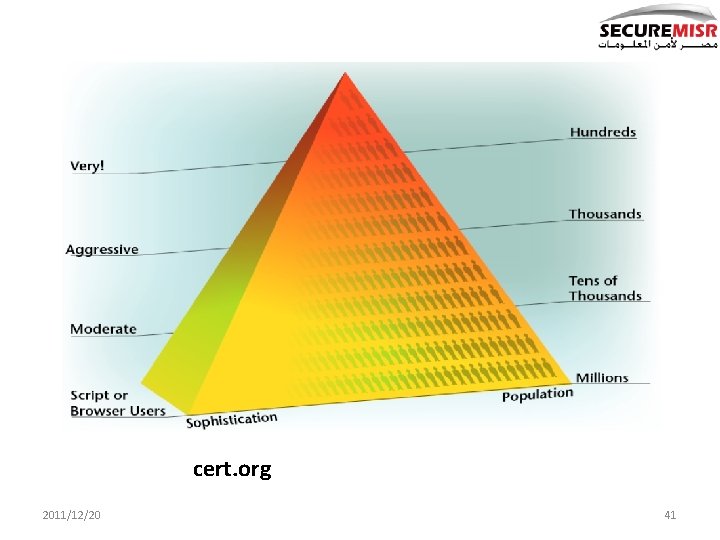
cert. org 2011/12/20 41

Security is Socio-technical & Physical! Security ≠ Technological Security 2011/12/20 42
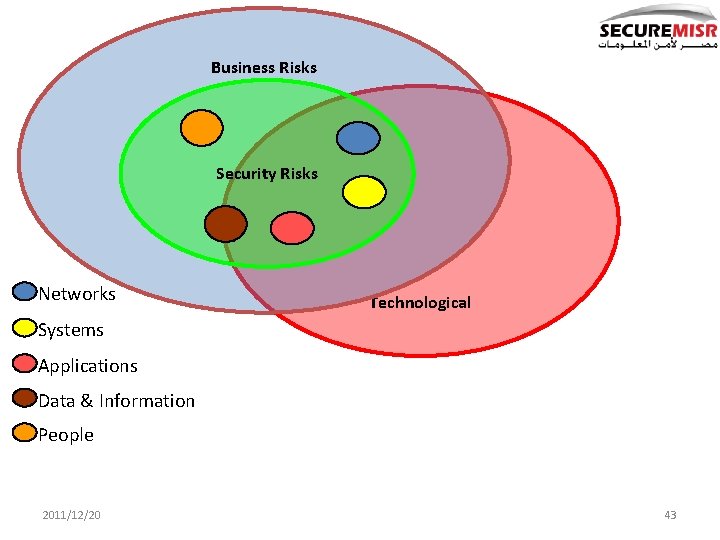
Business Risks Security Risks Networks Technological Systems Applications Data & Information People 2011/12/20 43

research agenda 2011/12/20 44

2011/12/20 http: //www. cra. org/ 45

http: //www. cra. org/ 2011/12/20 46

development agenda 2011/12/20 47

• The need for trustworthy technology – One possible approach • Build your own • Start from OSS to save time • Strong certification program to ensure quality • Invest in people – The true asset • Standards to ensure no short cuts are taken 2011/12/20 48

Conclusions • Information Security is a huge challenge • Appears to be a loosing battle at the moment • We need to education ourselves and understand the significance of infosec • Trustworthy technology and people at the right place • Invest in R&D 2011/12/20 49

Thank you Question? 2011/12/20 50

The bot-net trade 2011/12/20 51
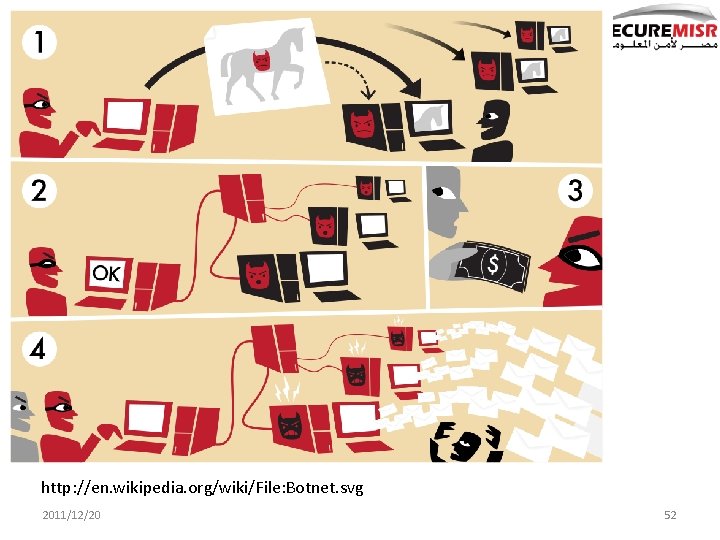
http: //en. wikipedia. org/wiki/File: Botnet. svg 2011/12/20 52

Types of attacks 2011/12/20 53

Types of Threats & Attacks • Technical – Using technological means to break into an organization's network and systems • Physical – Physically access and attack the enterprise • Social – Social engineering attacks

simple technical attacks field experience How easy is it? 2011/12/20 55

2011/12/20 56
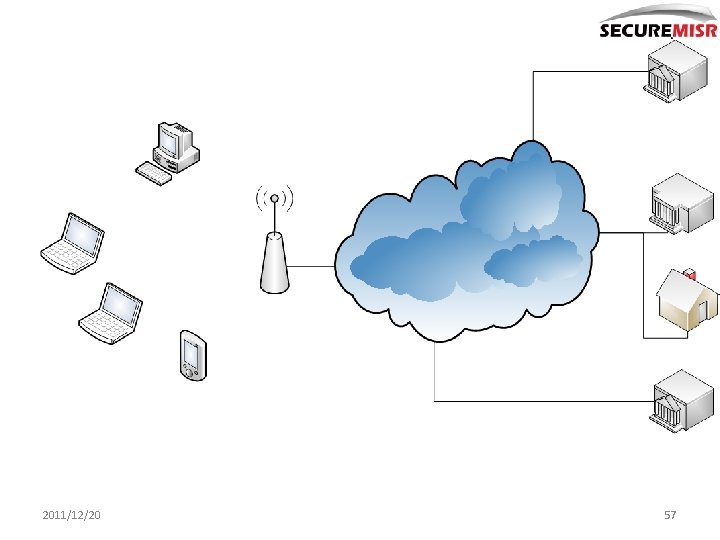
2011/12/20 57
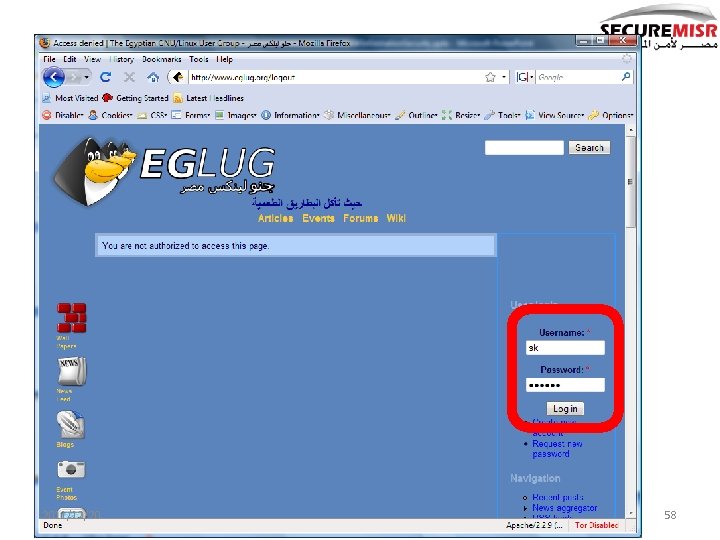
2011/12/20 58
2011/12/20 59
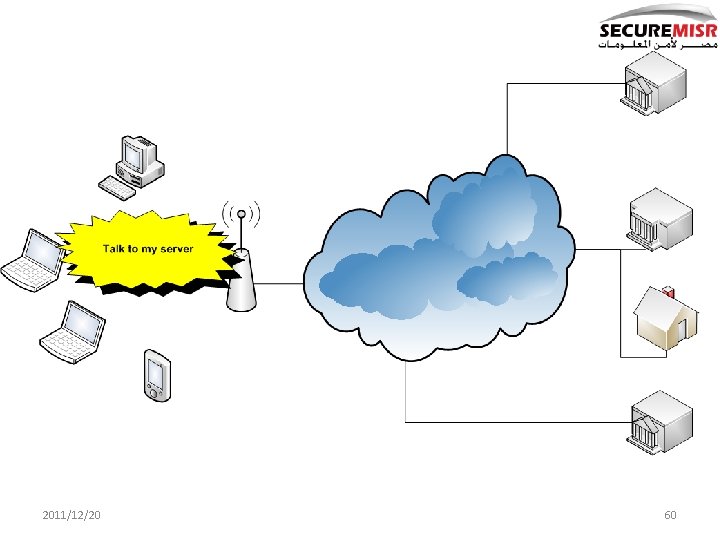
2011/12/20 60
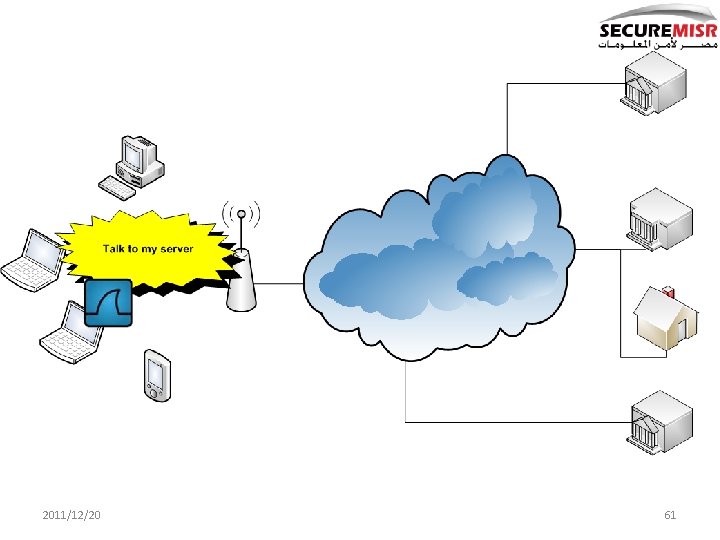
2011/12/20 61
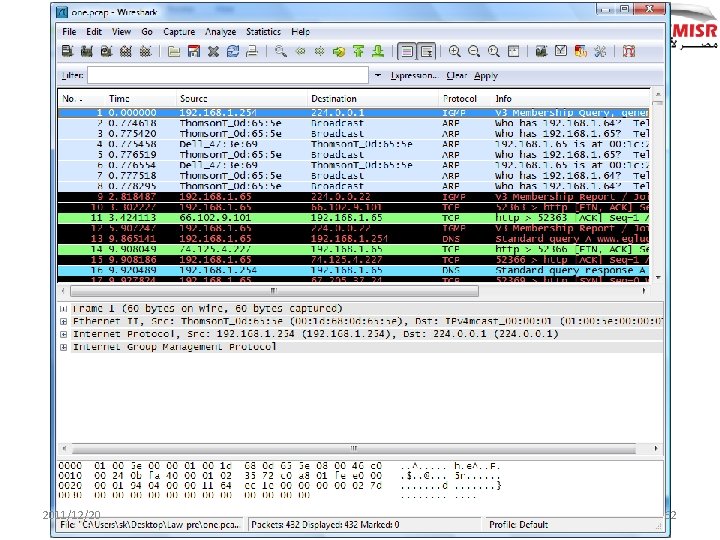
2011/12/20 62
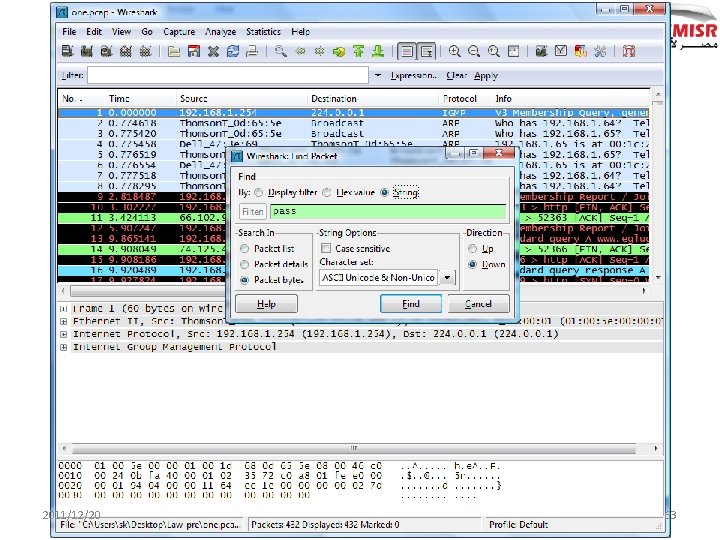
2011/12/20 63
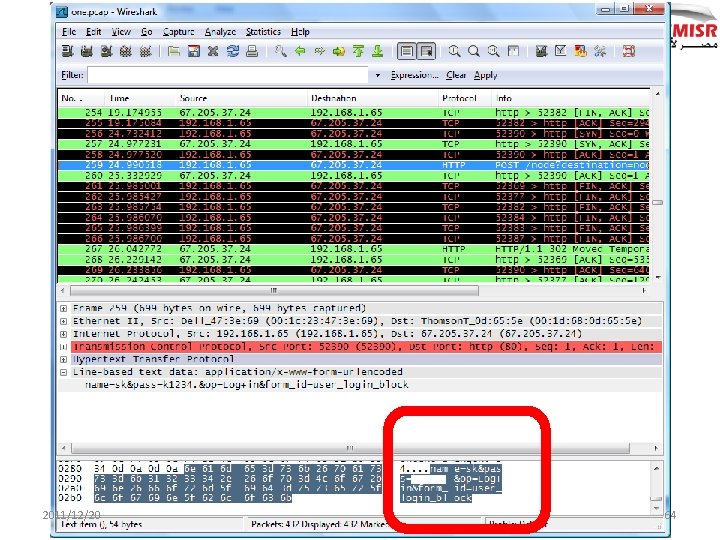
2011/12/20 64

name=sk pass=Linux 4 ever 2011/12/20 65

More field experience Google is a friend! 2011/12/20 66
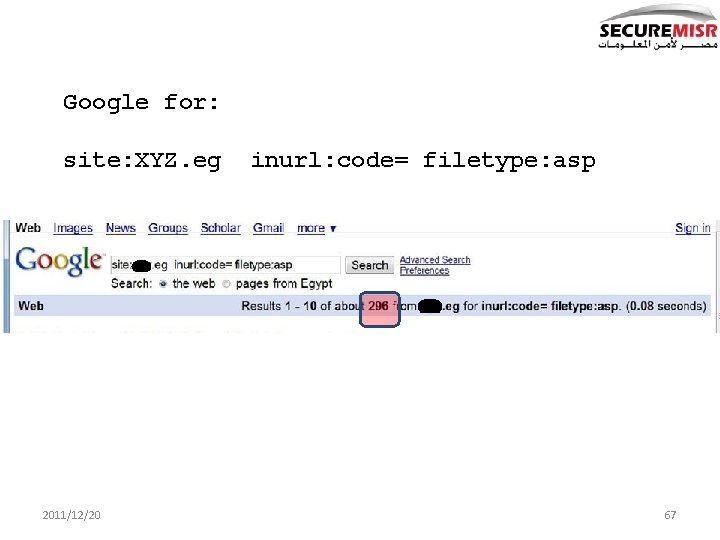
Google for: site: XYZ. eg 2011/12/20 inurl: code= filetype: asp 67
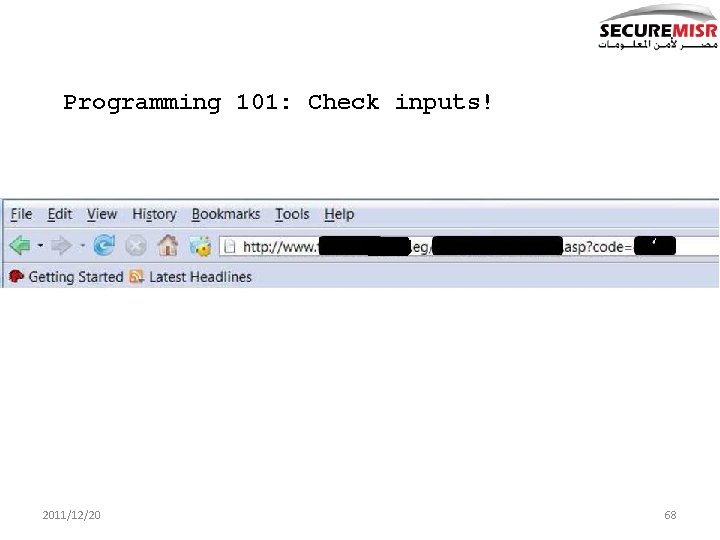
Programming 101: Check inputs! 2011/12/20 68
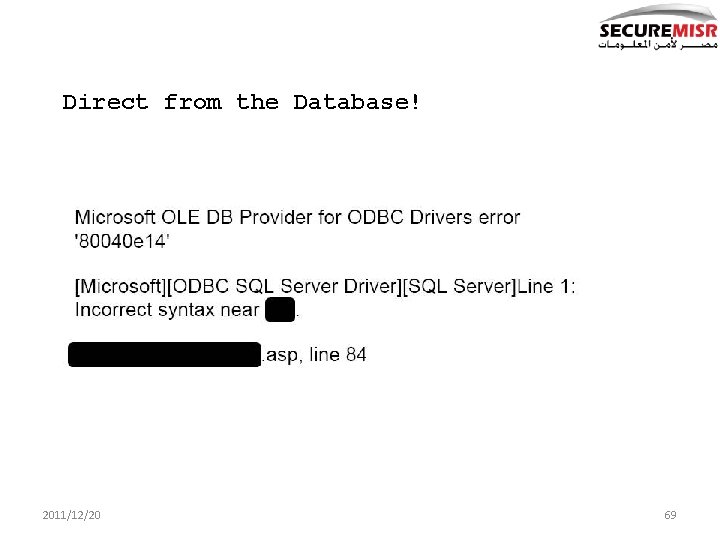
Direct from the Database! 2011/12/20 69

More field experience: Phishing 2011/12/20 70
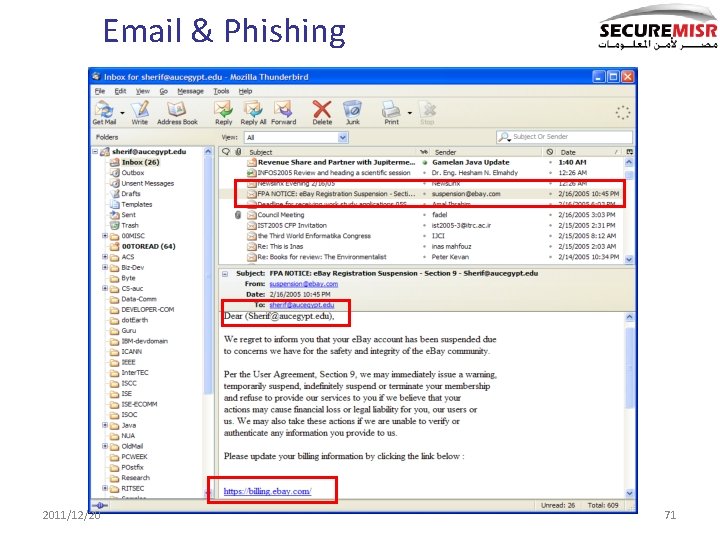
Email & Phishing 2011/12/20 71
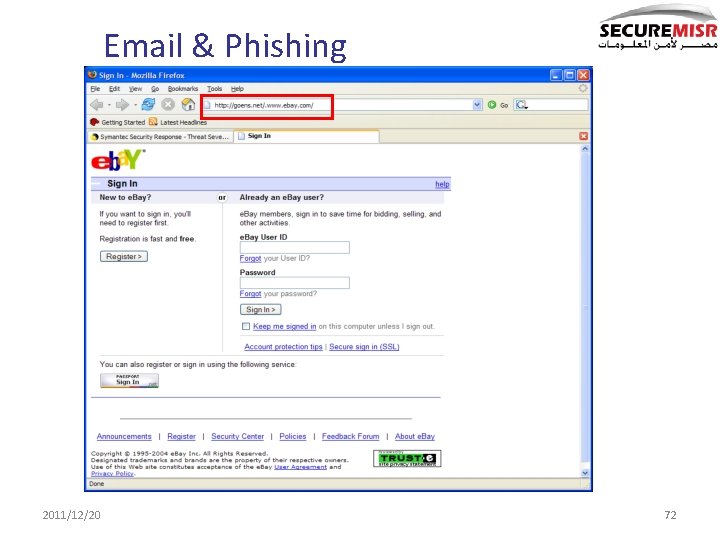
Email & Phishing 2011/12/20 72

physical attacks 2011/12/20 73

http: //www. answers. com/topic/keystroke-logger? cat=technology 2011/12/20 74

http: //www. linuxdevices. com/articles/AT 2016997232. html 2011/12/20 75
- Slides: 75