Information Security Behaviour A Critical Review and Research

Information Security Behaviour: A Critical Review and Research Directions Farkhondeh Hassandoust Angsana A. Techatassanasoontorn Harminder Singh Auckland University of Technology

Agenda • Introduction • Info. Sec Behaviours: Conceptualisation • Method • Findings • Discussion • Limitation and Future Research

Introduction • Info. Sec – ubiquitous issue and a pressing challenge for society and academics • Central topic for researchers: Info. Sec-related behaviour of individuals • Examples: complying with guidelines, engaging in protective behaviour, avoiding malicious attacks, or succumbing to them. • Each of these behaviours has been studied with a range of theories, focusing on drivers of behaviour such as individuals’ affect, emotions, identity, need for justice, and ability to extend control (e. g. Chowdhury, Adam and Skinner, 2019; Gulenko, 2014; Wang, Li and Rao, 2017). • Question: are they studying the "same thing"? what's common in what is being studied in the different studies?

Our argument • The construct of “Info. Sec-related behaviour” does not have clear boundaries and strong foundations, which has led to: • the definitions of “Info. Sec-related behaviour” (often) being restricted to deliberate actions, preventing us from exploring Info. Sec-related behaviours that are more automatic or intuitive. • difficulty in classifying or categorising various Info. Sec-related behaviours. • More broadly, the lack of an integrative framework for Info. Sec-related behaviour makes it difficult for Info. Sec researchers seeking to integrate or extend findings across domains.

What We Decided to Do 1. What is "behaviour"? --> Use recent developments on human behaviour from psychology to identify key dimensions of Info. Sec behaviour. 2. How has "behaviour" been conceptualised in the Info. Sec literature? --> classify the studies using the dimensions we identified. While there have been some recent meta-analyses in Info. Sec behaviour, our systematic review is different from those because we examined studies of Info. Sec behaviour that used any theory to study this phenomenon.
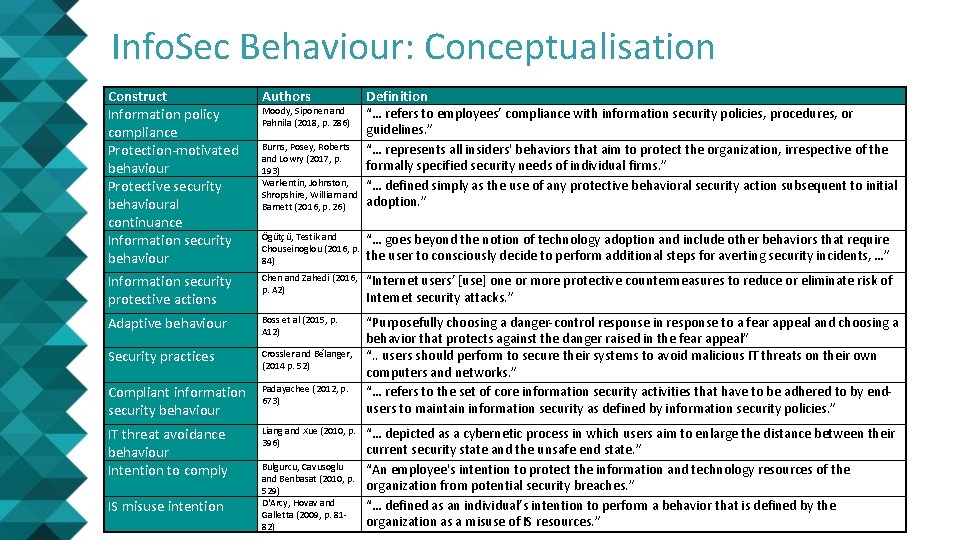
Info. Sec Behaviour: Conceptualisation Construct Information policy compliance Protection-motivated behaviour Protective security behavioural continuance Information security behaviour Authors Definition Burns, Posey, Roberts and Lowry (2017, p. 193) Warkentin, Johnston, Shropshire, William and Barnett (2016, p. 26) “… refers to employees’ compliance with information security policies, procedures, or guidelines. ” “… represents all insiders' behaviors that aim to protect the organization, irrespective of the formally specified security needs of individual firms. ” “… defined simply as the use of any protective behavioral security action subsequent to initial adoption. ” Ögütçü, Testik and Chouseinoglou (2016, p. 84) “… goes beyond the notion of technology adoption and include other behaviors that require the user to consciously decide to perform additional steps for averting security incidents, …” Information security protective actions Chen and Zahedi (2016, p. A 2) “Internet users’ [use] one or more protective countermeasures to reduce or eliminate risk of Internet security attacks. ” Adaptive behaviour Boss et al (2015, p. A 12) Security practices Crossler and Bélanger, (2014 p. 52) Compliant information security behaviour Padayachee (2012, p. 673) “Purposefully choosing a danger-control response in response to a fear appeal and choosing a behavior that protects against the danger raised in the fear appeal” “. . users should perform to secure their systems to avoid malicious IT threats on their own computers and networks. ” “… refers to the set of core information security activities that have to be adhered to by endusers to maintain information security as defined by information security policies. ” IT threat avoidance behaviour Intention to comply Liang and Xue (2010, p. 396) IS misuse intention Moody, Siponen and Pahnila (2018, p. 286) Bulgurcu, Cavusoglu and Benbasat (2010, p. 529) D'Arcy, Hovav and Galletta (2009, p. 8182) “… depicted as a cybernetic process in which users aim to enlarge the distance between their current security state and the unsafe end state. ” “An employee's intention to protect the information and technology resources of the organization from potential security breaches. ” “… defined as an individual’s intention to perform a behavior that is defined by the organization as a misuse of IS resources. ”
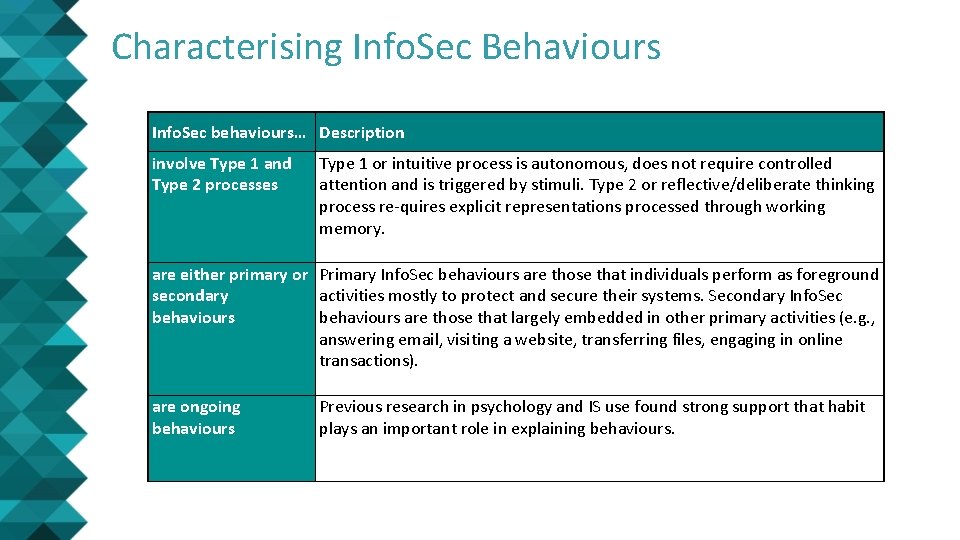
Characterising Info. Sec Behaviours Info. Sec behaviours… Description involve Type 1 and Type 2 processes Type 1 or intuitive process is autonomous, does not require controlled attention and is triggered by stimuli. Type 2 or reflective/deliberate thinking process re-quires explicit representations processed through working memory. are either primary or Primary Info. Sec behaviours are those that individuals perform as foreground secondary activities mostly to protect and secure their systems. Secondary Info. Sec behaviours are those that largely embedded in other primary activities (e. g. , answering email, visiting a website, transferring files, engaging in online transactions). are ongoing behaviours Previous research in psychology and IS use found strong support that habit plays an important role in explaining behaviours.
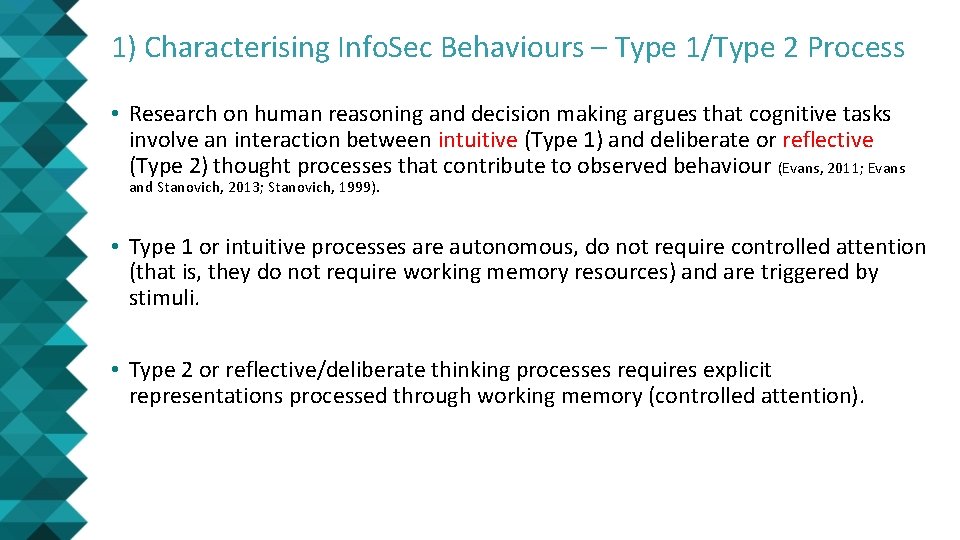
1) Characterising Info. Sec Behaviours – Type 1/Type 2 Process • Research on human reasoning and decision making argues that cognitive tasks involve an interaction between intuitive (Type 1) and deliberate or reflective (Type 2) thought processes that contribute to observed behaviour (Evans, 2011; Evans and Stanovich, 2013; Stanovich, 1999). • Type 1 or intuitive processes are autonomous, do not require controlled attention (that is, they do not require working memory resources) and are triggered by stimuli. • Type 2 or reflective/deliberate thinking processes requires explicit representations processed through working memory (controlled attention).

2) Characterising Info. Sec Behaviours – Primary/Secondary Behaviours • Info. Sec response behaviours can be either primary or secondary behaviours. Secondary behaviours are those that embedded in other activities, such as answering emails, or engaging in online transactions. • Secondary Info. Sec behaviours such as acting on a virus alert while browsing a website (Boss et al. , 2015), copying sensitive information to a USB memory stick without encryption (Vance, Siponen and Pahnila, 2012). • Other Info. Sec behaviours may not be embedded in other foreground activities and would be considered as primary behaviours such as backing up data, installing a firewall.

3) Characterising Info. Sec Behaviours – Ongoing Behaviours • Emerging research from psychology suggests that habits are an important mechanism that guides everyday behaviour and for achieving long-term goals (Gardner, 2015; Wood, 2017). • Habit plays an important role in explaining IS use (Limayem and Hirt, 2003) and online behaviours such as Internet use, online shopping and file downloads (Bayer and La. Rose, 2018). • Previous research reports that the importance of intention in explaining behaviour decreases as that behaviour becomes more habitual. This argument is also supported by findings from psychology (Oullette and Wood, 1998) and dual-process theories (Wood and Rünger, 2016).

Method • A systematic literature review to synthesise and organise the current body of knowledge, and to identify gaps and research opportunities (Cram et al. , 2017; Paré et al. , 2015; Rowe, 2014). • Search terms: ‘information security AND intention’, ‘information security AND habit’, and ‘information security AND behaviour’ for papers from 2008 to February 2019 • Scholarly databases: ACM Digital Library, IEEE Xplore, IGI Global’s Database, Pro. Quest Computing and Springer. Link • A final list of 78 papers, which were distributed among the three co-authors. Each article was read and coded by one co-author, and the results were checked by a second co-author. • The identified studies were analysed for the purpose of identifying applied theories, factors influencing individuals’ Info. Sec intentions and behaviours as well as the extent to which characteristics of Info. Sec behaviours have been considered.
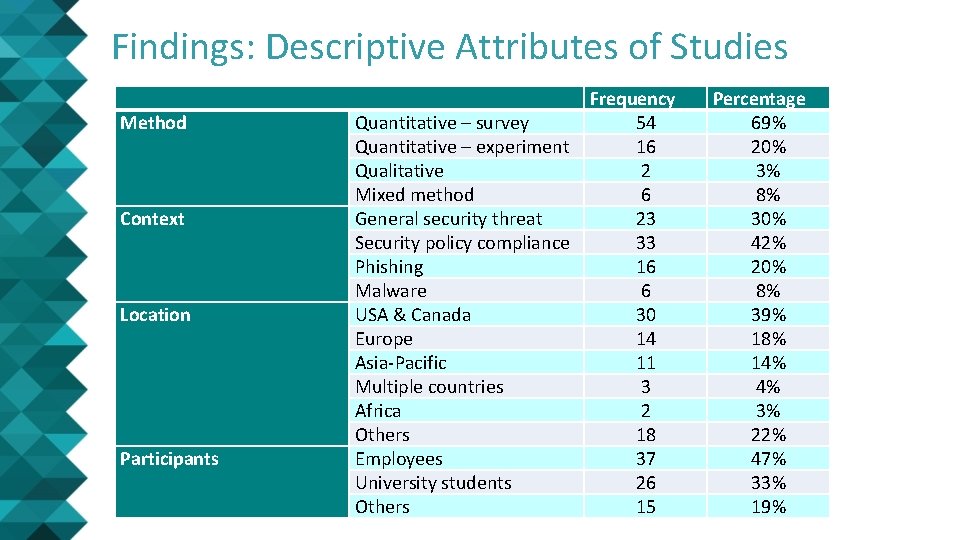
Findings: Descriptive Attributes of Studies Method Context Location Participants Frequency Quantitative – survey 54 Quantitative – experiment 16 Qualitative 2 Mixed method 6 General security threat 23 Security policy compliance 33 Phishing 16 Malware 6 USA & Canada 30 Europe 14 Asia-Pacific 11 Multiple countries 3 Africa 2 Others 18 Employees 37 University students 26 Others 15 Percentage 69% 20% 3% 8% 30% 42% 20% 8% 39% 18% 14% 4% 3% 22% 47% 33% 19%
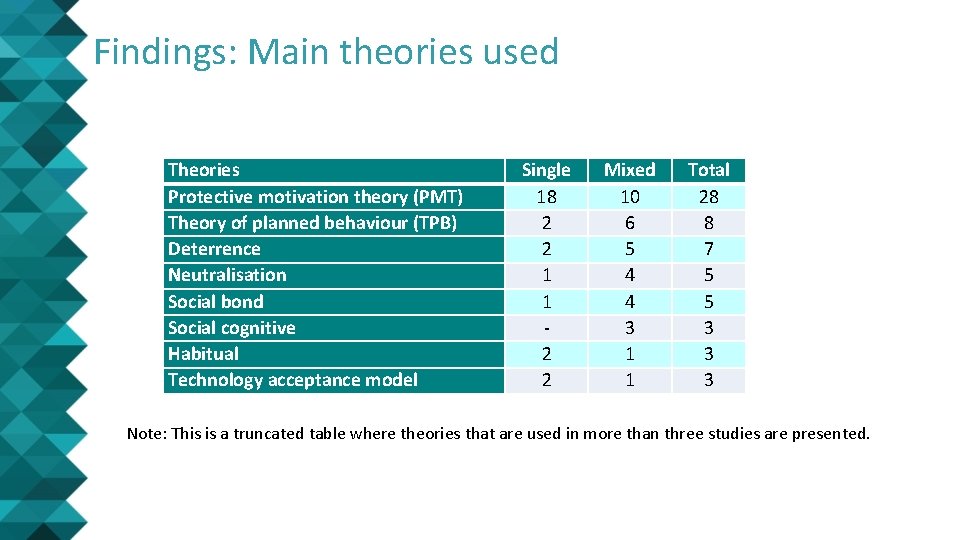
Findings: Main theories used Theories Protective motivation theory (PMT) Theory of planned behaviour (TPB) Deterrence Neutralisation Social bond Social cognitive Habitual Technology acceptance model Single 18 2 2 1 1 2 2 Mixed 10 6 5 4 4 3 1 1 Total 28 8 7 5 5 3 3 3 Note: This is a truncated table where theories that are used in more than three studies are presented.

Dimensions of behaviours Number of studies (%) Type 1 and Type 2 processes 50 studies (64%) investigated Info. Sec behaviours as reflective/deliberate thinking processes 14 studies (18%) investigated both the intuitive and reflective aspects of Info. Sec behaviours 14% of studies do not considering thinking processes Primary vs. Secondary behaviours 74 studies (95%) considered users’ Info. Sec behaviours as their primary activity on a computer Ongoing behaviours 4 studies (5%) consider Info. Sec as repeating behaviours in stable contexts 6 studies (8%) consider contextual cues 14 studies (18%) consider habit as one of the antecedents of Info. Sec behaviour Findings: Considerations of Characteristics of Info. Sec Behaviours

Discussion – Theoretical Considerations • Info. Sec behavioural research is dominated by Type 2 theories • This study provides evidence to support the conjecture: “there is a fundamental flaw in our understanding of information security behaviour because our [Type 2] theories and empirical research do not address the meaningful proportion of behaviour guided by [Type 1] cognition” (Dennis and Minas, 2018, p. 24) • Research on secondary behaviours should consider a contextualised approach in the study design • Future studies should look into both habit formation and habit performance in the context of Info. Sec behaviours

Discussion – Methodological Considerations • Methods chosen to study Info. Sec behaviours should be aligned with the nature of such behaviours • Future studies should consider alternative methodologies that record objective responses from individuals • Studies should consider a longitudinal design to examine habitual behaviours

Discussion – Considerations for Researchers • Before starting a research project on Info. Sec behaviours, researchers should ask themselves: • how does the behaviour being studied occur? – This query brings to the fore the need to understand the thinking processes preceding behaviour: what is the role of intuitive and reflective thinking processes? • when does the behaviour occur? – This highlights the need to pay attention as to whether the behaviour is a primary or secondary activity; • how often does the behaviour occur? – Here, the researcher has to take a step back, and ask her/himself whether the act is a repeated habit or a one-off, non-habitual response.

Next Step • Next Steps- Empirical Project • • Test out propositions using AUT as the research site Collaboration with AUT ICT Ethics approved - after multiple revisions : -( On hold till things go back to Level 1 (0? – COVID-19)

Questions and Comments?
- Slides: 19