Information Security Awareness The Need for Information Security













- Slides: 33

Information Security Awareness

The Need for Information Security In Small Businesses • In United States, small businesses make up 95% of all businesses. • These small businesses produce 50% of all the Gross National Products (GNP) and provide 50% of all new jobs in the country. • All the large scale businesses employ people, technology and resources to make all activities secure. This leads cyber criminals to attack less secure small businesses. • The average cost of informing a customer about a security breach that happened in your organization is well over $130. This means that if you have a client base of 1000 and a security breach takes place, you would end up in spending more than $1, 30, 000.

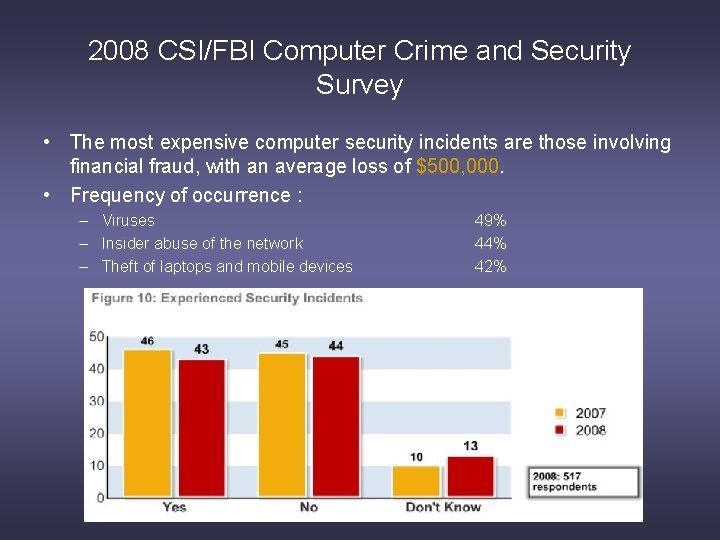
2008 CSI/FBI Computer Crime and Security Survey • The most expensive computer security incidents are those involving financial fraud, with an average loss of $500, 000. • Frequency of occurrence : – Viruses – Insider abuse of the network – Theft of laptops and mobile devices 49% 44% 42%

The Problem of Network Security • The Internet allows an attacker to attack from anywhere in the world from their home desk. • They just need to find one vulnerability: a security analyst need to close every vulnerability. • According to www. SANS. org , the top vulnerabilities available for a cyber criminal are – – Web Browser IM Clients Web Applications Excessive User Rights

Computer Virus • A virus attaches itself to a program, file, or disk • When the program is executed, the virus too is executed • When the program is given away (floppy/email) the virus spreads • The virus may be benign or malignant but executes its load pay at some point (often upon contact) • Viruses result in crashing of computers and loss of data. • In order to recover/prevent virus attacks: – Security Firewalls i. e. Comodo – Re-install operating system – Virus Protection. • Freeware i. e. Avast Antivirus, AVG Cough! Don’t come close! Program A Extra Code Program A infects

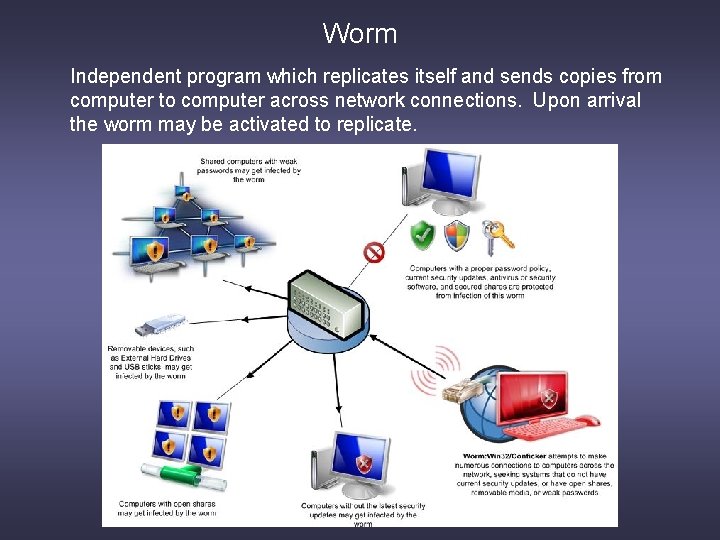
Worm Independent program which replicates itself and sends copies from computer to computer across network connections. Upon arrival the worm may be activated to replicate.

Logic Bomb Trojan Horse Logic Bomb: Malware logic will execute upon certain conditions. It is used for more legitimate reasons but could be used for nefarious purposes. • Software which will malfunction if maintenance fee is not paid • Employee triggering a database erase when he is fired. Trojan Horse: Malware has malicious purpose in addition to functional purpose • Social Engineering: “Try this game…it is so cool” – Game also emails password file. – The word Trojan war has a piece of history attached to it. (In Greek mythology, the Trojan War was waged against the city of Troy by the Achaeans (Greeks) after Paris of Troy stole Helen from her husband Menelaus, the king of Sparta. ) – More importantly, a large horse was given as a gift/peace offering and allowed inside the gates of the fortress and once inside enemy soldiers exited and defeated them. The moral being that you should beware of gifts that look too good.

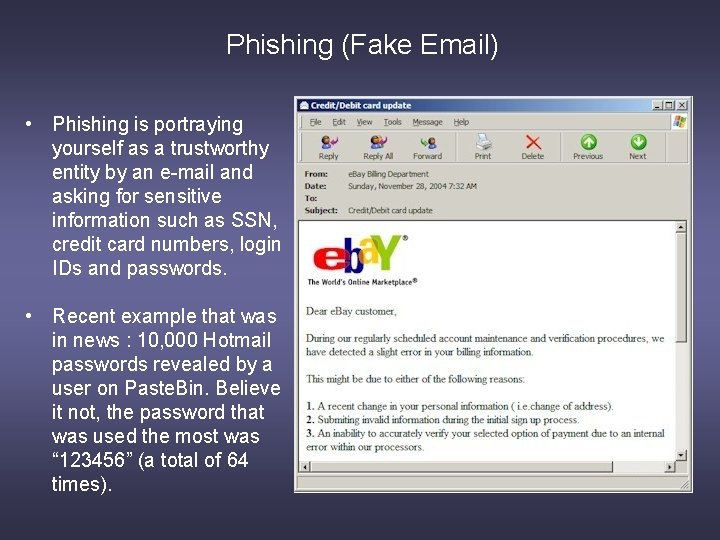
Phishing (Fake Email) • Phishing is portraying yourself as a trustworthy entity by an e-mail and asking for sensitive information such as SSN, credit card numbers, login IDs and passwords. • Recent example that was in news : 10, 000 Hotmail passwords revealed by a user on Paste. Bin. Believe it not, the password that was used the most was “ 123456” (a total of 64 times).

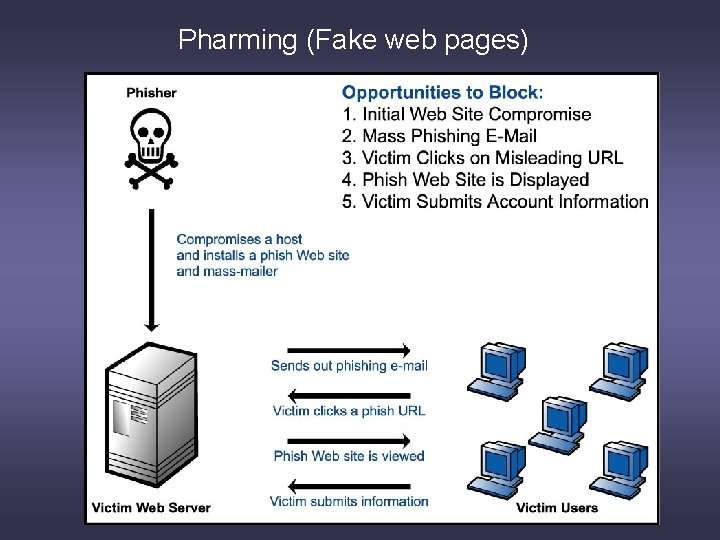
Pharming (Fake web pages)

Pharming : An Example The link provided in the e-mail leads to a fake webpage which collects all the important information and submits it to the owner.

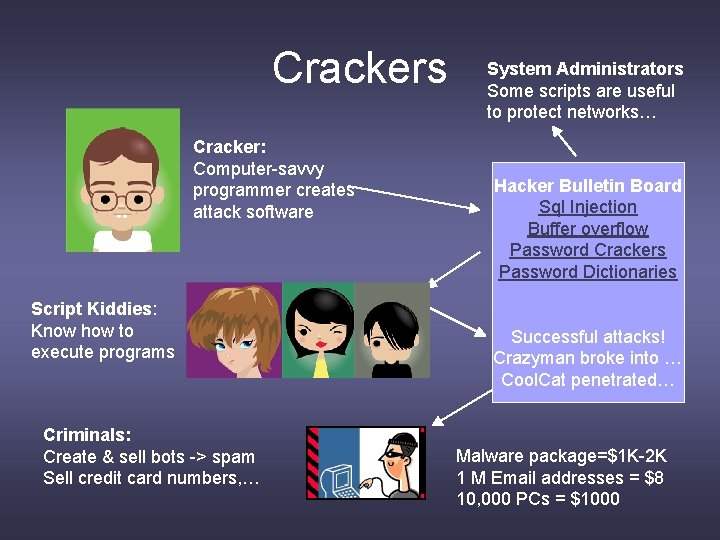
Crackers Cracker: Computer-savvy programmer creates attack software Script Kiddies: Know how to execute programs Criminals: Create & sell bots -> spam Sell credit card numbers, … System Administrators Some scripts are useful to protect networks… Hacker Bulletin Board Sql Injection Buffer overflow Password Crackers Password Dictionaries Successful attacks! Crazyman broke into … Cool. Cat penetrated… Malware package=$1 K-2 K 1 M Email addresses = $8 10, 000 PCs = $1000

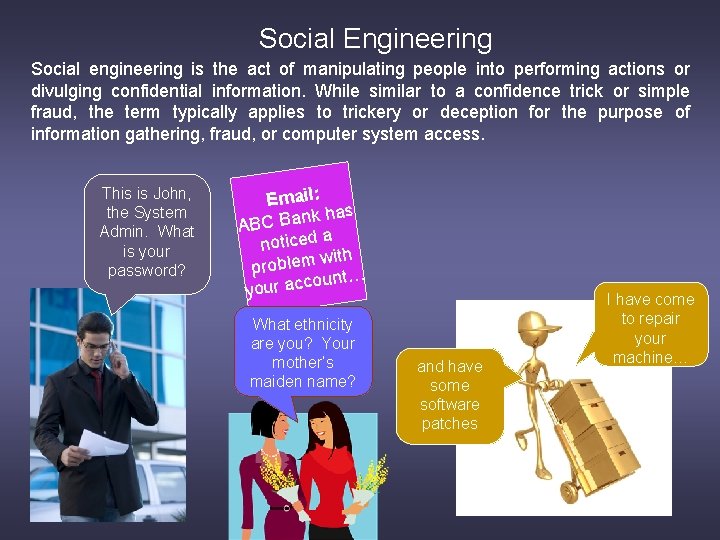
Social Engineering Social engineering is the act of manipulating people into performing actions or divulging confidential information. While similar to a confidence trick or simple fraud, the term typically applies to trickery or deception for the purpose of information gathering, fraud, or computer system access. This is John, the System Admin. What is your password? Email: k has n a B C B A noticed a with problem ount… c c a r u o y What ethnicity are you? Your mother’s maiden name? and have some software patches I have come to repair your machine…

How easy social engineering attacks are : An example

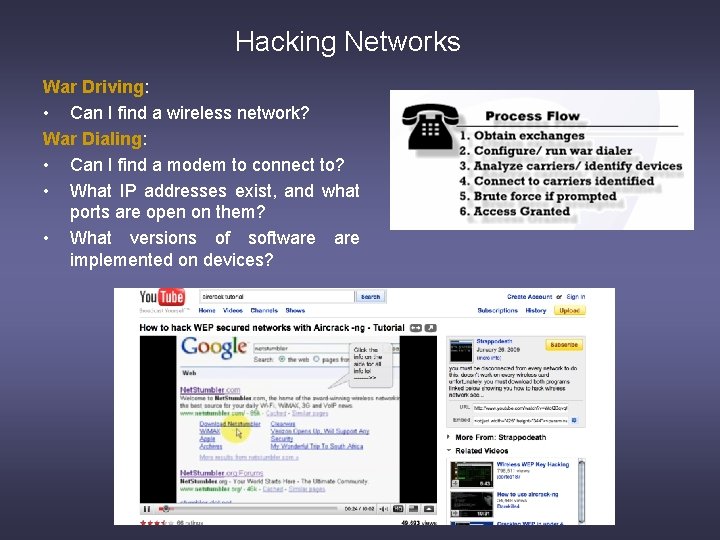
Hacking Networks War Driving: • Can I find a wireless network? War Dialing: • Can I find a modem to connect to? • What IP addresses exist, and what ports are open on them? • What versions of software implemented on devices?

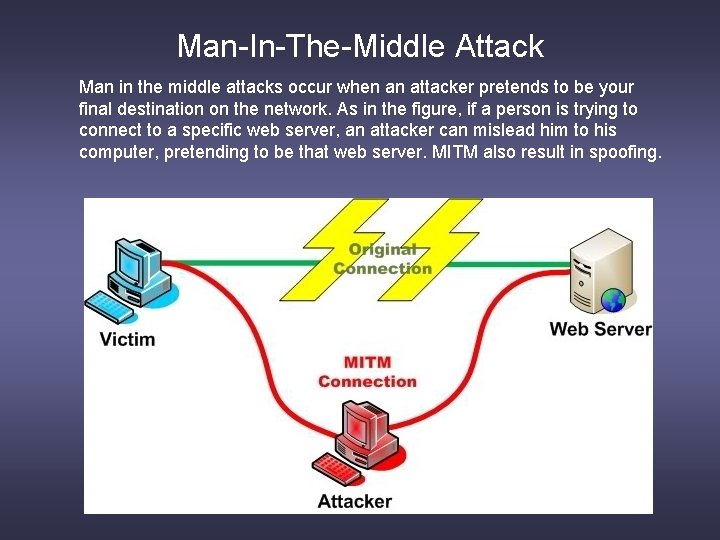
Man-In-The-Middle Attack Man in the middle attacks occur when an attacker pretends to be your final destination on the network. As in the figure, if a person is trying to connect to a specific web server, an attacker can mislead him to his computer, pretending to be that web server. MITM also result in spoofing.

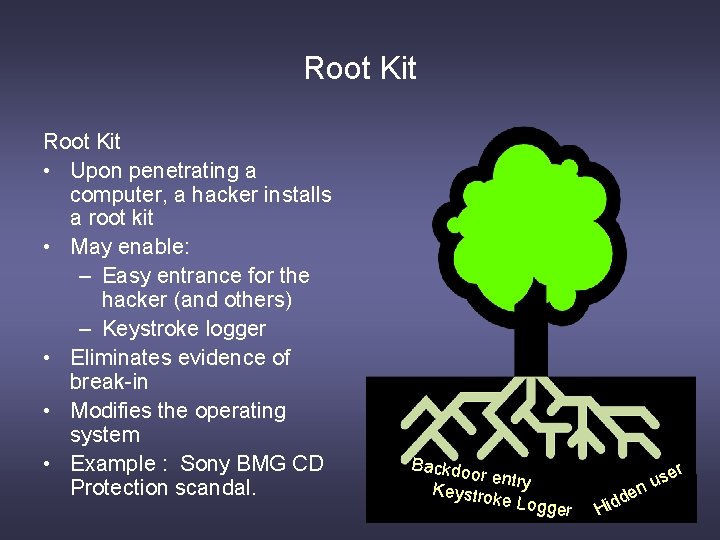
Root Kit • Upon penetrating a computer, a hacker installs a root kit • May enable: – Easy entrance for the hacker (and others) – Keystroke logger • Eliminates evidence of break-in • Modifies the operating system • Example : Sony BMG CD Protection scandal. Backdo or entry Keystro ke Logg er H en d id r e s u

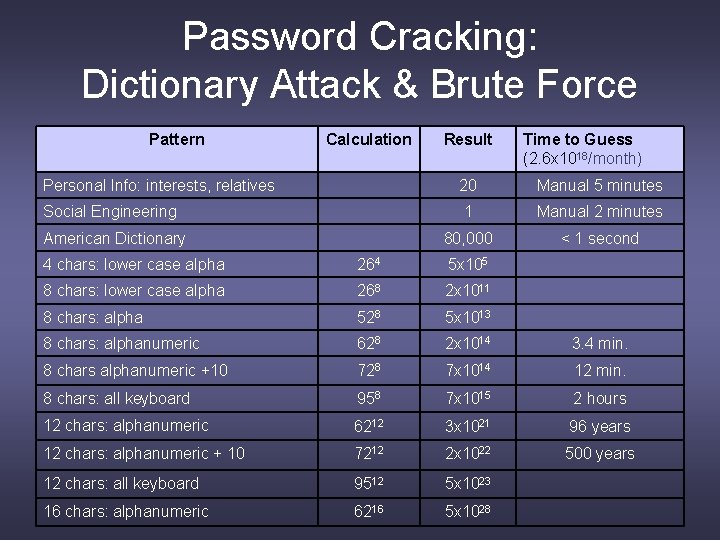
Password Cracking: Dictionary Attack & Brute Force Pattern Calculation Result Time to Guess (2. 6 x 1018/month) Personal Info: interests, relatives 20 Manual 5 minutes Social Engineering 1 Manual 2 minutes 80, 000 < 1 second American Dictionary 4 chars: lower case alpha 264 5 x 105 8 chars: lower case alpha 268 2 x 1011 8 chars: alpha 528 5 x 1013 8 chars: alphanumeric 628 2 x 1014 3. 4 min. 8 chars alphanumeric +10 728 7 x 1014 12 min. 8 chars: all keyboard 958 7 x 1015 2 hours 12 chars: alphanumeric 6212 3 x 1021 96 years 12 chars: alphanumeric + 10 7212 2 x 1022 500 years 12 chars: all keyboard 9512 5 x 1023 16 chars: alphanumeric 6216 5 x 1028

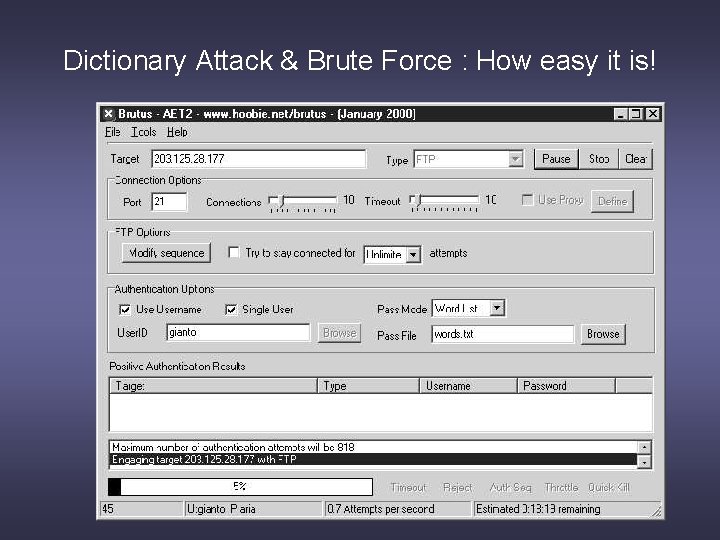
Dictionary Attack & Brute Force : How easy it is!

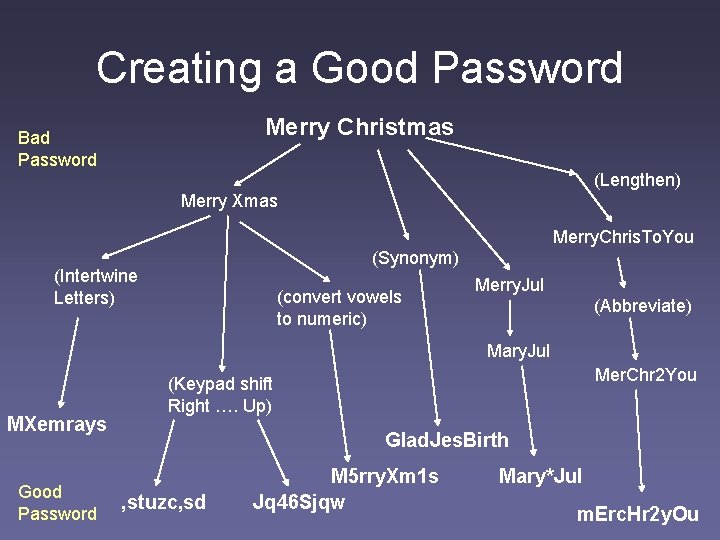
Creating a Good Password Merry Christmas Bad Password (Lengthen) Merry Xmas Merry. Chris. To. You (Synonym) (Intertwine Letters) (convert vowels to numeric) Merry. Jul (Abbreviate) Mary. Jul MXemrays Good Password Mer. Chr 2 You (Keypad shift Right …. Up) Glad. Jes. Birth , stuzc, sd M 5 rry. Xm 1 s Jq 46 Sjqw Mary*Jul m. Erc. Hr 2 y. Ou

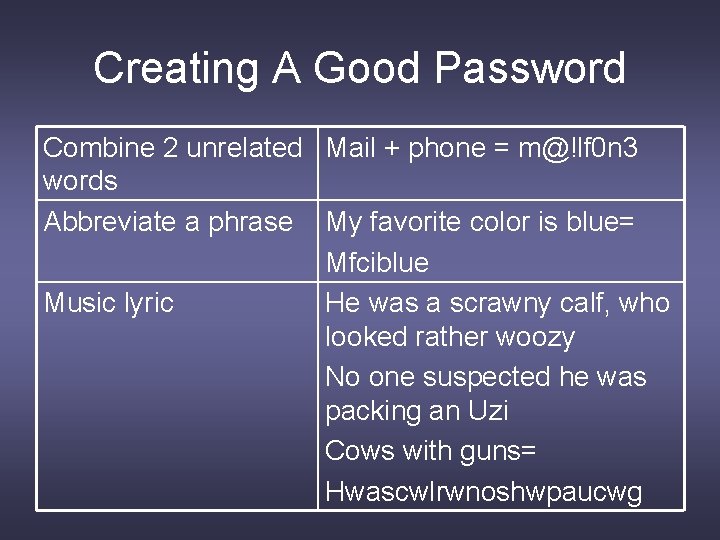
Creating A Good Password Combine 2 unrelated Mail + phone = m@!lf 0 n 3 words Abbreviate a phrase My favorite color is blue= Mfciblue Music lyric He was a scrawny calf, who looked rather woozy No one suspected he was packing an Uzi Cows with guns= Hwascwlrwnoshwpaucwg

Good Practices to Prevent Attacks

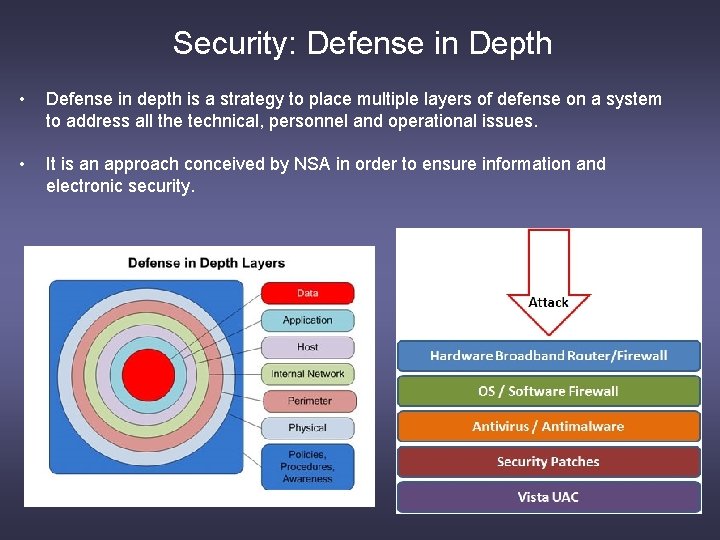
Security: Defense in Depth • Defense in depth is a strategy to place multiple layers of defense on a system to address all the technical, personnel and operational issues. • It is an approach conceived by NSA in order to ensure information and electronic security.

Protected Computer is… Computer fortified against attackers • Applications turned off • Operating system patched • Security configuration tightened – Authorization – Authentication – Physical Access • Using appropriate measures to stop malware, viruses, worms.

A Firewall is a Filter A firewall, as the name suggests acts as a wall between your computer/private network and the internet. There all sorts of things on the internet that include malicious content. A firewall only lets “good” content to pass through and blocks the malicious code.

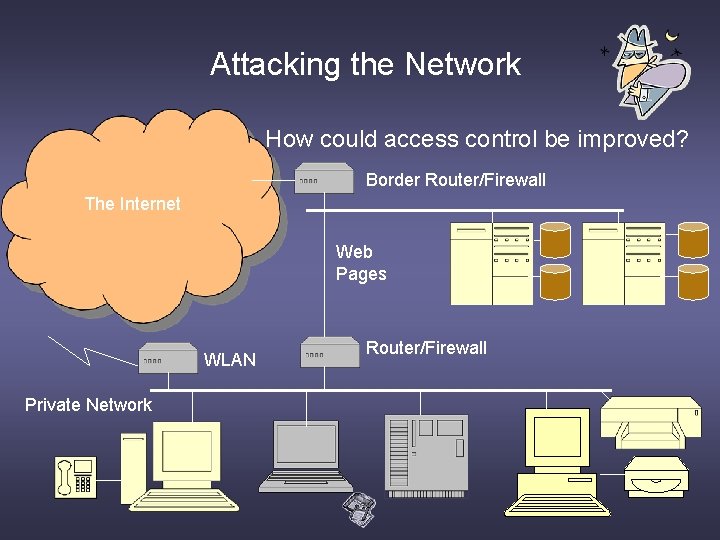
Attacking the Network How could access control be improved? Border Router/Firewall The Internet Web Pages WLAN Private Network Router/Firewall

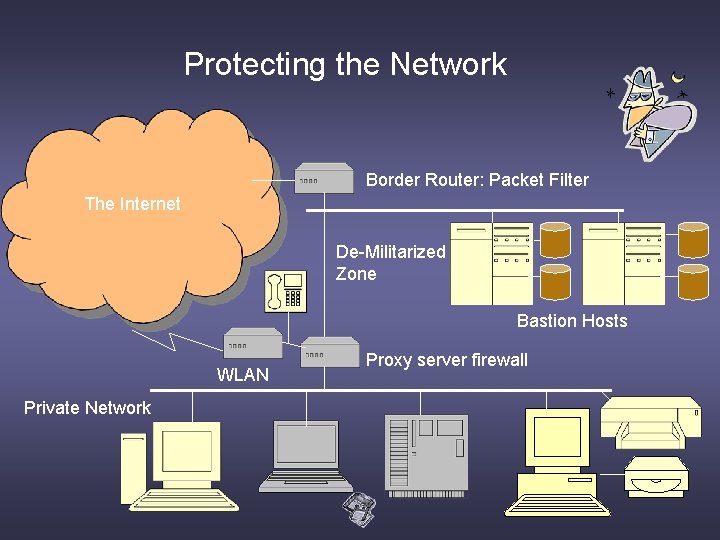
Protecting the Network Border Router: Packet Filter The Internet De-Militarized Zone Bastion Hosts WLAN Private Network Proxy server firewall

Password Recommendations • • • Change the default passwords on firewalls Never use ‘admin’ or ‘root’ or ‘administrator’ as a login for the admin – Use a software firewall on each computer system, with antivirus & antispyware. A good password is: – private: it is used and known by one person only – secret: it does not appear in clear text in any file or program or on a piece of paper pinned to the terminal – easily remembered: so there is no need to write it down – at least 8 characters – a mixture of at least 3 of the following: upper case letters, lower case letters, digits and punctuation – not guessable by any program in a reasonable time, for instance less than one week. Why you must change passwords • Even if you choose a good password, it can still be discovered: someone may see you typing it or capture it by snooping on the computer or network. If you accidentally type your password in place your login name, it may appear in system log files

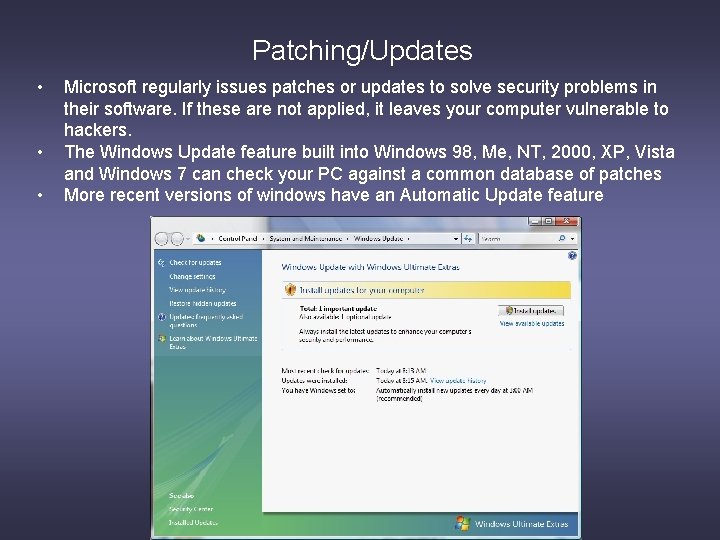
Patching/Updates • • • Microsoft regularly issues patches or updates to solve security problems in their software. If these are not applied, it leaves your computer vulnerable to hackers. The Windows Update feature built into Windows 98, Me, NT, 2000, XP, Vista and Windows 7 can check your PC against a common database of patches More recent versions of windows have an Automatic Update feature

Combat Viruses • Maintain Operating System Updates • Install anti-virus, anti-spyware software There are many freeware and paid options available in the market. • Beware of opening unknown attachments • Do not open email on your main server • In case you are infected with a virus there are various options available : system restore, virus removal tool, re-install OS.

Wisconsin 134. 98 Data Breach Notification Law Restricted data includes: • Social Security Number • Driver’s license # or state ID # • Financial account number (credit/debit) and access code/password • DNA profile (Statute 939. 74) • Biometric data National HIPAA protects: • Health status, treatment, or payment

Combat Information Theft • What information is valuable to you? • Who has access to that information? • Is your back-up: Recent? Off-site & Secure? Not with your System Administrator? Process Documented? Tested? Encrypted?

Recognizing a Break-in or Compromise Symptoms: • Antivirus software detects a problem • Pop-ups suddenly appear (may sell security software) • Disk space disappears • Files or transactions appear that should not be there • System slows down to a crawl • Stolen laptop (1 in 10 stolen in laptop lifetime) • Often not recognized Problem: • Many computer affected at once; all must be reloaded • Law: Personally Identifiable Information disclosed: Must notify individual • Accepted figures: – $200/record tangible cost – $6. 3 M per Breach (Ponemon Institute)

Security Audit Our Network Security Class will: • Audit your server or network for security holes • Talk to you about secure computer network policies • Train your System Administrator Class expected to run Fall ’ 10