Information Rights Management EMC Content Management and Archiving














- Slides: 19

Information Rights Management EMC Content Management and Archiving © Copyright 2008 EMC Corporation. All rights reserved. 1

Business Drivers for Content Security “Despite massive investment in security technology and services… Protect intellectual property – – Trade secrets Competitive information IP theft Secured collaboration Compliance 82% 18% – Regulations – Audits Risk mitigation …fewer than one in five companies feel that all their data is adequately protected. ” – Legal exposure – Data loss – Privacy breaches Source: Enterprise Strategy Group March 2006 © Copyright 2008 EMC Corporation. All rights reserved. 2

The Threat Profile Has Shifted + Perimeter-based Security Information-based Security Necessary but insufficient Addresses root cause Assume they’re already in result 84% of high cost security incidents are a Denial of Service, network intrusion, external attack Threat Privacy breach, intellectual property theft, insider attack Access availability Focus Authorization and accountability of and insiders sending confidential material Firewall, IPS/IDS, anti-malware Approach Identity management, data encryption outside of their company. Build and protect perimeters Solution Manage and protect information Keeping the bad guys out — Gartner 2006 © Copyright 2008 EMC Corporation. All rights reserved. 5

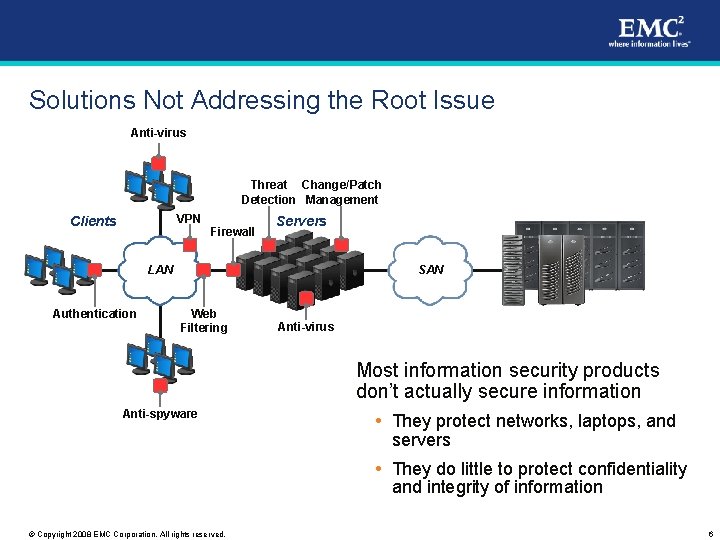
Solutions Not Addressing the Root Issue Anti-virus Threat Change/Patch Detection Management VPN Clients Firewall Servers LAN Authentication SAN Web Filtering Anti-virus Most information security products don’t actually secure information Anti-spyware They protect networks, laptops, and servers They do little to protect confidentiality and integrity of information © Copyright 2008 EMC Corporation. All rights reserved. 6

Your Content is in Motion Anti-virus Threat Change/Patch Detection Management VPN Clients Firewall Servers LAN Authentication SAN Web Filtering Anti-spyware Anti-virus Information is in constant motion throughout its lifecycle, making it difficult to lock down Perimeters and resources are constantly being traversed © Copyright 2008 EMC Corporation. All rights reserved. 7

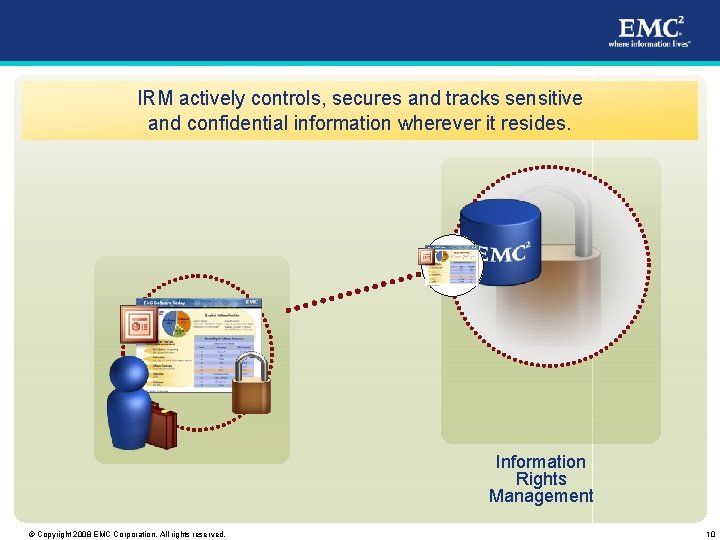
IRM actively controls, secures and tracks sensitive and confidential information wherever it resides. Information Rights Management © Copyright 2008 EMC Corporation. All rights reserved. 10

IRM Server Key and Policy Management Desktop Integration Content is always encrypted The keys are always separated from the content The local key is destroyed after use Workflow Integrations Content Owner File Share + Policy EMC Documentum Repository IRM Policy Server EMC Documentum e. Room © Copyright 2008 EMC Corporation. All rights reserved. 12

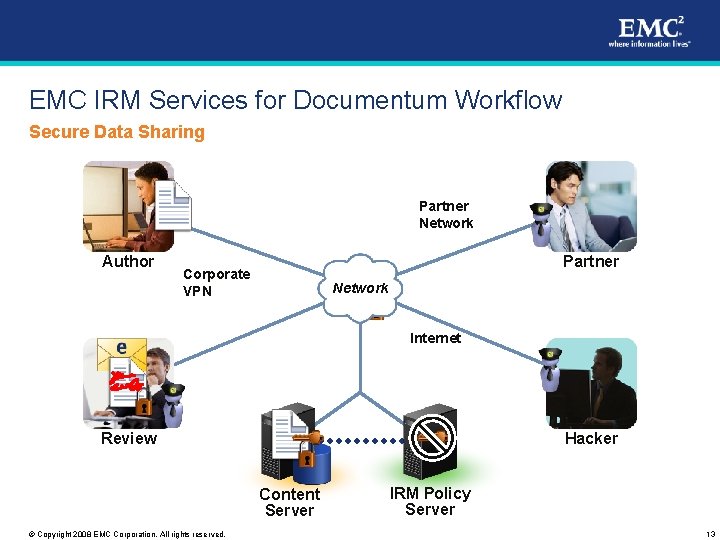
EMC IRM Services for Documentum Workflow Secure Data Sharing Partner Network Author Partner Corporate VPN Network Internet Review Hacker Content Server © Copyright 2008 EMC Corporation. All rights reserved. IRM Policy Server 13

EMC IRM Architecture Web Delivery Email. Xtender Internet Explorer Gateway e. Room Adobe MS Office File Share Documentum Admin API MS Outlook and Webtop Lotus Notes Java, WDK-based Information Rights Management SDK EMC Documentum IRM Server Authorization Authentication Auditing Key Mgmt Policy Mgmt Encryption Authentication Infrastructure ALL Authentication Domains LDAP © Copyright 2008 EMC Corporation. All rights reserved. Win X 509 RSA Documentum Custom 15

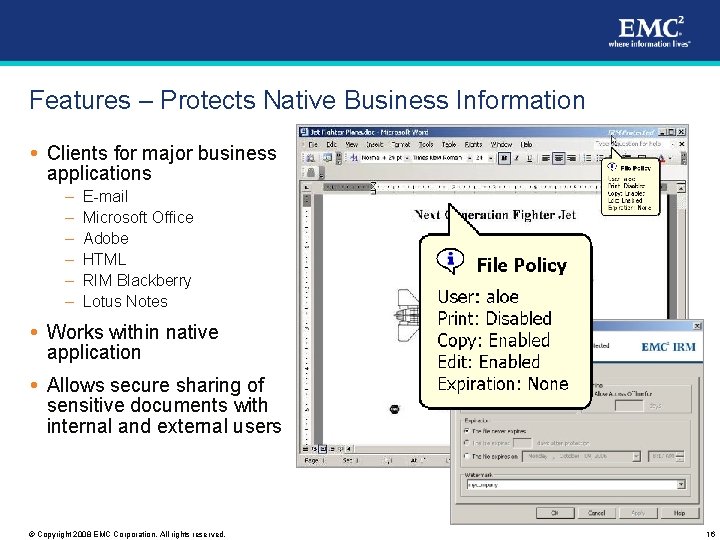
Features – Protects Native Business Information Clients for major business applications – – – E-mail Microsoft Office Adobe HTML RIM Blackberry Lotus Notes Works within native application Allows secure sharing of sensitive documents with internal and external users © Copyright 2008 EMC Corporation. All rights reserved. 16

Features – Rights Enforcement by Policy A document policy defines: Who can view What pages can be viewed (PDF only) When it can be viewed If copy or edit is allowed If printing is allowed If guest access is allowed If offline viewing is allowed Automatic expiration Dynamic watermarks © Copyright 2008 EMC Corporation. All rights reserved. 17

Features – Rights Enforcement by Policy Mandatory and discretionary policy enforcement options Choose rights enforcement using administratively-defined templates or ad-hoc policies Flexibility supports organizational rollout Allows for workgroup and enterprise-wide applications © Copyright 2008 EMC Corporation. All rights reserved. 18

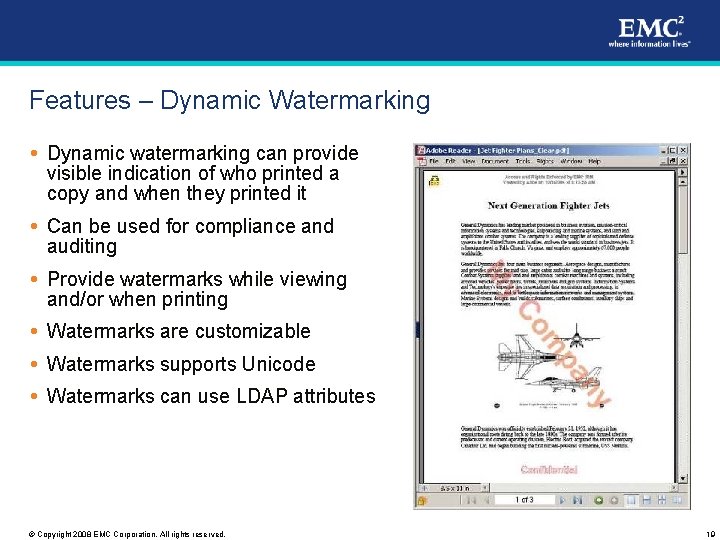
Features – Dynamic Watermarking Dynamic watermarking can provide visible indication of who printed a copy and when they printed it Can be used for compliance and auditing Provide watermarks while viewing and/or when printing Watermarks are customizable Watermarks supports Unicode Watermarks can use LDAP attributes © Copyright 2008 EMC Corporation. All rights reserved. 19

Feature – Dynamic Policy Control Dynamic policy control allows recipient entitlements to be changed on-the-fly when individual roles or business needs change, regardless of where the content resides. NEW Example: In April a price list with IRM is downloaded by a sales person The sales person e-mails the price list to a customer On May 17, prices change and new prices are issued At that time, rights on the old price list are revoked, affecting all copies, regardless of location © Copyright 2008 EMC Corporation. All rights reserved. 20

Feature – Continuous Audit Trail All events in IRM are auditable IRM provides granular audit trail of what recipients did with the documents, page by page See who did what, when Delivers on-going assurance of policy compliance Auditing is continuous, whether online or offline Leverage XML logging standards for reporting on audit trail © Copyright 2008 EMC Corporation. All rights reserved. 22

Customer Case Study Ford Motor Company Requirements Securely share the 10 year “Vehicle Vision” product plan for the Ford brands and keep away from competitors and the media Require multiple access levels for brand executives Must be easy to use for 1, 000 insiders around the world, including Chairman Bill Ford Jr. IRM Solution Document owner protects and distributes through portal No access outside of current insider list Username watermark raises the bar on distribution “We don’t want to see this in the Detroit Free Press…” © Copyright 2008 EMC Corporation. All rights reserved. 25

Case Study Challenges – Sharing price lists and competitive materials with 2000 sales agents and suppliers globally – High cost for logistics to distribute by paper – Competitors placing bounty on our price books IRM Solution – Access is tracked continuously and audited – Ensures only authorized users can access info. – Username is impressed as a watermark – Marketing can irrevocably delete at any time ROI: 6 month payback, elimination of paper and delivery costs Marketing update price books monthly instead of quarterly © Copyright 2008 EMC Corporation. All rights reserved. 26

Customer Case Study Off Wall Street Requirements Protect highly valuable financial information sold as a subscription Ensure that documents are not forwarded to unauthorized users, especially competitors Regulate what recipients can do with the information (e. g. , print, edit) consistently for all reports regardless of who distributes them IRM Solution “The product has been trouble-free from the start. We've never had a problem with the software, ever. “ — Mark Roberts, CEO Increases revenue: users cannot access reports without paying for it Provides policy-based usage controls and audit trail for information access © Copyright 2008 EMC Corporation. All rights reserved. 27

Industry Use Examples for IRM Manufacturing – Sharing of new product specifications, planning, R&D, and pricing documents Government – Share information on a need-to-know basis within intelligence community Healthcare – Communications with business associates – Control of PHI dissemination Financial and Legal Services – – On-line mergers and acquisitions Protect customer data High value research circulation control Secure distribution of bills of lading © Copyright 2008 EMC Corporation. All rights reserved. 28
 Emc content management
Emc content management Emc information storage and management
Emc information storage and management Positive rights vs negative rights
Positive rights vs negative rights Legal rights and moral rights
Legal rights and moral rights Legal rights and moral rights
Legal rights and moral rights Positive rights and negative rights
Positive rights and negative rights Characteristics of esp
Characteristics of esp Informix
Informix Littoral water rights
Littoral water rights Negative rights vs positive rights
Negative rights vs positive rights Negative right
Negative right Positive rights vs negative rights
Positive rights vs negative rights Dynamic content vs static content
Dynamic content vs static content Picture archiving and communication system
Picture archiving and communication system Email archiving and retention exchange 2012
Email archiving and retention exchange 2012 Europe healthcare archiving and ediscovery market outlook
Europe healthcare archiving and ediscovery market outlook Text archiving services
Text archiving services Oracle database archiving
Oracle database archiving Archiving by design
Archiving by design K-12 web archiving
K-12 web archiving