Information flowbased Risk Assessment in Access Control Systems

Information flow-based Risk Assessment in Access Control Systems Sofiene Boulares, Ph. D student Luigi Logrippo, Supervisor Université du Québec en Outaouais Gatineau, Québec, Canada sofiene. boulares@uqo. ca; luigi. logrippo@uqo. ca

Agenda I. III. IV. Toward flexible risk-based access control Risk based access control Expected Contributions Steps of the proposed Approach 1. 2. 3. 4. 5. Dynamic determination of objects and subjects security levels Information flow-based assessment of intrinsic likelihood Likelihood assessment Impact assessment Risk assessment V. Overall view of the approach VI. Process flow Based on XACML Architecture VII. Conclusion and future work 2

Toward flexible risk-based access control • Most current access control systems simply give a yes-no answer to access control requests, usually based on security administrator decisions which are taken off-line • In many applications, this is too rigid and static • No consideration of changing situations • We propose an information flow-based risk assessment approach that dynamically evaluates the risk of accessing information • Information flow is the transfer of information from subjects to objects and vice versa • As information moves in the system, risk levels for subjects and objects change • The results of this assessment can be used by access control systems in a variety of ways 3
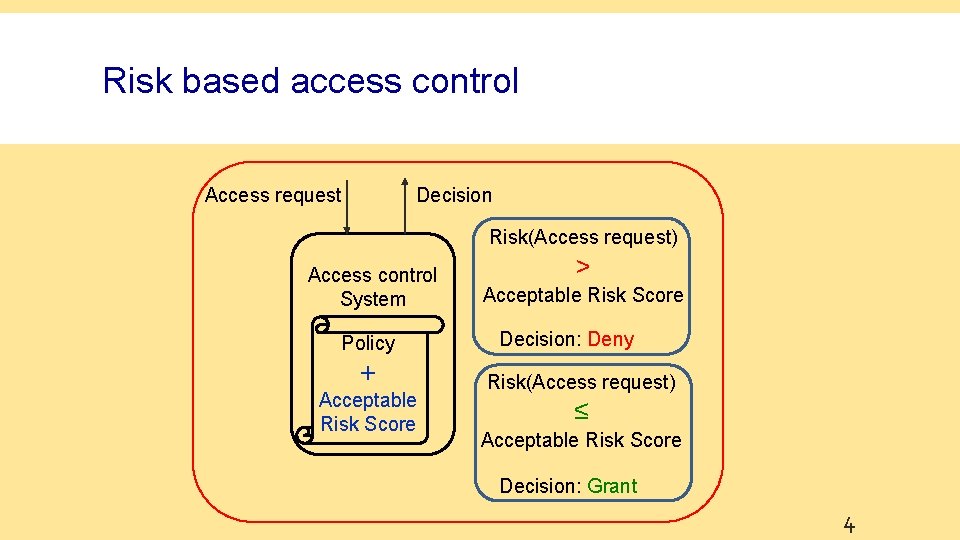
Risk based access control Decision Access request Risk(Access request) Access control System Policy + Acceptable Risk Score > Acceptable Risk Score Decision: Deny Risk(Access request) ≤ Acceptable Risk Score Decision: Grant 4

Expected Contributions • Dynamic determination of subjects’ and objects’ security levels : • History-based approach with consideration of past accesses • Threat likelihood assessment : • Information flow-based approach for assessing threat likelihood • Risk assessment : • Security controls in risk assessment • Evaluation principles will be given • Evaluation formulas will be proposed 5

Steps of the proposed approach for risk assessment 1. 2. 3. 4. 5. Security levels determination of objects and subjects Intrinsic likelihood assessment Likelihood assessment Impact assessment Risk assessment 6

Steps of the proposed approach for risk assessment 1. Security levels determination of objects and subjects 2. 3. 4. 5. Intrinsic likelihood assessment Likelihood assessment Impact assessment Risk assessment 7
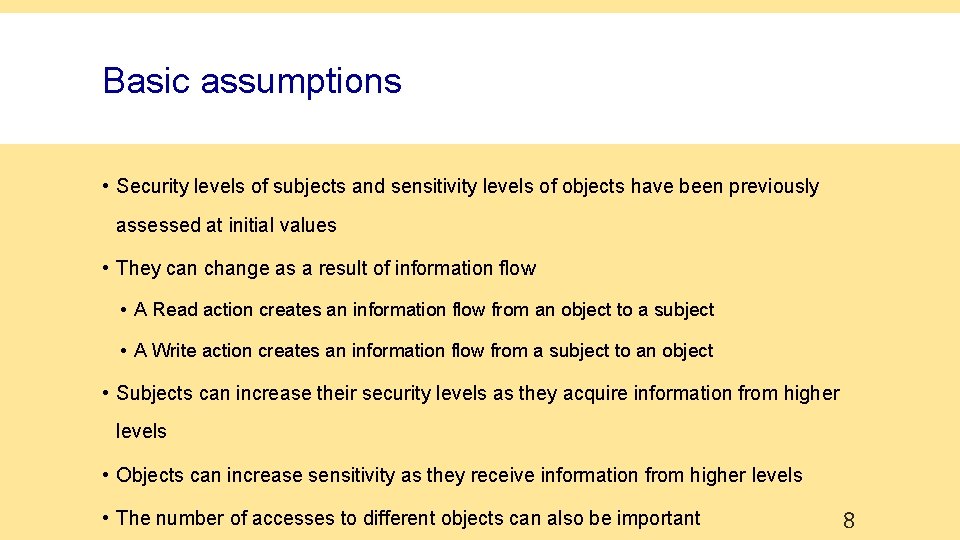
Basic assumptions • Security levels of subjects and sensitivity levels of objects have been previously assessed at initial values • They can change as a result of information flow • A Read action creates an information flow from an object to a subject • A Write action creates an information flow from a subject to an object • Subjects can increase their security levels as they acquire information from higher levels • Objects can increase sensitivity as they receive information from higher levels • The number of accesses to different objects can also be important 8
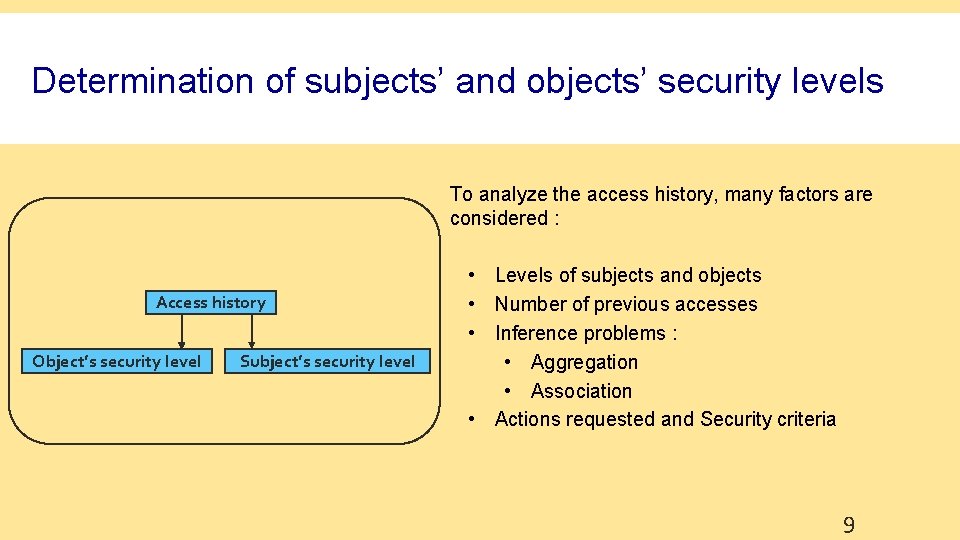
Determination of subjects’ and objects’ security levels To analyze the access history, many factors are considered : Access history Object’s security level Subject’s security level • Levels of subjects and objects • Number of previous accesses • Inference problems : • Aggregation • Association • Actions requested and Security criteria 9
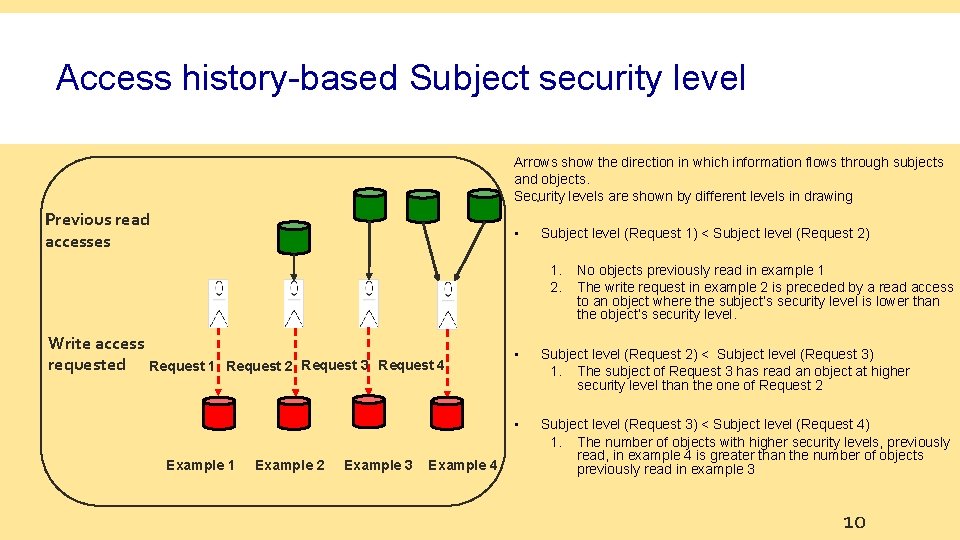
Access history-based Subject security level Arrows show the direction in which information flows through subjects and objects. Security levels are shown by different levels in drawing. Previous read accesses • Subject level (Request 1) < Subject level (Request 2) 1. 2. Write access requested Request 1 Request 2 Request 3 Request 4 Example 1 Example 2 Example 3 Example 4 No objects previously read in example 1 The write request in example 2 is preceded by a read access to an object where the subject’s security level is lower than the object’s security level. • Subject level (Request 2) < Subject level (Request 3) 1. The subject of Request 3 has read an object at higher security level than the one of Request 2 • Subject level (Request 3) < Subject level (Request 4) 1. The number of objects with higher security levels, previously read, in example 4 is greater than the number of objects previously read in example 3 10
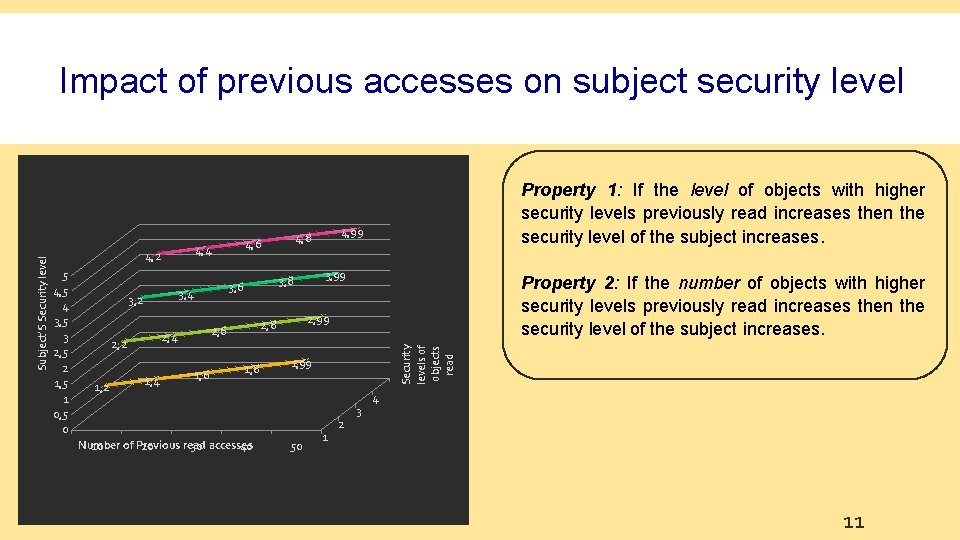
4, 4 4, 2 5 4, 5 4 3, 5 3 2, 5 2 1, 5 1 0, 5 0 3, 4 3, 2 1, 4 1, 6 1, 8 Number of Previous read 10 20 30 accesses 40 Property 2: If the number of objects with higher security levels previously read increases then the security level of the subject increases. 2, 99 2, 8 2, 6 2, 4 2, 2 3, 99 3, 8 3, 6 4, 99 4, 8 4, 6 Property 1: If the level of objects with higher security levels previously read increases then the security level of the subject increases. Security levels of objects read Subject’S Security level Impact of previous accesses on subject security level 1, 99 50 1 2 3 4 11
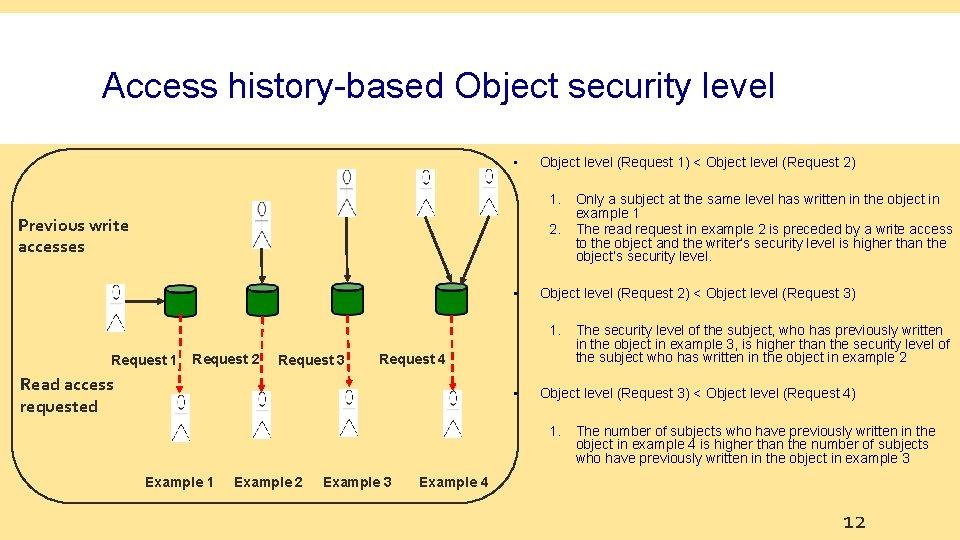
Access history-based Object security level • Object level (Request 1) < Object level (Request 2) 1. Previous write accesses 2. • Object level (Request 2) < Object level (Request 3) 1. Request 1 Request 2 Request 3 Request 4 Read access requested • Example 2 Example 3 The security level of the subject, who has previously written in the object in example 3, is higher than the security level of the subject who has written in the object in example 2 Object level (Request 3) < Object level (Request 4) 1. Example 1 Only a subject at the same level has written in the object in example 1 The read request in example 2 is preceded by a write access to the object and the writer’s security level is higher than the object’s security level. The number of subjects who have previously written in the object in example 4 is higher than the number of subjects who have previously written in the object in example 3 Example 4 12
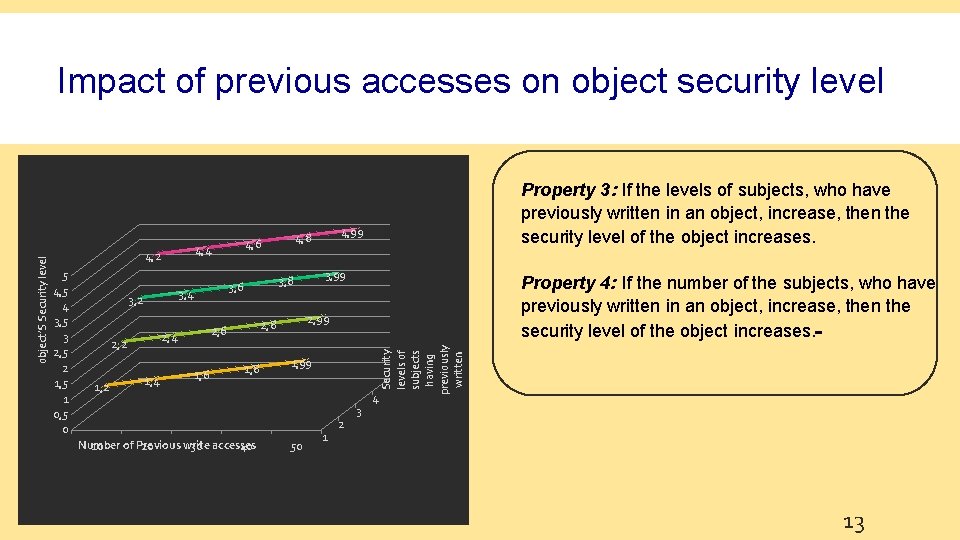
4, 4 4, 2 5 4, 5 4 3, 5 3 2, 5 2 1, 5 1 0, 5 0 3, 4 3, 2 1, 4 1, 6 1, 8 Number of Previous write 10 20 30 accesses 40 Property 4: If the number of the subjects, who have previously written in an object, increase, then the security level of the object increases. 2, 99 2, 8 2, 6 2, 4 2, 2 3, 99 3, 8 3, 6 4, 99 4, 8 4, 6 Property 3: If the levels of subjects, who have previously written in an object, increase, then the security level of the object increases. 1, 99 50 1 2 3 4 Security levels of subjects having previously written object’S Security level Impact of previous accesses on object security level 13
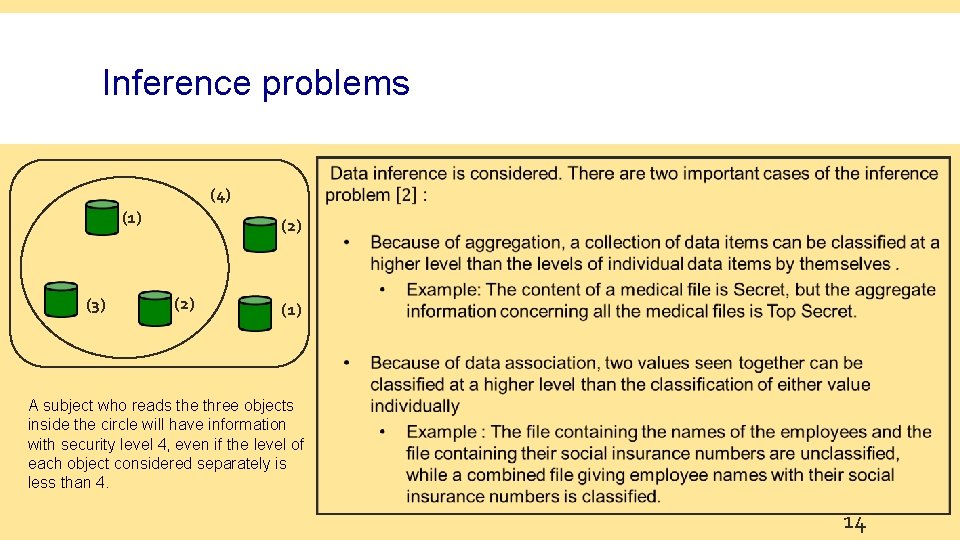
Inference problems (4) (1) (3) (2) (1) A subject who reads the three objects inside the circle will have information with security level 4, even if the level of each object considered separately is less than 4. 14

Steps of the proposed approach for risk assessment 1. Security levels determination of objects and subjects 2. Intrinsic likelihood assessment 3. Likelihood assessment 4. Impact assessment 5. Risk assessment 15
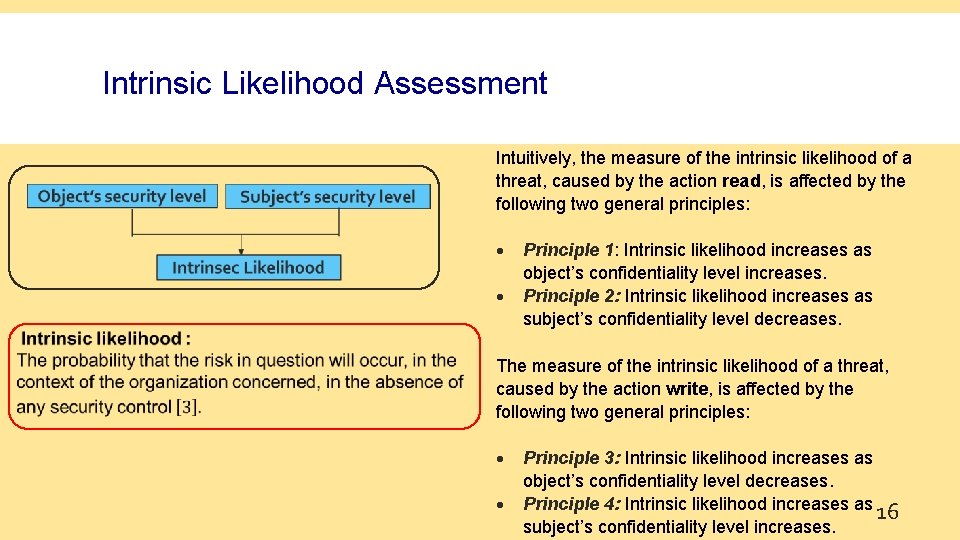
Intrinsic Likelihood Assessment Intuitively, the measure of the intrinsic likelihood of a threat, caused by the action read, is affected by the following two general principles: Principle 1: Intrinsic likelihood increases as object’s confidentiality level increases. Principle 2: Intrinsic likelihood increases as subject’s confidentiality level decreases. The measure of the intrinsic likelihood of a threat, caused by the action write, is affected by the following two general principles: Principle 3: Intrinsic likelihood increases as object’s confidentiality level decreases. Principle 4: Intrinsic likelihood increases as 16 subject’s confidentiality level increases.

Steps of the proposed approach for risk assessment 1. Security levels determination of objects and subjects 2. Intrinsic likelihood assessment 3. Likelihood assessment 4. Impact assessment 5. Risk assessment 17

Access requests risk knowledge base To assess the risk of access requests, we use an access requests risk knowledge base that includes: • The description of the characteristic elements of each access request risk • The information on the relevant security controls for each type of risk • The relationship between the quality of these controls • The effectiveness of risk reduction factors 13

Security controls for likelihood reduction • “Security controls are the management, operational, and technical safeguards or countermeasures prescribed for an information system to protect the confidentiality, integrity, and availability of a system and its information” [4] Example : • Case 1 : Access request in an environment where maximum level security controls are implemented (strong authentication, efficient encryption algorithm, etc. ) • Case 2 : The same access request in an environment where fewer security controls are implemented • Intuitively, Likelihood in case 1 is higher than in case 2. Security controls are a parameter to be considered when assessing the risk of access requests 19

Security controls categories • Dissuasive and preventive controls that act on likelihood • Dissuasive controls: Access auditing • Preventive controls: Strong authentication • Protective and palliative controls that act on impact • Protective: Interdiction of accesses • Palliative: for integrity, backing up files before authorizing access 20
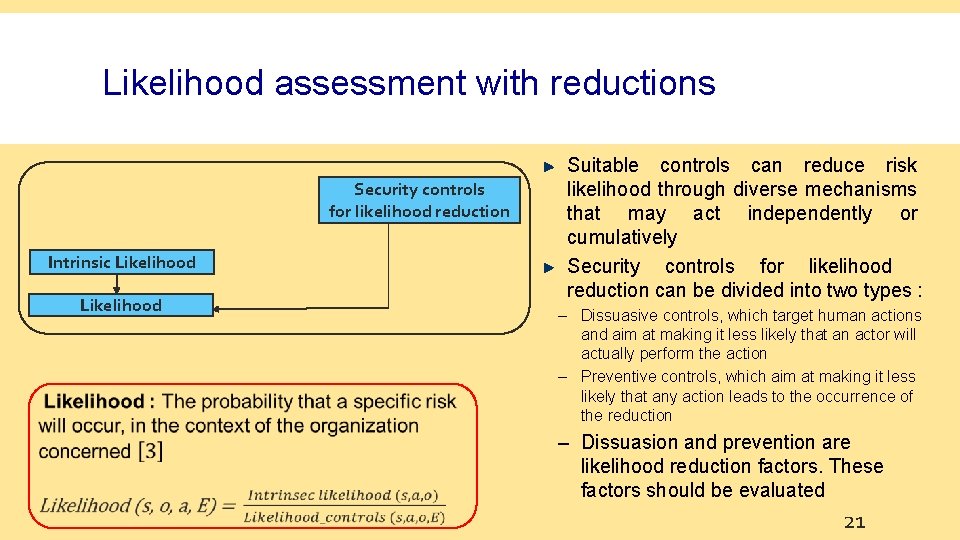
Likelihood assessment with reductions Security controls for likelihood reduction Intrinsic Likelihood Suitable controls can reduce risk likelihood through diverse mechanisms that may act independently or cumulatively Security controls for likelihood reduction can be divided into two types : – Dissuasive controls, which target human actions and aim at making it less likely that an actor will actually perform the action – Preventive controls, which aim at making it less likely that any action leads to the occurrence of the reduction – Dissuasion and prevention are likelihood reduction factors. These factors should be evaluated 21

Steps of the proposed approach for risk assessment 1. Security levels determination of objects and subjects 2. Intrinsic likelihood assessment 3. Likelihood assessment 4. Impact assessment 5. Risk assessment 22
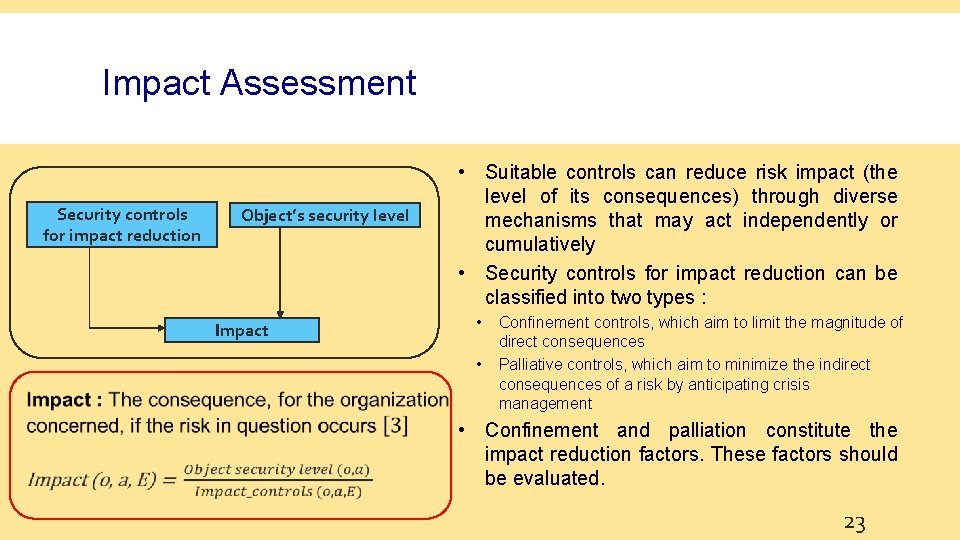
Impact Assessment Security controls for impact reduction Object’s security level Impact • Suitable controls can reduce risk impact (the level of its consequences) through diverse mechanisms that may act independently or cumulatively • Security controls for impact reduction can be classified into two types : • • Confinement controls, which aim to limit the magnitude of direct consequences Palliative controls, which aim to minimize the indirect consequences of a risk by anticipating crisis management • Confinement and palliation constitute the impact reduction factors. These factors should be evaluated. 23

Steps of the proposed approach for risk assessment 1. 2. 3. 4. Security levels determination of objects and subjects Intrinsic likelihood assessment Likelihood assessment Impact assessment 5. Risk assessment 24
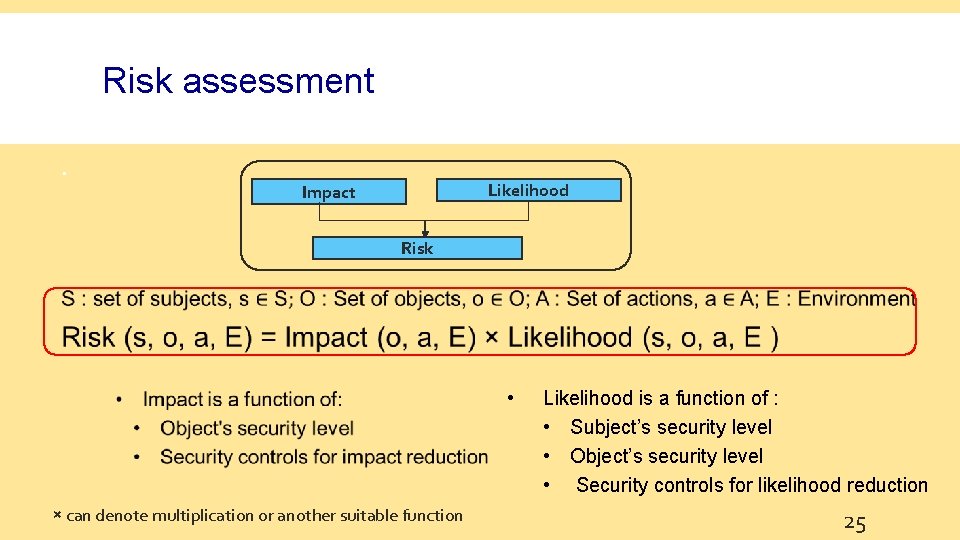
Risk assessment Likelihood Impact Risk • × can denote multiplication or another suitable function Likelihood is a function of : • Subject’s security level • Object’s security level • Security controls for likelihood reduction 25
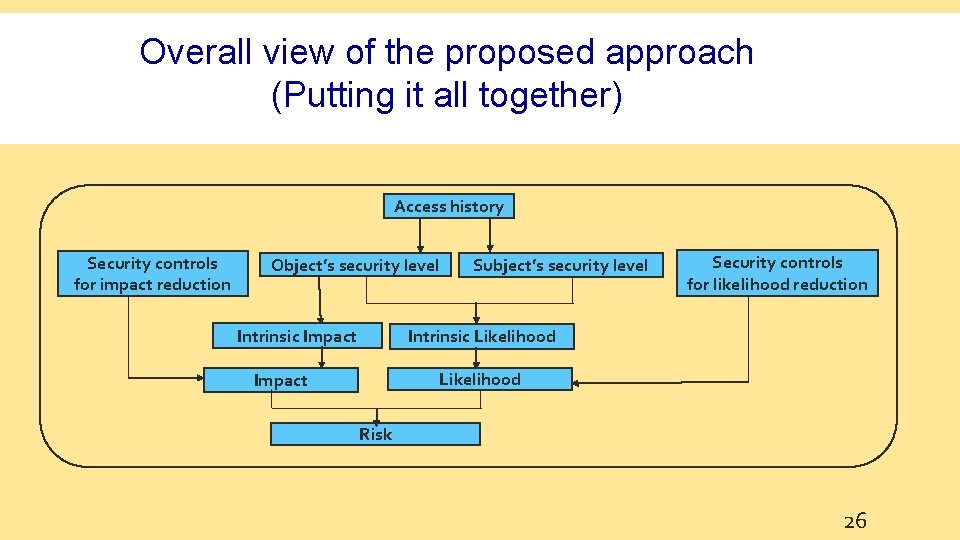
Overall view of the proposed approach (Putting it all together) Access history Security controls for impact reduction Object’s security level Intrinsic Impact Subject’s security level Security controls for likelihood reduction Intrinsic Likelihood Impact Risk 26
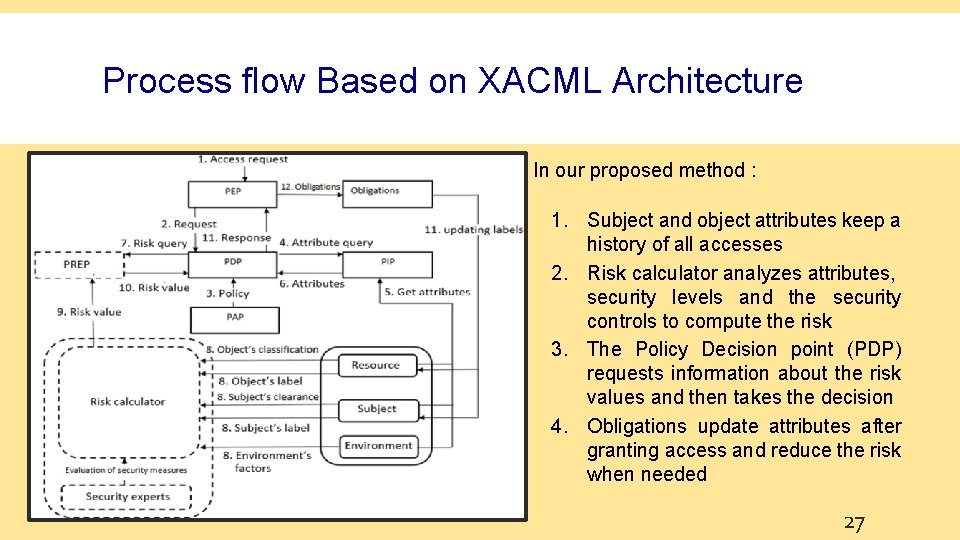
Process flow Based on XACML Architecture In our proposed method : 1. Subject and object attributes keep a history of all accesses 2. Risk calculator analyzes attributes, security levels and the security controls to compute the risk 3. The Policy Decision point (PDP) requests information about the risk values and then takes the decision 4. Obligations update attributes after granting access and reduce the risk when needed 27

Conclusion • Risk-based access control decisions, considering impact and likelihood • Impact and likelihood calculations are based on security levels of subjects and objects, determined according to information flow i. e. access histories • Security Controls for impact and likelihood reduction are also considered 28
Future work • Formalization of concepts. • Formulae for subjects and objects level determination • Formulae for likelihood and impact assessment. • Consideration of time and location to determine security levels of objects and subjects • Identification of obligations to act on precise parameters with precise values of risk reduction. 29

Research Framework This project is in the framework of other projects of our group that are investigating: Policy languages and Access Control models for the Cloud and for the Web Data access and flow control in workflow contexts 30
![References [1] http: //csrc. nist. gov/publications/nistpubs/800 -30/sp 800 -30. pdf [2] http: //profsandhu. com/articles/auerbach/a References [1] http: //csrc. nist. gov/publications/nistpubs/800 -30/sp 800 -30. pdf [2] http: //profsandhu. com/articles/auerbach/a](http://slidetodoc.com/presentation_image_h2/8c408fb54cfaf1e3c230a9809b2e70bb/image-31.jpg)
References [1] http: //csrc. nist. gov/publications/nistpubs/800 -30/sp 800 -30. pdf [2] http: //profsandhu. com/articles/auerbach/a 93 dsc. pdf [3] http: //www. clusif. asso. fr/fr/production/ouvrages/pdf/MEHARI-2010 Principles-Specifications. pdf [4] http: //nvlpubs. nist. gov/nistpubs/Special. Publications/NIST. SP. 80053 r 4. pdf 31
- Slides: 31