Information Flow CSSE 490 Computer Security Mark Ardis

![Example Confinement Model Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL] Example Confinement Model Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL]](https://slidetodoc.com/presentation_image_h2/92d851c2dac12e26e5c4b2b7facd1b45/image-10.jpg)
![Another Example Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL] confine(b) Another Example Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL] confine(b)](https://slidetodoc.com/presentation_image_h2/92d851c2dac12e26e5c4b2b7facd1b45/image-11.jpg)

![Example Iteration Statement while i < n do begin a[i] : = b[i]; i Example Iteration Statement while i < n do begin a[i] : = b[i]; i](https://slidetodoc.com/presentation_image_h2/92d851c2dac12e26e5c4b2b7facd1b45/image-19.jpg)
- Slides: 19

Information Flow CSSE 490 Computer Security Mark Ardis, Rose-Hulman Institute April 22, 2004 1

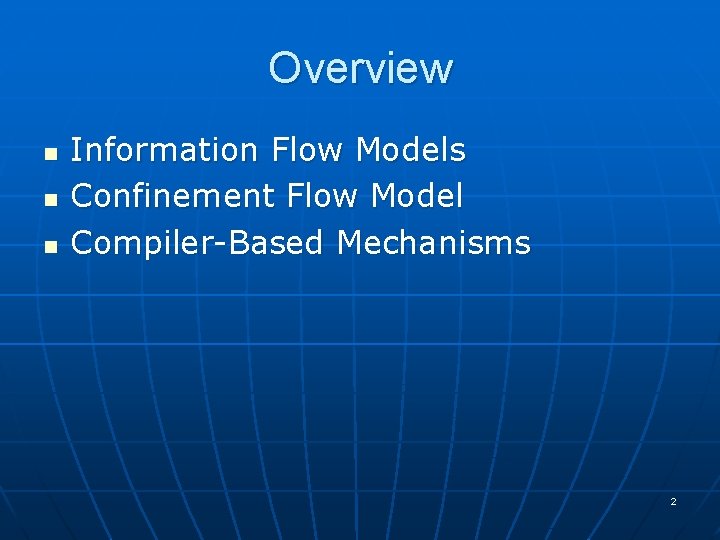
Overview n n n Information Flow Models Confinement Flow Model Compiler-Based Mechanisms 2

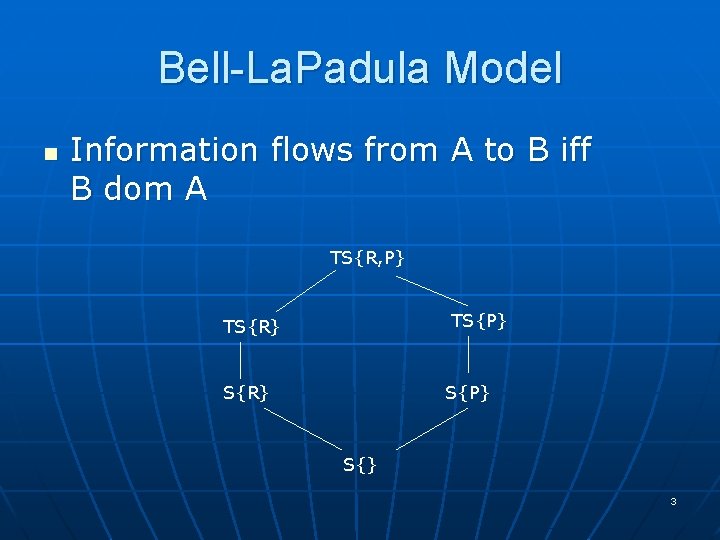
Bell-La. Padula Model n Information flows from A to B iff B dom A TS{R, P} TS{R} S{P} S{} 3

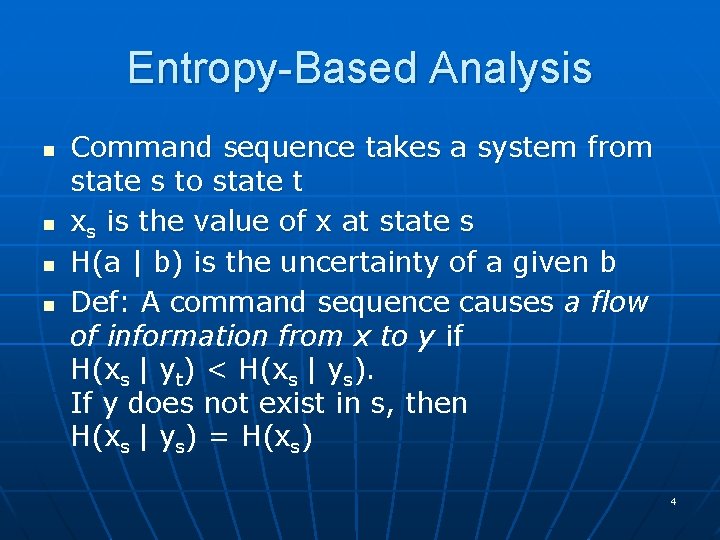
Entropy-Based Analysis n n Command sequence takes a system from state s to state t xs is the value of x at state s H(a | b) is the uncertainty of a given b Def: A command sequence causes a flow of information from x to y if H(xs | yt) < H(xs | ys). If y does not exist in s, then H(xs | ys) = H(xs) 4

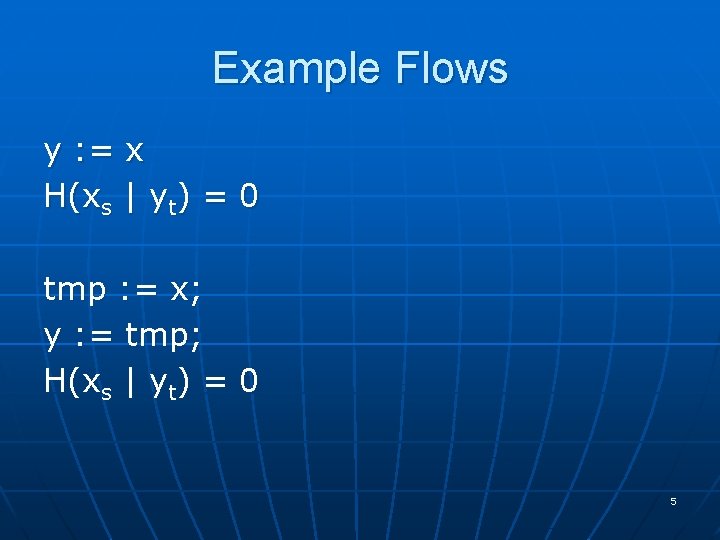
Example Flows y : = x H(xs | yt) = 0 tmp : = x; y : = tmp; H(xs | yt) = 0 5

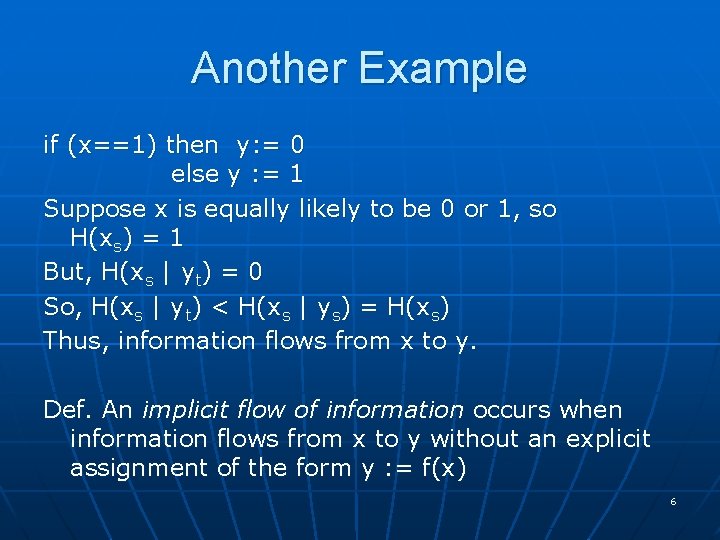
Another Example if (x==1) then y: = 0 else y : = 1 Suppose x is equally likely to be 0 or 1, so H(xs) = 1 But, H(xs | yt) = 0 So, H(xs | yt) < H(xs | ys) = H(xs) Thus, information flows from x to y. Def. An implicit flow of information occurs when information flows from x to y without an explicit assignment of the form y : = f(x) 6

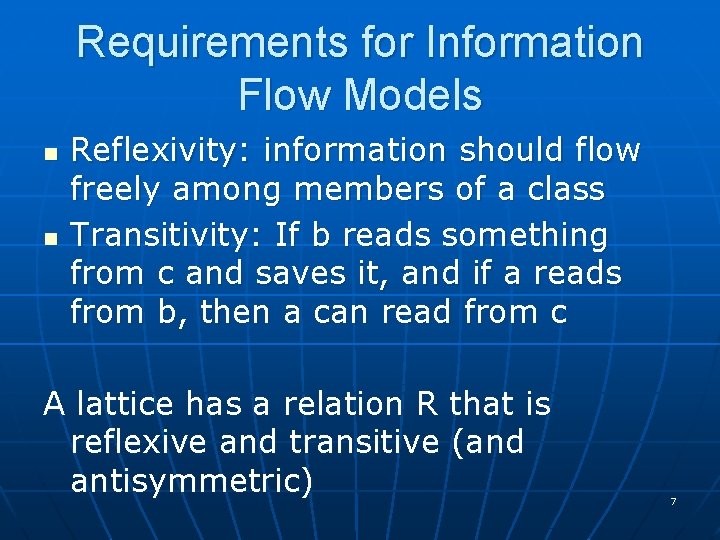
Requirements for Information Flow Models n n Reflexivity: information should flow freely among members of a class Transitivity: If b reads something from c and saves it, and if a reads from b, then a can read from c A lattice has a relation R that is reflexive and transitive (and antisymmetric) 7

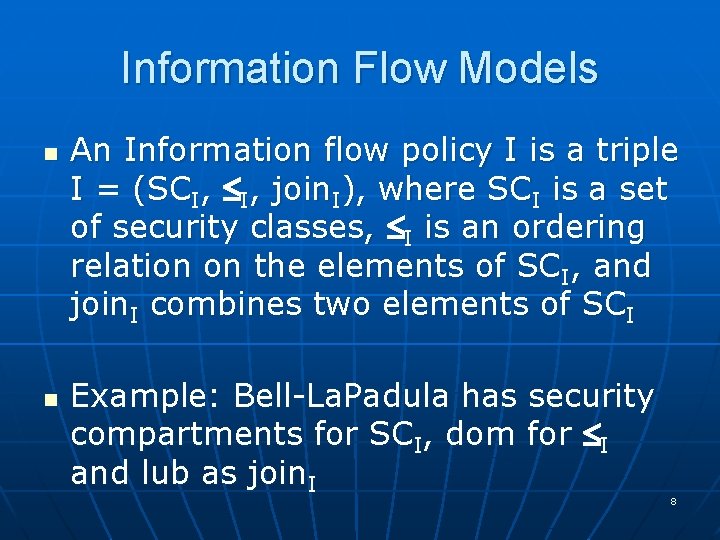
Information Flow Models n n An Information flow policy I is a triple I = (SCI, I, join. I), where SCI is a set of security classes, I is an ordering relation on the elements of SCI, and join. I combines two elements of SCI Example: Bell-La. Padula has security compartments for SCI, dom for I and lub as join. I 8

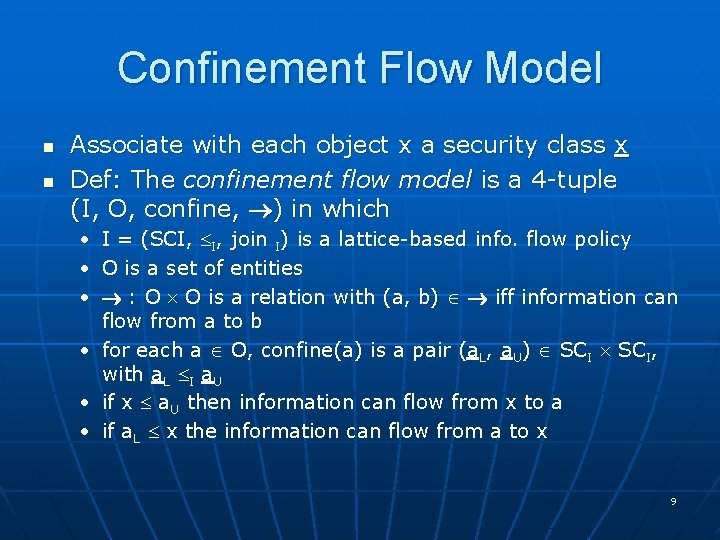
Confinement Flow Model n n Associate with each object x a security class x Def: The confinement flow model is a 4 -tuple (I, O, confine, ) in which • • • I = (SCI, I, join I) is a lattice-based info. flow policy O is a set of entities : O O is a relation with (a, b) iff information can flow from a to b • for each a O, confine(a) is a pair (a. L, a. U) SCI, with a. L I a. U • if x a. U then information can flow from x to a • if a. L x the information can flow from a to x 9
![Example Confinement Model Let a b and c O confinea CONFIDENTIAL CONFIDENTIAL Example Confinement Model Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL]](https://slidetodoc.com/presentation_image_h2/92d851c2dac12e26e5c4b2b7facd1b45/image-10.jpg)
Example Confinement Model Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL] confine(b) = [SECRET, SECRET] confine(c) = [TOPSECRET, TOPSECRET] Then a b, a c, and b c are the legal flows 10
![Another Example Let a b and c O confinea CONFIDENTIAL CONFIDENTIAL confineb Another Example Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL] confine(b)](https://slidetodoc.com/presentation_image_h2/92d851c2dac12e26e5c4b2b7facd1b45/image-11.jpg)
Another Example Let a, b, and c O confine(a) = [ CONFIDENTIAL, CONFIDENTIAL] confine(b) = [SECRET, SECRET] confine(c) = [CONFIDENTIAL, TOPSECRET] Then a b, a c, b c, and c a are the legal flows Note that b c and c a, but information cannot flow from b to a because b. L I a. U is false So, transitivity fails to hold 11

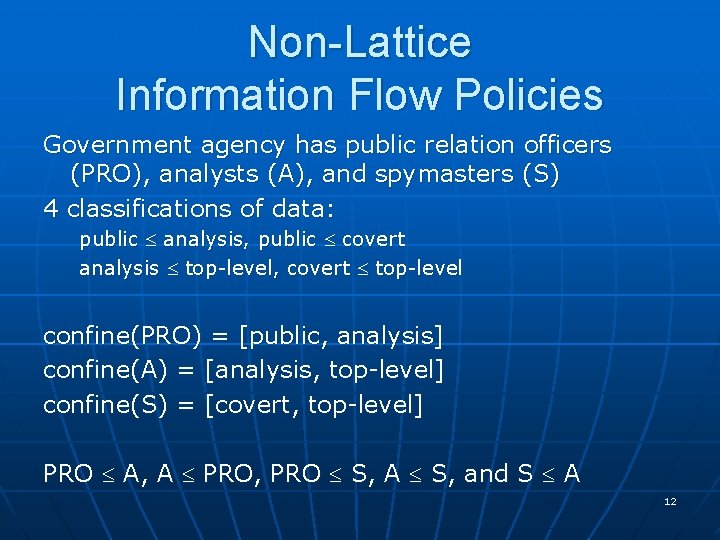
Non-Lattice Information Flow Policies Government agency has public relation officers (PRO), analysts (A), and spymasters (S) 4 classifications of data: public analysis, public covert analysis top-level, covert top-level confine(PRO) = [public, analysis] confine(A) = [analysis, top-level] confine(S) = [covert, top-level] PRO A, A PRO, PRO S, A S, and S A 12

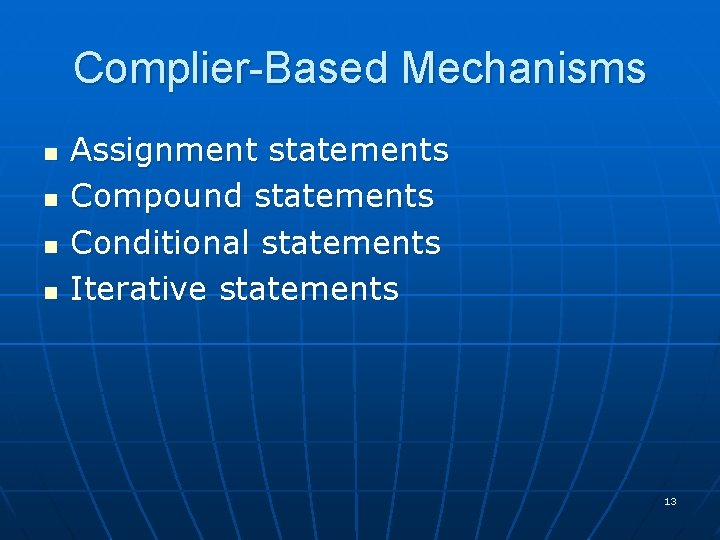
Complier-Based Mechanisms n n Assignment statements Compound statements Conditional statements Iterative statements 13

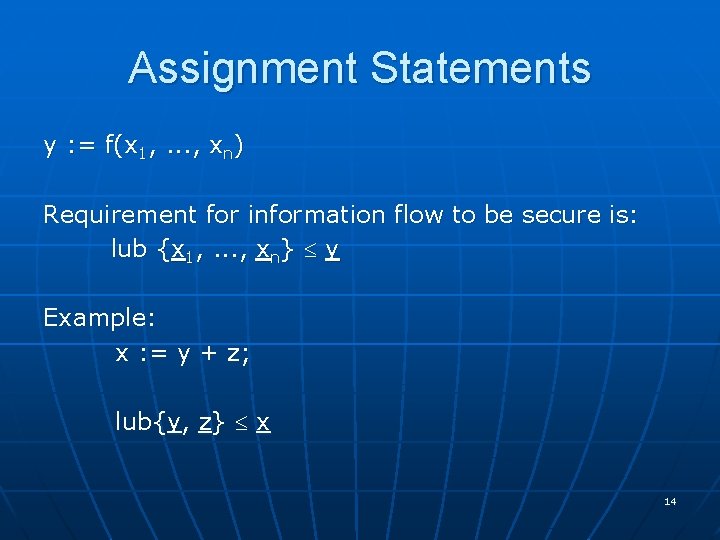
Assignment Statements y : = f(x 1, . . . , xn) Requirement for information flow to be secure is: lub {x 1, . . . , xn} y Example: x : = y + z; lub{y, z} x 14

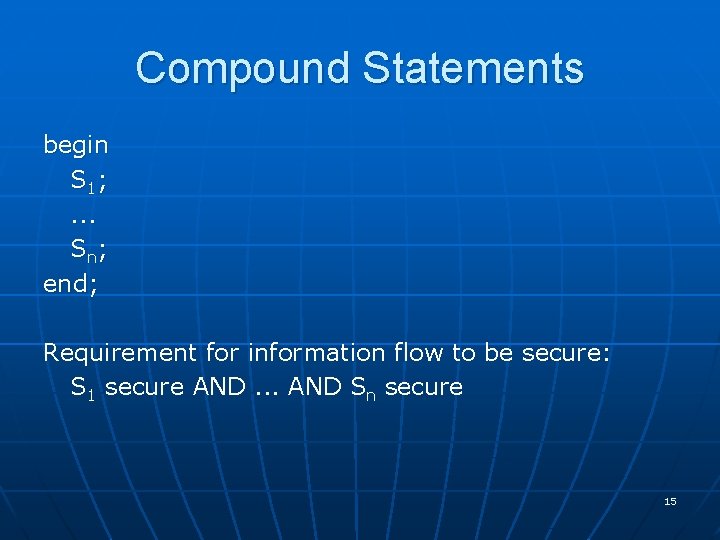
Compound Statements begin S 1; . . . Sn; end; Requirement for information flow to be secure: S 1 secure AND. . . AND Sn secure 15

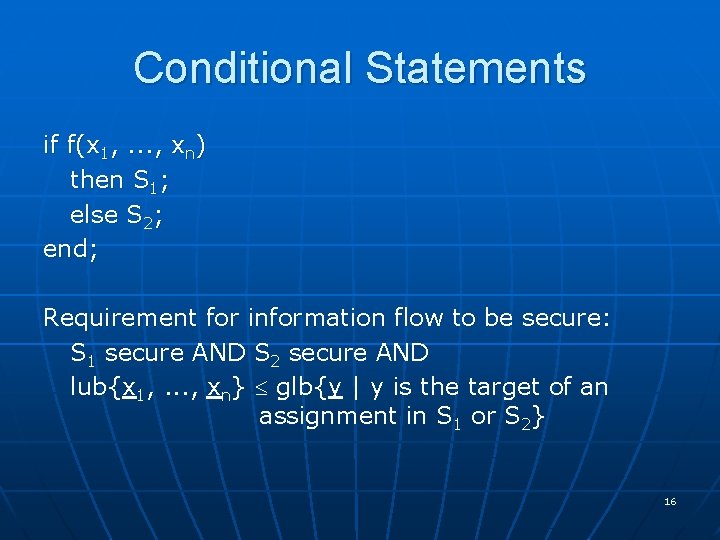
Conditional Statements if f(x 1, . . . , xn) then S 1; else S 2; end; Requirement for information flow to be secure: S 1 secure AND S 2 secure AND lub{x 1, . . . , xn} glb{y | y is the target of an assignment in S 1 or S 2} 16

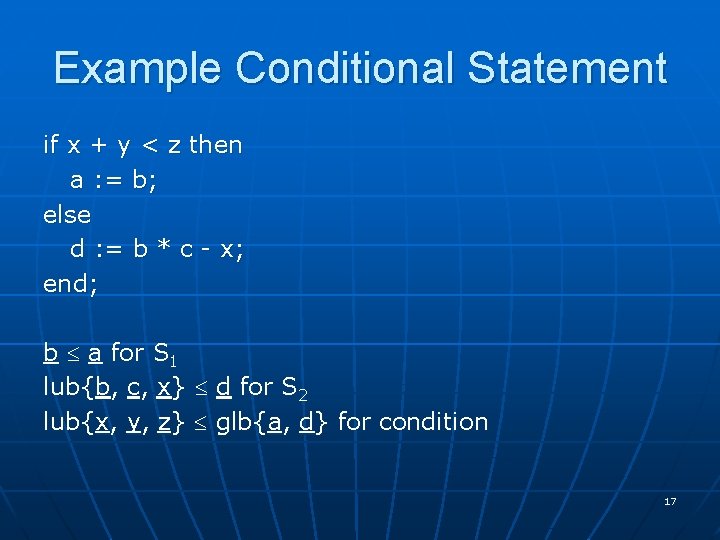
Example Conditional Statement if x + y < z then a : = b; else d : = b * c - x; end; b a for S 1 lub{b, c, x} d for S 2 lub{x, y, z} glb{a, d} for condition 17

Iterative Statements while f(x 1, . . . , xn) do S; Requirement for information flow to be secure: Iteration terminates S secure lub{x 1, . . . , xn} glb{y | y is the target of an assignment in S} 18
![Example Iteration Statement while i n do begin ai bi i Example Iteration Statement while i < n do begin a[i] : = b[i]; i](https://slidetodoc.com/presentation_image_h2/92d851c2dac12e26e5c4b2b7facd1b45/image-19.jpg)
Example Iteration Statement while i < n do begin a[i] : = b[i]; i : = i + 1; end; Loop terminates i a[i] AND b[i] a[i] for S 1 lub{i, b[i]} a[i] for compound statement lub{b[i], i, n} glb{a[i], i} for while condition 19