Information Delay 951610 Information Delay The reasons for





















































































































- Slides: 141

Information Delay 951610 范博鈞

Information Delay The reasons for the delay of information are Ø Old system Ø Human factors - Improperation Ø Natural disasters - fire, flood, earthquake…and so on Ø System compatible - Old and new systems interface properly

How it impact on business Information delay may cause some problem Ø Message too slow cause serious damage ex : Rescue injuries Ø Difficult to find potential problems Ø Date information is difficult to predict the future situation ex : Market conditions

The Solutions Problem solution ØUpdate System ØReduce unnecessary system ØRegular maintenance of the system ØReduce unnecessary procedures

Example(1) Example Ø Old traffic Information System will be slow return the status of traffic ØSome industries or organizations which need speed to task (ex: Hospital , Express delivery) have a great impact ØUpdated traffic information system is imperative ØThe immediate state of roads lets the transportation be better unobstructedly

Example(2) Seattle, Washington trafficview website (http: //trafficview. seattle. sidewalk 1. com. /) ØUsers can view ü Closed circuit television (CCTV) on the real-time traffic ü The current situation of road congestion ü Image update time is about 2. 5 minutes. ØOn the driver Travel information, the website provides highway travel time calculations. ü The shortest path ü Alternative path ü Start and end points, distance ü The travel time.

Data Leakage by Employee 961758 宋函娟

How it impact on business The competitor get your company’s latest research information without any cost. Reason – Employees use information or facilities carelessly, wrongly or abusively. Consequence - Up to 80% of data leakage incidents are due to the stolen computer or tape and other manual processes or information delivery on the negligent.

Example This case occurred in an IT equipment manufacturer. Lose about 10 GB of confidential documents. Staff ready to join their competitors, use many techniques to steal the company's important data.

Process 1. Scan Network Neighborhood on other colleague’s computers shared documents. 2. The company's confidential information stored in the removable hard disk. 3. Move the hard disk to the test computer without IT department control. 4. Set up his own VPN encrypted channel, transmit the confidential information in hard disk to his own laptop.

Technique 1 Virtual Private Network;VPN encapsulates data transfers between two or more networked devices not on the same private network so as to keep the transferred data private from other devices on one or more intervening local or wide area networks.

Process (continue) 5. Because the amoumt of information is too large, the employee use P 2 P software to transfer. 6. Transmission of information overload and illegal use of P 2 P software, caused IT staff concern twice. 7. Company found that employees acting suspiciously, then ask the information security consultant forensic for assistance. 8. Through file name keyword search, find the computer that using P 2 P software to leak information.

Technique 2 P 2 P A peer-to-peer, commonly abbreviated to P 2 P, is any distributed network architecture composed of participants that make a portion of their resources directly available to other network participants, without the need for central coordination instances. Peers are both suppliers and consumers of resources, in contrast to the traditional client–server model where only servers supply, and clients consume. Peer-to-peer was popularized by file sharing systems like Napster.

Result Even if the employees caught committing crimes, But the company's confidential information leakage concerns still. Because the information was leaked by P 2 P techniques, there may be other people get through the P 2 P network The staff was not allowed to resign, is also removed from any Internet jobs.

The Solutions Keys - public key : For others to access and encrypt or decrypt data - private key:Only their own self can possess and use Security Codes - password should be changed frequently - consist of unusual combinations Auditing IT Security

The Solutions Save the digital evidence - Business should save the log files of all the information security equipment and backup information.

Natural Disaster 951655 田祖劼

How it impact on a business Natural Disaster fire, flood, earthquake, lightning Power failure hard to avoid and predict Can’t solve the problem of Natural Disaster →Manager should establish disaster recovery plan

How it impact on a business Influence life-threatening information storage of IS interruption of transmission and use

Natural Disaster Response Process Prevention Task Data backup Emergency Response Evaluate the damage’s degree Ensure the smooth contingency process

Natural Disaster Response Process (conj) Disaster recovery Establish disaster recovery plan (DRP) Recover the system Contingency rehearse Use Disaster Recovery Service Backup contingency response

Natural Disaster recovery plans strategy 1. acceleration solving problem Circulating and speedy Information of problem Find the point of problem and solution 2. automatic recovery procedure Reduce the down time Reduce human mistake

Natural Disaster recovery plans strategy (conj) 3. Disaster recovery plan testing Regular rehearse Ensure the availability of recover tool and system 4. the value of play back-up data center Reconfiguration and distribute resources

Natural Disaster recovery plans strategy (conj) 5. In the virtual environment to achieve high availability and disaster recovery Reduce the hardware cost

Example Cathaylife https: //www. cathaylife. com. tw/bc/B 2 CStatic/index. html After viewing the enterprise’s consequence in many critical disaster, Cathaylife hope that in every situations, Insurance company can operate in the smooth operation anytime and anywhere , and at the most critical time to help customers, Cathaylife want to find a Institution to avoid the damage.

The Solutions Solution Use IBM e-Center Information Protection Service Ø Speedy data backup and store Managed Resiliency Services Ø Overseas data center Disaster Recovery Services ØProvide rehearse

The Solutions Solution (conj) Regular rehearse Rehearse 2~4 times in a year Update and adjust data Review , update and adjust the backup-data item of e-center to conform the Enterprise’s demand growth

Internal threats 951617 黃啟泰

Definition of internal threats—data misuse and abuse from employees, partners, customers and other users with network authorization.

How it impact on a business Ø Overlooking: the internal staff overlook the security policy. They may lack practical guidelines on the security operations and information systems. Ø Carelessness: the internal staff may notice the security policies, but they don’t know that sometimes their behaviors or actions may lead to bad results. Ø Disregarding the existence of security policies: Sometimes insiders use the way they know to breach the security policy, making their daily work become more easily. Ø Malicious employees: who have some grudge against the company (for being laid off or fired) and have malicious intentions in damaging the company or cause any loss.

Example In July of 2008, a disgruntled network administrator named Terry Childs allegedly hijacked the San Francisco government's new Fiber WAN (wide-area network), effectively locking out the city's remaining IT administrators. By most reports, over 60 percent of the city's traffic travels over this network, and while it was still operational at the time of Childs' arrest, the ability to keep the network functioning was teetering on the edge of a razor. At any point, Childs could potentially have brought the network to its knees.

Example Details on the methods Childs allegedly used and what, precisely, was modified on the network are still surfacing. However, it appears that Childs may have issued a slew of password changes to the routers and switches, and removed access permissions for all remaining employees of the San Francisco Department of Telecommunications and Information Systems, where he worked, leaving him alone with the proverbial keys to the kingdom.

The Solutions Set up an intrusion detection system (IDS): In the San Francisco case, an IDS could have detected the massive number of admin password changes and issued an alert about the suspicious behavior. Keep in mind that a mutinous attack will, by definition, start from inside the network, so concentrating all of your firepower on outside threats will leave you vulnerable. Invest in strong security systems: The key to strong security is building out and defending layers in your network, and constantly monitoring for suspicious behavior. Firewalls should be used to protect against outside threats; they can also be used to secure layers within your network.

The Solutions Strict separation of roles and duties If you can afford more than a couple of IT admins, split duties evenly between them, and don't give any particular person or group full access and permissions to the entire network. This ensures that no single person has the ability to take the whole system down. Encrypt the data: All sensitive data should be encrypted, even if your database servers are sufficiently locked down or application communication is only internal, restricted to the network.

Unauthorized use of computer system and networks (Internal threat) 961735 劉于瑄

What is Unauthorized use of computer system and networks Called time and resource theft Unauthorized use of company-owned computer networks by employees Range from private consulting、personal finances 、playing video games to Unauthorized use of the Internet on company networks.

EXAMPLE Xerox Corporation fired 40 people in October 1999 - in violation of corporate policy. Employees Unauthorized use pornography sites on the web. Unauthorized use online gambling, stock or download pornography.

What are threats possibly faced by a business in using any IS/IT? Access to inappropriate sites, viruses will caused the company shut down the system operation. Organization's security vulnerabilities. Confidential information may have theft.

How it impact on a business? Took so much network bandwidth that it choked the company network. Prevented co-workers from sending or receiving e-mail.

Solutions Lock the dangerous sites and prevent viruses from infecting. Use Network monitoring software.

Network monitoring software Called sniffers. Covertly search individual packets of data as they pass through the Internet. Capturing passwords or the entire contents. Block access to unauthorized websites.

How applying the solution Use sniffers to monitor the use of the Internet by employees at work. Use sniffers to monitor network traffic to evaluate network capacity, as well as reveal evidence of improper use.

Network monitoring software

PHISHING 961655 嚴勻希

THE IMPORTANCE OF” Assuring reliable and secure IS/IT product/service” (I) No matter how you measure cyber security threats, risks are increasing at an alarming rate. Consider the recent evidence of this growing problem: Online crime has increased nearly 600% in 2009 $1 trillion in intellectual property was lost in 2008 280 million records stolen in 2008 Unauthorized intrusions cost more than $70 k a year per breached company Cyber attacks increased 40% in 2008

THE IMPORTANCE OF” Assuring reliable and secure IS/IT product/service” (II) Malicious code threats increased by 165% from 2007 to 2008. This trend is continuing in 2009 There is 1 new infected webpage every 4. 5 seconds 86% of all computers are missing critical security patches , have outof-date anti-virus software, or have disabled firewalls. The average company encounters virus infections at a monthly rate of 1 for every 5 networked machines

THE THREATS POSSIBLY FACED BY A BUSINESS IN USING IS/IT Specialists in the field of information security distinguish two types of potential threats: External : such as worms, Trojan viruses, spy-programs, phishing, etc. Internal: Any company‘s security system is threatened from outside, and there becomes internal threats of information disclosure that make companies most vulnerable.

WHAT IS “ PHISING”? DEFINITION: Phishing is an illegal activity using social engineering technique to steal personal identity data and financial account information. ( A bad guy who set up a phishing scam is called a phisher. ) TARGET: Such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication.

What are threats possibly faced by a business in using any IS/IT? The damage caused by phishing is mainly substantial financial loss, especially in the USA and Europe. It is estimated that 45. 7 million pounds was stolen from UK online bank accounts in 2006. Figure is about Phishing Target

TYPE OF PHISHING (I) (1) Link manipulation Most methods of phishing use some form of technical deception designed to make a link in an e-mail (and the spoofed website it leads to) appear to belong to the spoofed organization. (2) Filter evasion Phishers have used images instead of text to make it harder for anti-phishing filters to detect text commonly used in phishing emails

TYPE OF PHISHING (II) (3) Website forgery Some phishing scams use Java. Script commands in order to alter the address bar. (example : XSS- Cross-site scripting )

Cross-site scripting (XSS) XSS is another popular method of phishing Website Forgery Example

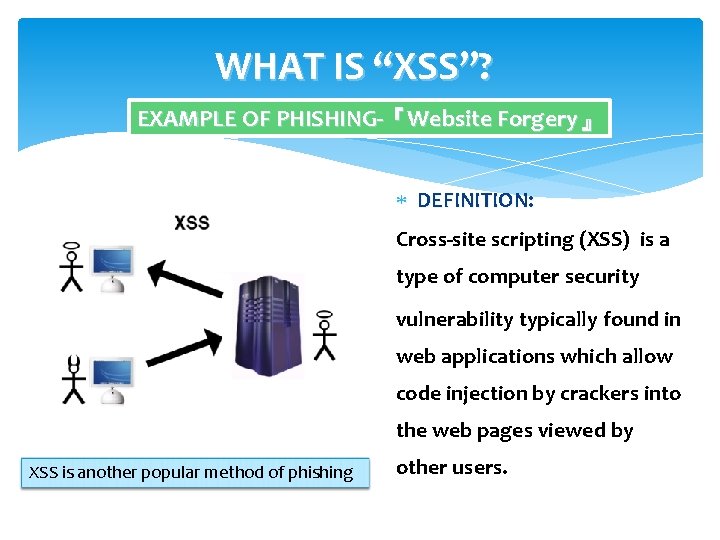
WHAT IS “XSS”? EXAMPLE OF PHISHING-『Website Forgery』 DEFINITION: Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow code injection by crackers into the web pages viewed by XSS is another popular method of phishing other users.

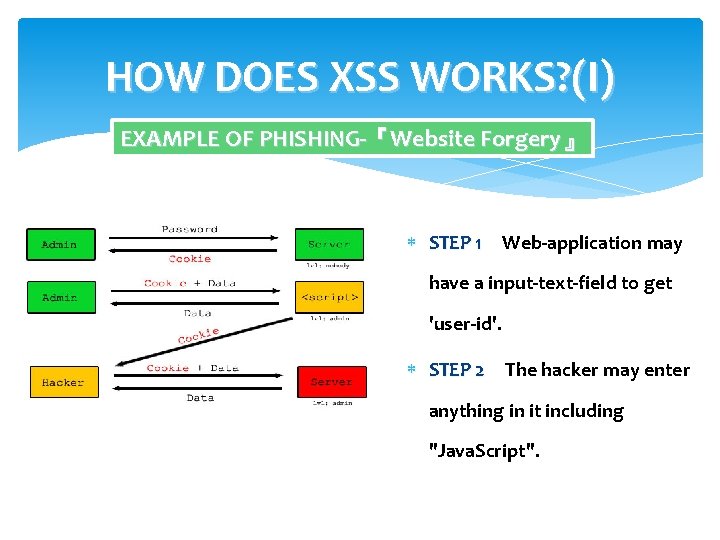
HOW DOES XSS WORKS? (I) EXAMPLE OF PHISHING-『Website Forgery』 STEP 1 Web-application may STEP 1 have a input-text-field to get 'user-id'. STEP 2 The hacker may enter STEP 2 anything in it including "Java. Script".

HOW DOES XSS WORKS? (II) EXAMPLE OF PHISHING-『Website Forgery』 STEP 3 If the hacker enters Java. Script (a malicious code), the STEP 3 server may process it, and then return it. STEP 4 In this case, user-id is not authenticated and it is sent as STEP 4 it is on the error page. STEP 5 If the user's input data is returned as it is, the java-script code may execute. And, hacker wins!!

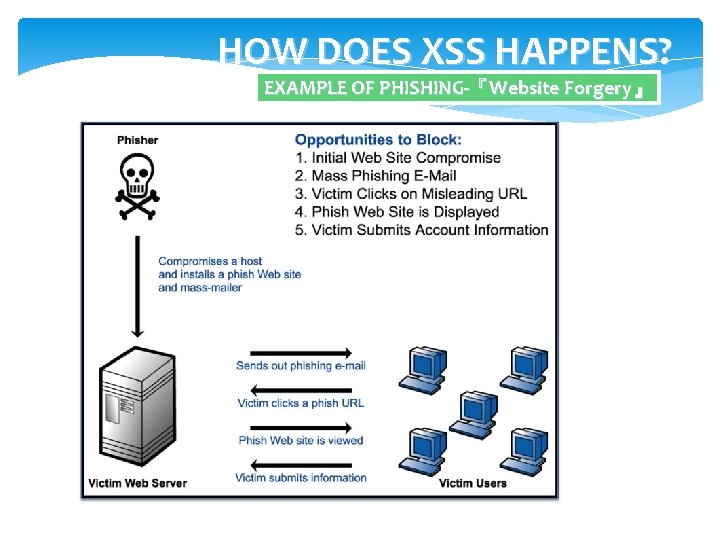
HOW DOES XSS HAPPENS? EXAMPLE OF PHISHING-『Website Forgery』

HOW TO AVOID XSS HOLES? (I) SOLUTION FOR COMMON WEBSITE For sites where the input is meant to be plain text, the fix is simple - Change everything as it is output as HTML (using an “escaping mechanism “ appropriate to where it is. ) FOR EXAMPLE-Changing the HTML & JAVASCRIPT as following: • Text in HTML and HTML attributes: change & to & ; change< to < ; change> to > ; change " to " ; change‘ to ' • Text in Java. Script strings: change to \ ; change / to / ; change ‘ to ' ; change " to ”

HOW TO AVOID XSS HOLES? (II) SOLUTION FOR THE SITES ALLOW USERS TO INPUT JAVASCRIPT For sites where users are allowed to use and provide input in HTML , the goal is not to transform the HTML input into “escaping mechanism”. But – To restrict what HTML features can be used. (The level of restriction depends on the site. ) FOR EXAMPLE: FOR EXAMPLE • A forum will probably limit users to P, BLOCKQUOTE, lists, simple inline styles, and perhaps images.

PROMINENT SITES AFFECTED BY XSS EXAMPLE OF PHISHING-『Website Forgery』 XSS vulnerabilities have been reported and exploited since the 1990 s. Some prominent sites that have been affected in the past: • The email services • The social networking sites- and , and • The online dictionary • Search engine • The online payment system - EXAMPLE FOR NEXT PAGE

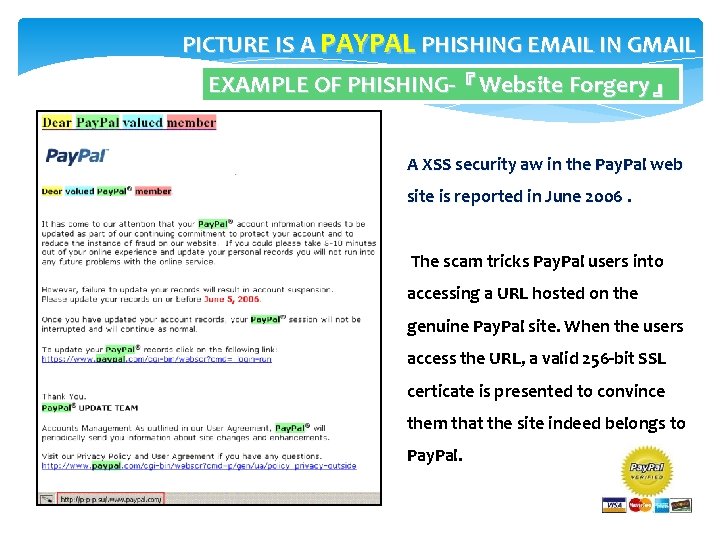
PICTURE IS A PAYPAL PHISHING EMAIL IN GMAIL EXAMPLE OF PHISHING-『Website Forgery』 A XSS security aw in the Pay. Pal web site is reported in June 2006. The scam tricks Pay. Pal users into accessing a URL hosted on the genuine Pay. Pal site. When the users access the URL, a valid 256 -bit SSL certicate is presented to convince them that the site indeed belongs to Pay. Pal.

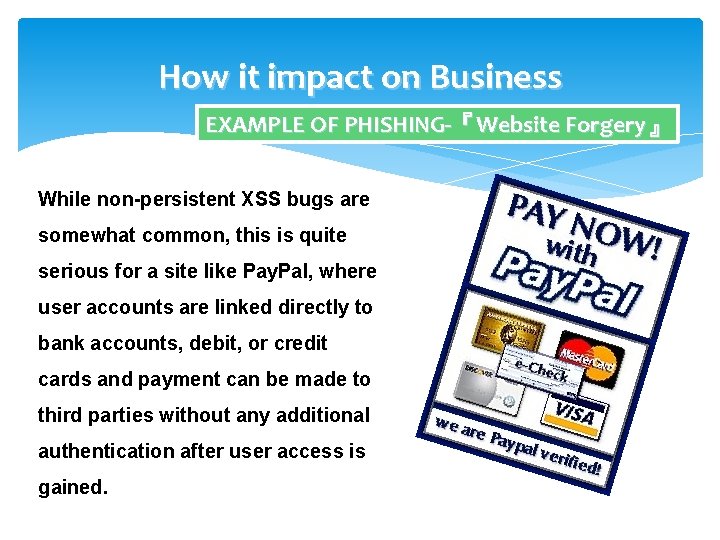
How it impact on Business EXAMPLE OF PHISHING-『Website Forgery』 While non-persistent XSS bugs are somewhat common, this is quite serious for a site like Pay. Pal, where user accounts are linked directly to bank accounts, debit, or credit cards and payment can be made to third parties without any additional authentication after user access is gained.

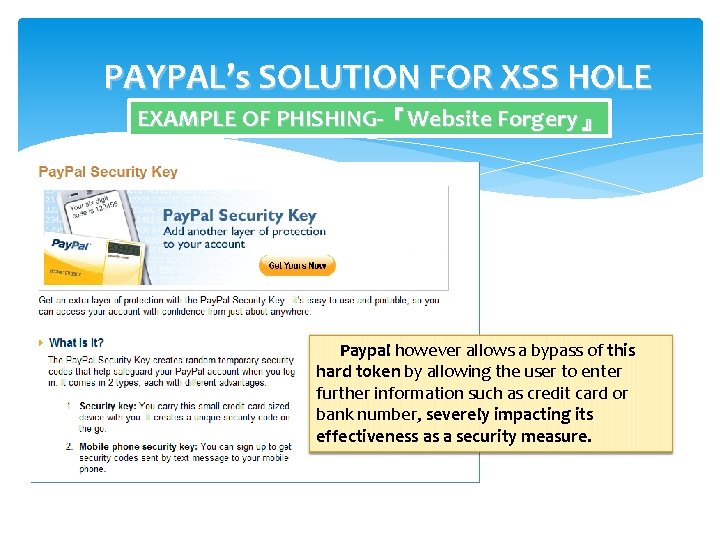
PAYPAL’s SOLUTION FOR XSS HOLE EXAMPLE OF PHISHING-『Website Forgery』 Paypal however allows a bypass of this hard token by allowing the user to enter further information such as credit card or bank number, severely impacting its effectiveness as a security measure.

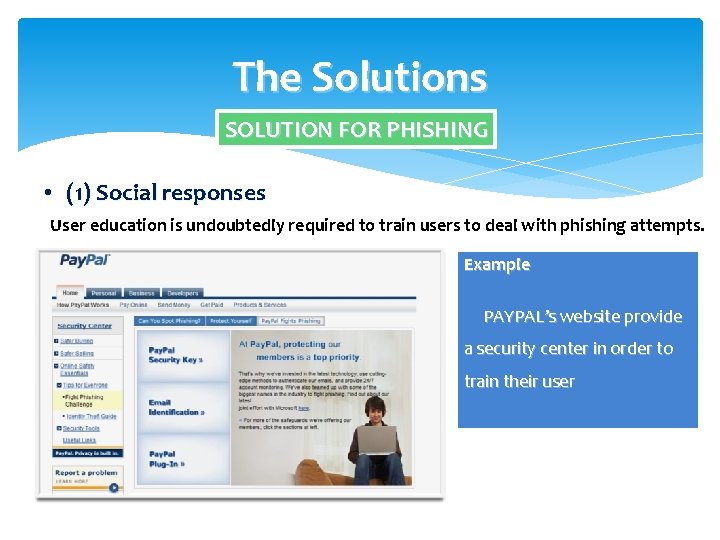
The Solutions SOLUTION FOR PHISHING • (1) Social responses User education is undoubtedly required to train users to deal with phishing attempts. . Example PAYPAL’s website provide a security center in order to train their user

The Solutions SOLUTION FOR PHISHING • (2) Technical Response Besides social response, many anti-phishing software available to identify phishing contents on websites. • (3) Legal Response On January 26, 2004, the RST lawsuit was led in U. S. against a suspected phisher. Other countries have followed the lead of the U. S. by tracing and arresting phishers.

The Future of Phishing • Phishing techniques could become obsolete : The APWG has suggested that conventional phishing techniques could become obsolete in the future as people are increasingly aware of the social engineering techniques used by phishers. • Become a common tool for stealing information: They propose that pharming and other uses of malware will become more common tools for stealing information.

Mobile Malware 961739 張天毓

Mobile Malware It designed to attack mobile devices. The objective was to create a malicious program for mobile devices. It attempts to send itself to other mobile devices.

The Object of Attack Mobile users with laptops Personal digital assistants(PDAs) Cell phones(Smartphone) Other mobile devices.

How it impact on business Remote control of a device Modify critical system files Damage existing applications (including anti-virus programs ) Block MMC memory card (Multi. Media. Card)

How it impact on business Internet downloads Bluetooth wireless connection Multimedia Messaging Service

The Threat Areas Text messages Contacts Video Phone transcription Call history Documentation Buffer overflows

Text messages Steal your private information and wreak havoc on your life and finances. Create an avenue for intercepting corporate data.

Contacts Steal a contact list and send out short messages containing malware or a link to malware. Packaged contact information and sent it to a malicious third-party.

Phone transcription It send the recorded file to an attacker via email or via the Multimedia Message Service (similar to SMS). It could use SMS to activate the recording function, turning a mobile into a tape recorder that could be turned on and off remotely.

Decrease Chances of Installing a Virus Turn off Bluetooth discoverable mode. Check security updates to learn about filenames you should keep an eye out for. Install some type of security software on your phone. Install a "security patch".

The Solutions Nokia's S 60 have already been victimized by Cabir worm. Solution Symantec Mobile Security 4. 0 Live. Update Wirless

Reference http: //www. mcafee. com/us/local_content/white_pap ers/threat_center/wp__malware_r 2_en. pdf http: //www. precisesecurity. com/mobilephone/symantec-mobile-security-40 -for-symbian/ http: //www. mobiletopsoft. com/board/2187/smartpho ne-and-pda-mobile-malware-threats-andprevention. html http: //tw. page. bid. yahoo. com/tw/auction/d 45730459? u=a 0938656552

Software Piracy 961728黃哲彥

Software Piracy • This increases the risk of corruption in consumer's computers by defective software and infected with viruses. • Prevents consumers from enjoying the full benefits of the software package • Unable to take advantage of technical support and product upgrades

P 2 P application Node to node communication through distributed computing or storage Speed up the information transmission Increase the security of information

How it impact on business Affect network bandwidth. Place malware on the P 2 P software. Hackers use the leak when the user use the P 2 P software : Foxy, Bit Comet, ez. Peer

Example The largest number of people using peer to peer sharing software "FOXY“. Many Record company and movie company combine to lay an accusation against the designer of “FOXY”. Because the music and movies sharing on the P 2 P software violate their copyright

The Solutions Installs firewall impediment file sharing Let the IP address will transmit this kind of junk mail to list as the blacklist Shorten the exposure time on the Internet Provide agreements for P 2 P software user to agree on

Free software Free software, generally meaning what refers to is entrusts with the user to study, the revision, the Reproduce, the dispersion and so on free right software

How it impact on business Infect virus by the free software Infringement lawsuit Impact goodwill, reduced investor confidence

Example Asus product “Eee. PC” use of Linux operating system accused by licensing issues Canada i 4 i company in March 2007 against Microsoft’s word violate the patent. Because Microsoft use the unauthorized specific XML function.

The Solutions • Download any software tool, from original official (Official) Web site, not from the portal or forum website • Prove that did not use free software, or to provide the use of free software list and Authorization

Control the program use Software Asset Management Use those function can help speedy solving the problem of Information security

Adware and Spyware 961745陳錚

Spyware is a type of malware that is installed on computers and collects little bits of information at a time about users without their knowledge.

How it impact on business performance of company’s computer: excessive error messages pop-ups browser crashing poor computer performance causes difficulty connecting to the Internet increased CPU usage badly infected systems resort to contacting technical support experts, or even buying a new computer because the existing system "has become too slow". It will cost a lot of money. It can transmit " chat sessions , user names , passwords , bank information, etc. " that companey confidential information might leak

Examples My. Web. Search (of Fun Web Products) has a plugin that displays a search toolbar near the top of a browser window, and it spies to report user search-habits. Zlob trojan , downloads itself to a computer via an Active. X codec and reports information back to Control Server. Some information can be the search-history, the Websites visited, and even keystrokes.

The Solutions install a web browser other than IE, such as Opera , Google Chrome or Mozilla Firefox. use network firewalls and web proxies to block access to Web sites known to install spyware. install a large hosts file which prevents the user's computer from connecting to known spyware-related web addresses.

Adware Is any software package which automatically plays, displays, or downloads advertisements to a computer after the software is installed on it or while the application is being used.

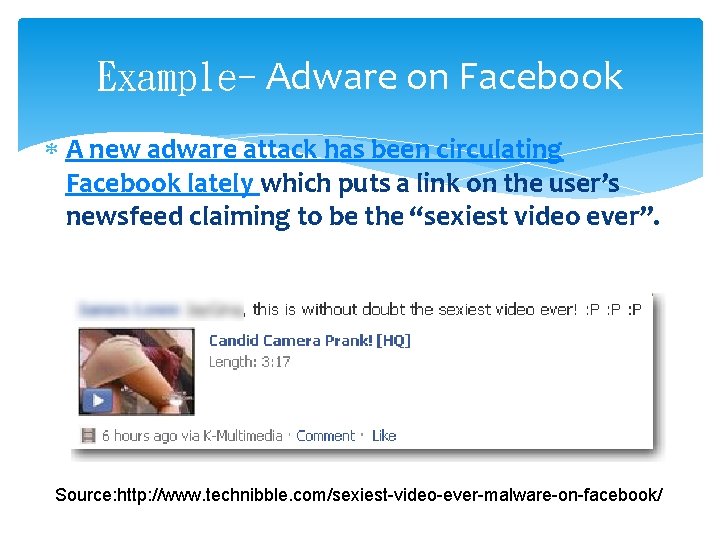
Example- Adware on Facebook A new adware attack has been circulating Facebook lately which puts a link on the user’s newsfeed claiming to be the “sexiest video ever”. Source: http: //www. technibble. com/sexiest-video-ever-malware-on-facebook/

Adware on Facebook(2) Clicking on the supposed video brought users to a Facebook application, which subsequently prompted them to download an updated media player to view the video The download actually was a payload for an adware program called Hotbar

Adware on Facebook(propose of adware creator) Creator can collects user’s information and advertise their products and it makes money

How it impact on business It displays advertisements in a user's browser based on web browsing habits It will pop up adverts when you use Internet Explorer and Windows Explorer It will start collecting user data

The Solutions Facebook promptly disabled the application and since has been deleting all posts related to the scam “We're advising people not to click on strange links, even when posted by friends, and to be cautious when using applications. ”

If you were one of them that got attacked scan your computer with an up-to-date antivirus change your passwords review your Facebook application settings learn not to be so quick as to fall for a simple social engineering trick like this in future

Other Examples 180 Search. Assistant is an adware program that displays pop-ups based on a user's browsing habits Zango , was a software company that provided users access to its partners' videos, games, tools and utilities in exchange for viewing targeted advertising placed on their computers.

Avoiding Adware Be very careful before downloading and installing any programs from the internet. Avoid going to sites that may have questionable reputation, especially sites with an excessive amount of advertising popups. You may consider changing your internet browser settings so some software from websites is not run automatically.

Physical Security : The Often Neglected Information Security 961616 鄭閔文

What is Physical Security ? Protection of personnel, hardware, programs, networks, and data from physical circumstances and events that could cause serious losses or damage to an enterprise, agency, or institution. This includes protection from fire, natural disasters, burglary, theft, vandalism, and terrorism.

Importance of Physical Security is a first line of defense for any device or system. Without physical security, no other security measures can be considered effective.

What are threats possibly faced by a business External Internal Personal

What are threats possibly faced by a business External :Refers to the natural threat from outside, such as typhoon, flood, fire, lightning and earthquake. Natural Disasters

What are threats possibly faced by a business Internal : The extinguishment of internal physical facilities , such as air conditioning system, waterpower system, and electric power system. . . etc.

What are threats possibly faced by a business Personal- Intentionally : such as theft, vandalism, intrusion System. Unintentionally : Such as kicking the power off accidentally, knocking over drinks in the room and piling up debris. . . etc.

Examples Stolen Boeing laptop puts employee information in jeopardy • Boeing, suffered three break-ins between November 2005 and December 2006, culminating with theft of a laptop from an employee’s car.

Examples Facing problem : The laptop contained the names, salary information, Social Security Numbers, home addresses, phone numbers, and dates of birth of 382, 000 current and former employees -The disclosure of personally identifiable information is because data unencrypted and physical security hole.

The Solution(I) Security Cables : These special cables can be one of the most cost-effective ways to secure laptops and computer towers from theft or loss. It very hard for the thief to just grab the computer or data storage device and take off with it.

The Solution(II) Locks : A tower can be completely locked and the keyboards locked away when not in use. Hardware keyloggers can and have been be used in corporate espionage situations to steal the keystrokes made by a victim. By locking your computer away somewhere safe, you protect yourself from this threat.

The Solution(III) Alarms , sensors : get smaller alarm set ups that protect computers from being moved or stolen. These smaller alarms are perfect for an office situation — especially when someone can't keep an eye on all the computers at once (during a lunch break for instance).

The Solution(IV) Camera Monitoring Systems : computer user can install a set of cameras around their office or residence and use the internet to keep an eye on what’s going on.

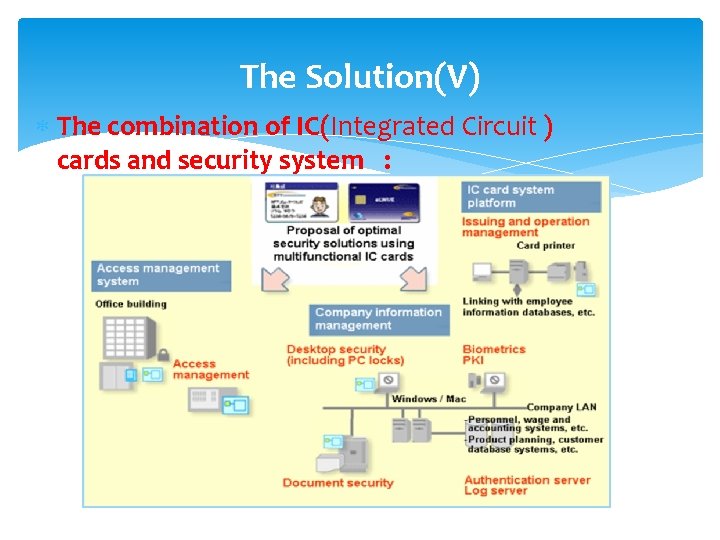
The Solution(V) The combination of IC(Integrated Circuit ) cards and security system :

How applying the solution Coast Guard Administration - Requirements (I) Establish a combination of physical and information security protection. (II) Intergrate various systems into an environment which takes single electronic certificate as foundation

How applying the solution Solution- Using an intergrated IC card system which combine the entrance guard and personal identification. Effect- (I) Reduce user’s confusion (II)Reduce the user’s burden of working and managing the passwords in the past. (III)Let entrance guard control more convenient

Conclusion In Conclusion Physical security is an essential aspect of information security. It does not matter how strong your firewall is or how up-to -date your antivirus software is — if your computer is not physically secured, the data is not protected. Although building an perfect physical security might cost a fortune , but it’s worthy!

Hacking and Cracking (External threat) 961740 趙世瑄

What is Hacking is the obsessive use of computers or the unauthorized access and use of network computer systems. Hackers can be ousiders or company employees who use the Internet and other networks to steal or damage data and programs.

What are threats possibly faced by a business monitor e-mail Web server access files transfers to extract passwords steal network files plant data that will cause a system to welcome intruders use remote services that allow one computer on a network to excute programs on another computer to gain privilsged access within a network.

How hacking impact on a business The website will be destroyed Internet service suspended, page replacement Disputing about e-commerce transaction Damage to company reputation Data leakage

The Solutions Data encryption, Digital signature Password Management Security code Access control Intruder detection Vulnerability identification Update software at any time Shut off unnecessary prot and service

Example - i. Pad hacking incident The hacking incident in which netted the email address of an estimated 114, 000 of AT&T Inc. ’s customers who use Apple Inc. ’s ipad. A group calling itself Goatse Security was able to exploit script on an AT&T website to get the e-mail address.

i. Pad hacking incident(weakness) AT&T’s website had a function that was designed to be able to provide e-mail address as long as people input their user name and ID number. Because of this vulnerability, hackers send a i. Pad SIM card number through a HTTP request, making AT&T website miscarriage of justice exposed the user’s e-mail.

i. Pad hacking incident(motivation of hakers) Goatse Security wanted to prove that AT&T’s website had a lot of vulnerabilities Prove their own capability Wants to be famous by this incident

How it impact on business Data leakage Started a panic Makeing people doubt the safety of AT&T’s website Damage to company reputation

The Solutions Password Management Intruder detection Vulnerability identification Update website at any time Shut off unnecessary port and service

How applying the solution The company held a conference on their information security negligence Decided to turn off the feature that provided the e-mail address right away So the problem had been fixed on that day and there is no exposure of any e-mail address.

Reference ZDNet, http: //www. zdnet. com Business Weekly, http: //www. bizjournals. com Wikipedia, http: //www. wikipedia. org

Espionage 951751 李洹宇

What is “Espionage” A spy is a person employed to obtain business secrets directly or indirectly. They might invade system or break company’s computer.

Espionage in business Espionage is usually part of an institutional effort, and the term is most readily associated with state spying on potential or actual enemies, primarily for military purposes, but this has been extended to spying involving corporations , known specifically as business espionage

How it impact on a business üCanada is losing $12 billion a year due to industrial espionage. üGerman companies were losing $87 billion and 30, 000 jobs to industrial espionage every year

Example: China bugs and burgles Britain THE TIMES in Britain : China bugs and burgles Britain http: //www. thesundaytimes. co. uk/sto/news/uk_news/article 196465. ece

Example: China bugs and burgles Britain The security service MI 5 has accused China of bugging and burgling UK business executives and setting up "honeytraps" in a bid to blackmail them into betraying sensitive commercial secrets.

Example: China bugs and burgles Britain During conferences or visits to Chinese companies you may be given gifts such as USB devices or cameras. There have been cases where these 'gifts' have contained Trojan devices and other types of malware

Example: China bugs and burgles Britain Chinese intelligence services have also been known to exploit vulnerabilities such as sexual relationships and illegal activities to pressurise individuals to cooperate with them

The Solutions • Security Classification ü Describing the different classification labels, Defining the criteria for information to be assigned a particular label, and listing the required security controls for each classification. as: Public, Sensitive, Private, Confidential. • Access Control ü Access to protected information must be restricted to people who are authorized to access the information.

The Solutions Monitoring & Controlling ü Monitoring and controlling the user and recording when system be used Security Intranet ü It also need internal security to protect secret information or chain reaction of crash