Information Classification Codes http wwwin cisco cominfosecpoliciesinfoclass shtml











- Slides: 20

Information Classification Codes http: //wwwin. cisco. com/infosec/policies/info_class. shtml Classification and Marking Cisco Public Cisco Confidential Session Number Presentation_ID Description Information that has been released to the public by a Cisco director or delegate, and can freely be given to anyone without any possible damage to Cisco Represents most information created or used within Cisco including most documents and email. Any document not otherwise designated is assumed to be Cisco Confidential, but authors are encouraged to actively designate this classification. Any Cisco-badged personnel with a business need can create and gain access to Cisco Confidential information. Cisco Highly Confidential – Controlled Access Includes more sensitive information that should be kept from the majority of Cisco-badged personnel. This includes security, personnel, financial and other particularly sensitive information. Most Cisco personnel are able to create Cisco Highly Confidential information and are then responsible for controlling its distribution. Cisco Restricted – Redistribution Prohibited Information is the most sensitive information to Cisco. It is generally only available to a very limited number of Ciscobadged personnel and has the strongest protections on its storage and distribution. This includes mergers and acquisition information, global financial information, investigations and similar information. © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 1

Data Security: Problems & Approaches Richard Puckett Infrastructure Security Architect November 2, 2006 Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 2

Data Security Problem Overview Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 3

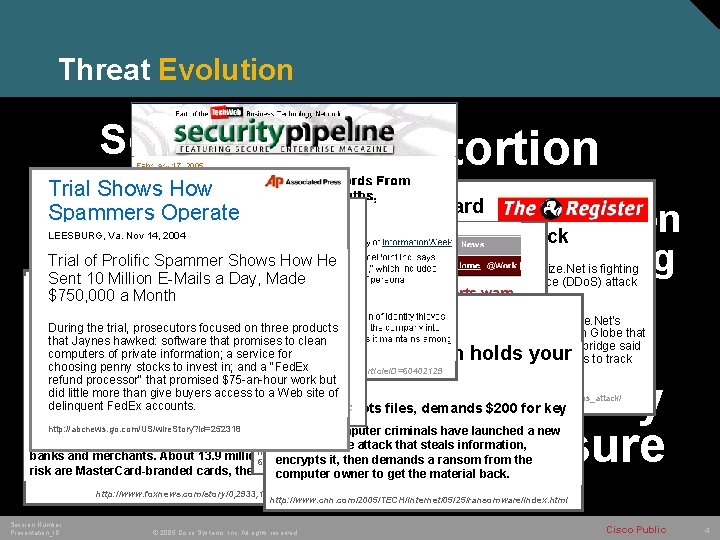
Threat Evolution Scams Extortion Trial Shows How Theft of US credit card. Information Spammers Operate firm fights DDo. S attack Customer Data Harvesting Security Breach May Put 40 Million Organized Credit Card Holders at Risk Fraud Crime New computer scam holds your LEESBURG, Va. Nov 14, 2004 Trial of Prolific Spammer Shows How He US credit card processing firm Authorize. Net is fighting Sent 10 Million E-Mails a Day, Made a sustained distributed denial of service (DDo. S) attack Viruses have teamed up, experts warn that has left it struggling to stay online. $750, 000 a Month By JACK KAPICA Globe and Mail Update. Glen Zimmerman, a spokesman for Authorize. Net's Saturday, June 18, 2005 During the trial, prosecutors focused on three products Friday, June 03, 2005 parent company, Lightbridge, told the Boston Globe that Jaynes hawked: software that promises to clean Three different viruses have been posing an increasing threat the attacks followed an extortion letter. Lightbridge said A security breach of customer information at a credit cardcomputers of private information; a service for because they work together in what security experts are it was working with law enforcements officials to track choosing penny stocks to invest in; and a "Fed. Ex processing company has exposed as many as 40 milliondown the attackers. calling a co-ordinated malware attack. http: //www. securitypipeline. com/show. Article. jhtml? article. ID=60402129 refund processor" that promised $75 -an-hour work but cardholders of all brands to potential fraud, Master. Card The attack involves three Trojans — Win 32. Glieder, did little more than give buyers access to a Web site of Win 32. Fantibag and Win 32. Mitglieder — which are displaying International Inc. (search) said Friday. http: //www. theregister. co. uk/2004/09/23/authorize_ddos_attack/ delinquent Fed. Ex accounts. signs of co-ordination as they spread and infect computer http: //abcnews. go. com/Technology/wire. Story? id=892609&CMP=OTC 'Trojan' encrypts files, demands $200 for key The credit card giant said its security division detected multiple systems. They combine different components in waves to -RSSFeeds 0312 instances of fraud that tracked back to Solutionscriminals have launched a new http: //abcnews. go. com/US/wire. Story? id=252318 Card. Systems compromise large numbers of PCs. (CNN) -- Computer Inc. (search) of Tucson, Ariz. , which processes for that steals information, typetransactions of online attack http: //www. theglobeandmail. com/servlet/story/RTGAM. 20050 banks and merchants. About 13. 9 million 603. gtvirusjun 3 ofencrypts those credit cards at it, then demands a ransom from the risk are Master. Card-branded cards, the company said computer owner to get the material back. info for ransom Corporate Espionage Blackmail Mandatory Disclosure http: //www. foxnews. com/story/0, 2933, 159943, 00. html http: //www. cnn. com/2005/TECH/internet/05/25/ransomware/index. html Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 4

Recent Statistics Additionally… According to a 2004 E-Crime Watch Survey: * • 70% of enterprises surveyed reported at least 1 e-crime or intrusion • Theftin of 2003 proprietary information causes greatest $2. 7 M per incident (2003) year • 43% financial reported loss: an increase over the previous • Ninety percent of respondents detected computer • 56% security reportedbreaches operational losses within last 12 months • 25% reported financial losses / FBIlosses Securitydue Study • 32% Source: do not. CSI track to 2003 e-crimes or intrusions • 41% do not have a formal plan for reporting and responding to e -crimes “Many companies still seem unwilling to report e-crime for fear of damaging their reputation” Survey by: CSO Magazine, the US Secret Service & the CERT Coordination Center Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 5

How our Data is at Risk Three Threats: Disruption, Loss, and Damage Disruption affects Productivity (The CIO Problem) 1. 2. 3. External source (e. g. DDo. S, Interrupted Data in-Motion) Internal source (e. g. virus breakout, Data Loss) Accidental source (e. g. Configuration Mistake = Exposure) Loss affects Value (The CFO Problem) 1. 2. 3. Random theft (e. g. uncoordinated break-in) Directed theft (e. g. espionage) Accidental loss (e. g. presentation left behind, picked up) Damage affects Reputation (The CEO Problem) 1. 2. 3. Session Number Presentation_ID Internet visage (e. g. web site defacement) Customer & shareholder confidence (loss of information) Accidental damage (e. g. making a misstep in industry) © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 6

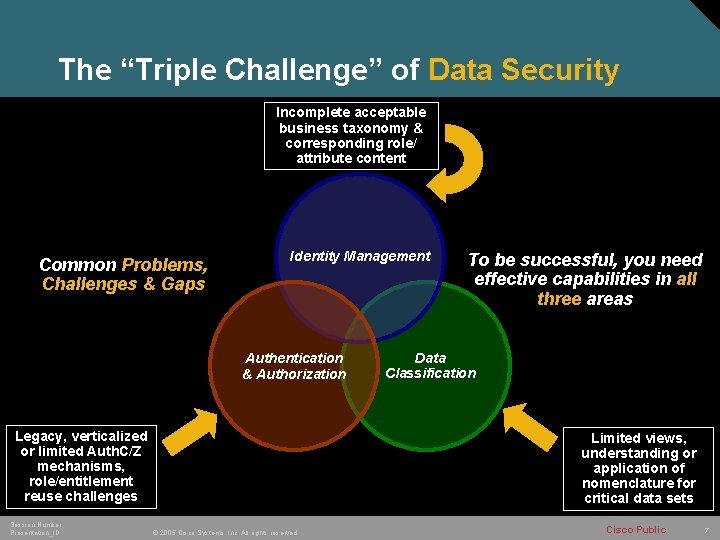
The “Triple Challenge” of Data Security Incomplete acceptable business taxonomy & corresponding role/ attribute content Common Problems, Challenges & Gaps Identity Management Authentication & Authorization Legacy, verticalized or limited Auth. C/Z mechanisms, role/entitlement reuse challenges Session Number Presentation_ID To be successful, you need effective capabilities in all three areas Data Classification Limited views, understanding or application of nomenclature for critical data sets © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 7

Data Security in Ecosystems “Core, convergent architectures have a substantial impact on Data Security models in both direct and abstract ways” Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 8

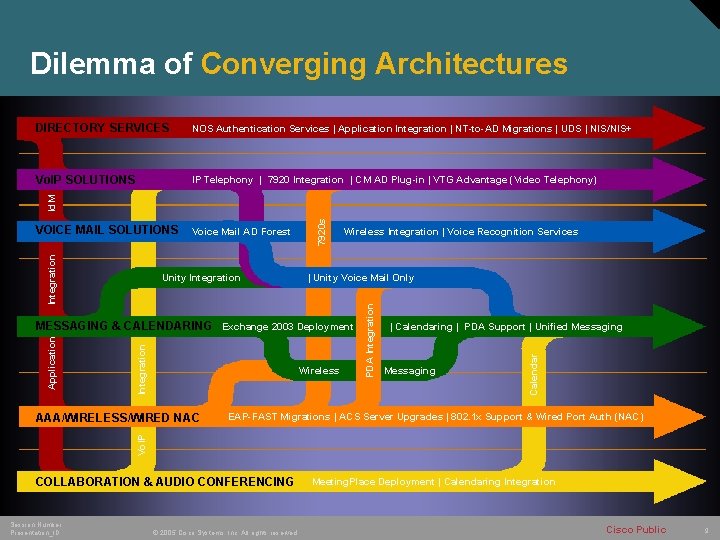
Dilemma of Converging Architectures NOS Authentication Services | Application Integration | NT-to-AD Migrations | UDS | NIS/NIS+ Vo. IP SOLUTIONS IP Telephony | 7920 Integration | CM AD Plug-in | VTG Advantage (Video Telephony) Voice Mail AD Forest | Unity Voice Mail Only Integration Application MESSAGING & CALENDARING Exchange 2003 Deployment Wireless Messaging EAP-FAST Migrations | ACS Server Upgrades | 802. 1 x Support & Wired Port Auth (NAC) Vo. IP AAA/WIRELESS/WIRED NAC | Calendaring | PDA Support | Unified Messaging Calendar Unity Integration Wireless Integration | Voice Recognition Services PDA Integration VOICE MAIL SOLUTIONS 7920 s Id. M DIRECTORY SERVICES COLLABORATION & AUDIO CONFERENCING Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Meeting. Place Deployment | Calendaring Integration Cisco Public 9

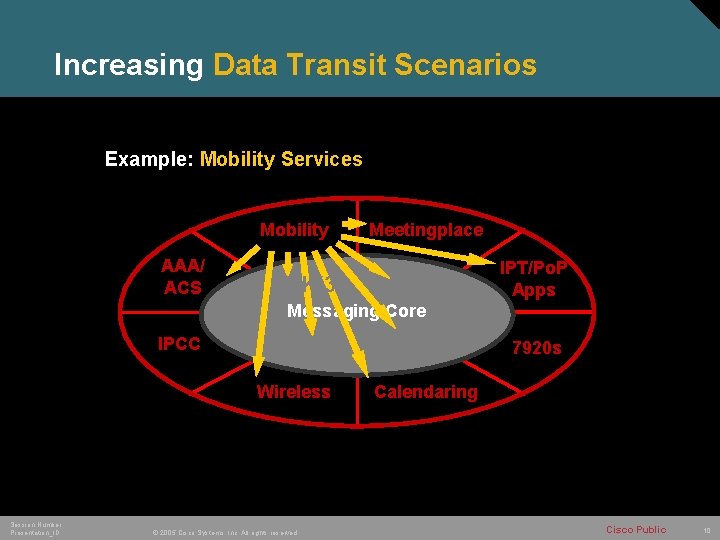
Increasing Data Transit Scenarios Example: Mobility Services Mobility AAA/ ACS E 2 K(3) Meetingplace AD IPT/Po. P Apps Messaging Core IPCC CM Wireless Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. UNITY 7920 s Calendaring Cisco Public 10

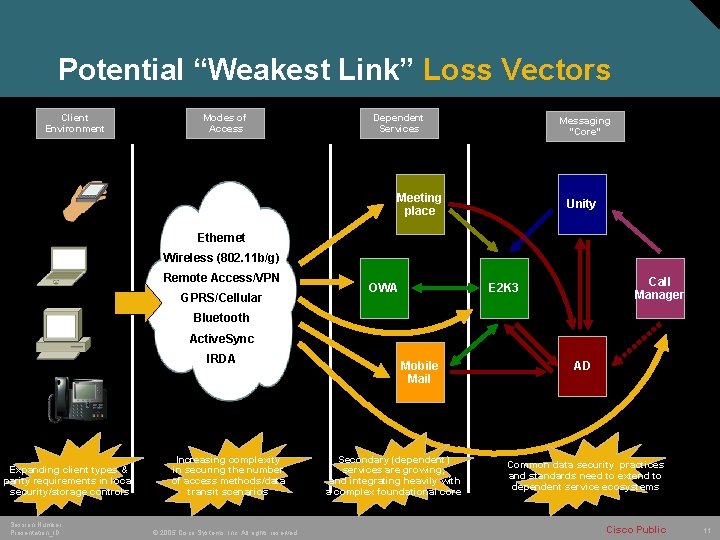
Potential “Weakest Link” Loss Vectors Client Environment Modes of Access Dependent Services Messaging “Core” Meeting place Unity Ethernet Wireless (802. 11 b/g) Remote Access/VPN GPRS/Cellular OWA Call Manager E 2 K 3 Bluetooth Active. Sync IRDA Expanding client types & parity requirements in local security/storage controls Session Number Presentation_ID Increasing complexity in securing the number of access methods/data transit scenarios © 2005 Cisco Systems, Inc. All rights reserved. Mobile Mail Secondary (dependent) services are growing, and integrating heavily with a complex foundational core AD Common data security practices and standards need to extend to dependent service ecosystems Cisco Public 11

Data Security Solutions Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 12

“We cannot solve our problems with the same thinking we used when we created them” Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 13

Building a Data Security Foundation • Core Categories of Assets What types of Critical Assets exist in your world today and why are they important to you? Who are they important to? (things like Source Code, Customer Information, Employee Data) • Creation of Asset Criticality Levels Ascribe criticality levels to describe the importance of data in each category (Cisco Highly Confidential – Controlled Access, Cisco Restricted – Redistribution Prohibited, etc. ) • Asset Storage Locations (Data at-Rest) Where is data stored? Where do backups/resiliency copies live? How is it stored/protected? (Logical and Physical) Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 14

Building a Data Security Foundation (cont’d) • Asset Use Scenarios (Data in-Motion) Data use patterns, flows and dependencies. How is the data created? Used? Destroyed? Application/Service mapping? Who has access to the data and why? (Administratively, Consumers, etc. ) Create Usage scenarios – or “stories” – for each asset use pattern What audit, monitoring and transaction logging capabilities exist, especially between systems? How do these tie to alerting & response functions today? • Review of Policy, Standards & Specifications Do policies exist for the handling critical assets? Do you have policies governing specific critical asset classes? What standards exist (if any) around data management & security of your most critical assets? (good standards = good security) Do you have Design documentation requirements around data mapping? Do you publish best practices & training toolkits for securing, managing and accessing your most critical assets? Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 15

Building a Data Security Foundation (end) • Regulatory & Governance Requirements What regulatory or governance requirements exist for your most critical asset classes? (ITAR, HIPPA, etc. ) Do you have the appropriate level of controls? Regulatory control projects can be effective fulcrums for instituting improvements in data security models • Data Security Current State Analysis Do you review use scenarios for your most critical assets? (“milk carton” expiration dates on review) How often do you revisit security when designs change or when new user communities are added? • Data Security Awareness Campaigns What types of awareness, guidance or education campaigns are you providing to your workforce? Do you have regular guidance occurring to staff on the importance of data security vigilance? Don’t underestimate the value of awareness functions, as they are often pivotal in influencing behaviors when new exposure issues arise, as well as educating decision-makers to evolving risks Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 16

Parting Thoughts… • Data Security is not a single product or service on your network • Data Security must be ingrained in your architecture at all 7 layers • There are no ‘silver bullets’; defense-in-depth is required today • Technology is an enabler. People, process, and technology together achieve the best data security posture for an enterprise • Communicate criticality & accountability; model data security conscious behavior for your organizations • Threat evolution is dynamic, your data security strategies should follow suit (Technical Darwinism… adapt or perish) • “You can’t secure what you don’t manage, you can’t manage what you don’t measure, ergo, you can’t secure what you don’t measure” Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 17

Questions? Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 18

Contact Information Richard Puckett Infrastructure Security Architect Corporate Security Programs Organization Cisco Systems, Inc. (rpuckett@cisco. com) Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 19

Session Number Presentation_ID © 2005 Cisco Systems, Inc. All rights reserved. Cisco Public 20