Information Assurance IATF Information Assurance Technical Framework Security







- Slides: 46

Information Assurance IATF Information Assurance Technical Framework Security System Engineering methodology Lecturer: Lynn Ackler Date: 10/28/08 1

Information Systems Security Engineering ISSE Art and science of discovering users' information protection needs. Designing systems with economy and elegance, so that safely resists the forces to which they will be subjected. Building and testing such systems. Lecturer: Lynn Ackler Date: 10/28/08 2

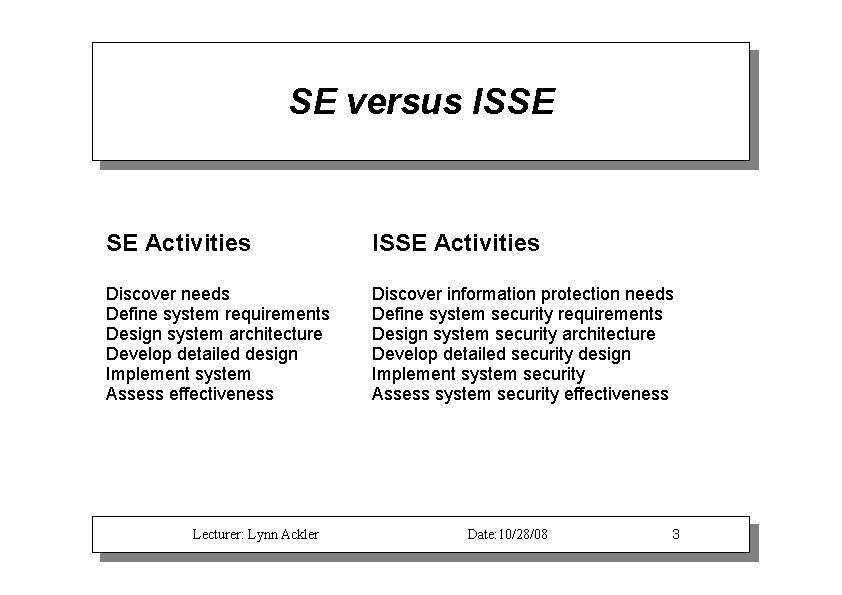
SE versus ISSE SE Activities ISSE Activities Discover needs Define system requirements Design system architecture Develop detailed design Implement system Assess effectiveness Discover information protection needs Define system security requirements Design system security architecture Develop detailed security design Implement system security Assess system security effectiveness Lecturer: Lynn Ackler Date: 10/28/08 3

Technical Security Countermeasures Determination of the appropriate technical security measures to address attacks at all layers in the information system. Lecturer: Lynn Ackler Date: 10/28/08 4

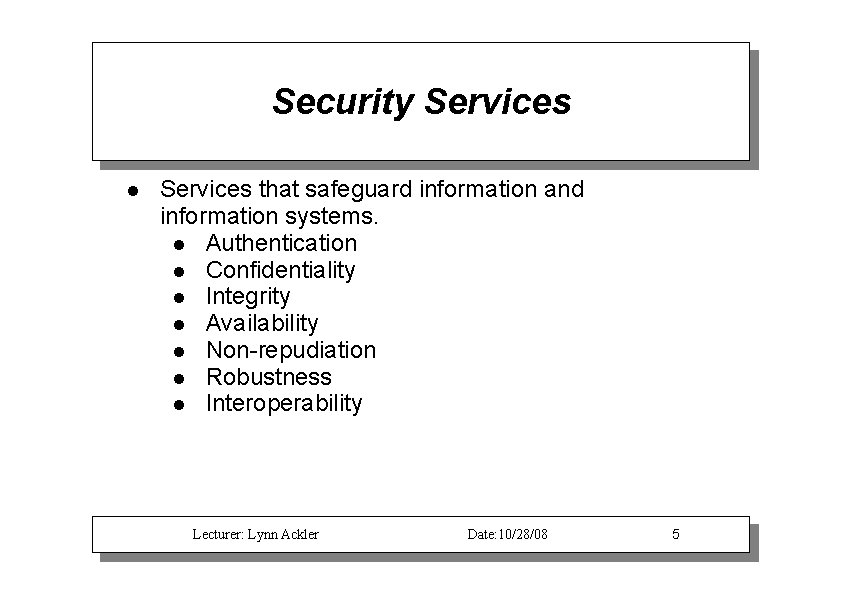
Security Services that safeguard information and information systems. Authentication Confidentiality Integrity Availability Non-repudiation Robustness Interoperability Lecturer: Lynn Ackler Date: 10/28/08 5

Potential Adversaries Nation States Hackers Terrorists Organized crime Other criminal elements International press Industrial competitors Disgruntled employees Careless employees Lecturer: Lynn Ackler Date: 10/28/08 6

Motivations Access to sensitive information Track operations Disrupt operations Steal money, products or services Free use Embarrassment Overcome technical challenge Compromise Lecturer: Lynn Ackler Date: 10/28/08 7

Classes of Attacks Passive attacks Active attacks Close-in attacks Insider attacks Distribution attacks Lecturer: Lynn Ackler Date: 10/28/08 8

Passive Attacks Monitoring open communication Decrypting weak encryption Ethernet sniffing WEP Password sniffing Traffic analysis Lecturer: Lynn Ackler Date: 10/28/08 9

Active Attacks Modify data in transit Replay Session hijacking Modify financial transactions Privileges of established session Masquerading Unauthorized access Lecturer: Lynn Ackler Date: 10/28/08 10

Active Attacks (cont'd) Exploiting app's or OS Outlook Express Exploit trust Transitive trust, e. g. PGP Lecturer: Lynn Ackler Date: 10/28/08 11

Active Attacks (cont'd) Data execution Inserting and exploiting code Open an attachment that is a script Trojan horse, back door Denial of service Lecturer: Lynn Ackler Date: 10/28/08 12

Close-in Attacks Access to comm's wires, RF, visual, etc. Information gathering System tampering IP addresses, IDs, passwords Bugging, keyboard sniffing SW Physical compromise Lecturer: Lynn Ackler Date: 10/28/08 13

Insider Attacks Malicious Modify/destroy data and security mechanisms Establish unauthorized access Cover channels Physical damage/alteration Non-malicious Modification of data/configuration Physical damage Lecturer: Lynn Ackler Date: 10/28/08 14

Distribution Attacks on the distribution chain of products or services Modification at vendor's facility Modification during distribution Lecturer: Lynn Ackler Date: 10/28/08 15

Primary Security Services Access control Confidentiality Integrity Availability Nonrepudiation Lecturer: Lynn Ackler Date: 10/28/08 16

Access Control Limiting access to information, services and communications Identity and authentication Authorization Access rights Decision You are who you say you are. Rights match demand Enforcement Grant/deny and log/notify Lecturer: Lynn Ackler Date: 10/28/08 17

Confidentiality Information state Data type Transmission, storage, proccessing Crypto keys, config files, text Amounts or parts of data Value and life of data Lecturer: Lynn Ackler Date: 10/28/08 18

Elements of Confidentiality Data protection Data separation Traffic flow protection Lecturer: Lynn Ackler Date: 10/28/08 19

Integrity Prevention of unauthorized data modification Detection and notification of unauthorized modification Logging all modifications Lecturer: Lynn Ackler Date: 10/28/08 20

Availability Protection from attack Protection from unauthorized use Resistance to routine failures Lecturer: Lynn Ackler Date: 10/28/08 21

Non-repudiation Repudiation: Denial by one entity in a multi-entity exchange that it participated. Non-repudiation: Proof of origin, proof of identity, time of origination Proof of delivery, time of delivery Audit trail Lecturer: Lynn Ackler Date: 10/28/08 22

Security Technologies APIs Crypto. API Cryptographic Service Providers File Encryptors Hardware tokens Intrusion detectors IPSec IKE Lecturer: Lynn Ackler Date: 10/28/08 23

Security Technologies (cont'd) Packet filter Stateful packet filter PKI SSL S/MIME Trusted Computing Base Virus detectors Tripwire Lecturer: Lynn Ackler Date: 10/28/08 24

Robustness Strategy Determine the Degree of Robustness Strength of Mechanism Levels of Assurance Lecturer: Lynn Ackler Date: 10/28/08 25

Purpose Security engineering guidance Levels of security mechanisms Security services appropriate to mission Levels of assurance Lecturer: Lynn Ackler Date: 10/28/08 26

Robustness Strategy Functions Assessment of strength mechanisms Definition of product requirements Subsequent risk assessments Recommend security requirements Lecturer: Lynn Ackler Date: 10/28/08 27

Robustness Strategy Process 1. Assess value 2. Assess threat 3. Determine strength level appropriate 4. Determine implementation necessary Lecturer: Lynn Ackler Date: 10/28/08 28

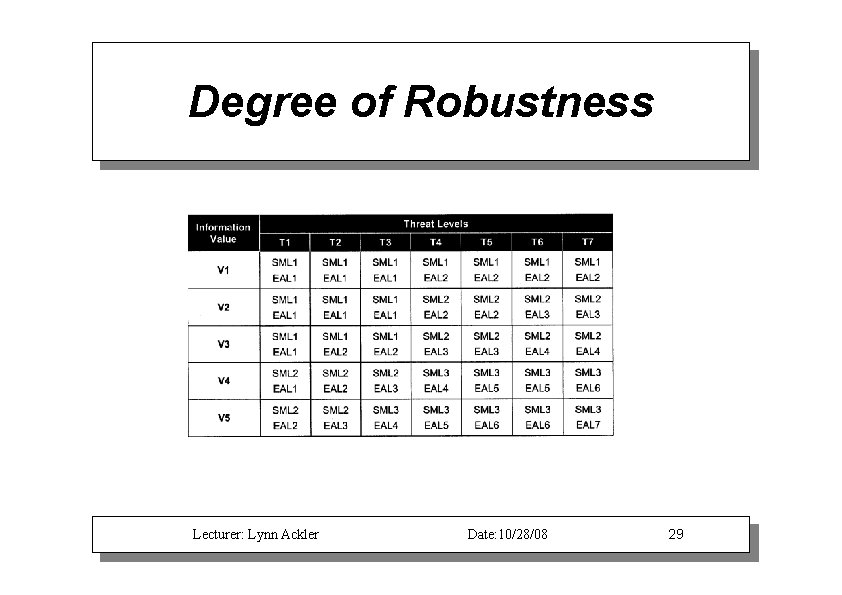
Degree of Robustness Lecturer: Lynn Ackler Date: 10/28/08 29

Degree of Robustness Determination Level of strength and assurance recommended for a potential security mechanism Depends on: 1. Value of information 2. Perceived threat environment Lecturer: Lynn Ackler Date: 10/28/08 30

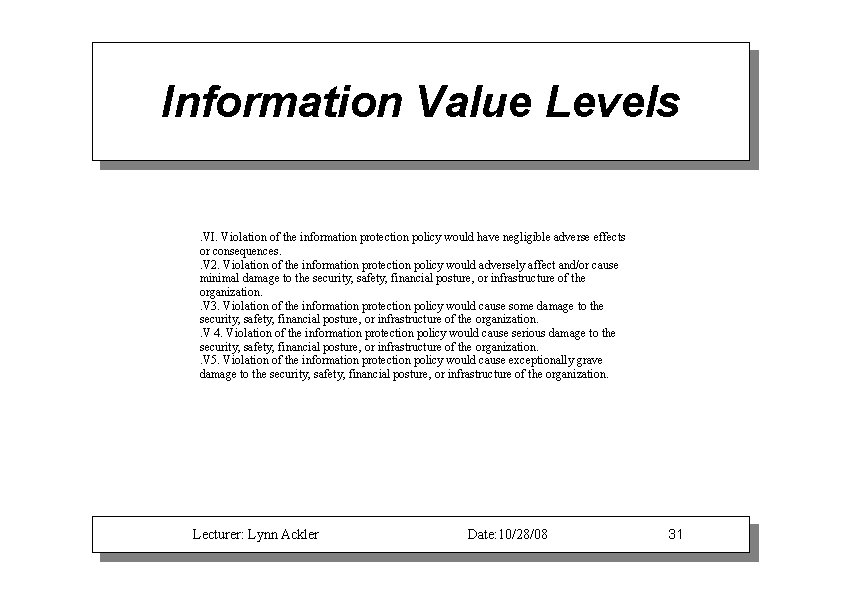
Information Value Levels. VI. Violation of the information protection policy would have negligible adverse effects or consequences. . V 2. Violation of the information protection policy would adversely affect and/or cause minimal damage to the security, safety, financial posture, or infrastructure of the organization. . V 3. Violation of the information protection policy would cause some damage to the security, safety, financial posture, or infrastructure of the organization. . V 4. Violation of the information protection policy would cause serious damage to the security, safety, financial posture, or infrastructure of the organization. . V 5. Violation of the information protection policy would cause exceptionally grave damage to the security, safety, financial posture, or infrastructure of the organization. Lecturer: Lynn Ackler Date: 10/28/08 31

Threat Levels . TI. Inadvertent or accidental events ( e. g. , tripping over a power cord). . T 2. Passive, casual adversary with minimal resources who is willing to take little risk ( e. g. , listening). . T 3. Adversary with minimal resources who is willing to take significant risk ( e. g. , unsophisticated hackers). . T 4. Sophisticated adversary with moderate resources who is willing to take little risk (e. g. , organized crime, sophisticated hackers, international corporations). . T 5. Sophisticated adversary with moderate resources who is willing to take significant risk (e. g. , international terrorists). . T 6. Extremely sophisticated adversary with abundant resources who is willing to take little risk (e. g. , well-funded national laboratory, nation-state, international corporation). . T 7. Extremely sophisticated adversary with abundant resources who is willing to take extreme risk (e. g. , nation-states in time of crisis). Lecturer: Lynn Ackler Date: 10/28/08 32

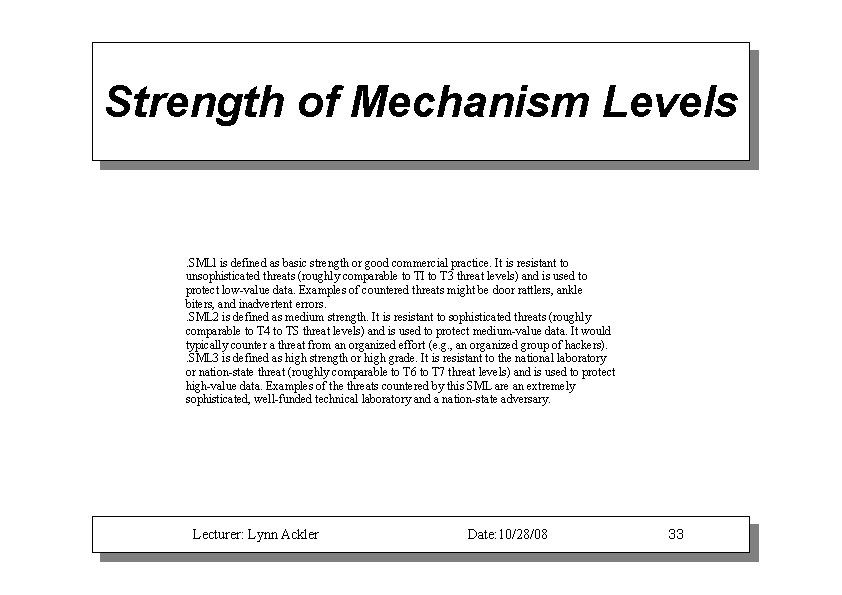
Strength of Mechanism Levels . SMLl is defined as basic strength or good commercial practice. It is resistant to unsophisticated threats (roughly comparable to TI to T 3 threat levels) and is used to protect low-value data. Examples of countered threats might be door rattlers, ankle biters, and inadvertent errors. . SML 2 is defined as medium strength. It is resistant to sophisticated threats (roughly comparable to T 4 to TS threat levels) and is used to protect medium-value data. It would typically counter a threat from an organized effort (e. g. , an organized group of hackers). . SML 3 is defined as high strength or high grade. It is resistant to the national laboratory or nation-state threat (roughly comparable to T 6 to T 7 threat levels) and is used to protect high-value data. Examples of the threats countered by this SML are an extremely sophisticated, well-funded technical laboratory and a nation-state adversary. Lecturer: Lynn Ackler Date: 10/28/08 33

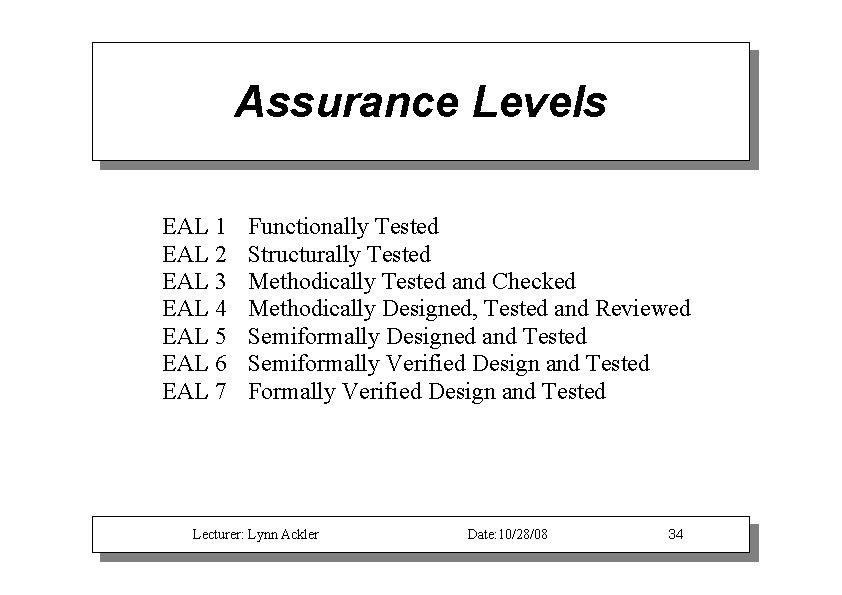
Assurance Levels EAL 1 EAL 2 EAL 3 EAL 4 EAL 5 EAL 6 EAL 7 Functionally Tested Structurally Tested Methodically Tested and Checked Methodically Designed, Tested and Reviewed Semiformally Designed and Tested Semiformally Verified Design and Tested Formally Verified Design and Tested Lecturer: Lynn Ackler Date: 10/28/08 34

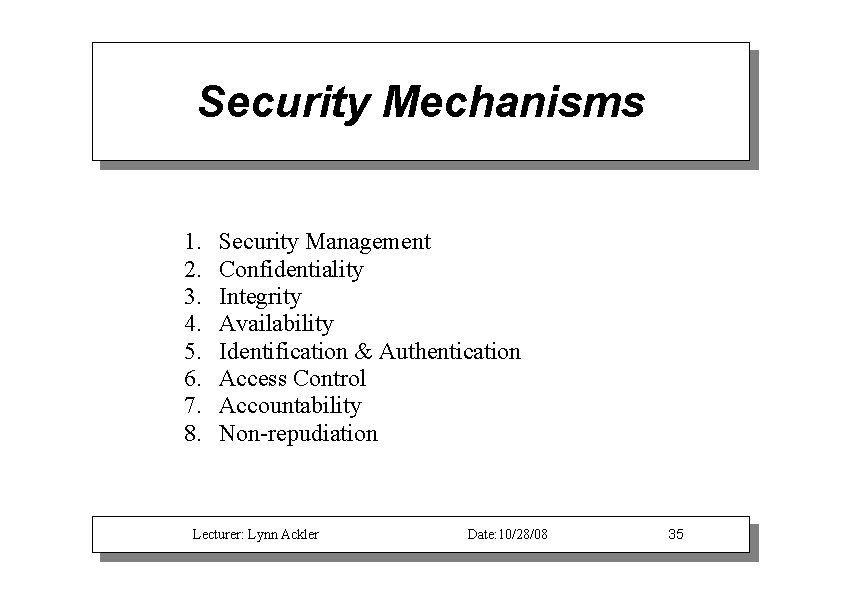
Security Mechanisms 1. 2. 3. 4. 5. 6. 7. 8. Security Management Confidentiality Integrity Availability Identification & Authentication Access Control Accountability Non-repudiation Lecturer: Lynn Ackler Date: 10/28/08 35

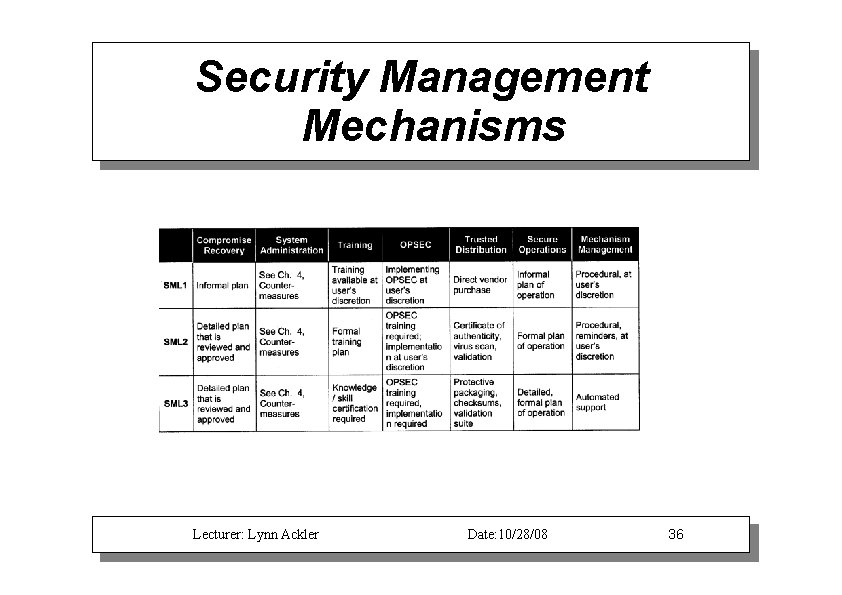
Security Management Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 36

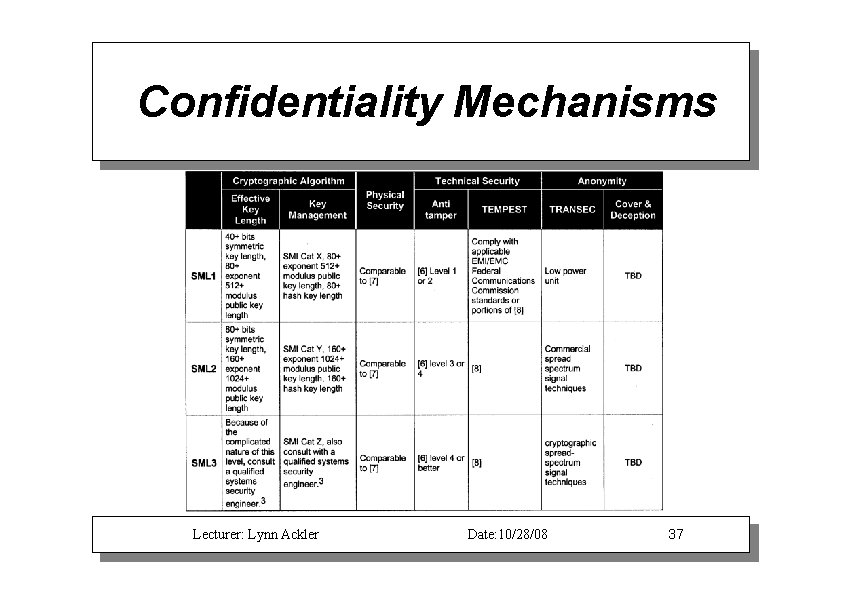
Confidentiality Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 37

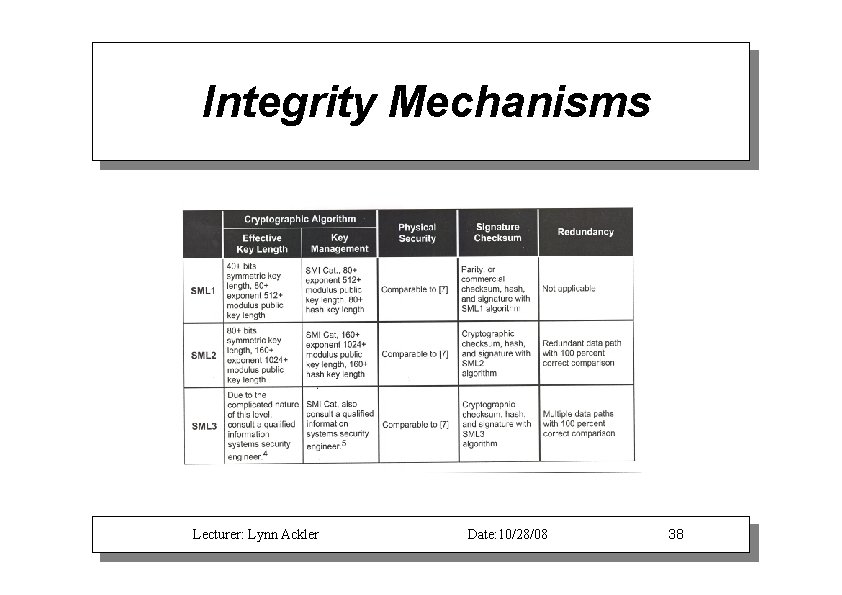
Integrity Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 38

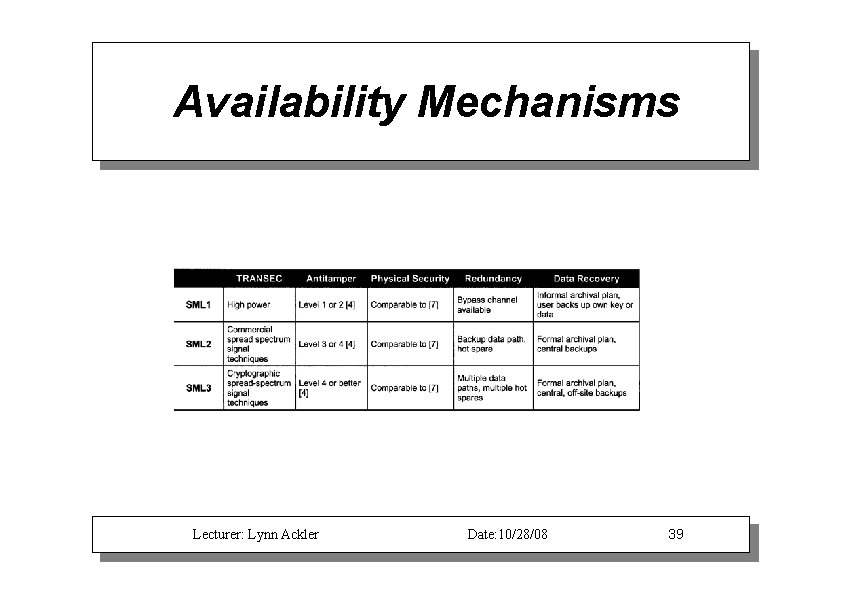
Availability Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 39

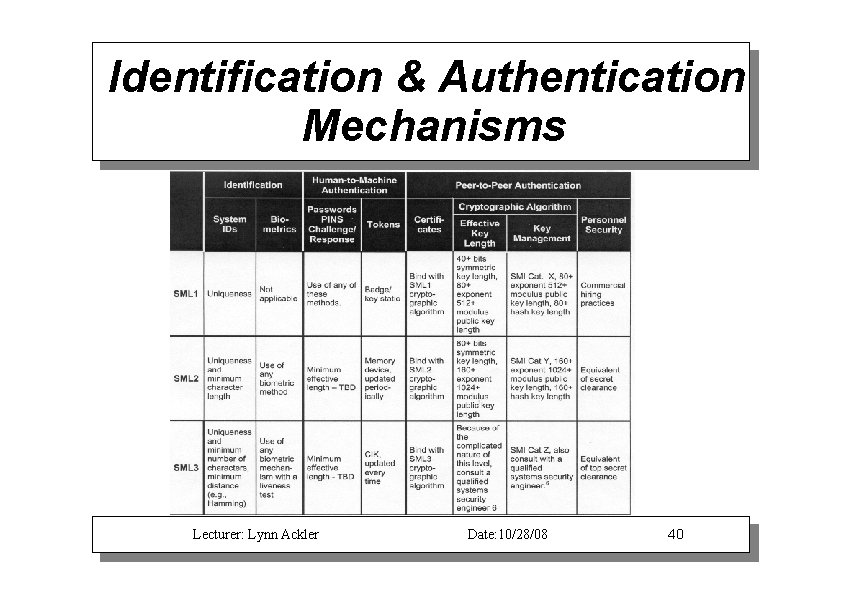
Identification & Authentication Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 40

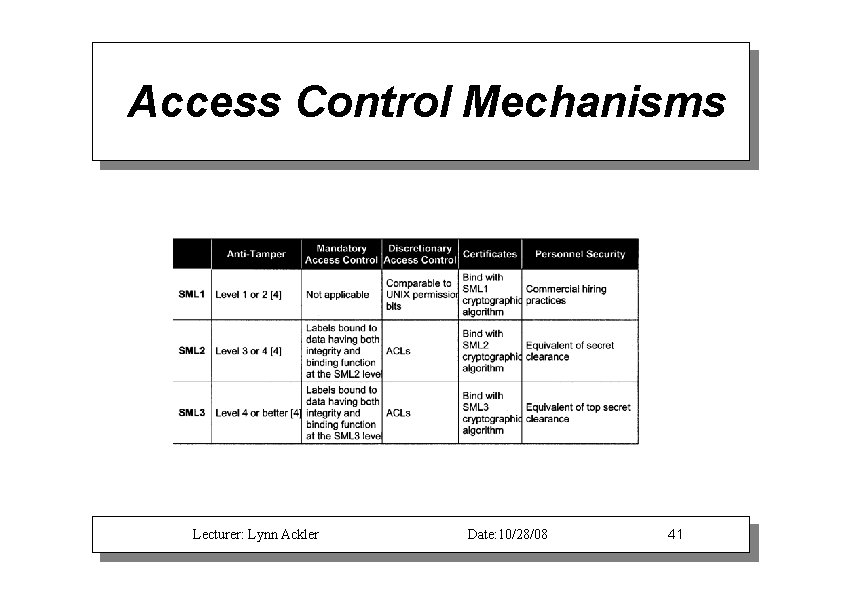
Access Control Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 41

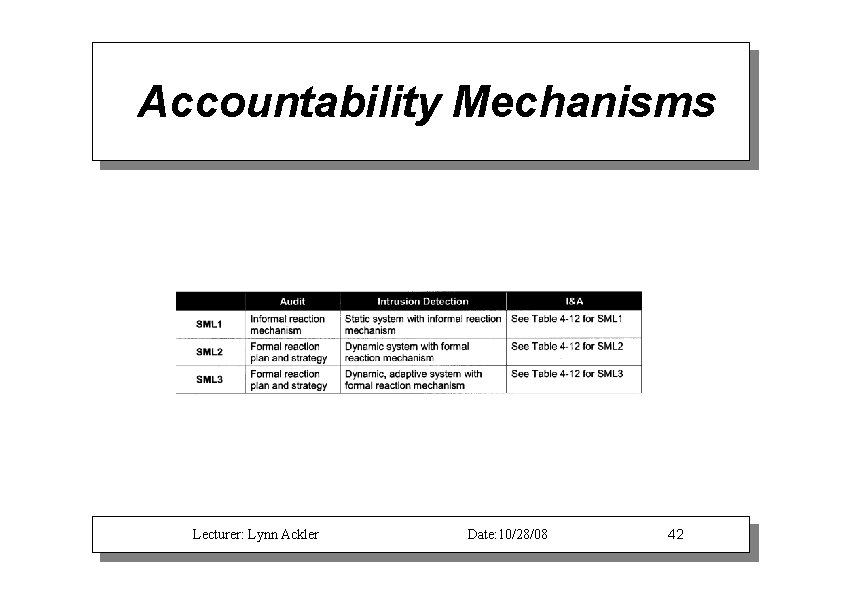
Accountability Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 42

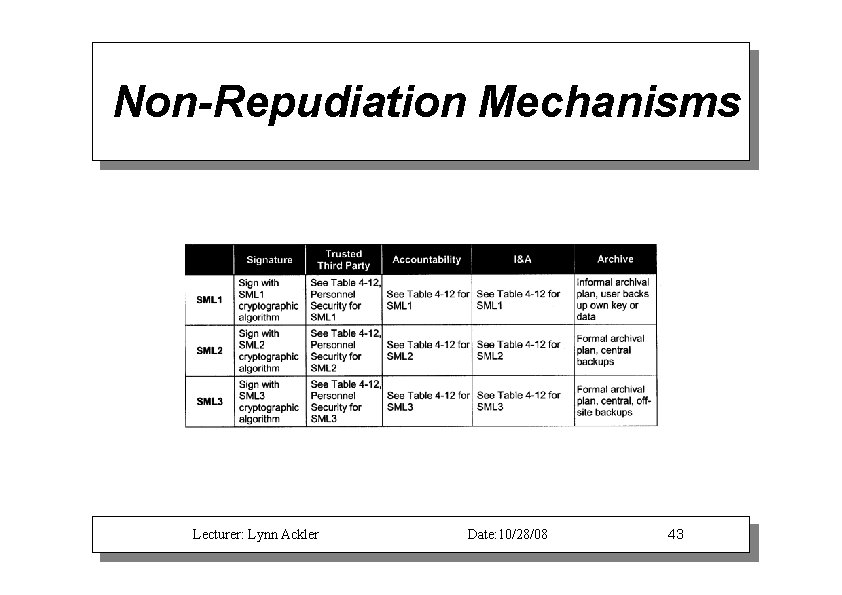
Non-Repudiation Mechanisms Lecturer: Lynn Ackler Date: 10/28/08 43

Interoperability Contemporary Systems involve multiple networks as well as multiple heterogeneous computer systems All systems depend on communication Security must be as transparent as possible in such a compute environment Lecturer: Lynn Ackler Date: 10/28/08 44

Elements of Interoperability 1. 2. 3. 4. 5. Architecture Security Protocols Standards Compliance Interoperable Certificate Management Agreement on Security Policies Lecturer: Lynn Ackler Date: 10/28/08 45

Interoperability Strategy 1. Foster Standards 2. Security Negotiation 3. Support Open Standards Lecturer: Lynn Ackler Date: 10/28/08 46