Information and Computer Security CPIS 312 Lab 9

Information and Computer Security CPIS 312 Lab 9 MAC & HASH FUNCTION TRIGUI Mohamed Salim 1

Lab Objectives To know what hashing is for 2. Practice how to implement MD cipher 1. 2
What is a Hash Function � Cryptographic hash function is another type of cryptographic algorithm. � A (one-way) hash function takes variable length input and produces a fixed length output called hash value. Also known as “message digest” or digest. � The hash function ensures that if the information has changed, an entirely different output value will be produced.
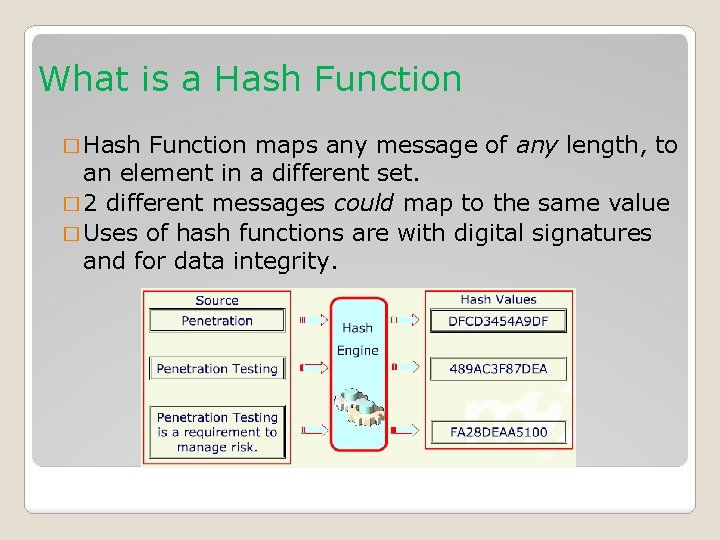
What is a Hash Function � Hash Function maps any message of any length, to an element in a different set. � 2 different messages could map to the same value � Uses of hash functions are with digital signatures and for data integrity.

Common hash algorithms

Technical Definition of MDAs � Message digest algorithms take Message <264 a message of arbitrary size and create a digest of fixed size. � The algorithm takes the message and splits it into blocks of equal length (the block size of. Block 0 Block 1 Block 2 … Block n the algorithm) � The last block is padded, with a total message length attached H(x) � Each block is sent through the function in order. � After all blocks are processed, the fixed digest value is retrieved Digest Value

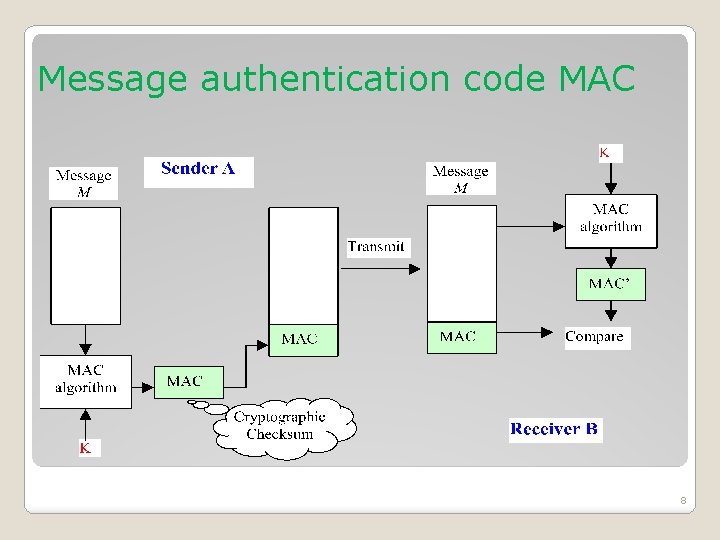
Message authentication code MAC � MAC is an algorithm that requires the use of a secret key. � MAC takes a variable-length message and a secret key as input and produces an authentication code. � Typically, MAC are used between two parties, say Alice and Bob, that share a secret key K in order to validate information transmitted between these parties. � When Alice has a message to send to Bob, she calculates the MAC as a function of the message and the key: MAC = C(K, M) where M=input message, C=MAC function, K=shared secret key. 7
Message authentication code MAC 8
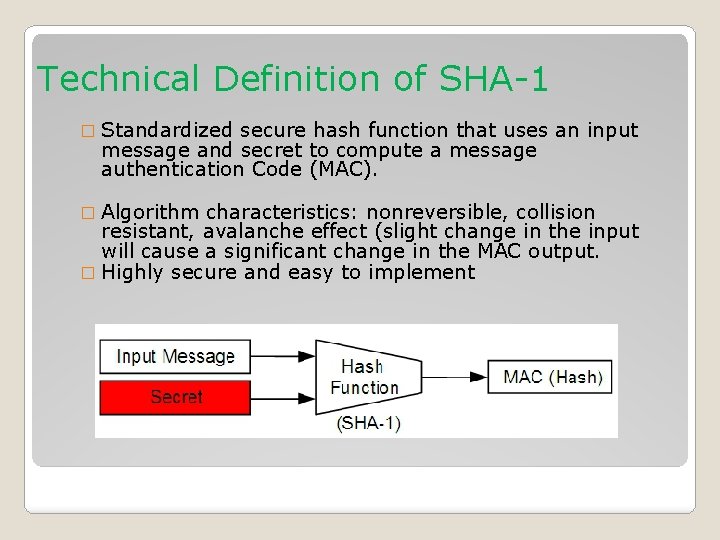
Technical Definition of SHA-1 � Standardized secure hash function that uses an input message and secret to compute a message authentication Code (MAC). � Algorithm characteristics: nonreversible, collision resistant, avalanche effect (slight change in the input will cause a significant change in the MAC output. � Highly secure and easy to implement
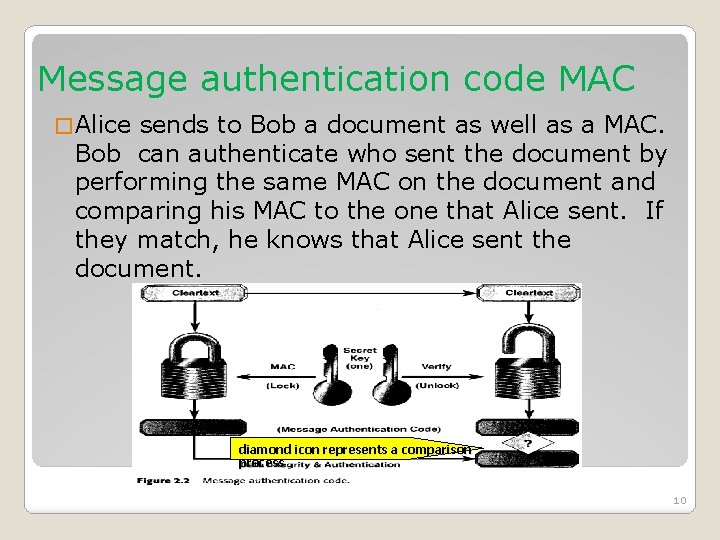
Message authentication code MAC � Alice sends to Bob a document as well as a MAC. Bob can authenticate who sent the document by performing the same MAC on the document and comparing his MAC to the one that Alice sent. If they match, he knows that Alice sent the document. diamond icon represents a comparison process 10
MAC in JAVA �Java Package: javax. crypto �Java Class : Mac �Methods: get. Instance(), init(), update(), do. Final(). �Algorithms: HMAC (Hashed MAC) 11
MD in JAVA � Java package: java. security � Java class: Message. Digest � Methods: get. Instance(), reset(), update(), digest(). � Algorithms: MD 5, SHA-1 12
- Slides: 12