INCS 775 Virtual Data Center Security using Linux



























- Slides: 55

INCS - 775 Virtual Data Center Security using Linux

What is a data center? A data center is a facility used to house mission critical computer systems and associated components. It generally includes environmental controls (air conditioning, fire suppression, etc. ), redundant/backup power supplies, redundant data communications connections and high security. (Wikipedia)

Data Center Physical Layout A data center can occupy one room of a building, one or more floors, or an entire building. Servers are stacked in rack cabinets Cabinets are arranged in rows with aisles in between them to allow access to both front and back of the servers

Data Center Physical Layout (cont. ) Air conditioning Backup power systems Raised floors – air circulation and power wiring Overhead cable trays – data wiring Fire prevention and extinguishing systems Physical security

Why Virtual Data Center? Several servers (virtual) implemented on one physical server Reduces operation costs AC requirements Power requirements Less IT personnel Easier to maintain More expensive equipment

Virtualization Environments Windows virtual environmnets: Microsoft Virtual PC Virtual Server VMware Linux virtual environments: Xen VMware

Why Linux? Linux is an Open Source operating system It is a fully 32/64 bit true multi user, multitasking, multiprocessor OS It is free There a lot of resources available It is more secure than Windows It is supported by virtualization environments

Why Linux? (cont. ) Has the X Windows GUI Coexists with other Operating Systems Runs on multiple platforms Includes the Source Code

Where to get it? There are different Linux Distributions Fedora Core – this is the one we will use in this course Debian Gentoo Slackware Ubuntu

History 1991 - Linux is created as a hobby by a student at University of Helsinki (Finland) 1992 - First public version 1993 - First prefabricated Linux distributions 1996 - Support for non-Intel processors 1999 - Linux 2. 2 released Current linux version is 2. 6

Linux environment Different runlevels Runlevel 0 – halt Runlevel 1 – single user mode Runlevel 2 – multiuser without NFS (same as runlevel 3 when networking is not present Runlevel 3 – full multiuser mode Runlevel 4 – unused Runlevel 5 – X 11 Runlevel 6 - reboot

Login Usually done at: Runlevel 3 Runlevel 5 Uses hashed passwords stored in a shadow password file WORD OF CAUTION: DO NOT LOGIN AS ROOT!!!

Work Environment Runlevel 3: console Runlevel 5: X 11 environment Window managers: GNOME KDE There are other window managers which require less space

XWindows • After login is successful work can be done in consoles using linux commands

Useful Commands ls more (followed by the file name) cat (followed by the file name) cd mv mkdir rm man (followed by the command name) – see next slide

Useful Commands (cont. ) • Man command

Useful commands (cont. ) • ls -l

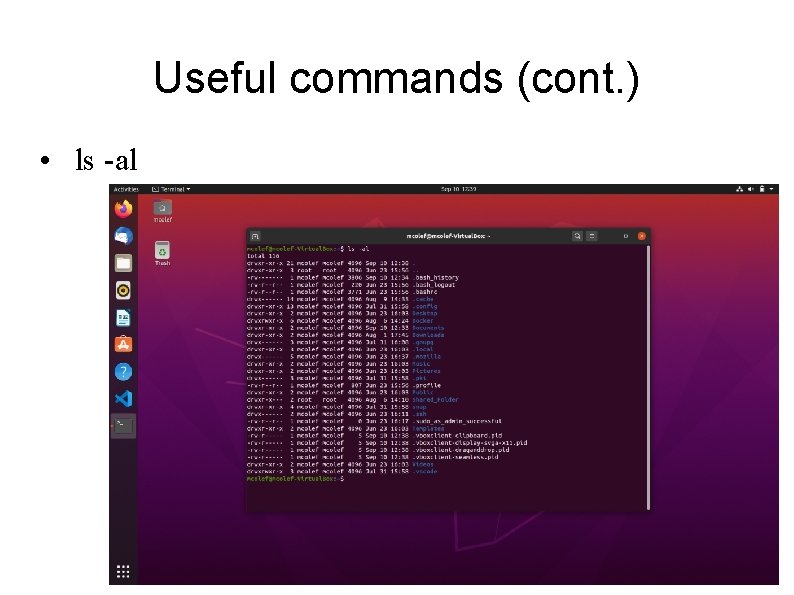
Useful commands (cont. ) • ls -al

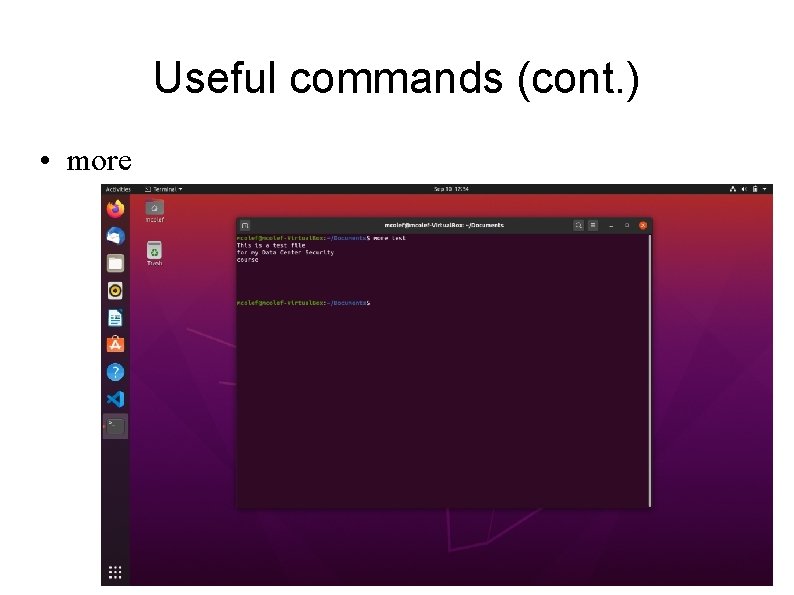
Useful commands (cont. ) • more

Basic Commands in Unix are typed into what is called a shell. Each command takes somenumber of arguments, which are known as “command-line arguments”, “arguments” or “options”. (In Microsoft lingo, these options are referred to as “switches”). The shell does not execute commands until the Enter key is pressed. Any errors are reported in the shell window.

Basic Commands When the lab starts, you will be presented with a black virtual terminal, and the current directory is your home directory. [Windows uses the name folder instead of directory. ] For the root user, home is at /root on Linux. For regular users, it is often found at /home/username, but it could be anywhere. Use the pwd command (present working directory) tosee what your home directory is: pwd

Basic Commands

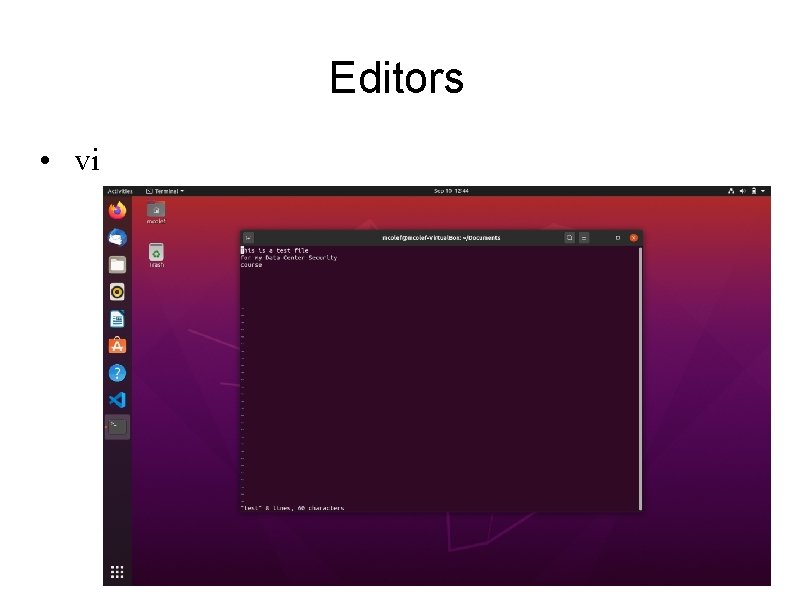
Editors vi emacs vim xemacs gedit

Editors • vi

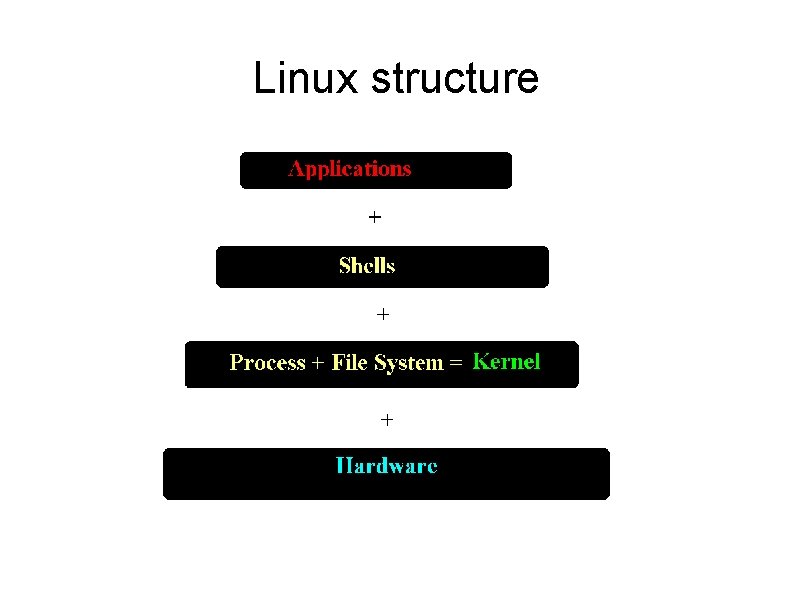
Linux structure

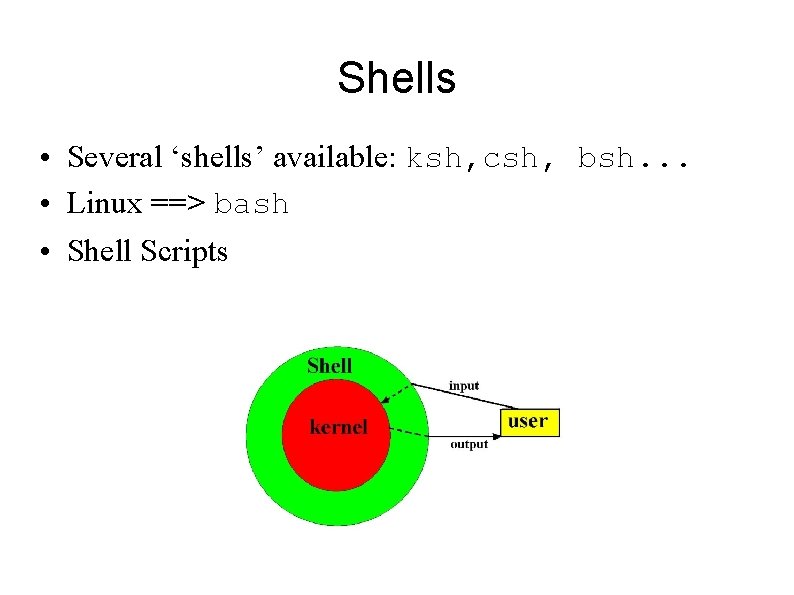
Shells • Several ‘shells’ available: ksh, csh, bsh. . . • Linux ==> bash • Shell Scripts

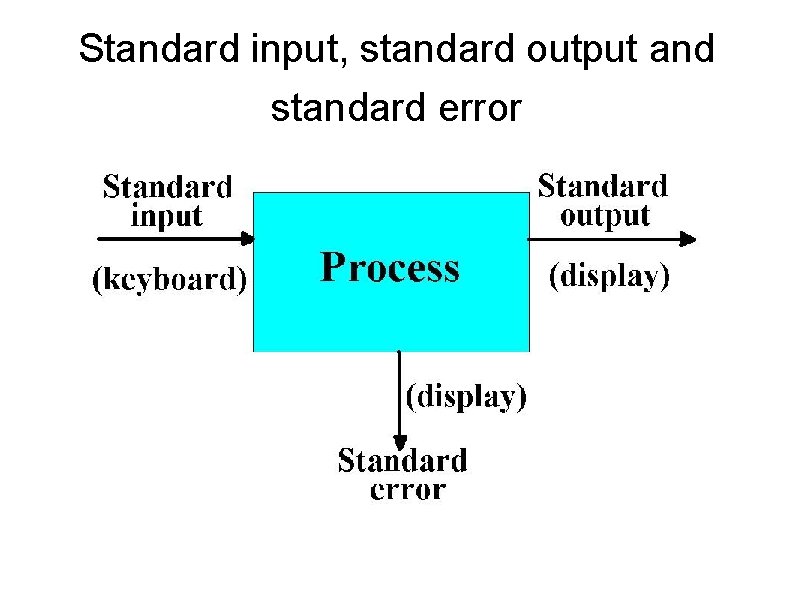
Standard input, standard output and standard error

Important! Everything in Linux is either a file or a process

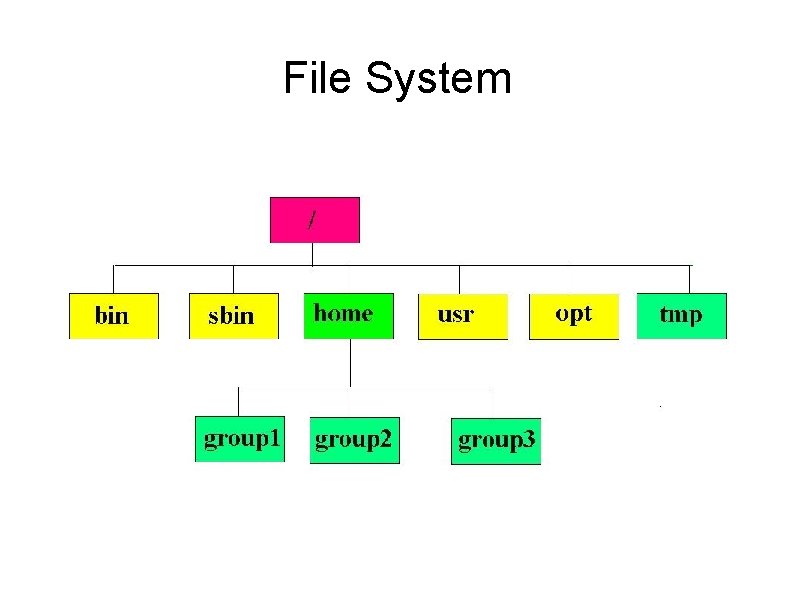
File System

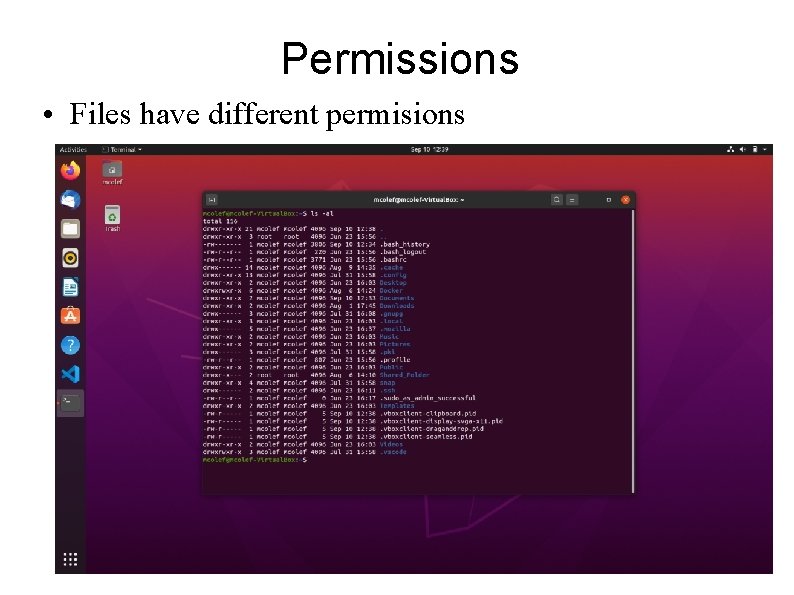
Permissions • Files have different permisions

Permissions (cont. ) Directories are special files Links are special files ugw - rwx

Processes ps –ef shows the running processes kill – command to kill a process

Pipes and Filters Pipes and filters: Pipes makes the output of the command to become the input for the next command Filters read from input and write to standard output command | filter

Print lpr –P<queue name> lpq –P<queue name>

More Help with Linux man – for commands http: //www. linux. org

Docker and Containers Docker is an open-source project that automates the deployment of applications inside software containers, by providing an additional layer of abstraction and automation of operating system– level virtualization on Linux. Provide a uniformed wrapper around a software package: «Build, Ship and Run Any App, Anywhere» November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -36

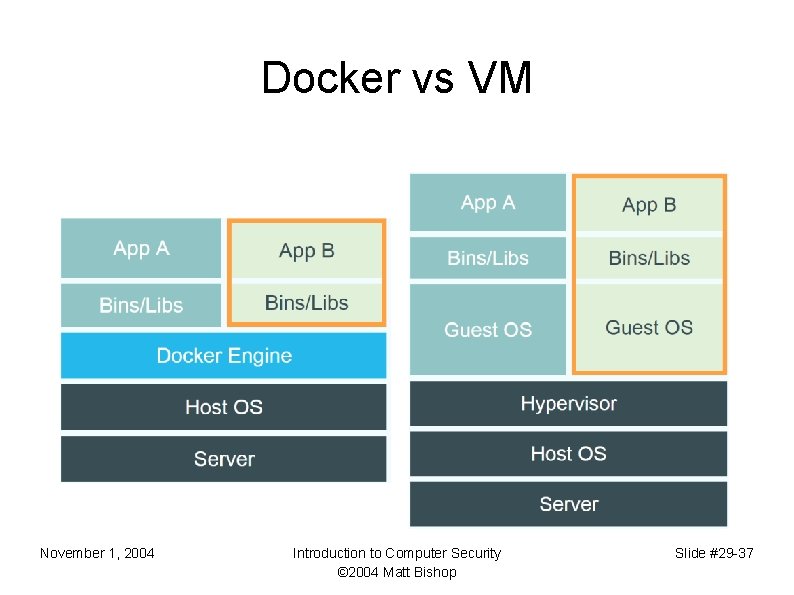
Docker vs VM November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -37

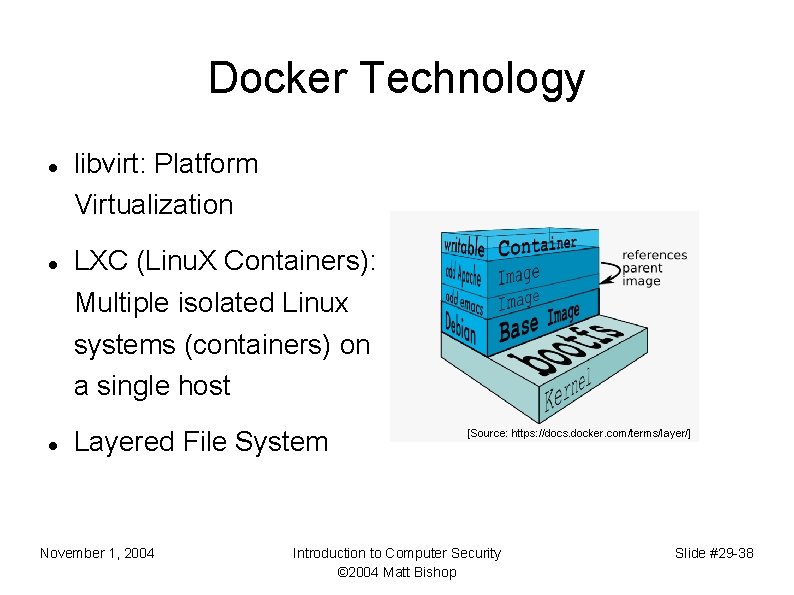
Docker Technology libvirt: Platform Virtualization LXC (Linu. X Containers): Multiple isolated Linux systems (containers) on a single host Layered File System November 1, 2004 [Source: https: //docs. docker. com/terms/layer/] Introduction to Computer Security © 2004 Matt Bishop Slide #29 -38

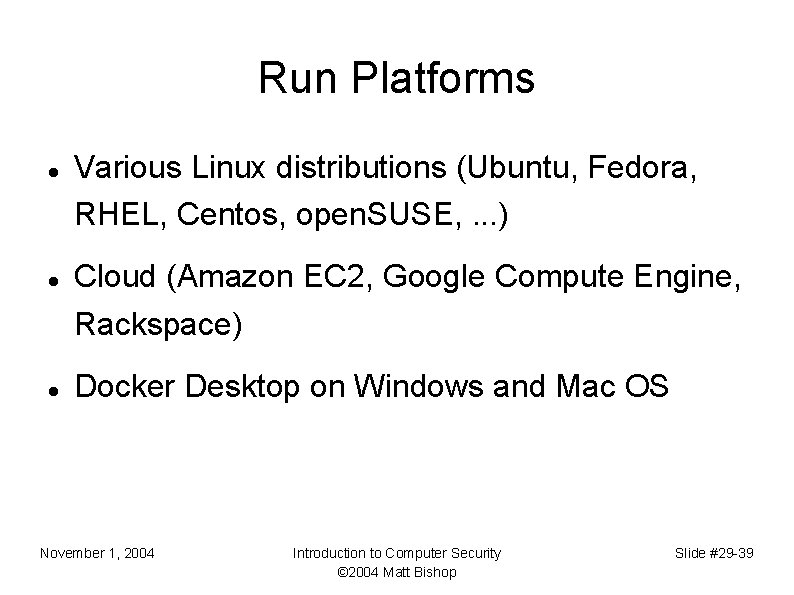
Run Platforms Various Linux distributions (Ubuntu, Fedora, RHEL, Centos, open. SUSE, . . . ) Cloud (Amazon EC 2, Google Compute Engine, Rackspace) Docker Desktop on Windows and Mac OS November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -39

Hello World Simple Command - Ad-Hoc Container docker run ubuntu echo Hello World - docker images [-a] - docker ps –a November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -40

Terminology - Image Persisted snapshot that can be run images: List all local images run: Create a container from an image and execute a command in it tag: Tag an image pull: Download image from repository rmi: Delete a local image This will also remove intermediate images if no longer November 1, 2004 Introduction to Computer Security Slide #29 -41 used © 2004 Matt Bishop

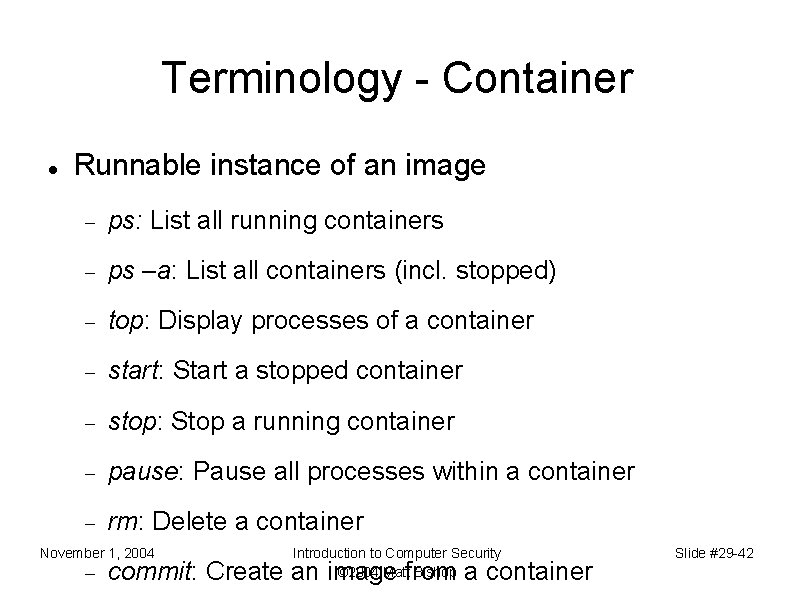
Terminology - Container Runnable instance of an image ps: List all running containers ps –a: List all containers (incl. stopped) top: Display processes of a container start: Start a stopped container stop: Stop a running container pause: Pause all processes within a container rm: Delete a container November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop commit: Create an image from a container Slide #29 -42

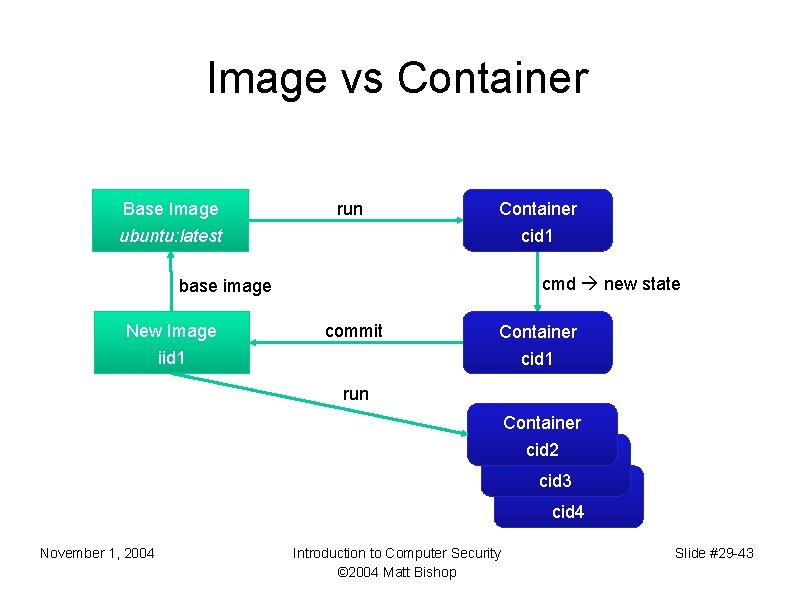
Image vs Container Base Image ubuntu: latest run Container cid 1 cmd new state base image New Image iid 1 commit Container cid 1 run Container cid 2 Container cid 3 Container cid 4 November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -43

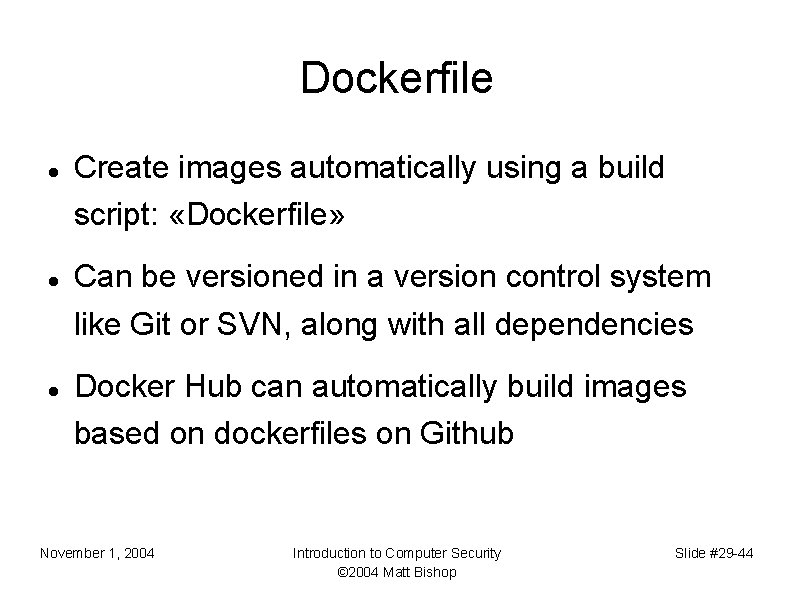
Dockerfile Create images automatically using a build script: «Dockerfile» Can be versioned in a version control system like Git or SVN, along with all dependencies Docker Hub can automatically build images based on dockerfiles on Github November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -44

Dockerfile Example Create images automatically using a build script: «Dockerfile» Can be versioned in a version control system like Git or SVN, along with all dependencies Docker Hub can automatically build images based on dockerfiles on Github November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -45

Mount Volumes docker run –ti –v /host. Log: /log ubuntu Run second container: Volume can be shared docker run –ti --volumes-from first. Container. Name ubuntu November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -46

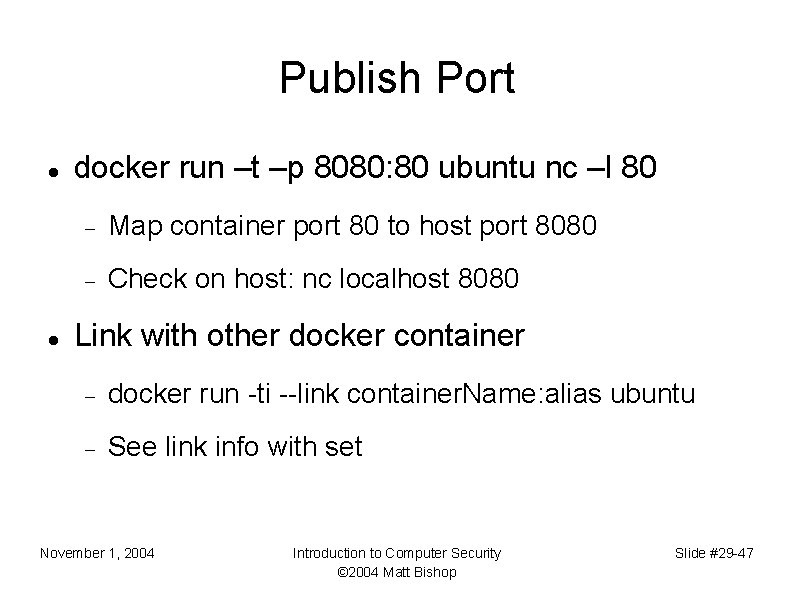
Publish Port docker run –t –p 8080: 80 ubuntu nc –l 80 Map container port 80 to host port 8080 Check on host: nc localhost 8080 Link with other docker container docker run -ti --link container. Name: alias ubuntu See link info with set November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -47

How can you use Docker? Three ways to use it: Install on Linux Use Oracle Virtualbox Install a Linux OS guest in Virtualbox Install Docker on the Linux guest Install Docker Desktop Works on Windows and Mac OS November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -48

Which editor to use to create the Docker images and other files? You can use Visual Studio Code which works on Linux, Windows and Mac OS Visual Studio Code is free and has Docker extensions support November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -49

Labtainers are based on Docker containers They can be downloaded from https: //nps. edu/web/c 3 o/labtainers November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -50

How are we going to use this technology in class? You will install Virtualbox and labtainers for students. There are several labtainers we will use during the semester to augment the knowledge from the lectures. November 1, 2004 Introduction to Computer Security © 2004 Matt Bishop Slide #29 -51

Virtualbox installation Go to: https: //www. virtualbox. org/wiki/Virtual. Box Download the appropriate file to install Virtualbox from Use the Virtualbox User Manual and follow the directions to configure it and to install guest operating systems. Labtainer. VM is based on Ubuntu.

Virtualbox and Labtainers Once the Labtainer. VM is installed using the student installation instructions, you can use it to get familiar with UNIX/Linux commands See next slide and read the nix– commands pdf file

UNIX/Linux Commands Boot your Linux system or VM. If necessary, log in and then open a terminal window and cd to the labtainer/labtainerstudent directory. The pre -packaged Labtainer VM will start with such a terminal open for you. Then start the lab: labtainer nix-commands

Other Usage of Virtualbox You will also use Virtualbox to complete a semester project. The project will consist of creating a small infrastructure of VMs and securing it. You will get more details later on in the semester.