INCOMPLETE INCORRECT FIGURE 6 from Client to Server

- Slides: 9

INCOMPLETE / INCORRECT FIGURE - (6) from Client to Server and (9) was missing - Communication (6) and (8) between LG and S is controlled by S Establish. Session 1 <dss: Sign. Request> 2 3 A URL & SID Client B REF C 4 & REF 5 URL SID <dss: Sign. Response> Connect LSCD Gateway URL Server 6 + 8 LOCAL (Secure) Signature Creation Device 8 Sign Digest SID Key. Selector <dss: Sign. Request> 7 9 6 6 <dss: Sign. Response> S LG / C S : <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> S LG / C S : <lsp: List. Certificates. Request> , followed by <lsp: List. Certificates. Response>

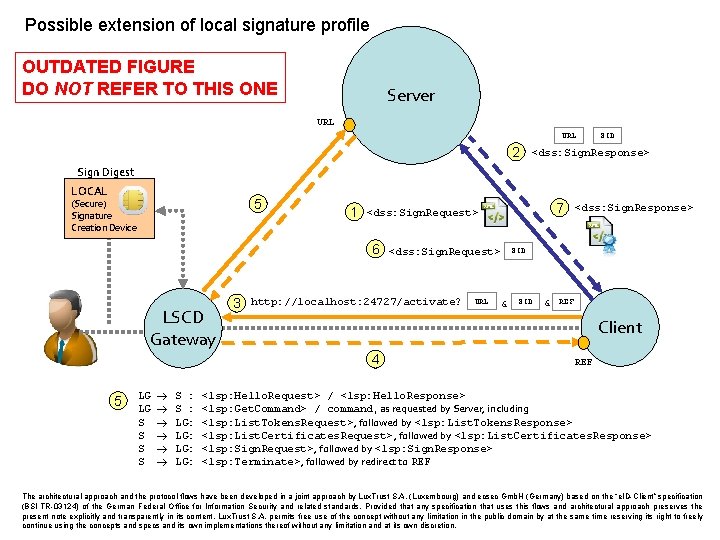
Possible extension of local signature profile OUTDATED FIGURE DO NOT REFER TO THIS ONE Server URL 2 SID <dss: Sign. Response> Sign Digest LOCAL 5 (Secure) Signature Creation Device 1 6 LSCD Gateway 3 LG LG S S S : LG: LG: <dss: Sign. Request> http: //localhost: 24727/activate? URL <dss: Sign. Response> SID & REF Client 4 5 7 <dss: Sign. Request> REF <lsp: Hello. Request> / <lsp: Hello. Response> <lsp: Get. Command> / command, as requested by Server, including <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> <lsp: List. Certificates. Request>, followed by <lsp: List. Certificates. Response> <lsp: Sign. Request>, followed by <lsp: Sign. Response> <lsp: Terminate>, followed by redirect to REF The architectural approach and the protocol flows have been developed in a joint approach by Lux. Trust S. A. (Luxembourg) and ecsec Gmb. H (Germany) based on the “e. ID-Client” specification (BSI TR-03124) of the German Federal Office for Information Security and related standards. Provided that any specification that uses this flows and architectural approach preserves the present note explicitly and transparently in its content, Lux. Trust S. A. permits free use of the concept without any limitation in the public domain by at the same time reserving its right to freely continue using the concepts and specs and its own implementations thereof without any limitation and at its own discretion.

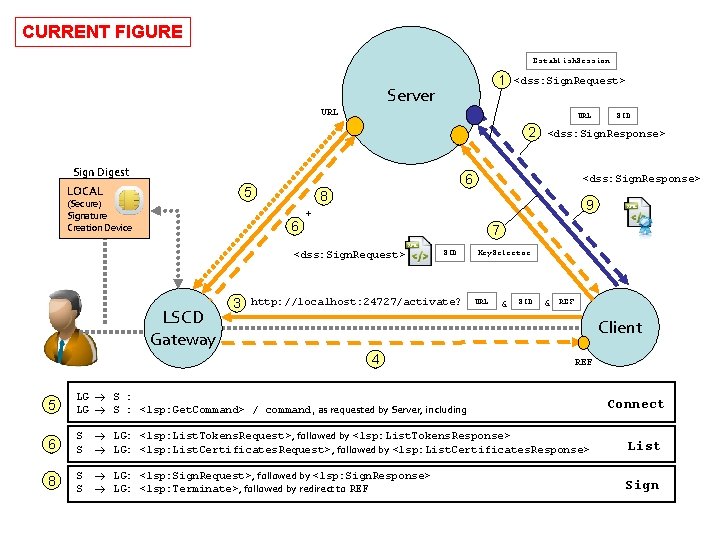
CURRENT FIGURE Establish. Session 1 Server <dss: Sign. Request> URL 2 Sign Digest LOCAL 9 + 7 <dss: Sign. Request> LSCD Gateway <dss: Sign. Response> 8 6 3 <dss: Sign. Response> 6 5 (Secure) Signature Creation Device SID http: //localhost: 24727/activate? Key. Selector URL & SID & REF Client 4 REF 5 LG S : <lsp: Get. Command> / command, as requested by Server, including 6 S S LG: <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> LG: <lsp: List. Certificates. Request>, followed by <lsp: List. Certificates. Response> List 8 S S LG: <lsp: Sign. Request>, followed by <lsp: Sign. Response> LG: <lsp: Terminate>, followed by redirect to REF Sign Connect

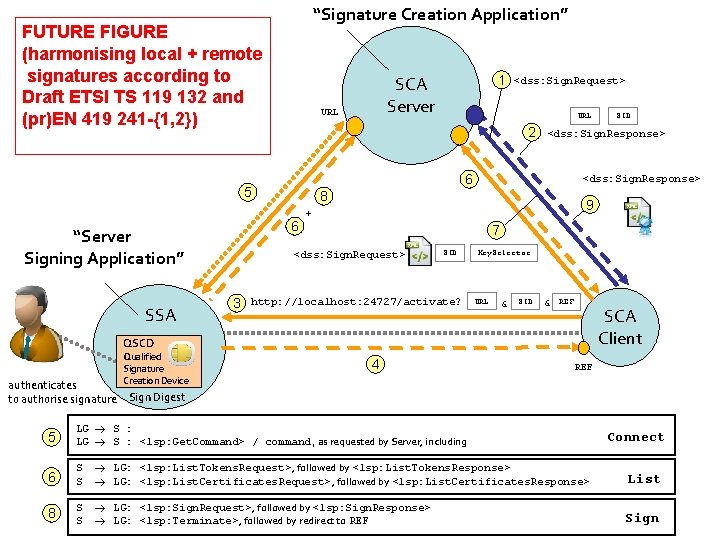
“Signature Creation Application” FUTURE FIGURE (harmonising local + remote signatures according to Draft ETSI TS 119 132 and (pr)EN 419 241 -{1, 2}) URL SSA URL <dss: Sign. Response> 8 9 + 7 <dss: Sign. Request> SID http: //localhost: 24727/activate? Key. Selector URL & SID & REF SCA Client QSCD Qualified Signature Creation Device SID <dss: Sign. Response> 6 6 3 <dss: Sign. Request> 2 5 “Server Signing Application” 1 SCA Server 4 REF authenticates to authorise signature Sign Digest 5 LG S : <lsp: Get. Command> / command, as requested by Server, including 6 S S LG: <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> LG: <lsp: List. Certificates. Request>, followed by <lsp: List. Certificates. Response> List 8 S S LG: <lsp: Sign. Request>, followed by <lsp: Sign. Response> LG: <lsp: Terminate>, followed by redirect to REF Sign Connect

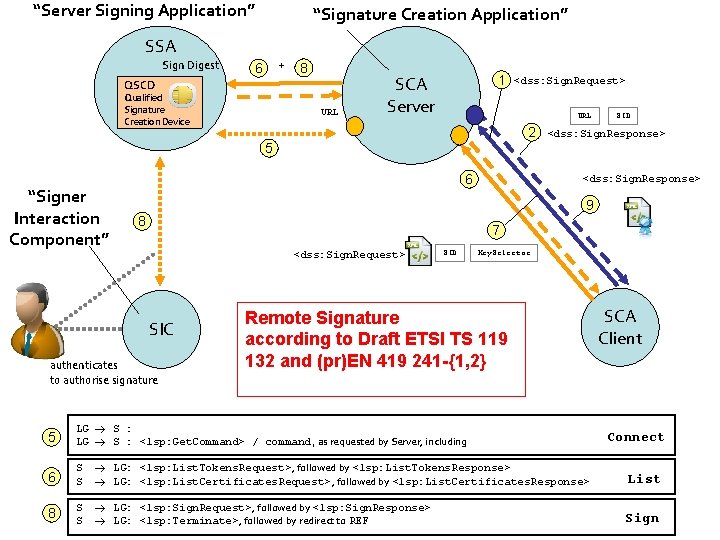
“Server Signing Application” “Signature Creation Application” SSA Sign Digest + 6 8 QSCD Qualified Signature Creation Device URL 1 SCA Server <dss: Sign. Request> URL 2 SID <dss: Sign. Response> 5 “Signer Interaction Component” 6 <dss: Sign. Response> 9 8 7 <dss: Sign. Request> SIC authenticates to authorise signature SID Key. Selector Remote Signature according to Draft ETSI TS 119 132 and (pr)EN 419 241 -{1, 2} SCA Client 5 LG S : <lsp: Get. Command> / command, as requested by Server, including 6 S S LG: <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> LG: <lsp: List. Certificates. Request>, followed by <lsp: List. Certificates. Response> List 8 S S LG: <lsp: Sign. Request>, followed by <lsp: Sign. Response> LG: <lsp: Terminate>, followed by redirect to REF Sign Connect

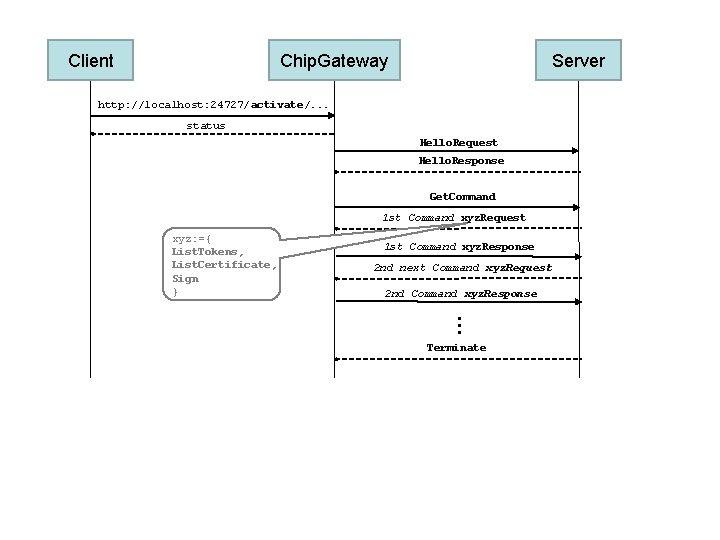
Client Chip. Gateway Server http: //localhost: 24727/activate/. . . status Hello. Request Hello. Response Get. Command 1 st Command xyz. Request xyz: ={ List. Tokens, List. Certificate, Sign } 1 st Command xyz. Response 2 nd next Command xyz. Request 2 nd Command xyz. Response … Terminate

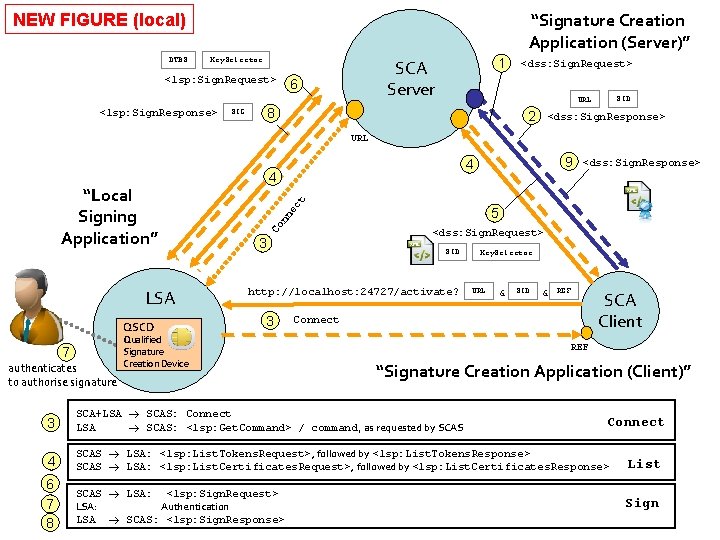
“Signature Creation Application (Server)” NEW FIGURE (local) DTBS Key. Selector <lsp: Sign. Request> <lsp: Sign. Response> 1 SCA Server 6 SID URL 8 SIG <dss: Sign. Request> 2 <dss: Sign. Response> URL LSA QSCD 7 authenticates to authorise signature <dss: Sign. Response> ec t 4 5 nn Co “Local Signing Application” 9 4 <dss: Sign. Request> 3 SID http: //localhost: 24727/activate? 3 Qualified Signature Creation Device Key. Selector URL & SID & REF Connect SCA Client REF “Signature Creation Application (Client)” 3 SCA+LSA SCAS: Connect LSA SCAS: <lsp: Get. Command> / command, as requested by SCAS 4 SCAS LSA: <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> SCAS LSA: <lsp: List. Certificates. Request>, followed by <lsp: List. Certificates. Response> List 6 7 8 SCAS LSA: <lsp: Sign. Request> LSA: Authentication LSA SCAS: <lsp: Sign. Response> Sign Connect

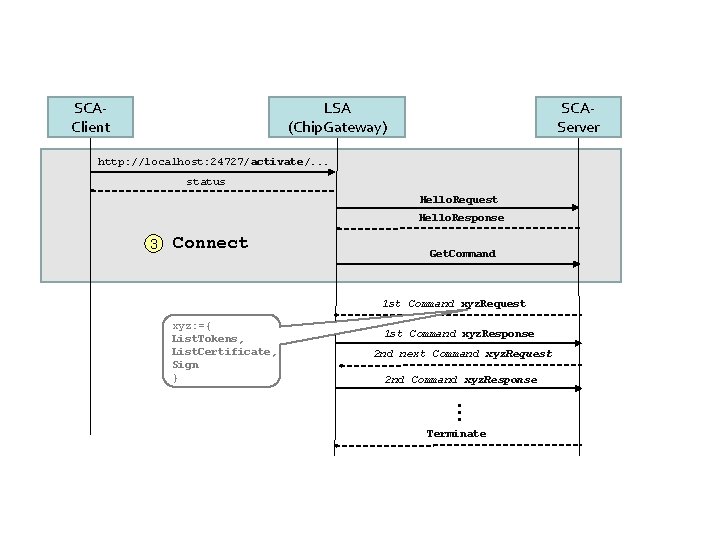
SCAClient LSA (Chip. Gateway) SCAServer http: //localhost: 24727/activate/. . . status Hello. Request Hello. Response 3 Connect Get. Command 1 st Command xyz. Request xyz: ={ List. Tokens, List. Certificate, Sign } 1 st Command xyz. Response 2 nd next Command xyz. Request 2 nd Command xyz. Response … Terminate

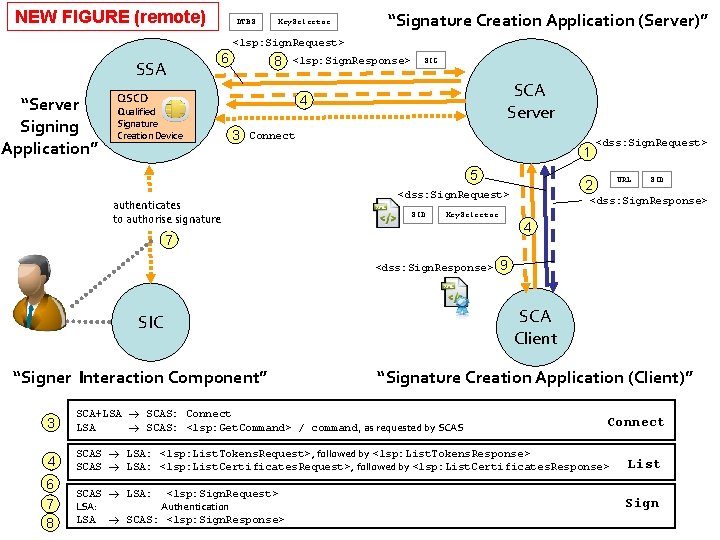
NEW FIGURE (remote) DTBS Key. Selector “Signature Creation Application (Server)” <lsp: Sign. Request> SSA “Server Signing Application” 6 8 <lsp: Sign. Response> QSCD Qualified Signature Creation Device SIG SCA Server 4 3 Connect 1 5 authenticates to authorise signature Key. Selector <dss: Sign. Response> 9 SCA Client SIC “Signer Interaction Component” SID 4 7 <dss: Sign. Response> URL 2 <dss: Sign. Request> SID <dss: Sign. Request> “Signature Creation Application (Client)” 3 SCA+LSA SCAS: Connect LSA SCAS: <lsp: Get. Command> / command, as requested by SCAS 4 SCAS LSA: <lsp: List. Tokens. Request>, followed by <lsp: List. Tokens. Response> SCAS LSA: <lsp: List. Certificates. Request>, followed by <lsp: List. Certificates. Response> List 6 7 8 SCAS LSA: <lsp: Sign. Request> LSA: Authentication LSA SCAS: <lsp: Sign. Response> Sign Connect