Improving Cost Performance and Security of Memory Encryption



- Slides: 19

Improving Cost, Performance, and Security of Memory Encryption and Authentication Chenyu Yan, Brian Rogers§, Daniel Englender, Yan Solihin§, Milos Prvulovic Georgia Tech § NC STATE UNIVERSITY

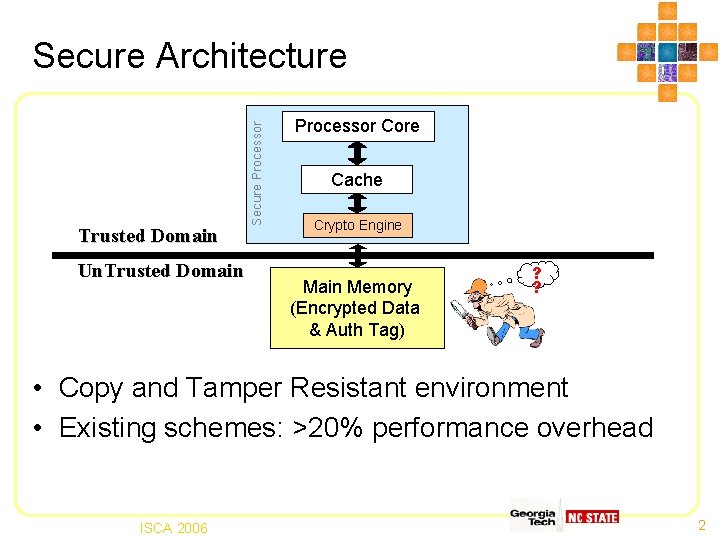
Trusted Domain Un. Trusted Domain Secure Processor Secure Architecture Processor Core Cache Crypto Engine Main Memory (Encrypted Data & Auth Tag) ? ? • Copy and Tamper Resistant environment • Existing schemes: >20% performance overhead ISCA 2006 2

Contributions • Split counters – Smaller counters (better caching, less space overhead) – Reduce re-encryption work, off critical path • Use Galois/Counter Mode (GCM) – Overlap most authentication work with memory latency – Provide precise authentication w/ little perf. overhead • Improved security – Solve pitfall in counter mode encryption 3

Outline Ø Background Ø Split Counter Mode Encryption • Split Counters Ø Memory Authentication with GCM Ø A Security Pitfall and Solution Ø Evaluation Ø Conclusion 4

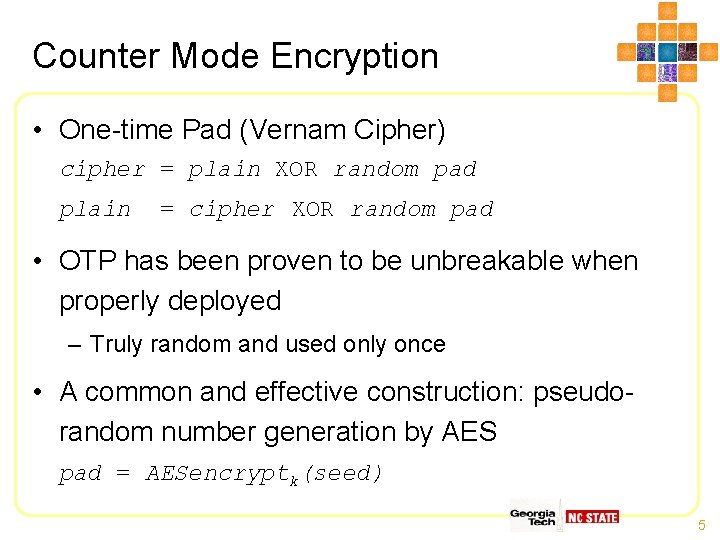
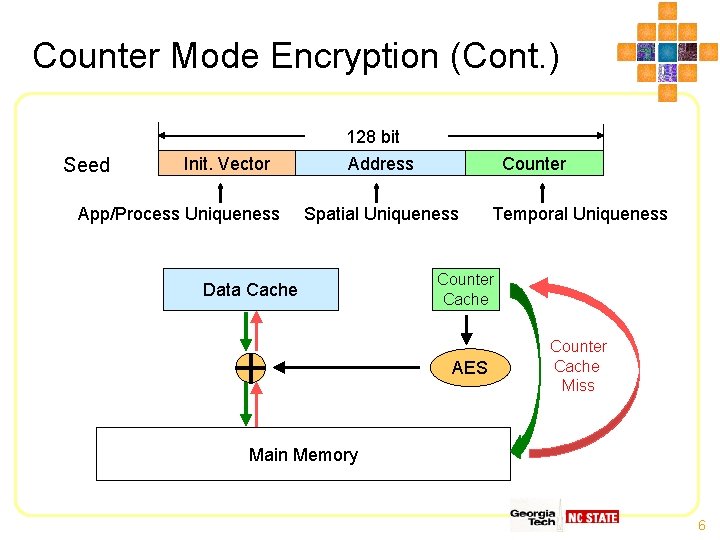
Counter Mode Encryption • One-time Pad (Vernam Cipher) cipher = plain XOR random pad plain = cipher XOR random pad • OTP has been proven to be unbreakable when properly deployed – Truly random and used only once • A common and effective construction: pseudorandom number generation by AES pad = AESencryptk(seed) 5

Counter Mode Encryption (Cont. ) Seed Init. Vector App/Process Uniqueness 128 bit Address Counter Spatial Uniqueness Data Cache Temporal Uniqueness Counter Cache AES Counter Cache Miss Main Memory 6

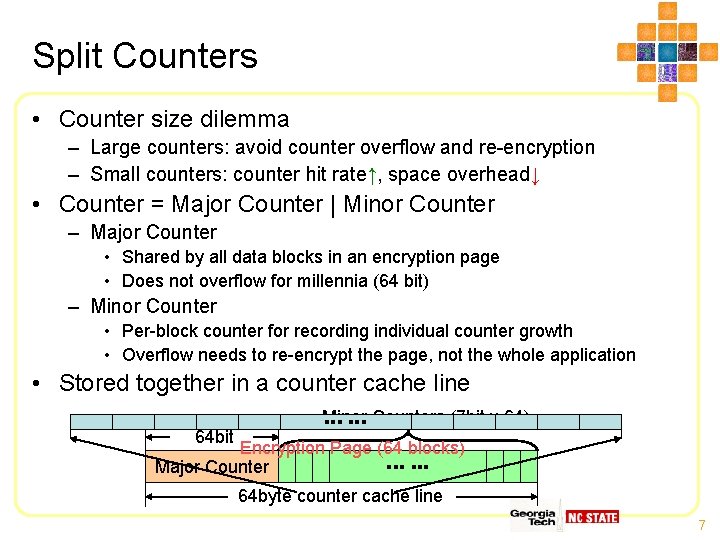
Split Counters • Counter size dilemma – Large counters: avoid counter overflow and re-encryption – Small counters: counter hit rate↑, space overhead↓ • Counter = Major Counter | Minor Counter – Major Counter • Shared by all data blocks in an encryption page • Does not overflow for millennia (64 bit) – Minor Counter • Per-block counter for recording individual counter growth • Overflow needs to re-encrypt the page, not the whole application • Stored together in a counter cache line Minor ▪▪▪ Counters (7 bit x 64) 64 bit Encryption Page (64 blocks) Major Counter ▪▪▪ 64 byte counter cache line 7

Outline Ø Background Ø Split Counter Mode Encryption Ø Memory Authentication with GCM Ø A Security Pitfall and Solution Ø Evaluation Ø Conclusion 8

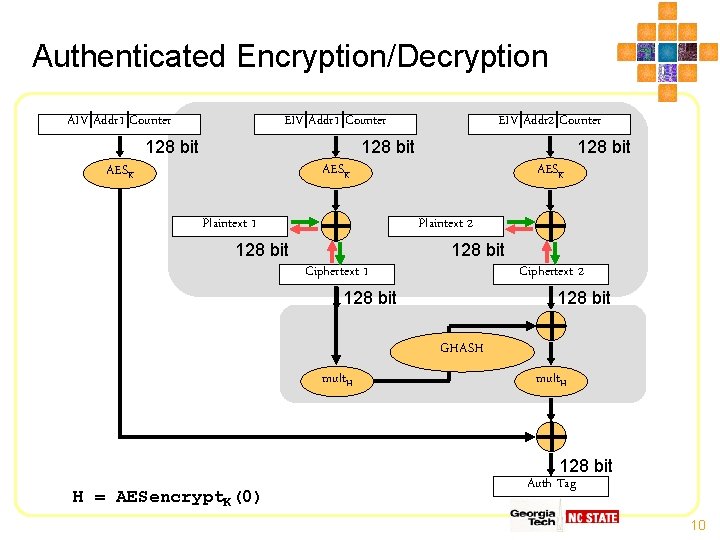
Galois Counter Mode • Authenticated Encryption Mode – Mc. Grew and Viega, 2005 • Counter mode encryption coupled with pad-based authentication • Can be pipelined and parallelized – Pre-compute pad – When ciphertext arrives, MAC quickly generated 9

Authenticated Encryption/Decryption AIV|Addr 1|Counter EIV|Addr 1|Counter 128 bit EIV|Addr 2|Counter 128 bit AESK Plaintext 1 AESK Plaintext 2 128 bit Ciphertext 1 Ciphertext 2 128 bit GHASH mult. H H = AESencrypt. K(0) mult. H 128 bit Auth Tag 10

Outline Ø Background Ø Split Counter Mode Encryption Ø Memory Authentication with GCM Ø A Security Pitfall and Solution • Counter Replay Attack • Protect Counter Integrity Ø Evaluation Ø Conclusion 11

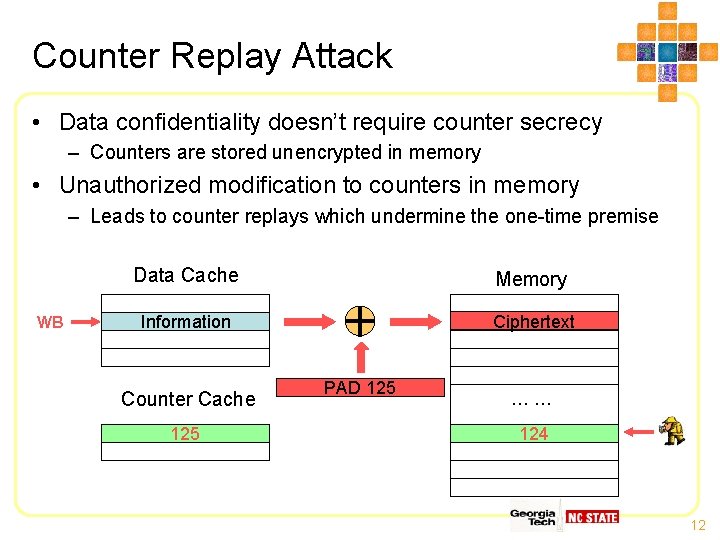
Counter Replay Attack • Data confidentiality doesn’t require counter secrecy – Counters are stored unencrypted in memory • Unauthorized modification to counters in memory – Leads to counter replays which undermine the one-time premise WB Data Cache Memory Information Ciphertext Counter Cache 125 PAD 125 …… 124 12

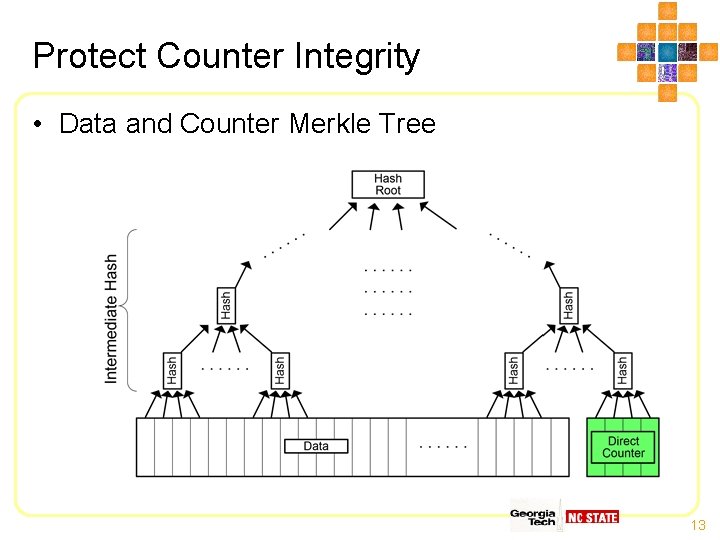
Protect Counter Integrity • Data and Counter Merkle Tree 13

Outline Ø Background Ø Split Counter Mode Encryption Ø Memory Authentication with GCM Ø Data and Counter Integrity Issues Ø Evaluation Ø Conclusion 14

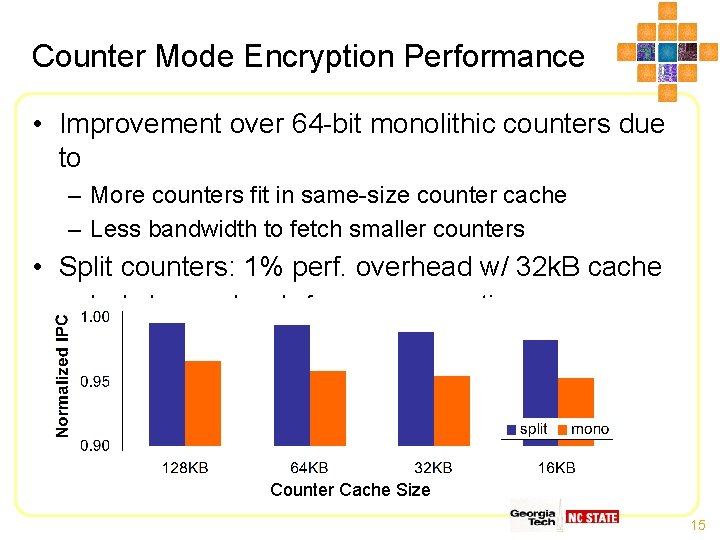
Counter Mode Encryption Performance • Improvement over 64 -bit monolithic counters due to – More counters fit in same-size counter cache – Less bandwidth to fetch smaller counters • Split counters: 1% perf. overhead w/ 32 k. B cache – Includes overhead of page re-encryptions Counter Cache Size 15

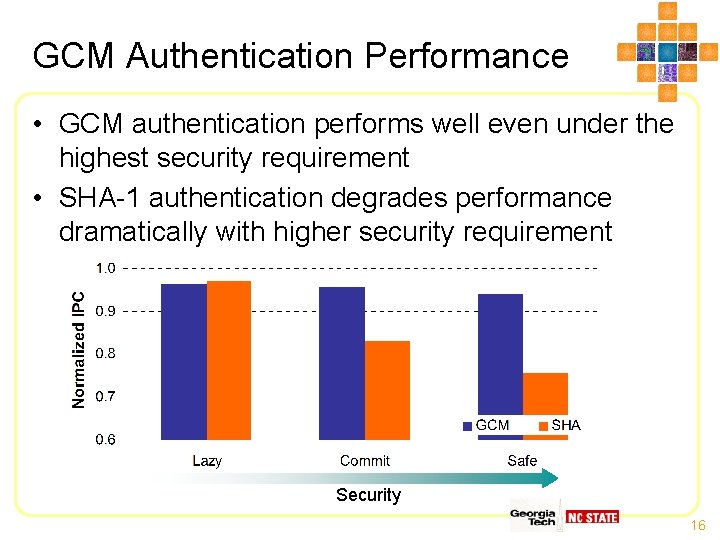
GCM Authentication Performance • GCM authentication performs well even under the highest security requirement • SHA-1 authentication degrades performance dramatically with higher security requirement Security 16

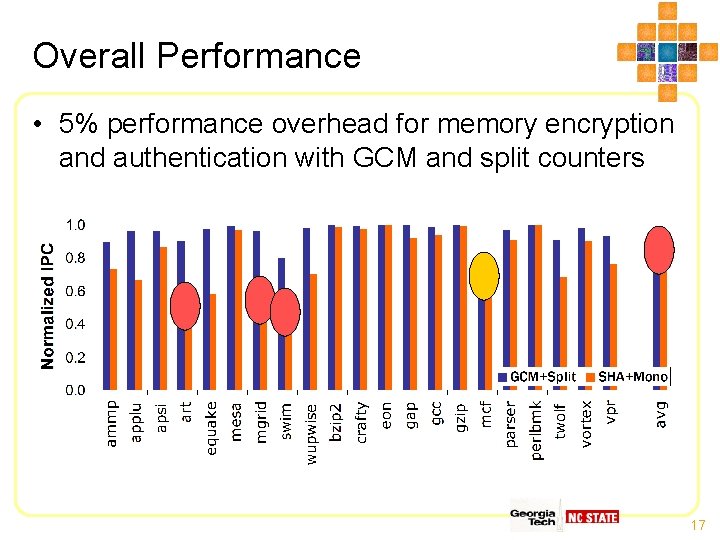
Overall Performance • 5% performance overhead for memory encryption and authentication with GCM and split counters 17

Conclusions • Split counters – Improve counter caching – Reduce counter storage overhead – Remove re-encryption glitches, allow optimization • GCM – Large reduction of authentication overheads – Complements counter-mode encryption naturally • Protect counter integrity to keep data safe – Negligible performance impact 18

Questions Email: cyan@cc. gatech. edu Georgia Tech § NC STATE UNIVERSITY 19