Implementing Secure Workstations via Advanced Authentication and Secure












- Slides: 35

Implementing Secure Workstations via Advanced Authentication and Secure Application Access Roy Lopez Director, Systems Engineering New York District Novell Inc. , rlopez@novell. com June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Novell one Net vision Novell exte. Nd™ Opening the door to Web services : Novell Ngage SM : : The experience to solve your business problems Novell Nsure™ : Securely getting the right information to the right people Novell Nsure solutions take identity management to a whole new level. Novell Nterprise Combining award-winning™products, customer-driven services The best foundation forand your committed business partnerships, mixed environment Novell Nsure gives you the power to control access so you can confidently deliver the right resources to the right people — securely, efficiently and, best of all, affordably. 2 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Summary of the Solution Goal: Implement a Secure Workspace for our Employees, Customers or Partners Solution: 1. Implement Secure Authentication above, or in addition to standard Password Authentication 2. Implement a Single Sign On Solution for the required applications 3. Extend the Single Sign On Solution with Advanced Authentication 3 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Agenda • Implement Secure Authentication above, or in addition to standard Password Authentication – Using Novell Modular Authentication Services • Implement a Single Sign On Solution for the required applications – Using Novell Secure. Login • Extend the Single Sign On Solution with Advanced Authentication • Demo 4 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Password Management Problem Poor end user experience Too many to remember! ***** johnnyjjohnson_04 jjohnson 077 johnnyj 294 johnmeister_192 johnnyjohn **** jj 122 bigjohn_92 johnny_thegolfer 413 **************************************** jjohnson 077 ****** johnnyj 294 ***** st. john_140 johnnyboy_313 johnathan_17 jjj_021 john_Johnson_45 ****** June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by: 5

What is NMAS? Secure Enterprise Access Management Novell Modular Authentication Services provides a framework in support of alternative authentication, which adds more security support for Workstation Access, while reducing the risk of information compromise within the organization by enabling strong authentication and advanced authorization Currently in its 2. 1 version, and shipping since 1999 While focused initially on just the Net. Ware platform, it has now delivered as a component of Novell’s e. Directory, and by definition is a cross-platform framework available on AIX, Linux, Net. Ware, Solaris, Windows NT, and Windows 2000. NMAS is included with e. Directory 8. 7. 1!!! 6 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

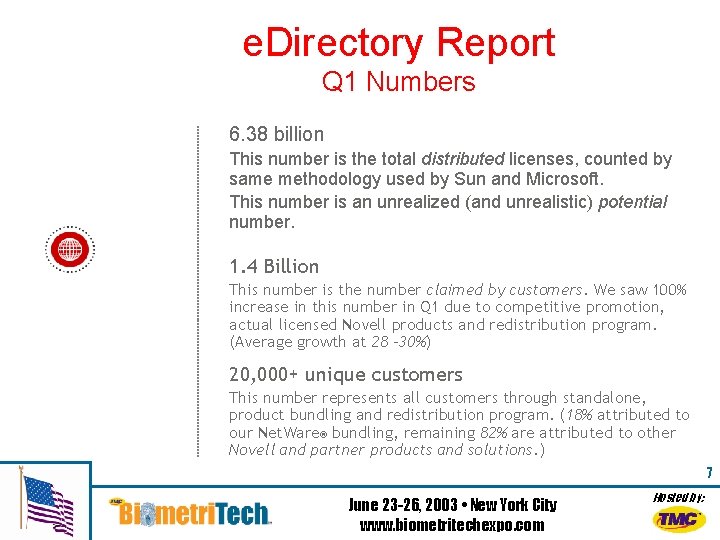
e. Directory Report Q 1 Numbers 6. 38 billion This number is the total distributed licenses, counted by same methodology used by Sun and Microsoft. This number is an unrealized (and unrealistic) potential number. 1. 4 Billion This number is the number claimed by customers. We saw 100% increase in this number in Q 1 due to competitive promotion, actual licensed Novell products and redistribution program. (Average growth at 28 -30%) 20, 000+ unique customers This number represents all customers through standalone, product bundling and redistribution program. (18% attributed to our Net. Ware® bundling, remaining 82% are attributed to other Novell and partner products and solutions. ) 7 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

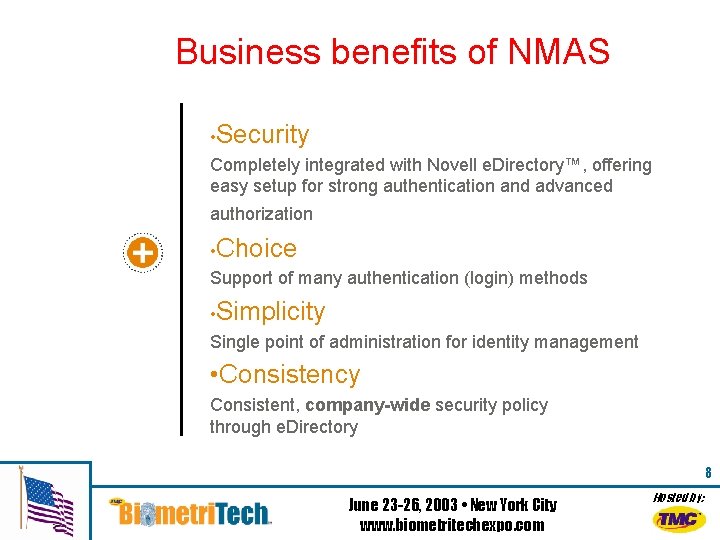
Business benefits of NMAS • Security Completely integrated with Novell e. Directory™, offering easy setup for strong authentication and advanced authorization • Choice Support of many authentication (login) methods • Simplicity Single point of administration for identity management • Consistency Consistent, company-wide security policy through e. Directory 8 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

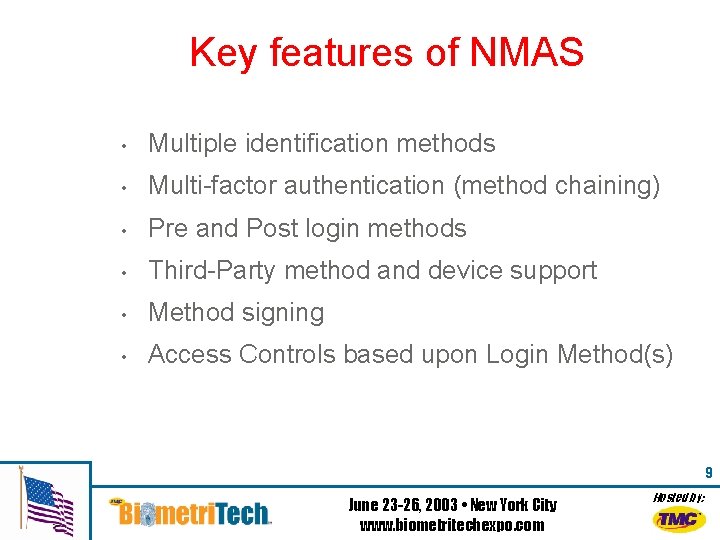
Key features of NMAS • Multiple identification methods • Multi-factor authentication (method chaining) • Pre and Post login methods • Third-Party method and device support • Method signing • Access Controls based upon Login Method(s) 9 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

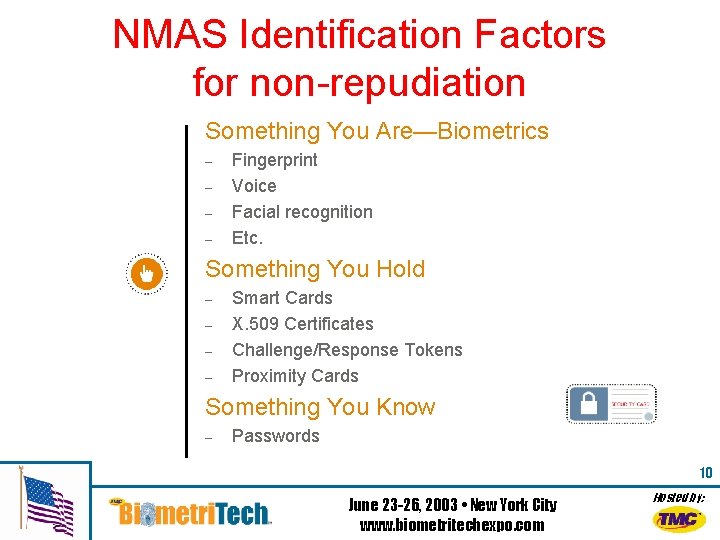
NMAS Identification Factors for non-repudiation Something You Are—Biometrics – – Fingerprint Voice Facial recognition Etc. Something You Hold – – Smart Cards X. 509 Certificates Challenge/Response Tokens Proximity Cards Something You Know – Passwords 10 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

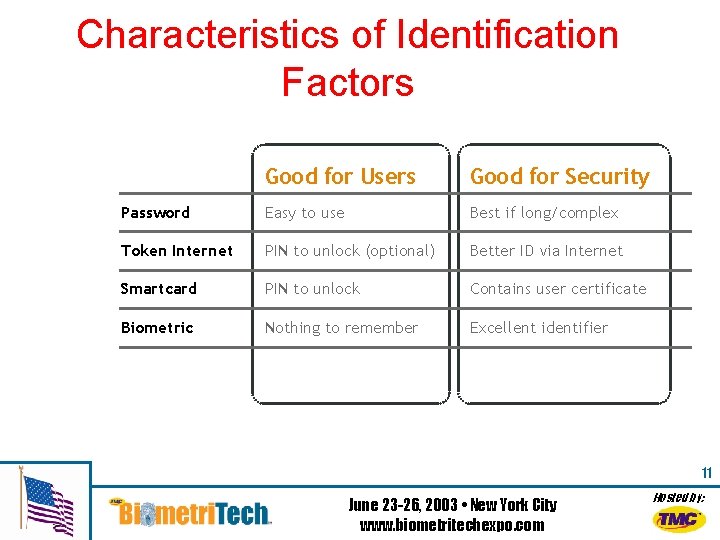
Characteristics of Identification Factors Good for Users Good for Security Password Easy to use Best if long/complex Token Internet PIN to unlock (optional) Better ID via Internet Smartcard PIN to unlock Contains user certificate Biometric Nothing to remember Excellent identifier 11 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Deception – Social Engineering • Kevin and Company was able to make an end run around all security device by using social engineering. • He has book describes how he and others were able to obtain passwords and more. 12 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

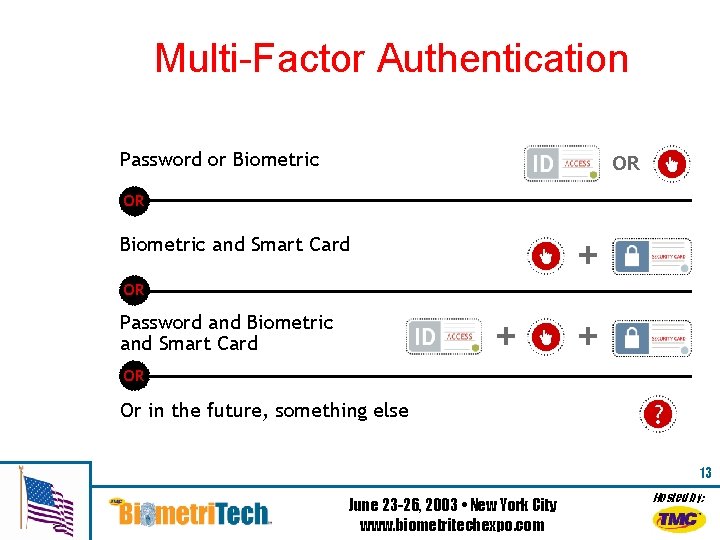
Multi-Factor Authentication Password or Biometric OR OR Biometric and Smart Card OR Password and Biometric and Smart Card OR Or in the future, something else 13 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Third-party Method and Device Support http: //www. novell. com/products/nmas/partners/ June 23 -26, 2003 • New York City www. biometritechexpo. com 14 Hosted by:

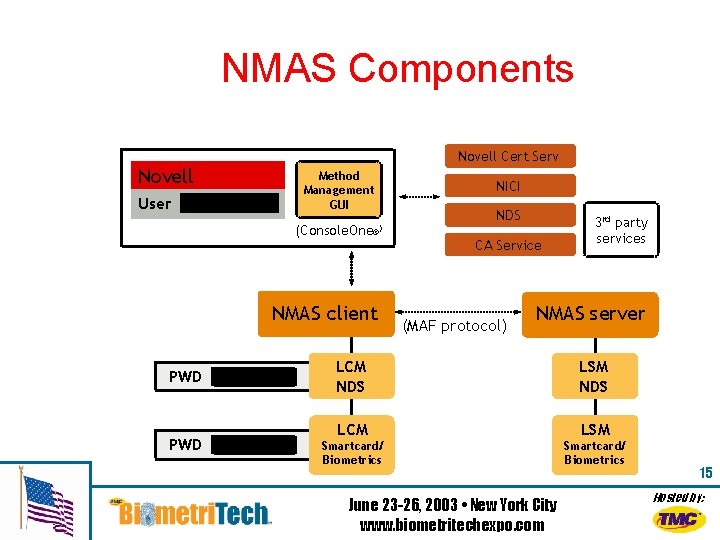
NMAS Components Novell User Novell Cert Serv Method Management GUI (Console. One®) NMAS client PWD NICI NDS CA Service (MAF protocol) 3 rd party services NMAS server LCM ™ (Console. One ) NDS LSM NDS LCM LSM Smartcard/ Biometrics June 23 -26, 2003 • New York City www. biometritechexpo. com 15 Hosted by:

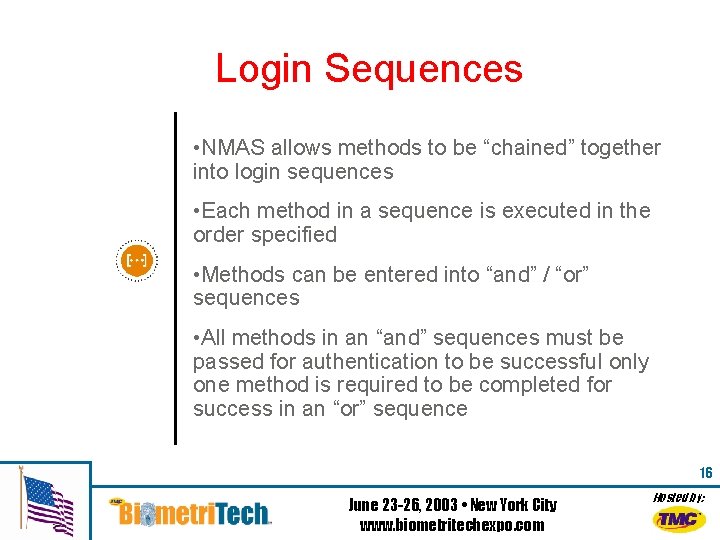
Login Sequences • NMAS allows methods to be “chained” together into login sequences • Each method in a sequence is executed in the order specified • Methods can be entered into “and” / “or” sequences • All methods in an “and” sequences must be passed for authentication to be successful only one method is required to be completed for success in an “or” sequence 16 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Login sequences are stored on a multi-valued attribute of the login policy object 17 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

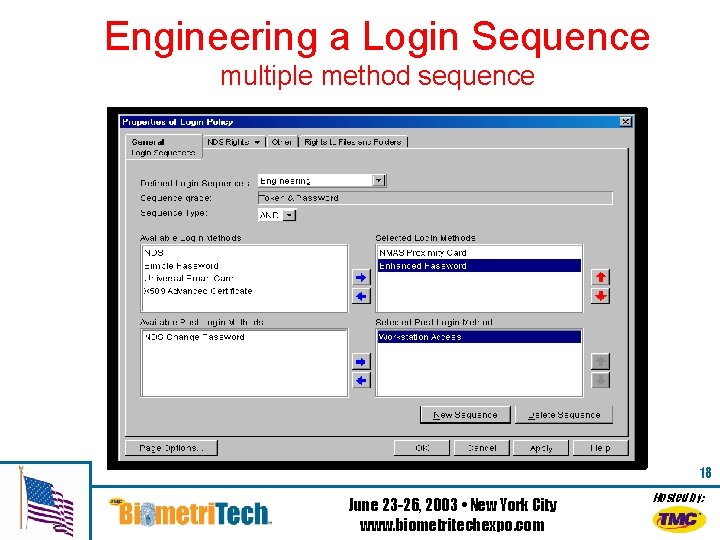
Engineering a Login Sequence multiple method sequence 18 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

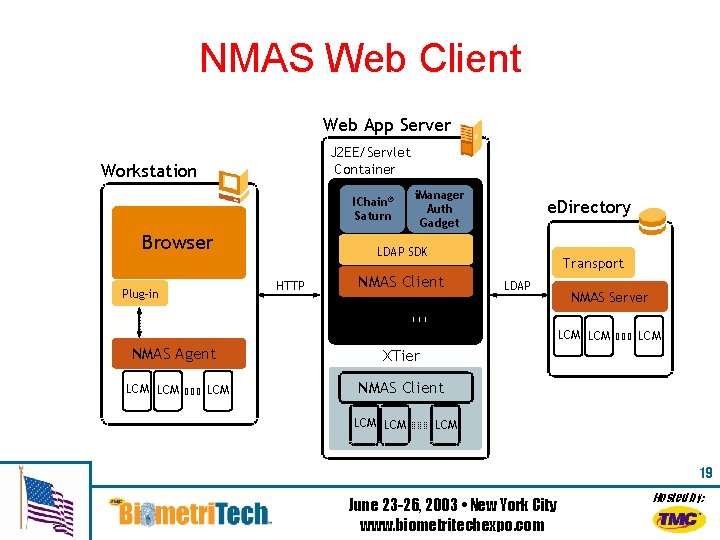
NMAS Web Client Web App Server J 2 EE/Servlet Container Workstation IChain® Saturn Browser e. Directory LDAP SDK HTTP Plug-in i. Manager Auth Gadget Transport NMAS Client LCM LDAP NMAS Server LCM LCM NMAS Agent LCM LCM XTier NMAS Client LCM LCM 19 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Authentication Grading • Use multi-factor authentication for better security • Novell Directory Services® (NDS®) password + token = password + token access • X. 509 cert + skin analysis = password + bio access • Fingerprint + smartcard + password = B + T + P access • Associate clearance levels depending on how the user authenticates • Set security labels on volumes controls visibility to single sign-on applications Currently Authentication Grading is only available for Net. Ware Volumes, but is targeted to go x. Platform 20 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

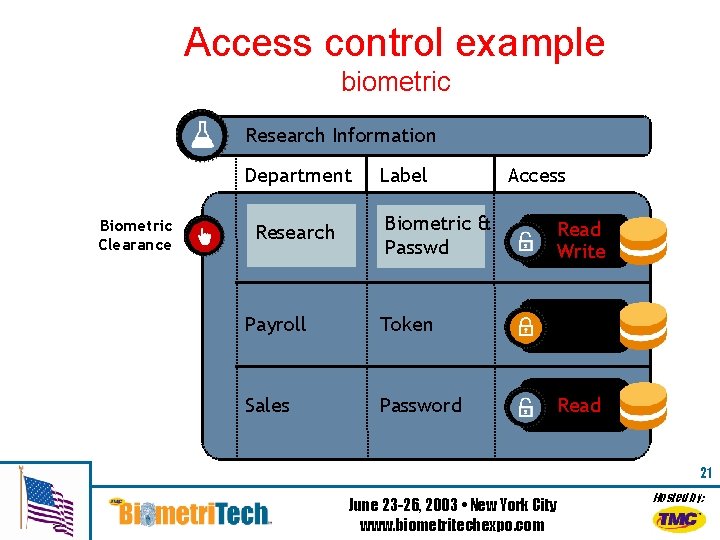
Access control example biometric Research Information Department Biometric Clearance Research Label Biometric & Passwd Payroll Token Sales Password Access Read Write Read 21 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

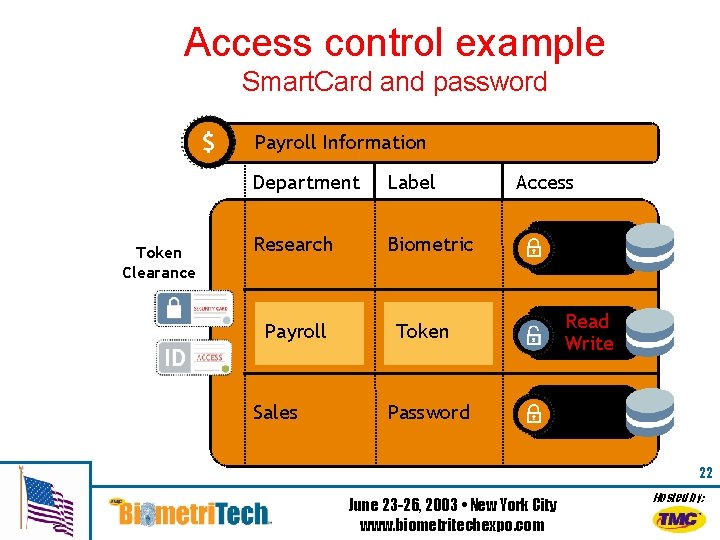
Access control example Smart. Card and password Payroll Information Token Clearance Department Label Research Biometric Payroll Sales Access Token Read Write Password 22 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Agenda • Implement Secure Authentication above, or in addition to standard Password Authentication – Using Novell Modular Authentication Services • Implement a Single Sign On Solution for the required applications – Using Novell Secure. Login • Extend the Single Sign On Solution with Advanced Authentication • Demo 23 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

The Application Authentication Problem Too many interfaces! 24 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Single Sign-On Solution Novell Secure. Login A solution that single sign-on enables Windows, web, Citrix/Terminal Server, and host-based applications • Solves 95% of password management problems (IDC) • #1 Market Share Leader (IDC) • Originally created by Jason Hart at Protocom • For the past two years, has been OEMed by Novell • 25 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

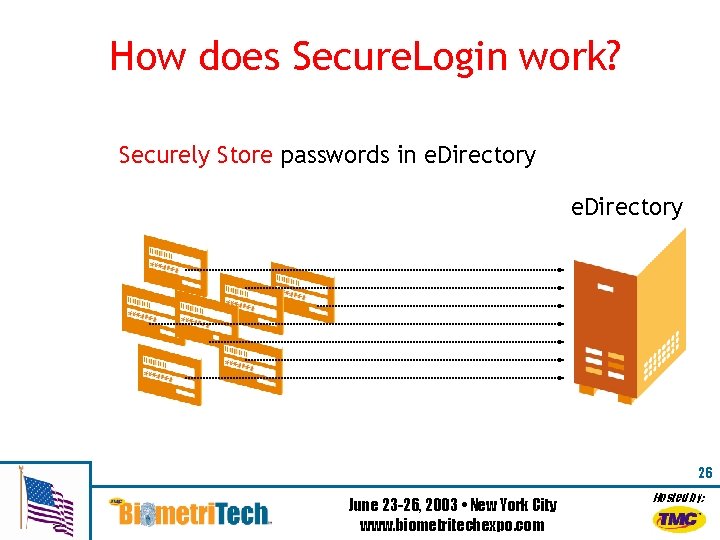
How does Secure. Login work? Securely Store passwords in e. Directory 26 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

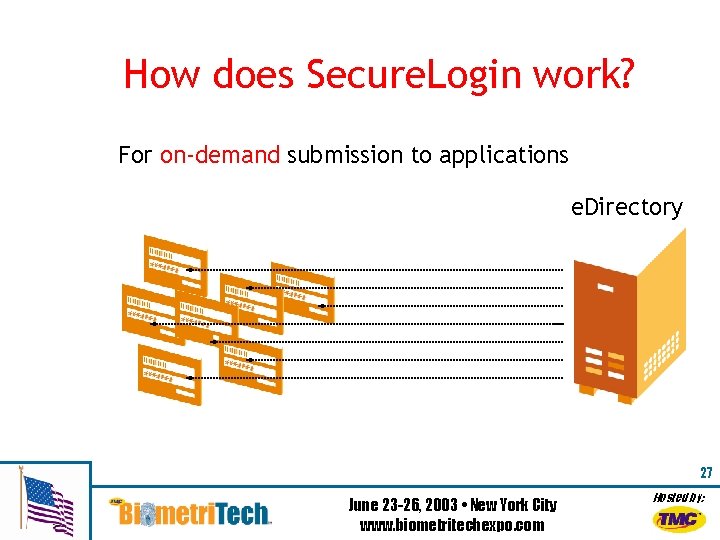
How does Secure. Login work? For on-demand submission to applications e. Directory 27 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

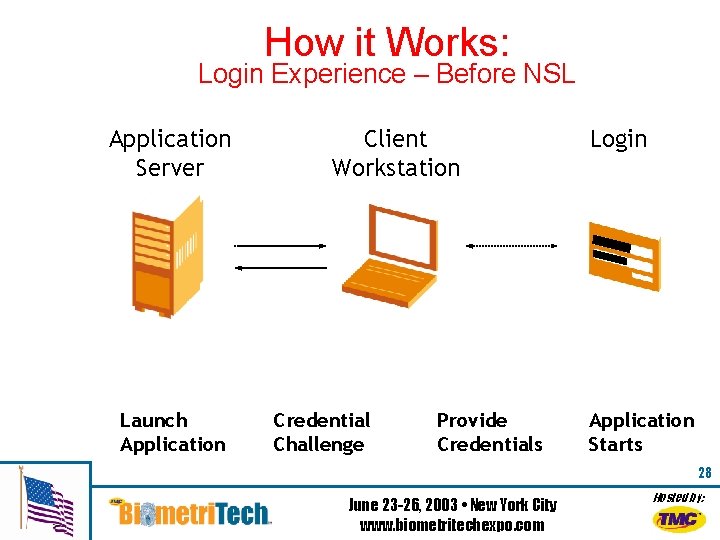
How it Works: Login Experience – Before NSL Application Server Launch Application Client Workstation Credential Challenge Provide Credentials Login Application Starts 28 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

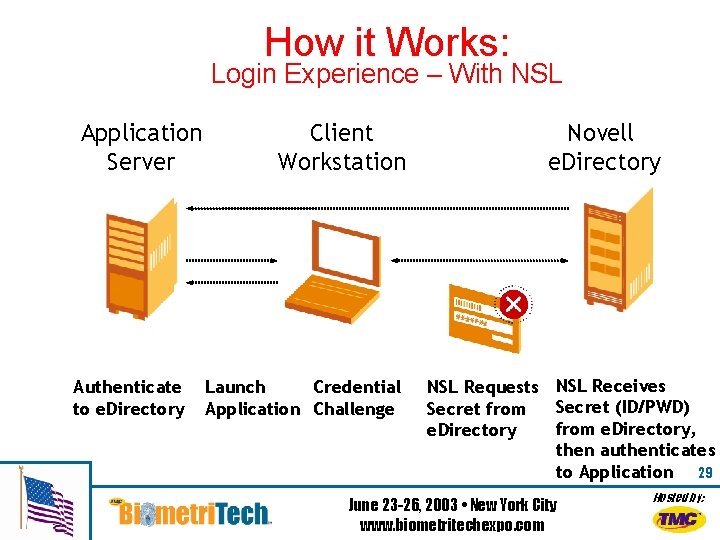
How it Works: Login Experience – With NSL Application Server Authenticate to e. Directory Client Workstation Launch Credential Application Challenge Novell e. Directory NSL Requests NSL Receives Secret (ID/PWD) Secret from e. Directory, e. Directory then authenticates to Application 29 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Agenda • Implement Secure Authentication above, or in addition to standard Password Authentication – Using Novell Modular Authentication Services • Implement a Single Sign On Solution for the required applications – Using Novell Secure. Login • Extend the Single Sign On Solution with Advanced Authentication • Demo 30 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Scripting Commands 46 Easy to remember scripting commands give you all the power you need to control your application! • • • AAVerify Add Break Call Change. Password Class Click Ctrl Delay Dialog / End. Dialog Display. Variables Divide • End. Script • Get. Text • Get. URL • Goto. URL • GT / LT / EQ • If / Else / End. If • Increment / Decrement • Kill. App • Local • Message. Box • Multiply • Parent / End. Parent • Pick. List. Add • Pick. List. Display • Read. Text • Reg. Split • Repeat / End. Repeat • Restrict. Variable • Run • Send. Key • Set. Cursor • Set. Focus • Set. Plat • Set. Prompt • Strcat • Sub / Endsub • Submit • Subtract • Title • Type • Wait. For. Focus • Wait. For. Text 31 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

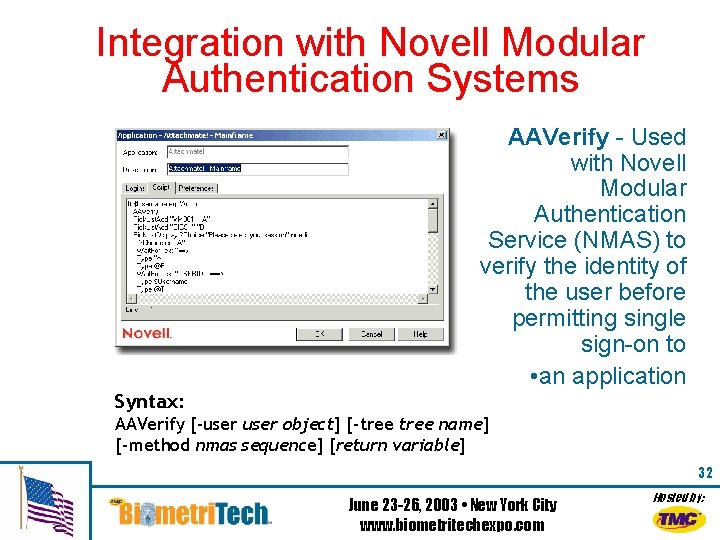
Integration with Novell Modular Authentication Systems Syntax: AAVerify - Used with Novell Modular Authentication Service (NMAS) to verify the identity of the user before permitting single sign-on to • an application AAVerify [-user object] [-tree name] [-method nmas sequence] [return variable] 32 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

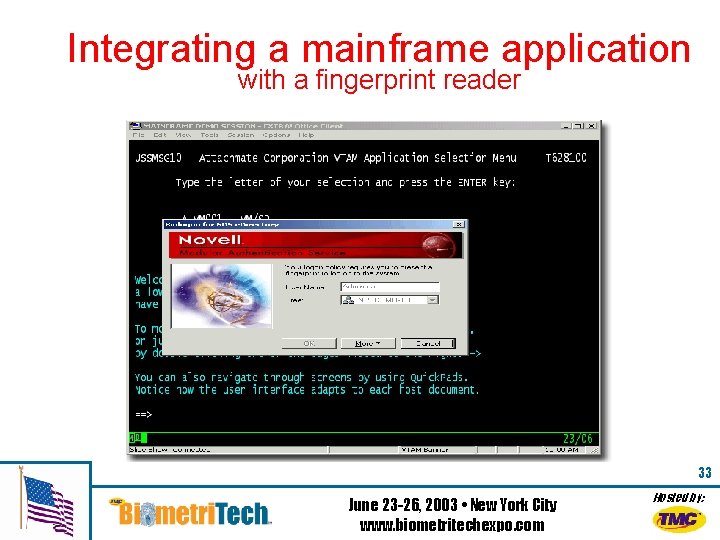
Integrating a mainframe application with a fingerprint reader 33 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

Demonstration and Questions/Answers 34 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by:

35 June 23 -26, 2003 • New York City www. biometritechexpo. com Hosted by: