Implementing Federated Identity Management across a Multicampus Statewide













- Slides: 25

Implementing Federated Identity Management across a Multi-campus Statewide System: The Texas Experience William A. Weems Assistant Vice President Academic Technology Associate Dean Information Technology Medical School U. Texas Health Science Center at Houston

BRIITE 20071004 Camelot in Cyberspace • Everyone has a single authentication credential • Permits authentication of one’s physical identity by any application to which it is presented. • If approved by the credentialed individual or required by law, the application may then request specific personal attributes from trusted sources of authorities. • The application utilizes the acquired personal attributes to make authorization decisions, activate additional workflow, create digital signatures, evaluate digital signatures, etc. 2

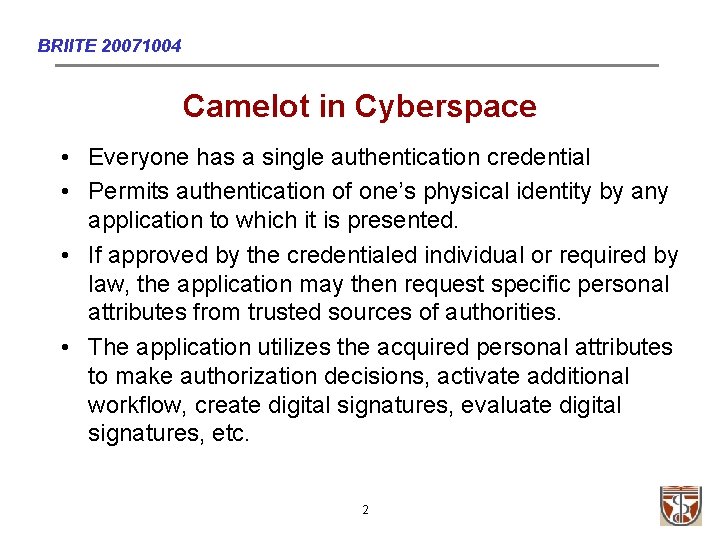
BRIITE 20071004 An authentication credential when presented to a relying party: 1. can only be activated by the certified person, 2. positively identifies the physical claimant, 3. positively identifies the certifying authority (CA) – i. e. the identity provider (Id. P) 4. provides a certified unique identifier issued to the vetted individual and registered with the CA, and 5. asserts a defined level of assurance (LOA) that the credential is presentable only by the person it authenticates. 3

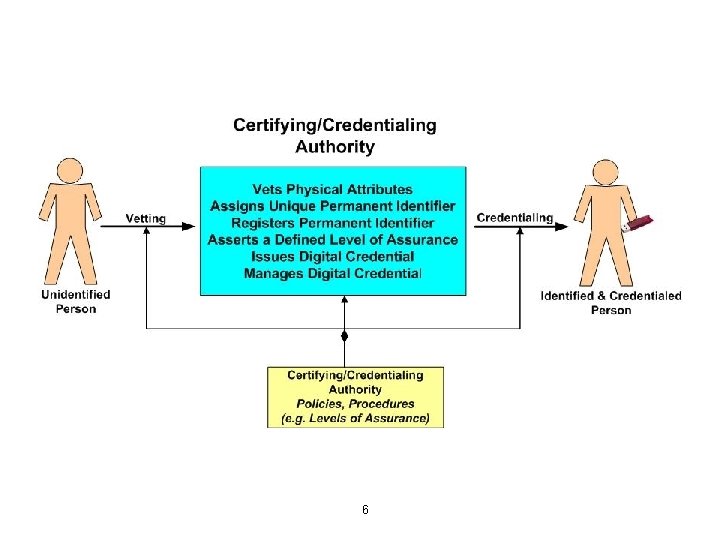
What is Identity? Concepts of “identity” vary widely, and the word is often imprecisely used. Within the context of Identity Management, there are two types of “identity”; and, they relate to authentication and authorization. 4

Two Kinds of Identity • Physical Identity - which is unique to only one person or entity. (Its certification is the responsibility of a certifying/credentialing authority) – – – • Facial picture, Fingerprints Retina Scan Identity Attributes – are a time-varying set of attributes associated with each unique individual. – – – Common name, Address, Institutional affiliations - e. g. faculty, student, staff, contractor, Specific group memberships, Roles, Etc. 5

6

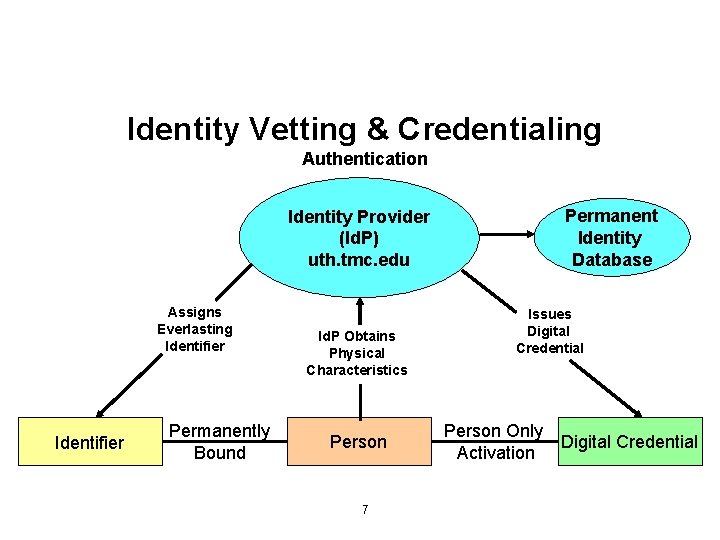
Identity Vetting & Credentialing Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Permanently Bound Id. P Obtains Physical Characteristics Person 7 Issues Digital Credential Person Only Activation Digital Credential

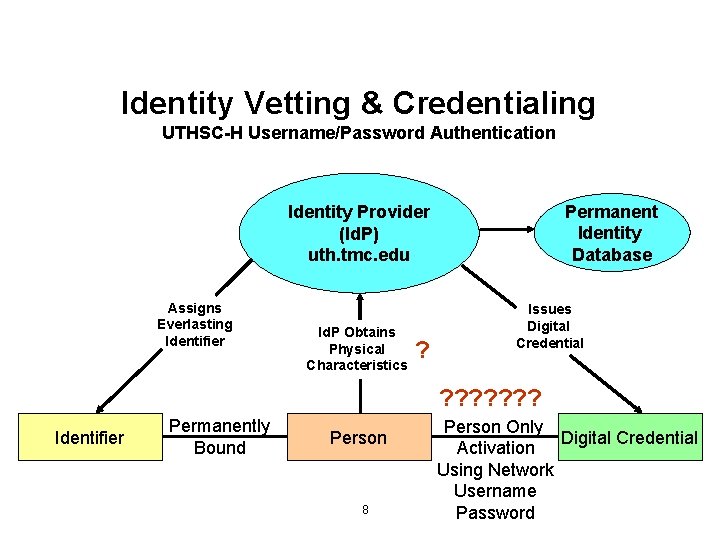
Identity Vetting & Credentialing UTHSC-H Username/Password Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Id. P Obtains Physical Characteristics ? Issues Digital Credential ? ? ? ? Identifier Permanently Bound Person 8 Person Only Digital Credential Activation Using Network Username Password

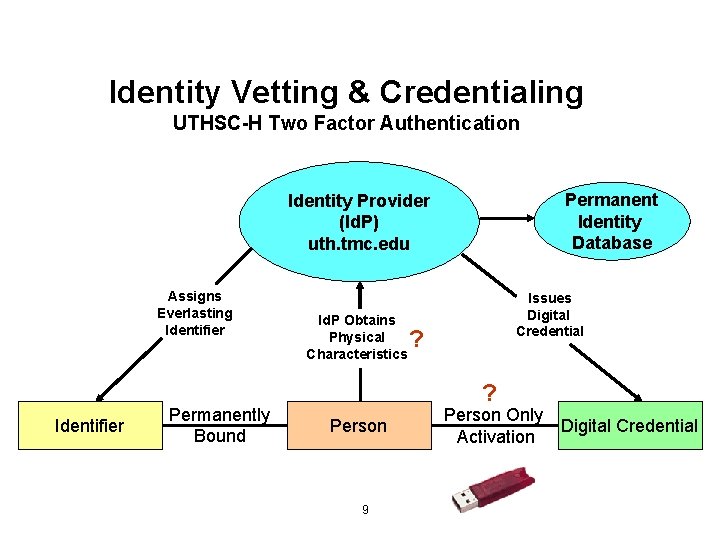
Identity Vetting & Credentialing UTHSC-H Two Factor Authentication Permanent Identity Database Identity Provider (Id. P) uth. tmc. edu Assigns Everlasting Identifier Permanently Bound Id. P Obtains Physical Characteristics Issues Digital Credential ? ? Person 9 Person Only Activation Digital Credential

Ideally, individuals would each like a single digital credential that can be securely used to authenticate his or her identity anytime authentication of identity is required to secure any transaction. 10

UTTouch e-Learning Grid Computing UT Institution A = Authentication of Some Kind = Authorization 11 = User Password ? ? ?

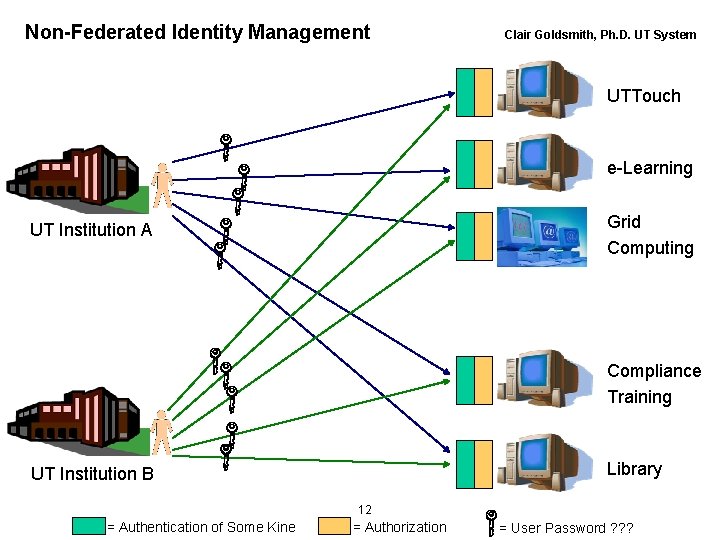
Non-Federated Identity Management Clair Goldsmith, Ph. D. UT System UTTouch e-Learning Grid Computing UT Institution A Compliance Training Library UT Institution B 12 = Authentication of Some Kine = Authorization = User Password ? ? ?

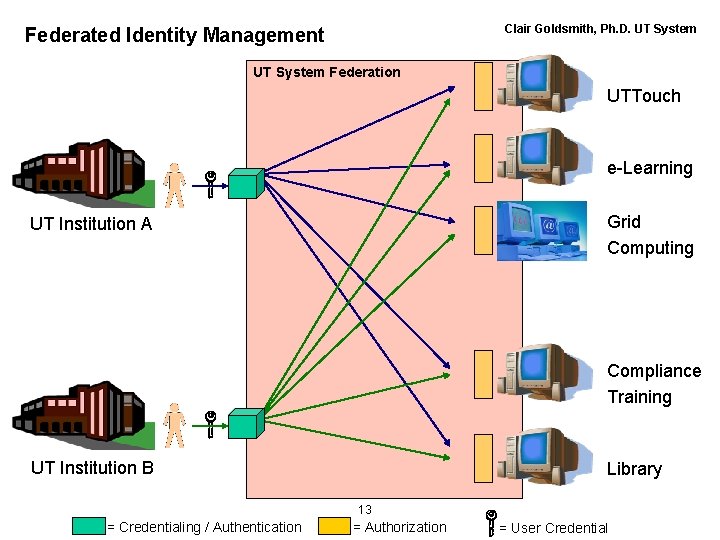
Clair Goldsmith, Ph. D. UT System Federated Identity Management UT System Federation UTTouch e-Learning Grid Computing UT Institution A Compliance Training UT Institution B Library 13 = Credentialing / Authentication = Authorization = User Credential

Today, most organizations and communities of interest recognize that Id. M systems and their associated policies and procedures are a necessity. However, nearly all Id. M projects currently utilize policies and procedures that are applicable only to a single enterprise or community of interest. 14

Federal E-Authentication Initiative http: //www. cio. gov/eauthentication/ • Levels of assurance (Different Requirements) – – Level 1 – e. g. no identity vetting Level 2 - e. g. specific identity vetting requirements Level 3 – e. g. cryptographic tokens required Level 4 – e. g. cryptographic hard tokens required • Credential Assessment Framework Suite (CAF) • Federal Bridge Certification Authority (FBCA) – http: //www. cio. gov/fbca/ – The FBCA is an information system that facilitates an entity accepting certificates issued by another entity for a transaction. 15

UT Federation Strategic Authentication Goals • Two types of authentication credentials – Single university ID (UID) and password (LOA 2 ) – Public Key Digital ID on Token (two-factor authentication using public/private keys) (LOA 3 => 4) • Digital Signatures – Authenticates senders – Guarantees messages are unaltered, i. e. message integrity – Provides for non-repudiation – Legal signature • Encryption of email and other documents • Highly Secure Access Control • Potential for inherent global trust 16

Some Core Id. M Concepts 1. Any time the same certified authentication credential is presented, relying parties can assume at some level of trust that the claimant is always the same physical person. 2. An authentication credential can be used to initially provision a system. 3. Once the credential is accepted, the relying party can, if so privileged, obtain certain “identity attributes” of a claimant from certified source(s) of authority. 4. Attribute exchange is determined by attribute release policies (ARPs) and attribute acceptance policies (AAPs). 17

18

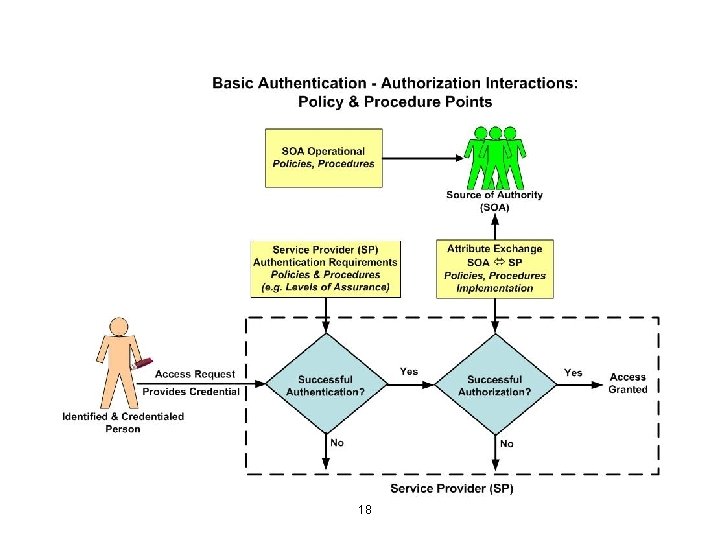
Source of Authority (SOA) Responsibilities An organizational entity officially responsible for identifying individuals having explicitly defined affiliations/attributes within an enterprise constitutes a “source of authority” (SOA). The SOA is responsible for • Identifying an individual, • Maintaining the appropriate records that define a person's affiliations/ attributes, • Providing others with information about the specifics of affiliation(s) and, • Determining if an affiliation/attribute is currently active or inactive 19

Identifiers & Privacy 1. Identifiers should NEVER be used as authenticators! 2. Personal attributes should NEVER be divulged to unapproved entities. 3. Collaboration requires that entities have identifiers. 4. edu. Person. Targeted. ID: A persistent, non-reassigned, privacy preserving identifier for a principal shared between a pair of coordinating entities. 5. What to do when multiple entities must collectively know that they are considering and/or interacting with the same person? 20

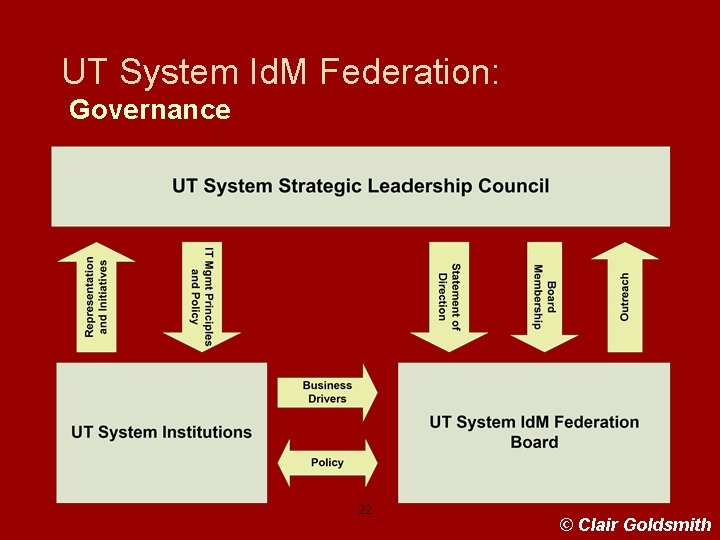
BRIITE 20071004 UT System Identity Management Federation • Established September 2006 • Operates Under Authority of the UT Board of Reagents • UT Id. M Federation Board of Appointed Members • Policy and Procedure Federation Documents • Current Membership the 16 U. Texas Institutions – 9 Academic Institutions – 6 Health Institutions – U. T. System • > 40 Federated Applications Operational • An Employee Benefits Application for Use By All employees under development 21

UT System Id. M Federation: Governance 22 © Clair Goldsmith

BRIITE 20071004 Governance: Issues to Ponder • The Technical implementation aspects of Federation can get way ahead of Policy and Governance • Governance entangled with power / autonomy conflicts • Priorities vary by institution • Conventions may be seen as dictates • Managing trust relationships is complex enough when dealing with institutions within the same system (among “family”. ) Complexity increases as diversity of membership increases 23 © Clair Goldsmith

BRIITE 20071004 UT System Id. M Federation Foundation Documents https: //idm. utsystem. edu/utfed/ 1. 2. 3. 4. 5. 6. Federation Charter Membership Agreement Operating Practices and Procedures Membership Operating Practices (MOP) Fee Schedule Common Identity Attributes 24

References 1. In. Common Federation a. http: //www. incommon. org/ 2. UC Trust: The University of California Identity Management Federation a. http: //www. ucop. edu/irc/itlc/uctrust/ 3. U. Texas System Identity Management Federation a. https: //idm. utsystem. edu/utfed/ 4. SAFE: Signature and Authentication For Everyone a. http: //www. safe-biopharma. org/ 25