Implementing and Testing IPsec NISTs Contributions and Future

Implementing and Testing IPsec: NIST’s Contributions and Future Developments Sheila Frankel Systems and Network Security Group NIST sheila. frankel@nist. gov RSA 2000 - Jan. 20, 2000

An SAT-type Analogy: The Question IPsec : Security a) foundation : house b) hammer : nail c) electron : chemistry d) government : progress RSA 2000 - Jan. 20, 2000 2

Topics • Overview of IPsec • NIST’s IPsec Reference Implementations • NIST’s IPsec Web-Based Interoperability Tester (IPsec-WIT) • Current Status of IPsec • Future Directions of IPsec RSA 2000 - Jan. 20, 2000 3
At Which Network Layer Should Security Be Provided? • Application Layer • Transport (Sockets) Layer • Internet Layer RSA 2000 - Jan. 20, 2000 4

Why Internet Layer Security? • Implement once, in a consistent manner, for multiple applications • Centrally-controlled access policy • Enable multi-level, layered approach to security RSA 2000 - Jan. 20, 2000 5
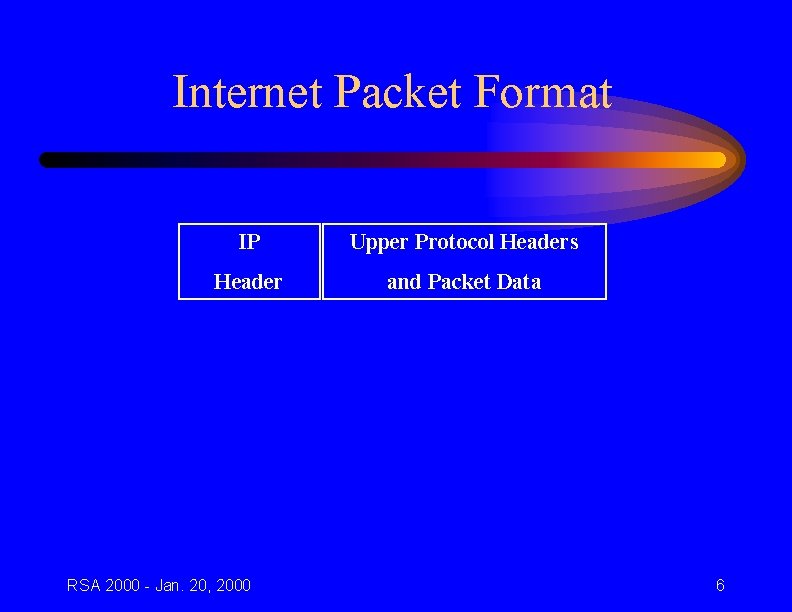
Internet Packet Format IP Upper Protocol Headers Header and Packet Data RSA 2000 - Jan. 20, 2000 6
Types of Security Provided by IPsec • • • Data Origin Authentication Connectionless Integrity Replay Protection Confidentiality (Encryption) Traffic Flow Confidentiality RSA 2000 - Jan. 20, 2000 7

Authentication Header (AH) • • • Data origin authentication Connectionless integrity Replay protection (optional) Transport or tunnel mode Mandatory algorithms: – – – HMAC-MD 5 HMAC-SHA 1 Other algorithms optional RSA 2000 - Jan. 20, 2000 8
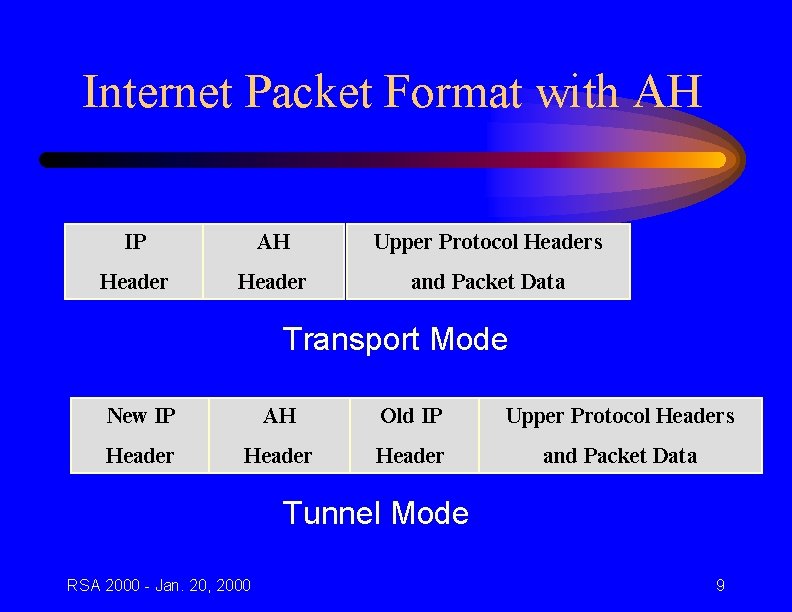
Internet Packet Format with AH IP AH Upper Protocol Headers Header and Packet Data Transport Mode New IP AH Old IP Upper Protocol Headers Header and Packet Data Tunnel Mode RSA 2000 - Jan. 20, 2000 9
Encapsulating Security Payload (ESP) • Confidentiality • Limited traffic flow confidentiality (tunnel mode only) • Data origin authentication • Connectionless integrity • Replay protection (optional) • Transport or tunnel mode RSA 2000 - Jan. 20, 2000 10
Encapsulating Security Payload (ESP) (continued) • Mandatory algorithms: – – – DES-CBC HMAC-MD 5 HMAC-SHA 1 Null Authentication algorithm Null Encryption algorithm Other algorithms optional RSA 2000 - Jan. 20, 2000 11
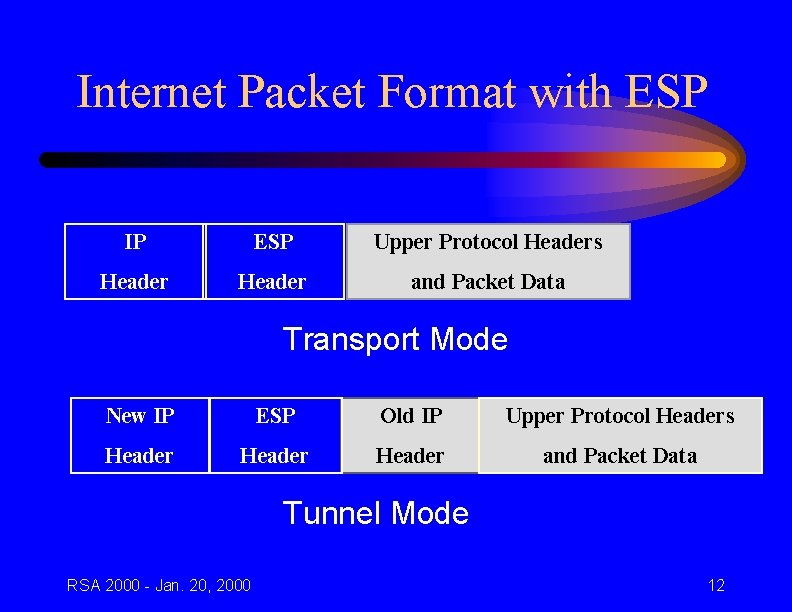
Internet Packet Format with ESP IP ESP Upper Protocol Headers Header and Packet Data Transport Mode New IP ESP Old IP Upper Protocol Headers Header and Packet Data Tunnel Mode RSA 2000 - Jan. 20, 2000 12
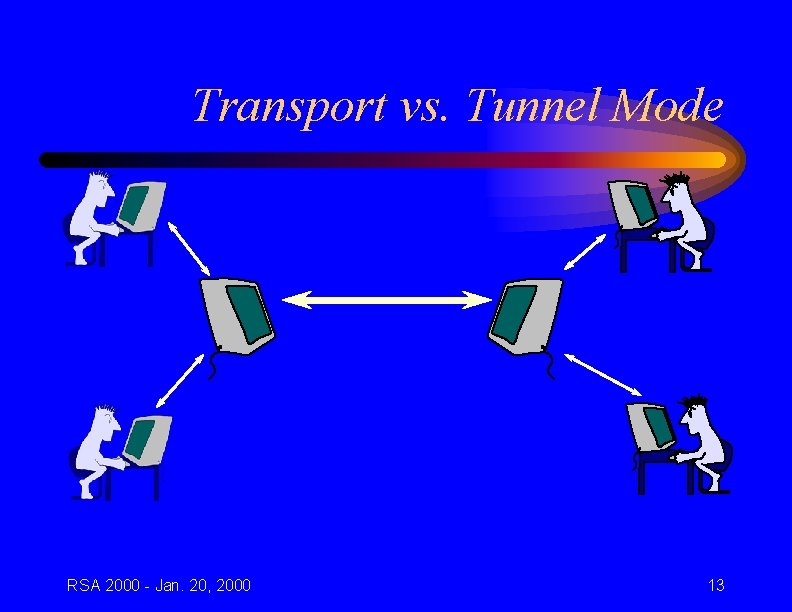
Transport vs. Tunnel Mode RSA 2000 - Jan. 20, 2000 13
Constructs Underlying IP Security • • Security Association (SA) Security Association Database (SAD) Security Parameter Index (SPI) Security Policy Database (SPD) RSA 2000 - Jan. 20, 2000 14

Internet Key Exchange (IKE) • Negotiate: – – Communication Parameters Security Features • Authenticate Communicating Peer • Protect Identity • Generate, Exchange, and Establish Keys in a Secure Manner • Delete Security Associations RSA 2000 - Jan. 20, 2000 15

Internet Key Exchange (IKE) (continued) • Threat Mitigation – Denial of Service – Replay – Man in Middle – Perfect Forward Secrecy • Usable by IPsec and other domains RSA 2000 - Jan. 20, 2000 16

Internet Key Exchange (IKE) (continued) • Components: – – – Internet Security Association and Key Management Protocol (ISAKMP) Internet Key Exchange (IKE, aka ISAKMP/Oakley) IP Security Domain of Interpretation (IPsec DOI) RSA 2000 - Jan. 20, 2000 17

IKE Negotiations - Phase 1 • Purpose: Establish ISAKMP SA (“Secure Channel”) • Steps (4 -6 messages exchanged): – Negotiate Security Parameters – Diffie-Hellman Exchange – Authenticate Identities • Main Mode vs. Aggressive Mode RSA 2000 - Jan. 20, 2000 18

IKE Negotiations - Phase 2 • Purpose: Establish IPsec SA • Steps (3 -5 messages exchanged): – Negotiate Security Parameters – Optional Diffie-Hellman Exchange – Final Verification • Quick Mode RSA 2000 - Jan. 20, 2000 19
NIST’s Contributions to IPsec • Cerberus - Linux-based reference implementation of Ipsec • Pluto. Plus - Linux-based reference implementation of IKE • IPsec-WIT - Web-based IPsec interoperability test facility RSA 2000 - Jan. 20, 2000 20

NIST’s Contributions to Ipsec (continued) • Goals: – – Enable smaller industry vendors to jump-start their entry into IPsec Facilitate ongoing interoperability testing of multiple IPsec implementations RSA 2000 - Jan. 20, 2000 21
IPsec-WIT: Motivation • Inter-operability of multiple implementations essential for IPsec to succeed • Existing test modalities – Interoperability “Bake-offs” – Pre-planned Web-based interoperability testing • Needed: spontaneous Web-based testing RSA 2000 - Jan. 20, 2000 22

User-Related Objectives • Accessible from remote locations • Available at any time • Require no modification to the tester’s IPsec implementation • Allow testers to resume testing at a later time • Configurable • Well-documented • RSA Easy to use 2000 - Jan. 20, 2000 23
Implementation Objectives • Simultaneous access by multiple users • Rapid, modular implementation • Easily modified and expanded as IPsec/IKE specifications evolve • Built around NIST’s IPsec/IKE Reference Implementations, Cerberus and Pluto. Plus RSA 2000 - Jan. 20, 2000 24

Implementation Objectives (continued) • Require minimal changes to Cerberus and Pluto. Plus • Operator intervention not required RSA 2000 - Jan. 20, 2000 25
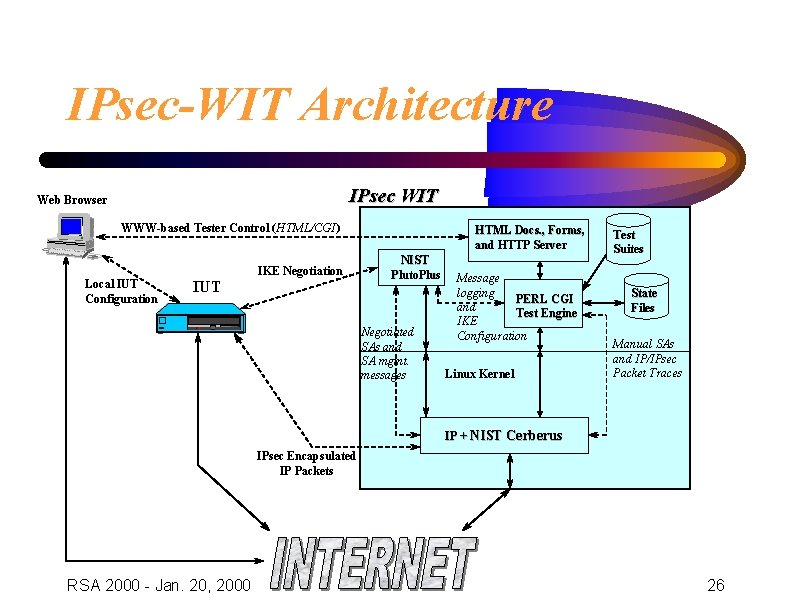
IPsec-WIT Architecture IPsec WIT Web Browser WWW-based Tester Control (HTML/CGI) Local IUT Configuration IKE Negotiation IUT HTML Docs. , Forms, and HTTP Server NIST Pluto. Plus Negotiated SAs and SA mgmt. messages Message logging PERL CGI and Test Engine IKE Configuration Linux Kernel Test Suites State Files Manual SAs and IP/IPsec Packet Traces IP + NIST Cerberus IPsec Encapsulated IP Packets RSA 2000 - Jan. 20, 2000 26
Implementation • • Perl cgi-bin tester HTML forms Executable test cases Output – Pluto. Plus: tracing the IKE negotiation – Cerberus: dumping the ping packets – expect command: color-coded output RSA 2000 - Jan. 20, 2000 27

Implementation (continued) • Individual tester files – Tester-specific parameters – Tester’s individual output – Storage and expiration RSA 2000 - Jan. 20, 2000 28

Current Capabilities • Key establishment: manual or IKE negotiation • IKE negotiation: Initiator or Responder • Peer authentication: pre-shared secrets • ISAKMP hash: MD 5 or SHA • ISAKMP encryption: DES or 3 DES • Diffie-Hellman exchange: 1 st Oakley group RSA 2000 - Jan. 20, 2000 29

Current Capabilities (continued) • Configurable port for IKE negotiation • IPsec AH algorithms: HMAC-MD 5 or HMAC-SHA 1 • IPsec ESP algorithms: – Encryption: DES, 3 DES, IDEA, RC 5, Blowfish, or ESP-Null – Authentication (optional): HMAC-MD 5 or HMAC-SHA 1 – Variable key length for RC 5 and Blowfish RSA 2000 - Jan. 20, 2000 30
Current Capabilities (continued) • IPsec encapsulation mode: transport or tunnel • Perfect Forward Secrecy (PFS) • Verbosity of IKE/IPsec output configurable • IPsec SA tested using “ping” command • Transport-mode SA: host-to-host RSA 2000 - Jan. 20, 2000 31

Current Capabilities (continued) • Tunnel-mode SA: host-to-host or host-togateway – Host-to-gateway SA tests communications with tester’s host behind gateway • Sample test cases for testers without a working IKE/IPsec implementation • Current/cumulative test results can be viewed via browser or emailed to tester RSA 2000 - Jan. 20, 2000 32

Limitations • Re-keying • Crash/disaster recovery • Complex policy-related scenarios RSA 2000 - Jan. 20, 2000 33

Lessons Learned • Voluntary interoperability testing is useful and used • Interoperability tests can also serve as conformance tests • Stateful protocols can be tested using a Web-based tester • “Standard” features are more useful than “cutting edge” RSA 2000 - Jan. 20, 2000 34

Lessons Learned (continued) • Some human intervention is required • Productive and informative multi-protocol interaction is challenging • Users do the “darnedest” - and most unexpected - things RSA 2000 - Jan. 20, 2000 35
Future Horizons - Pluto. Plus • Additional Diffie-Hellman groups • More complex policy options – Multiple proposals – Adjacent SA’s – Nested SA’s • Peer authentication: public key • PKI interaction and certificate exchanges RSA 2000 - Jan. 20, 2000 36
Future Horizons - IPsec-WIT • Test IPsec SA’s with UDP/TCP connections, rather than ICMP • Better diagnostics from underlying protocols RSA 2000 - Jan. 20, 2000 37

Futuristic Horizons • Negative testing • Robustness testing RSA 2000 - Jan. 20, 2000 38

Current Status of IPsec • Basic IPsec and IKE functionality defined in RFC’s • Add-ons and additional functionality defined in Internet Drafts • Numerous IPsec implementations in hardware and software • Periodic interoperability/conformance testing at IPsec “Bake-offs” RSA 2000 - Jan. 20, 2000 39

Current Status of IPsec (continued) • Deployed in Auto Industry Networks (ANX and ENX) • Used for Virtual Private Networks (VPNs) RSA 2000 - Jan. 20, 2000 40
Future Directions of IPsec • • PKI profiles for IPsec Policy configuration and control (IPSP) Secure remote access (IPSRA) Transport-friendly ESP (TF-ESP) RSA 2000 - Jan. 20, 2000 41

An SAT-type Analogy: The Answer ? ? To Be Announced ? ? RSA 2000 - Jan. 20, 2000 42

Contact/Usage Information • IPsec-WIT: http: //ipsec-wit. antd. nist. gov • Cerberus documentation: http: //www. antd. nist. gov/cerberus • Pluto. Plus documentation: http: //ipsec-wit. antd. nist. gov/newipsecdoc/pluto. html • For further information, contact: – Sheila Frankel: sheila. frankel@nist. gov – Rob Glenn: rob. glenn@nist. gov RSA 2000 - Jan. 20, 2000 43
- Slides: 43