Implementation of PermissionBased Sending PBS NSLP Network Traffic

Implementation of Permission-Based Sending (PBS) NSLP: Network Traffic Authorization draft-hong-nsis-pbs-nslp-02 Se Gi Hong*, Henning Schulzrinne*, Swen Weiland** *Columbia University, ** University of Goettingen Presented by Henning Schulzrinne March 2009 IETF 74 - NSIS 1

Overview of PBS NSLP • Objective – Preventing Denial-of-Service (Do. S) attacks and other forms of unauthorized traffic. • Authorization – Permission is granted by the intended receiver. – Permission represents the authority to send data. • Deny-by-default – In closed network (all end users have PBS NSLP functionalities) • The unauthorized traffic without permission are dropped at the first router by default. – In the open Internet (some end users do not have PBS NSLP functionalities) • The traffic from the end users who do not have PBS NSLP functionalities are rate-limited by default. March 2009 IETF 74 - NSIS 2

PBS NSLP Signaling Message • Two-way handshake – Query message • Sent by a sender to request permission. • Carry the flow identification (5 -tuple) of the data packet. • Flow identification: descriptor of flow – Permission message • • Sent by a receiver. Set up (grant), remove (revoke) and modify permission state. Carry permission, time limit, flow identification Trigger reaction mechanism against the attacks. • Soft-state – Robustness of the system – Periodic refreshment of the permission state • Peer-to-Peer delivery – The signaling messages are delivered in peer-to-peer fashion between the nodes that have PBS NSLP functionality March 2009 IETF 74 - NSIS 3

PBS NSLP architecture • On-path signaling (PBS NSLP processing/ GIST processing) – – Install and maintain permission state. Monitor attacks. Trigger reaction mechanism against the attacks. Distribute public key (X. 509 certificate) and session key • Authorization – Decide the grants of permission (amount of data volume) for a flow – Detect and identify the attack. – Decide the reaction mechanism against the attacks. • IPsec AH • Changing data path • Traffic management – Handle all incoming message. – IP packet filter drops the unauthorized packets. – Monitor data flow (check the total volume of the data flow). March 2009 IETF 74 - NSIS 4
Implementation structure • PBS NSLP / GIST – Finite state machine • FSM controls the state of each node. – Message creation and parsing • Signaling messages are created and parsed at each node that has a PBS NSLP functionality. – Public key distribution • Open. SSL: X. 509 certificate – Signaling message authentication • Open. SSL: The public key cryptography for the message authentication – GIST API • IPC (Unix socket): Communication between GIST and PBS NSLP • Selection of UDP/TCP/TLS: channel reliability and security March 2009 IETF 74 - NSIS 5
Implementation structure • Authorization – State table • Hashtable: permission state, IPsec state • Traffic management – Userspace IPsec module: A modular IPsec stack which relies on user space • netfilter queue module: get the packets (if a rule matches) to user space • Open. SSL: public key cryptography for IPsec authentication field – Netfilter/IPtables • libiptc: interface filter tables in the kernel space • iptables: filter IP packets – Linux kernel routing table • route: set up the data path (Linux kernel routing table is used). March 2009 IETF 74 - NSIS 6
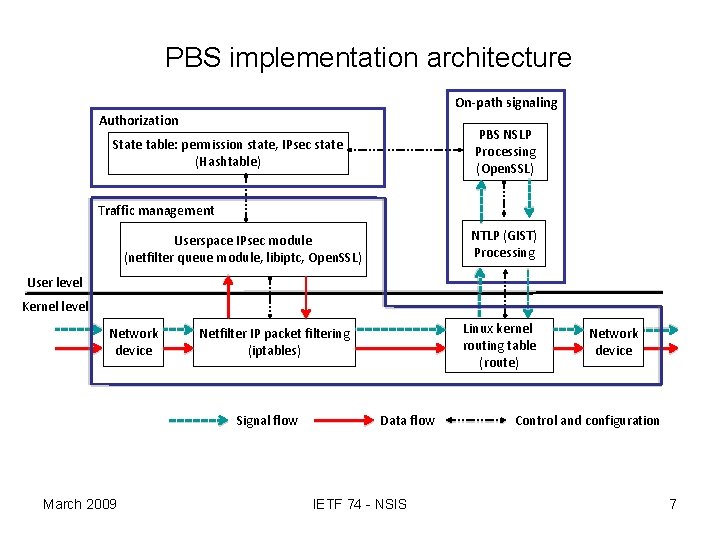
PBS implementation architecture On-path signaling Authorization PBS NSLP Processing (Open. SSL) State table: permission state, IPsec state (Hashtable) Traffic management NTLP (GIST) Processing Userspace IPsec module (netfilter queue module, libiptc, Open. SSL) User level Kernel level Network device Signal flow March 2009 Linux kernel routing table (route) Netfilter IP packet filtering (iptables) Data flow IETF 74 - NSIS Network device Control and configuration 7
CPU usage • • AMD Opteron Processor 148 2 GB RAM Single processor (2. 2 GHz CPU) Linux with kernel version 2. 6. 15
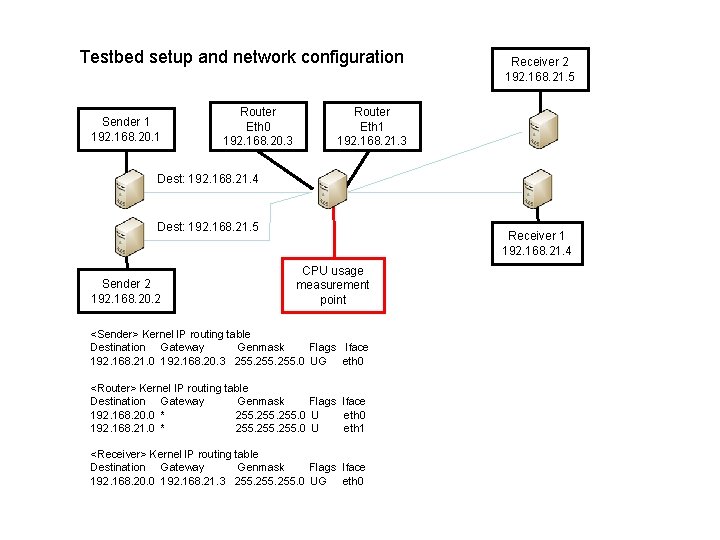
Testbed setup and network configuration Sender 1 192. 168. 20. 1 Router Eth 0 192. 168. 20. 3 Receiver 2 192. 168. 21. 5 Router Eth 1 192. 168. 21. 3 Dest: 192. 168. 21. 4 Dest: 192. 168. 21. 5 Sender 2 192. 168. 20. 2 Receiver 1 192. 168. 21. 4 CPU usage measurement point <Sender> Kernel IP routing table Destination Gateway Genmask Flags Iface 192. 168. 21. 0 192. 168. 20. 3 255. 0 UG eth 0 <Router> Kernel IP routing table Destination Gateway Genmask Flags Iface 192. 168. 20. 0 * 255. 0 U eth 0 192. 168. 21. 0 * 255. 0 U eth 1 <Receiver> Kernel IP routing table Destination Gateway Genmask Flags Iface 192. 168. 20. 0 192. 168. 21. 3 255. 0 UG eth 0
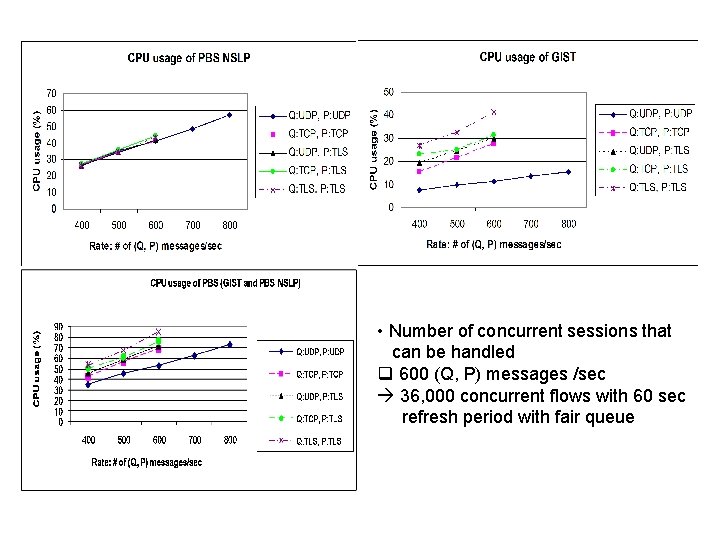
• Number of concurrent sessions that can be handled q 600 (Q, P) messages /sec 36, 000 concurrent flows with 60 sec refresh period with fair queue

Backup slides March 2009 IETF 74 - NSIS 11
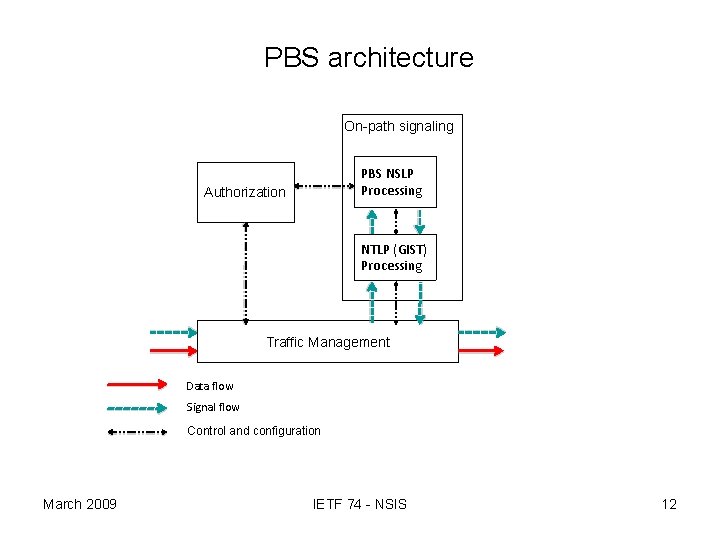
PBS architecture On-path signaling PBS NSLP Processing Authorization NTLP (GIST) Processing Traffic Management Data flow Signal flow Control and configuration March 2009 IETF 74 - NSIS 12
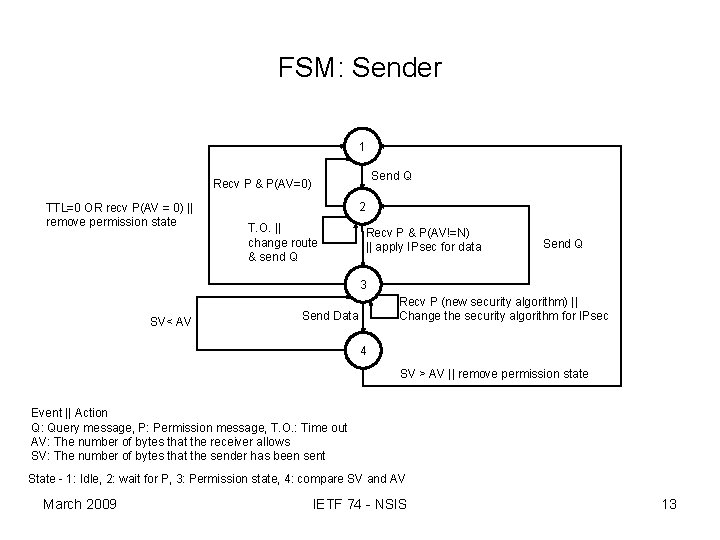
FSM: Sender 1 Send Q Recv P & P(AV=0) TTL=0 OR recv P(AV = 0) || remove permission state 2 T. O. || change route & send Q Recv P & P(AV!=N) || apply IPsec for data Send Q 3 SV< AV Recv P (new security algorithm) || Change the security algorithm for IPsec Send Data 4 SV > AV || remove permission state Event || Action Q: Query message, P: Permission message, T. O. : Time out AV: The number of bytes that the receiver allows SV: The number of bytes that the sender has been sent State - 1: Idle, 2: wait for P, 3: Permission state, 4: compare SV and AV March 2009 IETF 74 - NSIS 13
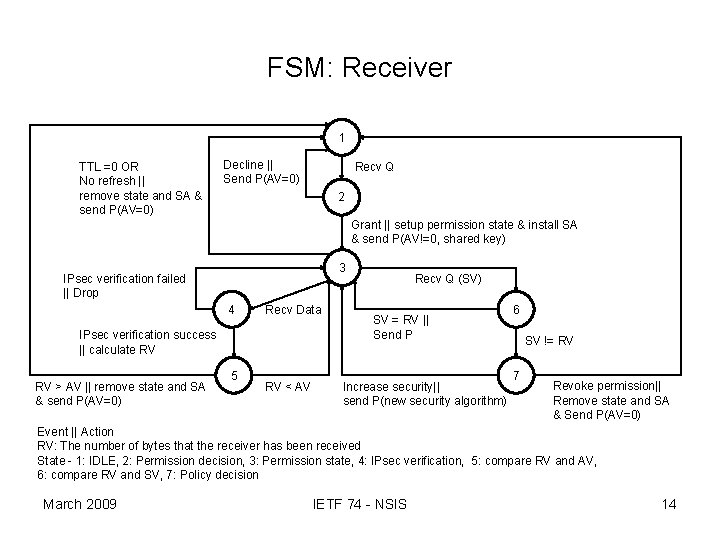
FSM: Receiver 1 TTL =0 OR No refresh || remove state and SA & send P(AV=0) Decline || Send P(AV=0) Recv Q 2 Grant || setup permission state & install SA & send P(AV!=0, shared key) 3 IPsec verification failed || Drop 4 Recv Data IPsec verification success || calculate RV RV > AV || remove state and SA & send P(AV=0) 5 RV < AV Recv Q (SV) SV = RV || Send P Increase security|| send P(new security algorithm) 6 SV != RV 7 Revoke permission|| Remove state and SA & Send P(AV=0) Event || Action RV: The number of bytes that the receiver has been received State - 1: IDLE, 2: Permission decision, 3: Permission state, 4: IPsec verification, 5: compare RV and AV, 6: compare RV and SV, 7: Policy decision March 2009 IETF 74 - NSIS 14
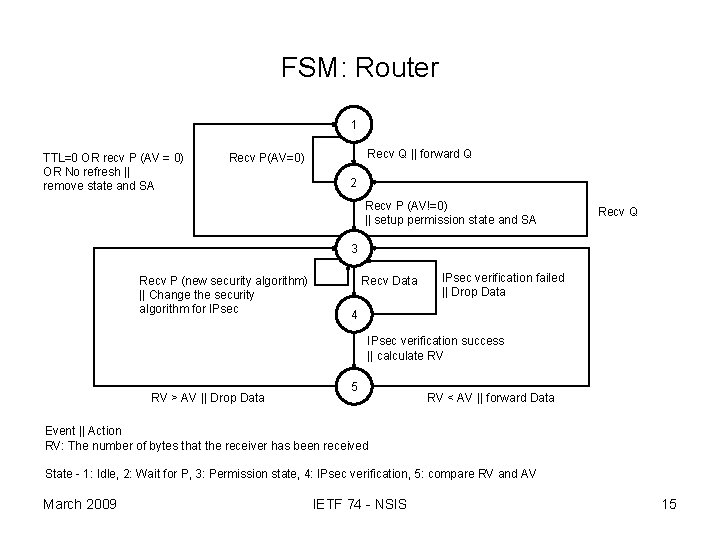
FSM: Router 1 TTL=0 OR recv P (AV = 0) OR No refresh || remove state and SA Recv Q || forward Q Recv P(AV=0) 2 Recv P (AV!=0) || setup permission state and SA Recv Q 3 Recv P (new security algorithm) || Change the security algorithm for IPsec Recv Data IPsec verification failed || Drop Data 4 IPsec verification success || calculate RV RV > AV || Drop Data 5 RV < AV || forward Data Event || Action RV: The number of bytes that the receiver has been received State - 1: Idle, 2: Wait for P, 3: Permission state, 4: IPsec verification, 5: compare RV and AV March 2009 IETF 74 - NSIS 15
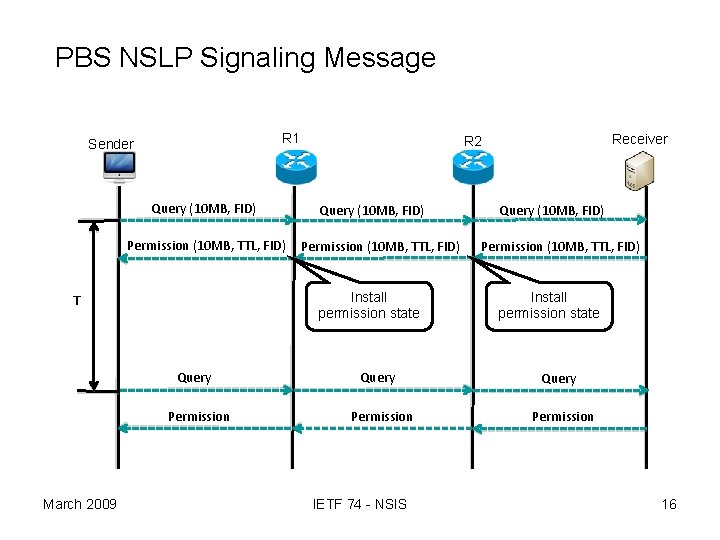
PBS NSLP Signaling Message 16 R 1 Sender Query (10 MB, FID) Permission (10 MB, TTL, FID) Query Permission March 2009 Query (10 MB, FID) Permission (10 MB, TTL, FID) Install permission state T Receiver R 2 Query Permission IETF 74 - NSIS Query (10 MB, FID) Permission (10 MB, TTL, FID) Install permission state Query Permission 16
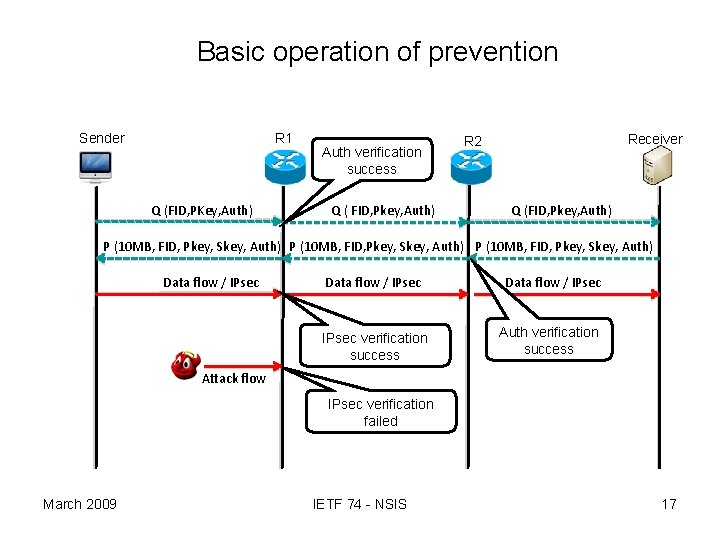
Basic operation of prevention 17 Sender R 1 Q (FID, PKey, Auth) Auth verification success Q ( FID, Pkey, Auth) Receiver R 2 Q (FID, Pkey, Auth) P (10 MB, FID, Pkey, Skey, Auth) Data flow / IPsec verification success Auth verification success Attack flow IPsec verification failed March 2009 IETF 74 - NSIS 17
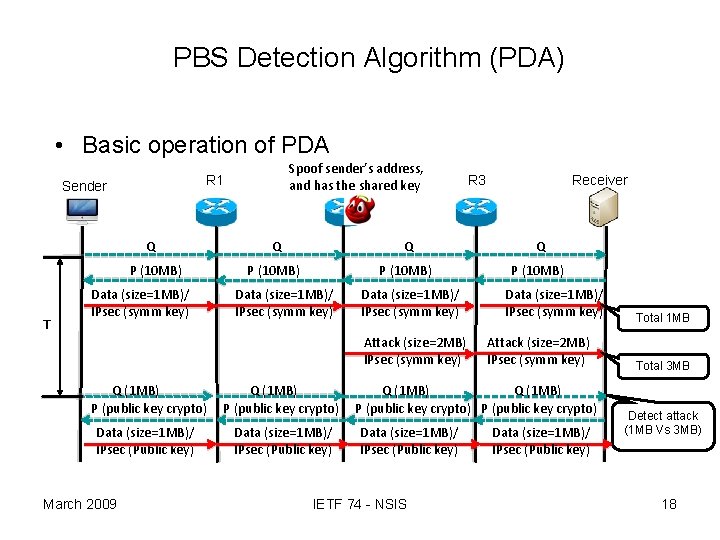
PBS Detection Algorithm (PDA) • Basic operation of PDA Sender Q P (10 MB) T Spoof sender’s address, and has the shared key R 1 Data (size=1 MB)/ IPsec (symm key) Receiver Q Q Q P (10 MB) Data (size=1 MB)/ IPsec (symm key) Attack (size=2 MB) IPsec (symm key) Q (1 MB) P (public key crypto) Data (size=1 MB)/ IPsec (Public key) March 2009 R 3 Data (size=1 MB)/ IPsec (symm key) Attack (size=2 MB) IPsec (symm key) Q (1 MB) P (public key crypto) Data (size=1 MB)/ IPsec (Public key) IETF 74 - NSIS Data (size=1 MB)/ IPsec (Public key) Total 1 MB Total 3 MB Detect attack (1 MB Vs 3 MB) 18
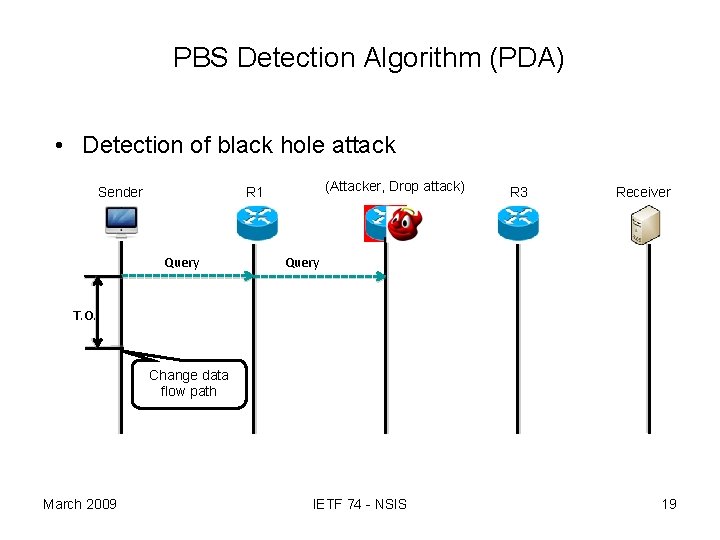
PBS Detection Algorithm (PDA) • Detection of black hole attack Sender (Attacker, Drop attack) R 1 Query R 3 Receiver Query T. O. Change data flow path March 2009 IETF 74 - NSIS 19
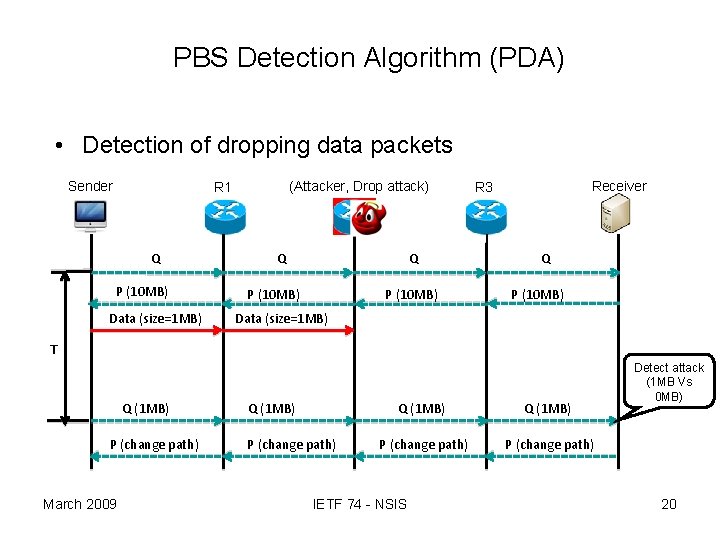
PBS Detection Algorithm (PDA) • Detection of dropping data packets Sender (Attacker, Drop attack) R 1 Q P (10 MB) Data (size=1 MB) Q Q P (10 MB) Receiver R 3 Q P (10 MB) Data (size=1 MB) T Q (1 MB) P (change path) March 2009 Q (1 MB) P (change path) IETF 74 - NSIS Detect attack (1 MB Vs 0 MB) 20
- Slides: 20