Impact of Plugins on Web Application Security James

Impact of Plugins on Web Application Security James Walden, Maureen Doyle Northern Kentucky University Students: Andrew Plunkett, Rob Lenhof, John Murray

Topics 1. 2. 3. 4. 5. 6. Web Application Security Plugins Plugin Vulnerabilities Comparing Core and Plugin Security Vulnerabilities by Category Conclusions IMI Security Symposium 2010 2
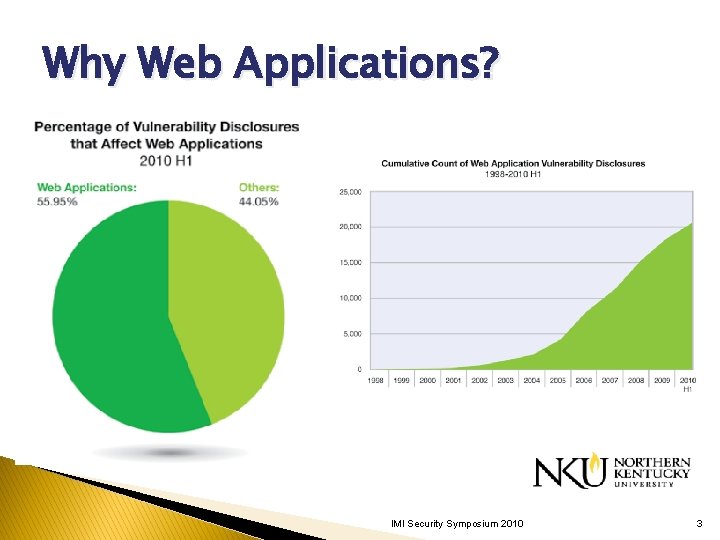
Why Web Applications? IMI Security Symposium 2010 3
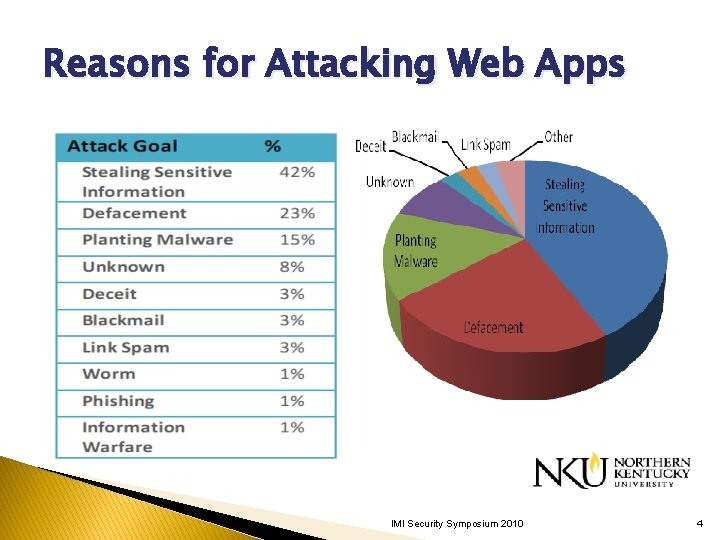
Reasons for Attacking Web Apps IMI Security Symposium 2010 4
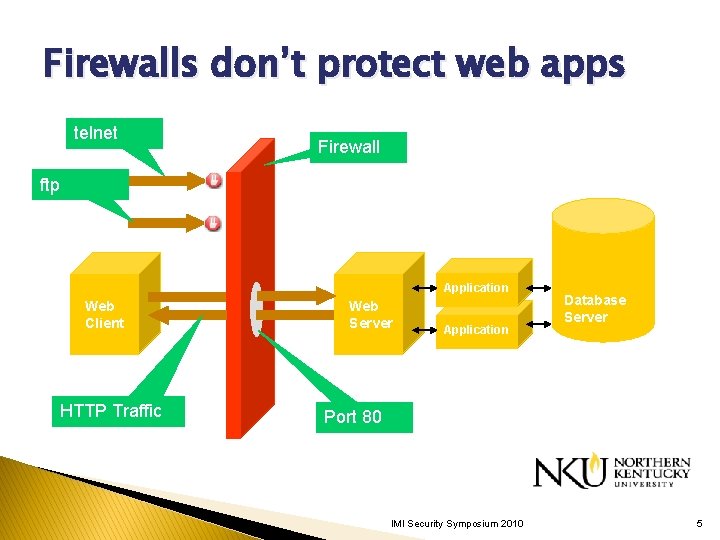
Firewalls don’t protect web apps telnet Firewall ftp Application Web Client HTTP Traffic Web Server Application Database Server Port 80 IMI Security Symposium 2010 5
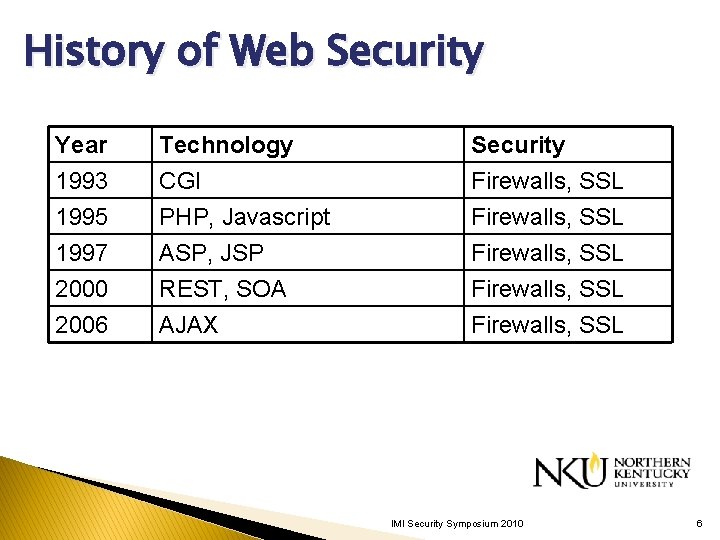
History of Web Security Year 1993 1995 1997 Technology CGI PHP, Javascript ASP, JSP Security Firewalls, SSL 2000 2006 REST, SOA AJAX Firewalls, SSL IMI Security Symposium 2010 6
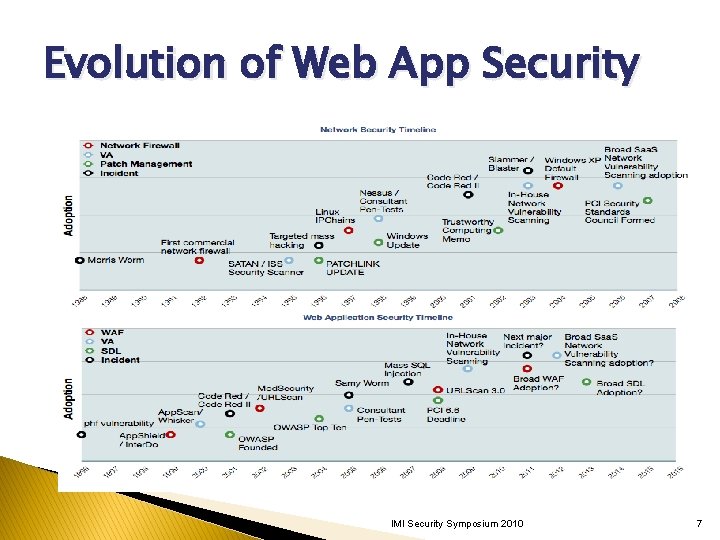
Evolution of Web App Security IMI Security Symposium 2010 7
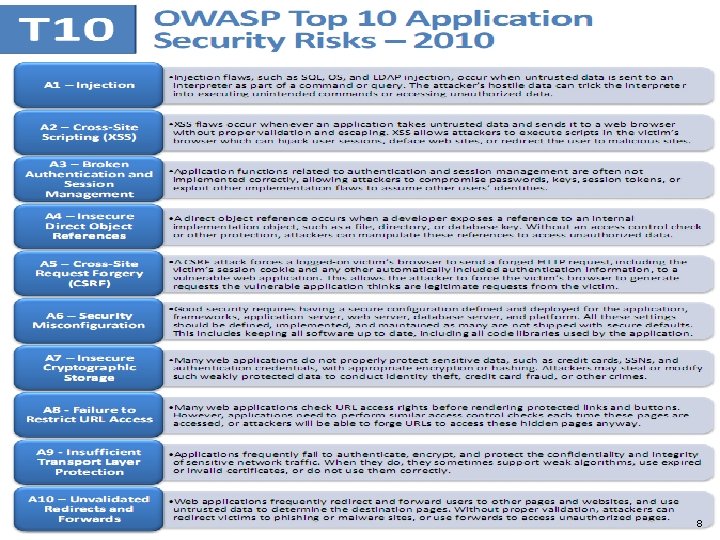
IMI Security Symposium 2010 8
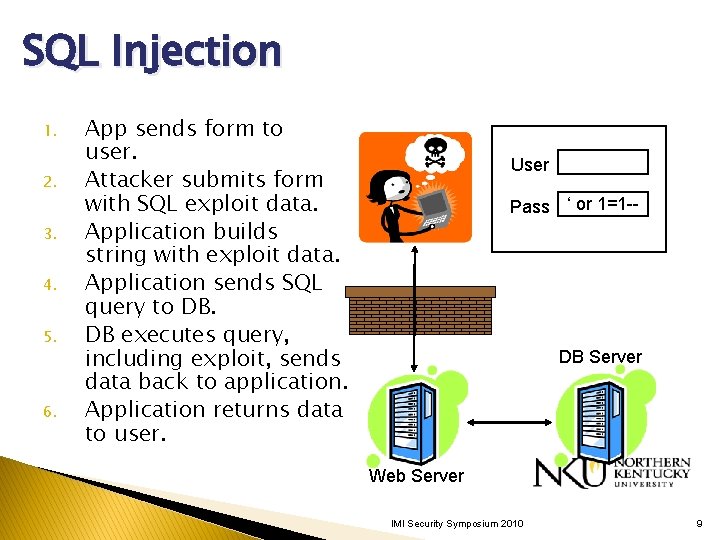
SQL Injection 1. 2. 3. 4. 5. 6. App sends form to user. Attacker submits form with SQL exploit data. Application builds string with exploit data. Application sends SQL query to DB. DB executes query, including exploit, sends data back to application. Application returns data to user. Attacker User Pass ‘ or 1=1 -- Firewall DB Server Web Server IMI Security Symposium 2010 9
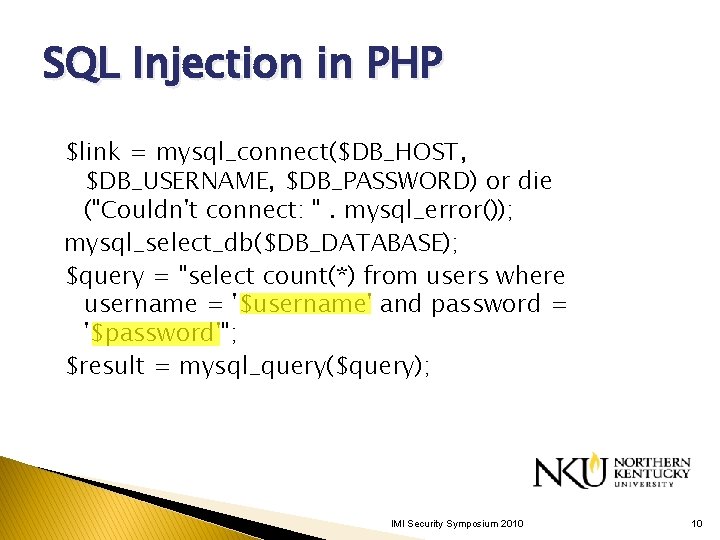
SQL Injection in PHP $link = mysql_connect($DB_HOST, $DB_USERNAME, $DB_PASSWORD) or die ("Couldn't connect: ". mysql_error()); mysql_select_db($DB_DATABASE); $query = "select count(*) from users where username = '$username' and password = '$password'"; $result = mysql_query($query); IMI Security Symposium 2010 10

SQL Injection Attack #1 Unauthorized Access Attempt: password = ’ or 1=1 -- SQL statement becomes: select count(*) from users where username = ‘user’ and password = ‘’ or 1=1 -Checks if password is empty OR 1=1, which is always true, permitting access. IMI Security Symposium 2010 11

SQL Injection Attack #2 Database Modification Attack: password = foo’; delete from table users where username like ‘% DB executes two SQL statements: select count(*) from users where username = ‘user’ and password = ‘foo’ delete from table users where username like ‘%’ IMI Security Symposium 2010 12
Exploits of a Mom http: //www. xkcd. com/327/ IMI Security Symposium 2010 13
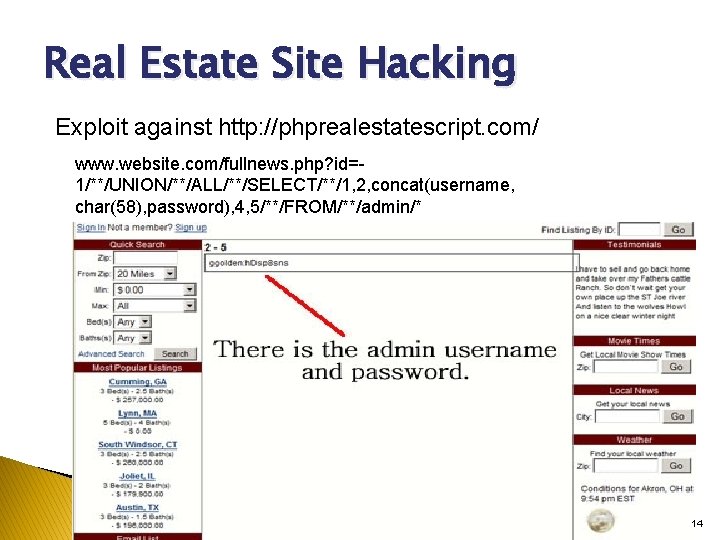
Real Estate Site Hacking Exploit against http: //phprealestatescript. com/ www. website. com/fullnews. php? id=1/**/UNION/**/ALL/**/SELECT/**/1, 2, concat(username, char(58), password), 4, 5/**/FROM/**/admin/* IMI Security Symposium 2010 14

Cross-Site Scripting (XSS) Attacker causes a legitimate web server to send user executable content (Javascript, Flash Active. Script) of attacker’s choosing. XSS used to obtain session ID for ◦ Bank site (transfer money to attacker) ◦ Shopping site (buy goods for attacker) ◦ E-mail Key ideas ◦ Attacker sends malicious code to server. ◦ Victim’s browser loads code from server and runs it. IMI Security Symposium 2010 15
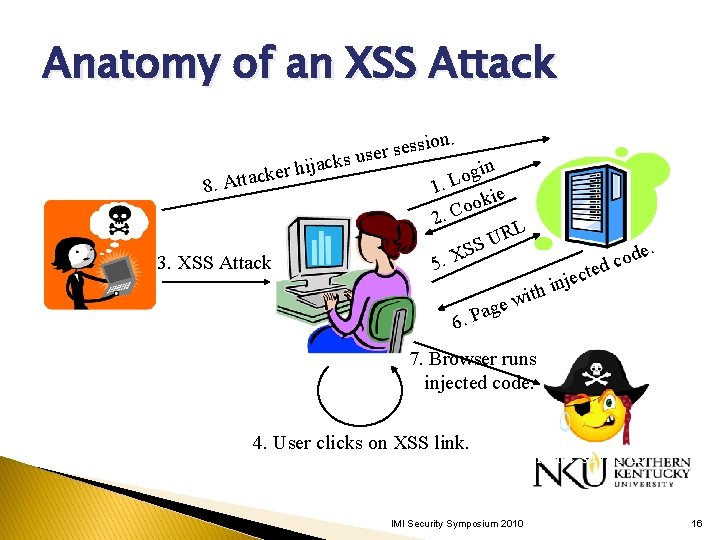
Anatomy of an XSS Attack Web Server sion. s e s r e s us Attacker ack j i h r e ck 8. Atta User 3. XSS Attack gin o L 1. kie o o 2. C RL U SS X. 5 6. P ith w age od c d cte e j n i e. 7. Browser runs injected code. 4. User clicks on XSS link. Evil site saves ID. IMI Security Symposium 2010 16
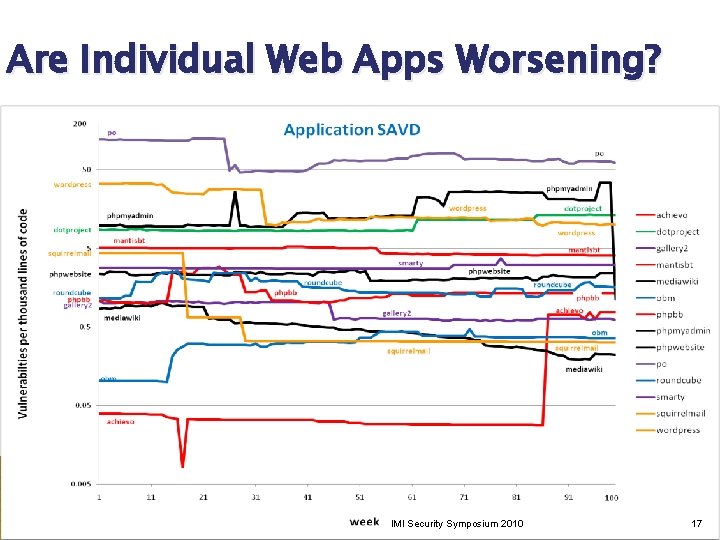
Are Individual Web Apps Worsening? IMI Security Symposium 2010 17
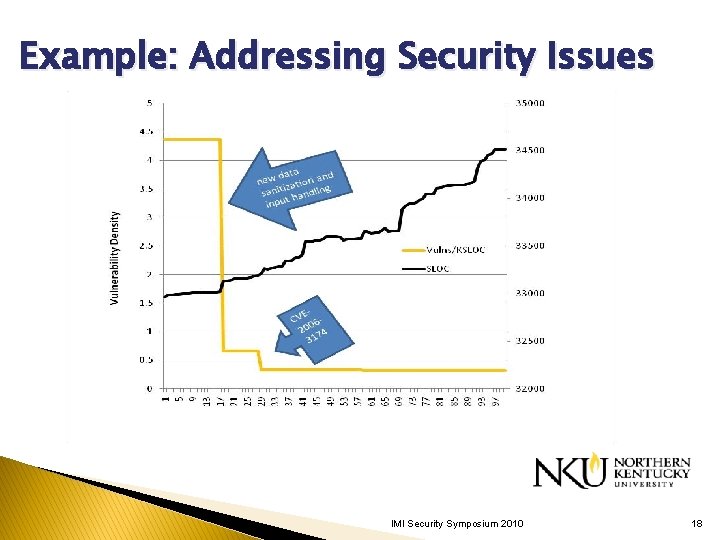
Example: Addressing Security Issues IMI Security Symposium 2010 18
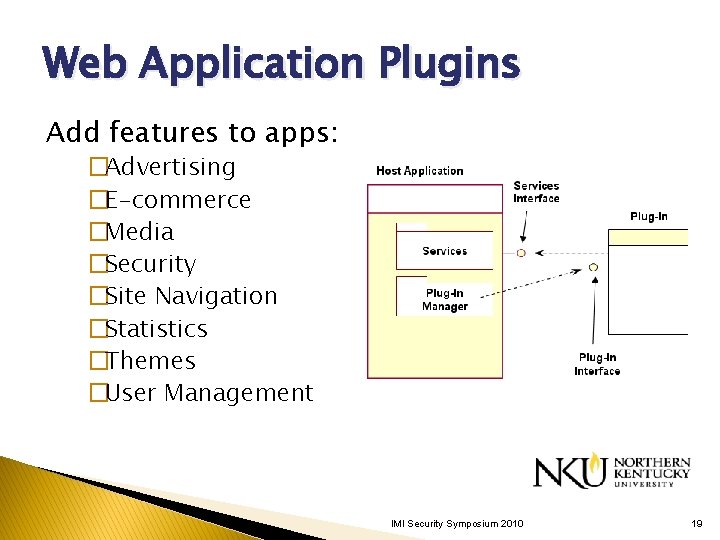
Web Application Plugins Add features to apps: �Advertising �E-commerce �Media �Security �Site Navigation �Statistics �Themes �User Management IMI Security Symposium 2010 19
What makes up a web application? Is it the core code or core code + plugins? �Some apps are almost always deployed with plugins. �Plugins are written by non-core developers. �Core site may or may not track plugin security. Some apps are packaged in distributions with plugins such as Drupal which has: �Open. Atrium (Development Seed) �Acquia Drupal �Open. Publish �Pressflow (Four Kitchens) IMI Security Symposium 2010 20

Research Objective Goal: Identify differences between security of core code and plugins for web applications. Research questions: 1. Are plugins less secure than core code? 2. How are vulnerabilities distributed across plugins? 3. How do different applications compare in terms of plugin security? IMI Security Symposium 2010 21
Open Source and PHP Security Open Source ◦ Evaluate source code that has no barriers to access ◦ 85% of businesses use open source software ◦ Probably all if embedded open source is counted, such as printers, routers, projectors, etc. PHP is most widely used language for OS web ◦ 35. 3% of web apps on Freshmeat are PHP, 14% Java ◦ Most popular apps written in PHP: Drupal, Joomla, Mediawiki, php. BB, Php. My. Admin, Word. Press IMI Security Symposium 2010 22

Open Source Web Apps are Targets IMI Security Symposium 2010 23
Open Source Web Applications Selection process �PHP web applications from freshmeat. net. �A central plugin repository. �Automatable downloads. �At least 10 plugins. Why PHP? �Most popular web applications written in PHP. �Can compare applications evenly. Range of projects � 12 projects met selection criteria. � 13, 535 plugins for these applications. �Plugins per app ranged from 10 to 8989 plugins. IMI Security Symposium 2010 24
Measuring Vulnerabilities Reported Vulnerabilities in NVD or OSVD ◦ Coarse-grained time evolution. ◦ Difficult to correlate with revision. ◦ Undercounts actual vulnerabilities. Dynamic Analysis ◦ Expensive. ◦ False positives and negatives. ◦ Must install and execute application. Static Analysis ◦ Expensive. ◦ False positives and negatives. ◦ Requires application installation IMI Security Symposium 2010 25
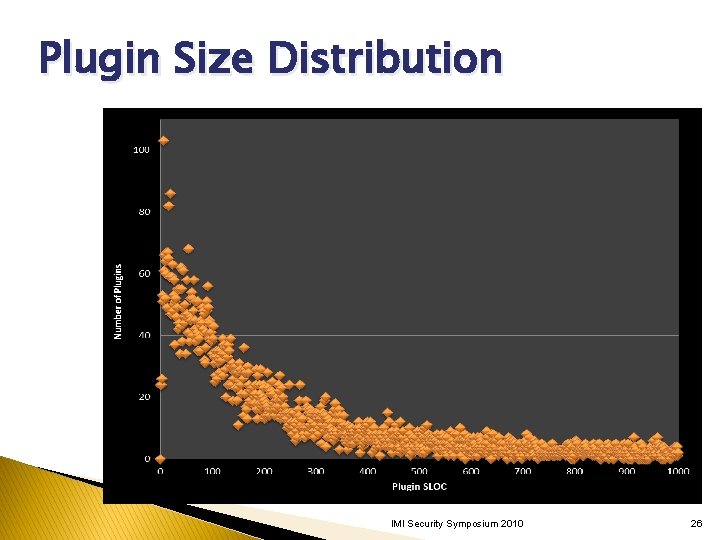
Plugin Size Distribution IMI Security Symposium 2010 26
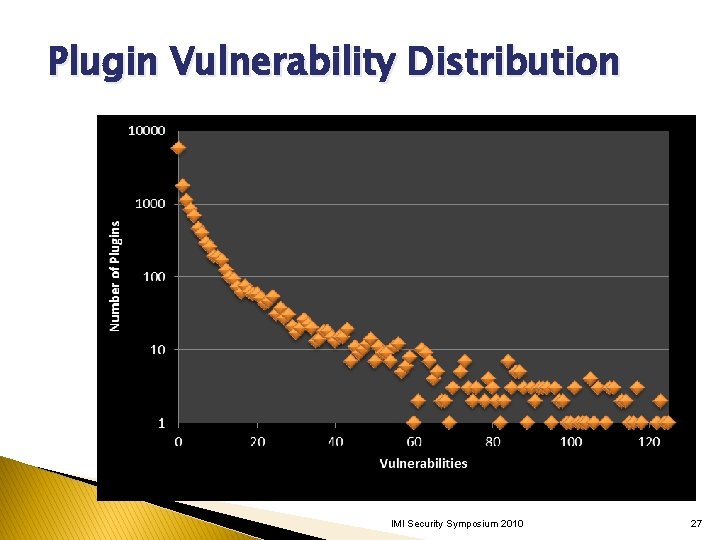
Plugin Vulnerability Distribution IMI Security Symposium 2010 27
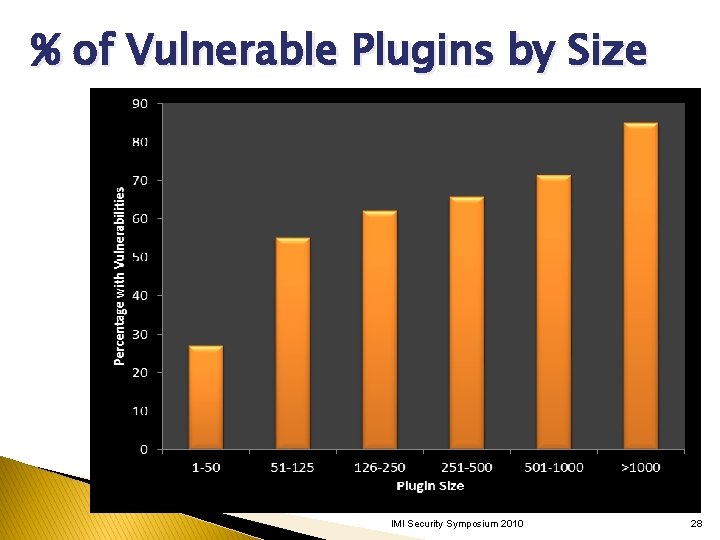
% of Vulnerable Plugins by Size IMI Security Symposium 2010 28
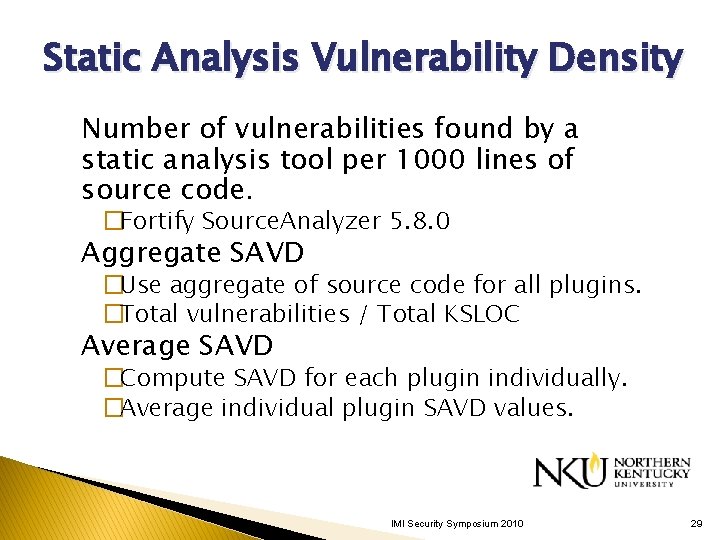
Static Analysis Vulnerability Density Number of vulnerabilities found by a static analysis tool per 1000 lines of source code. �Fortify Source. Analyzer 5. 8. 0 Aggregate SAVD �Use aggregate of source code for all plugins. �Total vulnerabilities / Total KSLOC Average SAVD �Compute SAVD for each plugin individually. �Average individual plugin SAVD values. IMI Security Symposium 2010 29
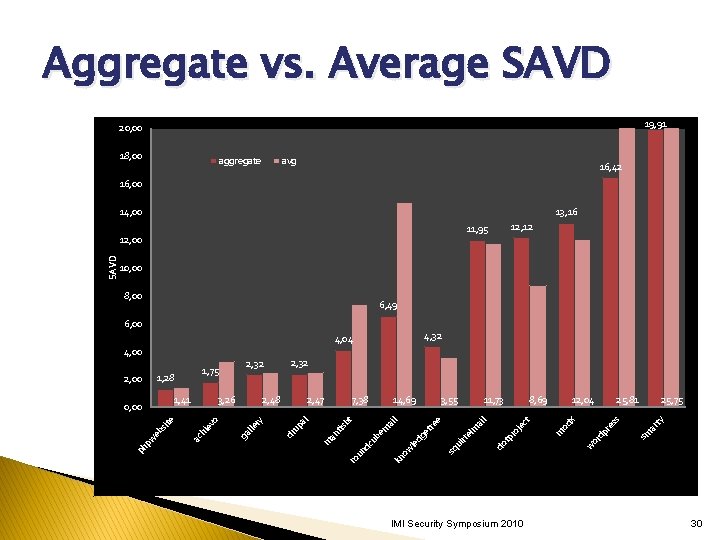
Aggregate vs. Average SAVD 19, 91 20, 00 18, 00 aggregate avg 16, 42 16, 00 14, 00 13, 16 10, 00 8, 00 6, 49 6, 00 4, 32 4, 04 2, 32 ar ty 25, 75 sm or dp re ss 25, 81 w m ro tp do m el irr sq u IMI Security Symposium 2010 12, 04 od x 8, 69 ai e re et dg le w dc ub em 11, 73 je ct 3, 55 l 14, 69 ai l t un isb ro an t m up 7, 38 kn o 2, 47 al 2, 48 ry ev hi ac sit e eb pw 3, 26 o 1, 41 0, 00 ga lle 1, 28 2, 00 2, 32 1, 75 dr 4, 00 ph SAVD 12, 12 11, 95 12, 00 30

Do plugins make a site less secure? Core code developed by small core team. �Team experienced with core code over years. �May or may not be paid full-time developers. �Most sites have some form of security information. Plugins developed by many people. �Wide variety of programming experience. �Few develop more than one plugin and so have little experience with application compared to core team. �Few plugins mention security unless a vulnerability has been previously reported. IMI Security Symposium 2010 31
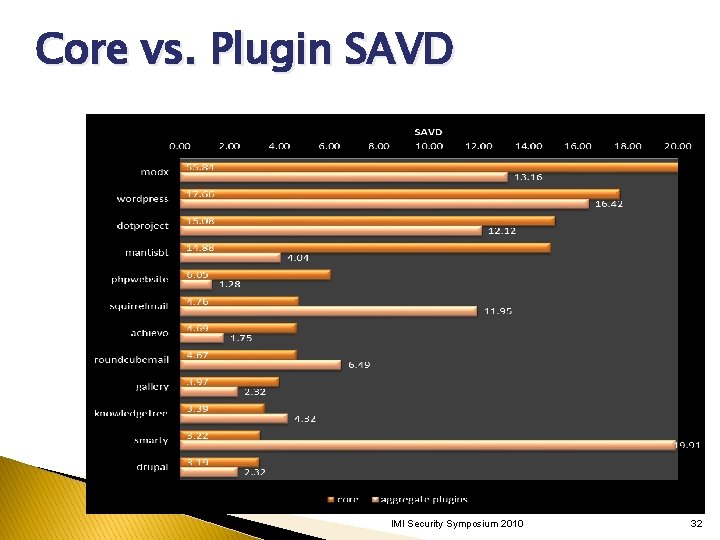
Core vs. Plugin SAVD IMI Security Symposium 2010 32
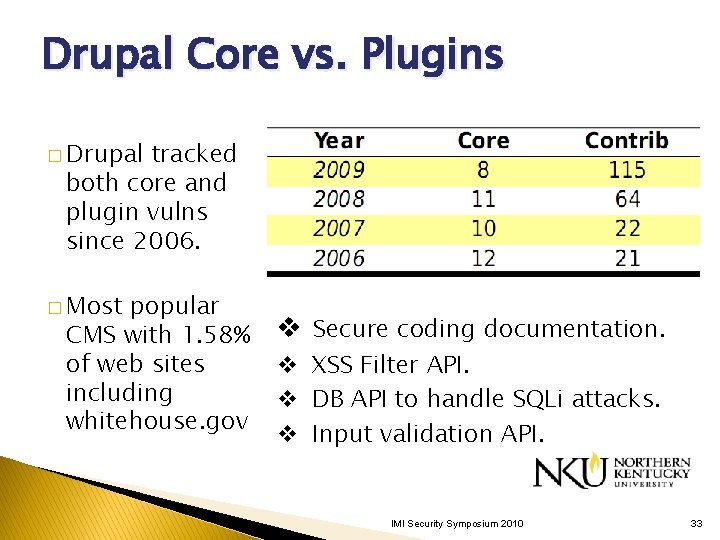
Drupal Core vs. Plugins � Drupal tracked both core and plugin vulns since 2006. � Most popular CMS with 1. 58% of web sites including whitehouse. gov www. drupalsecurityreport. org v Secure coding documentation. v XSS Filter API. v DB API to handle SQLi attacks. v Input validation API. IMI Security Symposium 2010 33
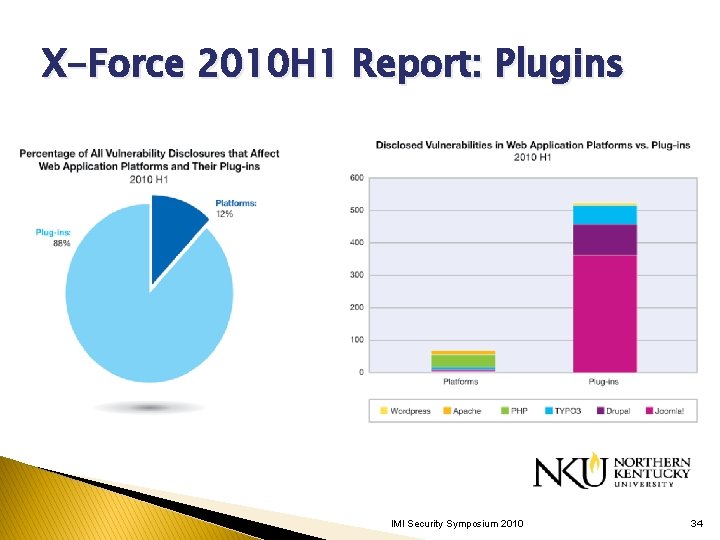
X-Force 2010 H 1 Report: Plugins IMI Security Symposium 2010 34
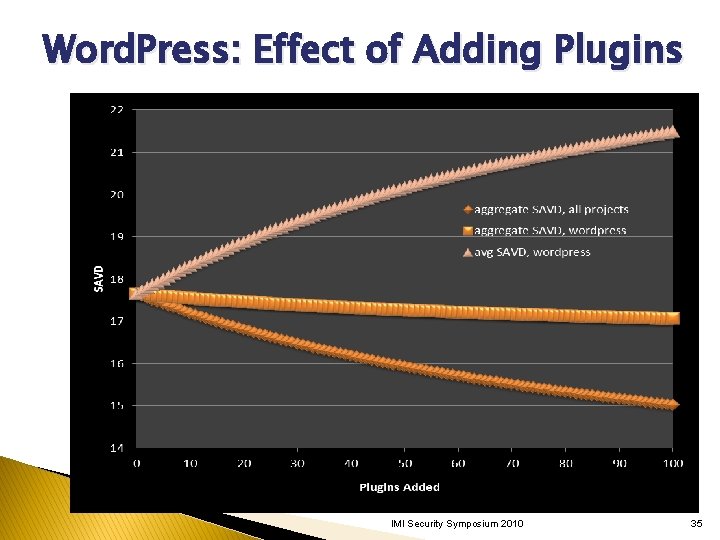
Word. Press: Effect of Adding Plugins IMI Security Symposium 2010 35
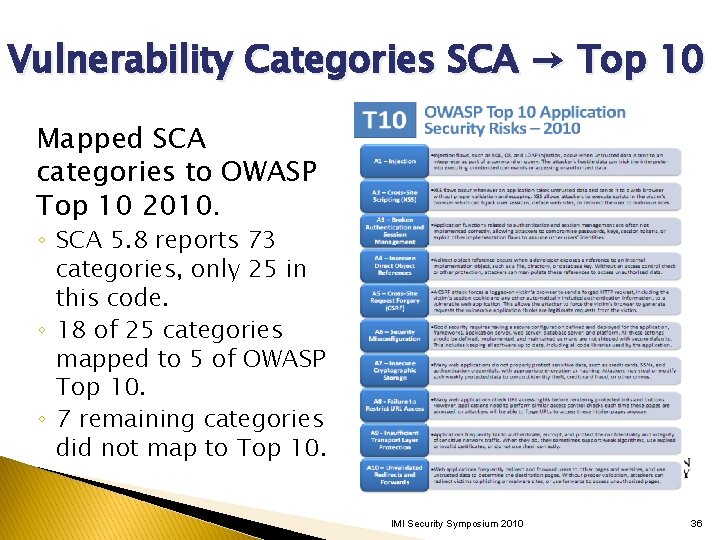
Vulnerability Categories SCA → Top 10 Mapped SCA categories to OWASP Top 10 2010. ◦ SCA 5. 8 reports 73 categories, only 25 in this code. ◦ 18 of 25 categories mapped to 5 of OWASP Top 10. ◦ 7 remaining categories did not map to Top 10. IMI Security Symposium 2010 36
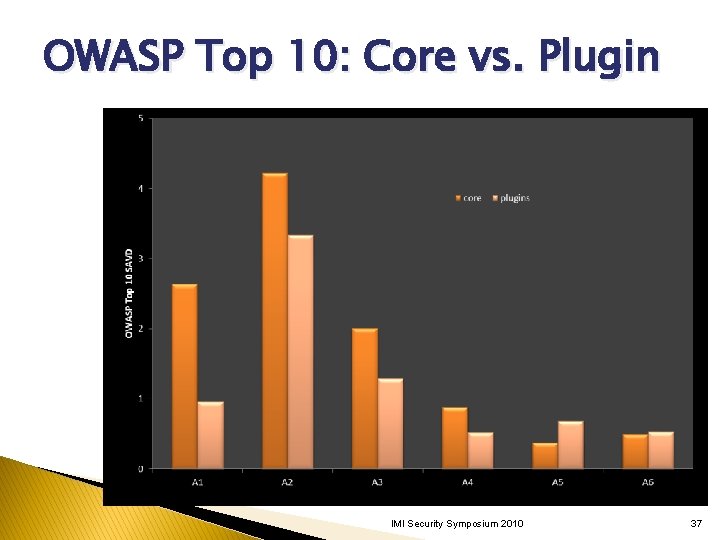
OWASP Top 10: Core vs. Plugin IMI Security Symposium 2010 37
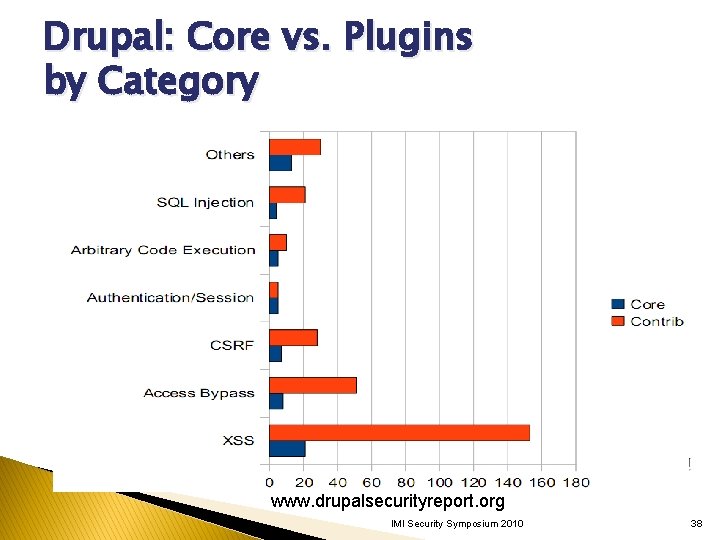
Drupal: Core vs. Plugins by Category www. drupalsecurityreport. org IMI Security Symposium 2010 38
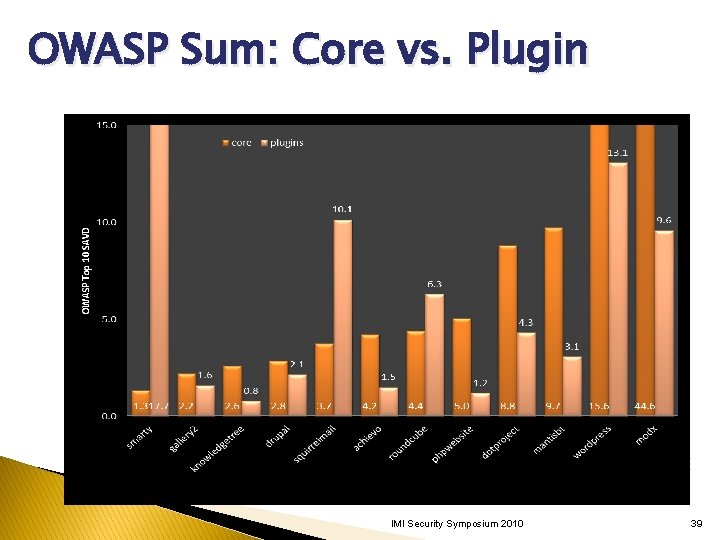
OWASP Sum: Core vs. Plugin IMI Security Symposium 2010 39
Conclusions Plugins slightly less secure than core. �Plugins made up 91% of 11. 7 MLOC. �Contained 92% of 135, 907 vulnerabilities. Plugin SAVD correlates with code size. �ρ = 0. 91 (strong correlation) �Larger plugins are more likely to have vulnerabilities. Core SAVD does not correlate w/ code size. IMI Security Symposium 2010 40

Additional Material IMI Security Symposium 2010 41
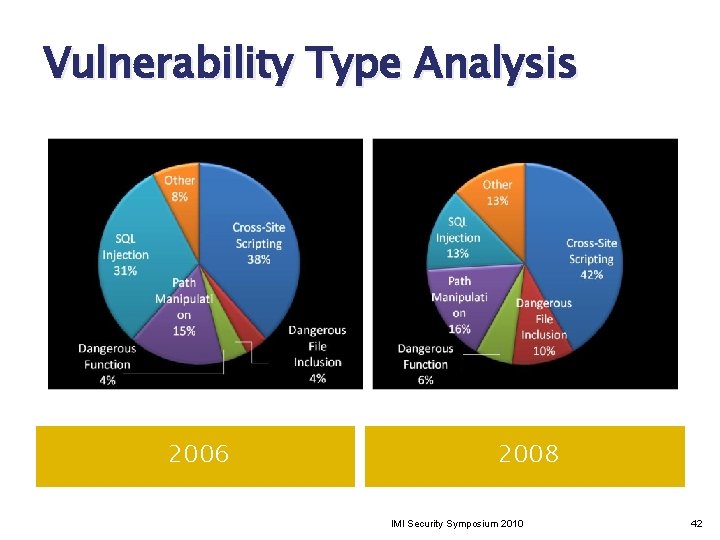
Vulnerability Type Analysis 2006 2008 IMI Security Symposium 2010 42
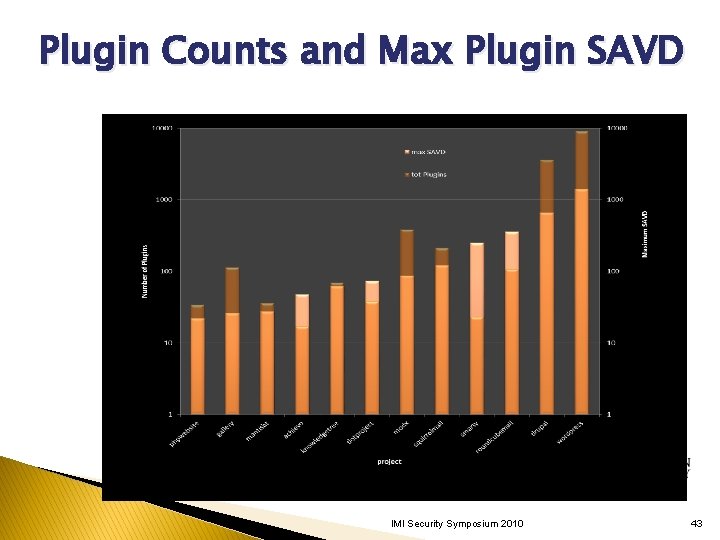
Plugin Counts and Max Plugin SAVD IMI Security Symposium 2010 43
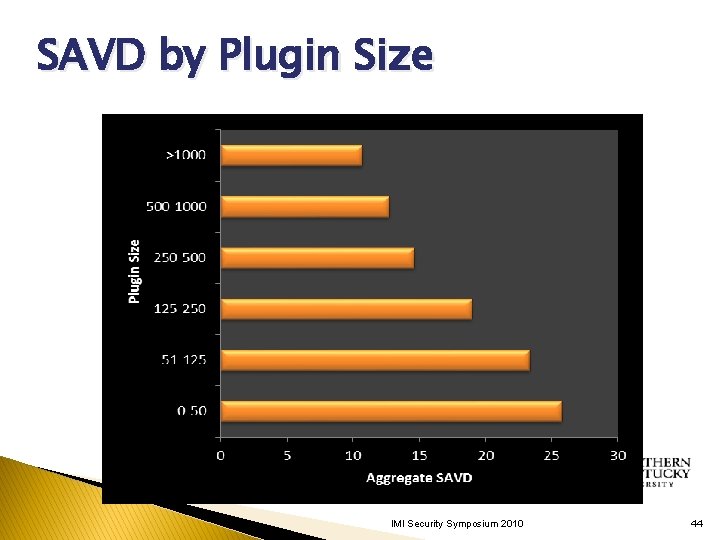
SAVD by Plugin Size IMI Security Symposium 2010 44
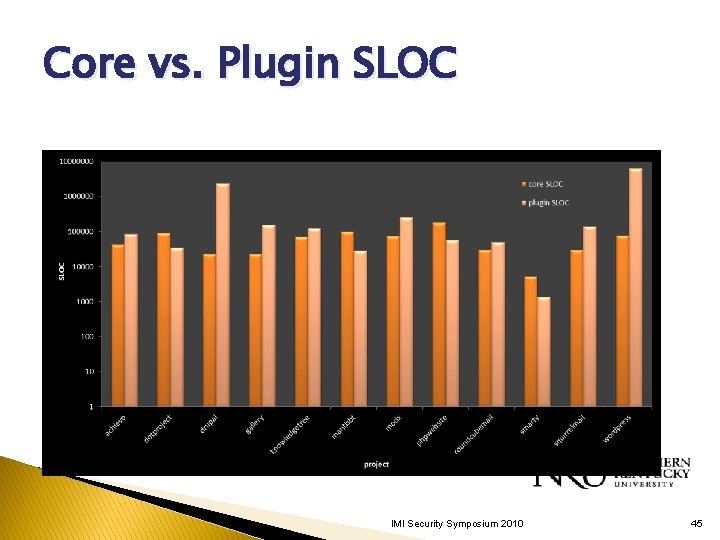
Core vs. Plugin SLOC IMI Security Symposium 2010 45
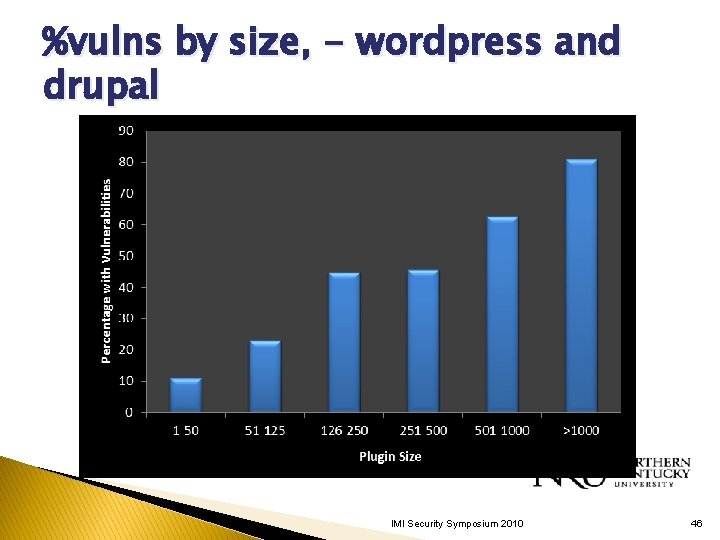
%vulns by size, - wordpress and drupal IMI Security Symposium 2010 46
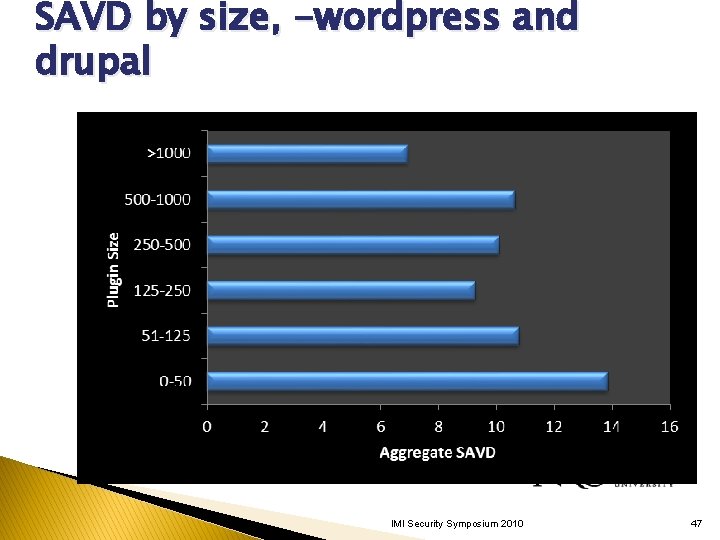
SAVD by size, -wordpress and drupal IMI Security Symposium 2010 47
- Slides: 47