IEEE 802 21 MEDIA INDEPENDENT HANDOVER DCN 21








- Slides: 19

IEEE 802. 21 MEDIA INDEPENDENT HANDOVER DCN: 21 -08 -0 xxx-00 -0 sec-3 gpp-security-non 802 handover Title: A Study on Security Solutions in non- IEEE 802 Wireless – 3 GPP AKA and Interworking with WLAN Date Submitted: September 3, 2008 Presented at IEEE 802. 21 session #28 in Big Island, HI Authors or Source(s): Lily Chen (NIST) Abstract: This presentation reviews security solutions for 3 GPP and 3 GPP - WLAN interworking. The purpose is to explore possible security handover strategies with non-802 networks. 21 -08 -0 xxx-00 -0 sec

IEEE 802. 21 presentation release statements This document has been prepared to assist the IEEE 802. 21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. The contributor grants a free, irrevocable license to the IEEE to incorporate material contained in this contribution, and any modifications thereof, in the creation of an IEEE Standards publication; to copyright in the IEEE’s name any IEEE Standards publication even though it may include portions of this contribution; and at the IEEE’s sole discretion to permit others to reproduce in whole or in part the resulting IEEE Standards publication. The contributor also acknowledges and accepts that this contribution may be made public by IEEE 802. 21. The contributor is familiar with IEEE patent policy, as outlined in Section 6. 3 of The contributor is familiar with IEEE patent policy, as stated in Section 6 of the IEEE-SA Standards Board Operations Manual IEEE-SA Standards Board bylaws <http: //standards. ieee. org/guides/opman/sect 6. html#6. 3> and in <http: //standards. ieee. org/guides/bylaws/sect 6 -7. html#6> and in Understanding Patent Issues During IEEE Standards Development http: //standards. ieee. org/board/pat/guide. html> http: //standards. ieee. org/board/pat/faq. pdf> 21 -08 -0 xxx-00 -0 sec

Purpose • Study non-IEEE 802 wireless network security solutions • Explore possible security handover strategies with non-IEEE 802 networks. 21 -08 -0 xxx-00 -0 sec

Outline • UMTS Authentication and Key Agreement (AKA) • EAP-AKA • 3 GPP and WLAN interworking • Interworking vs. handover 21 -08 -0 xxx-00 -0 sec

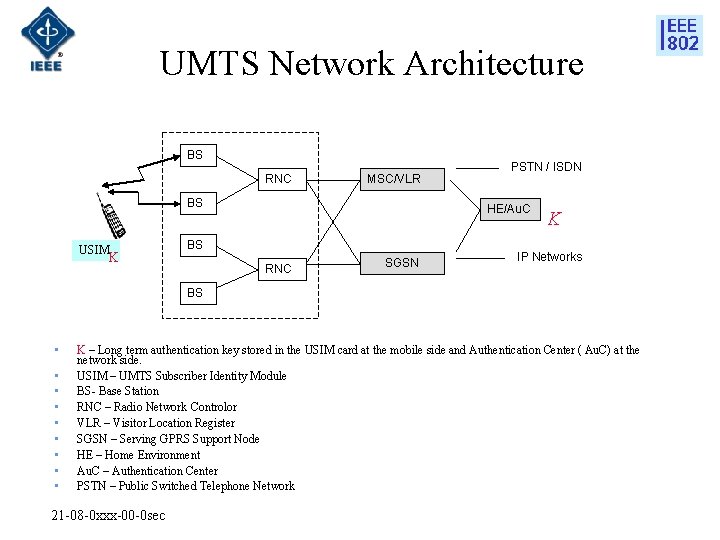
UMTS Network Architecture BS RNC MSC/VLR BS USIM K PSTN / ISDN HE/Au. C BS RNC SGSN K IP Networks BS • • • K – Long term authentication key stored in the USIM card at the mobile side and Authentication Center ( Au. C) at the network side. USIM – UMTS Subscriber Identity Module BS- Base Station RNC – Radio Network Controlor VLR – Visitor Location Register SGSN – Serving GPRS Support Node HE – Home Environment Au. C – Authentication Center PSTN – Public Switched Telephone Network 21 -08 -0 xxx-00 -0 sec

Authentication and Key Agreement (AKA) - Introduction • AKA is the subscriber authentication and session key generation protocol specified in 3 GPP for UMTS (see 3 GPP TS 33. 102). • The authentication is based on symmetric key method, assuming that the subscriber and the network share a long term key K. • The main idea is to use “Authentication Vectors (AVs)” to delegate the authentication to VLR/SGSN. 21 -08 -0 xxx-00 -0 sec

Authentication and Key Agreement (AKA) - Authentication Vector • An authentication vector is a quintuplet: AV = (RAND||AUTN||XRES||CK||IK) • The components are • • • RAND – Random challenge AUTN – Authentication token to authenticate the network XRES – Expected response to RAND CK – Cipher (encryption) key IK – Integrity key 21 -08 -0 xxx-00 -0 sec

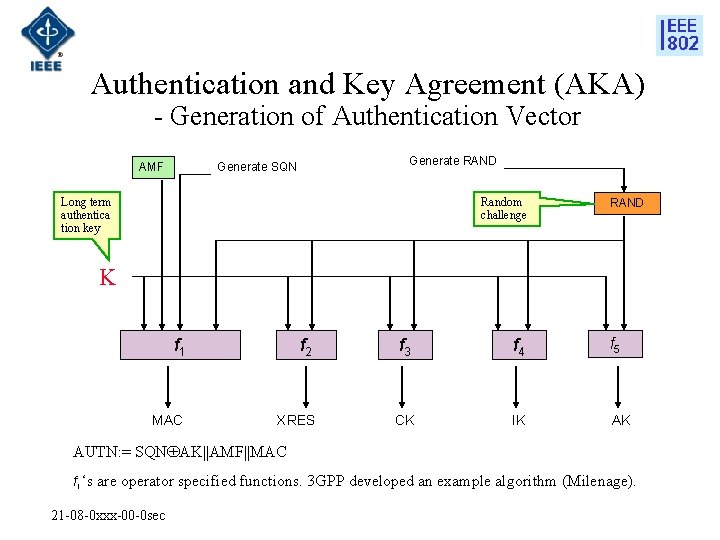
Authentication and Key Agreement (AKA) - Generation of Authentication Vector AMF Generate RAND Generate SQN Long term authentica tion key Random challenge RAND K f 1 f 2 f 3 f 4 f 5 MAC XRES CK IK AK AUTN: = SQN AK||AMF||MAC fi ‘s are operator specified functions. 3 GPP developed an example algorithm (Milenage). 21 -08 -0 xxx-00 -0 sec

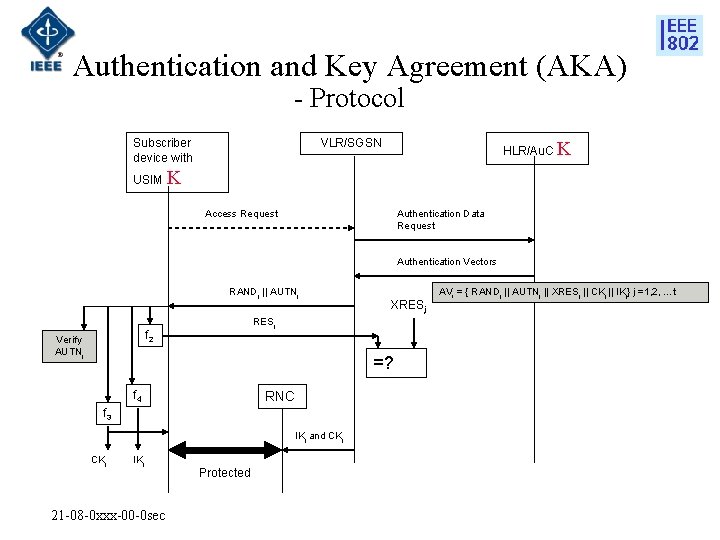
Authentication and Key Agreement (AKA) - Protocol Subscriber device with USIM VLR/SGSN HLR/Au. C K K Authentication Data Request Access Request Authentication Vectors RANDj || AUTNj RESj f 2 Verify AUTNj XRESj =? f 4 RNC f 3 IKj and CKj IKj 21 -08 -0 xxx-00 -0 sec Protected AVi = { RANDj || AUTNj || XRESj || CKj || IKj} j =1, 2, …t

UMTS Security in Handover • AKA is executed for each registration not for each handover. HLR • Session keys IK and CK are generated for each AKA execution. Authentication Center MSC VLR • The same session keys can be used by different RNCs. They are distributed through handover. • UMTS allows the different RNCs to share the same session keys, while in IEEE 802. 11, different APs are not trusted to share the same session keys! 21 -08 -0 xxx-00 -0 sec CK, IK RNC 2 Radio Access Network CK, IK RNC 1

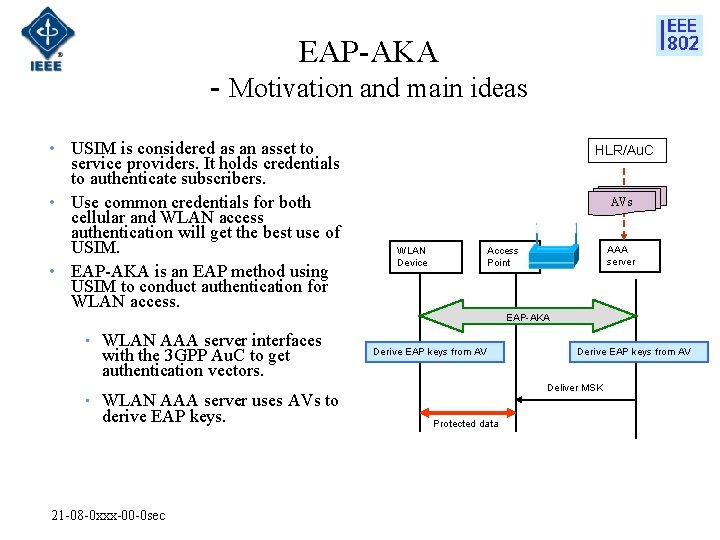
EAP-AKA - Motivation and main ideas • USIM is considered as an asset to service providers. It holds credentials to authenticate subscribers. • Use common credentials for both cellular and WLAN access authentication will get the best use of USIM. • EAP-AKA is an EAP method using USIM to conduct authentication for WLAN access. HLR/Au. C AVs WLAN Device AAA server Access Point EAP-AKA • • WLAN AAA server interfaces with the 3 GPP Au. C to get authentication vectors. WLAN AAA server uses AVs to derive EAP keys. 21 -08 -0 xxx-00 -0 sec Derive EAP keys from AV Deliver MSK Protected data

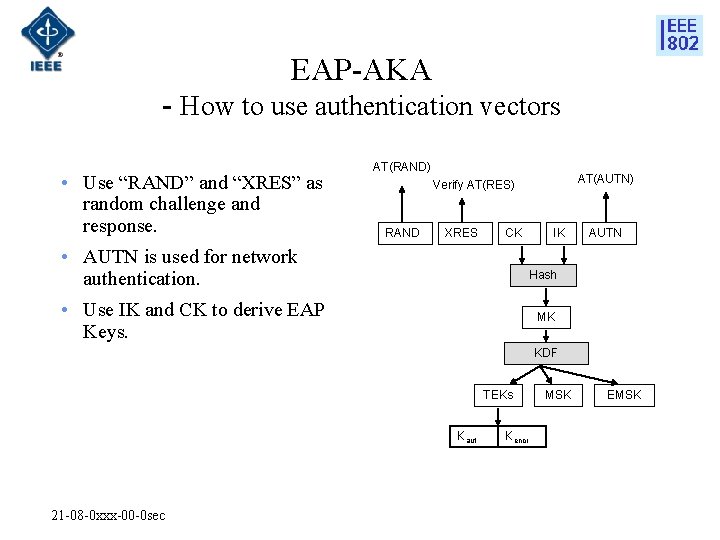
EAP-AKA - How to use authentication vectors • Use “RAND” and “XRES” as random challenge and response. AT(RAND) AT(AUTN) Verify AT(RES) RAND XRES CK • AUTN is used for network authentication. IK AUTN Hash • Use IK and CK to derive EAP Keys. MK KDF TEKs Kaut 21 -08 -0 xxx-00 -0 sec Kencr MSK EMSK

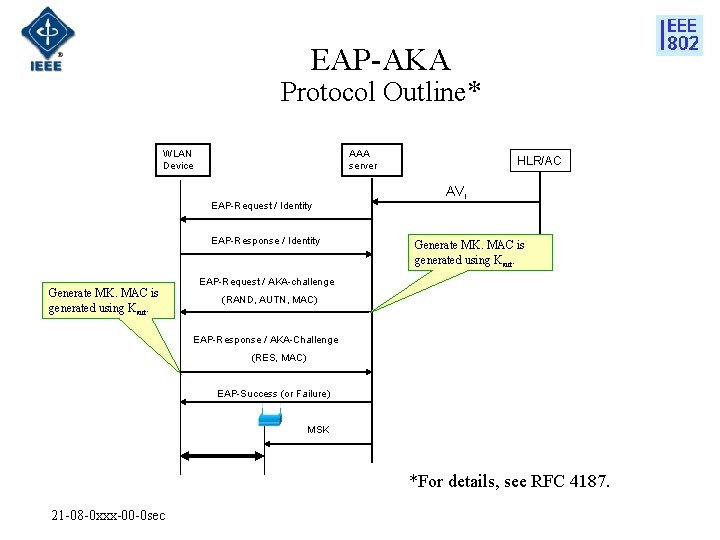
EAP-AKA Protocol Outline* AAA server WLAN Device EAP-Request / Identity EAP-Response / Identity Generate MK. MAC is generated using Kaut. HLR/AC AVi Generate MK. MAC is generated using Kaut. EAP-Request / AKA-challenge (RAND, AUTN, MAC) EAP-Response / AKA-Challenge (RES, MAC) EAP-Success (or Failure) MSK *For details, see RFC 4187. 21 -08 -0 xxx-00 -0 sec

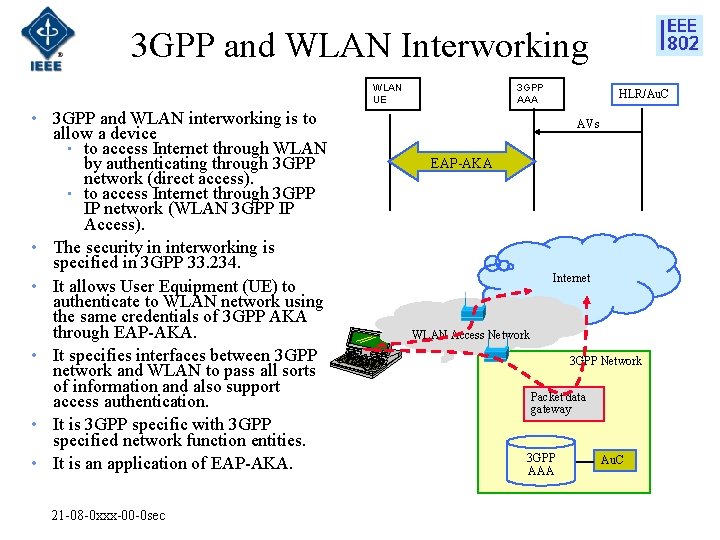
3 GPP and WLAN Interworking WLAN UE • 3 GPP and WLAN interworking is to allow a device • to access Internet through WLAN by authenticating through 3 GPP network (direct access). • to access Internet through 3 GPP IP network (WLAN 3 GPP IP Access). • The security in interworking is specified in 3 GPP 33. 234. • It allows User Equipment (UE) to authenticate to WLAN network using the same credentials of 3 GPP AKA through EAP-AKA. • It specifies interfaces between 3 GPP network and WLAN to pass all sorts of information and also support access authentication. • It is 3 GPP specific with 3 GPP specified network function entities. • It is an application of EAP-AKA. 21 -08 -0 xxx-00 -0 sec 3 GPP AAA HLR/Au. C AVs EAP-AKA Internet WLAN Access Network 3 GPP Network Packet data gateway 3 GPP AAA Au. C

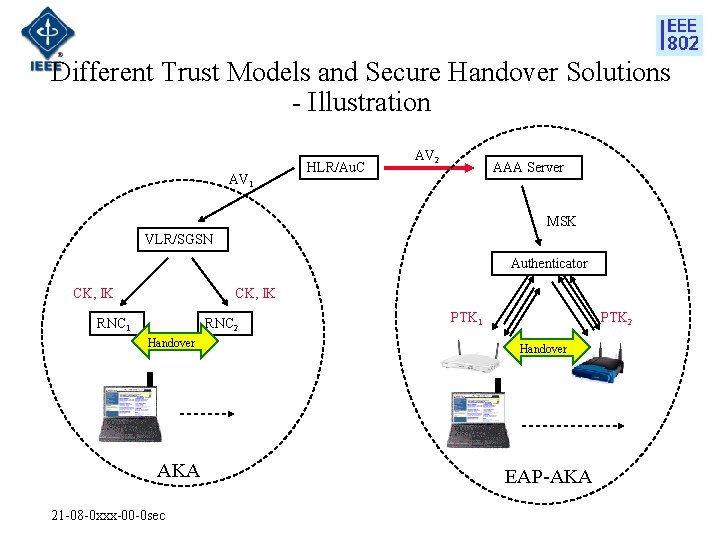
AKA vs. EAP-AKA • Interworking allows using AKA authentication vector for WLAN access authentication and key establishment. • AKA and EAP-AKA have different trust models: • Session keys generated through AKA can be shared among RNCs. • MSK, generated through EAP-AKA, is specific for an given authenticator. Wireless protection session keys are AP specific. • UMTS and IEEE 802 network have different secure handover solutions. • UMTS has infrastructure to handover the session keys. • IEEE 802 (e. g. 802. 11 r) executes a handshake in each handover to generate new session keys. • Interworking does not provide mechanisms to handover keys between IEEE 802 wireless network and non-802 network. 21 -08 -0 xxx-00 -0 sec

Different Trust Models and Secure Handover Solutions - Illustration AV 1 HLR/Au. C AV 2 AAA Server MSK VLR/SGSN Authenticator CK, IK RNC 1 RNC 2 Handover AKA 21 -08 -0 xxx-00 -0 sec PTK 1 PTK 2 Handover EAP-AKA

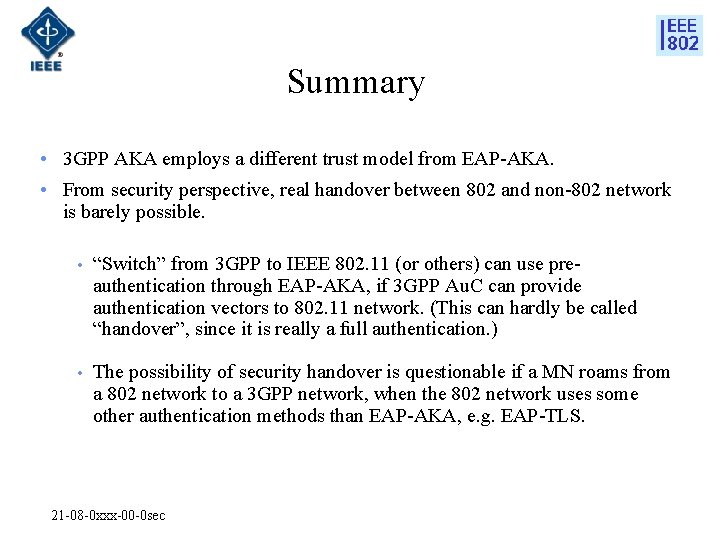
Summary • 3 GPP AKA employs a different trust model from EAP-AKA. • From security perspective, real handover between 802 and non-802 network is barely possible. • “Switch” from 3 GPP to IEEE 802. 11 (or others) can use preauthentication through EAP-AKA, if 3 GPP Au. C can provide authentication vectors to 802. 11 network. (This can hardly be called “handover”, since it is really a full authentication. ) • The possibility of security handover is questionable if a MN roams from a 802 network to a 3 GPP network, when the 802 network uses some other authentication methods than EAP-AKA, e. g. EAP-TLS. 21 -08 -0 xxx-00 -0 sec

Back Up slides 21 -08 -0 xxx-00 -0 sec

EAP-AKA Fast Re-authentication • After a full EAP-AKA execution, the TEK = (Kencr, Kaut) can be used for a fast re-authentication. • The server generates a random number NS and use Kencr to encrypt it. The server message includes a MAC. • Upon receiving E(Kencr, NS), the peer decrypts it. The MN generates a MAC over NS using Kaut and sends it to the server. The MAC serves as an authentication response. • For each fast re-authentication, it generates a new MK using the old MK and NS. • A counter is maintained to record the number of fast reauthentications. 21 -08 -0 xxx-00 -0 sec
 Bridges from 802.x to 802.y
Bridges from 802.x to 802.y Bridges from 802.x to 802.y
Bridges from 802.x to 802.y Ieee802.22
Ieee802.22 Arquitetura ieee 802
Arquitetura ieee 802 Estandares ieee 802
Estandares ieee 802 Ieee 802 standard
Ieee 802 standard Bluetooth ieee 802
Bluetooth ieee 802 802 ieee
802 ieee Ieee 802
Ieee 802 Ieee 802 family
Ieee 802 family Ieee 802 3 compliance
Ieee 802 3 compliance Isbar example
Isbar example Sbar handover
Sbar handover Standard 6 clinical handover
Standard 6 clinical handover Sbar
Sbar Standard 6 clinical handover
Standard 6 clinical handover Network slicing handover
Network slicing handover Sbar handover
Sbar handover Sbar nhs england
Sbar nhs england Mobility mode
Mobility mode