IEEE 802 21 MEDIA INDEPENDENT HANDOVER DCN 21






- Slides: 8

IEEE 802. 21 MEDIA INDEPENDENT HANDOVER DCN: 21 -10 -0204 -00 -0 sec Title: Option III: EAP to conduct service authentication and MIH packet protection: FLAGS and MIHS. Date Submitted: September 28, 2010 Present at IEEE 802. 21 meeting in September 28, 2010 teleconference Authors or Source(s): Fernando Bernal, Rafa Marín-López Abstract: 1

IEEE 802. 21 presentation release statements This document has been prepared to assist the IEEE 802. 21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. The contributor grants a free, irrevocable license to the IEEE to incorporate material contained in this contribution, and any modifications thereof, in the creation of an IEEE Standards publication; to copyright in the IEEE’s name any IEEE Standards publication even though it may include portions of this contribution; and at the IEEE’s sole discretion to permit others to reproduce in whole or in part the resulting IEEE Standards publication. The contributor also acknowledges and accepts that this contribution may be made public by IEEE 802. 21. The contributor is familiar with IEEE patent policy, as stated in Section 6 of the IEEE-SA Standards Board bylaws <http: //standards. ieee. org/guides/bylaws/sect 6 -7. html#6> and in Understanding Patent Issues During IEEE Standards Development http: //standards. ieee. org/board/pat/faq. pdf> 2

Flags Needed in MIH Header • Bit P – To indicate that a proactive authentication is being performed. • Bit F – To indicate that the last two messages of the authentication is being performed. • These bits could be placed in the field: Reserved 2 in 802. 21 Header. 3

Final ciphersuite? Confidentiality algorithms ENCR_AES_CBC Reference NIST 800 -38 A ENCR_NULL Integrity algorithms Reference INTR_HMAC_SHA_96 FIPS 180 -1 INTR_CMAC_AES NIST 800 -38 B INTR_NULL Confidentiality and Integrity algorithms INTR_ENC_AES_CCM Reference NIST 800 -38 C KDF algorithms Reference PRF_CMAC_AES NIST 800 -108 PRF_HMAC_SHA 1 NIST 800 -108 Cipher-required TLV must be removed, due to using ENCR_NULL the same information is given. 4

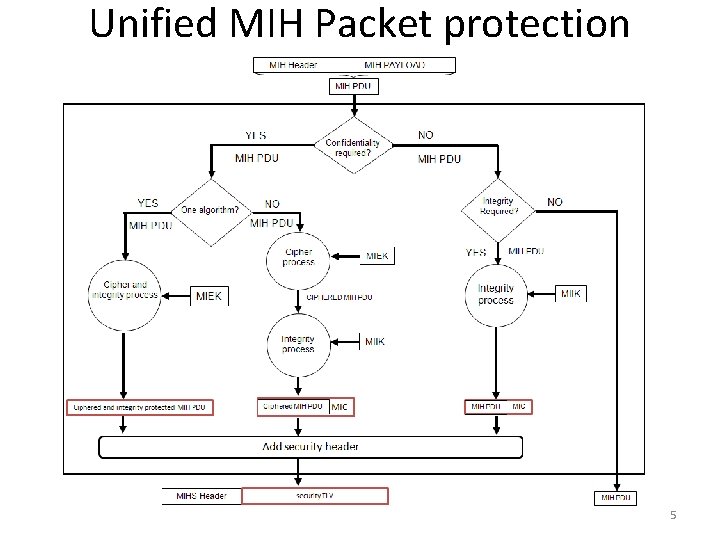
Unified MIH Packet protection 5

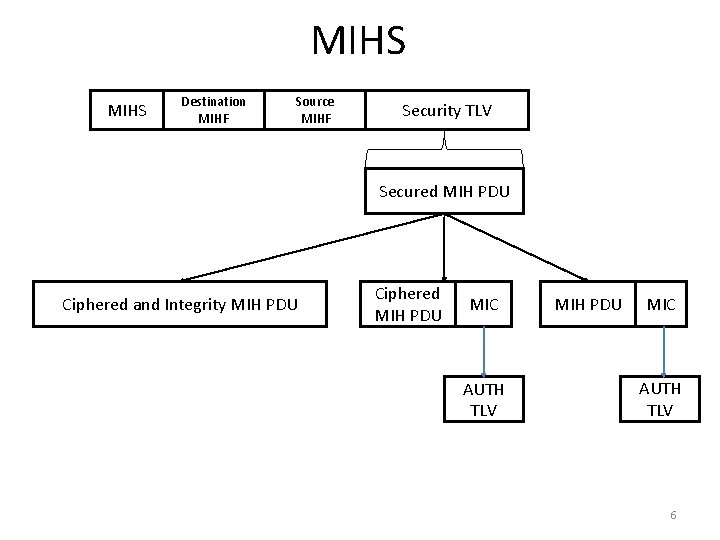
MIHS Destination MIHF Source MIHF Security TLV Secured MIH PDU Ciphered and Integrity MIH PDU Ciphered MIH PDU MIC AUTH TLV 6

MIHS • This header must be an extension of the MIH header. • Bit S: to indicate that is a MIHS • Bit P: to indicate a proactive situation • These bits could be placed in the field: Reserved 2 in the 802. 21 header. • MIHS PDU is the same as in Subir’s proposal. – The TLS TLV in MIHS PDU should be updated to security TLV. To merge both proposals. • To provide integrity an AUTH TLV must be added to the MIHS PDU. 7

Discussion • Does MIH Finalization phase should be removed? • Capability Discovery should parameters be removed? – Network selecction could be affected • Should Session ID TLV be removed? • Do we really need the MIHS? – Do we need protect the MIH Header? 8















