IE Security Past Present and Future Tony Chor
















![IE Security: Future “If all Windows users were running Vista [with IE 7], the IE Security: Future “If all Windows users were running Vista [with IE 7], the](https://slidetodoc.com/presentation_image_h2/512f7bd6eb99b7d21380c669198039b4/image-23.jpg)





- Slides: 28

IE Security: Past, Present, and Future Tony Chor Group Program Manager Rob Franco Lead Program Manager Internet Explorer Microsoft Corporation

About this presentation Past Present Guiding principles for IE Security The Security Development Lifecycle (SDL) Future High level browser threat model How IE 7 addresses the threats

Past Compatibility and features trumped security Users fooled into making bad trust decisions Malware installed via architectural flaws Powerful extensibility misused Security seen as a servicing problem Adversarial relationship with community

Past “I suggest dumping Microsoft’s Internet Explorer Web browser, which has a history of security breaches. ” Walt Mossberg Wall Street Journal September 2004

Present: IE is back! IE team reborn 24 months ago Improved security response IE 6. 0 for Windows XP SP 2 New versions Engaging the community Security is integral to our engineering practices

Present: Guiding principles The web must be safe Reduce attack surface Build defense-in-depth Secure by default Enable users to make smarter choices The web must be useful App compat and site compat are critical Corporate IT has different needs from consumers Partner with the community

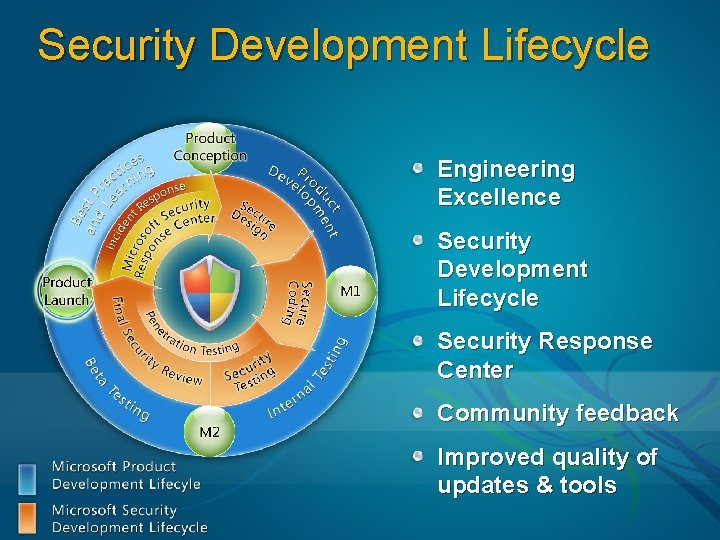
Security Development Lifecycle Engineering Excellence Security Development Lifecycle Security Response Center Community feedback Improved quality of updates & tools

IE Security: Present “The assumption that Internet Explorer is easier to exploit is a common misconception…Internet Explorer has become quite tough, and it is very difficult to find vulnerabilities in it. ” Security Focus Newsletter May 12, 2005

Future: IE 7 SDL-driven security strategy Dynamic protection against fraud User control over extensibility Architectural enhancements against malware Proactive engagement with community

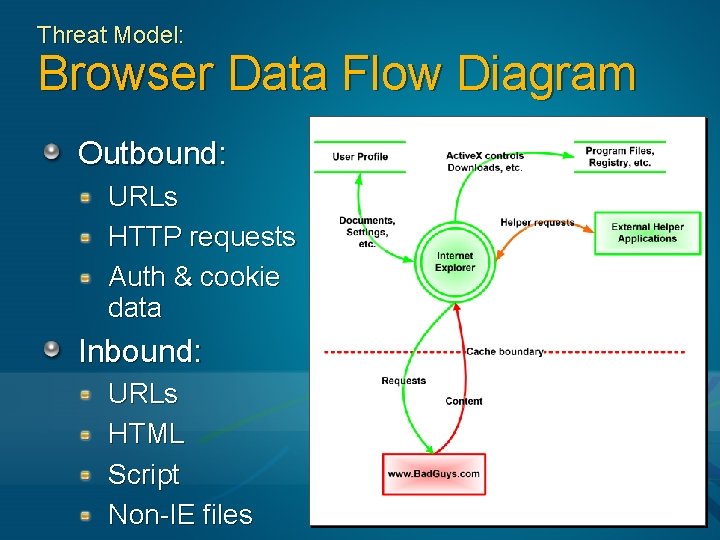
Threat Model: Browser Data Flow Diagram Outbound: URLs HTTP requests Auth & cookie data Inbound: URLs HTML Script Non-IE files

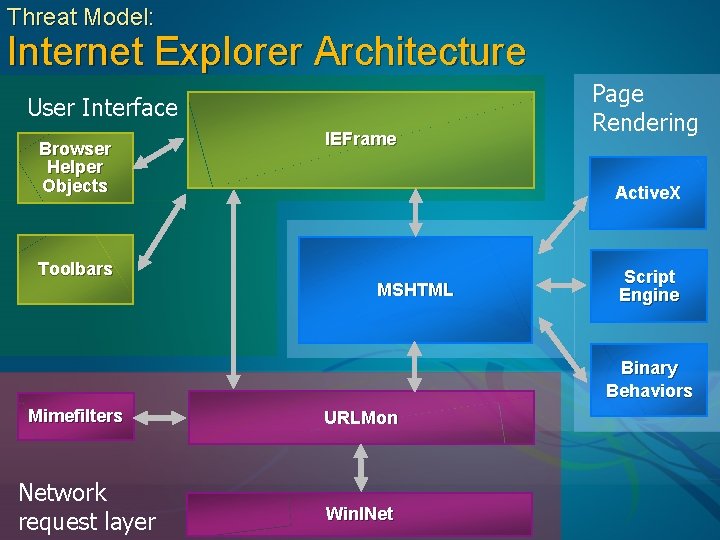
Threat Model: Internet Explorer Architecture User Interface Browser Helper Objects Toolbars IEFrame Page Rendering Active. X MSHTML Script Engine Binary Behaviors Mimefilters Network request layer URLMon Win. INet

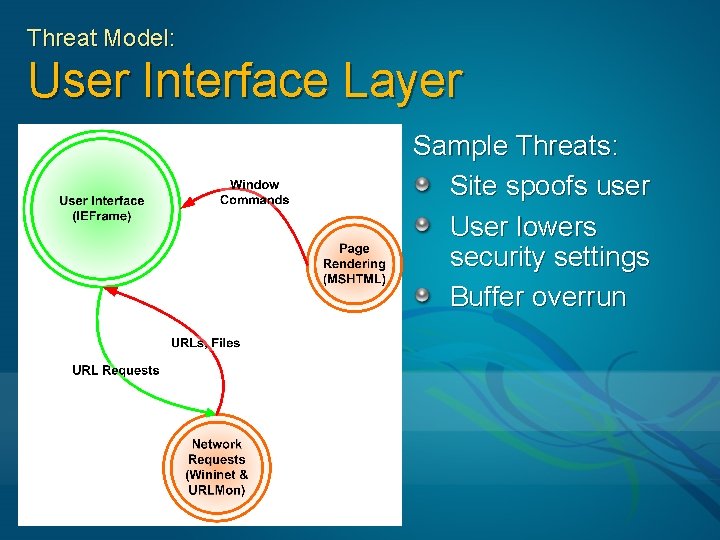
Threat Model: User Interface Layer Sample Threats: Site spoofs user User lowers security settings Buffer overrun

Demo: User Interface Mitigations In this demo, you will see how IE 7: Uses a phishing filter to dynamically protect users from fraud Warns users about unsafe settings

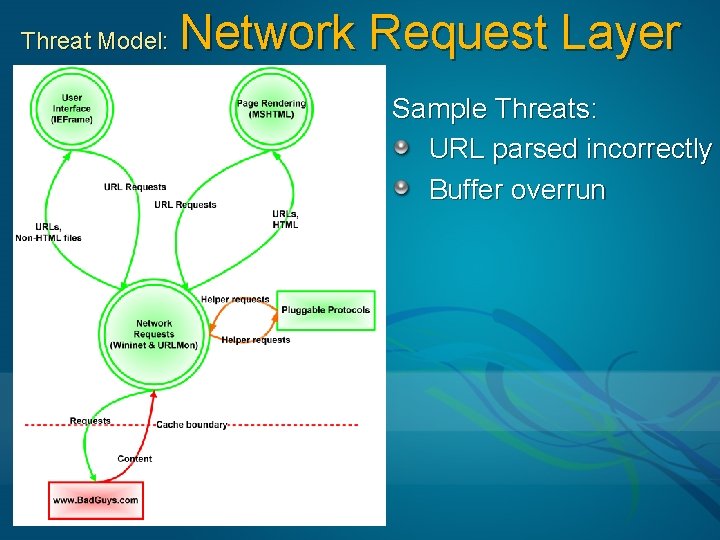
Threat Model: Network Request Layer Sample Threats: URL parsed incorrectly Buffer overrun

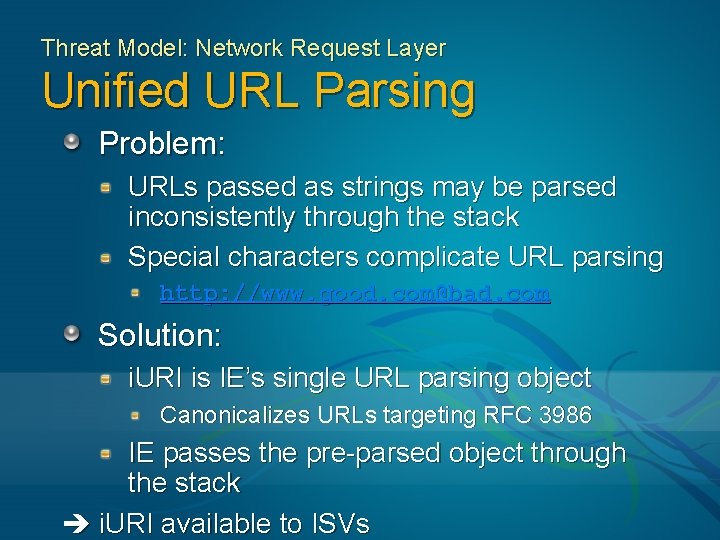
Threat Model: Network Request Layer Unified URL Parsing Problem: URLs passed as strings may be parsed inconsistently through the stack Special characters complicate URL parsing http: //www. good. com@bad. com Solution: i. URI is IE’s single URL parsing object Canonicalizes URLs targeting RFC 3986 IE passes the pre-parsed object through the stack i. URI available to ISVs

Threat Model: Page Rendering Layer Sample Threats Active. X controls misused Page Access rules fail Unsafe access defaults Page Redirects Buffer overrun

Threat Model: Page Rendering Layer Active. X Opt-in Problem: Active. X controls can expose dangerous functions and security bugs to any page on the web Solution: Pre-installed Active. X controls will prompt on first use the same as downloaded controls Users can run in Add-ons disabled mode to shut off more extensions like BHOs “This move is worth praise. ” Joe Wilcox, Jupiter Research, September 13, 2005

Threat Model: Page Rendering Layer Cross Domain Security Problem: Hackers use script protocols to run domainless script javascript: alert(document. body. inner. HTML) Solution: Migrate the script protocol to run as script in the originating page

Threat Model: General Prevent Buffer Overruns Problem: Attacker finds a place where the parser does not check for size of an argument Solutions: Automated code review tools Safe memory APIs Fuzz testing These tools are part of Visual Studio 2005

Threat Model: General EOP: Today Admin-Rights Access Install an Active. X control Exploit can install MALWARE IExplore. exe Change Settings, Download a Picture Exploit can install MALWARE HKLM Program Files User-Rights Access HKCU My Documents Startup Folder Temp Internet Files Cache Web content Untrusted files & settings

Threat Model: General Broker Process Integrity Control Protected Mode IE Compat Redirector EOP: Protected Mode Admin-Rights Access Install an Active. X control HKLM HKCR Program Files Change settings, Save a picture Cache Web content User-Rights Access HKCU My Documents Startup Folder Temp Internet Files Untrusted files & settings Redirected settings & files

Demo: Protected Mode IE In this demo, you will see how IE 7: Runs with restrictions to prevent exploits from installing malware on users’ systems Keeps the web useful Still allows users to download files or change settings Allows Intranet sites to run without restrictions
![IE Security Future If all Windows users were running Vista with IE 7 the IE Security: Future “If all Windows users were running Vista [with IE 7], the](https://slidetodoc.com/presentation_image_h2/512f7bd6eb99b7d21380c669198039b4/image-23.jpg)
IE Security: Future “If all Windows users were running Vista [with IE 7], the Internet would be a much safer place. ” Larry Seltzer e. Week July 29, 2005

Internet Explorer 7. 0 Win reviews and the popular vote Improving Trustworthy Browsing Amazing Everyday Browsing Good Web Developer Platform Release dates Windows Vista: 2 nd half of 2006 Windows XP SP 2, Windows Server 2003 SP 1, x 64: TBD Status Beta 1 released in June Beta 2 Preview in October Beta 2 later this year

Resources Books Writing Secure Code Second Edition Michael Howard and David Le. Blanc Threat Modeling Frank Swiderski and Window Snyder Resources blogs. msdn. com/ie/ secure@microsoft. com Tools Visual Studio 2005

Conclusion We’ve come a long way. We have a long way to go. We’d like your help Test IE 7 for security and compatibility Give us feedback – we’re listening!

Q&A Your quotes? Your thoughts? Your questions?

secure@microsoft. com