Identity Theft and Congressional Response Johnny Yeh CPSC




















































- Slides: 57

Identity Theft and Congressional Response Johnny Yeh CPSC 457 Student Presentation

Outline q q q Overview of Identity Theft Statistics Historical Starting Point Response From Congress and Impacts Conclusion Questions / Discussion

Overview of Identity Theft v What is Identity Theft (IDT)? § Theft of Documents? Money? Rights? Innocence? v The class consensus thus far § IDT requires impersonation with intent to co-opt some major part of a victim’s identity § Requires impersonation to go beyond immediate monetary benefits (i. e. cash withdrawal, credit card use, etc. )

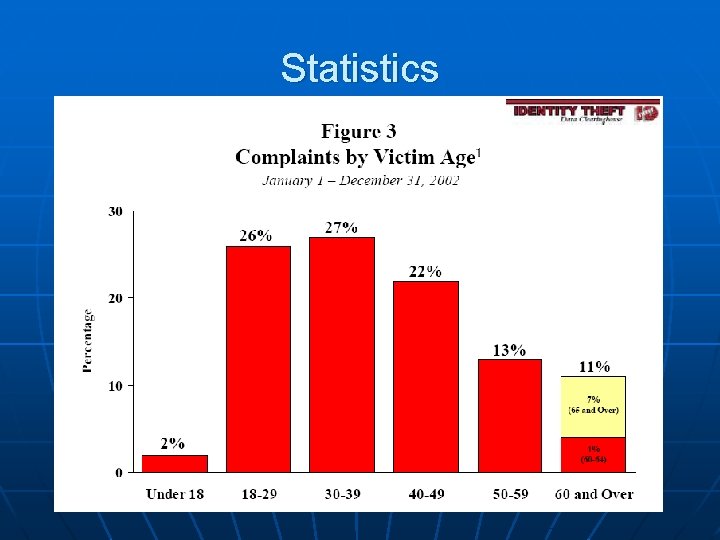
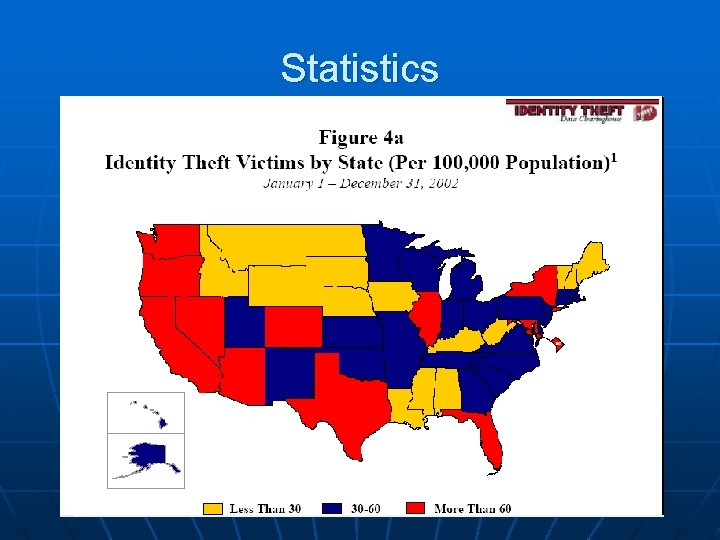
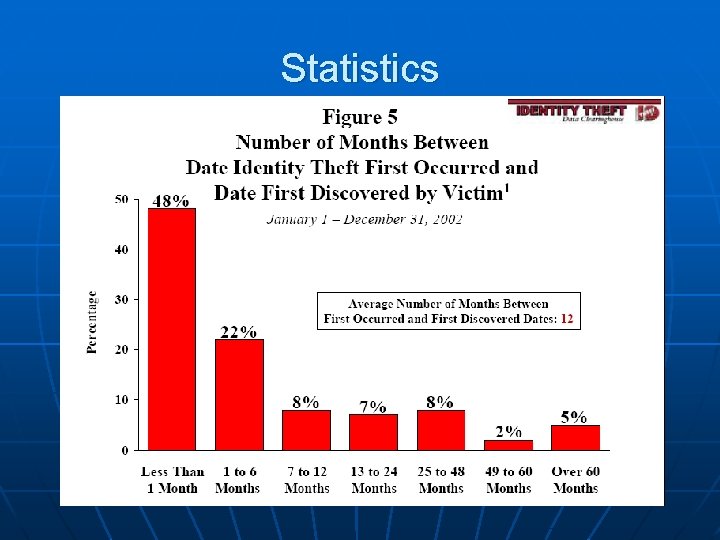
Statistics v Staggering levels of ID Theft § 1992 to 1997 there is a 16 fold increase § 1997 – 9, 455 Cases

Statistics v Staggering levels of ID Theft § 1992 § 1997 § 2000 to 1997 there is a 16 fold increase – 9, 455 Cases – 500, 000 – 700, 000 Cases

Statistics v Staggering levels of ID Theft § 1992 § 1997 § 2000 § 2002 to 1997 there is a 16 fold increase – 9, 455 Cases – 500, 000 – 700, 000 Cases – 161, 819 Reported Cases

Statistics v Staggering levels of ID Theft § 1992 § 1997 § 2000 § 2002 § 2003 § § to 1997 there is a 16 fold increase – 9, 455 Cases – 500, 000 – 700, 000 Cases – 161, 819 Reported Cases – 9. 91 Million Cases Cost of $5 Billion to consumers at $500 per victim Cost of 47. 6 Billion to businesses at $4, 800 per victim

Statistics

Statistics

Statistics

Statistics

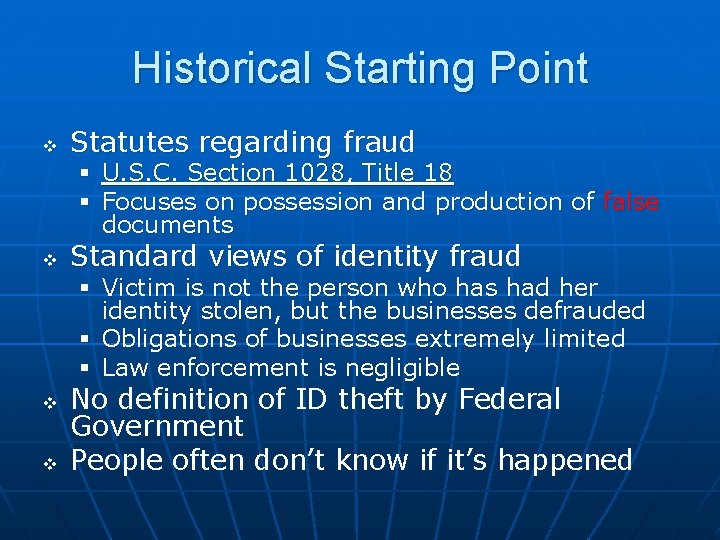
Historical Starting Point v Statutes regarding fraud § U. S. C. Section 1028, Title 18 § Focuses on possession and production of false documents v Standard views of identity fraud § Victim is not the person who has had her identity stolen, but the businesses defrauded § Obligations of businesses extremely limited § Law enforcement is negligible v v No definition of ID theft by Federal Government People often don’t know if it’s happened

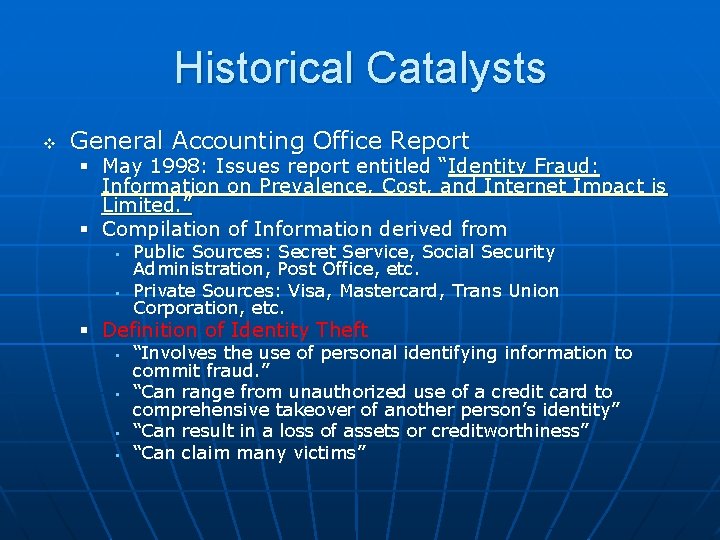
Historical Catalysts v General Accounting Office Report § May 1998: Issues report entitled “Identity Fraud: Information on Prevalence, Cost, and Internet Impact is Limited. ” § Compilation of Information derived from § § Public Sources: Secret Service, Social Security Administration, Post Office, etc. Private Sources: Visa, Mastercard, Trans Union Corporation, etc. § Definition of Identity Theft § § “Involves the use of personal identifying information to commit fraud. ” “Can range from unauthorized use of a credit card to comprehensive takeover of another person’s identity” “Can result in a loss of assets or creditworthiness” “Can claim many victims”

Four Types of Laws v 1) Retributive § Detailing of crime, punishments, etc. v 2) Reconstructive § Helping victims reconstruct files, setting things right v 3) Integrative § Rallying government institutions to aid v 4) Functional § Adopting measures to help detect and prevent identity theft

Identity Theft and Assumption Deterrence Act of 1998 v Historical Details § Presented by Sen. Jon Kyl (R-AZ) on March 21, 1997 § First “real” piece of IDT Legislation § Reinforced by GAO Report § Passes Senate and goes to House where mirror this one a similar legislation is amended to § Retributive, reconstructive and integrative

Provisions v Section 001. Short Title. § Act identified as “Identity Theft and Assumption Deterrence Act of 1998” v Section 002. Constitutional Authority to Enact this Legislation. § Acquires its authority from Article 1, Section 8, Clause 3 of the Constitution § “To regulate Commerce with foreign Nations, and among the several States, and with the Indian Tribes”

Provisions v Section 003. Identity Theft. § Establishes the offense of identity theft § § “knowingly transfers or uses, without lawful authority, a means of identification of another person, with the intent to commit, or to aid or abet, any unlawful activity that constitutes a violation of federal law, or that constitutes a felony under any applicable State or local law. ” Effect: Criminalizes identity theft and brings it to the federal level. Adopts broad definition of identity theft.

Provisions v Section 003. Identity Theft. (continued) § Sets down first level punishment (15 years and a fine) § “(D) an offense under paragraph (7) of such subsection that involves the transfer or use of 1 or more means of identification if, as a result of the offense, any individual committing the offense obtains anything of value aggregating $1, 000 or more during any 1 -year period. § Expands types of identification that may be abused § “or transfer of an identification document or” “, transfer, or use of a means of identification, an identification document, or a”; § Sets down second level punishment (20 years and a fine) § § § “(A) to facilitate a drug trafficking crime” “(B) in connection with a crime of violence” “(C) after a prior conviction under this section becomes final § Forfeiture of property § “Forfeiture to the United States of any personal property used or intended to be used to commit the offense”

Provisions v Section 003. Identity Theft. (continued) § Definitions § § “(1) the term ‘document-making implement’ means any implement, impression, electronic device, or computer hardware or software, that is specifically configured or primarily used for making an identification document, a false identification document, or another document-making implement; ” “(2) the term ‘identification document’ means a document made or issued by or under the authority of the United States Government, a State, political subdivision of a State, a foreign government, political subdivision of a foreign government, an international governmental or an international quasi-governmental organization which, when completed with information concerning a particular individual, is of a type intended or commonly accepted for the purpose of identification of individuals. ”

Provisions v Section 003. Identity Theft. (continued) § Definitions § § § Means of Identification: “(A) name, social security number, date of birth, official State or government issued driver’s license or identification number, alien registration number, government passport number, employer or taxpayer identification number; ” “(B) Unique biometric data, such as fingerprint, voice print, retina or iris image, or other unique physical representation; ” “(C) unique electronic identification number, address, or routing code; or” “(D) telecommunication identifying information or access device” Effects: Makes the coverage of this act very broad and long-lasting § Attempt and Conspiracy § § “Any person who attempts or conspires to commit any offense under this section shall be subject to the same penalties as those prescribed for the offense, the commission of which was the object of the attempt or conspiracy. ” Effect: Establishes a very rudimentary preventative measure

Provisions v Section 004. Amendment of Federal Sentencing Guidelines for Offenses Under Section 1028 § Implies new version of “victim” § Amending federal sentencing guidelines for appropriate punishments § Takes into account: § Impact of crime, means of identification, extent of loss, range of conduct, and so forth

Provisions v Section 005. Centralized Complaining and Consumer Education Service for Victims of Identity Theft. § Three duties § § § “(1) log and acknowledge the receipt of complaints by individuals who certify that they have a reasonable belief that 1 or more of their means of identifications… have been assumed, stolen, or otherwise unlawfully acquired in violation of section 1028 of Title 18, United States Code, as amended by this Act; “(2) provide information materials to individuals described in paragraph (1); and” “(3) refer complaints described in paragraph (1) to appropriate entities, which may include referral to— § “(A) the 3 major national consumer reporting agencies; and” § “(B) appropriate law enforcement agencies for potential law enforcement action. ” § Effect: Creates infrastructure for combating identity theft

Positive Effects v v Leads to FTC hotline, database, and education campaign Educates law enforcement and gives them a crime to pursue Makes more clear the legal basis for identity theft law Promotes new version of the “victim”

Problems v v Law enforcement will often not investigate “small thefts” even as internet helps violators target many victims No true pro-active measures to prevent identity theft Still difficult for people to detect identity theft Difficulty cleaning up a victim’s record

The Identity Theft Prevention Act of 2000 v Historical Details § Presented by Rep. Darlene Hooley (D-OR) in House and Sen. Dianne Feinstein (D-CA) in the Senate § Previous legislation seen as reactive, not proactive § Reconstructive and Functional

Provisions v Section 1. Short Title. § Act identified as “Identity Theft Prevention Act of 2000” v Section 2. Findings. § Statistics § Arguments against social security numbers § “(6) Credit issuers, credit reporting agencies, and other organizations with access to sensitive personal data have an obligation to handle such information responsibly, and should take affirmative steps to prevent identity criminals from intercepting such information; ” § Reinforces consumer as the victim and points out the inadequacy of the current system for helping them § “(9) credit reporting agencies and credit issuers should have uniform reporting requirements and effective fraud alerts to assist identity theft victims in repairing and protecting their credit” § Consumers need information about what information is collected on them

Provisions v Section 3. Change of Address. § Confirmation of changes of address § § § “(1) In general - Not later than 10 days after receiving notification from a cardholder of a change of address, a card issuer shall send to the cardholder, both to the new address and to the former address thereof, written confirmation of that change of address “(2) Notification of request for additional cards – If a card issuer receives a request for an additional credit card with respect to an existing credit account not later than 30 days after receiving notification of a change of address for that account, the card issuer shall notify the cardholder of the request at both the new address and the former address. ” Effect: Forces closer coordination between business and consumer § Duty of consumer reporting agencies § § “Notice of potential fraud – a consumer reporting agency shall notify each user of a consumer report that is a creditor… if the agency becomes aware that an application to the card issuer to open a new credit card account bears an address for the consumer that is different from the address in the file of the consumer. ” Effect: Forces corporations to search out discrepancies

Provisions v Section 3. Change of address. (Continued) § Enforcement § § v Grants FTC authority for enforcement Supremacy of the Truth in Lending Act Section 4. Fraud alerts. § Process § § Consumers request fraud alerts on file Reporting agency tells all users of this file of the existence of a fraud alert Penalties if no compliance Prevents issuance of credit unless issuer obtains verbal authorization from consumer at a number provided by the consumer or the issuer complies with preauthorization procedures mutually agreed upon by the consumer and the reporting agency

Provisions v Section 5. Regulations on duty to investigate § “Not later than 6 months after the date of enactment of this Act, the FTC shall promulgate regulations to require each consumer reporting agency… to investigate discrepancies between personal or identifying information contained in the file maintained by the agency with respect to a consumer and in the personal and identifying supplied to the agency by the user of the consumer report. § Effect: Forces closer scrutiny on parts of corporations to root out identity theft v Section 6. Free Reports Annually. § “Free annual disclosure – Upon the request of the consumer, a consumer reporting agency shall make all disclosures pursuant to section 609 once during any 12 -month period without charge to the consumer. ” § Effect: Allows people to have free annual disclosures v Section 7. Identifying information. § Amends the Fair Credit Reporting Act § Ensures certain information can only be placed in a consumer report

Provisions v Section 8. Individual Reference Services § Upon request, a service shall § “(1) clearly and accurately disclose to the consumer the nature, content, and substance of all information in the file maintained by the provider with respect to the consumer at the time of the request that is obtainable based upon the identifying information supplied by the consumer when making such request; and” § “(2) if the consumer has made a written request, deliver a written copy or photocopy of all information described in paragraph (1), together with a clear, simple, and plain meaning explanation of the information provided under this subsection, in a readable format and type, which shall in no case be smaller than 10 point type. ” § Effect: Provides better and clearer information to consumers

Provisions v Section 10. Model Forms § “In general – Six months after the date of enactment of this Act, the FTC shall develop a model form and standard procedures to be used by consumers that are victims of identity fraud in contacting and informing creditors and credit reporting agencies of such fraud, if the Commission determines, at that time, that issuers of a credit and credit reporting agencies have failed to jointly develop such a model form and standard procedures. § Effect: Standard procedure for proving that identity theft has occurred

Positive Effects v v Reallocates responsibility for protection onto businesses Tries to ensure some level of consumer awareness Early detection of identity theft Attempts to standardize fraud reporting practices

Problems v Corporate resistance § Rejects bill based on costs of reporting infrastructure § Dislikes government intervention of business practice v Present status § (House) Sitting in House Committee on Banking and Financial Services § (Senate) Sitting in Senate Committee on Banking, Housing, and Urban Affairs

Internet False Identification Prevention Act of 2000 v Historical Details § Presented by Sen. Susan Collins (RME) and Rep. Mark Green (R-WI) § Follow-up to 1998 Act § Technological aspects are addressed § Retributive and integrative

Provisions v Section 1. Short Title. § Identifies act as the “Internet False Identification Prevention Act of 2000” v Section 2. Coordinating Committee on False Identification § “(a) In general – The Attorney General and the Secretary of the Treasury shall establish a coordinating committee to ensure, thought existing interagency task forces or other means, that the creation and distribution of false identification documents is vigorously investigated and prosecuted. ” § (b) “The coordinating committee shall consist of the Secret Service, the FBI, the Department of Justice, the Social Security Administration, and the Immigration and Naturalization Services” § Effect: Combines agency efforts to combat identity theft § Term – Committee will terminate after 2 years

Provisions v Section 2. Coordinating Committee on False Identification (continued) § Committee will report to the Committee on the Judiciary in Congress - report will include: § § § “(A) the total number of indictments and informations, guilty pleas, convictions, and acquittals resulting from the investigation and prosecution of the creation and distribution of false identification documents during the preceding year. ” “(B)” Identification of the Federal judicial districts in which the indictments and informations were filed, and in which the subsequent guilty pleas, convictions, and acquittals occurred. ” “(C) specification of the Federal statutes utilized for prosecution. ” “(D)” A brief factual description of significant investigations and prosecutions; and” “(E) Specification of the sentence imposed as result of each guilty plea and conviction. ” Effects: Gives Congress a better idea of how these laws are doing.

Provisions v Section 3. False Identification. § Amends Section 1028 of Title 18 § § “(7) knowingly produces or transfers a document-making implement that is designed for use in the production of a false identification document. ” “(3) the term ‘false identification document’ means an identification document of a type intended or commonly accepted for the purposes of identification of individuals that. ” § “(A) is not issued by or under the authority of a government entity; and” § “(B) appears to be issued by o under the authority of the United States Government, a State, political subdivision of a State, a foreign government, political subdivision of a foreign government, an international governmental or an international quasi-governmental organization; ’; and”

Provisions v Section 3. False Identification. (continued) § Definition of Interactive Computer Service – “a service, system, or access software provider that-” § § § “(A) provides an information location tool to refer or link users to an online location, including a directory, index, or hypertext link; or” “(B) is engaged in the transmission, storage retrieval, hosting, formatting, or translation of a communication made by another person without selection or alteration of the content of the communication, other than that done in good faith to prevent or avoid a violation of the law. ” Effects: Gives a nod to internet technology.

Provisions v Section 3. False Identification. (continued) § Exceptions § “In general – Subsection (a)(7) shall not apply to an interactive computer service used by another person to produce or transfer a document making implement in violation of that subsection except- § “(A) to the extend that such service conspires with such other person to violate subsection (a)(7) § “(B) if, with respect to the particular activity at issue, such service has knowingly permitted its computer server or system to be used to engage in, or otherwise aided and abetted, activity that is prohibited by subsection (a)(7), with specific intent of an officer, director, partner, or controlling shareholder of such service that such server or system to be used for such purpose, or § “(c) if the material or activity available through such service consists primarily of material or activity that is prohibited by subsection (a)(7) § Effects: Negates responsibility

Effects v Positive § Brings together Federal bodies in a more cohesive manner than before § Takes into account computer services v Problems § Doesn’t deal with novelty gifts

The Identity Theft Victims Assistance Act of 2003 v Historical Details § Presented by Sen. Maria Cantwell (DWA) on September 3, 2003. § Latest legislation to deal with IDT § Functional and integrative

Provisions v Section 1. Short Title. § Identifies act as the “Identity Theft Victims Assistance Act of 2003. ” v Section 2. Findings. § Similar to the Feinstein legislation v Section 3. Treatment of Identity Theft Mitigation § Definitions § Provision of records for consumers § § To the victim Any government law enforcement agency

Provisions v Section 3. Treatment of Identity Theft Mitigation (continued) § If victim wishes to acquire a report, must provide at the corporation’s discretion § § “(A) the presentation of a government-issued identification card; ” “(B) personally identifying information of the same type as was provided to the business entity by the unauthorized person; or” “(C) personally identifying information that the business entity typically requests from new applicants or for new transactions at the time of the victim’s request for information; ” Effects: Even higher standards of security and closer coordination

Provisions v Section 3. Treatment of Identity Theft Mitigation (continued) § If a victim wishes to prove the occurrence of identity theft, must provide – at the discretion of the business § § § “(A) a copy of a police report evidencing the claim of the victim of identity theft. ” “(B) a properly completed copy of a standardized affidavit of identity theft developed and made available by the FTC; or” “(C) any properly completed affidavit of fact that is acceptable to the business entity for that purpose. ”

Provisions v Section 3. Treatment of Identity Theft Mitigation (continued) § Limitations on liability for corporations § Ability to reject the provision of information § No new record keeping obligations § Enforcement § § Attorney General can bring civil action against businesses in violation of this Act FTC powers

Provisions v Section 3. Treatment of Identity Theft Mitigation (continued) § State civil actions – attorney general of a state can bring civil action against a business to § § Enforce compliance Obtain actual damages and punitive damages (if violation is willful) Other “equitable” relief Will be limited by Federal action

Provisions v Section 5. Coordinating Committee Study § Extends Internet False Identification Prevention Act of 2000 Committee § Ends on December 28, 2005 § Report would contain § § § “(F) a comprehensive description of Federal assistance provided to State and local law enforcement agencies to address identity theft” “(G) a comprehensive description of coordination activities between Federal, State, and local law enforcement agencies that address identity theft; and” Recommend legislations and administrative changes

Effects v Positive § § § v Re-ignites corporate responsibility as an issue Balances requirements with leniency Attempts to study identity theft Problems § Same as before

Online Privacy Protection Act of 2003 v Historical details § Introduced by Rodney Frelinghuysen (R-NJ) on January 7, 2003 § Beginning to worry about flow of information in databases § Addresses internet § Ensures corporate freedoms § Functional and integrative

Provisions v Section 1. Short Title. § Identifies Act as the “Online Privacy Protection Act of 2003. ” v Section 2. Regulation of Unfair and Deceptive Acts… § Acts prohibited § § “(1) In general – it is unlawful for an operator of a web site or online service to collect use or disclose personal information in a manner that violates the regulations prescribed under subsection (b). But will not be held liable if disclosure is done in good faith

Provisions v Section 2. Regulation of Unfair and Deceptive Acts… (continued) § “(A) Require the operator of any web site or online service” § § “(i) to provide notice on its web site, in a clear and conspicuous manner, of the identity of the operator, what personal information is collected by the operator, how the operator uses such information, and what information may be shared with other companies; and” Effects: Clarity behind web site policies. “(ii) to provide a meaningful and simple online process for individuals to consent to or limit the disclosure of personal information for purposes unrelated to those for which such information was obtained or described in the notice under clause (i)” Effects: Simple consent procedures

Provisions v Section 3. Safe Harbors § Self-regulatory guidelines § If approved by FTC, deemed compliant v Section 4. Actions by States § Civil Torts § “In any case in which the attorney general of a State has reason to believe that an interest of the residents of that State has been or is threatened or adversely affected by the engagement of any person in a practice that violates any regulation of the Commission prescribed under section 2(b), the State may bring a civil action on behalf of the residents of the State in a district court of the United States of appropriate jurisdiction. ”

Effects v Positive § § § v Focus on internet Leniency for businesses Civil actions Problems § Very few

Federalism and State Rights

State Laws v Connecticut § Criminal § § (a) A person is guilty of identity theft when such person intentionally obtains personal identifying information of another person without the authorization of such other person and uses that information for any unlawful purpose including, but not limited to, obtaining, or attempting to obtain, credit, goods, services or medical information in the name of such other person without the consent of such other person. As used in this section, "personal identifying information" means a motor vehicle operator's license number, Social Security number, employee identification number, mother's maiden name, demand deposit number, savings account number or credit card number. (b) Identity theft is a class D felony.

State Laws v Connecticut § Civil § § a) Any person aggrieved by an act constituting a violation of section 53 a-129 a may bring a civil action in the Superior Court for damages against the person who committed the violation. (b) In any civil action brought under this section in which the plaintiff prevails, the court shall award the greater of one thousand dollars or treble damages, together with costs and a reasonable attorney's fee.

Conclusions (What Must Be Done) v Damage control § FTC should assist in the reconstruction of a victim’s identity § Clean their record, dismiss bankruptcies, negate criminal charges v Extend range and scope of investigations § Investigation of all IDT claims § Law enforcement reluctant to investigate smaller claims § Internet promotes multiple small transactions
 Nn identity
Nn identity Wells fargo identity theft repair kit
Wells fargo identity theft repair kit Nn identity
Nn identity Identity theft graph
Identity theft graph Identity theft prevention program
Identity theft prevention program Identity theft
Identity theft Yeh-ching chung
Yeh-ching chung Jason yeh md
Jason yeh md Peter yeh md
Peter yeh md Dr alex yeh
Dr alex yeh Bibi zehra ye dua hai lyrics in urdu written
Bibi zehra ye dua hai lyrics in urdu written Beauty poem class 6 word meaning
Beauty poem class 6 word meaning Fina3210
Fina3210 Tse-yu yeh
Tse-yu yeh Eros anne stevenson analysis
Eros anne stevenson analysis Albert yeh
Albert yeh Nc dmv license and theft bureau
Nc dmv license and theft bureau What is data interception and theft
What is data interception and theft Natural and forced response
Natural and forced response Natural response circuit
Natural response circuit Primary immune response and secondary immune response
Primary immune response and secondary immune response Identity map
Identity map Pitham v hehl
Pitham v hehl Marking cars for theft
Marking cars for theft Construction site theft prevention
Construction site theft prevention Class c misdemeanor texas
Class c misdemeanor texas Plagiarism is theft
Plagiarism is theft Cookie jar theft picture
Cookie jar theft picture Actus reus of theft
Actus reus of theft Sclc and sncc venn diagram
Sclc and sncc venn diagram Presidential and congressional reconstruction venn diagram
Presidential and congressional reconstruction venn diagram What does reconstruct mean
What does reconstruct mean With malice toward none meaning
With malice toward none meaning Father knows least
Father knows least Chapter 5 lesson 1 congressional membership
Chapter 5 lesson 1 congressional membership Congressional act of 1830
Congressional act of 1830 The structure of congress lesson 1 congressional membership
The structure of congress lesson 1 congressional membership Powers of congress
Powers of congress The structure of congress lesson 1 congressional membership
The structure of congress lesson 1 congressional membership Number of representatives per state
Number of representatives per state Reconstruction refers to the period
Reconstruction refers to the period Development of congressional powers chapter 6 answer key
Development of congressional powers chapter 6 answer key Development of congressional powers chapter 6 answer key
Development of congressional powers chapter 6 answer key Restraint on congressional salaries amendment
Restraint on congressional salaries amendment Strengthening the mid-atlantic region for tomorrow
Strengthening the mid-atlantic region for tomorrow The outsider plot diagram
The outsider plot diagram Outsiders playlist project
Outsiders playlist project Johnny from the outsiders in the hospital
Johnny from the outsiders in the hospital Johnny brown
Johnny brown How to make a johnny appleseed hat
How to make a johnny appleseed hat Dallas winston personality traits
Dallas winston personality traits Johnny tremain chapter 3
Johnny tremain chapter 3 Johnny cupcakes blog
Johnny cupcakes blog Johnny villalobos
Johnny villalobos Johnny bravo 1995
Johnny bravo 1995 Nada kth
Nada kth Johnny appleseed poem
Johnny appleseed poem Johnny rockets fresno
Johnny rockets fresno