Identity Management in Open Environments Manel Medina UPC







- Slides: 11

Identity Management in Open Environments Manel Medina UPC/ Se. Market medina@escert. upc. edu Estíbaliz Delgado ESI estibaliz. delgado@esi. es Diego Fernández ISDEFE dfvazquez@isdefe. es

Content Security Requirements Security Architecture Quantitative Identity Trustworthiness Quality Attributes and metrics Concluding remarks

Security Requirements * Perspectives: – business, legal, user and technical * User can choose any trusted digital identity * Identity management, through identity federation allows – the multi-identification and role assignment * Trust environment: – user and service need a common recognition – Integrated: PKI and different biometric identification methods (LAP compliant)

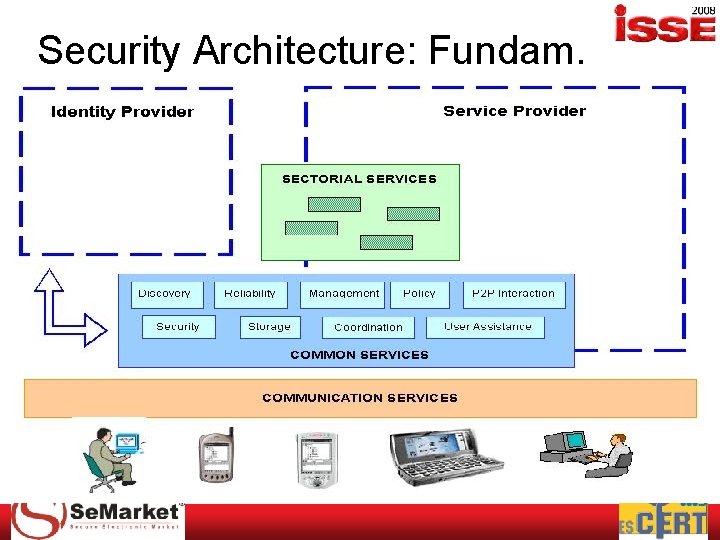
Security Architecture: Fundam.

Security Architecture: Additional Discovery, find trustable services. Reliability, to prevent Denial of Service Management, continuity security policy Storage, long term preserve documents Policy, provide trust to the whole circle. Coordination or agreement, security related to the components behaviour P 2 P Interaction, user and SP collaboration User Assistance, social engineering threats

Identity Trustworthiness Trust Management Service Level Agreement Quantitative Framework Identity manag. system trustworthiness level Monitoring and enhancement of Trust, Security and Dependability (TSD) – monitoring quality metrics on the system – periodically evaluating their trustworthiness – controlling them

Quantitative Trustworthiness User satisfaction about the requirements and expected Qo. S Trustworthiness Model – Trustworthiness Evaluation and Trustee’s decision-making – Trusted’s profile is defined and described in a Quality Profile: Trustor Quality Attrib. metrics – Trustworthiness Profile: Trustee requirements Trust Management Framework Model – Trustee evaluate Trusted trustworthiness level

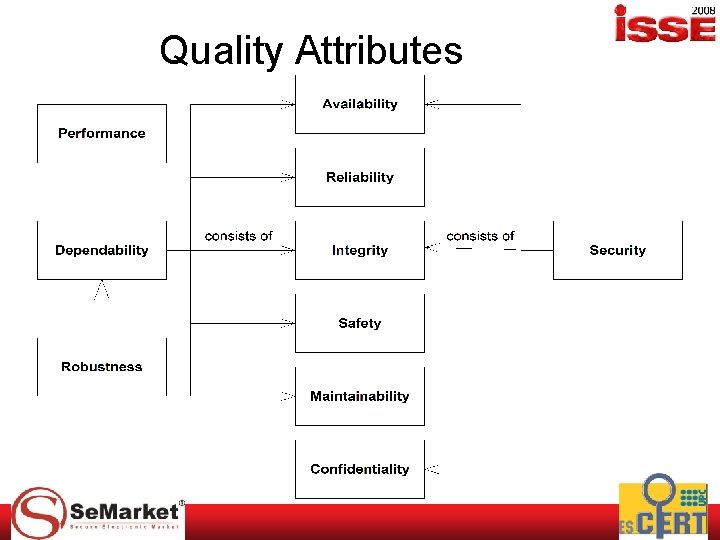
Quality Attributes

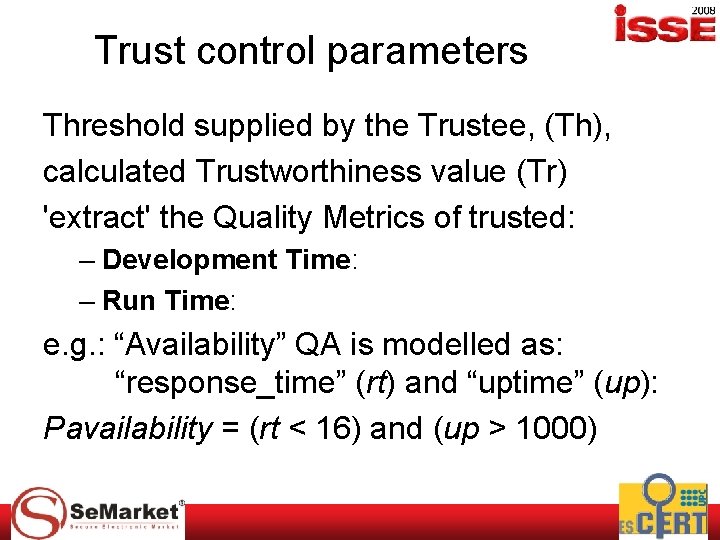
Trust control parameters Threshold supplied by the Trustee, (Th), calculated Trustworthiness value (Tr) 'extract' the Quality Metrics of trusted: – Development Time: – Run Time: e. g. : “Availability” QA is modelled as: “response_time” (rt) and “uptime” (up): Pavailability = (rt < 16) and (up > 1000)

Examples of trust control A negative compliance of the required trust level may result in: Replacement of a service e. g. – deactivation of a component c 2 that offers a security functionality and being substituted by a safer one. – the initialization of a component c 2 that allows the new component. A decrease in measure m 1 may – trigger a re-estimation of the trust attributes and compliance re-evaluation. – be re-instantiated in a different mode of operation or in a controlled environment.

Conclusions Integrate security measurement tools: – prevent abuse of confidence from other components of the environment Create chains of trust between users and (web) service providers through SLA: – multiple controls, business, ethics, PDP Identity attributes have to be shared – personal attributes will not be lost, damaged or misused by any of the intermediaries involved complex web services provision
 Vicente medina upc
Vicente medina upc Manel els millors professors europeus
Manel els millors professors europeus Open innovation open science open to the world
Open innovation open science open to the world Retail information system
Retail information system Social identity mapping
Social identity mapping Poetas murcianos para niños
Poetas murcianos para niños Salomon aguilar medina
Salomon aguilar medina Quadratic function song
Quadratic function song Emilio medina delgado
Emilio medina delgado Emperador carlos medina del campo
Emperador carlos medina del campo Edad maxima
Edad maxima Dracunculus medinensis
Dracunculus medinensis




















