Identification Authentication Lecture 15 Authentication Allows an entity

















- Slides: 25

Identification Authentication Lecture 15

Authentication Allows an entity (a user or a system) to prove its identity to another entity n Typically, the entity whose identity is verified reveals knowledge of some secret S to the verifier n Strong authentication: the entity reveals knowledge of S to the verifier without revealing S to the verifier n 2

Authentication Information Must be securely maintained by the system. 3

Elements of Authentication n n Person/group/code/system: to be authenticated Distinguishing characteristic: differentiates the entities to be authenticated Proprietor/system owner/administrator: responsible for the system Authentication mechanism: verify the distinguishing characteristic Access control mechanism: grant privileges upon successful authentication 4

Authentication Requirements n Network must ensure ¨ Data exchange is established with addressed peer entity not with an entity that masquerades or replays previous messages n n Network must ensure data source is the one claimed Authentication generally follows identification ¨ Establish validity of claimed identity ¨ Provide protection against fraudulent transactions 5

User Authentication n What the user knows ¨ Password, n What the user possesses ¨ Physical n personal information key, ticket, passport, token, smart card What the user is (biometrics) ¨ Fingerprints, voiceprint, signature dynamics 6

Passwords n n Commonly used method For each user, system stores (user name, F(password)), where F is some transformation (e. g. , one-way hash) in a password file ¨ F(password) is easy to compute ¨ From F(password), password is difficult to compute ¨ Password is not stored in the system n When user enters the password, system computes F(password); match provides proof of identity 7

Vulnerabilities of Passwords n Inherent vulnerabilities ¨ Easy to guess or snoop ¨ No control on sharing n Practical vulnerabilities ¨ Visible if unencrypted in distributed and network environment ¨ Susceptible for replay attacks if encrypted naively n Password advantage ¨ Easy to modify compromised password. 8

Weak Passwords n Bell Labs study (Morris and Thompson, 1979), 3289 passwords were examined ¨ 15 single ASCII characters, 72 two ASCII characters, 464 three ASCII characters, 477 four ASCII characters, 706 five letters (all lower case or all upper case), 605 six letters, all lower case, 492 week passwords (name, dictionary words, etc. ) ¨ Summary: 2831 passwords (86% of the sample) were weak, i. e. , either too easy to predict or too short 9

Attacks on Password Guessing attack/dictionary attack n Social Engineering n Sniffing n Trojan login n Van Eck sniffing n 10

Guessing Attack Exploits human nature to use easy to remember passwords n Trial-and-error attack n Easy to detect (failed logins) and block n Need audit mechanism n 11

Social Engineering Attacker asks for password by masquerading as somebody else (not necessarily an authenticated user) n May be difficult to detect n Protection against social engineering: strict security policy and users’ education n 12

Dictionary Attacks on Passwords n n n Attack 1: ¨ Create dictionary of common words and names and their simple transformations ¨ Use these to guess password Attack 2: ¨ Usually F is public and so is the password file (encrypted) ¨ Compute F(word) for each word in dictionary ¨ Find match Attack 3: ¨ Pre-compute dictionary ¨ Look up matches 13

Password Salt n n n Used to make dictionary attack more difficult Salt is a 12 bit number between 0 and 4095 It is derived from the system clock and the process identifier Compute F(password+salt); both salt and F(password+salt) are stored in the password table User: gives password, system finds salt and computes F(password+salt) and check for match Note: with salt, the same password is computed in 4096 ways 14

Password Management Policy Educate users to make better choices n Define rules for good password selection and ask users to follow them n Ask or force users to change their password periodically n Actively attempt to break user’s passwords and force users to change broken ones n Screen password choices n 15

One-time Password Use the password exactly once! 16

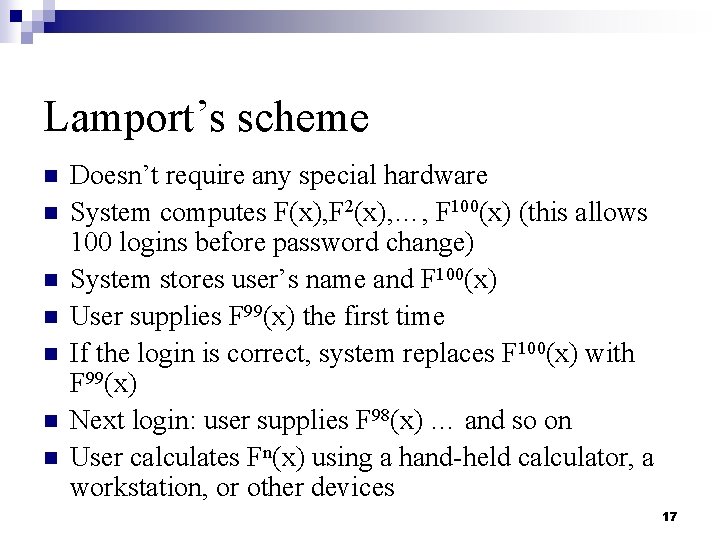
Lamport’s scheme n n n n Doesn’t require any special hardware System computes F(x), F 2(x), …, F 100(x) (this allows 100 logins before password change) System stores user’s name and F 100(x) User supplies F 99(x) the first time If the login is correct, system replaces F 100(x) with F 99(x) Next login: user supplies F 98(x) … and so on User calculates Fn(x) using a hand-held calculator, a workstation, or other devices 17

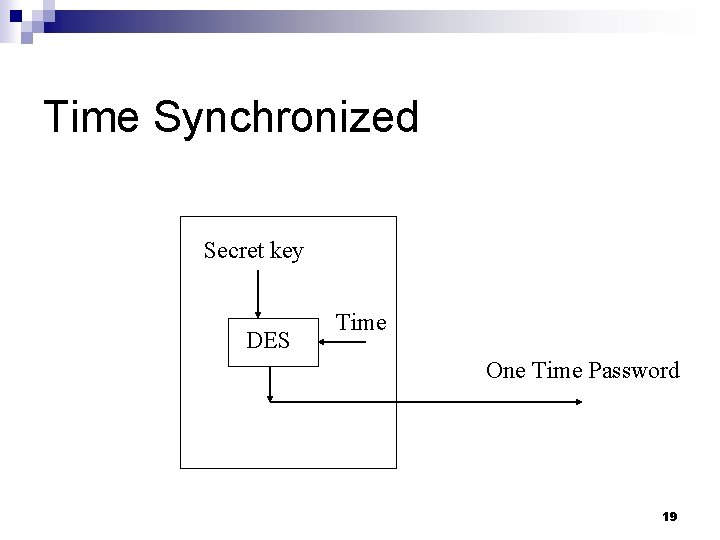
Time Synchronized n There is a hand-held authenticator ¨ It contains an internal clock, a secret key, and a display ¨ Display outputs a function of the current time and the key ¨ It changes about once per minute n n n User supplies the user id and the display value Host uses the secret key, the function and its clock to calculate the expected output Login is valid if the values match 18

Time Synchronized Secret key DES Time One Time Password 19

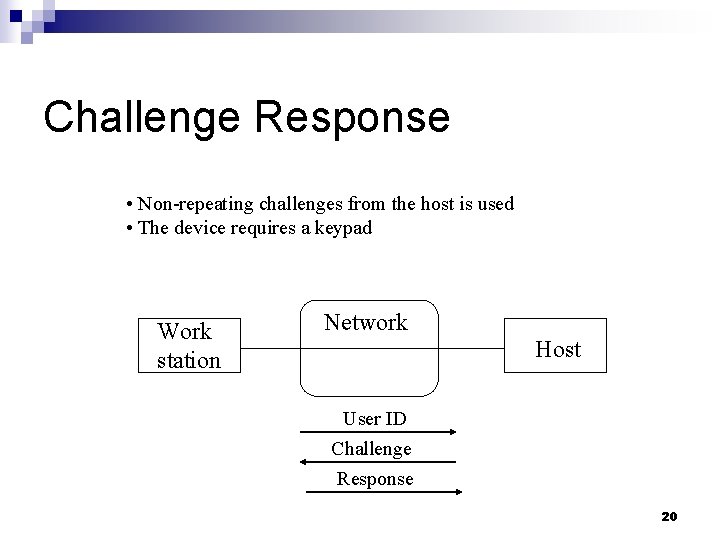
Challenge Response • Non-repeating challenges from the host is used • The device requires a keypad Work station Network Host User ID Challenge Response 20

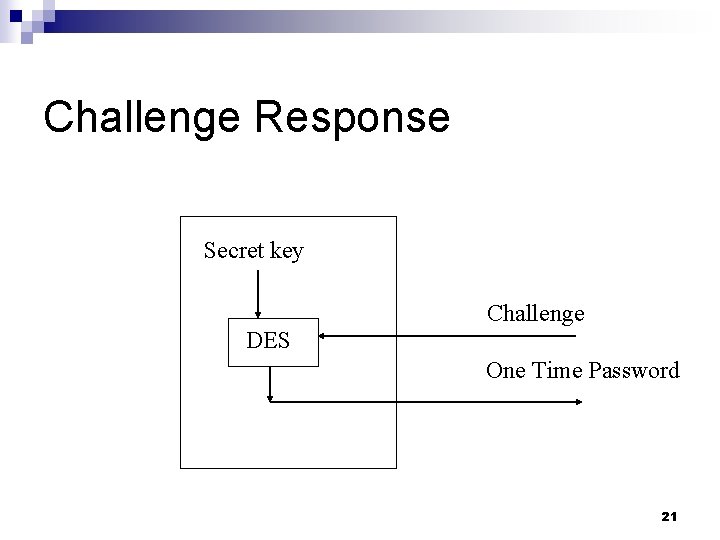
Challenge Response Secret key Challenge DES One Time Password 21

Devices with Personal Identification Number (PIN) Devices are subject to theft, some devices require PIN (something the user knows) n PIN is used by the device to authenticate the user n Problems with challenge/response schemes n ¨ Key database is extremely sensitive ¨ This can be avoided if public key algorithms are used 22

Smart Cards Portable devices with a CPU, I/O ports, and some nonvolatile memory n Can carry out computation required by public key algorithms and transmit directly to the host n Some use biometrics data about the user instead of the PIN n 23

Biometrics Fingerprint n Retina scan n Voice pattern n Signature n Typing style n 24

Problems with Biometrics n Expensive ¨ Retina scan (min. cost) about $ 2, 200 ¨ Voice (min. cost) about $ 1, 500 ¨ Signature (min. cost) about $ 1, 000 n False readings ¨ Retina scan 1/10, 000+ ¨ Signature 1/50 ¨ Fingerprint 1/500 n Can’t be modified when compromised 25