ICS Cyber Kill Chain Case Study Dr Stephen

ICS Cyber Kill Chain – Case Study Dr. Stephen Hayne Deputy Director, Colorado Center for Cyber Security

Introduction ● ICS are a High Value Target (!) ● rival nations’ want to attack each others infrastructure ● hackers want to collect ransom ● hacktivists want to disrupt business ● 56% of organizations using ICS reported a breach in the past year, and only 11% indicate they have never been breached (Forrester) ● ICS are growing at 6. 6% as new projects come online and are controlled across global networks
ICS Attack Highlights ● Stuxnet (2010) – four “ 0 -days”, infected 200 k+ computers and damaged 1000 centrifuges. ● Shamoon (2012) – damaged 50 k+ servers ● Black. Energy 3 (2015) – caused outage to 225 k+ customers ● unkown (2016) – valves hacked and chemical mix manipulated ● Triton (2017) – took over entire plant’s Safety Instrument Systems ● Ryuk (2019) – locked down admin systems

Ukraine Power Grid Attack (M. Mc. Kinney) ● Cyber-attack on Ukraine Power Grid - December 23, 2015. ● Highly coordinated and efficient cyber attack on three Ukrainian “oblenergos” (energy company) – simultaneously. ● Attacks on the Ukrainian oblenergos were executed within 30 minutes of each other. ● Attack impacted 225, 000 customers who lost power for many hours. ● Attack required the oblenergos to move to manual operations.
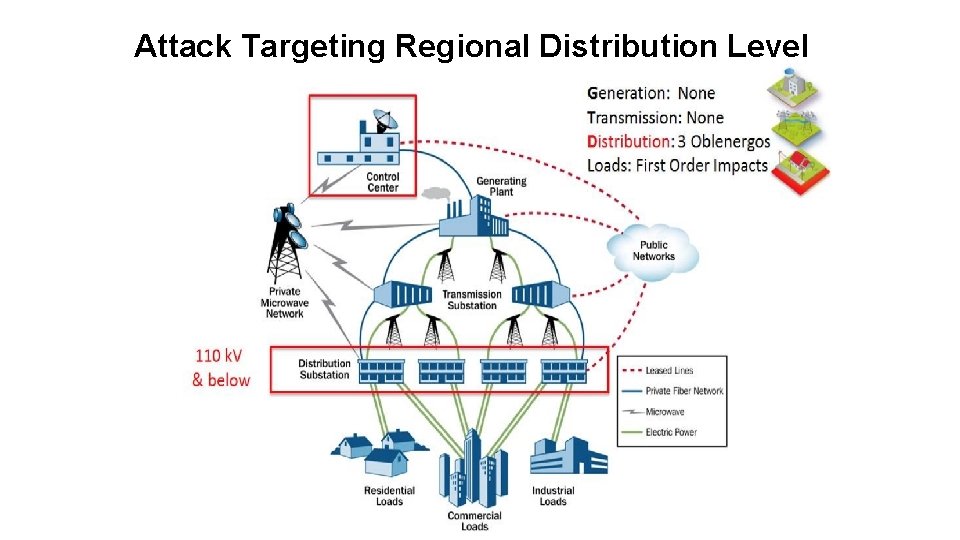
Attack Targeting Regional Distribution Level
Ukraine Power Grid Attack – At A Glance Spear phishing to gain access to the business networks of the oblenergos. ● Planting of Black. Energy 3 (toolkit) at the three oblenergos. ● Theft of credentials from the business networks. ● Use of VPN to enter the ICS network (SCADA) using same credentials(!). ● Use of existing remote access tools to issue commands directly from a remote station as it was an operator HMI. ● Downloading and installing firmware on serial-to-ethernet communication devices. ● Use of modified Kill. Disk to erase the MBR and for targeted deletion of logs. ● Disrupting UPS system to impact connected load on service outage. ● Telephone denial-of-service attack on the call center. ●
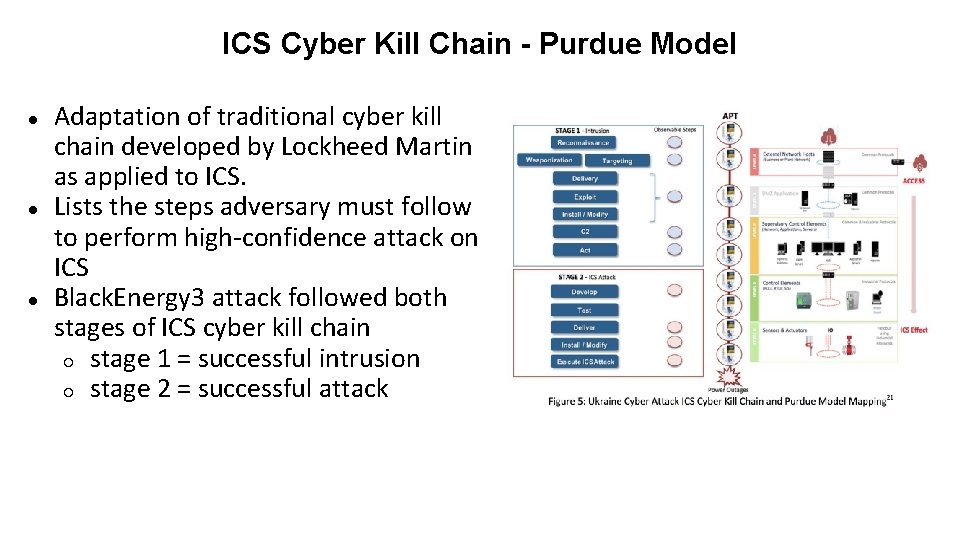
ICS Cyber Kill Chain - Purdue Model ● ● ● Adaptation of traditional cyber kill chain developed by Lockheed Martin as applied to ICS. Lists the steps adversary must follow to perform high-confidence attack on ICS Black. Energy 3 attack followed both stages of ICS cyber kill chain ○ stage 1 = successful intrusion ○ stage 2 = successful attack
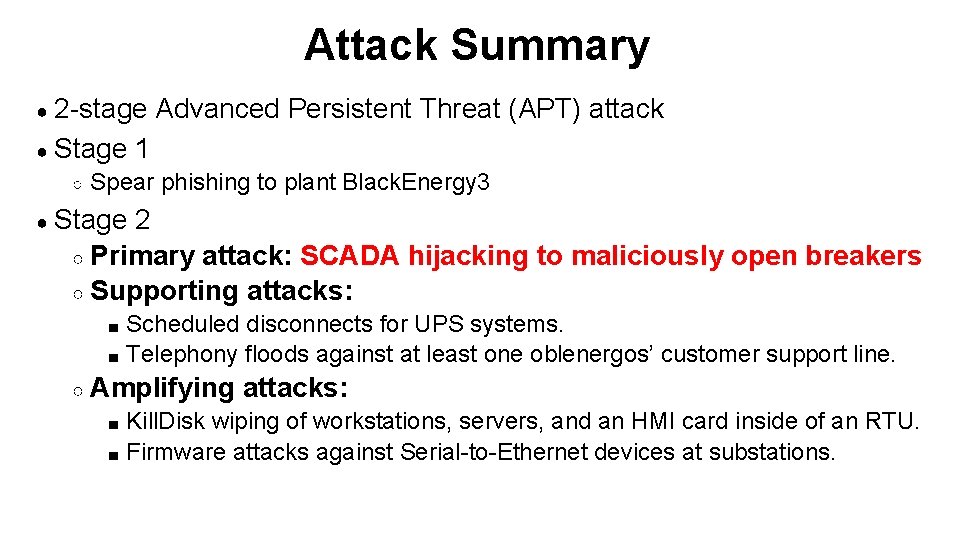
Attack Summary ● 2 -stage ● Stage ○ Advanced Persistent Threat (APT) attack 1 Spear phishing to plant Black. Energy 3 ● Stage 2 ○ Primary attack: SCADA hijacking to maliciously open breakers ○ Supporting attacks: Scheduled disconnects for UPS systems. ■ Telephony floods against at least one oblenergos’ customer support line. ■ ○ Amplifying attacks: Kill. Disk wiping of workstations, servers, and an HMI card inside of an RTU. ■ Firmware attacks against Serial-to-Ethernet devices at substations. ■

Why Could the Attack Happen? ● Open-source and publicly available information on ICS systems and types of equipment. ○ Detailed list of types of infrastructure equipment (such as RTU) and versions posted online by ICS vendors. ● VPNs into the ICS lacked two-factor authentication. ● Firewall on the ICS network allowed the adversary to remote admin out of the ICS environment using capability native to the systems. ● Total lack of mechanisms and tools to continually monitor the ICS network and search for abnormalities and threats.
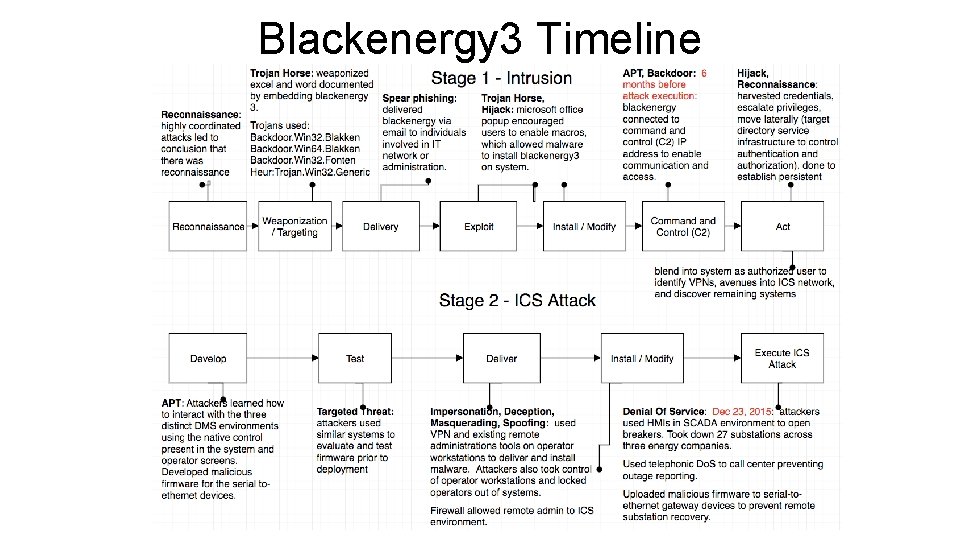
Blackenergy 3 Timeline
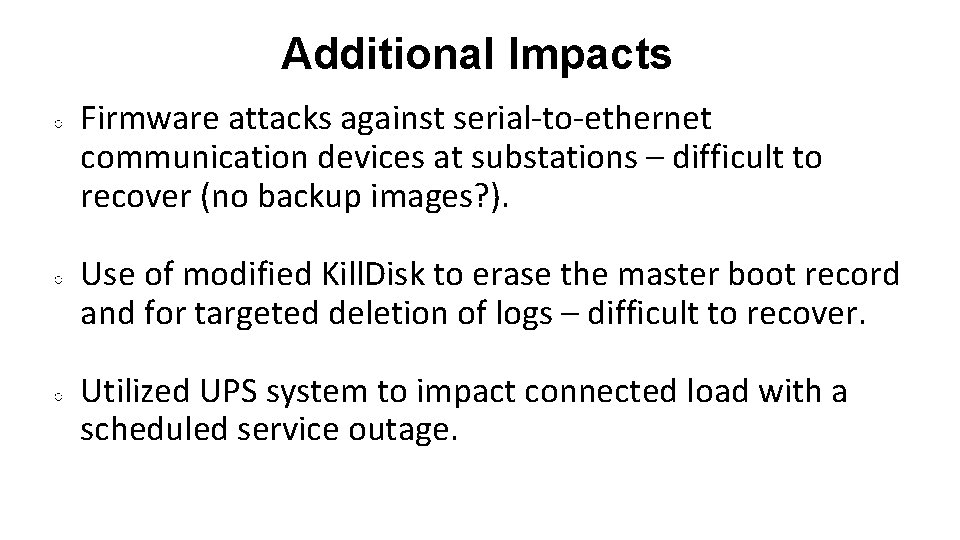
Additional Impacts ○ ○ ○ Firmware attacks against serial-to-ethernet communication devices at substations – difficult to recover (no backup images? ). Use of modified Kill. Disk to erase the master boot record and for targeted deletion of logs – difficult to recover. Utilized UPS system to impact connected load with a scheduled service outage.

Thoughts ● ● ● Spearphishing - exploits used took advantage of macro functionality built into MS Office to launch attack on windows computers. All Windows computers capable of using these macros can be exploited by Black. Energy trojans. Used existing tools to gain access to ICS network Neither Black. Energy 3 nor Kill. Disk contained the automated components to cause the outage. The outages were caused by use of the control systems and their software through direct interaction by the adversary.

Takeaways ○ IT and Ops networks ARE connected ○ Attack surface increases in a non-linear fashion… when GPS, RFID, and Wi-Fi devices can connect. ○ Ops networks appear to be unmonitored ○ “Integrated” audits should be performed ○ Automated attacks are coming for Ops networks ○ Honeynet reveals FOUR 0 -days (Cy. Con May, 2020)

Contact Info Stephen Hayne Colorado State University Stephen. Hayne@Colo. State. EDU +1 -970 -491 -7511

References ● ● ● ● https: //ics. sans. org/media/E-ISAC_SANS_Ukraine_DUC_5. pdf https: //usa. kaspersky. com/resource-center/threats/blackenergy https: //www. sans. org/reading-room/whitepapers/ICS/industrial-controlsystem-cyber-kill-chain-36297 https: //www. oilandgas-blog. com/en/anatomy-cyber-attack-1/ https: //www. oilandgas-blog. com/en/counter-measures-cyber-attack/ https: //ccdcoe. org/library/publications/12 th-international-conference-oncyber-conflict-20 -20 -vision-the-next-decade-proceedings-2020/ https: //www. theregister. com/2016/03/24/water_utility_hacked/
- Slides: 15