IBM Software Group Integrated Security Architecture James Andoniadis

® IBM Software Group Integrated Security Architecture James Andoniadis IBM Canada © 2004 IBM Corporation
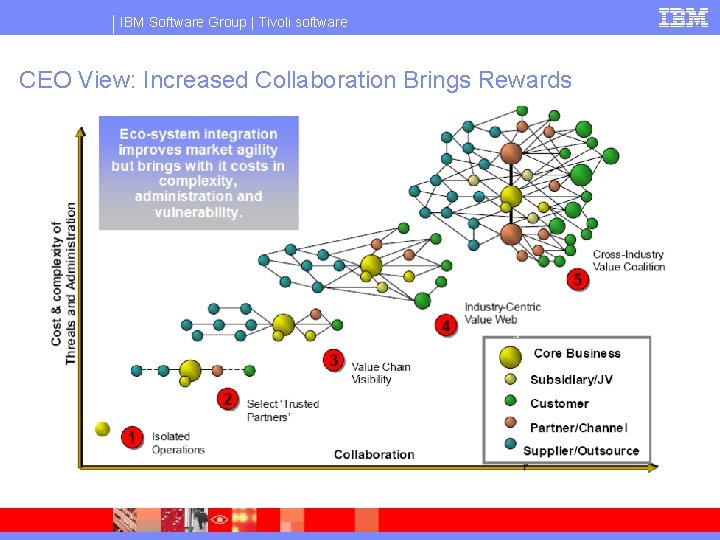
IBM Software Group | Tivoli software CEO View: Increased Collaboration Brings Rewards

IBM Software Group | Tivoli software Layers of security Perimeter Defense Control Layer Assurance Layer Keep out unwanted with • Firewalls • Anti-Virus • Intrusion Detection, etc. Control Layer • Which users can come in? • What can users see and do? • Are user preferences supported? • Can user privacy be protected? Assurance Layer • Can I comply with regulations? • Can I deliver audit reports? • Am I at risk? • Can I respond to security events?
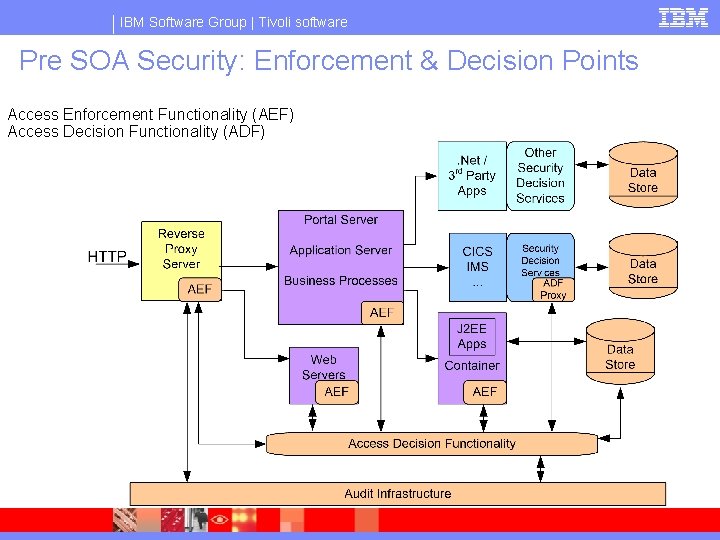
IBM Software Group | Tivoli software Pre SOA Security: Enforcement & Decision Points Access Enforcement Functionality (AEF) Access Decision Functionality (ADF)
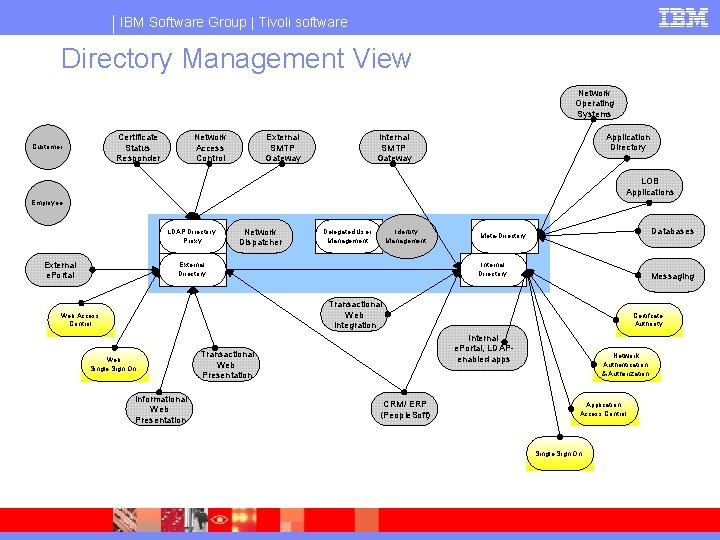
IBM Software Group | Tivoli software Directory Management View Network Operating Systems Certificate Status Responder Customer Network Access Control External SMTP Gateway Application Directory Internal SMTP Gateway LOB Applications Employee LDAP Directory Proxy External e. Portal Network Dispatcher Delegated User Management Identity Management External Directory Databases Meta-Directory Internal Directory Messaging Transactional Web Integration Web Access Control Web Single Sign On Informational Web Presentation Certifcate Authority Internal e. Portal, LDAPenabled apps Transactional Web Presentation CRM/ ERP (People. Soft) Network Authentication & Authorization Application Access Control Single Sign On
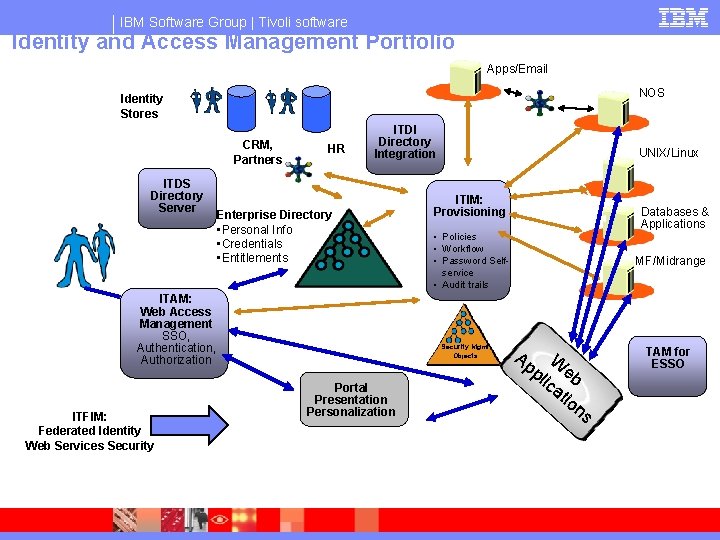
IBM Software Group | Tivoli software Identity and Access Management Portfolio Apps/Email NOS Identity Stores CRM, Partners ITDS Directory Server HR ITDI Directory Integration Enterprise Directory • Personal Info • Credentials • Entitlements ITAM: Web Access Management SSO, Authentication, Authorization ITFIM: Federated Identity Web Services Security UNIX/Linux ITIM: Provisioning • Policies • Workflow • Password Selfservice • Audit trails Security Mgmt Objects Portal Presentation Personalization Databases & Applications MF/Midrange Ap W pl eb ica tio ns TAM for ESSO
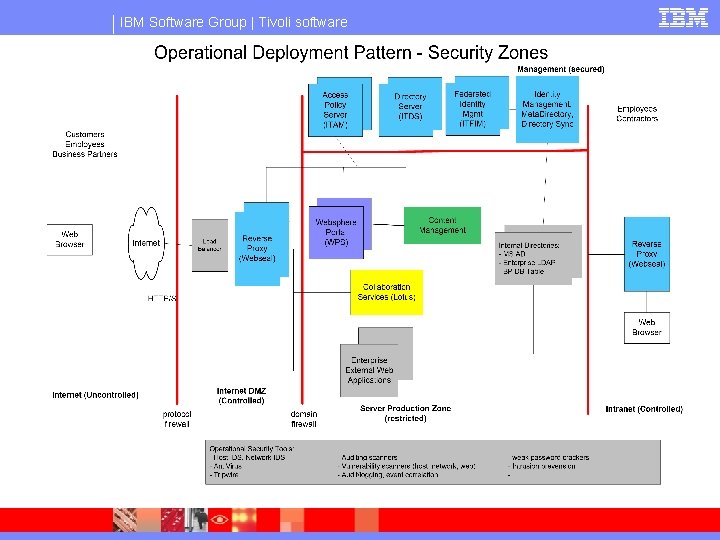
IBM Software Group | Tivoli software

IBM Software Group | Tivoli software Governments as Identity Providers Users “TRUST provides ACCESS” Germany: Identity Provider USA: Identity Provider The United States is an “Identity Provider” because it issues a Passport as proof of identification USA Vouches for its Citizens Users China: Identity Provider
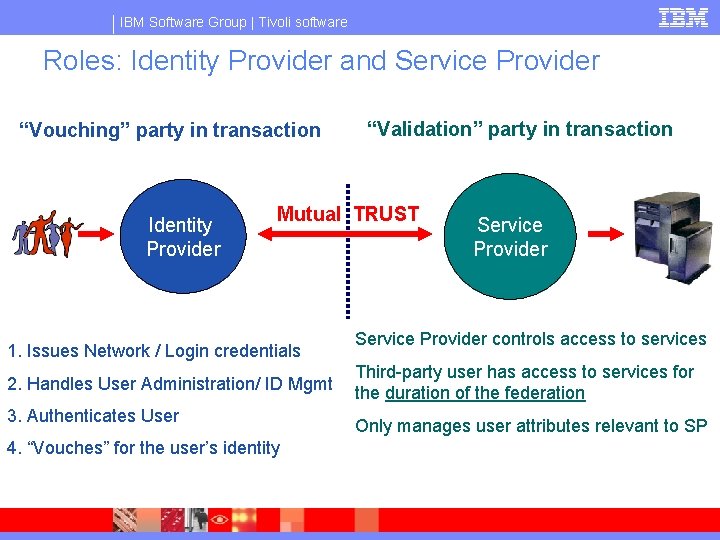
IBM Software Group | Tivoli software Roles: Identity Provider and Service Provider “Vouching” party in transaction Identity Provider “Validation” party in transaction Mutual TRUST 1. Issues Network / Login credentials 2. Handles User Administration/ ID Mgmt 3. Authenticates User 4. “Vouches” for the user’s identity Service Provider controls access to services Third-party user has access to services for the duration of the federation Only manages user attributes relevant to SP
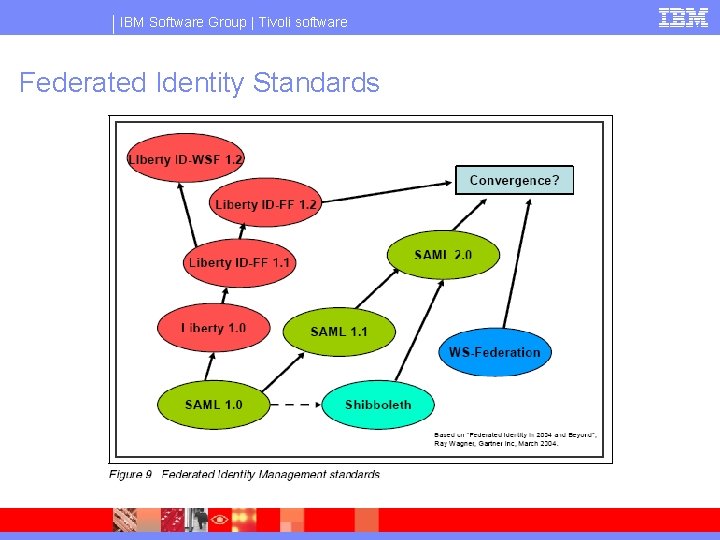
IBM Software Group | Tivoli software Federated Identity Standards

IBM Software Group | Tivoli software Agenda § Enterprise Security Architecture – MASS Intro § Identity, Access, and Federated Identity Management § SOA Security
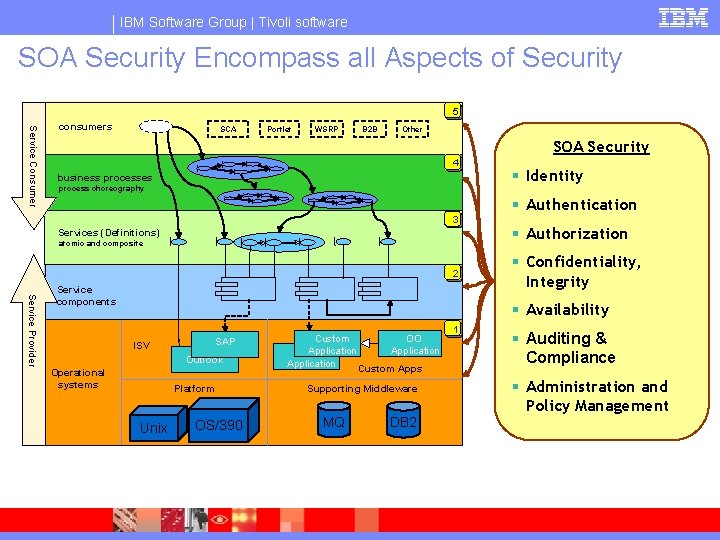
IBM Software Group | Tivoli software SOA Security Encompass all Aspects of Security 55 Service Consumer consumers SCA Portlet WSRP B 2 B Other SOA Security 44 businessprocesses process choreography § Identity § Authentication 33 Services services (Definitions) atomic and composite 22 Service Provider Service components § Authorization § Confidentiality, Integrity § Availability ISV Operational systems Packaged SAP Packaged Application Outlook Application Platform Unix OS/390 Custom Application OO Application Custom Apps Supporting Middleware MQ DB 2 11 § Auditing & Compliance § Administration and Policy Management
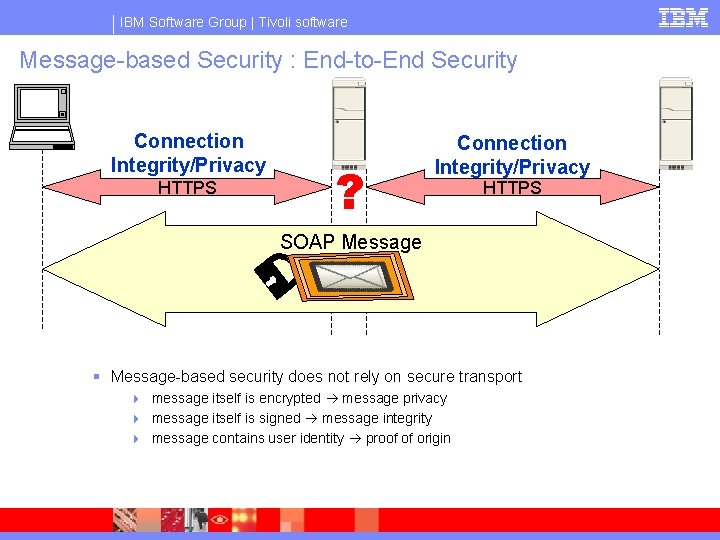
IBM Software Group | Tivoli software Message-based Security : End-to-End Security Connection Integrity/Privacy HTTPS ? Connection Integrity/Privacy HTTPS SOAP Message § Message-based security does not rely on secure transport 4 message itself is encrypted message privacy 4 message itself is signed message integrity 4 message contains user identity proof of origin
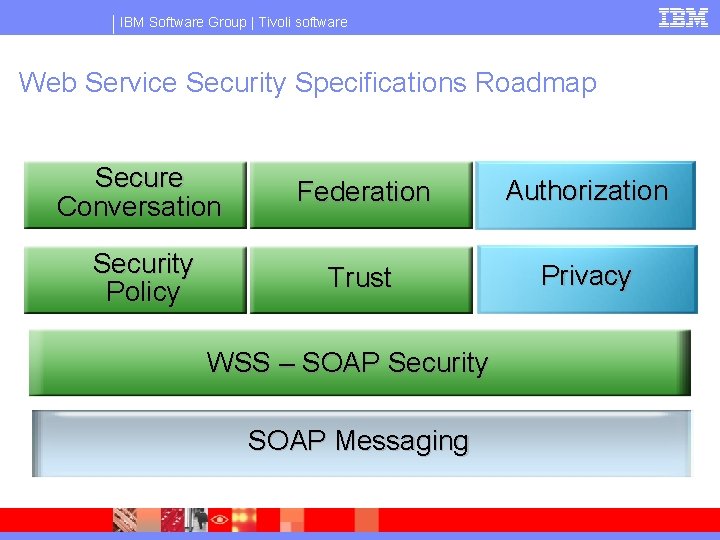
IBM Software Group | Tivoli software Web Service Security Specifications Roadmap Secure Conversation Federation Authorization Security Policy Trust Privacy WSS – SOAP Security SOAP Messaging
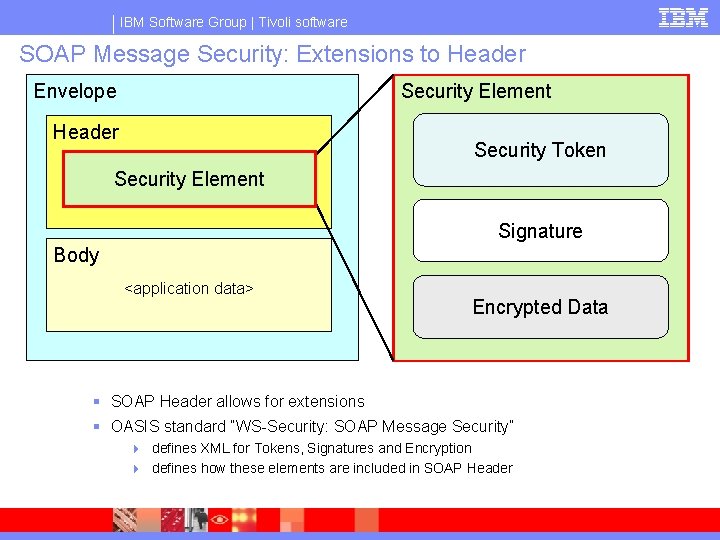
IBM Software Group | Tivoli software SOAP Message Security: Extensions to Header Envelope Security Element Header Security Token Security Element Signature Body <application data> Encrypted Data § SOAP Header allows for extensions § OASIS standard “WS-Security: SOAP Message Security” 4 defines XML for Tokens, Signatures and Encryption 4 defines how these elements are included in SOAP Header
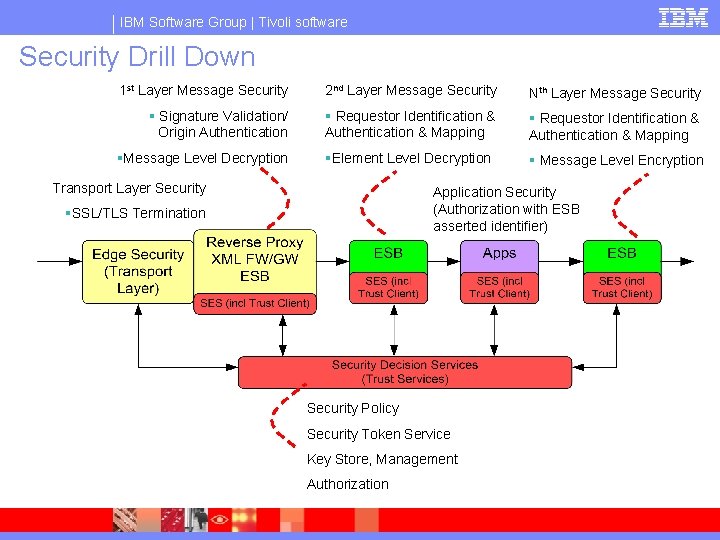
IBM Software Group | Tivoli software Security Drill Down 1 st Layer Message Security 2 nd Layer Message Security Nth Layer Message Security § Signature Validation/ Origin Authentication § Requestor Identification & Authentication & Mapping §Element Level Decryption § Message Level Encryption §Message Level Decryption Transport Layer Security Application Security (Authorization with ESB asserted identifier) §SSL/TLS Termination Security Policy Security Token Service Key Store, Management Authorization
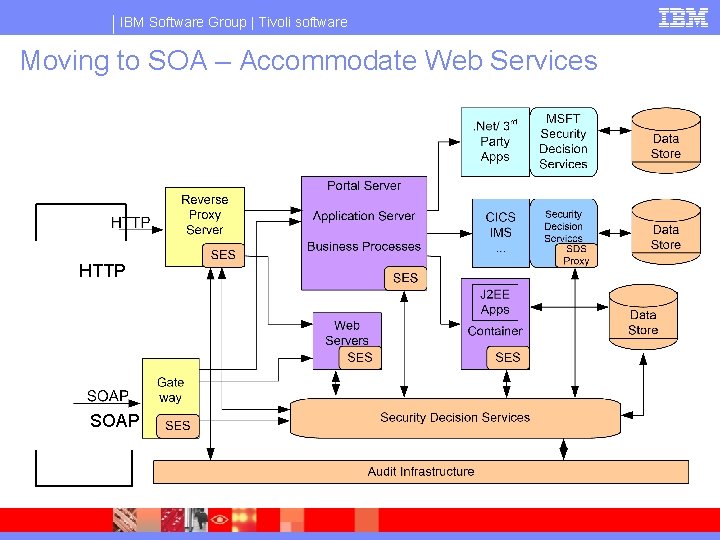
IBM Software Group | Tivoli software Moving to SOA – Accommodate Web Services HTTP SOAP
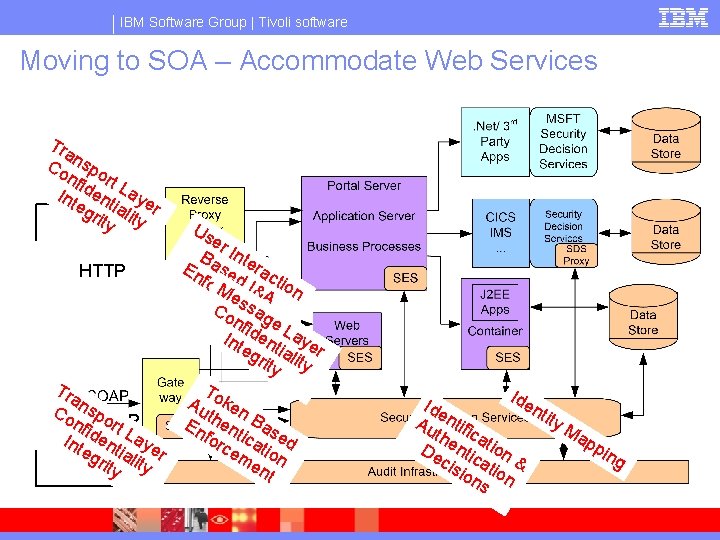
IBM Software Group | Tivoli software Moving to SOA – Accommodate Web Services Tra Co nspo nfi rt Int dent Laye eg ial r rity HTTP Tra Co nspo nfi SOAP rt L d e Int nt aye eg ial r rity Us er Ba Inte En se rac for. M d I& tio cee A n sse Co m a nfi ngt e L Int dent aye eg ial r rity To Au ken t En hen Bas for tica ed ce tio me n nt Ide nti ty Au ntifi Ma the cat pp De ntic ion ing cis at & ion s
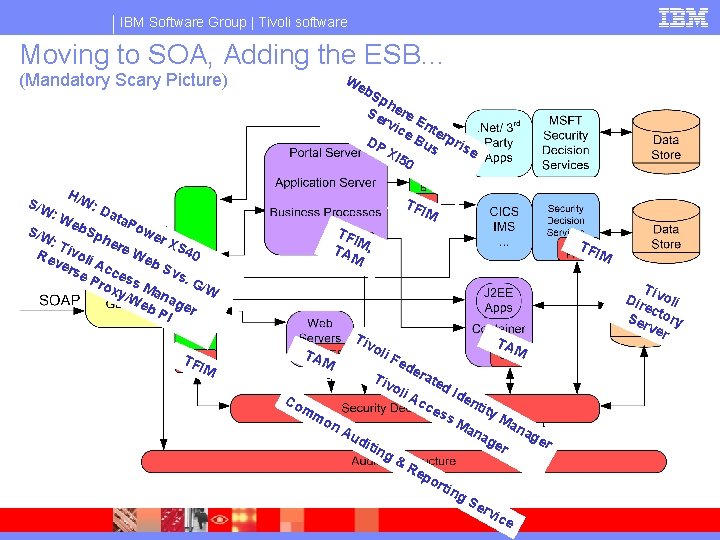
IBM Software Group | Tivoli software Moving to SOA, Adding the ESB… (Mandatory Scary Picture) S/W We b. S ph Se ere rvi En ce ter Bu pri DP se s XI 5 0 H/W TFI M : D ata : W Po e b S/W we Sp he r. X : T re S 4 i v We Re 0 oli ver b. S Ac se c vs. Pro ess G/W M xy/ a n We ag b P er I TFI M TA , M TA M TFI Tiv M oli Fe d TA M era Tiv ted oli Ide Ac Co nti c mm es ty s. M Ma on na an Au ge a dit ge r r ing &R ep ort ing Se rvi ce T Dir ivoli ec Ser tory ver
IBM Software Group | Tivoli software Further Reading § On Demand Operating Environment: Security Considerations in an Extended Enterprise 4 http: //publib-b. boulder. ibm. com/abstracts/redp 3928. html? Open § Web Services Security Standards, Tutorials, Papers 4 http: //www. ibm. com/developerworks/views/webservices/standards. jsp 4 http: //www. ibm. com/developerworks/views/webservices/tutorials. jsp 4 http: //webservices. xml. com/ § Websphere Security Fundamentals / WAS 6. 0 Security Handbook 4 http: //www. redbooks. ibm. com/redpieces/abstracts/redp 3944. html? Open 4 http: //www. redbooks. ibm. com/redpieces/abstracts/sg 246316. html? Open § IBM Tivoli Product Home Page 4 http: //www. ibm. com/software/tivoli/solutions/security/

IBM Software Group | Tivoli software Summary § End-to-end Security Integration is complex § Web Services and SOA security are emerging areas 4 Moving from session level security to message level security § Identity Management incorporates several security services, but other security services need to be integrated as well 4 Audit and Event Management, Compliance and Assurance 4 Etc. § Security technology is part – process, policy, people are the others and often harder to change § Only Constant is Change, but evolve around the fundamentals 4 Establish separation of application and security management 4 Use of open standards will help with integration of past and future technologies

IBM Software Group | Tivoli software Questions?
IBM Software Group | Tivoli software Security 101 Definitions § Authentication - Identify who you are 4 Userid/password, PKI certificates, Kerberos, Tokens, Biometrics § Authorization – What you can access 4 Access Enforcement Function / Access Decision Function 4 Roles, Groups, Entitlements § Administration – Applying security policy to resource protection 4 Directories, administration interfaces, delegation, self-service § Audit – Logging security success / failures 4 Basis of monitoring, accountability/non-repudiation, investigation, forensics § Assurance – Security integrity and compliance to policy 4 Monitoring (Intrusion Detection, Anti. Virus, Compliance), Vulnerability Testing § Asset Protection 4 Data Confidentiality, Integrity, Data Privacy § Availability 4 Backup/recovery, disaster recovery, high availability/redundance

IBM Software Group | Tivoli software Agenda § Enterprise Security Architecture – MASS Intro § Identity, Access, and Federated Identity Management § SOA Security
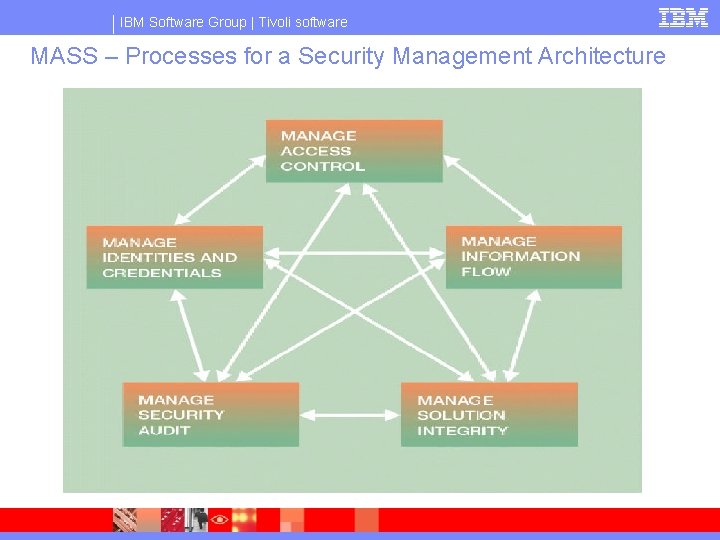
IBM Software Group | Tivoli software MASS – Processes for a Security Management Architecture

IBM Software Group | Tivoli software Access Control Subsystem Purpose: § Enforce security policies by gating access to, and execution of, processes and services within a computing solution via identification, authentication, and authorization processes, along with security mechanisms that use credentials and attributes. Functions: § Access control monitoring and enforcement: Policy Enforcement Point/Policy Decision Point/ Policy Administration Point § Identification and authentication mechanisms, including verification of secrets, cryptography (encryption and signing), and single-use versus multiple-use authentication mechanisms § Authorization mechanisms, to include attributes, privileges, and permissions § Enforcement mechanisms, including failure handling, bypass prevention, banners, timing and timeout, event capture, and decision and logging components Sample Technologies: § RACF, platform/application security, web access control

IBM Software Group | Tivoli software Identity and Credential Subsystem Purpose: § Generate, distribute, and manage the data objects that convey identity and permissions across networks and among the platforms, the processes, and the security subsystems within a computing solution. Functions: § Single-use versus multiple-use mechanisms, either cryptographic or noncryptographic § Generation and verification of secrets § Identities and credentials to be used in access control: identification, authentication, and access control for the purpose of user-subject binding § Credentials to be used for purposes of identity in legally binding transactions § Timing and duration of identification and authentication § Lifecycle of credentials § Anonymity and pseudonymity mechanisms Sample Technologies: § Tokens (PKI, Kerberos, SAML), User registries (LDAP, AD, RACF, …), Administration consoles, Session management

IBM Software Group | Tivoli software Information Flow Control Subsystem Purpose: § Enforce security policies by gating the flow of information within a computing solution, affecting the visibility of information within a computing solution, and ensuring the integrity of information flowing within a computing solution. Functions: § Flow permission or prevention § Flow monitoring and enforcement § Transfer services and environments: open or trusted channel, open or trusted path, media conversions, manual transfer, and import to or export between domain § Encryption § Storage mechanisms: cryptography and hardware security modules Sample Technologies: § Firewalls, VPNs, SSL

IBM Software Group | Tivoli software Security Audit Subsystem Purpose: § Provide proof of compliance to the security policy. Functions: § Collection of security audit data, including capture of the appropriate data, trusted transfer of audit data, and synchronization of chronologies § Protection of security audit data, including use of time stamps, signing events, and storage integrity to prevent loss of data § Analysis of security audit data, including review, anomaly detection, violation analysis, and attack analysis using simple heuristics or complex heuristics § Alarms for loss thresholds, warning conditions, and critical events Sample Technologies: § syslog, application/platform access logs

IBM Software Group | Tivoli software Solution Integrity Subsystem Purpose: § address the requirement for reliable and correct operation of a computing solution in support of meeting the legal and technical standard for its processes Functions: § Physical protection for data objects, such as cryptographic keys, and physical components, such as cabling, hardware, and so on § Continued operations including fault tolerance, failure recovery, and self-testing § Storage mechanisms: cryptography and hardware security modules § Accurate time source for time measurement and time stamps § Alarms and actions when physical or passive attack is detected Sample Technologies: § Systems Management solutions - performance, availability, disaster recovery, storage management § Operational Security tools: , Host and Network Intrusion Detection Sensors (Snort), Event Correlation tools, Host security monitoring/enforcement tools (Tripwire, TAMOS), Host/Network Vulnerability Monitors/Scanners (Neesus), Anti-Virus software
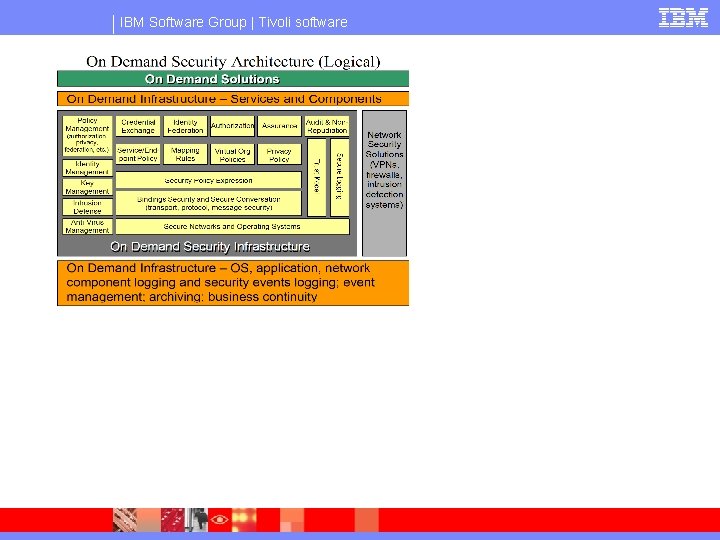
IBM Software Group | Tivoli software
- Slides: 31