IBM SOA Security Total SOA Assurance A framework

® IBM SOA Security Total SOA Assurance. A framework for SOA Security Template Documentation © IBM Corporation
IBM SOA Security Agenda Introduction to SOA Security Reference Model SOA Security Scenarios SOA Security Logical Architecture Summary 2

® IBM SOA Security Introduction to Service Oriented Architecture Template Documentation © IBM Corporation

IBM SOA Security What is the SOA model? Business Componentization Business components Re-defining today’s monolithic enterprise processes as a set of standardized modular business process components Service Oriented Architecture SOA application components * An IT model which mirrors the interaction of business components through a set of IT applications implemented as real-time services that interact dynamically Web Services WS Protocols (XML, SOAP, WSDL, UDDI) provide an interface toolkit for components A set of vendor neutral and platform agnostic standards that can be used to define how SOA components interact * Each SOA application component may be made up of multiple applications Business components SOA components Components interfaces Web Services protocols 4
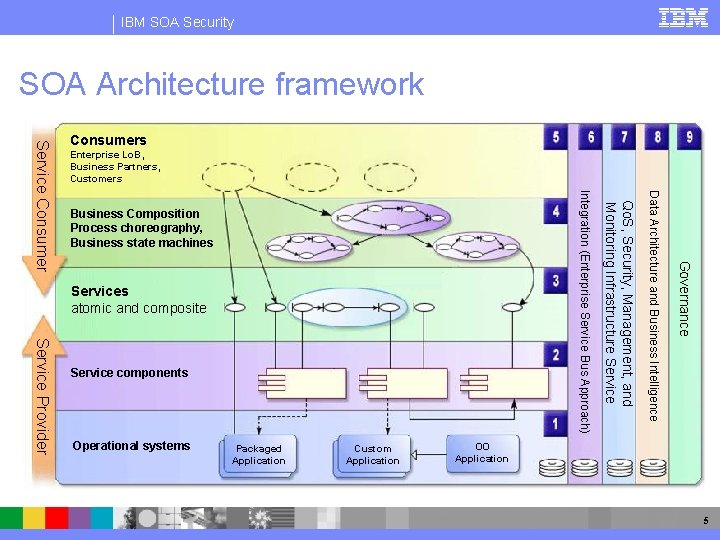
IBM SOA Security SOA Architecture framework Enterprise Lo. B, Business Partners, Customers Service Provider Service components Operational systems Packaged Application Custom Application Governance Services atomic and composite Data Architecture and Business Intelligence Business Composition Process choreography, Business state machines Qo. S, Security, Management, and Monitoring Infrastructure Service Integration (Enterprise Service Bus Approach) Service Consumers OO Application 5
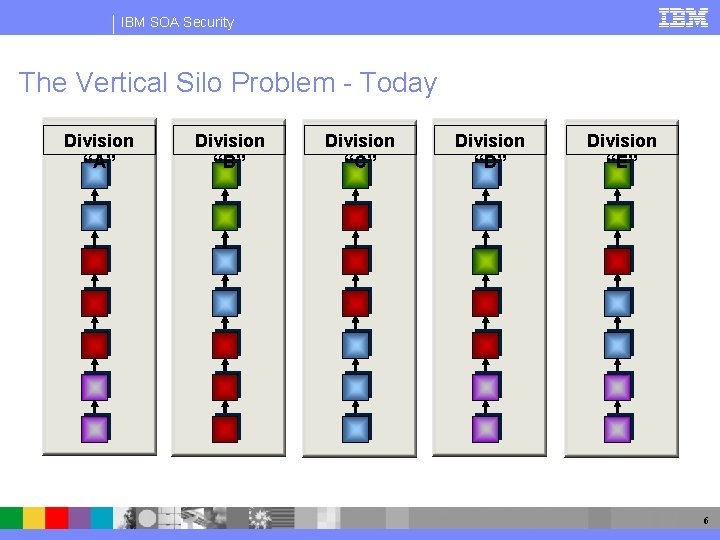
IBM SOA Security The Vertical Silo Problem - Today Division “A” Division “B” Division “C” Division “D” Division “E” 6
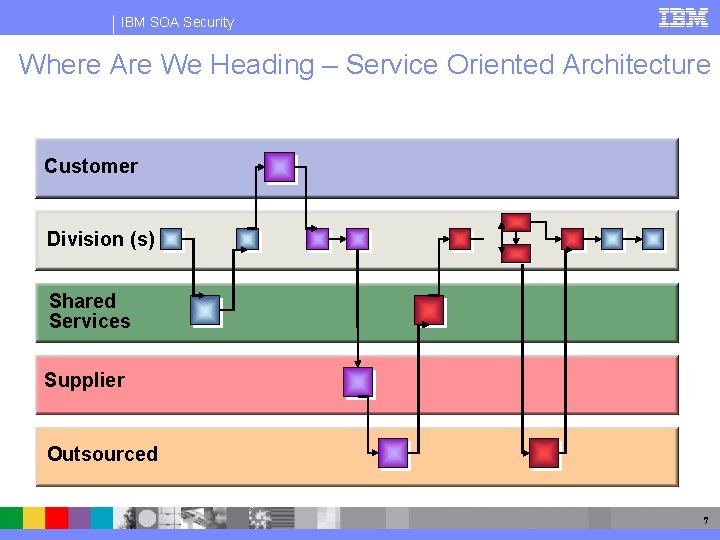
IBM SOA Security Where Are We Heading – Service Oriented Architecture Customer Division (s) Shared Services Supplier Outsourced 7

IBM SOA Security Service Oriented Architecture Benefits A Service Oriented Architecture enables flexible connectivity of applications or resources by Representing every application or resource as a service with a standardized interface Enabling them to exchange structured information (messages, documents, ‘business objects’) Mediating the message exchange through an Enterprise Service Bus This flexibility enables new and existing applications to be easily and quickly combined to address changing business needs. The ability to easily combine/choreograph applications allows IT services to more readily reflect business processes The SOA infrastructure is also used to facilitate the management of business performance and quality of service 8

® IBM SOA Security Template Documentation © IBM Corporation
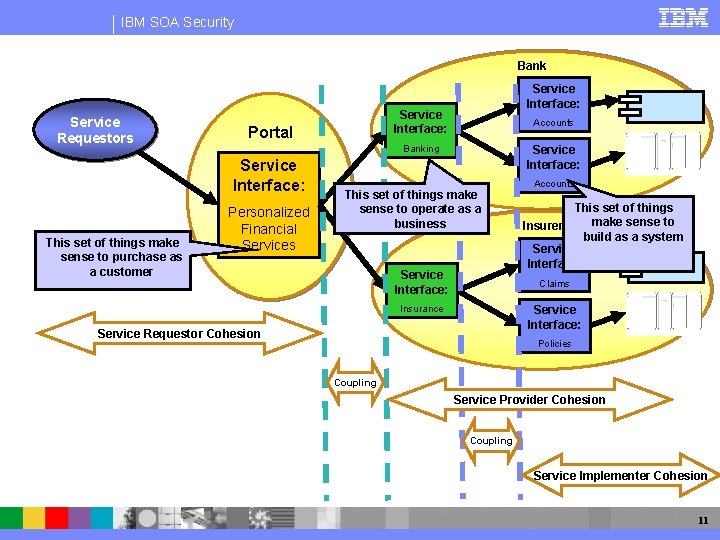
IBM SOA Security Bank Service Requestors Service Interface: Portal Accounts Banking Service Interface: This set of things make sense to purchase as a customer Service Interface: Personalized Financial Services Service Interface: This set of things make sense to operate as a business Service Interface: Accounts This set of things make sense to Insurer build as a system Service Interface: Claims Insurance Service Interface: Service Requestor Cohesion Policies Coupling Service Provider Cohesion Coupling Service Implementer Cohesion 11

IBM SOA Security Considerations for SOA Entities/Identities – users, services Services have identities Identities and/or credentials are propagated across services Users and services are now subject to the same security controls Organizational/enterprise boundaries Perimeter is obscure Identities are managed across boundaries Trust relationships are established across boundaries Composite applications Ensuring proper security controls are enacted for each service and when used in combination Greater focus on data/information Protecting data at transit and at rest Apply consistent protection measures Access to data by applications and services Governance, Risk, and Compliance Auditing ie. entity identification to specific transactions 12
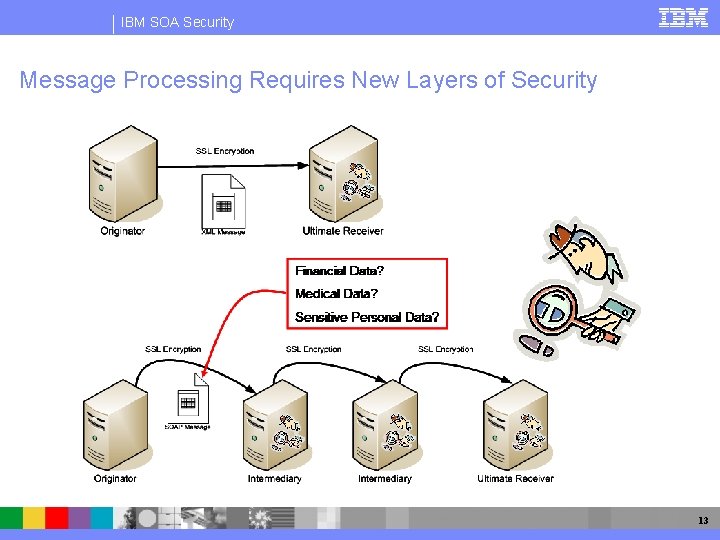
IBM SOA Security Message Processing Requires New Layers of Security 13

® IBM SOA Security Reference Model Template Documentation © IBM Corporation
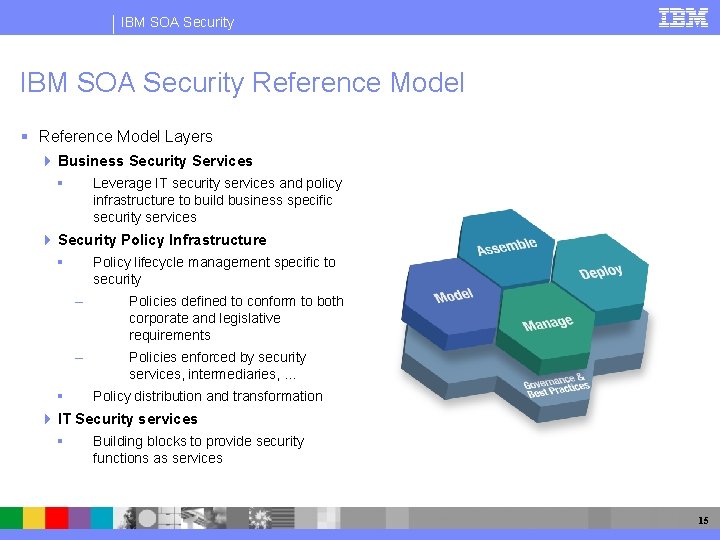
IBM SOA Security Reference Model Layers Business Security Services Leverage IT security services and policy infrastructure to build business specific security services Security Policy Infrastructure Policy lifecycle management specific to security – Policies defined to conform to both corporate and legislative requirements – Policies enforced by security services, intermediaries, … Policy distribution and transformation IT Security services Building blocks to provide security functions as services 15
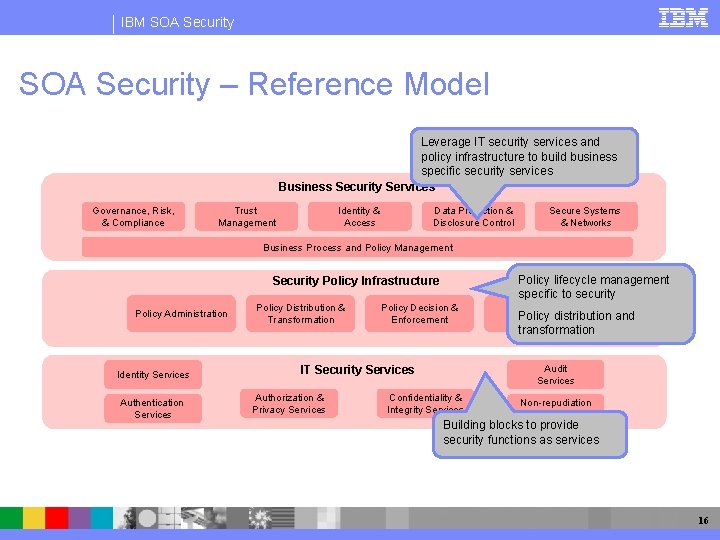
IBM SOA Security – Reference Model Leverage IT security services and policy infrastructure to build business specific security services Business Security Services Governance, Risk, & Compliance Trust Management Identity & Access Data Protection & Disclosure Control Secure Systems & Networks Business Process and Policy Management Policy lifecycle management specific to security Security Policy Infrastructure Policy Administration Identity Services Authentication Services Policy Distribution & Transformation Policy Decision & Enforcement IT Security Services Authorization & Privacy Services Monitoring & Policy distribution Reporting and transformation Audit Services Confidentiality & Integrity Services Non-repudiation Services Building blocks to provide security functions as services 16
IBM SOA Security Business Security Services Governance, Risk, and Compliance Governance – organizational roles and responsibilities defined Process and authority Risk - Management process to decide security cost / value proposition Compliance - Assessment and reporting Trust Management Trusted relationships and domains – system-to-system, business-to-business, etc Identity and Access Management Lifecycle of identity and access control Data Protection & Disclosure Control Content and data protection in transit and at rest Message protection Privacy policy Secure Systems and Networks Operational security management Business Process and Policy Management Coordination and integration of business processes 17
IBM SOA Security Policy Infrastructure Policy Administration Policy lifecycle management Creation, maintenance, change, and deletion Associate policy to resources Policy Distribution and Transformation Virtualization, transformation, and distribution of policy to the decision and enforcement endpoints Policy Decision and Enforcement Determination if pending action conforms to policies Monitoring and Reporting Audit trail of activity 18
IBM SOA Security Services Identity Services Unique identification of entities Assurance of accountability Authentication Services Validation of identity for access control purposes Authorization & Privacy Services Allow or deny access to resources based on a set of policies Protection, use, and disclosure of sensitive information Confidentiality & Integrity Services Protection of sensitive information from disclosure Detection of the unauthorized modification of data Audit Services Collection of event data Non-repudiation Services Protection of requestor and provider from false denials that data has been sent or received 19

® IBM SOA Security Management Template Documentation © IBM Corporation

IBM SOA Security SOA Management - scope Strategy Business Strategy Implementati on Design Processes Services Applications Management Infrastructure Governance and Management SOA Management 21
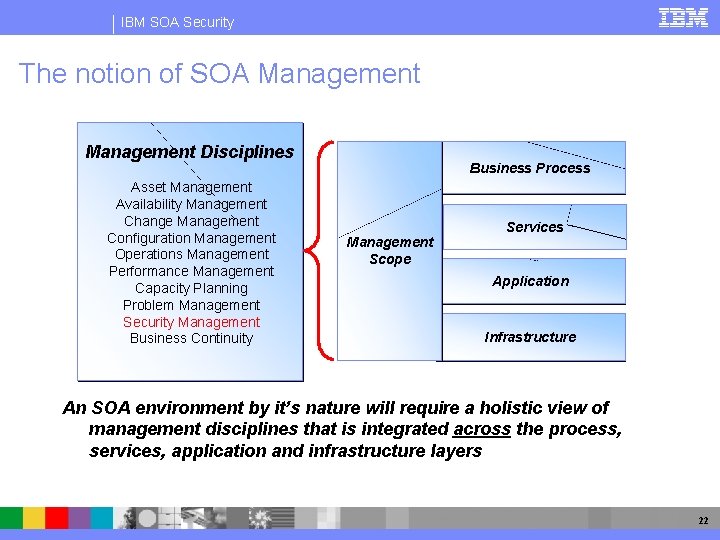
IBM SOA Security The notion of SOA Management Disciplines Asset Management Availability Management Change Management Configuration Management Operations Management Performance Management Capacity Planning Problem Management Security Management Business Continuity Business Process Management Scope Services Application Infrastructure An SOA environment by it’s nature will require a holistic view of management disciplines that is integrated across the process, services, application and infrastructure layers 22

IBM SOA Security SOA Management – Lifecycle context Strategy Design Implementati on Management Governance (Definition of Policy) Business Strategy Goals Analysis & Function Componentization Enterprise Architecture Application Portfolio Analysis Service Analysis & Design SOA Management (Operation) Application Modernization Meta-Data Repository & Registry SOA Management combines life-cycle management of services and their supporting components with the operation aspects of web services management Process Interactions Meta-Data flow 23
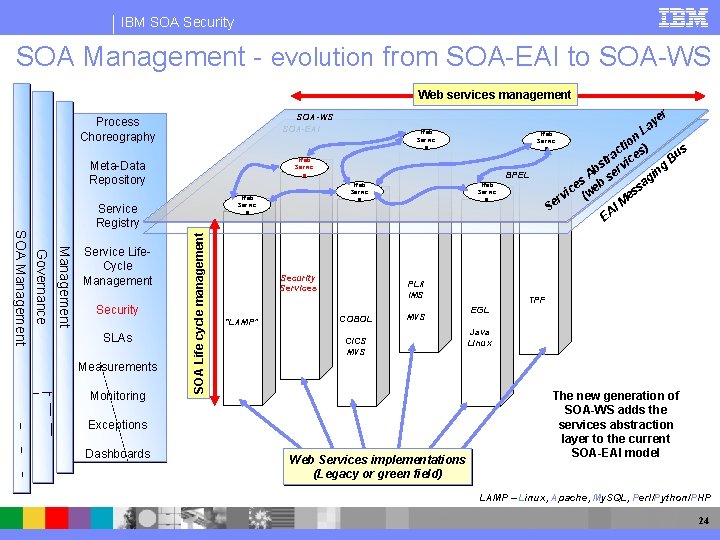
IBM SOA Security SOA Management - evolution from SOA-EAI to SOA-WS Web services management Measurements Monitoring SOA Life cycle management Management Governance SOA Management SLAs Security Services “LAMP” Web Servic e PL/I IMS COBOL MVS CICS MVS Exceptions Dashboards Web Servic e BPEL Web Servic e Service Registry Security Web Servic e Meta-Data Repository Service Life. Cycle Management er SOA-WS SOA-EAI Process Choreography Web Services implementations (Legacy or green field) y La n tio s) c us ra ice B t s v g in Ab ser g s sa ce web s i e rv ( M I Se EA TPF EGL Java Linux The new generation of SOA-WS adds the services abstraction layer to the current SOA-EAI model LAMP – Linux, Apache, My. SQL, Perl/Python/PHP 24
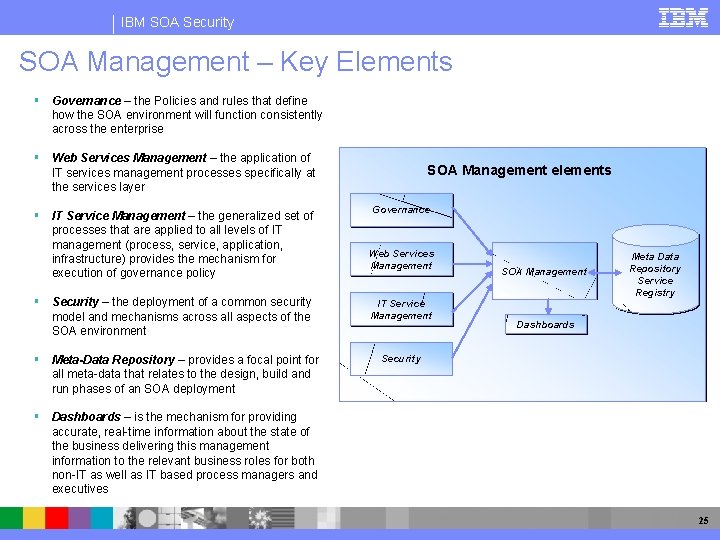
IBM SOA Security SOA Management – Key Elements Governance – the Policies and rules that define how the SOA environment will function consistently across the enterprise Web Services Management – the application of IT services management processes specifically at the services layer IT Service Management – the generalized set of processes that are applied to all levels of IT management (process, service, application, infrastructure) provides the mechanism for execution of governance policy Security – the deployment of a common security model and mechanisms across all aspects of the SOA environment Meta-Data Repository – provides a focal point for all meta-data that relates to the design, build and run phases of an SOA deployment SOA Management elements Governance Web Services Management IT Service Management SOA Management Meta Data Repository Service Registry Dashboards Security Dashboards – is the mechanism for providing accurate, real-time information about the state of the business delivering this management information to the relevant business roles for both non-IT as well as IT based process managers and executives 25

® IBM SOA Security Scenarios Template Documentation © IBM Corporation
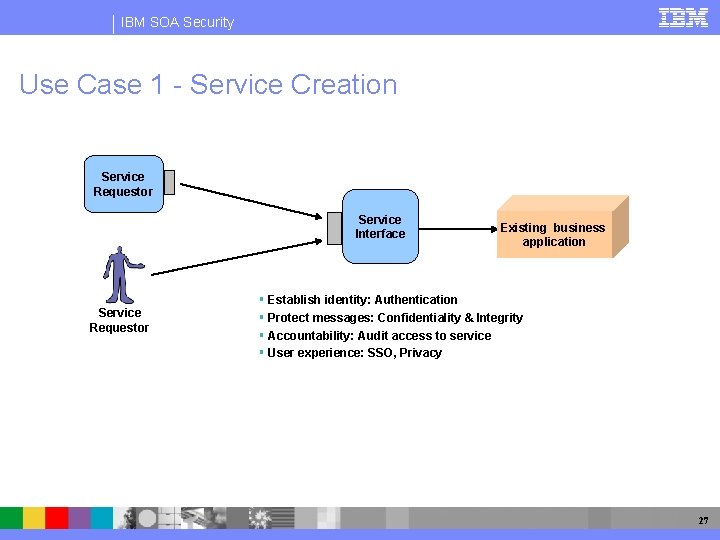
IBM SOA Security Use Case 1 - Service Creation Service Requestor Service Interface Service Requestor Existing business application Establish identity: Authentication Protect messages: Confidentiality & Integrity Accountability: Audit access to service User experience: SSO, Privacy 27
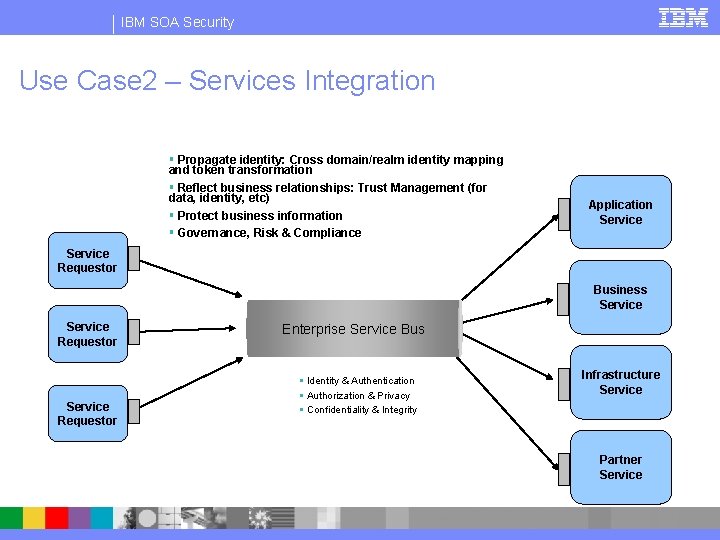
IBM SOA Security Use Case 2 – Services Integration Propagate identity: Cross domain/realm identity mapping and token transformation Reflect business relationships: Trust Management (for data, identity, etc) Protect business information Governance, Risk & Compliance Application Service Requestor Business Service Requestor Enterprise Service Bus Identity & Authentication Authorization & Privacy Confidentiality & Integrity Infrastructure Service Partner Service
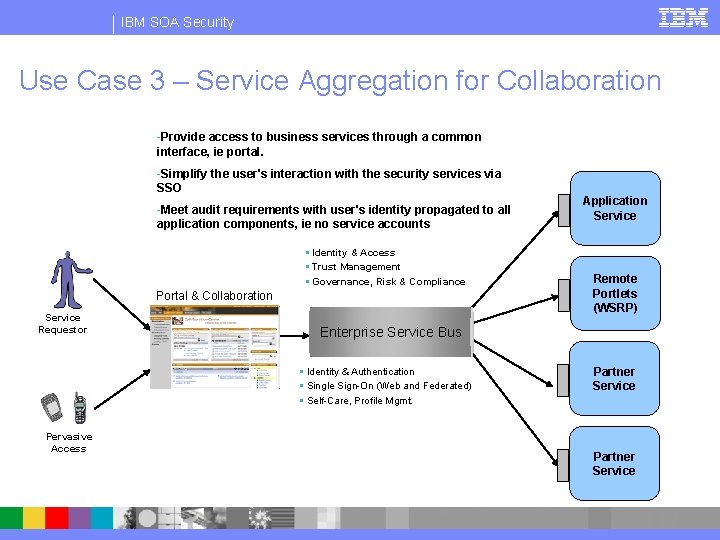
IBM SOA Security Use Case 3 – Service Aggregation for Collaboration -Provide access to business services through a common interface, ie portal. -Simplify the user's interaction with the security services via SSO -Meet audit requirements with user's identity propagated to all application components, ie no service accounts Identity & Access Trust Management Governance, Risk & Compliance Portal & Collaboration Service Requestor Remote Portlets (WSRP) Enterprise Service Bus Identity & Authentication Single Sign-On (Web and Federated) Self-Care, Profile Mgmt. Pervasive Access Application Service Partner Service

IBM SOA Security in a Typical Deployment Architecture Transport Security Message Security Transport. Security Web Application Server/Portal Server ESB Proxy Firewall Client System (browser, rich client) Firewall Enterprise Information System Existing Application Federate Identities with partners Auditing Confidentiality & Integrity Propagate identity Fine level authorization Audit Data Server/ Services Existing Applications/ Services Propagate identity Application level authorization 30

IBM SOA Security Standards for IT Security Services Service Identity Services Authentication Services Authorization and Privacy Services Audit Services Relevant Standards Id. AS, SPML, SAML, WS-Federation WS-Trust, Kerberos, SAML, PKI XACML, JACC, WSAuthorization, IDMix CBE extensions, Audit web service (in
IBM SOA Security References Redbook on SOA Security in the works (Expected formal draft – 10/1) Service Oriented Architecture Security Whitepaper Nataraj Nagaratnam, Anthony Nadalin, Sridhar Muppidi(draft available) Business Driven Application Security Nataraj Nagaratnam, Anthony Nadalin, Maryann Hondo, et alwww. research. ibm. com/journal/sj/444/nagaratnam. html Securing Service Oriented Applications Anthony Nadalin, Nataraj Nagaratnam, Maryann Hondo Service-oriented architecture: Programming model and product architecture. D. F. Ferguson et al. IBM Systems Journal, VOL 44, NO 4, 2005. http: //researchweb. watson. ibm. com/journal/sj/444/ferguson. pdf IBM’s SOA Foundation: An Architectural Introduction and Overview. Version 1. 0, November, 2005. Rob High, Jr. et al. http: //download. boulder. ibm. com/ibmdl/pub/software/dw/webservices/ws-soa-whitepaper. pdf Patterns: SOA Foundation: Service Creation Scenario. John Ganci et al. Draft Redbook. http: //www. redbooks. ibm. com/redpieces/pdfs/sg 247240. pdf Patterns: SOA Foundation Service Connectivity Scenario. Carla Sadtler et al. Redbook http: //www. redbooks. ibm. com/redbooks/pdfs/sg 247228. pdf Patterns: SOA Foundation -Business Process Management Scenario. Martin Keen et al. Redbook. http: //www. redbooks. ibm. com/redbooks/pdfs/sg 247234. pdf Patterns: SOA with an Enterprise Service Bus. Martin Keen et al. Redbook. http: //www. redbooks. ibm. com/redbooks/pdfs/sg 246494. pdhttp: //www-128. ibm. com/developerworks/library/ws-model 7 Other WS-* specifications 32
IBM SOA Security Summary Comment: needs updating Security is about business, no longer just about technology SOA enables better Application Integration Web Services Security standards optimizes the development, deployment and management of Composite Applications Identity Management is a critical component of SOA Federation is the “bridge” by which ID Management integrates with Service Oriented Architectures 33
- Slides: 32