IBM Service Management The Foundation for Effective Governance

IBM Service Management: The Foundation for Effective Governance, Risk Management and Compliance Efforts Don O’Toole Director, Tivoli Strategy March 21, 2007 © 2006 IBM Corporation

IBM Service Management: A Closed Loop Approach IBM Service Management Connecting the asset to the service Process management Service management platform Operational management Best practices and services Managing end to end services 2 Aligning the service with the business © 2006 IBM Corporation
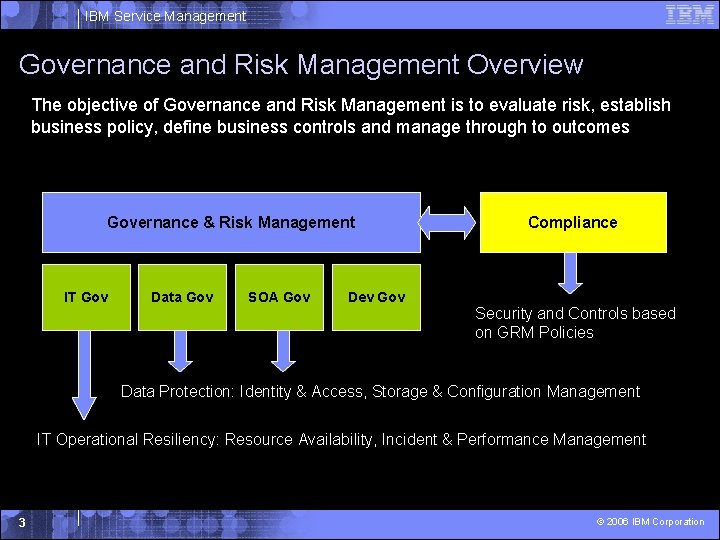
IBM Service Management Governance and Risk Management Overview The objective of Governance and Risk Management is to evaluate risk, establish business policy, define business controls and manage through to outcomes Governance & Risk Management IT Gov Data Gov SOA Gov Dev Gov Compliance Security and Controls based on GRM Policies Data Protection: Identity & Access, Storage & Configuration Management IT Operational Resiliency: Resource Availability, Incident & Performance Management 3 © 2006 IBM Corporation
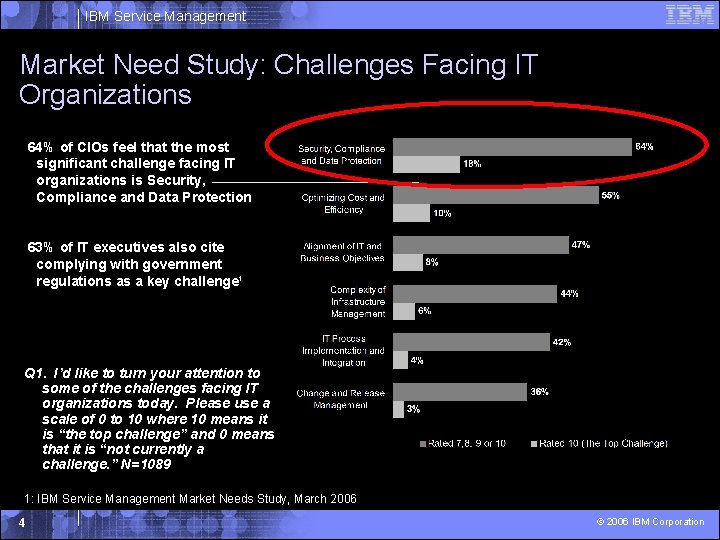
IBM Service Management Market Need Study: Challenges Facing IT Organizations 64% of CIOs feel that the most significant challenge facing IT organizations is Security, Compliance and Data Protection 63% of IT executives also cite complying with government regulations as a key challenge¹ Q 1. I’d like to turn your attention to some of the challenges facing IT organizations today. Please use a scale of 0 to 10 where 10 means it is “the top challenge” and 0 means that it is “not currently a challenge. ” N=1089 1: IBM Service Management Market Needs Study, March 2006 4 © 2006 IBM Corporation

IBM Service Management Compliance Management Challenges § Increasing Requirements – Hundreds of compliance regulations and initiatives – Improved monitoring and control are needed to avoid risks, penalties, and lost business § Increasing Complexity – Disparate technologies and infrastructures fragment and hamper compliance efforts – Linking infrastructure-level to business-level compliance is desirable, but challenging § 43% of CFOs think that improving governance, controls and risk management is their top challenge. § Increasing Cost – Lack of predictability and visibility across complex infrastructures drives rapid cost inflation – Failure to achieve compliance or to prevent security breaches can impose enormous costs CFO Survey: Current state & future direction, IBM Business Consulting Services 5 © 2006 IBM Corporation
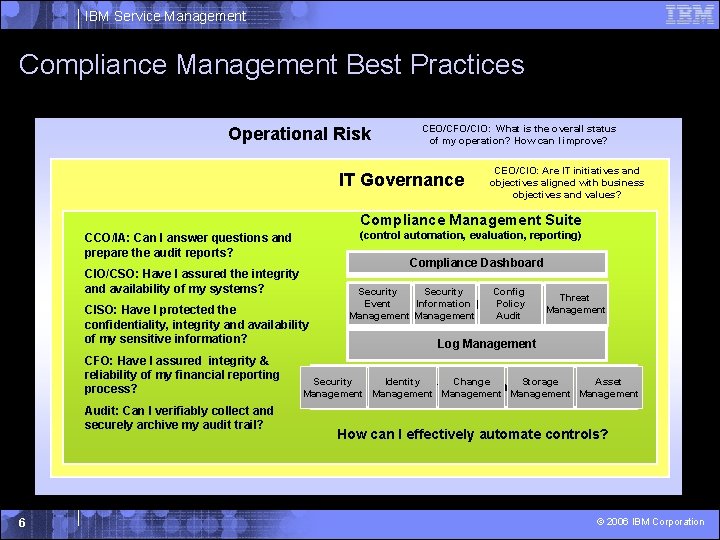
IBM Service Management Compliance Management Best Practices Operational Risk CEO/CFO/CIO: What is the overall status of my operation? How can I improve? IT Governance CEO/CIO: Are IT initiatives and objectives aligned with business objectives and values? Compliance Management Suite (control automation, evaluation, reporting) CCO/IA: Can I answer questions and prepare the audit reports? Compliance Dashboard Reporting CIO/CSO: Have I assured the integrity and availability of my systems? CISO: Have I protected the confidentiality, integrity and availability of my sensitive information? CFO: Have I assured integrity & reliability of my financial reporting process? Audit: Can I verifiably collect and securely archive my audit trail? 6 Security Event Information Audit Trail Management Config Policy Analysis Audit Threat Management Log Management Audit Trail Collection Security Identity Change Storage Asset Control Automation Management Management How can I effectively automate controls? © 2006 IBM Corporation

IBM Service Management: Compliance and Security Offerings IBM Service Management IT Process Management Compliance, Information & Governance Processes Service Management Platform Service Visibility, Control and Automation IT Operational Management Security and Compliance Products Best Practices and Services Compliance Management Auditing, Reporting, Forensics, Compliance Dashboard 7 Operational Security Mgmt Identity, Access & Storage § Integrated Threat Monitoring § Security Configuration Manager § Secure Infrastructure: Network, Storage § § § § User Provisioning User Activity Monitoring Authentication & Authorization Directory Infrastructure Mainframe Security Audit Federated Identity Mgmt Data Back Up and Storage © 2006 IBM Corporation

IBM Service Management IBM Tivoli Compliance and Security Product Portfolio Where do you begin to improve your business risk equation? Compliance Management Tivoli Compliance Manager (Consul) Operational Security Mgmt Identity, Access & Storage § Security Operations Manager § Security Compliance Manager § Internet Security Systems § Storage Manager § Identity Manager § Access Manager § Directory Server § Directory Integrator § Federated Identity Manage § Continuous Data Protection • IT Operational Resiliency - IBM Tivoli’s operational security portfolio enabling: • Real-time threat recognition to support IT and business controls • System Security and policy enforcement to reduce vulnerabilities • Incident management integrated into NOC Management solutions improves time to resolution 8 © 2006 IBM Corporation

IBM Service Management Operational Integration between NOC and SOC Converged Operations SOC and NOC platforms should share workflow information and ticketing: Network Operations Security Operations Level 2 • Facilitates incident management • Maximizes network and service uptime Level 1 Level 2 Shared Workflow Shared Ticketing Level 3 Incident Analysis Image Courtesy of Nemertes Research 2005 9 © 2006 IBM Corporation
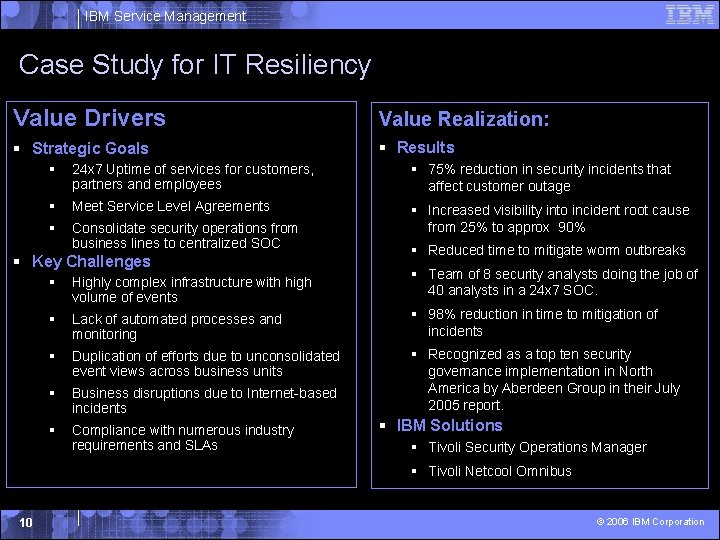
IBM Service Management Case Study for IT Resiliency Value Drivers Value Realization: § Strategic Goals § Results § 24 x 7 Uptime of services for customers, partners and employees § 75% reduction in security incidents that affect customer outage § Meet Service Level Agreements § Consolidate security operations from business lines to centralized SOC § Increased visibility into incident root cause from 25% to approx 90% § Key Challenges § Reduced time to mitigate worm outbreaks § Highly complex infrastructure with high volume of events § Team of 8 security analysts doing the job of 40 analysts in a 24 x 7 SOC. § Lack of automated processes and monitoring § 98% reduction in time to mitigation of incidents § Duplication of efforts due to unconsolidated event views across business units § Business disruptions due to Internet-based incidents § Recognized as a top ten security governance implementation in North America by Aberdeen Group in their July 2005 report. § Compliance with numerous industry requirements and SLAs § IBM Solutions § Tivoli Security Operations Manager § Tivoli Netcool Omnibus 10 © 2006 IBM Corporation

IBM Service Management IBM Tivoli Compliance and Security Product Portfolio Compliance Management Where do you begin to improve your business risk equation? Tivoli Compliance Manager (Consul) Operational Security Mgmt Identity, Access & Storage § Security Operations Manager § Security Compliance Manager § Internet Security Systems § Storage Manager § Identity Manager § Access Manager § Directory Server § Directory Integrator § Federated Identity Manager § Continuous Data Protection • IT Operational Resiliency - IBM Tivoli’s operational security portfolio enabling: • Real-time threat recognition to support IT and business controls • System Security and policy enforcement to reduce vulnerabilities • Incident management integrated into NOC Management solutions improves time to resolution • Privacy and Data Protection - IBM Tivoli’s Identity, Access & Storage Portfolio: • Provisioning and de-provisioning and self-service • Controlled access to applications and assets • Back up and storage of critical data 11 © 2006 IBM Corporation

IBM Service Management Privacy and Data Protection in Context 86% of internal security incidents are perpetrated by a company’s most privileged and technical users such as administrators, outsourcers, consultants, or other power users. * Detect when an authorized but unfamiliar identity accesses a system containing future design concepts Be alerted when an unauthorized user attempts to access pricing data server Identify when an authorized user accesses an abnormal number of customer records Validate that medical records have been kept private Observe that the database administrator has accessed the payroll records * U. S Secret Service and CERT Coordination Center/SEI -- Insider Threat Study: Computer System Sabotage in Critical Infrastructure Sectors May 2005 12 © 2006 IBM Corporation

IBM Service Management IBM Tivoli Compliance and Security Product Portfolio Compliance Management Tivoli Compliance Manager (Consul) Where do you begin to improve your business risk equation? Operational Security Mgmt Identity, Access & Storage § Security Operations Manager § Security Compliance Manager § Internet Security Systems § Storage Manager § Identity Manager § Access Manager § Directory Server § Directory Integrator § Federated Identity Manager § Continuous Data Protection • IT Operational Resiliency - IBM Tivoli’s operational security portfolio enabling: • Real-time threat recognition to support IT and business controls • System Security and policy enforcement to reduce vulnerabilities • Incident management integrated into NOC Management solutions improves time to resolution • Privacy and Data Protection - IBM Tivoli’s identity, access & management portfolio: • Provisioning and de-provisioning and self-service • Controlled access to applications and privacy of data • Back up and storage of critical data • Audit and Reporting • Dashboard to determine compliance posture • Reporting engine for deliverables to management, audit and regulatory bodies 13 © 2006 IBM Corporation

IBM Service Management Full Audit and Compliance Reporting Monitor, Audit & Report Manage Logs Analysis Engine Report Center Collect & Store Normalize • Who Monitoring & Auditing Privileged Users Instigate & Retrieve • What Custom Log Continuity Reporting • On What Policy Best Practices • When • Where from • Where to Real-Time Correlation Compliance • • ISO 17799 Basel II SAS 70 HIPAA GLBA Capabilities: § Hundreds of reports § Compliance modules § Real-time alerts § Custom reports SOX PCI Alerts 14 © 2006 IBM Corporation

IBM Service Management Case Study – Compliance – Food Retailer Value Drivers Value Realization: § Strategic Goals § Results § Monitor user activity of 350, 000 employees more efficiently and effectively § Move resources from compliance management to revenue-building projects § Key Challenges § Cost of audit and compliance initiatives § Duplication of efforts in developing reports for audits § Managing 40, 000 monthly changes in access rights § Managing and monitoring usage in a distributed environment 15 § Automated access monitoring across mainframe and distributed environment § Reporting modules for audit inquiries fully integrated into IT department § Re-distribution of 15% of IT resources from compliance to revenue related projects § IBM Solutions § Tivoli Compliance Manager (Consul) © 2006 IBM Corporation

IBM Service Management Benefits of Leveraging IBM Service Management for Governance, Risk Management and Compliance Management § Improve efficiency and reduce costs – Automate previously manual processes § Enhance compliance readiness – Consistent and comprehensive approach enables more accurate and timely reporting – Allows for easy reuse for other regulations § Improve effectiveness – Consistent and comprehensive policy management and enforcement § Reduce risk – Better managed control of who, what, when – Better visibility into potential exposures Look at Compliance Management as an enabler that will drive the ultimate value out of your IT Investments. 16 © 2006 IBM Corporation

IBM Service Management 17 © 2006 IBM Corporation
IBM Service Management Disclaimers and Trademarks No part of this document may be reproduced or transmitted in any form without written permission from IBM Corporation. Product data has been reviewed for accuracy as of the date of initial publication. Product data is subject to change without notice. Any statements regarding IBM's future direction and intent are subject to change or withdrawal without notice, and represent goals and objectives only. THE INFORMATION PROVIDED IN THIS DOCUMENT IS DISTRIBUTED "AS IS" WITHOUT ANY WARRANTY, EITHER EXPRESS OR IMPLIED. IBM EXPRESSLY DISCLAIMS ANY WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT. IBM products are warranted according to the terms and conditions of the agreements (e. g. IBM Customer Agreement, Statement of Limited Warranty, International Program License Agreement, etc. ) under which they are provided. IBM customers are responsible for ensuring their own compliance with legal requirements. It is the customer's sole responsibility to obtain advice of competent legal counsel as to the identification and interpretation of any relevant laws and regulatory requirements that may affect the customer's business and any actions the customer may need to take to comply with such laws. The following terms are trademarks or registered trademarks of the IBM Corporation in either the United States, other countries or both: DB 2, e-business logo, e. Server, IBM logo, Lotus, Tivoli, Web. Sphere, Rational, z/OS, z. Series, System z. Java and all Java-based trademarks are trademarks of Sun Microsystems, Inc. in the United States and/or other countries. Microsoft, Windows NT, and the Windows logo are trademarks of Microsoft Corporation in the United States and/or other countries. UNIX is a registered trademark of The Open Group in the United States and other countries. Linux is a trademark of Linus Torvalds in the United States and other countries. Other company, product, or service names may be trademarks or service marks of others. ITIL® is a Registered Trade Mark, and a Registered Community Trade Mark of the Office of Government Commerce, and is Registered in the U. S. Patent and Trademark Office. IT Infrastructure Library® is a Registered Trademark of the Central Computer and Telecommunications Agency which is now part of the Office of Government Commerce. 18 © 2006 IBM Corporation
- Slides: 18