i Twins By Sushant Burde Vaibhav Deshmukh What

i. Twins By Sushant Burde Vaibhav Deshmukh
What is itwins i. Twin is like the two ends of a cable, without the cable. i. Twin is a revolutionary new file sharing and remote access device brought to you by a company called i. Twin. It's like two ends of a cable, without the cable. It's as simple to use as a flash drive. It's literally plug and play. i. Twin can connect any two online computers anywhere in the world. i. Twin enables you to have access to any or all of your home computer's files and folders while you're on-the-go you can also use i. Twin to access to any or all of your office computer's files and folders There's no in-built limit to the amount of storage you can access with i. Twin

Need of i. Twins Transferring data from one PC to another can be difficult, especially if it's a large amount of data. For example, if you want to send some data to somebody in another country, you’re going to have to go through the hassle of either sending it via e-mail, or upload it to some file hosting service. Chances are, if your file is too large, you’ll probably need to buy more storage. Enter i. Twin. This new USB dongle/USB drive allows users to remotely access data from anywhere in the world. It’s a one time investment

Requirements Windows and Mac OS X compatible You can use i. Twin on any of both Windows and Mac OSX platforms. Minimum 512 MB 1 GB ram needed 15 MB space on hard disk USB 2. 0 port Broadband connection uploading speed should be 1 Mbps
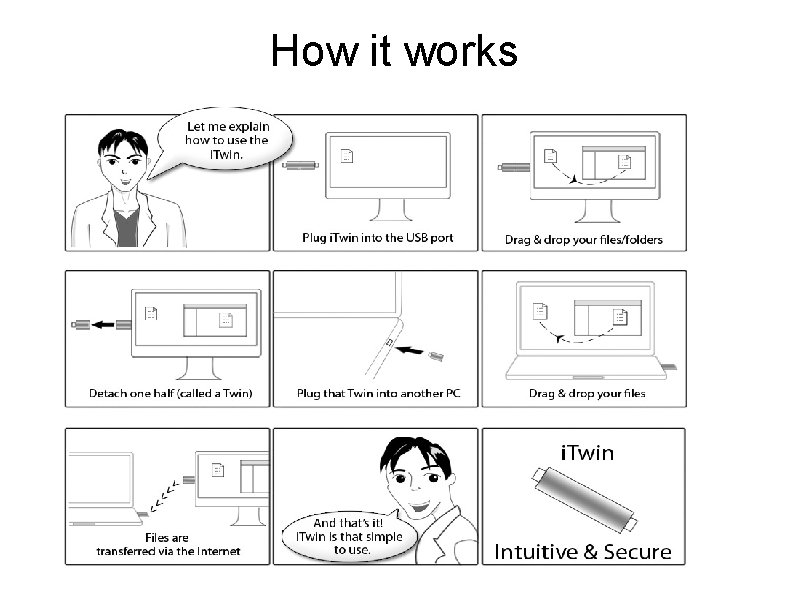
How it works

Hardware Length : 3. 54 inches (90 mm). Width : 0. 82 inch (21 mm). Depth : 0. 314 inch (8. 0 mm). Weight : 0. 11 pound (50 g). Operating Requirements Operating temperature: 32° to 158° F (0° to 70° C). Relative humidity: 5% to 95% noncondensing. Maximum operating altitude: 10, 000 feet (3000 m). Completely symmetrical, first of its kind in the market. During physical pairing, connector is used to securely transfer crypto key between the 2 halves of i. Twin. LED Indicator LED lights indicate status. Constant Blue light : i. Twin is fully functional. Blinking Blue light : on-going data transfer. Constant red light : error.
Features Multi-language support No storage limitations No “temp” files
Protection from malware i. Twin does not facilitate malware distribution. Malware spreads through regular USB drives, when a malicious program executes and writes itself to the USB drive automatically (without your permission or without you even realizing it). When the infected USB drive is plugged into another computer, the software may be able to automatically run. There are two necessary conditions for malware spread. 1) Infected File should be copied to a new computer. 2) Infected File should executed on the new computer. With i. Twin, you explicitly select the files that needs to be copied. And the i. Twin device does not store any unauthorized files on itself - it only stores i. Twin application files. Malicious files cannot trick i. Twin into copying files automatically. However, if you use i. Twin (or any file transfer system) to knowingly copy suspicious files on to your computer and you execute them (by clicking on them) you might be opening malware.
What is Malware, short for malicious software, consists of programming (code, scripts, active content, and other software) it is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior malware is disguised as genuine software, and may come from an official site. Therefore, some security programs, such as Mc. Afee may call malware "potentially unwanted programs" or "PUP".
Effects of malware Spyware is a piece of software that collects and sends information (such as browsing patterns in the more benign case or credit card numbers in more serious ones) on users. They usually work and spread like Trojan horses. The category of spyware is sometimes taken to include adware of the less-forthcoming sort. Trojan horses are similar to viruses in that they get executed by being part of an otherwise useful piece of software. To spread, Trojan horses rely on the useful features of the host software, which trick users to install them.

Data security i. Twin doesn't store any data on itself. It just enables a secure connection between two computers. Your remote data can only be accessed if you have the physical i. Twin with you. Additionally, you can set up your i. Twin to require a password. i. Twin is a secure USB device providing Two-Factor Authentication (hardware device + password). We also allow you to remotely disable i. Twin with our remote disable feature. So you can rest assured that your data is safe, even if you lose your i. Twin device.

Twin. Trust Authentication Before allowing any data transfer, every i. Twin is authenticated by i. Twin's Twin. Trust servers. All communication between i. Twin and Twin. Trust is secured using industry strength HTTPS (RSA 1024 bit, 128 bit RC 4) protocol. After successful authentication by Twin. Trust, Twin. Trust assist i. Twin to discover its other half.

Two-Factor Authentication After authenticating with Twin. Trust, two halves of i. Twin mutually authenticate each other using their pre-shared AES 256 bit crypto key. If password is set, then password verification is performed on both i. Twins before data transfer is initiated between two i. Twins.
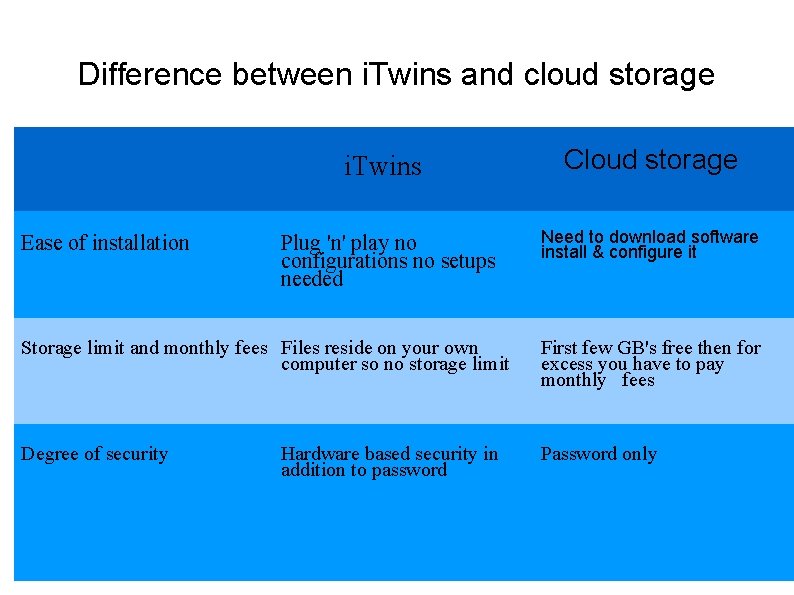
Difference between i. Twins and cloud storage i. Twins Ease of installation Plug 'n' play no configurations no setups needed Cloud storage Need to download software install & configure it Storage limit and monthly fees Files reside on your own computer so no storage limit First few GB's free then for excess you have to pay monthly fees Degree of security Password only Hardware based security in addition to password

i. Twins vs flash drive i. Twins Flash drive capacity Access to computer's entire hard drive & any attached storage. 2 GB to 256 GB (depending on model). Remote disable If you lose one half, you can remotely disable it. Your data remains safe as nothing is stored on the device itself. If you lose the device, you lose and expose your data. Data Encryption AES 256 -bit. Standard USB devices don't support encryption. Need additional software.
- Slides: 15