i 3 Live Security Paul Wisniewski UWMadison August




- Slides: 6

i 3 Live Security Paul Wisniewski UW-Madison August, 2010

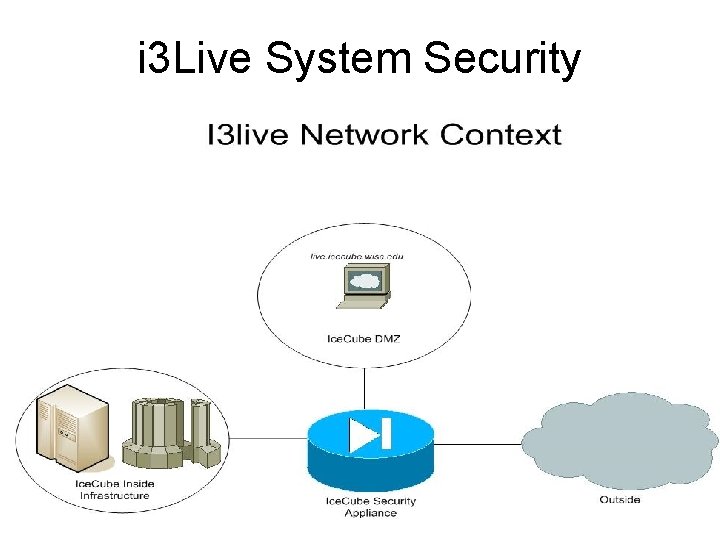
i 3 Live System Security Safe Guards Vulnerability Reduction Operating System - Package Management - FS Permission-ing Application - Package Management - Role Based Access Control - Django Input Sanitizing Network - Firewall-ed DMZ placement - Packet Filtering rules restricts types of access - Connection Logging - Periodic Scanning & Penetration Testing

i 3 Live System Security

i 3 Live Security • SUMMARY – Number of hosts which were alive during the test : 1 – Number of security holes found : 0 – Number of security warnings found : 2 – Number of security notes found : 28 – TESTED HOSTS 128. 104. 255. 59 (Security warnings found) Warning found on port https (443/tcp) Synopsis : Debugging functions are enabled on the remote web server. Description : The remote webserver supports the TRACE and/or TRACK methods. TRACE and TRACK are HTTP methods that are used to debug web server connections. Warning found on port https (443/tcp) Synopsis : The remote web server discloses information due to a configuration weakness. Description : The web server on the remote host allows read access to '. svn/entries' files. This exposes all file names in your svn module on your website. This flaw can also be used to download the source code of the scripts (PHP, JSP, etc. . . ) hosted on the remote server.

I 3 live System Security Breach Detection & Containment Detection Periodic Logging Analysis User and Campus Feed. Back Host Monitoring via Nagios Containment Quarantining via network partitioning Assessment via out-of-band access Quick Recovery using Kickstart methods

I 3 live System Security Discussion Impact of a Breach ? How much detector downtime is tolerable ? How much Ice. Cube Live downtime is tolerable ? Can data taking be unlinked from Ice. Cube Live ?