HYBRIS ARCHITECTURE TECHNOLOGY October 2014 01 OVERVIEW ARCHITECTURE


HYBRIS ARCHITECTURE & TECHNOLOGY October 2014
01 OVERVIEW
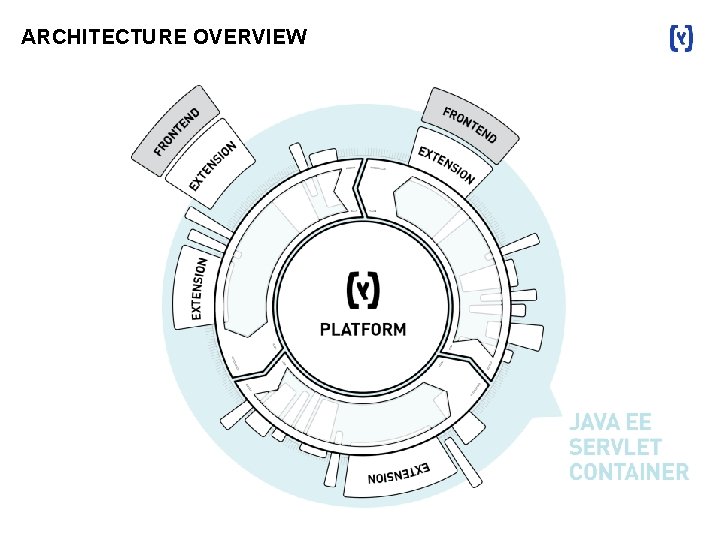
ARCHITECTURE OVERVIEW
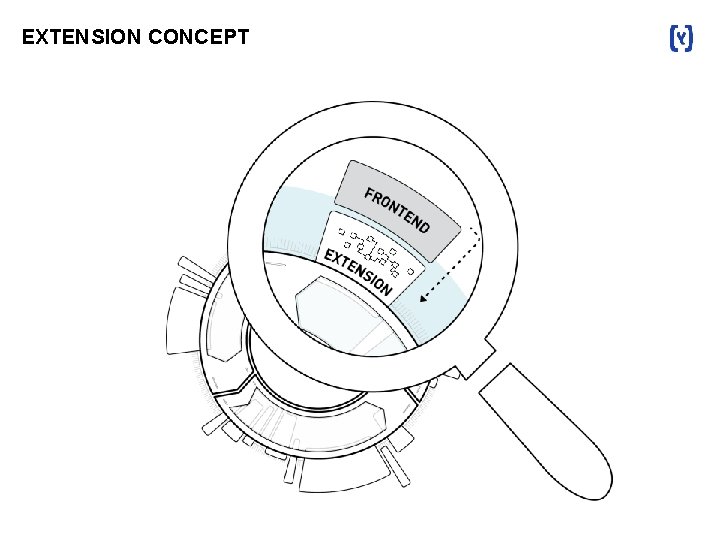
EXTENSION CONCEPT
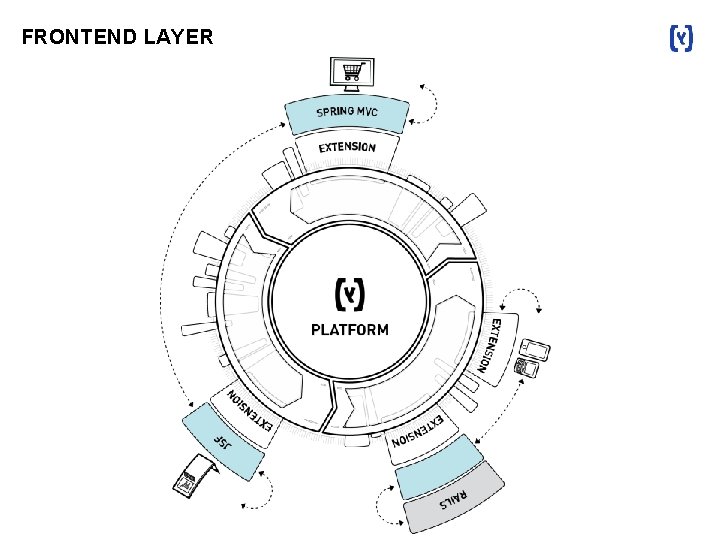
FRONTEND LAYER
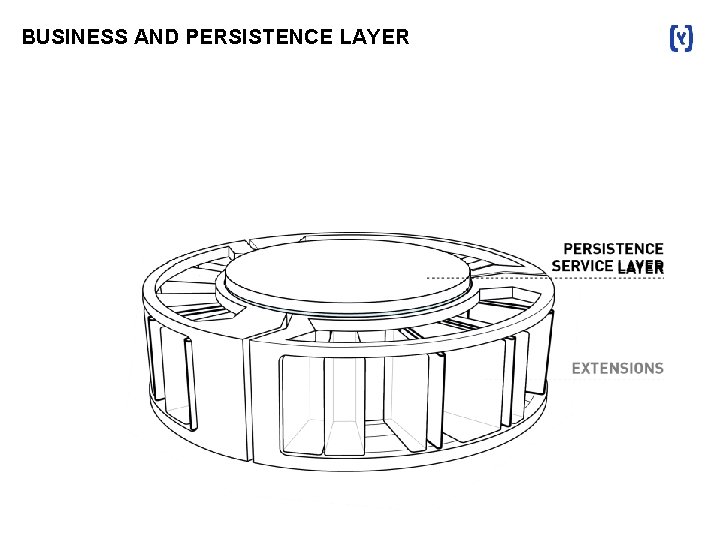
BUSINESS AND PERSISTENCE LAYER
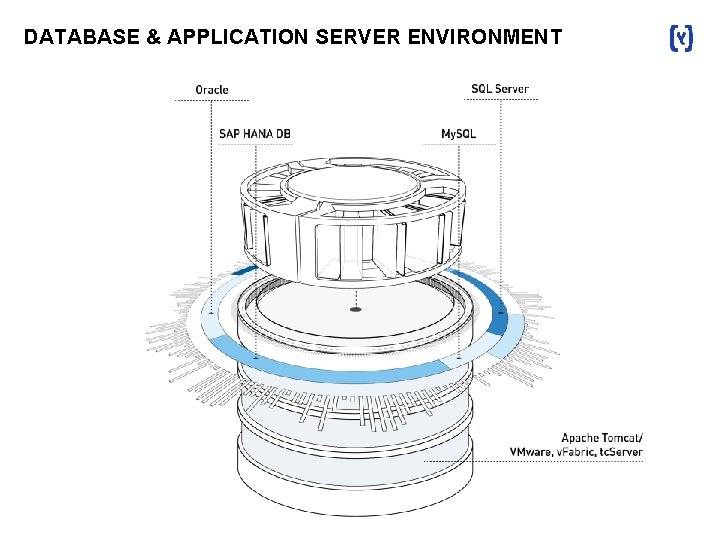
DATABASE & APPLICATION SERVER ENVIRONMENT
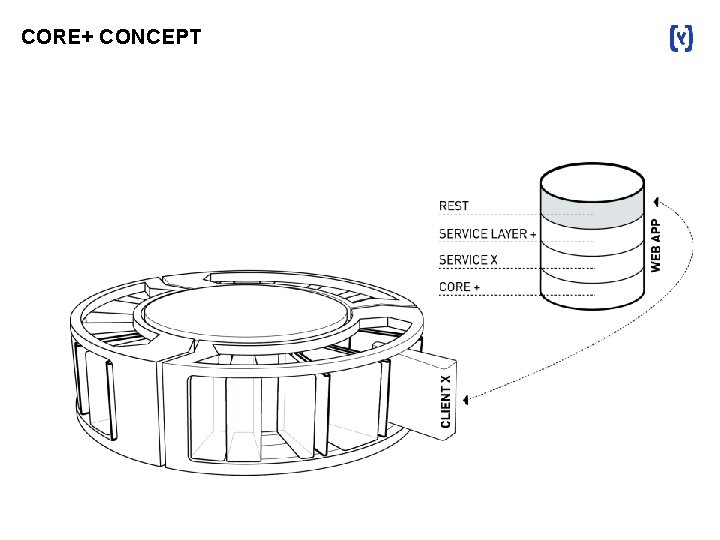
CORE+ CONCEPT
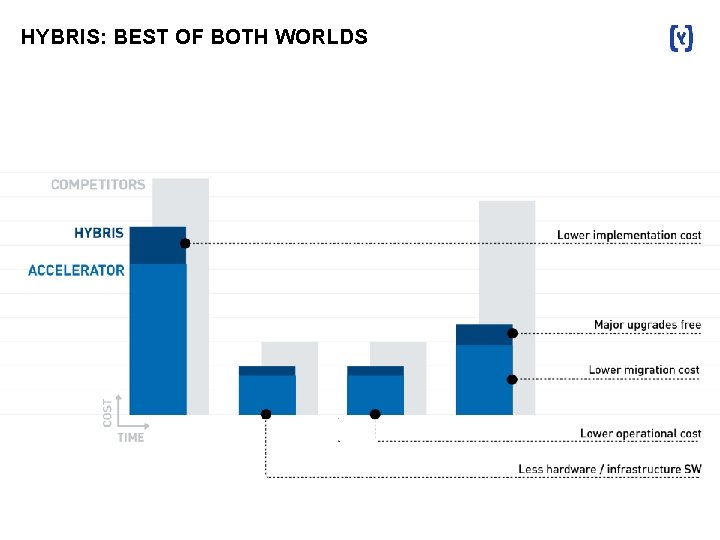
HYBRIS: BEST OF BOTH WORLDS

02 DEVELOPMENT
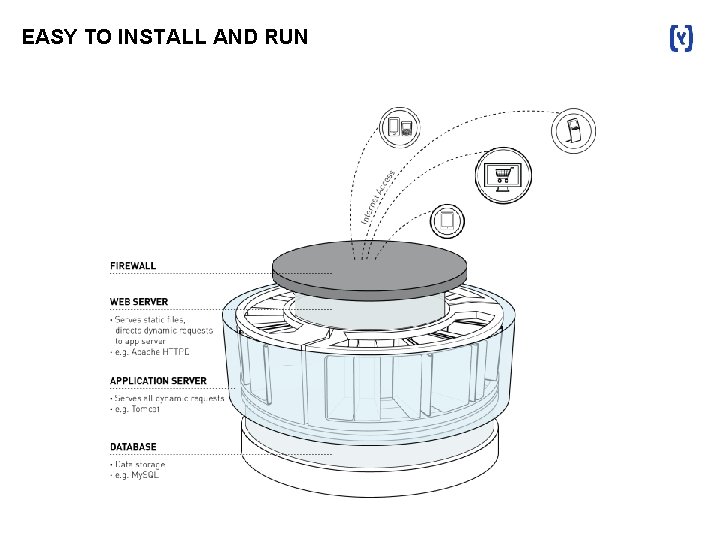
EASY TO INSTALL AND RUN
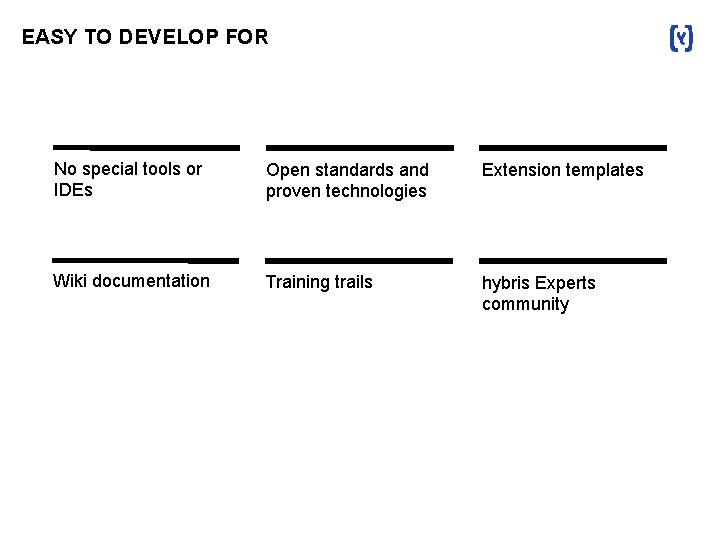
EASY TO DEVELOP FOR No special tools or IDEs Open standards and proven technologies Extension templates Wiki documentation Training trails hybris Experts community
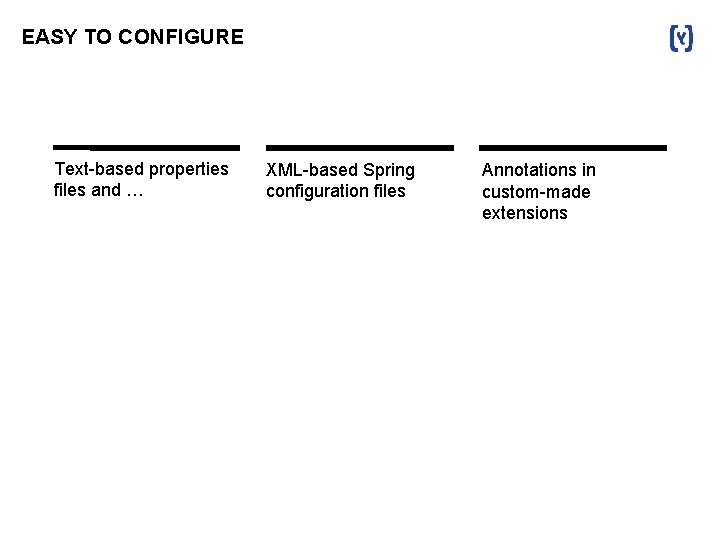
EASY TO CONFIGURE Text-based properties files and … XML-based Spring configuration files Annotations in custom-made extensions
JAVA FRAMEWORKS, LIBRARIES AND STANDARDS
03 CUSTOMIZATION

FLEXIBLE BUSINESS OBJECTS
SERVICES IN THE SERVICELAYER Three steps to exchange the service: 1 Find the service interface. 2 Implement the new service. 3 Replace the alias of the service.
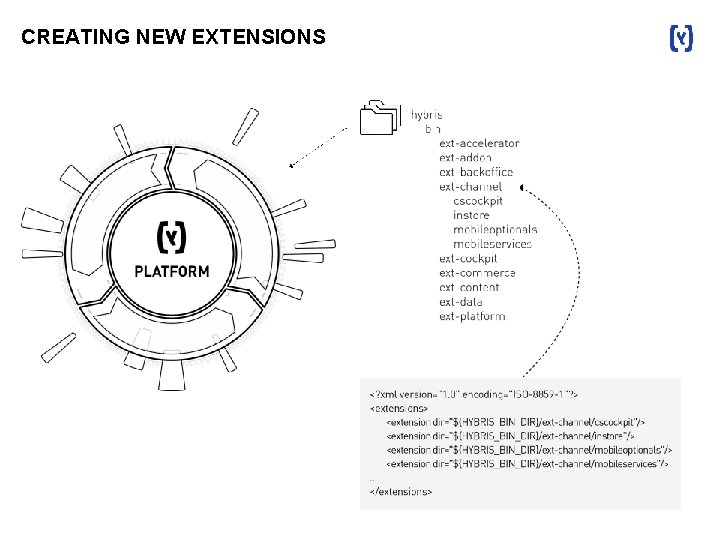
CREATING NEW EXTENSIONS
HYBRIS COMMERCE ACCELERATOR
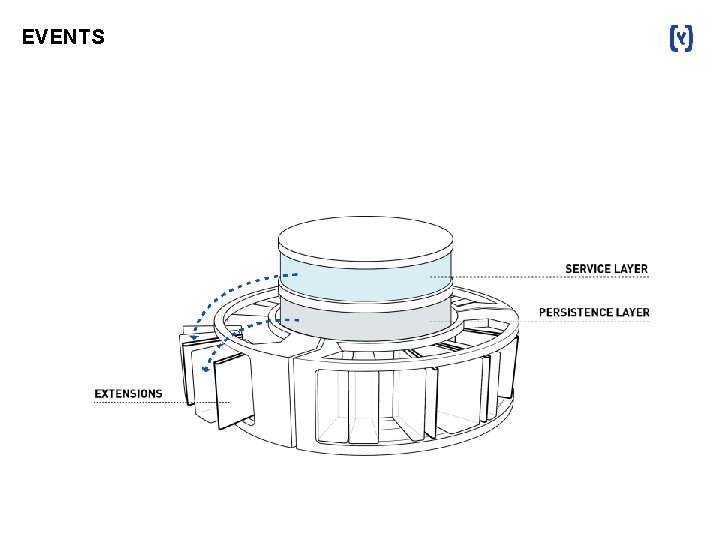
EVENTS
INTERNATIONALIZATION
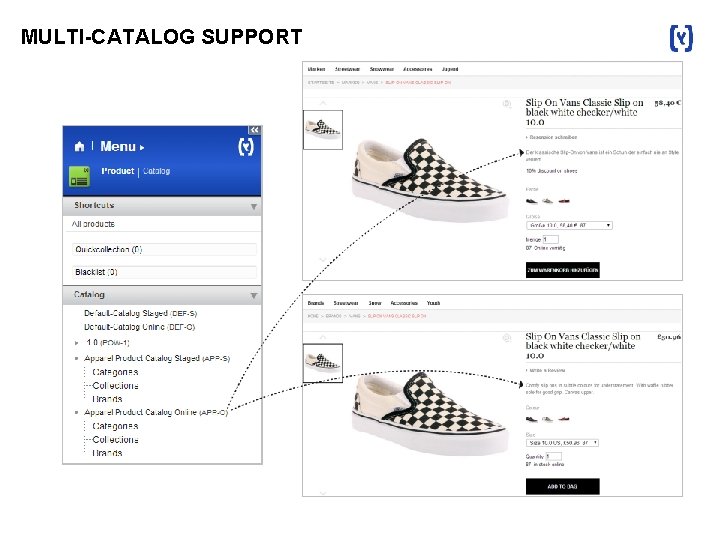
MULTI-CATALOG SUPPORT
COCKPIT CUSTOMIZATION
04 INTEGRATION
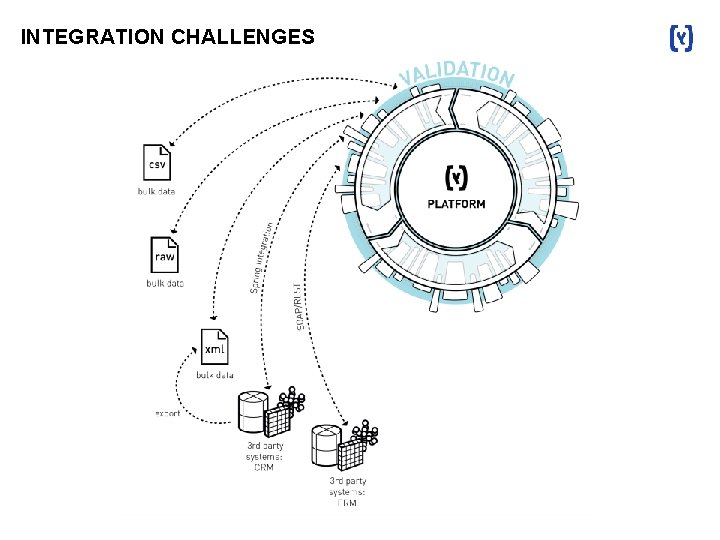
INTEGRATION CHALLENGES
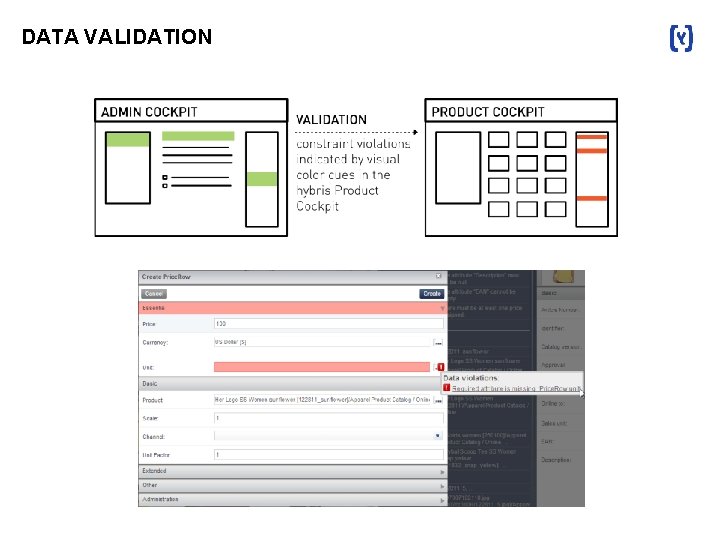
DATA VALIDATION
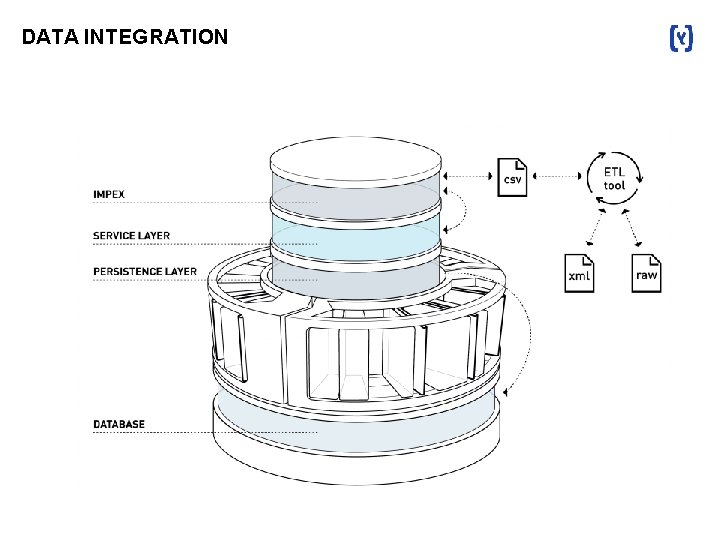
DATA INTEGRATION
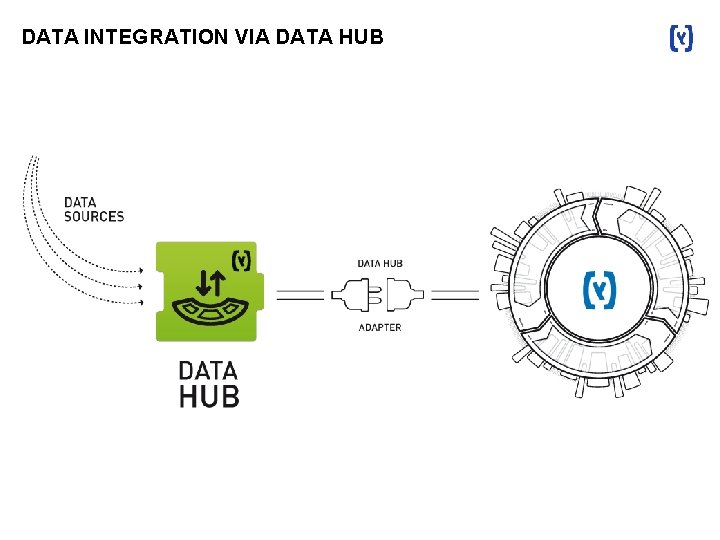
DATA INTEGRATION VIA DATA HUB
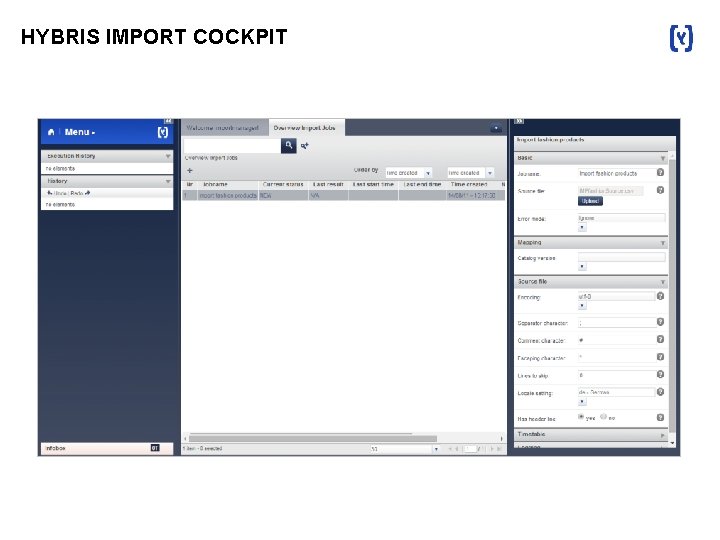
HYBRIS IMPORT COCKPIT
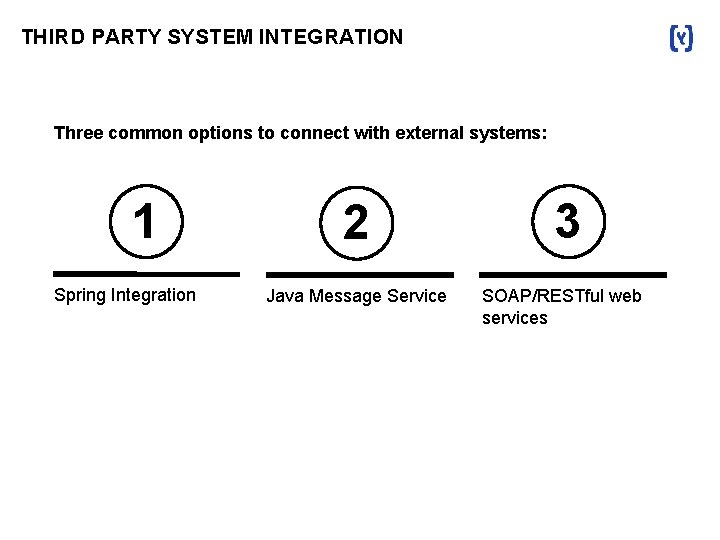
THIRD PARTY SYSTEM INTEGRATION Three common options to connect with external systems: 1 Spring Integration 2 Java Message Service 3 SOAP/RESTful web services
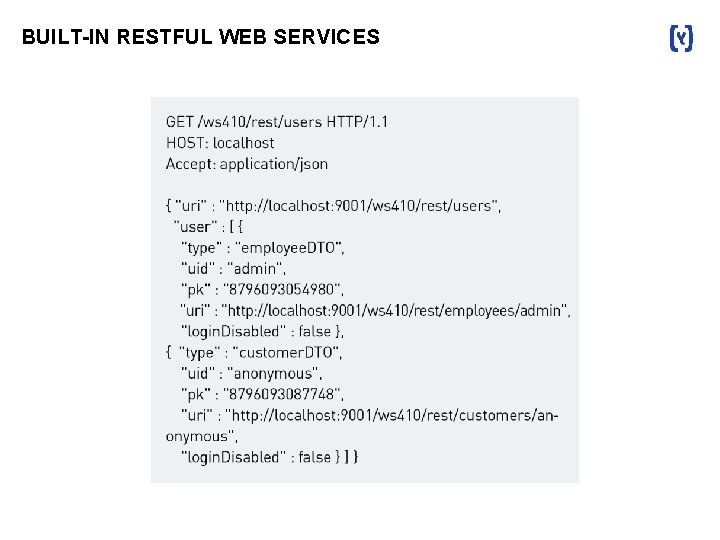
BUILT-IN RESTFUL WEB SERVICES

SPRING INTEGRATION & JAVA MESSAGE SERVICE
05 OPERATIONS

MINIMAL SYSTEM INFRASTRUCTURE
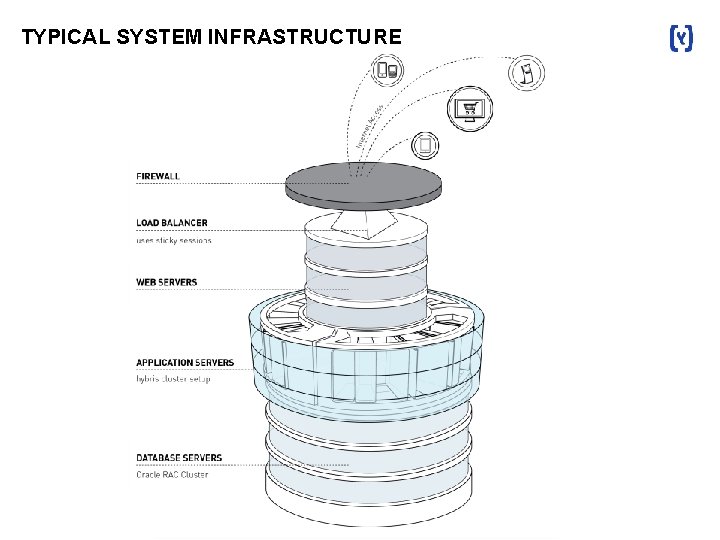
TYPICAL SYSTEM INFRASTRUCTURE
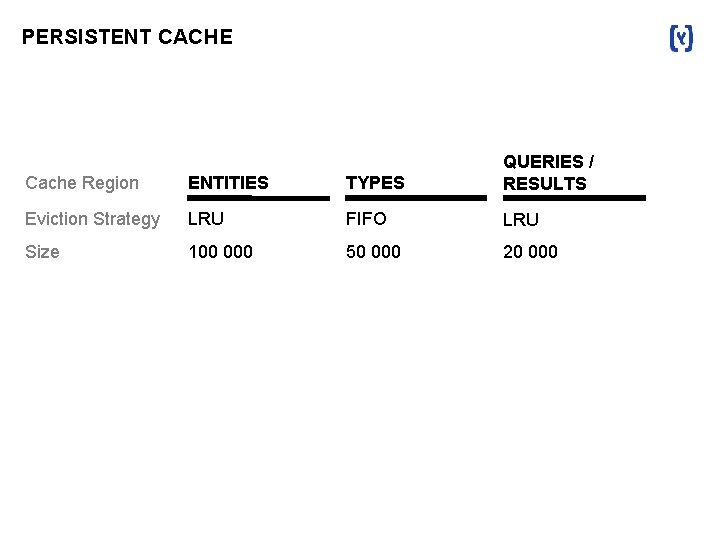
PERSISTENT CACHE Cache Region ENTITIES TYPES QUERIES / RESULTS Eviction Strategy LRU FIFO LRU Size 100 000 50 000 20 000
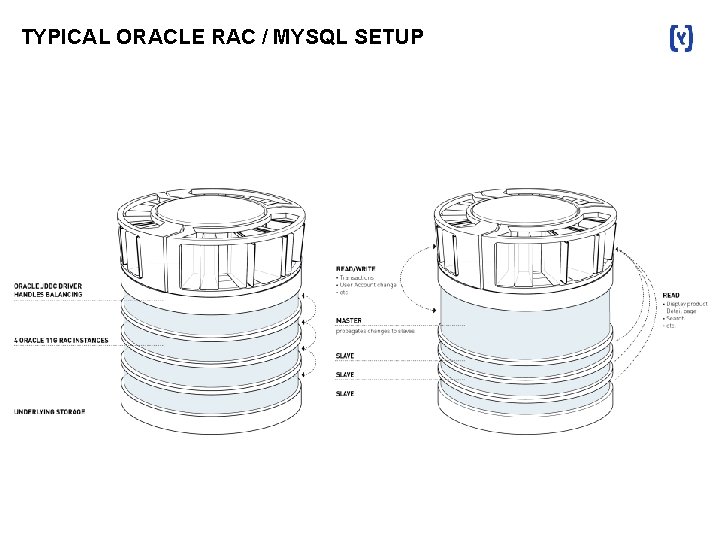
TYPICAL ORACLE RAC / MYSQL SETUP
SESSION FAILOVER Partial of full session failover. Transparent to users. Support for Oracle Coherence and Tomcat Session replication.
VIRTUALIZATION
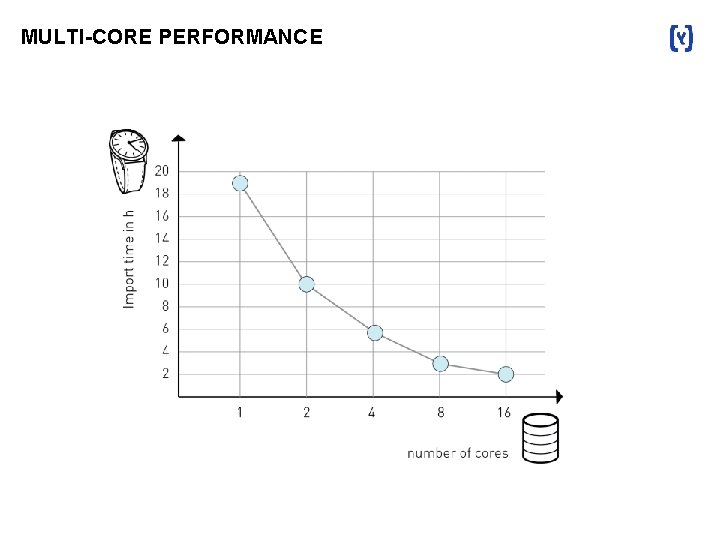
MULTI-CORE PERFORMANCE
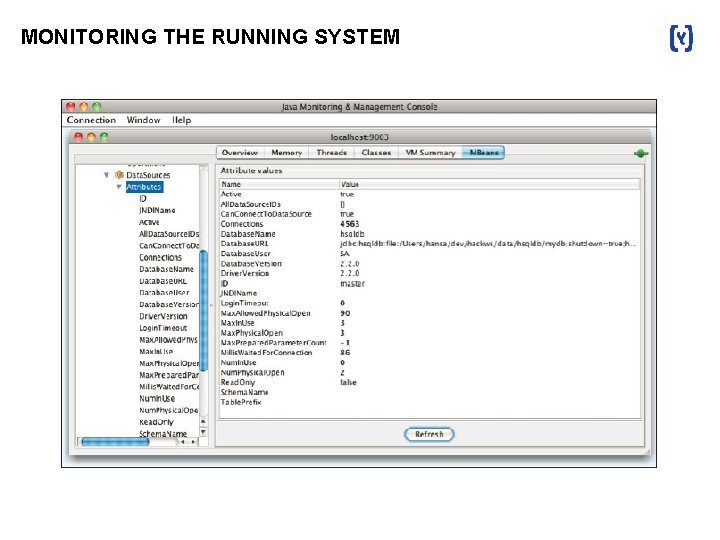
MONITORING THE RUNNING SYSTEM
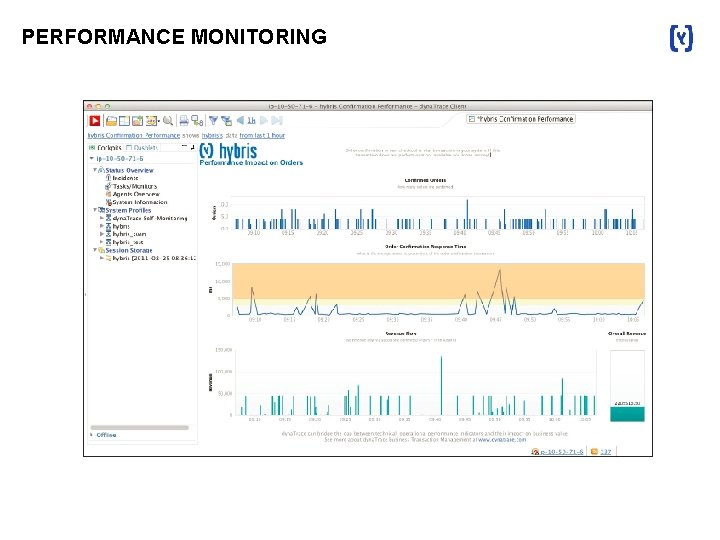
PERFORMANCE MONITORING

06 SECURITY

SECURITY
ROLE CREATION All security decisions based on user roles. Multiple roles for each user. Tools for hierarchical roles creation. Security check performed before execution of an action. Roles mapping stored on LDAP servers or hybris persistence.
SECURING YOUR MODEL Control of CRUD operations. Secured on the basis of user roles. Spring security mechanisms. hybris Flexible. Search filters.
SECURING YOUR DATA Hashing and encryption of sensitive data. Encryption of highly sensitive data. Managed through back-end administration UI. PCI compliancy support. Transparent Attribute Encryption.

AUDIT TRAILS All changes to information are recorded. Improved security maintenance. Type of change, user/entity, time, original and new values. Help identify loopholes, violations and spoofing.

AUTHENTICATION AND AUTHORIZATION WITH LDAP Integration with LDAP and Active directories. Importing of LDIF files and search results. Verification of user accounts. Support for Single. Sign-On.

- Slides: 51