http www grnet gr Firewall on Demand A




- Slides: 22

http: //www. grnet. gr Firewall on Demand A multidomain approach Leonidas Poulopoulos , Yannis Mitsos – GRNET NOC Firewall on Demand workshop TF-MSP meeting 27 -28 November 2014

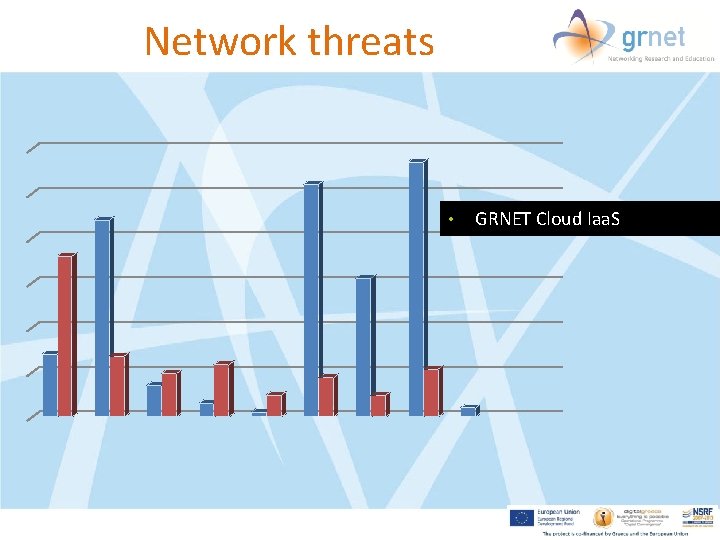
Network threats • GRNET Cloud Iaa. S

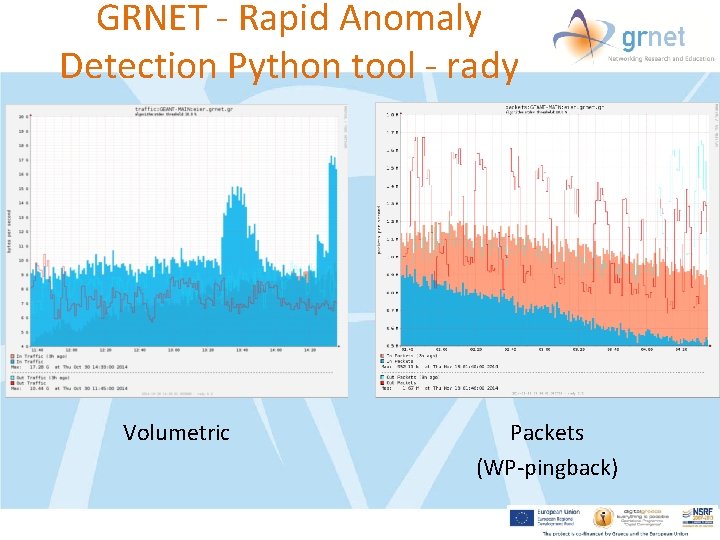
GRNET - Rapid Anomaly Detection Python tool - rady Volumetric Packets (WP-pingback)

Consequences • Performance degradation – GÉANT Backbone – NRENs • Outages • Services malfunction • Resources – Human – Equipment

Mitigation Techniques though time acls, firewall filters RTBH BGP flowspec

The BGP way • Well established model of trust • Stable and robust – Powers the internet • Remote triggered black-hole routing • BGP flow specification – “My name is Wall, Fire Wall”

Who are you BGP Flowspec? • • • BGP Flowspec defined in RFC 5575 Layer 4 (TCP and UDP) firewall filters to be distributed in BGP on both a intradomain and inter-domain basis Match – – – – • source/dest prefix source/dest port ICMP type/code packet size DSCP TCP flag fragment type Etc Actions – – – accept discard rate-limit sample redirect etc

A firewall filter over BGP? ? ? • Propagates wherever BGP flow spec is enabled – Currently supported by Juniper • To the very ends of the network • To peering networks – Downstream – Upstream Ideas! • Apply to a single point and let it propagate to my borders • Sounds like attacks are now mitigated closer to source!!! – YES!!!! • Seems that it is more granular than RTBH – YES!!!! • Can we automate this? ? Can we go from RFC to tool? – Have already done this!!!

Can you remind me why we need BGP flowspec? BGP RTHB ACLS • • • Distributed across the network Closer to the source Fine-grained even on core/backbone networks Multidomain easy propagation towards the upstream via BGP Easy automation & integration • • • Flowspec: enhancement of RTBH Does not affect all traffic to victim Less coarse More actions Separate NLRI

Firewall on Demand – from RFC to tool NEED FOR BETTER TOOLS TO MITIGATE TRANSIENTATTACKS DEVELOPED BY: GRNET GRANULARITY: Per-flow level ACTION: Drop, rate-limit, redirect SPEED: 1 -2 orders of magnitude quicker EFFICIENCY: closer to the source, multi-domain AUTOMATION: integration with other systems MANAGEABILITY: status track, web interface

GRNET setup

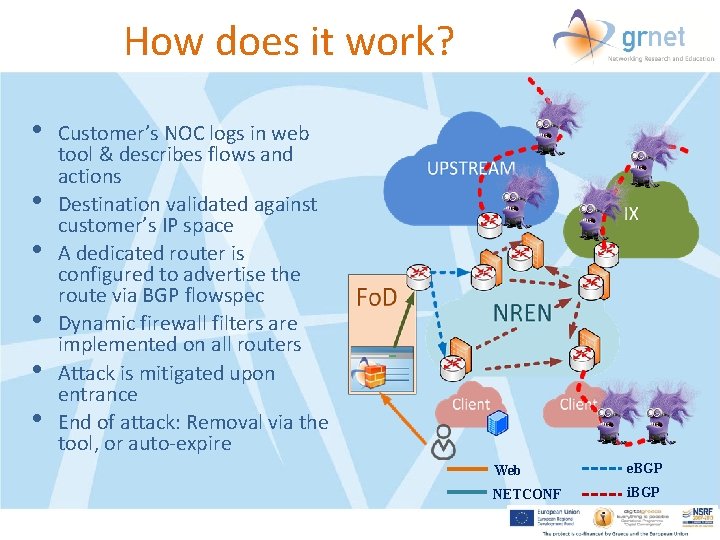
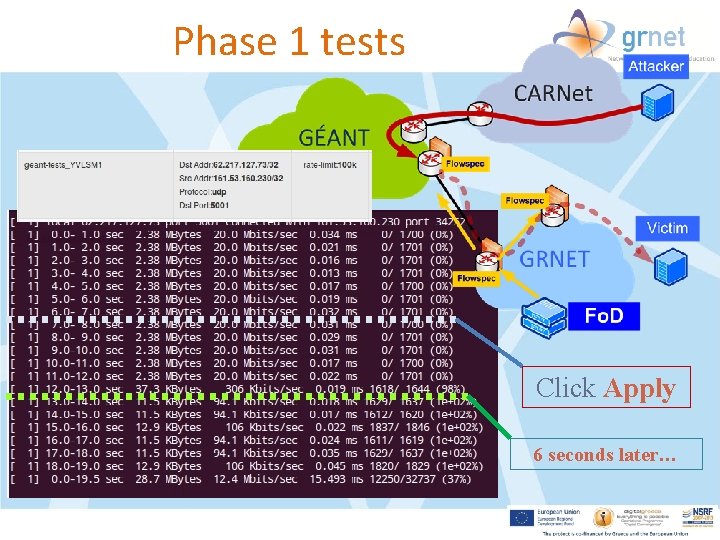
How does it work? • • • Customer’s NOC logs in web tool & describes flows and actions Destination validated against customer’s IP space A dedicated router is configured to advertise the route via BGP flowspec Dynamic firewall filters are implemented on all routers Attack is mitigated upon entrance End of attack: Removal via the tool, or auto-expire Web e. BGP NETCONF i. BGP

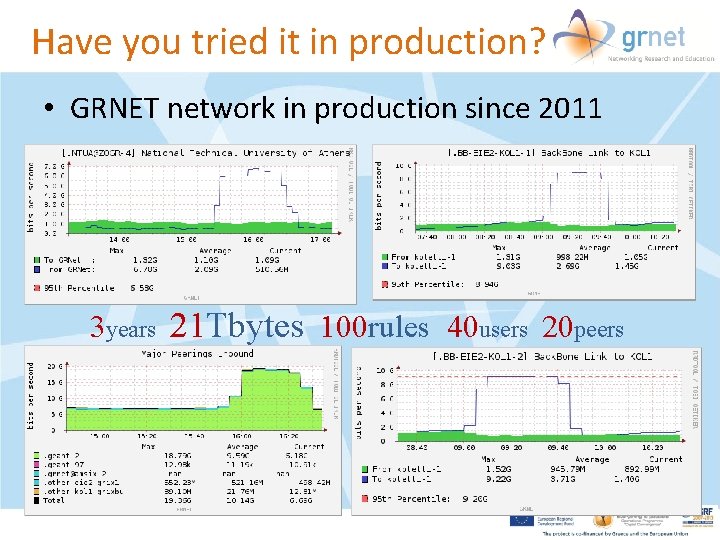
Have you tried it in production? • GRNET network in production since 2011 3 years 21 Tbytes 100 rules 40 users 20 peers

Time to go multidomain fod. geant. net

Fo. D recipe • 1 central Fo. D instance • BGP flowspec enabled in GÉANT routers • 3 flavors – NREN without BGP flowspec supporting equipment – NREN with BGP flowspec equipment that uses local Fo. D – NREN with BGP flowspec equipment that uses GEANT’s Fo. D

Phase 1 tests Click Apply 6 seconds later…

Fo. D Application Architecture OPEN SOURCE • https: //code. grnet. gr/projects/flowspy • http: //flowspy. readthedocs. org

Under the hood • Django application – 1. 4 – Debian Wheezy system packages • Application server – Gunicorn • HTTP server – Apache Proxy module • Database – My. SQL • Caching – Memcached • Job scheduler – Celeryd • Que – Beanstalkd • Network client – Ncclient - NETCONF

Installation and monitoring • Extensively tested on Debian Wheezy – Using system packages • Done in ~ 30 mins • Monitored components – Host checks – Service checks • Apache (check_http) • Gunicorn (check_mk) • Celeryd (check_mk)

Joining Fo. D • Shibboleth attributes: – email (maps to HTTP_EMAIL) – persistent-nameid or persistent-id or targeted-id (all map to HTTP_REMOTE_USER) • A valid institution/peer with active subnets

Support • GRNET will actively support Fo. D • Same codebase • Small changes in single and multidomain – Shibboleth vs. edu. GAIN • Full installation documentation of multidomain flavor will be provided by the end of Nov 2014

http: //www. grnet. gr Thank you