http mail im tku edu twychou ftp mail






















































































- Slides: 106

資訊安全專題 淡江大學 資訊管理系 侯 永 昌 http: //mail. im. tku. edu. tw/~ychou ftp: //mail. im. tku. edu. tw/Prof_Hou



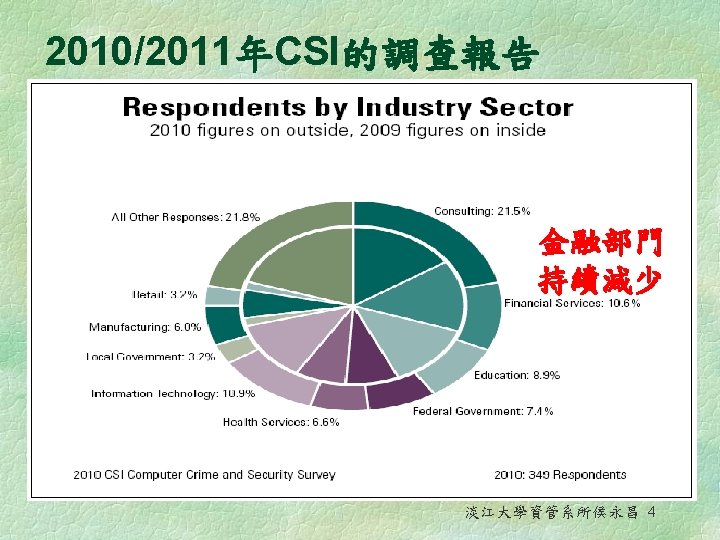
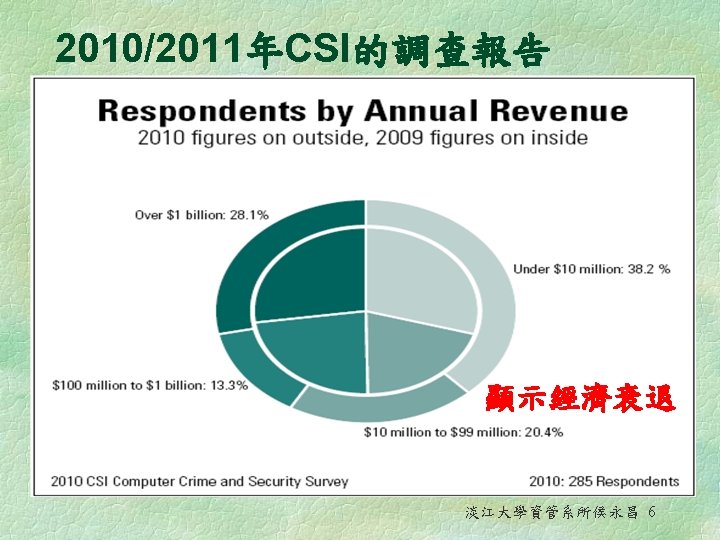
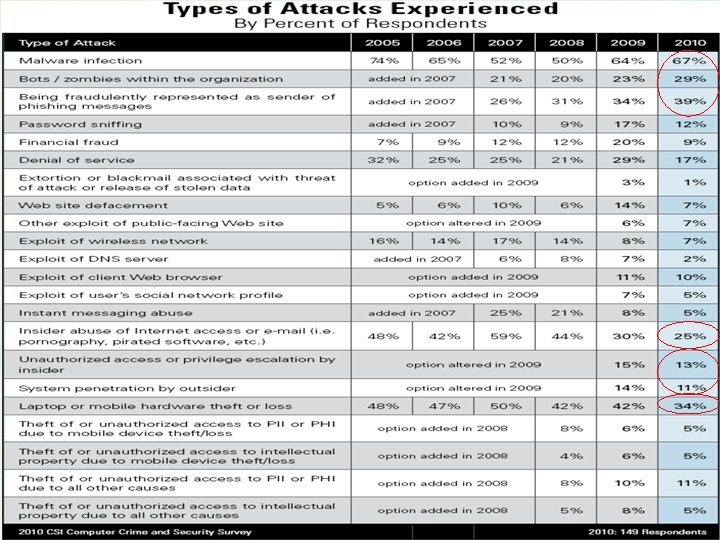
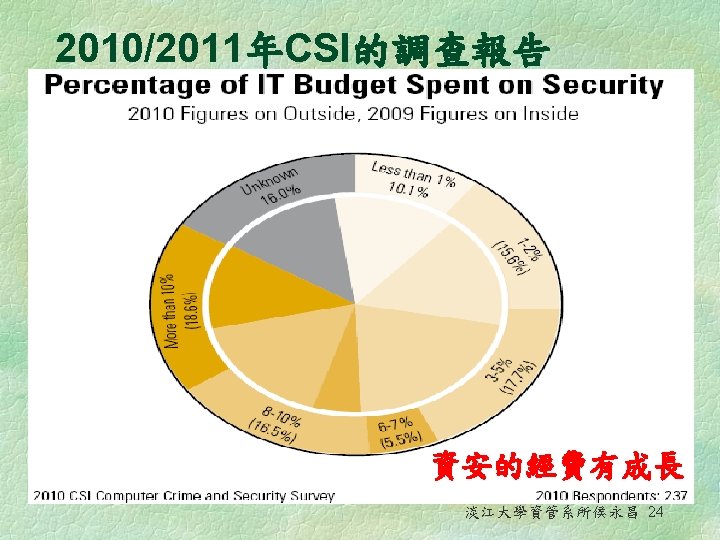
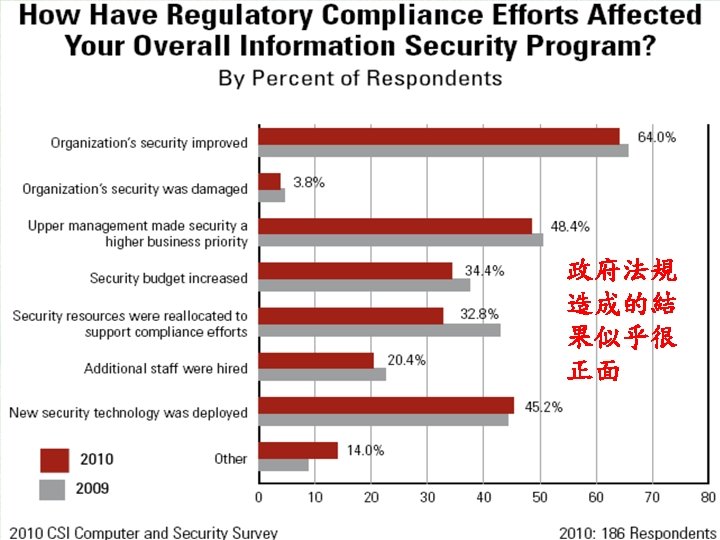
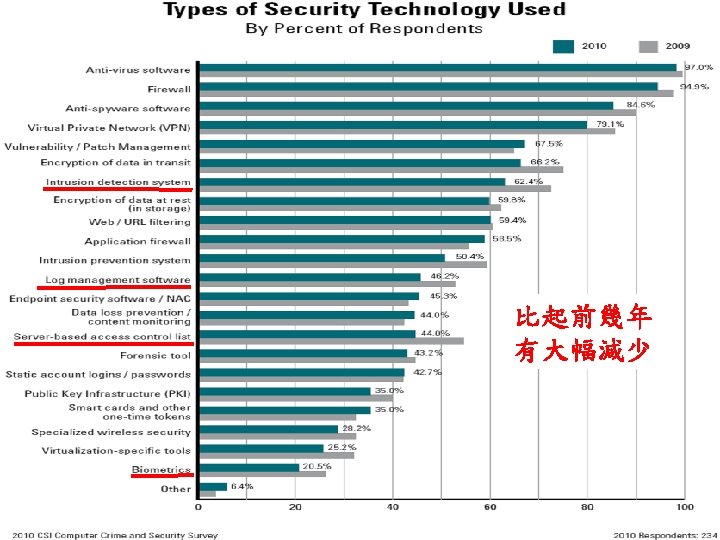
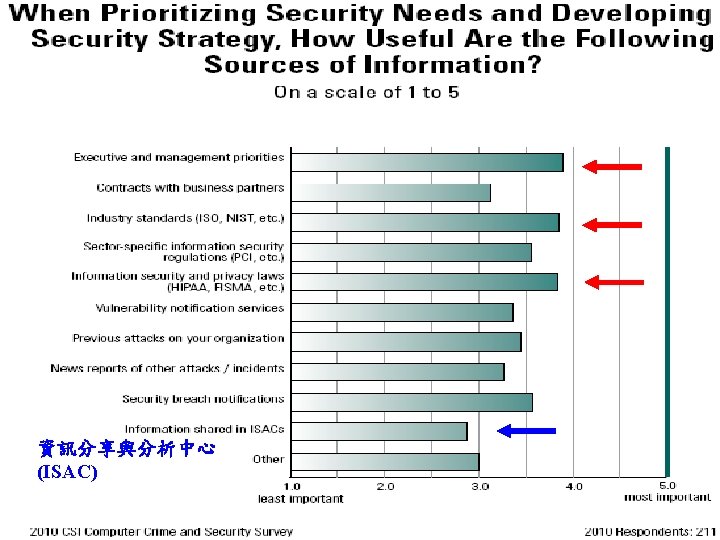
2010/2011年Computer Security Institute 的調查報告 - 15 th annual edition 淡江大學資管系所侯永昌 3







2010/2011年CSI的調查報告 Opportunistic vs. Targeted Harm to an organization vs. Stealing something of value No skill attacks vs. Sophisticated attacks 淡江大學資管系所侯永昌 10

2010/2011年CSI的調查報告 § Basic attacks l 例如︰phishing, port scans, brute force attacks on password-protected accounts, and old-school viruses § Malware attacks l 例如︰malware created from generation and customization toolkits, phishing attacks use real names known to victims in order to improve the credibility of the scam, tools that scan for unpatched systems with known vulnerabilities § Attacks 2. 0 – Advanced Persistent Threat l Attackers are spending more energy customizing malware to make it more effective in targeted attacks 淡江大學資管系所侯永昌 11























2010/2011年CSI調查報告的結語 § 整體資訊安全的狀況比想像的好,資安事件似乎變少了,平 均損失也下降,人們對於現有資安 具/技術也還滿意。但 攻擊的方式越來越複雜,一旦攻擊成功,金錢和資料的損失 都很可觀 § 等到web applications更加蓬勃時,也許問題又會變多了,因 為很多軟體並沒有好好的規劃,也沒有好好的測試 § 雖然對於targeted attacks談得很多,多數使用者似乎也不察覺 § 使用者關心的議題圍繞著better visibility into networks, web applications, and endpoints (particularly as those endpoints become increasingly mobile) § 網路環境愈來愈複雜的原因︰Virtualization (虛擬化) blurs the boundaries between servers and redraws network topologies. Cloud computing blurs the locality of data and running processes. The number of things in the world that have IP addresses blast the number of endpoints 淡江大學資管系所侯永昌 34


What Kinds of Security Questions Arise? § 使用者關心的議題: l l l How can the user be sure that the Web server is owned and operated by a legitimate company? 是否由合法的業者所擁有? How does the user know that the Web page and form do not contain some malicious or dangerous code or content? 是否含有病毒? How does the user know that the owner of the Web site will not distribute the information the user provides to some other party? 是否會洩漏 個人隱私? 淡江大學資管系所侯永昌 36

What Kinds of Security Questions Arise? § 業者關心的議題: l l How does the company know the user will not attempt to break into the Web server or alter the pages and content at the site? 網頁是否 會被人破壞? How does the company know that the user will not try to disrupt the server so that it is not available to others? 服務是否會被人中斷? 淡江大學資管系所侯永昌 37

What Kinds of Security Questions Arise? § 使用者與業者都關心的議題: l l How do both parties know that the network connection is free from eavesdropping by a third party “listening” on the line? 資料在傳送 過程中是否被人竊取? How do they know that the information sent back-and-forth between the server and the user’s browser has not been altered? 資料在 傳送過程中是否被人惡意串改? 淡江大學資管系所侯永昌 38

Basic Security Issues (I) § Authentication 認證 l The process by which one entity verifies that another entity is who he, she, or it claims to be • Something known: e. g. password • Something possessed: e. g. smartcard • Something unique: e. g. signature § Authorization 授權 l The process that ensures that a person has the right to access certain resources • Comparing with access control information associated with the resource being accessed 淡江大學資管系所侯永昌 39

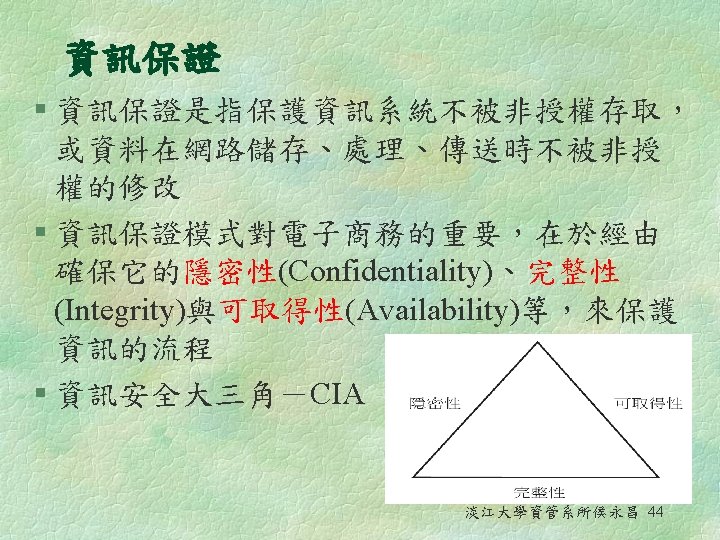
Basic Security Issues (II) § Auditing 稽核 l The process of collecting information about attempts to access particular resources, use particular privileges, or perform other security actions • Log file § Confidentiality (Privacy) 隱密性(隱私) l Information that is private or sensitive should not be disclosed to unauthorized individuals, systems, or software processes • Encryption 淡江大學資管系所侯永昌 40

Basic Security Issues (III) § Integrity 完整性 l Protecting data from being altered or destroyed in an unauthorized or accidental manner • Encryption while it is in transit § Availability 可取得性 l Ensuring that data and services are available when needed • Load-balancing hardware and software 淡江大學資管系所侯永昌 41

Basic Security Issues (III) § Non-repudiation 不可否認性 l Ability to limit parties from refuting that a legitimate transaction took place • Signature 淡江大學資管系所侯永昌 42

General Security Issues at EC Sites 淡江大學資管系所侯永昌 43







Nontechnical Attacks § “The key to successful social engineering is trust. You try to make an emotional connection with the person on the other side to create a sense of trust ~ Mitnick and Simon 2002 and then exploit it. ” § 由於成功的社交 程取決於受騙者的合作,因此對 抗社交 程攻擊也一樣是取決於受騙者 § A multiprong approach should be used to combat social engineering l l l Education and training Policies and procedures Penetration testing 淡江大學資管系所侯永昌 50



Denial-of-service Attacks § Denial-of-service (Do. S) attack 阻斷服務 l An attack on a Web site in which an attacker uses specialized software to send a flood of data packets to the target computer with the aim of overloading its resources § Distributed Dos (DDo. S) attack l A denial-of-service attack in which the attacker gains illegal administrative access to as many computers on the Internet as possible and uses the multiple computers to send a flood of data packets to the target computer 淡江大學資管系所侯永昌 53

Using Zombies in a DDo. S Attack 淡江大學資管系所侯永昌 54

Malicious Code Attacks § 惡意軟體(Malware)日益盛行的原因為: l l Mixing data and executable instructions Increasingly homogenous computing environments Unprecedented connectivity Larger clueless user base 淡江大學資管系所侯永昌 55


Managing EC Security § Common mistakes in managing security risks: l l l Undervalued information:不了解資訊的價值以致於不 受重視 Narrowly defined security boundaries:只重視內部網路 的安全而忽略外部 (例如:上下游客戶) 的影響 Reactive security management:等到事情發生了才來 亡羊補牢 Dated security management processes:安全的設施、 知識與訓練跟不上環境的變化 Lack of communication about security responsibilities: 安全被認為是 IT 部門的 作,而非整個組織的 作,以 致於大部分的人不關心也不懂 淡江大學資管系所侯永昌 57

Security Risk Management § A systematic process for determining the likelihood of various security attacks and for identifying the actions needed to prevent or mitigate those attacks § Security risk management consists of three phases: l l l Asset identification Risk assessment Implementation 淡江大學資管系所侯永昌 58

Security Risk management § Asset identification l Inventory organization’s information assets, determine the relative value and criticality § Risk assessment l l l Delineate threats against those assets, such as hackers, viruses, disgruntled employees, human error, system failures Identify the vulnerabilities of the systems Calculate quantitative risk for each asset in order to determine which assets should be safeguarded and which threats need to be minimized 淡江大學資管系所侯永昌 59

Security Risk management § Implementation Organization arrives a set of security policies defining which threats are tolerable and which are not • Particular technologies are chosen to address the high priority threats l Establish an incident response team and contingency plan l Establish process for audit and review at least every 6 months • Which policies and technologies are successful • Which are unsuccessful and need modification • What types of new threats are appearing on the horizon l 淡江大學資管系所侯永昌 60


對稱式(私鑰)系統 § Symmetric (private) key system l 在對稱式(私鑰)系統中,相同一把鑰匙用以加密 與解密原始明文資料 § Data Encryption Standard (DES) l The standard symmetric encryption algorithm supported the NIST and used by U. S. government agencies until October 2, 2000 § Rijndael l The new Advanced Encryption Standard (AES) used to secure U. S. government Communications since October 2, 2000 淡江大學資管系所侯永昌 62



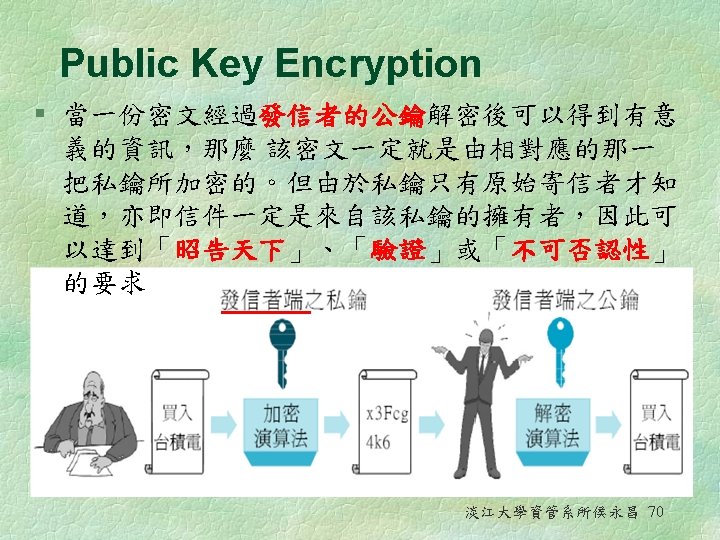
Public key infrastructure § Asymmetric (Public) Key Encryption l l 公鑰(非對稱式)加密是使用一對配合的鑰匙 — a public key to encrypt a message and a private key to decrypt it, or vice versa • Public key 公鑰:它可以公開給任何人 • Private key 私鑰:它僅可以給擁有者知道 最常用的公鑰加密演算法是非對稱式加密法(RSA)。 RSA使用金鑰長度範圍從 512位元至 1024位元 淡江大學資管系所侯永昌 65










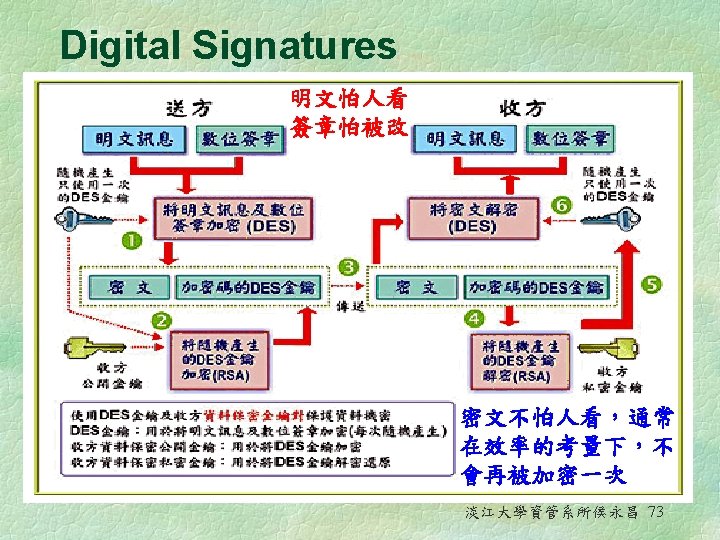
Digital Signatures § Hash 雜湊 l A mathematical computation that is applied to a message, using a private key, to encrypt the message § Message digest 資訊摘要 l A summary of a message, converted into a string of digits, after the hash has been applied § Digital signature 數位簽章 l An identifying code that can be used to authenticate the identity of the sender of a document § Digital envelope 數位信封 l The combination of the encrypted original message and the digital signature, using the recipient’s public key 淡江大學資管系所侯永昌 75

Digital Signatures § The recipient has evidence that the sender sent the message because (theoretically) the sender is the only one with access to private key § The recipient knows that the message has not been tampered with, because if it had been the two hashes would not have matched 淡江大學資管系所侯永昌 76


Public key infrastructure § 當某人告訴你說他是侯永昌,並給你一個 public key,請你傳訊息給他。你怎麼知道他就是真的侯 永昌?這個 key 是不是真的侯永昌的 public key? § Digital certificate l l Verification that the holder of a public or private key is who he or she claims to be A certificate contains things such as the holder’s name, validity period, public key information, and a signed hash of the certificate data with the CA’s private key § Certificate authorities (CAs) l Third parties that issue digital certificates 淡江大學資管系所侯永昌 78

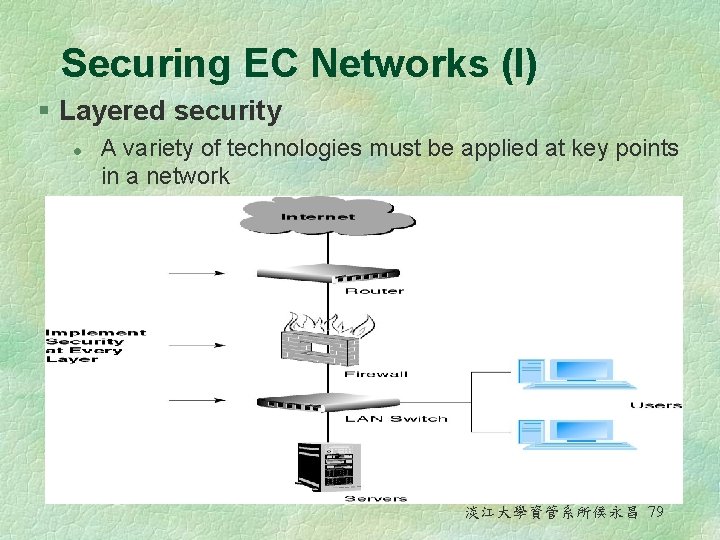
Securing EC Networks (I) § Layered security l A variety of technologies must be applied at key points in a network 淡江大學資管系所侯永昌 79

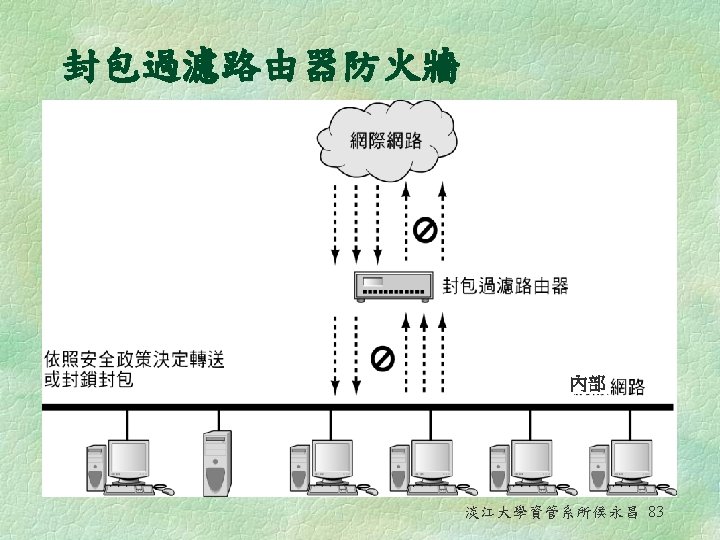
Firewalls § A network node consisting of both hardware and software that isolates a private network from a public network § There are basically two types of firewalls: l Packet-filtering routers l Application-level proxies 淡江大學資管系所侯永昌 80








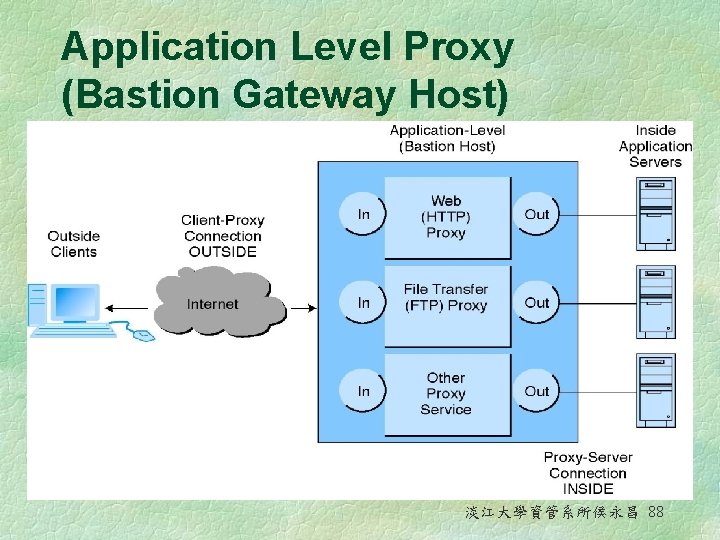
Application Level Proxy (Bastion Gateway Host) 淡江大學資管系所侯永昌 88




Application-level proxy § Bastion gateway 防禦主機 l A special hardware server that utilizes application-level proxy software to limit the types of requests that can be passed to an organization’s internal networks from the public Internet § Proxies 代理服務 l Special software programs that run on the gateway server and pass repackaged packets from one network to the other 淡江大學資管系所侯永昌 92







Application-Level Proxies § In addition to controlling inbound traffic, all outbound traffic requests look as if they were coming from a single computer rather than multiple computers. In this way, the IP address of the internal computers are hidden to the outside § Disadvantage: l l It takes more processing time to tie particular packets to particular applications The users on the internal network must configure their machines or browsers to send their Internet requests via the proxy server 淡江大學資管系所侯永昌 99


Virtual Private Networks (VPNs) § With a private line, the chance of a hacker eavesdropping on the communications between the companies would be nil, but it is an expensive way to do business § VPNs which enable secure transmissions across the Internet are generally used to support site-to-site transmissions between B 2 B partners or communications between a mobil and remote worker and a LAN at a central office 淡江大學資管系所侯永昌 101


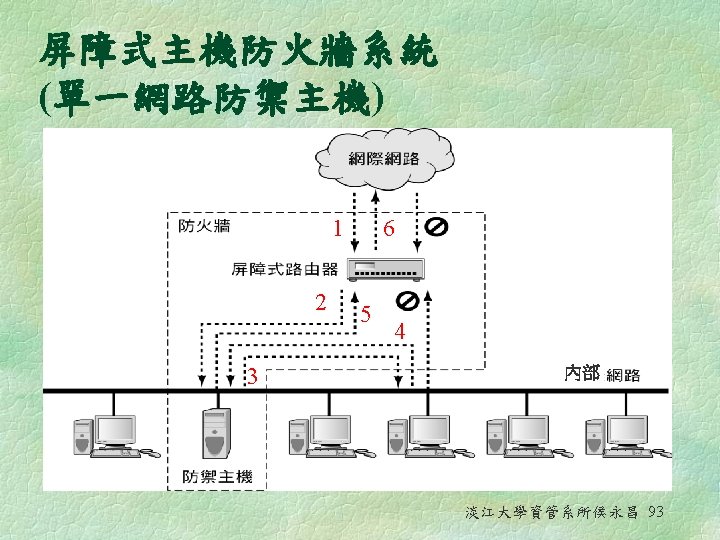
Intrusion Detection Systems (IDS) § In the past, audit logs were manually reviewed for excessive failed logon attempts, failed file and database access attempt, and other application and system violations § 現今有一些特殊種類的軟體能監督橫跨一個 網路或一個主機的活動,監視可疑的活動, 以及根據它所看到的自動採取一些行動,這 類的軟體稱為入侵偵測系統 (Intrusion Detection Systems; IDS) 淡江大學資管系所侯永昌 103

Intrusion Detection Systems (IDS) § Host-based IDS resides on the server or other host system that is being monitored § It is good at detecting l Whether critical or security-related files have been tampered with l Whether a user attempts to access files that he is not authorized to use § It computes a special signature or checksum for each file. Then, it checks files on regular basis to see if the current signatures match the previous signatures. If it doesn’t match, security personnel are immediately notified 淡江大學資管系所侯永昌 104

Intrusion Detection Systems (IDS) § Network-based IDS uses rules to analyze suspicious activity at the perimeter of a network or at key locations in the networks l Examine network traffic for known patterns of attack l Automatically notify security personnel when specific events or event thresholds occur l Perform certain actions when an attack occurs. For instance, it can terminate network connections or reconfigure network devices based on security policies 淡江大學資管系所侯永昌 105