HP World 2005 Securing your Unix environment with





















![Public Key Exchange: Change prompt • PS 1= [8476#] echo ${PS 1} Wed Jun Public Key Exchange: Change prompt • PS 1= [8476#] echo ${PS 1} Wed Jun](https://slidetodoc.com/presentation_image_h2/a663e9b0d991c8e7c8e83c0d91273989/image-33.jpg)


![Public Key Exchange: Home directory permissions [1168#] env | grep HOME=/root/ Thu Jun 2 Public Key Exchange: Home directory permissions [1168#] env | grep HOME=/root/ Thu Jun 2](https://slidetodoc.com/presentation_image_h2/a663e9b0d991c8e7c8e83c0d91273989/image-38.jpg)





- Slides: 46

HP World 2005 Securing your Unix environment with HP Secure Shell Steven E Protter Senior Systems Administrator I. S. N. Corporation

Secure Shell Presentation Outline 1 • Presenter information – Qualifications and experience. – Warning !! – How he got here. • What is HP Secure Shell – Advantages – Challenges – Components

Secure Shell Presentation Outline 2 • Where do I get HP Secure Shell • How do I install HP Secure Shell • Why should I use HP Secure Shell

Secure Shell Presentation Outline 3 • Step by step for installation and exchange of public keys. – Downloading the software. – Installation. – Exchanging public keys. • Questions and (hopefully) answers

Getting Started

Qualifications and Experience 1 10 years of systems administration work on HP-UX 10. 20, 11 and 11 i v 1 • Actual Experience with a disaster involving major loss of data. • Five years of experience as a Linux administrator • HP-UX CSA (Can pass a multiple choice examination) • Two major Unix OS/Hardware conversions.

Qualifications and Experience 2 • 14 ½ Years @ the Jewish United Fund • Experience as a programmer. • Systems Analyst • Software AG and Oracle DBA • HP-UX Administrator • Married 10 years to a Russian American • Recently moved to Israel

Warning! Try this at your shop! • I do not have complete knowledge on topic – Nobody can, its two complex. – Have made this work in a mixed HP-UX/Linux environment. • Can only understand Russian accented English. • This is something you want to try at home.

How Steve Protter Got here • Found a call for presentations at http: //forums. itrc. hp. com – Sent in two suggestions – Both were accepted • Flew from Tel Aviv to Newark, NJ • Drove from Connecticut to San Francisco – Made several consulting stops in route

What is HP Secure Shell? • Hewlett-Packard’s port of openssh • Open source product • More information @ http: //www. openssh. org

More Information

Advantages of HP Secure Shell? • Hewlett-Packard’s Port of openssh – – Some bugs were fixed prior to HP release. Released in depot format Port insures smooth operation with HP-UX Replaces insecure products such as rsh and remesh – Session and passwords are encrypted

Challenges of HP Secure Shell? • Sometimes you have to wait for it. • The environment is slightly different than what it replaces. • You can not completely remove the old protocols and still do Ignite Imaging. • To be announced.

Secure Shell Components 1 • ssh: Secure Shell – Replaces rsh, rexec, remesh, telnet • sftp: Secure file transfer protocol – Common command set with ftp – Knows the difference between binary and ascii files – No mput – Scriptable

Secure Shell Components 2 • scp: Secure copy – Replaces rcp – Can copy large file systems – Makes my life easier

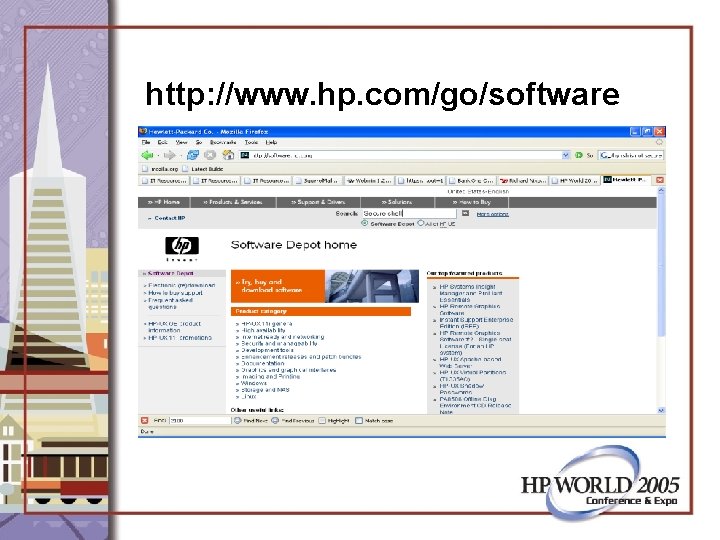
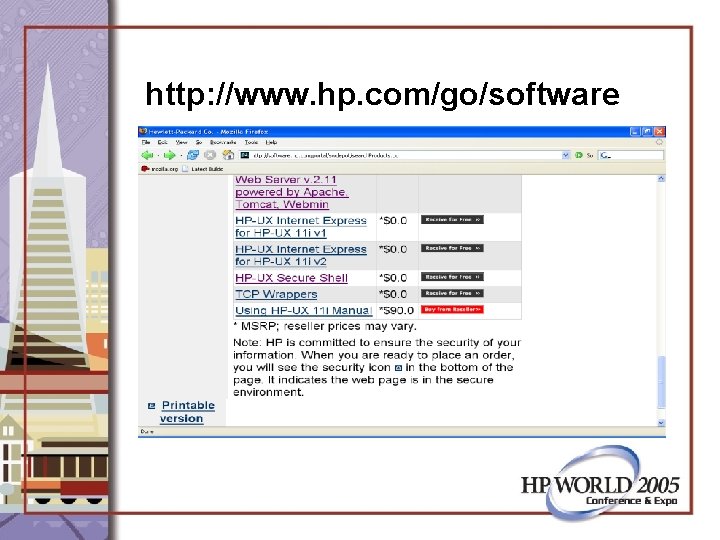
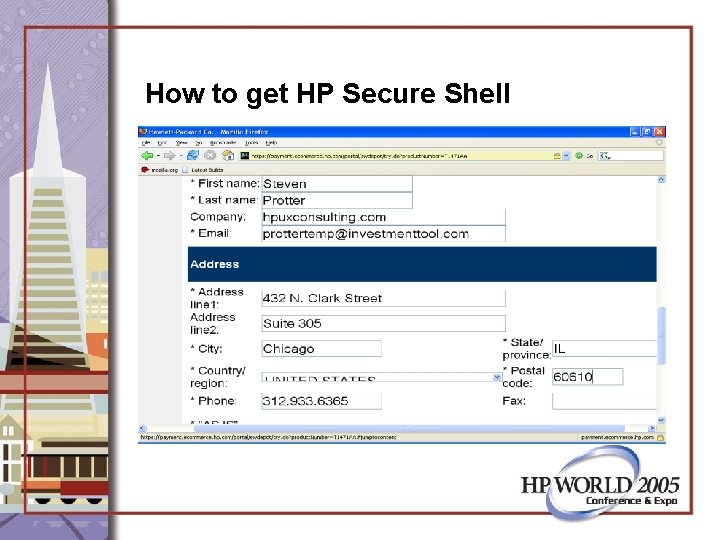
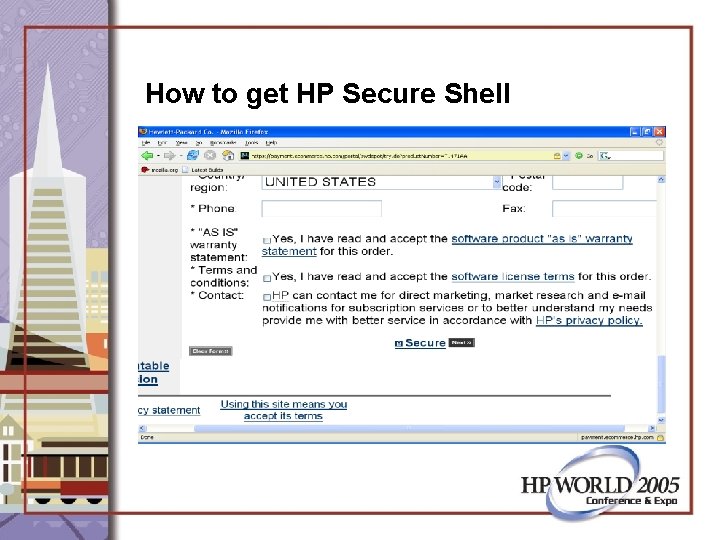
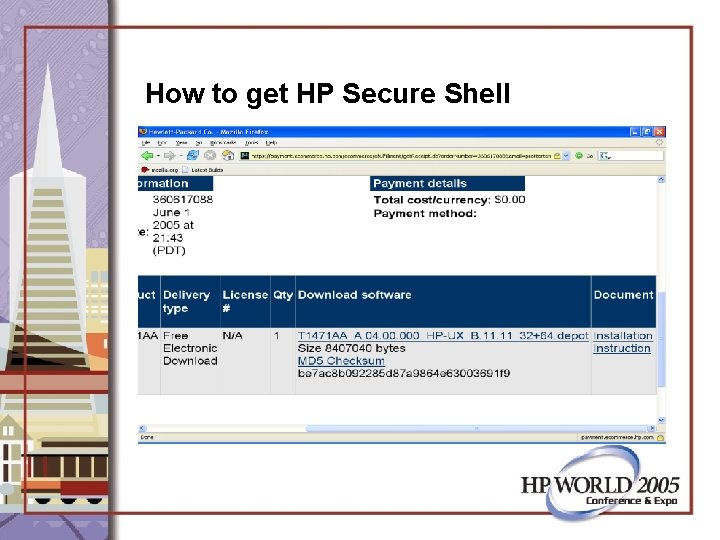
How to get HP Secure Shell • Core OS: It is/may be an install option • Application CD: Released every 6 months • http: //www. hp. com/go/software

http: //www. hp. com/go/software

http: //www. hp. com/go/software

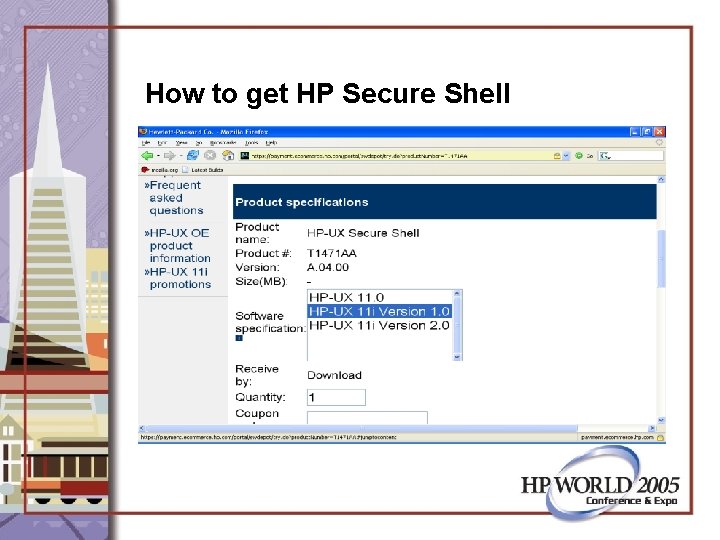
How to get HP Secure Shell

How to get HP Secure Shell

How to get HP Secure Shell

How to get HP Secure Shell

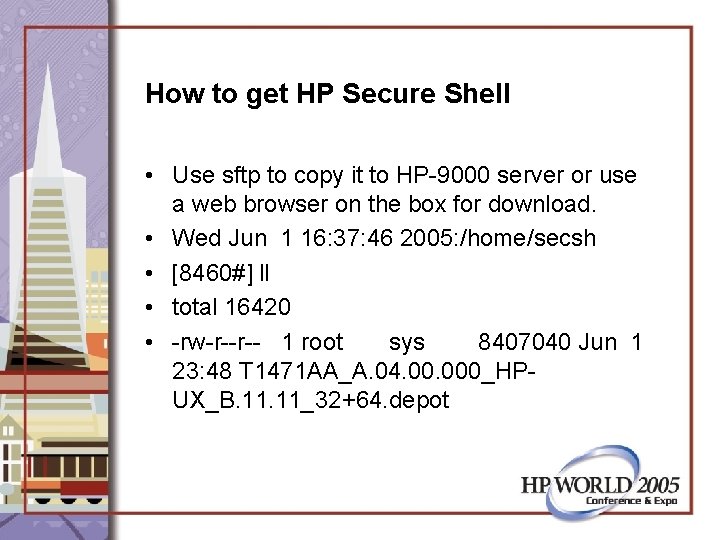
How to get HP Secure Shell • Use sftp to copy it to HP-9000 server or use a web browser on the box for download. • Wed Jun 1 16: 37: 46 2005: /home/secsh • [8460#] ll • total 16420 • -rw-r--r-- 1 root sys 8407040 Jun 1 23: 48 T 1471 AA_A. 04. 000_HPUX_B. 11_32+64. depot

Before you install • Read the installation instructions – Not because you don’t know how to swinstall. – Because there may be patch recommendations and other helpful information.

Patches • 11 i version 1 patches – Pam patch: PHCO_30402 – OS patch: PHCO_26466 swlist –l product | grep PHCO_30402 swlist –l product | grep PHCO_26466 • Why? It may still install but give trouble later.

How to install HP Secure Shell swinstall -s /home/secsh/T 1471 AA_A. 04. 000_ HP-UX_B. 11_32+64. depot *

“The command line is the Systems Administrators best friend. ” Steven E Protter Senior Systems Administrator ISN Corporation

“Because someday it may be all you have. ” Steven E Protter Senior Systems Administrator ISN Corporation

Situations with no GUI tools: • Single User Mode (hpux –is) • LM mode (hpux –lm)

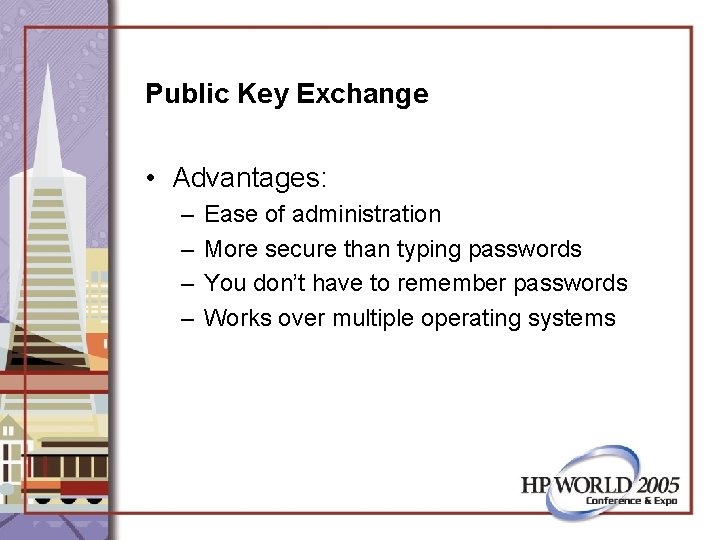
Public Key Exchange • Advantages: – – Ease of administration More secure than typing passwords You don’t have to remember passwords Works over multiple operating systems

Public Key Exchange • Challenges: – You may someday boot the wrong system – If a root password is compromised on one system root access is granted on all systems with public key exchange.

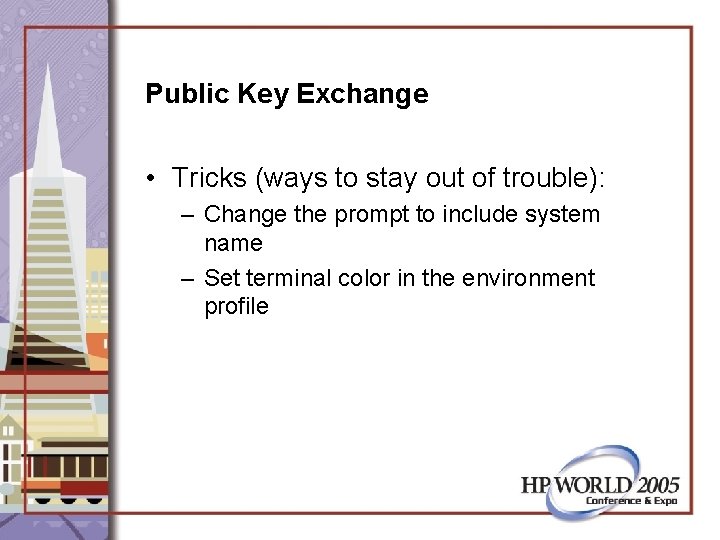
Public Key Exchange • Tricks (ways to stay out of trouble): – Change the prompt to include system name – Set terminal color in the environment profile
![Public Key Exchange Change prompt PS 1 8476 echo PS 1 Wed Jun Public Key Exchange: Change prompt • PS 1= [8476#] echo ${PS 1} Wed Jun](https://slidetodoc.com/presentation_image_h2/a663e9b0d991c8e7c8e83c0d91273989/image-33.jpg)
Public Key Exchange: Change prompt • PS 1= [8476#] echo ${PS 1} Wed Jun 1 16: 37: 46 2005: $PWD [!#] In /etc/profile ENV=/. kshrc

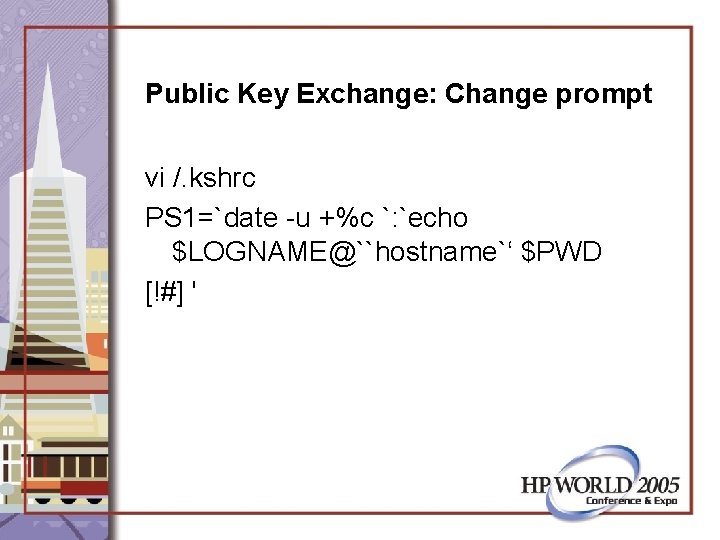
Public Key Exchange: Change prompt vi /. kshrc PS 1=`date -u +%c `: `echo $LOGNAME@``hostname`‘ $PWD [!#] '

Public Key Exchange: Change prompt • A prompt that lets you know where you are Thu Jun 2 13: 50: 10 2005: root@eilat /root/ [1158#]

Public Key Exchange: Generate keys ssh-keygen -t dsa. Press <ENTER> for the next 3 questions This creates a directory called. ssh cd. ssh

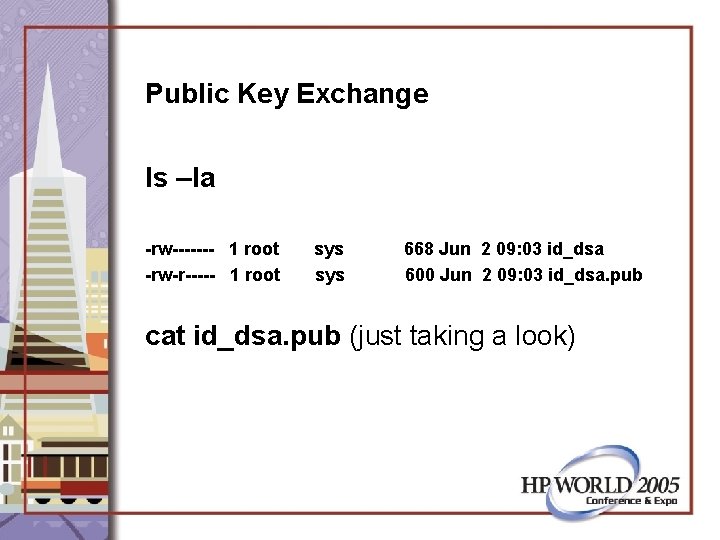
Public Key Exchange ls –la -rw------- 1 root -rw-r----- 1 root sys 668 Jun 2 09: 03 id_dsa 600 Jun 2 09: 03 id_dsa. pub cat id_dsa. pub (just taking a look)
![Public Key Exchange Home directory permissions 1168 env grep HOMEroot Thu Jun 2 Public Key Exchange: Home directory permissions [1168#] env | grep HOME=/root/ Thu Jun 2](https://slidetodoc.com/presentation_image_h2/a663e9b0d991c8e7c8e83c0d91273989/image-38.jpg)
Public Key Exchange: Home directory permissions [1168#] env | grep HOME=/root/ Thu Jun 2 13: 50: 10 2005: root@eilat /root/. ssh [1169#] chmod 755 $HOME Thu Jun 2 13: 50: 10 2005: root@eilat /root/. ssh

Public Key Exchange: Host setup ssh hpweb The authenticity of host 'hpweb (192. 168. 0. 70)' can't be established. RSA key fingerprint is 97: 1 d: cb: bf: b 3: 54: 9 f: 54: 12: 8 f: 2 f: 3 a: aa: b 9: 10: 7 c. Are you sure you want to continue connecting (yes/no)? yes <enter> Warning: Permanently added 'hpweb, 192. 168. 0. 70' (RSA) to the list of known hosts. Password:

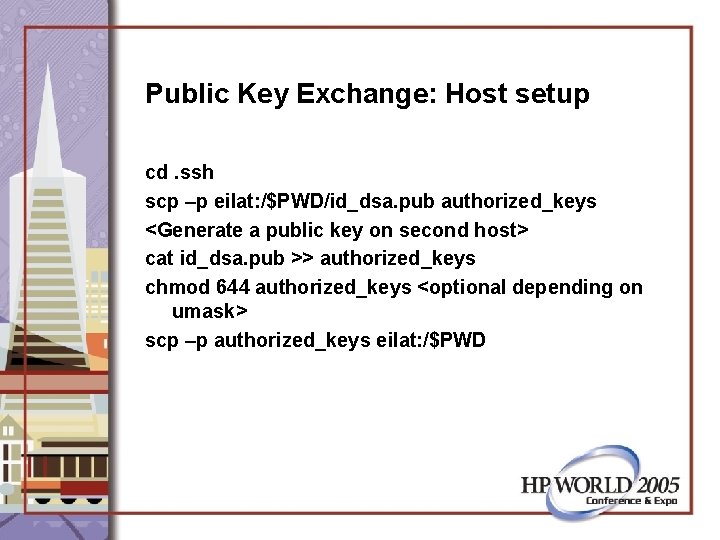
Public Key Exchange: Host setup cd. ssh scp –p eilat: /$PWD/id_dsa. pub authorized_keys <Generate a public key on second host> cat id_dsa. pub >> authorized_keys chmod 644 authorized_keys <optional depending on umask> scp –p authorized_keys eilat: /$PWD

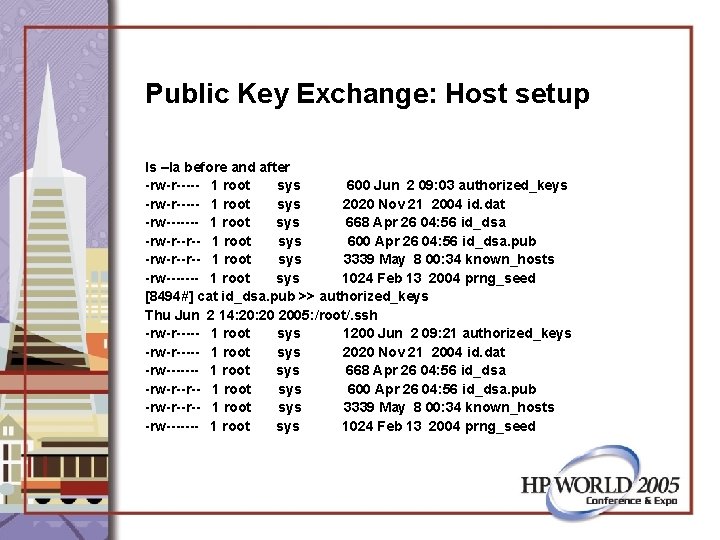
Public Key Exchange: Host setup ls –la before and after -rw-r----- 1 root sys 600 Jun 2 09: 03 authorized_keys -rw-r----- 1 root sys 2020 Nov 21 2004 id. dat -rw------- 1 root sys 668 Apr 26 04: 56 id_dsa -rw-r--r-- 1 root sys 600 Apr 26 04: 56 id_dsa. pub -rw-r--r-- 1 root sys 3339 May 8 00: 34 known_hosts -rw------- 1 root sys 1024 Feb 13 2004 prng_seed [8494#] cat id_dsa. pub >> authorized_keys Thu Jun 2 14: 20 2005: /root/. ssh -rw-r----- 1 root sys 1200 Jun 2 09: 21 authorized_keys -rw-r----- 1 root sys 2020 Nov 21 2004 id. dat -rw------- 1 root sys 668 Apr 26 04: 56 id_dsa -rw-r--r-- 1 root sys 600 Apr 26 04: 56 id_dsa. pub -rw-r--r-- 1 root sys 3339 May 8 00: 34 known_hosts -rw------- 1 root sys 1024 Feb 13 2004 prng_seed

Public Key Exchange: Host setup scp –p authorized_keys eilat: /$PWD You will be prompted for a password. Try it again, you should not be prompted for a password. DONE!

Public Key Exchange: Summary • Permissions are crucial. – If prompted for a password when you think you should not be prompted, go back and check permissions

Questions & (Hopefully) Answers

More Information • • http: //forums. itrc. hp. com http: //docs. hp. com http: //itrc. hp. com http: //www. hp. com/go/software
