How to Use NIST SP 800 16 Information












































- Slides: 52

How to Use NIST SP 800 -16 “Information Technology Security Training Requirements: A Role- and Performance-Based Model” Mark Wilson, CISSP Computer Security Division, ITL National Institute of Standards and Technology - January 19, 2005 mark. wilson@nist. gov (301) 975 -3870 (voice) (301) 975 -4007 (fax) http: //csrc. nist. gov/

2

Today’s Menu. . . • • FISMA & OPM Say. . . NIST SP 800 -16 Background Break NIST SP 800 -16 Building Blocks How to Use NIST SP 800 -16 Break Exercise Wrap Up 3

Objectives of This Workshop • Understand: – – – The NIST Special Publication (SP) 800 -16 Learning Continuum Awareness Versus Training Why Role-Based Training SP 800 -16 Roles Relationship Between Cells and Job Functions (Roles) Relationship Between Topics & Concepts and Cells • Be Able to: – Draft an Outline or Complete Course Structure – Determine if a Training Course “Meets NIST SP 800 -16” 4

Introductions: Who Are We? • • • Who What (is your title? ) Where (do you work; what is your affiliation? ) Why (are you here? ) For How Long ( in information security, training development, OIG, or other discipline? ) 5

FISMA Says. . . • Each agency shall develop, document, and implement an agencywide information security program. . . that includes. . . security awareness training [we call that “awareness”] to inform personnel, including contractors and other users of information systems that support the operations and assets of the agency. . . 6

When We Say “Users”. . . • “Users” Does Not Mean Only Employees • Users Include: – – – – Employees Contractors Foreign or domestic guest researchers Other agency personnel Visitors Guests Other collaborators or associates requiring access 7

FISMA Also Says. . . • The head of each agency shall. . . delegate to the agency Chief Information Officer. . . training and overseeing personnel with significant responsibilities for information security. . . • The head of each agency shall. . . ensure that the agency has trained personnel sufficient to assist the agency with complying with. . . 8

FISMA: Train People with Significant Responsibilities. . . • Who? – CIO? – CISO & Security Staff? – System Owners? – Application Owners? – Data Owners? – Contractors? 9

FISMA: Train People with Significant Responsibilities. . . • Who? – Network Administrators? – System Administrators? – Server (e. g. , mail, web) Administrators? – Records Management Officials? – Law Enforcement Officials? – General Counsel? 10

FISMA: Train People with Significant Responsibilities. . . • How to Decide? – – – – Documented in Policy? Documented in Position Descriptions? Documented in Performance Plans? Documented in Security Plans? Documented in Contingency Plans, COOPs? Documented in IG Reports? (Wait for IG Report? ) Just Makes Sense? Good Security Practice? (Get Buyin) 11

OPM (June 2004) Says. . . • Develop awareness and training plan • All users of federal information systems must be exposed to awareness materials at least annually • Identify employees with significant information security responsibilities and provide role-specific training in accordance with NIST standards and guidance 12

OPM Also Says. . . • Train: – Executives – Program and functional managers – CIOs, IT security program managers, auditors, and other security oriented personnel (e. g. , system and network administrators, and system/ application security officers) – IT function management and operations personnel 13

SP 800 -16 Background • • Written by a FISSEA Workgroup Published in April 1998 Supersedes NIST SP 500 -172 (circa 1989) On-line at: – http: //csrc. nist. gov/publications/nistpubs/index. html – http: //csrc. nist. gov/ATE/index. html 14

Primary Authors • • Dee de Zafra – DHHS (Ret. ) Sadie Pitcher - Dept. of Commerce (Ret. ) John Tressler - Dept. of Education (? ) John Ippolito - Allied Technology 15

Significant Others • • K Rudolph - Native Intelligence Vic Maconachy - NSA Corey Schou - Idaho State University Roger Quane - NSA 16

Why Role-Based Training? • • • Current IT environment is more complex Roles, not titles, allow fine-tuning More than one role person possible Because FISMA hints at it Because OPM requires it More efficient than topic-based training 17

Questions? Comments? Time for a Break? 18

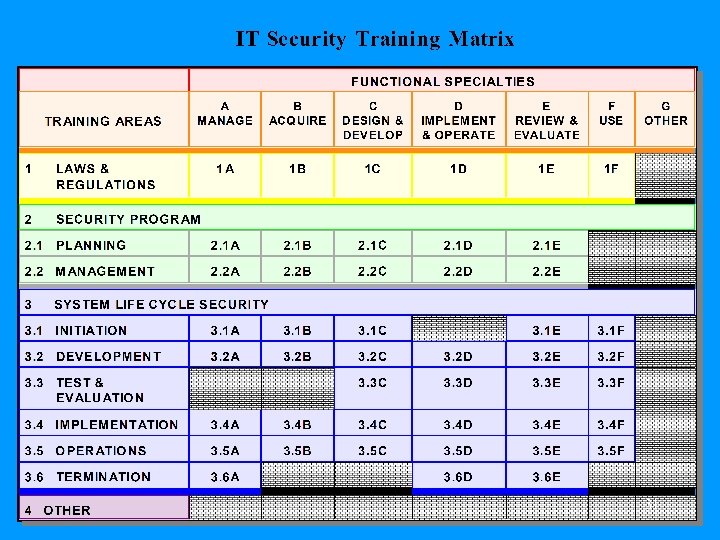
SP 800 -16 Building Blocks • • • The NIST Model IT Security Training Matrix 6 Functional Specialties 3 Fundamental Training Content Categories 26 Role-Based Job Functions 12 Body of Knowledge Topics & Concepts 19

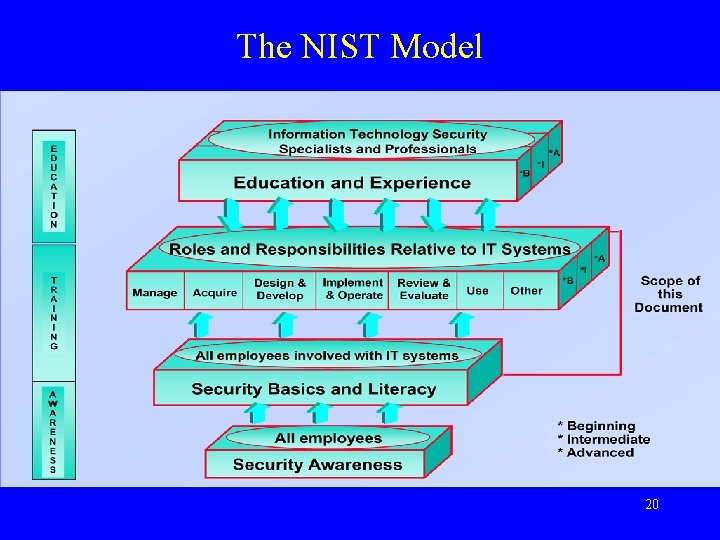
The NIST Model 20

“NIST Model” Highlights • Learning Continuum – Awareness – Training – Education • Basics and Literacy • Role-Based Training 21

Learning Continuum • Awareness – What: Focus attention on IT Security – Who: All employees • Training – What: Provide knowledge, skills, and abilities – Who: Depends on roles and responsibilities • Education – What: Provide long-term understanding – Who: IT Security professionals 22

Basics and Literacy • Transition from awareness to training • Provides foundation for training • Basics – Core set of IT Security terms & concepts – “The ABCs” - The IT Security alphabet • Literacy – Curriculum framework 23

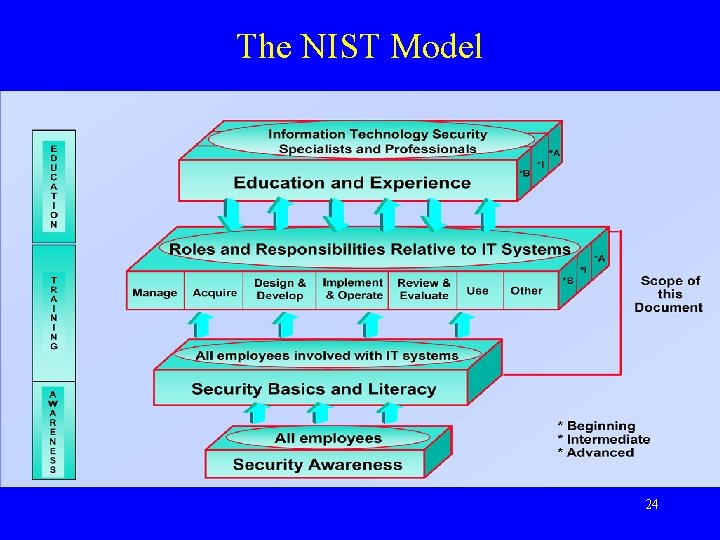
The NIST Model 24

25

Six Functional Specialties* • • Manage Acquire Design & Develop Implement & Operate Review & Evaluate Use *(Other. . . Expandable) 26

Three Fundamental Training Content Categories* • • Laws and Regulations The IT Security Program System Life Cycle Security *(Other - expandable) 27

Role-Based Training: 26 Job Functions (Roles) • • • Auditor, External Auditor, Internal Certification Reviewer Chief Information Officer (CIO) Contracting Officer’s Technical Representative (COTR) Data Center Manager Database Administrator Designated Approving Authority (DAA) Freedom of Information Act Official Senior IRM Official Information Resources Manager • • • • IT Security Program Officer/Manager Network Administrator Privacy Act Official Program Manager Programmer/Systems Analyst Records Management Official Source Selection Board Member System Administrator System Designer/Developer System Owner Systems Operations Personnel Technical Support Personnel Telecommunications Specialist User 28

IT Security Body of Knowledge Topics and Concepts • • Laws and Regulations IT Security Program System Environment System Interconnection Information Sharing Sensitivity Risk Management • Management Controls • Acquisition/ Development/ Installation/ Implementation Controls • Operational Controls • Awareness, Training, and Education Controls • Technical Controls 29

Sources of Topics and Concepts • • • OMB Circular A-130, Appendix III OMB Bulletin 90 -08 NIST SP 800 -12 (The NIST Handbook) NIST SP 800 -14 (GSSPs) Material developed during SP 800 -16 development 30

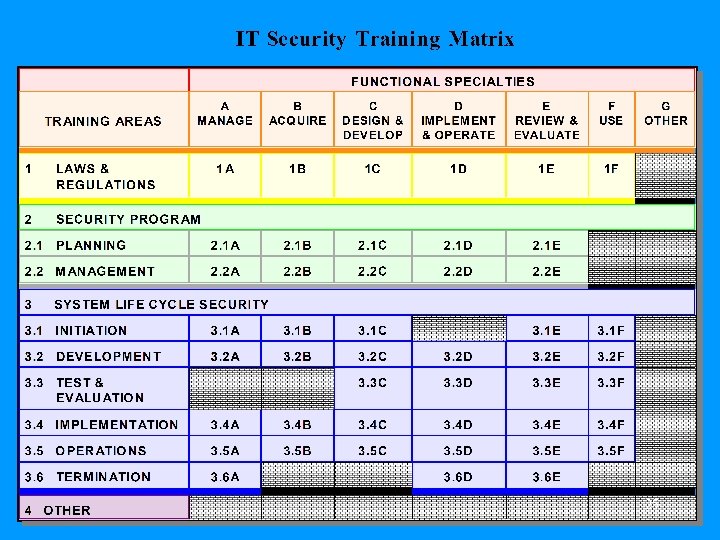
31

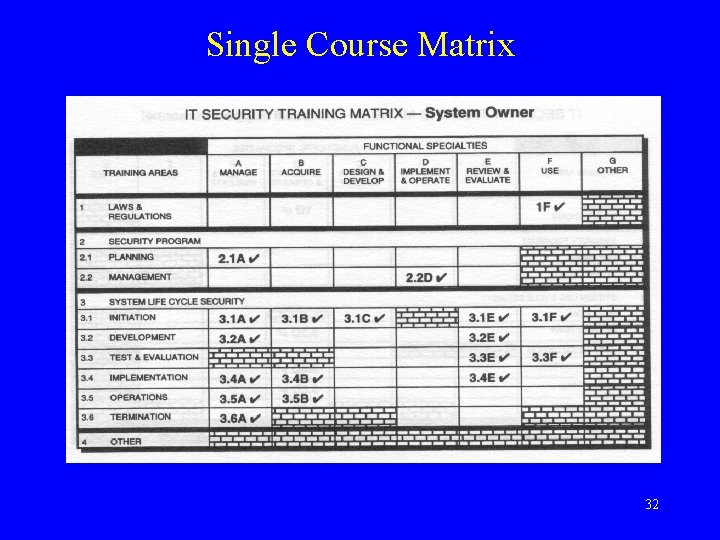
Single Course Matrix 32

NIST Model Wrap-up • Learning Continuum • Basics and Literacy • Role-Based Training – 6 functional specialties – 3 fundamental training content categories – 26 job functions or roles – 46 training matrix cells – 12 body of knowledge topics and concepts 33

From Model To Minutia Model Training Matrix Single Course Matrix Cells That Comprise A Course Body Of Knowledge Topics & Concepts Per Cell 34

How to Use SP 800 -16 • Select a Job Function (Role) • Identify All Cells that Make Up the Job Function [Appendix E] • Understand Definition, Behavioral Outcome, and Learning Objectives for Each Cell [Chapter 4] • Identify the Body of Knowledge Topics and Concepts that Make Up Each Cell [Chapter 4] • Populate Each Cell 35

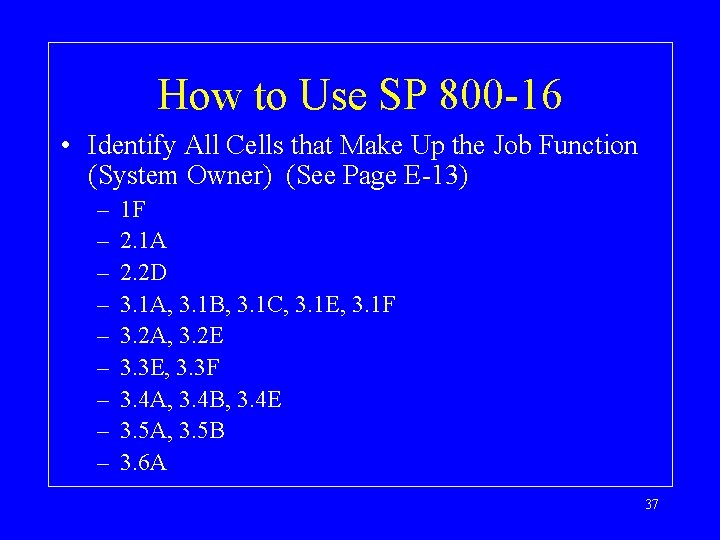
How to Use SP 800 -16 • Select a Job Function. . . System Owner (See Appendix E) 36

How to Use SP 800 -16 • Identify All Cells that Make Up the Job Function (System Owner) (See Page E-13) – – – – – 1 F 2. 1 A 2. 2 D 3. 1 A, 3. 1 B, 3. 1 C, 3. 1 E, 3. 1 F 3. 2 A, 3. 2 E 3. 3 E, 3. 3 F 3. 4 A, 3. 4 B, 3. 4 E 3. 5 A, 3. 5 B 3. 6 A 37

How to Use SP 800 -16 • Identify the Body of Knowledge Topics and Concepts that Make Up Each Cell - Start with Cell 1 F (See Pages 69 & 70) – #1 – Laws and Regulations – #8 – Management Controls 38

How to Use SP 800 -16 • Identify the Body of Knowledge Topics and Concepts that Make Up Each Cell - Cell 2. 1 A (See Pages 73 & 74) – All 12 Topics and Concepts Are Used 39

How to Use SP 800 -16 • Identify the Body of Knowledge Topics and Concepts that Make Up Each Cell - Cell 2. 2 D (See Pages 89 & 90) – All 12 Topics and Concepts Are Used 40

How to Use SP 800 -16 • Identify the Body of Knowledge Topics and Concepts that Make Up Each Cell - Cell 3. 1 A (See Pages 95 & 96) – #2 – IT Security Program – #5 – Information Sharing – #6 – Sensitivity – #8 – Management Controls – #9 – Acquisition/Development/Installation/ Implementation Controls 41

How to Use SP 800 -16 • Identify the Body of Knowledge Topics and Concepts that Make Up Each Cell • Do This for Each of the 18 Cells in “System Owner” Job Function (Role) • You Will Eventually Have. . . 42

How to Use SP 800 -16 43

How to Use SP 800 -16 • How to Populate Each Cell (Start With 1 F): – Read Definition – Read Behavioral Outcome – Select Knowledge Level (Beginning) – Read Applicable Learning Objective – Read Applicable Topics and Concepts (p. 70) – Select Body of Knowledge Details from Applicable Topics and Concepts in Exhibit 4 -4 (p. 48 & 51) 44

How to Use SP 800 -16 • How to Select Body of Knowledge Details from Applicable Topics and Concepts in Exhibit 4 -4 (Start With #1): – Read Topic and Concept (#1 = Laws and Regulations) – Select Those Details (and/or Add Your Own) That Allow Your Audience to Achieve the Behavioral Outcome Shown in Cell 1 F – May Not Use All Detailed Information Shown 45

Caveats (Yes, But. . . ) to 800 -16 • No Departments/Agencies Will Identify All 26 Roles as Having “Significant Responsibilities” (Wilson’s Bet) • Organization Culture Must be Considered • Hybrid Courses/Roles Possible • Add a Cell; Delete a Cell – it’s OK! • This Methodology is Flexible!! • Add Your Own Detailed Information to That Which is in Exhibit 4 -4 46

Questions? Confusions? Break, Then Exercise 47

Always Time for Exercise • Pick a Role (System Owner) • Identify All of the Cells (Appendix E) • List All Topics and Concepts Used in Each Cell (Chapter 4) • Select (or Add Your Own) Detailed Information for Each Topic and Concept Used in Each Cell (Exhibit 4 -4) [*We’ll Do This By Table or Group*] 48

Evaluating Training Effectiveness • Why? Training Must Be Meaningful? • “Meaningful” Requires Measurement • How and What Do We Measure? – Student Satisfaction (Level 1) – Learning (Teaching) Effectiveness (Level 2) – Performance Effectiveness (Level 3) – Training Program Effectiveness (Level 4) 49

Summary • We Discussed: – The NIST Special Publication (SP) 800 -16 Learning Continuum – Awareness Versus Training – Why Role-Based Training – SP 800 -16 Roles – Relationship Between Cells and Job Functions (Roles) – Relationship Between Topics & Concepts and Cells 50

Summary, Continued • We Did: – Select Detailed Information From Topics and Concepts to Match Each Cell • We Should Be Able to: – Draft an Outline or Complete Course Structure – Determine if a Training Course “Meets NIST SP 800 -16” 51

Questions? Comments? Please Complete Evaluation Form - Thank You Mark Wilson, CISSP Computer Security Division, ITL National Institute of Standards and Technology - January 19, 2005 mark. wilson@nist. gov (301) 975 -3870 (voice) (301) 975 -4007 (fax)