How Technology People and Processes Converged to Achieve




















- Slides: 26

How Technology, People, and Processes Converged to Achieve a 95 Percent Reduction in Security Incidents! Tammy L. Clark, Asst. Director-UCCS, Information Security William Monahan, Information Security Administrator Lead

A Little Background Info n n n Georgia State’s information security program launched in 2000 Currently, 3 dedicated staff members serve the campus community 6000 -8000 staff and faculty 20, 000+ students Decentralized information technology environment 2

In 2004, Our Campus Averaged 20 to 40 Security Incidents a Day… n n n 2 million attacks launched against our systems each week 95% or more of the successful ones targeted Win 2 k or XP workstations 5% aimed at servers and network equipment 580+ desktops ravaged by Sasser within a week’s time 250+ of these compromised by hackers within a day or two later 20 -40 successful malware invasions per day on university and residential systems combined 3

Most Common Threats n n n n Emailed worm attachments and URL’s that install spyware and Trojan Horses Exploited backdoors left behind by worms used to get “root” and install hacker utilities Cracking weak passwords to get root Using automated exploits such as “DCOM” to get root NT and unix rootkits IRC hackers turning systems into bots for use in DDOS attacks or as warez servers Spam propagation through various exploits that install SMTP engines on workstations and mail servers misconfigured as open mail relays 4

Georgia State’s Security Architecture n n n In addition to AV on the desktops and/or servers, robust gateway scanners… √ Control or restriction at the edge or on segments via a firewall √ Dynamic blocking at the edge via IPS…√ Centrally-maintained patch management √ IPS at the desktop, on servers, at the edge √ Ability to mandate use of “strong” passwords, through a combination of policy and technology √ VPN for remote access √ Encrypted data transmission √ Secure email and/or FTP Vulnerability assessment and risk analysis √ A SIM or central logging facility to gather disparate data gathered daily from firewalls, IDS, IPS, AV, etc. , with data correlation and reporting 24/7 monitoring and incident detection/response 5

Security Architecture Continued n n n Regulatory compliance in ensuring minimum levels of security on networked devices processing sensitive info √ Developing a security awareness course (we used Web. CT Vista) that can be distributed to faculty, staff, and students √ Establishment of secure, trusted zones that are separated from the rest of the network √ Access/authentication requirements on every wired port (except public access stations) and wireless areas √ Identity management system Self defending networks 6

Our Information Security Roadmap n n n n Information Security Plan based on ISO 17799 Policy Committees and Taskforces Security Solutions Security Operations Security Awareness Defense In depth through layering in new solutions 7

Campus Security Plan n n Organized and aligned with ISO 17799 domains (12) Identifies areas that require policy, guidelines, standards, and solutions Takes into account the academic and information technology strategic objectives Provides a 3 year roadmap after which we will seek accreditation 8

Policy n In 2001, GSU president’s Administrative Counsel approved three important policies that provided the initial impetus allowing us to improve the security posture at our university n n n Mandatory AV on all university-owned computers Mandatory server registration and adherence with minimum standards for security configurations Mandatory requirement to adhere to specified security standards on all systems processing, storing, and transmitting sensitive information 9

Committees and Taskforces n n In 2001, the creation of the Information Technology Systems and Security committee, staffed by college technology managers, faculty, legal affairs, campus police, human resources, etc. , brought the GSU community together for the purpose of improving computer security, developing policies, standards, evaluating and recommending solutions From this committee, smaller working groups were developed to create new policies, pilot security tools, standardize security configurations for workstations and servers, and create the university’s CSIRT policy, guidelines and formal incident response team 10

Security Solutions n n n While the previous measures discussed have made a positive impact, the university still suffered from spikes in worm and hacking activity that resulted in many systems being reinstalled and lost worker productivity from Fall 2000 through Spring 2004 The IDS solution introduced in 2000 allowed us to quickly detect and respond to these attacks but didn’t assist in reducing them Fall 2004, we noticed that incidents had markedly dropped off, allowing us to begin to take a proactive approach rather than a reactive one While we used to experience between 20 -40 incidents (worm infections, copyright violations and compromises) per day on our network we now find that we only have on average, zero to two per day at this point in time and very infrequent spikes in activity We attribute this incident reduction to the synergy of people, processes and new technology solutions we implemented 11

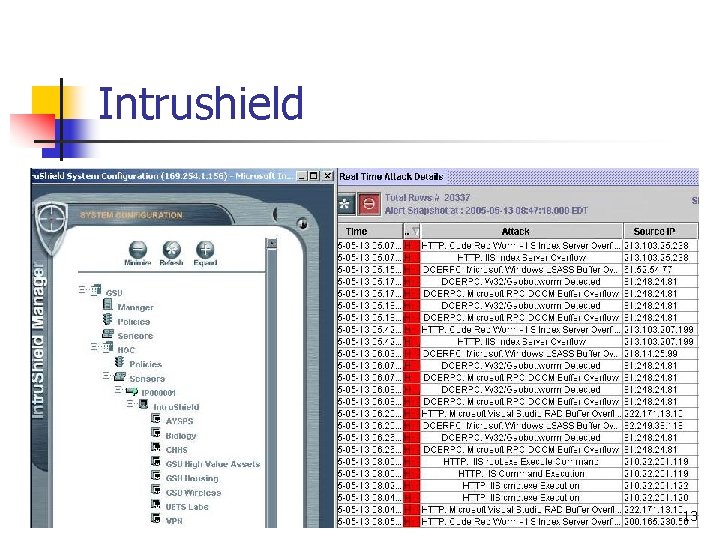
IPS at The Edge, Anyone? n n We evaluated Mc. Afee’s Intrushield 4000 appliance and also did some R&D with Tippingpoint and ISS Proventia’ TECHNOLOGY: We selected Intrushield as it allows us to create thousands of virtual ‘child’ domains with just one appliance that can apply very granular, customized policies to protect networked devices. Unlike our ISS Realsecure IDS, which we still maintain due to auditing capabilities that allow us to easily detect IRC bots and compromised systems, the Intrushield IPS allows us to dynamically block attacks in realtime, 24/7 PROCESS: We maintain an overall GSU policy that is applied to networked devices not housed under specific child domains. We also shield a group of high risk devices with a very restrictive policy. We create child domains for various colleges and departments and allow them to specify additional things they want to restrict via their departmental policies, such as P 2 P applications PEOPLE: We provide training to campus systems administrators and allow them to obtain a child domain, maintain their own policies and gain access to the management console to view all activity on just their specific areas 12

Intrushield 13

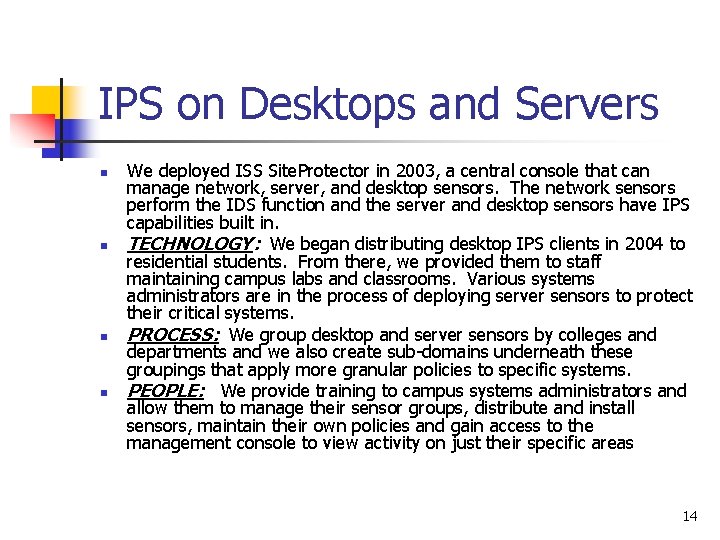
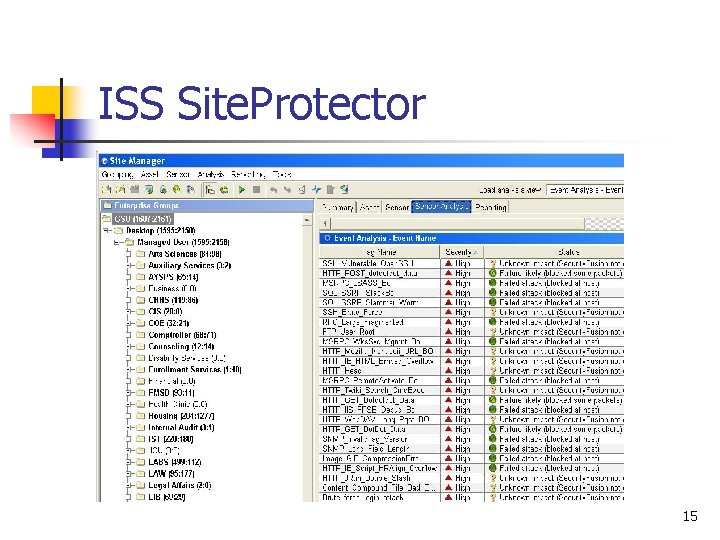
IPS on Desktops and Servers n n We deployed ISS Site. Protector in 2003, a central console that can manage network, server, and desktop sensors. The network sensors perform the IDS function and the server and desktop sensors have IPS capabilities built in. TECHNOLOGY: We began distributing desktop IPS clients in 2004 to residential students. From there, we provided them to staff maintaining campus labs and classrooms. Various systems administrators are in the process of deploying server sensors to protect their critical systems. PROCESS: We group desktop and server sensors by colleges and departments and we also create sub-domains underneath these groupings that apply more granular policies to specific systems. PEOPLE: We provide training to campus systems administrators and allow them to manage their sensor groups, distribute and install sensors, maintain their own policies and gain access to the management console to view activity on just their specific areas 14

ISS Site. Protector 15

Managed Antivirus n n n TECHNOLOGY: We distribute Symantec antivirus to all Windows and Mac systems on campus and allow users to install it on remote systems as well PROCESS: We provide a managed client that allows us to “push” AV updates as they come out and group the clients by the college or department they fall into. We also provide an unmanaged client for our remote users PEOPLE: We provide targeted information about worms and viruses to campus administrators and plan to allow them access to their own groups on our management console once Symantec releases the ability to distribute management of AV clients 16

Symantec Antivirus 17

GSU’s Secure Computing Initiative n n In response to regulatory requirements to protect customer information, we established a program that mandates (yes, you heard this right!) the use of IPS, strong passwords, secure device configurations, and an electronic security awareness course TECHNOLOGY: ISS Proventia’ desktop IPS and Symantec’s antivirus client. We also ask systems admins to either obtain ISS’ server sensor or allow us to place their device behind the “shield” with a restrictive policy PROCESS: We require college/department information technology representatives to provide us with an inventory of systems and a survey questionnaire specifying what steps they are taking in the areas of backups, disaster recovery, etc. We provide them with training on the ISS Site. Protector management system, checklists that specify configuration requirements on XP and 2000 workstations (which are prevalent on our campus), and conduct a risk analysis of their area PEOPLE: College/department technology representatives distribute and install the IPS and antivirus software, ensure that users’ systems are configured via our checklist requirements, and we contact users to take the security awareness course 18

HIPAA Compliance Matrix 19

Risk Analyses and Security Reviews n n As colleges and dept’s at GSU acquire new technology from vendors to assist in their academic or business endeavors, we get involved in assessing the potential risk that new devices, software, etc. , can introduce TECHNOLOGY: We run vulnerability scans on these vendor-supplied systems PROCESS: We also conduct risk analyses to determine the use of encryption in data transmission, examine security configurations, determine whether sensitive data is involved PEOPLE: We work with vendors to resolve problems prior to systems going into production; we also place high risk systems behind the “shield” 20

Residential Segments of the Network n n This past year we implemented Perfigo’s Clean. Machines solution and it proved very successful in ensuring that students maintained reasonable levels of security on their systems. TECHNOLOGY: We provided residents with the Clean. Machines agent, ISS desktop IPS, and the Symantec antivirus client on a CD PROCESS: We configured Clean. Machines to check for the presence of the IPS, AV, and completion of Windows updates. We provided training to housing staff members and student assistants and a ‘clearinghouse’ website to go to for info PEOPLE: Workstation support techs in our department assisted residents who could not successfully navigate Clean. Machines due to worm infested systems and network techs helped residents with connectivity issues caused by bad “nic” cards or cables. 21

Security Operations n n We have several security monitoring systems that provide critical information to us about attacks and intrusions 24/7 TECHNOLOGY: We establish automated alerting and reporting mechanisms within Intrushield and ISS Siteprotector to provide targeted information PROCESS: We are offering training to network operations and helpdesk technicians to allow them to field alerts 24/7 and create Remedy helpdesk tickets, make notifications, and contact us to analyze information that comes in about potential attacks and incidents PEOPLE: We have an experienced security operations/incident handler in our department who collects data and manages incidents during business hours. We also have a CSIRT on campus and a policy that we are allowed to decide to disrupt network services to any device that represents a threat to the university if necessary without prior notification 22

Security Awareness n n n TECHNOLOGY: We provide security awareness presentations on demand are in the process of distributing a Web. CT Vista security awareness course to campus users PROCESS: We are working to have this electronic course distributed to all incoming freshman students as part of their “freshman communities” curriculum. We require everyone on campus processing sensitive information to take the course and achieve a passing score on the test that accompanies it PEOPLE: We are working with human resources staff members to include the course in their new employee orientations 23

Defense In Depth n n n The challenge we all face in seeking to protect customer information and university technical resources is achieving a delicate balance between applying controls and utilizing these resources at optimum levels of efficiency and effectiveness From 2000 to the third quarter of 2004, we layered existing technological solutions, devised processes that often required the active participation of the campus community and we found that we could not stem the tide of blended threats that managed to evade our controls The emergence of IPS at the edge, on servers and desktops, along with regulatory requirements that mandate minimum levels of security have evolved our efforts to allow us to be more proactive, to manage security efforts “end to end” on the network, rather than exist in a purely reactive mode. These controls are transparent for the most part to our campus community, as we do not deploy some of the more intrusive measures these solutions are capable of. . 24

Defense in Depth Cont. n n We constantly devise policies and processes that can be instituted to better protect network devices, more often than not, without user intervention. We focus on educating staff, faculty, and users about policies, mandated requirements, and about the threats and vulnerabilities they will encounter when they utilize systems connected to the internet… We’ve achieved a measure of success at this point, but we continue to examine new technologies that surface such as ‘self defending networks’ and complex ones such as ‘IDMS’ to allow us to mitigate the effects of mobile users bringing infected systems to campus and access/authentication issues 25

Questions? Copyright Tammy Clark, May 2005. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. 26