How ransomware works Mark Loman Director Engineering September

How ransomware works Mark Loman Director, Engineering September, 2016 James Burchell Senior Sales Engineer
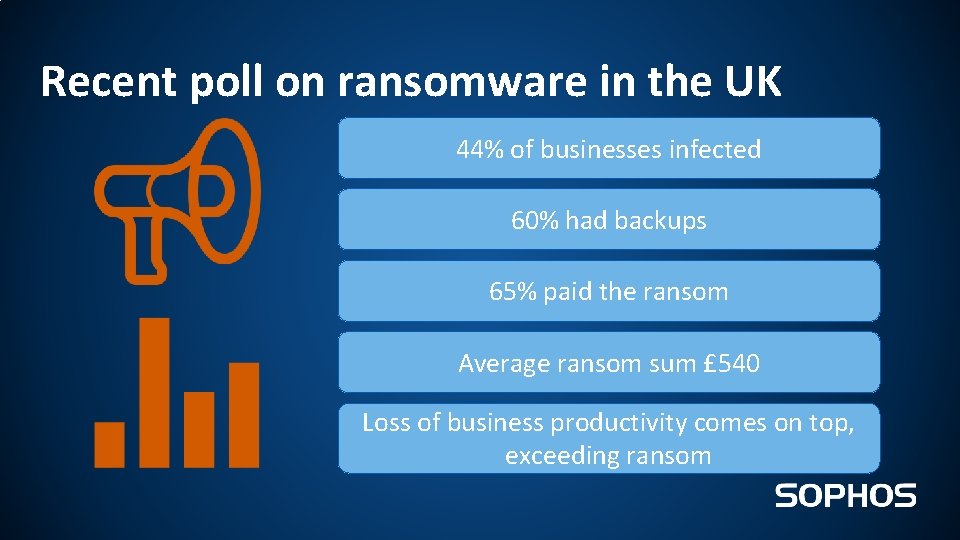
Recent poll on ransomware in the UK 44% of businesses infected 60% had backups 65% paid the ransom Average ransom sum £ 540 Loss of business productivity comes on top, exceeding ransom
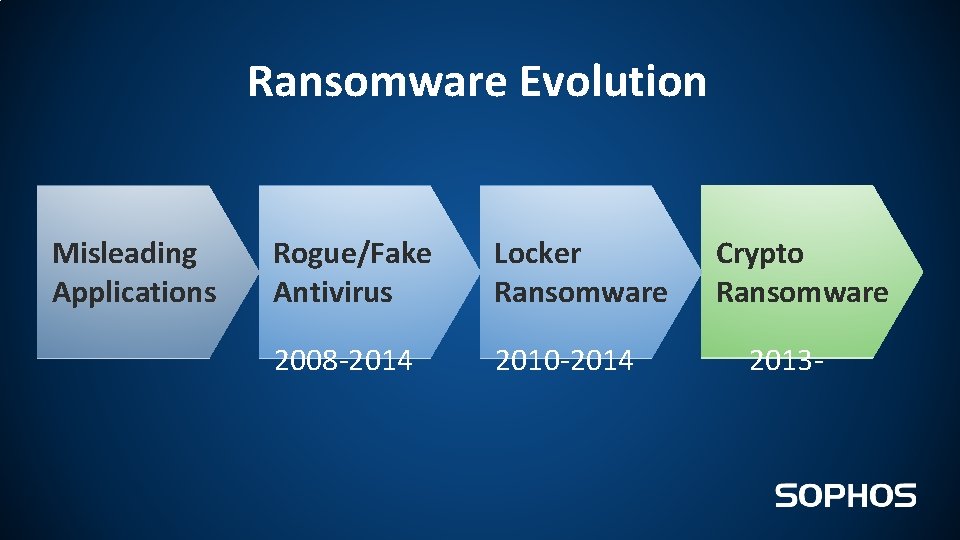
Ransomware Evolution Misleading Applications Rogue/Fake Antivirus Locker Ransomware 2008 -2014 2010 -2014 Crypto Ransomware 2013 -
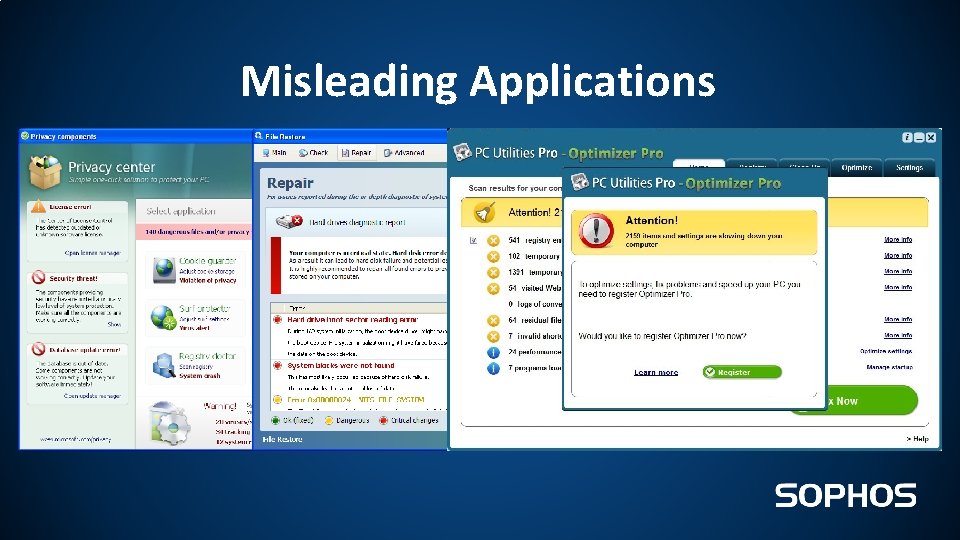
Misleading Applications

Rogue/Fake Antivirus

Rogue/Fake Antivirus
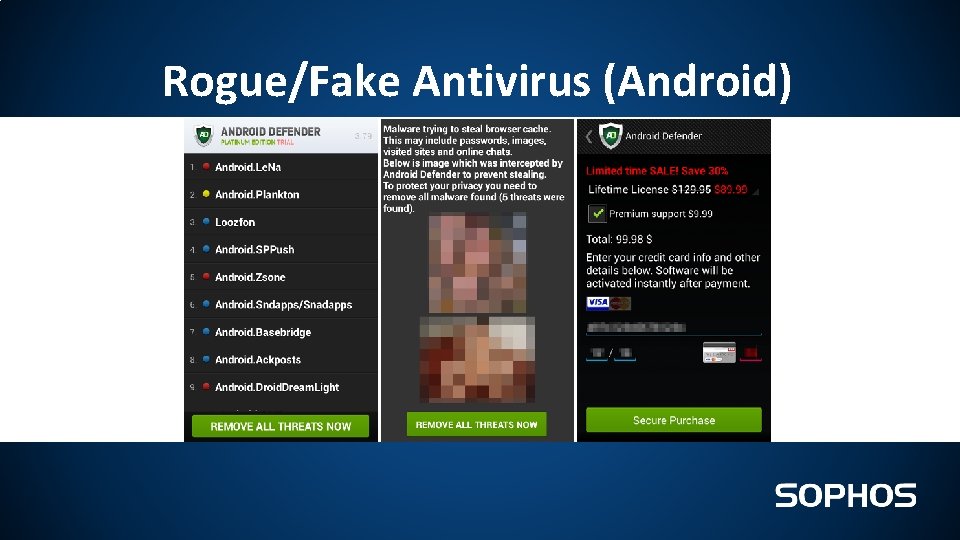
Rogue/Fake Antivirus (Android)
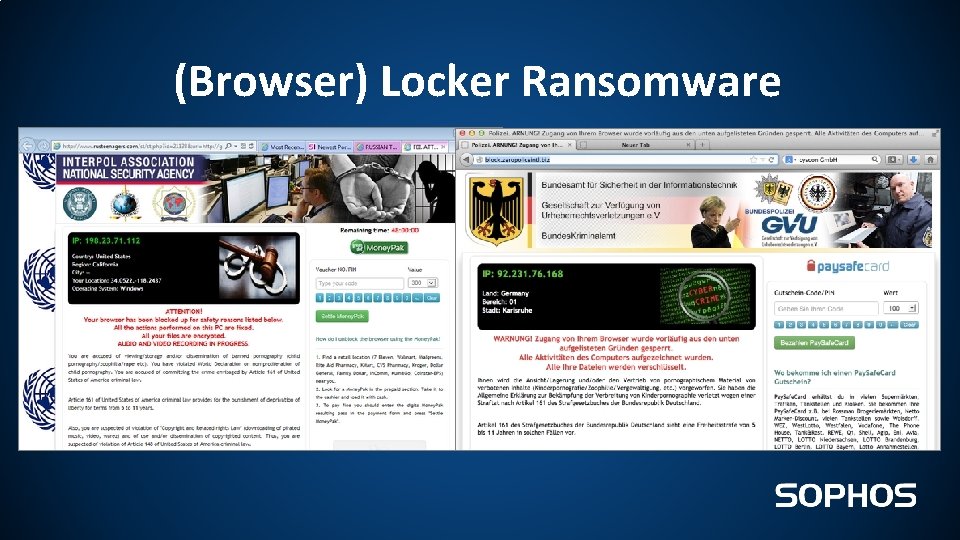
(Browser) Locker Ransomware
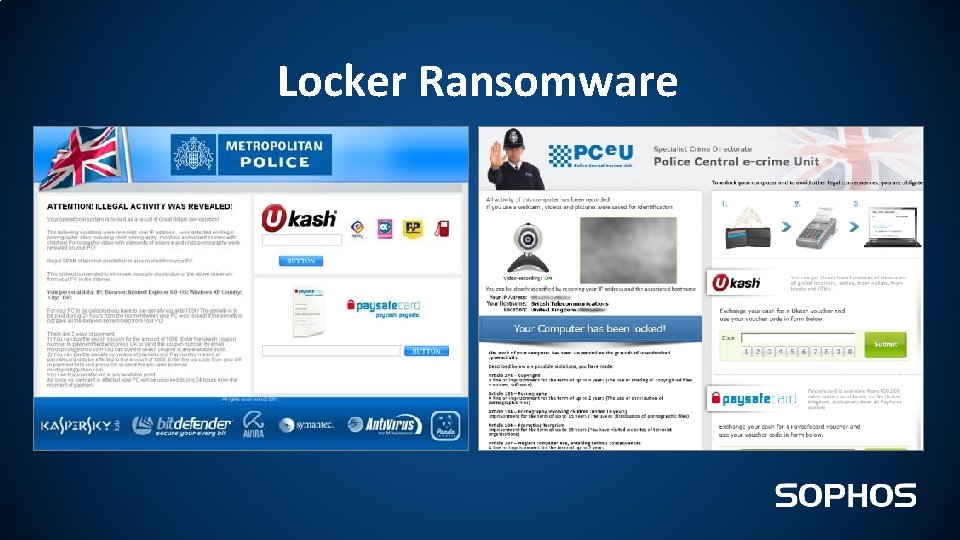
Locker Ransomware
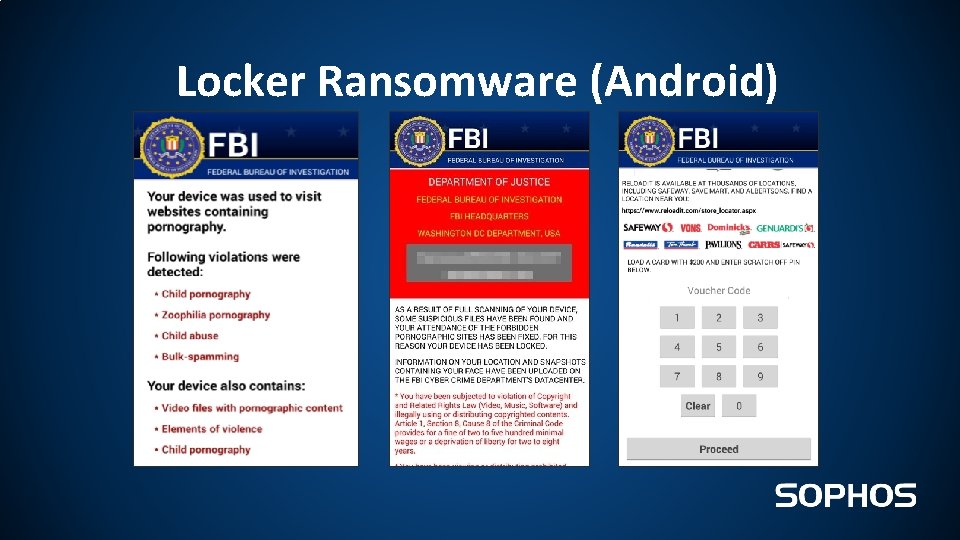
Locker Ransomware (Android)
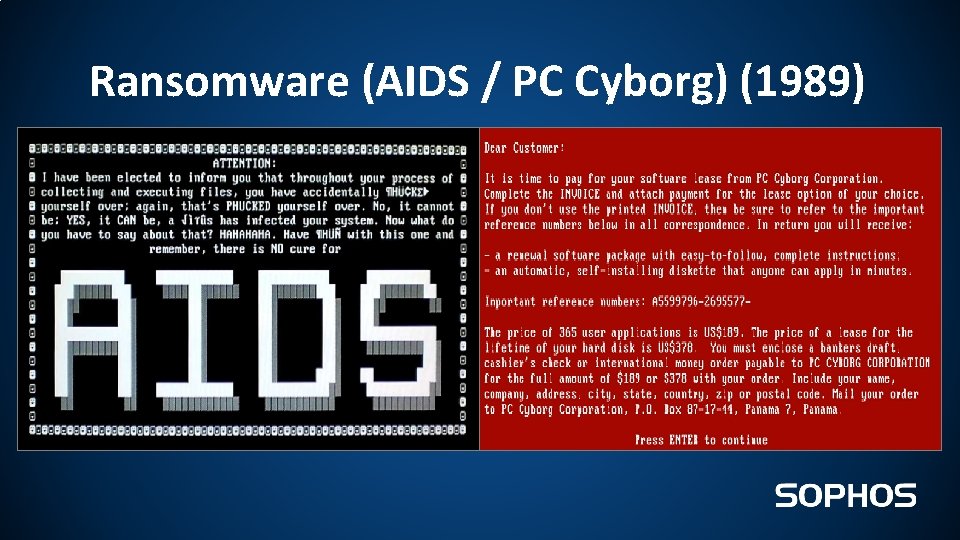
Ransomware (AIDS / PC Cyborg) (1989)
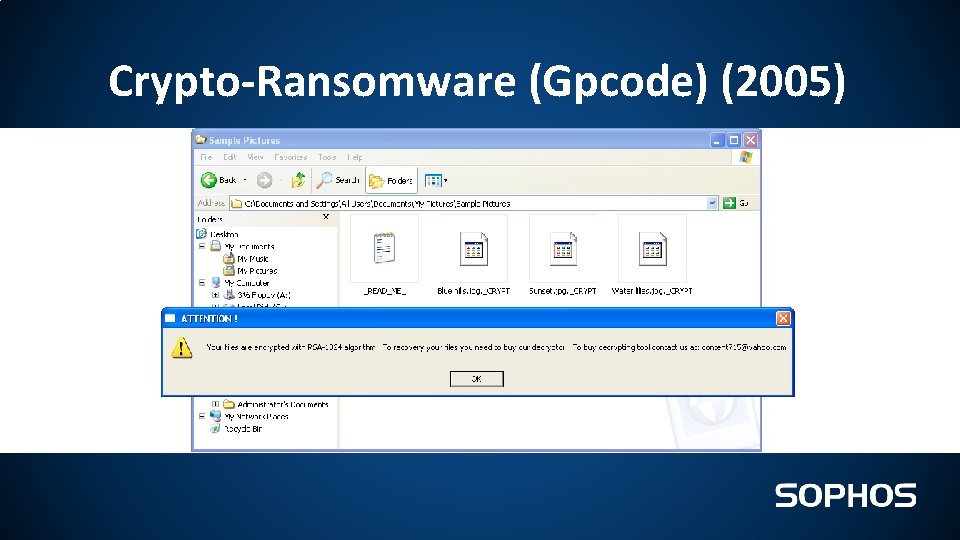
Crypto-Ransomware (Gpcode) (2005)
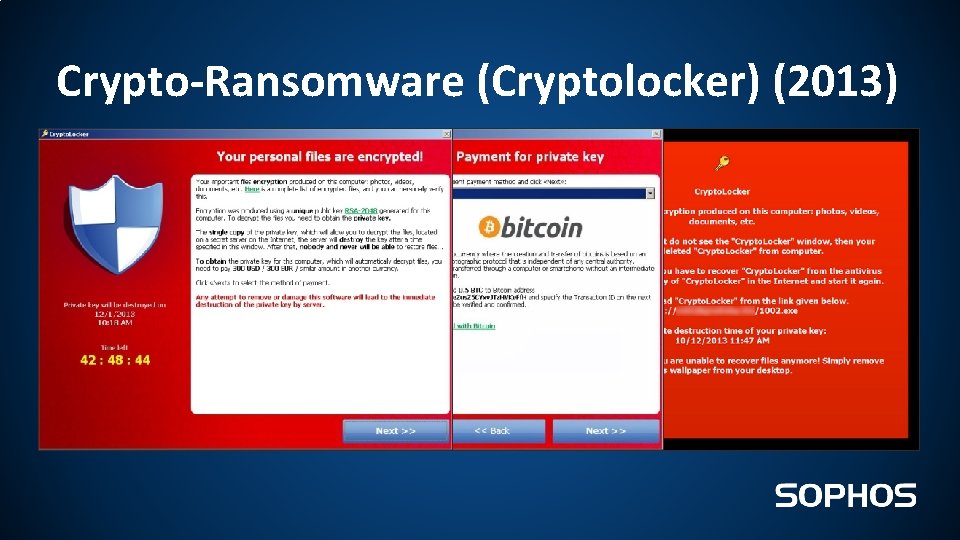
Crypto-Ransomware (Cryptolocker) (2013)
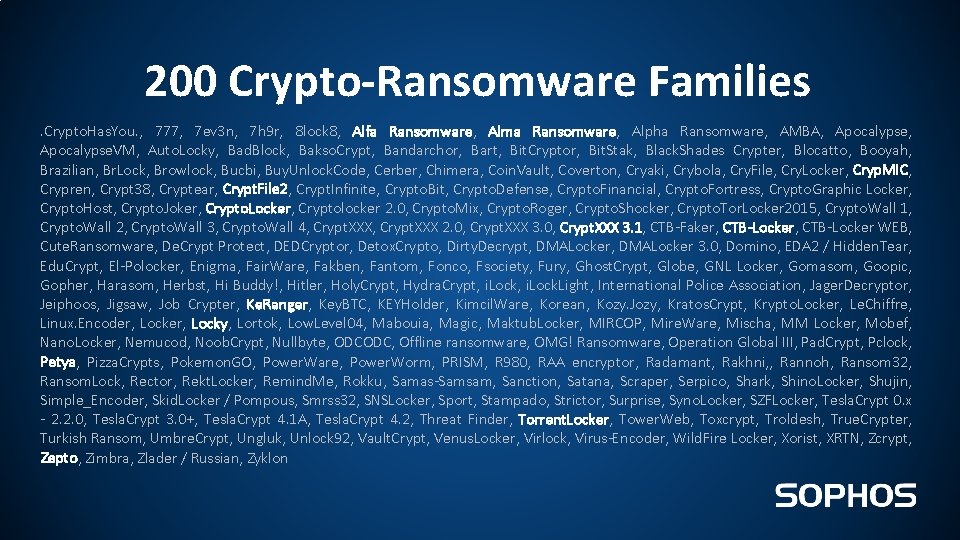
200 Crypto-Ransomware Families. Crypto. Has. You. , 777, 7 ev 3 n, 7 h 9 r, 8 lock 8, Alfa Ransomware, Alma Ransomware, Alpha Ransomware, AMBA, Apocalypse. VM, Auto. Locky, Bad. Block, Bakso. Crypt, Bandarchor, Bart, Bit. Cryptor, Bit. Stak, Black. Shades Crypter, Blocatto, Booyah, Brazilian, Br. Lock, Browlock, Bucbi, Buy. Unlock. Code, Cerber, Chimera, Coin. Vault, Coverton, Cryaki, Crybola, Cry. File, Cry. Locker, Cryp. MIC, Crypren, Crypt 38, Cryptear, Crypt. File 2, Crypt. Infinite, Crypto. Bit, Crypto. Defense, Crypto. Financial, Crypto. Fortress, Crypto. Graphic Locker, Crypto. Host, Crypto. Joker, Crypto. Locker, Cryptolocker 2. 0, Crypto. Mix, Crypto. Roger, Crypto. Shocker, Crypto. Tor. Locker 2015, Crypto. Wall 1, Crypto. Wall 2, Crypto. Wall 3, Crypto. Wall 4, Crypt. XXX 2. 0, Crypt. XXX 3. 1, CTB-Faker, CTB-Locker WEB, Cute. Ransomware, De. Crypt Protect, DEDCryptor, Detox. Crypto, Dirty. Decrypt, DMALocker 3. 0, Domino, EDA 2 / Hidden. Tear, Edu. Crypt, El-Polocker, Enigma, Fair. Ware, Fakben, Fantom, Fonco, Fsociety, Fury, Ghost. Crypt, Globe, GNL Locker, Gomasom, Goopic, Gopher, Harasom, Herbst, Hi Buddy!, Hitler, Holy. Crypt, Hydra. Crypt, i. Lock. Light, International Police Association, Jager. Decryptor, Jeiphoos, Jigsaw, Job Crypter, Ke. Ranger, Key. BTC, KEYHolder, Kimcil. Ware, Korean, Kozy. Jozy, Kratos. Crypt, Krypto. Locker, Le. Chiffre, Linux. Encoder, Locky, Lortok, Low. Level 04, Mabouia, Magic, Maktub. Locker, MIRCOP, Mire. Ware, Mischa, MM Locker, Mobef, Nano. Locker, Nemucod, Noob. Crypt, Nullbyte, ODCODC, Offline ransomware, OMG! Ransomware, Operation Global III, Pad. Crypt, Pclock, Petya, Pizza. Crypts, Pokemon. GO, Power. Ware, Power. Worm, PRISM, R 980, RAA encryptor, Radamant, Rakhni, , Rannoh, Ransom 32, Ransom. Lock, Rector, Rekt. Locker, Remind. Me, Rokku, Samas-Samsam, Sanction, Satana, Scraper, Serpico, Shark, Shino. Locker, Shujin, Simple_Encoder, Skid. Locker / Pompous, Smrss 32, SNSLocker, Sport, Stampado, Strictor, Surprise, Syno. Locker, SZFLocker, Tesla. Crypt 0. x - 2. 2. 0, Tesla. Crypt 3. 0+, Tesla. Crypt 4. 1 A, Tesla. Crypt 4. 2, Threat Finder, Torrent. Locker, Tower. Web, Toxcrypt, Troldesh, True. Crypter, Turkish Ransom, Umbre. Crypt, Ungluk, Unlock 92, Vault. Crypt, Venus. Locker, Virlock, Virus-Encoder, Wild. Fire Locker, Xorist, XRTN, Zcrypt, Zepto, Zimbra, Zlader / Russian, Zyklon
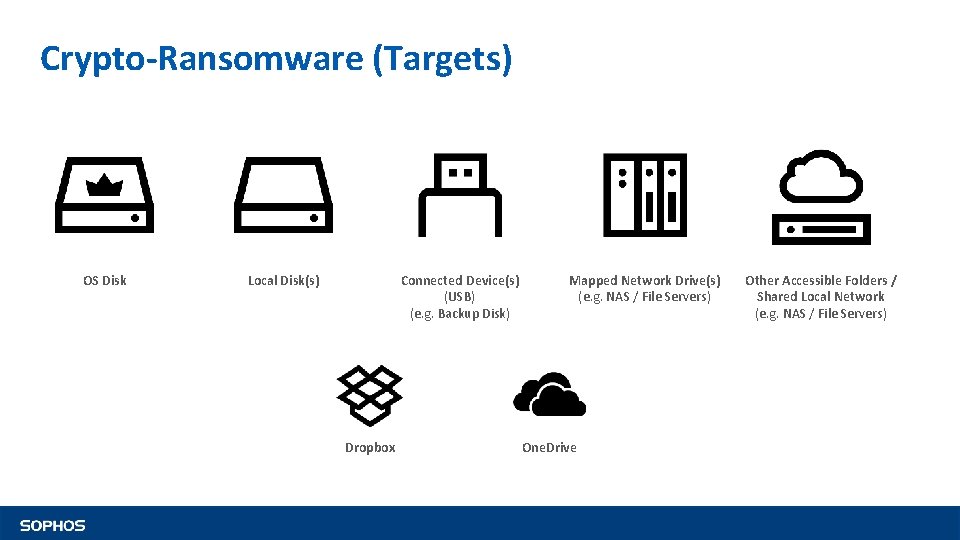
Crypto-Ransomware (Targets) OS Disk Local Disk(s) Connected Device(s) (USB) (e. g. Backup Disk) Dropbox Mapped Network Drive(s) (e. g. NAS / File Servers) One. Drive Other Accessible Folders / Shared Local Network (e. g. NAS / File Servers)
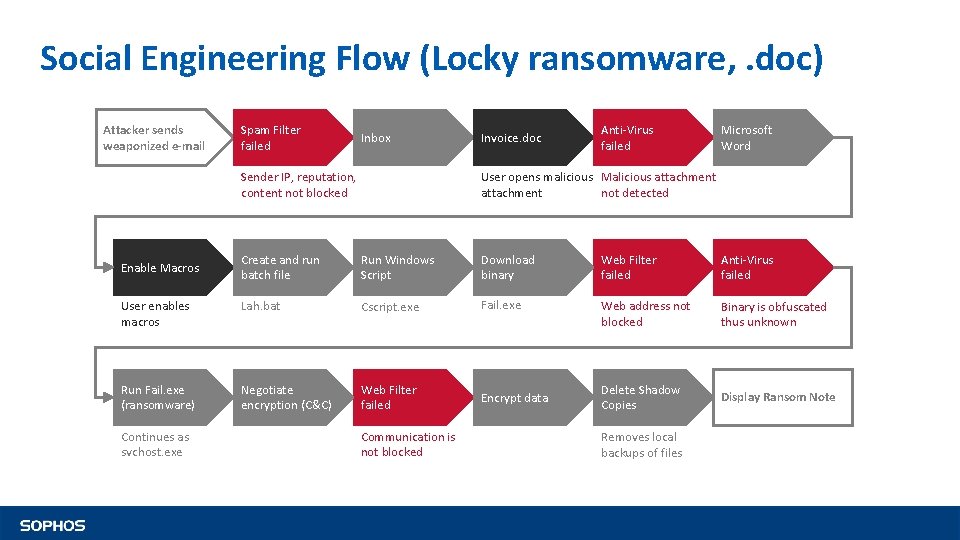
Social Engineering Flow (Locky ransomware, . doc) Attacker sends weaponized e-mail Spam Filter failed Inbox Sender IP, reputation, content not blocked Invoice. doc Anti-Virus failed Microsoft Word User opens malicious Malicious attachment not detected Create and run batch file Run Windows Script Download binary Web Filter failed Anti-Virus failed User enables macros Lah. bat Cscript. exe Fail. exe Web address not blocked Binary is obfuscated thus unknown Run Fail. exe (ransomware) Negotiate encryption (C&C) Web Filter failed Encrypt data Delete Shadow Copies Display Ransom Note Enable Macros Continues as svchost. exe Communication is not blocked Removes local backups of files
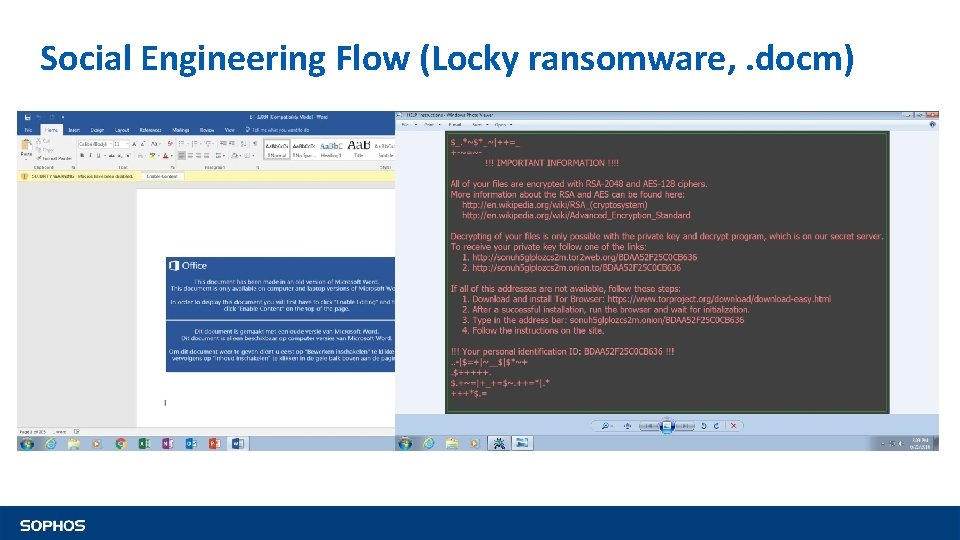
Social Engineering Flow (Locky ransomware, . docm)

Security Overview ”The State of the Nation” Today’s approach to IT Security is Falling Behind.

“Two things are infinite: The universe and human stupidity, and I’m not so sure about the former. ” - Albert Einstein
What is social engineering?
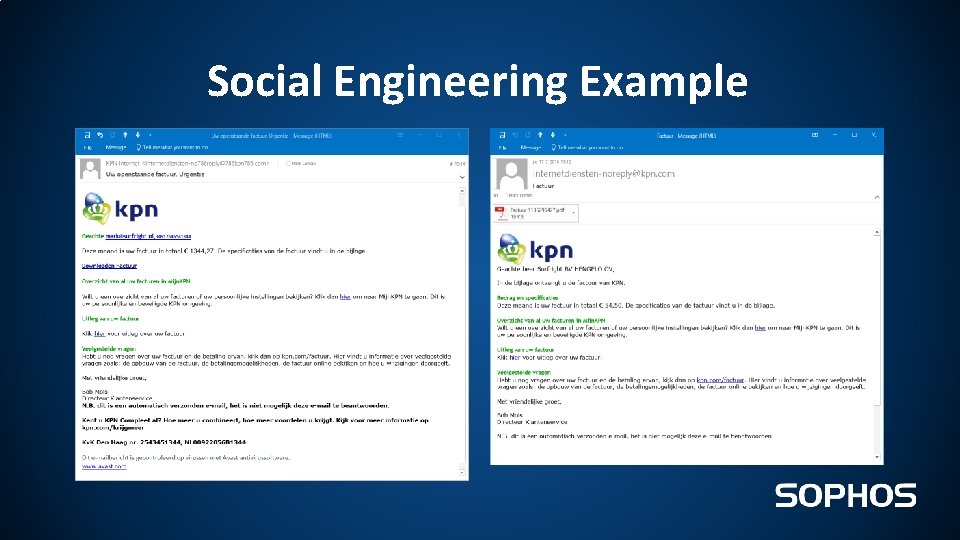
Social Engineering Example
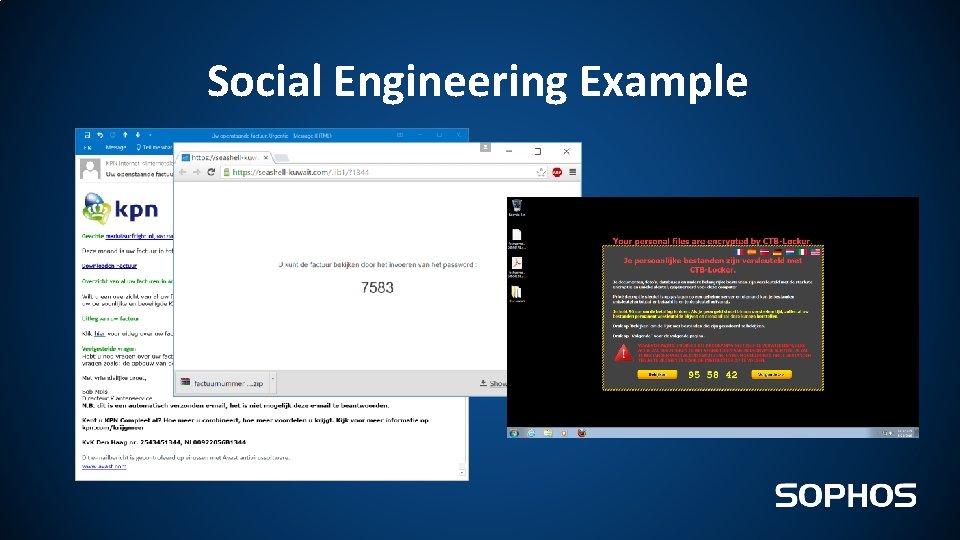
Social Engineering Example
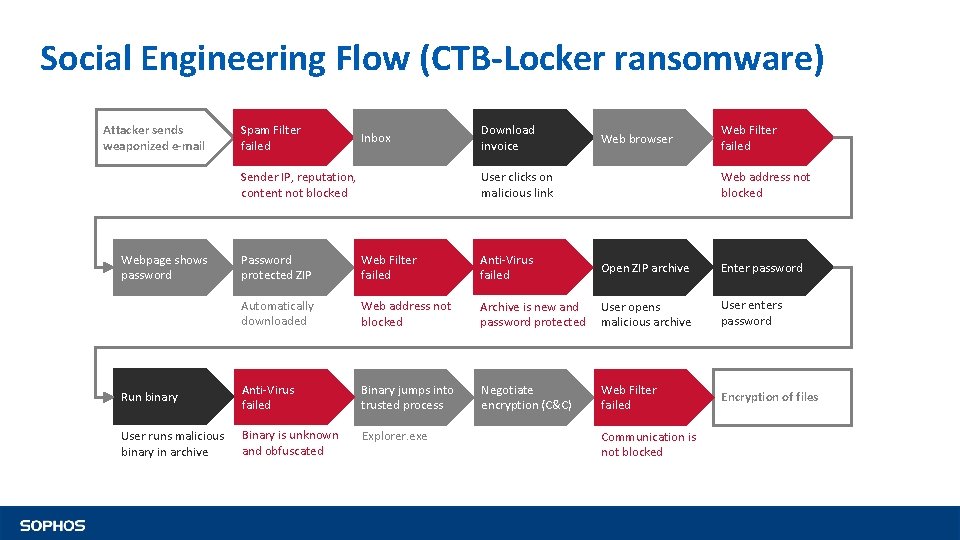
Social Engineering Flow (CTB-Locker ransomware) Attacker sends weaponized e-mail Spam Filter failed Inbox Sender IP, reputation, content not blocked Download invoice Web browser User clicks on malicious link Web Filter failed Web address not blocked Password protected ZIP Web Filter failed Anti-Virus failed Open ZIP archive Enter password Automatically downloaded Web address not blocked Archive is new and password protected User opens malicious archive User enters password Run binary Anti-Virus failed Binary jumps into trusted process Negotiate encryption (C&C) Web Filter failed Encryption of files User runs malicious binary in archive Binary is unknown and obfuscated Explorer. exe Webpage shows password Communication is not blocked

Comparison: Spam vs Exploit Kits Why email?
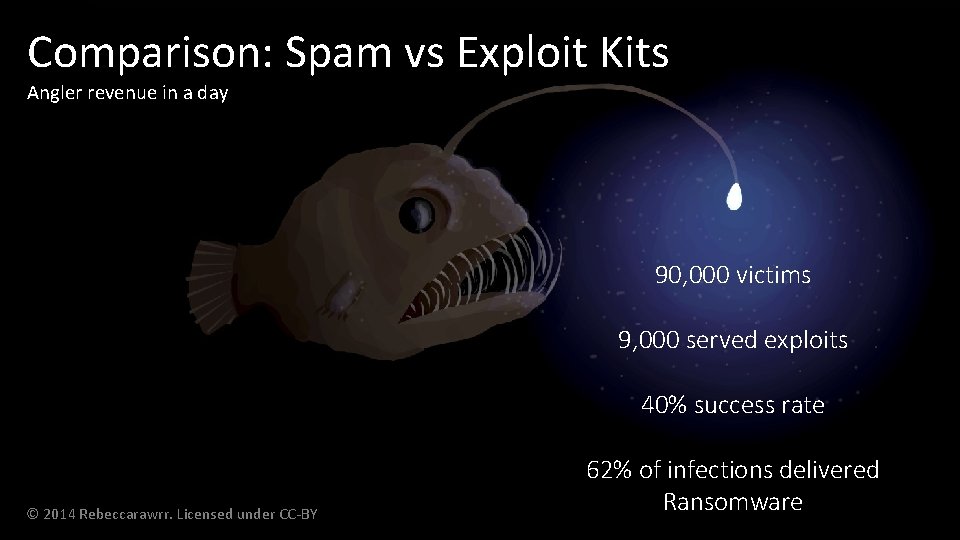
Comparison: Spam vs Exploit Kits Angler revenue in a day 90, 000 victims 9, 000 served exploits 40% success rate © 2014 Rebeccarawrr. Licensed under CC-BY 62% of infections delivered Ransomware
Understanding vulnerabilities Flaws Features User error © The Preiser Project, Licensed under CC-BY

DEMO
New tricks • Use of other accepted file extensions (e. g. . WSF, . WSH, . HTA, . PUB files) o Bypasses filters that proactively block known dangerous (ZIP) attachments (containing e. g. . EXE, . PDF. EXE, . JS, . DOCM as extension) • Use of a. DLL file (payload) instead of an. EXE (e. g. Locky/Zepto) o o In-memory attack; exploit attack delivers no files on the disk Bypasses sandbox, signature and ‘math-based, next-gen’ products • Use of other active content in weaponized documents (no macros) o e. g. RAA Ransomware • Use of only trusted binaries, part of the OS (no new code on machine) o Bypasses application whitelisting, signature & ‘math-based, next-gen’ products • Manipulate timestamp, create extension-less copy, encrypt copy and delete original o Cripple / shake off behavior-based monitoring • Multi-language support by attackers, to help victims pay the ransom o Including chat support
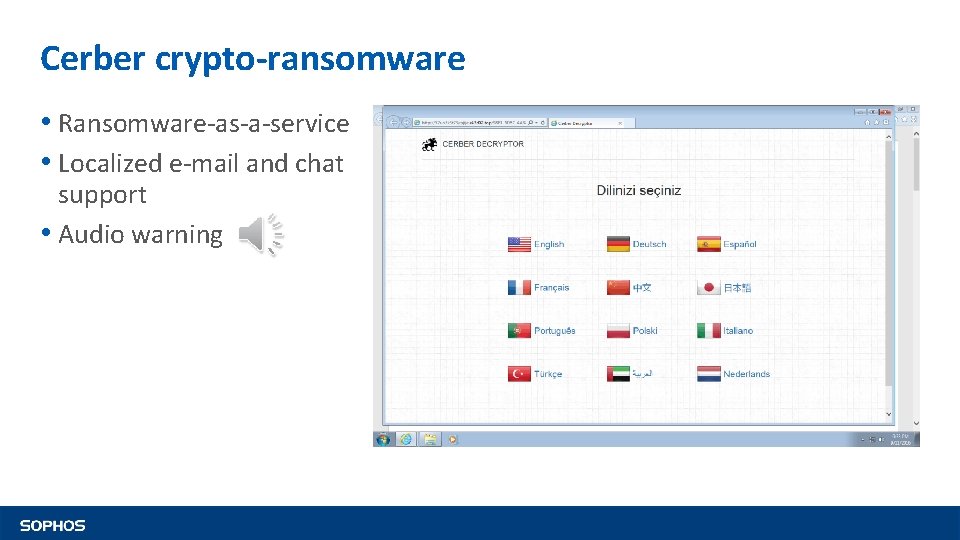
Cerber crypto-ransomware • Ransomware-as-a-service • Localized e-mail and chat support • Audio warning
Synchronized Security Enhancing layered security As a minimum you should: • Deploy antivirus protection • Block spam • Use a sandboxing solution • Block risky file extensions (javascript, vbscript, chm etc…) • Password protect archive files • Use URL filtering (block access to C&C servers) • Use HTTPS filtering • Use HIPS (host intrusion prevention service) & other signature-less technologies • Activate your client firewalls • Use a whitelisting solution

Reducing the threat ”Additional Steps” Education Encrypt Company Data Use Security Analysis Tools

32
- Slides: 32