How Attacks Are Perpetrated Detected and Prevented Overview








- Slides: 46

How Attacks Are Perpetrated, Detected and Prevented Overview

Agenda • How Attackers Attack – Different Types of Attacks • What Detection Mechanisms Are Available – What Kinds of Attacks Does Each One Detect • Traditional Security Products – The Intended Roles and Limitations of These Products • What IS Prevention – What Leaves You Vulnerable and What Works • Introducing a New Category-Intrusion Detection and Prevention 2 Net. Screen Confidential

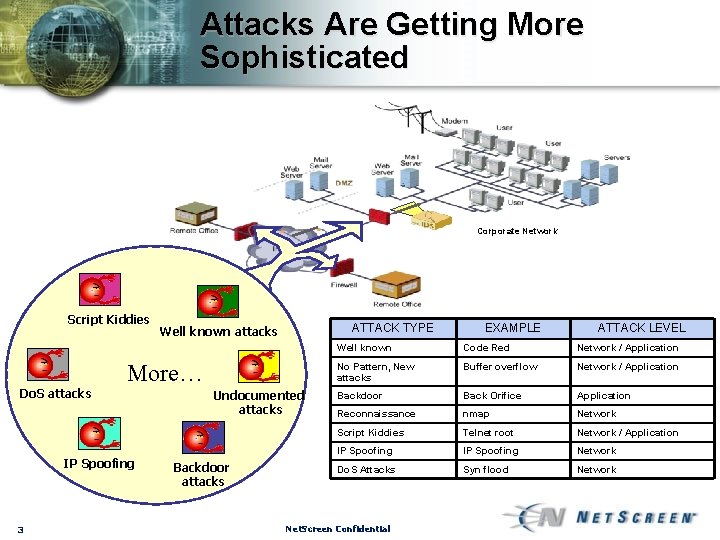
Attacks Are Getting More Sophisticated Corporate Network Script Kiddies ATTACK TYPE Well known attacks More… Do. S attacks IP Spoofing 3 Undocumented attacks Backdoor attacks EXAMPLE ATTACK LEVEL Well known Code Red Network / Application No Pattern, New attacks Buffer overflow Network / Application Backdoor Back Orifice Application Reconnaissance nmap Network Script Kiddies Telnet root Network / Application IP Spoofing Network Do. S Attacks Syn flood Network Net. Screen Confidential

How do Attackers Attack? • Attacks on your network are inevitable, so it is important to arm yourself with the knowledge of what you are up against. . . • There are two ways to gain access: – Vulnerability Exploits – Social Engineering • Vulnerabilities can be further broken into: – Software bugs – Configuration errors – Implementation mistakes 4 Net. Screen Confidential

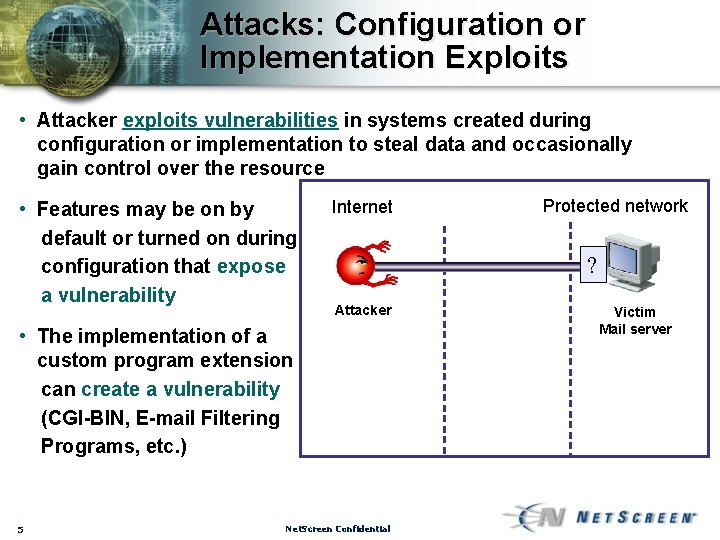
Attacks: Configuration or Implementation Exploits • Attacker exploits vulnerabilities in systems created during configuration or implementation to steal data and occasionally gain control over the resource • Features may be on by default or turned on during configuration that expose a vulnerability Internet ? Attacker • The implementation of a custom program extension can create a vulnerability (CGI-BIN, E-mail Filtering Programs, etc. ) 5 Protected network Net. Screen Confidential Victim Mail server

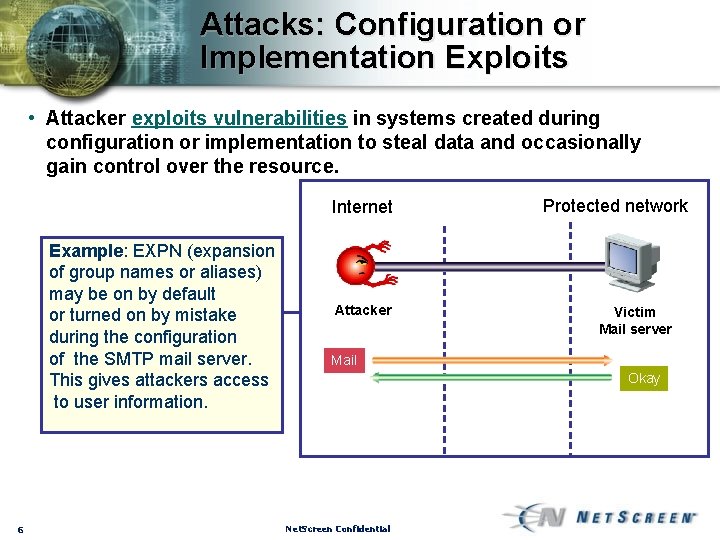
Attacks: Configuration or Implementation Exploits • Attacker exploits vulnerabilities in systems created during configuration or implementation to steal data and occasionally gain control over the resource. Internet Example: EXPN (expansion of group names or aliases) may be on by default or turned on by mistake during the configuration of the SMTP mail server. This gives attackers access to user information. 6 Attacker Protected network Victim Mail server Mail Okay Net. Screen Confidential

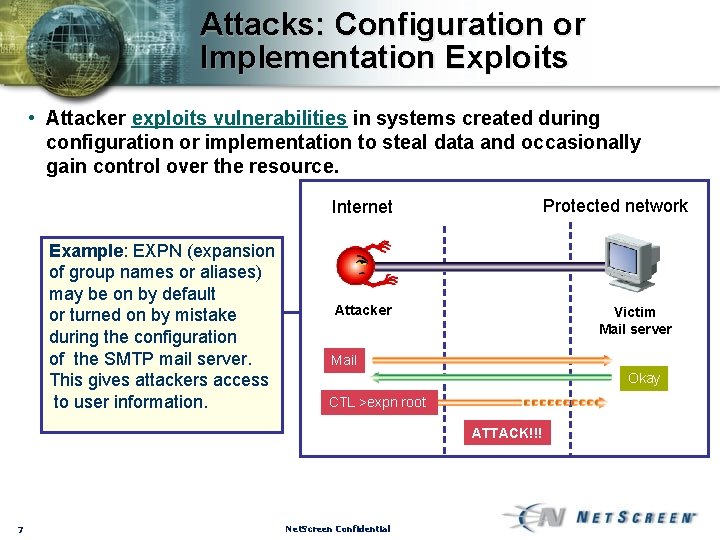
Attacks: Configuration or Implementation Exploits • Attacker exploits vulnerabilities in systems created during configuration or implementation to steal data and occasionally gain control over the resource. Protected network Internet Example: EXPN (expansion of group names or aliases) may be on by default or turned on by mistake during the configuration of the SMTP mail server. This gives attackers access to user information. Attacker Victim Mail server Mail Okay CTL >expn root ATTACK!!! 7 Net. Screen Confidential

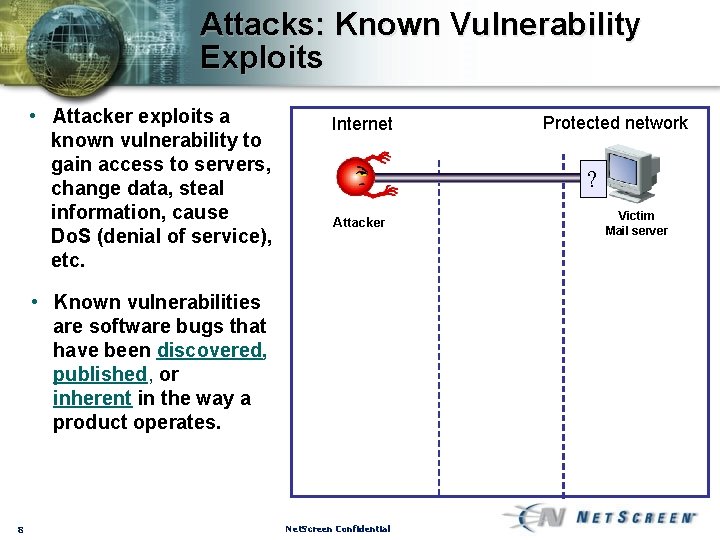
Attacks: Known Vulnerability Exploits • Attacker exploits a known vulnerability to gain access to servers, change data, steal information, cause Do. S (denial of service), etc. Internet ? Attacker • Known vulnerabilities are software bugs that have been discovered, published, or inherent in the way a product operates. 8 Protected network Net. Screen Confidential Victim Mail server

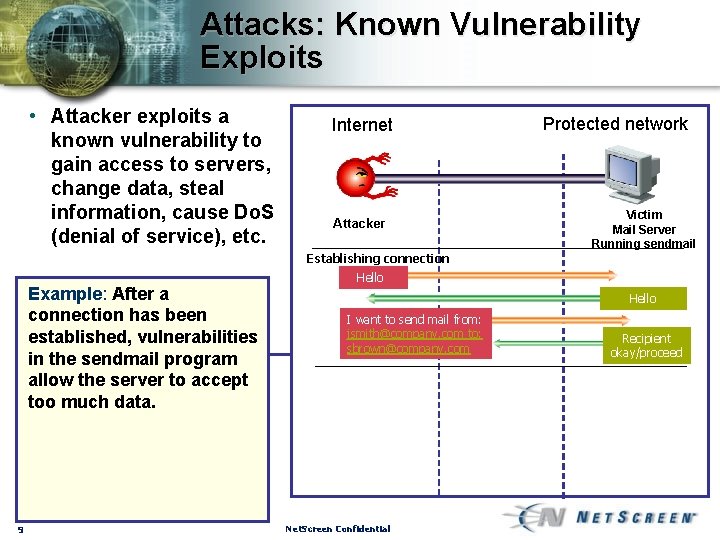
Attacks: Known Vulnerability Exploits • Attacker exploits a known vulnerability to gain access to servers, change data, steal information, cause Do. S (denial of service), etc. Internet Attacker Establishing connection Example: After a connection has been established, vulnerabilities in the sendmail program allow the server to accept too much data. 9 Protected network Victim Mail Server Running sendmail Hello I want to send mail from: jsmith@company. com to: sbrown@company. com Net. Screen Confidential Recipient okay/proceed

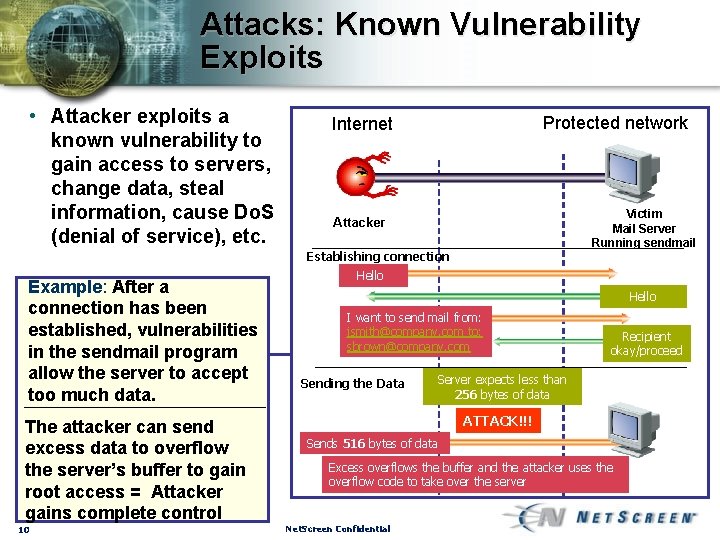
Attacks: Known Vulnerability Exploits • Attacker exploits a known vulnerability to gain access to servers, change data, steal information, cause Do. S (denial of service), etc. Protected network Internet Victim Mail Server Running sendmail Attacker Establishing connection Example: After a connection has been established, vulnerabilities in the sendmail program allow the server to accept too much data. The attacker can send excess data to overflow the server’s buffer to gain root access = Attacker gains complete control 10 Hello I want to send mail from: jsmith@company. com to: sbrown@company. com Sending the Data Recipient okay/proceed Server expects less than 256 bytes of data ATTACK!!! Sends 516 bytes of data Excess overflows the buffer and the attacker uses the overflow code to take over the server Net. Screen Confidential

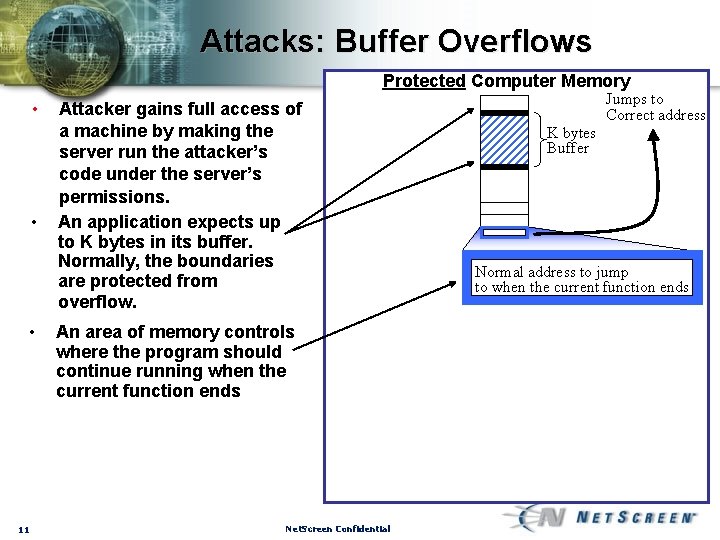
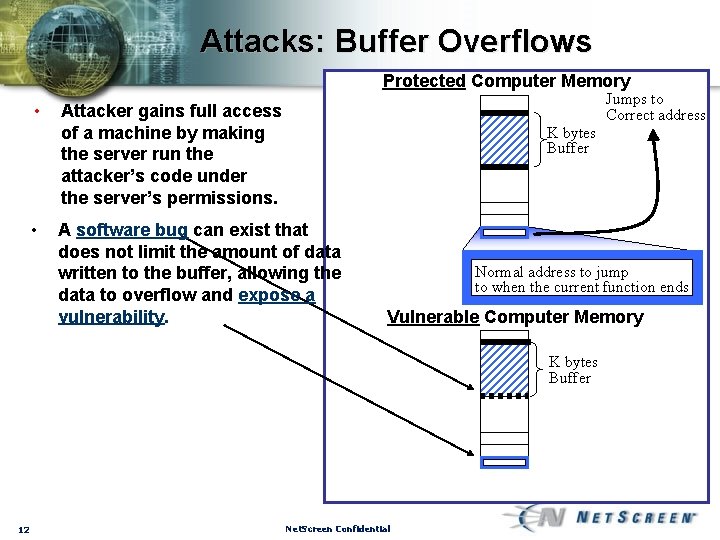
Attacks: Buffer Overflows Protected Computer Memory • • • 11 Attacker gains full access of a machine by making the server run the attacker’s code under the server’s permissions. An application expects up to K bytes in its buffer. Normally, the boundaries are protected from overflow. An area of memory controls where the program should continue running when the current function ends Net. Screen Confidential Jumps to Correct address K bytes Buffer Normal address to jump to when the current function ends

Attacks: Buffer Overflows Protected Computer Memory • • Jumps to Correct address Attacker gains full access of a machine by making the server run the attacker’s code under the server’s permissions. K bytes Buffer A software bug can exist that does not limit the amount of data written to the buffer, allowing the data to overflow and expose a vulnerability. Normal address to jump to when the current function ends Vulnerable Computer Memory K bytes Buffer 12 Net. Screen Confidential

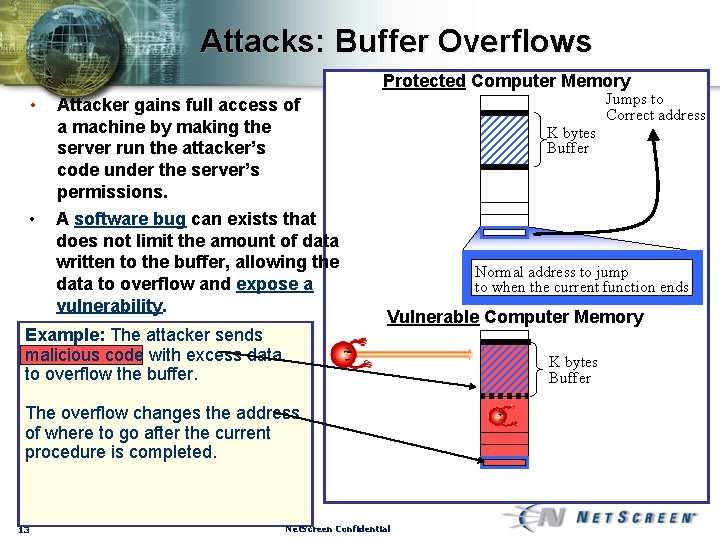
Attacks: Buffer Overflows Protected Computer Memory • • Jumps to Correct address Attacker gains full access of a machine by making the server run the attacker’s code under the server’s permissions. A software bug can exists that does not limit the amount of data written to the buffer, allowing the data to overflow and expose a vulnerability. Example: The attacker sends malicious code with excess data to overflow the buffer. K bytes Buffer Normal address to jump to when the current function ends Vulnerable Computer Memory K bytes Buffer The overflow changes the address of where to go after the current procedure is completed. 13 Net. Screen Confidential

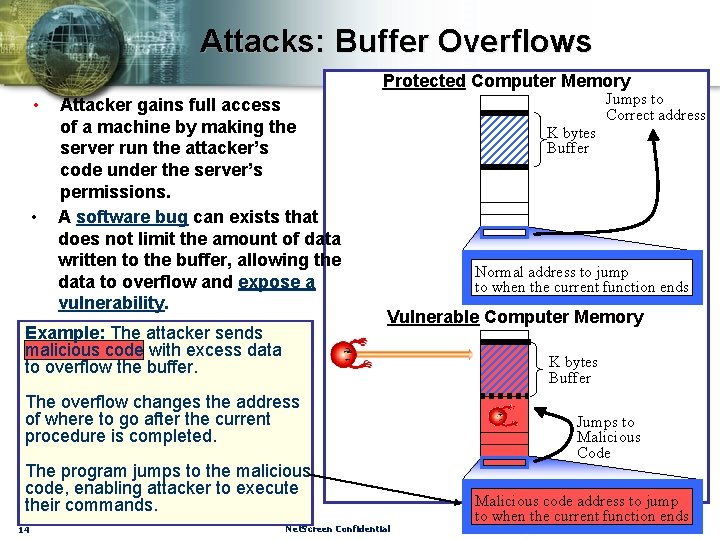
Attacks: Buffer Overflows Protected Computer Memory • • Attacker gains full access of a machine by making the server run the attacker’s code under the server’s permissions. A software bug can exists that does not limit the amount of data written to the buffer, allowing the data to overflow and expose a vulnerability. Example: The attacker sends malicious code with excess data to overflow the buffer. Jumps to Correct address K bytes Buffer Normal address to jump to when the current function ends Vulnerable Computer Memory K bytes Buffer The overflow changes the address of where to go after the current procedure is completed. The program jumps to the malicious code, enabling attacker to execute their commands. 14 Net. Screen Confidential Jumps to Malicious Code Malicious code address to jump to when the current function ends

Attacks: Trojans • Attacker uses social engineering or other means to install the malicious program on the victim. For example, the attacker may send an e-mail with an executable, such as a singing birthday card, to an unsuspecting user. Attacker Attack activity Mail Client • When the user runs the executable, it installs a malicious program in the background without the users knowledge. 15 E-mail Trojan “Trojan” downloads backdoor Net. Screen Confidential

Attacks: Trojans • Attacker uses social engineering or other means to install the malicious program on the victim. For example, the attacker may send an e-mail with an executable, such as a singing birthday card, to an unsuspecting user. Attacker Attack activity Mail Client • When the user runs the executable, it installs a malicious program in the background without the users knowledge. The attacker then interacts with the malicious program to gain control over the victim host, allowing them to do whatever they want on the network from behind the firewall. 16 E-mail Trojan “Trojan” downloads backdoor Attacker accesses backdoor, and server is compromised. The attacker has full control over the server Net. Screen Confidential

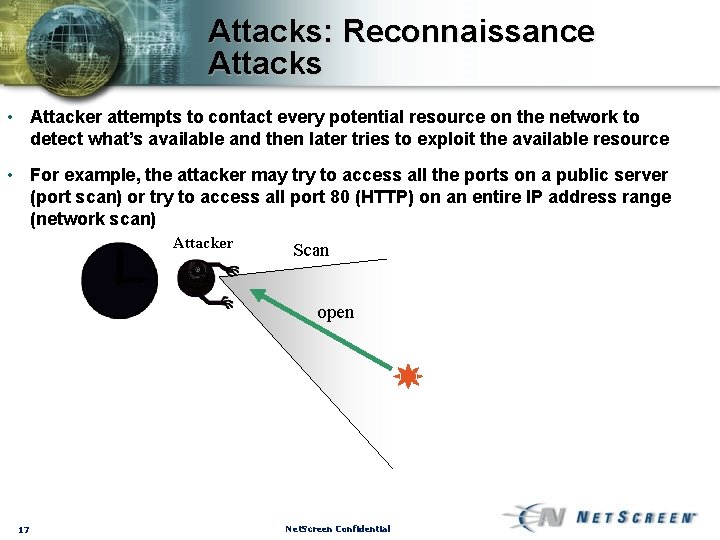
Attacks: Reconnaissance Attacks • Attacker attempts to contact every potential resource on the network to detect what’s available and then later tries to exploit the available resource • For example, the attacker may try to access all the ports on a public server (port scan) or try to access all port 80 (HTTP) on an entire IP address range (network scan) Attacker Scan open 17 Net. Screen Confidential

Attacks: Reconnaissance Attacks • Attacker attempts to contact every potential resource on the network to detect what’s available and then later tries to exploit the available resource • For example, the attacker may try to access all the ports on a public server (port scan) or try to access all port 80 (HTTP) on an entire IP address range (network scan) Attacker 18 Net. Screen Confidential

So How Can You Detect These Attacks? • No Detection Mechanism Can Detect All Types of Attacks • How Do the Available Detection Mechanisms Work & What Types of Attacks Are They Optimal for Detecting: • • • 19 Packet vs. Stateful Signatures Protocol Anomaly Detection Backdoor Detection Honeypot Traffic Anomaly Others Net. Screen Confidential

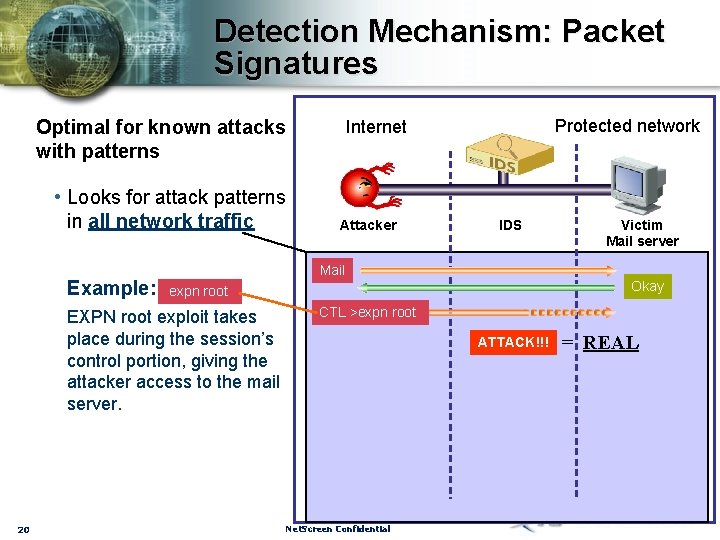
Detection Mechanism: Packet Signatures Optimal for known attacks with patterns • Looks for attack patterns in all network traffic Example: Attacker IDS Victim Mail server Mail Okay expn root EXPN root exploit takes place during the session’s control portion, giving the attacker access to the mail server. 20 Protected network Internet CTL >expn root ATTACK!!! Net. Screen Confidential = REAL

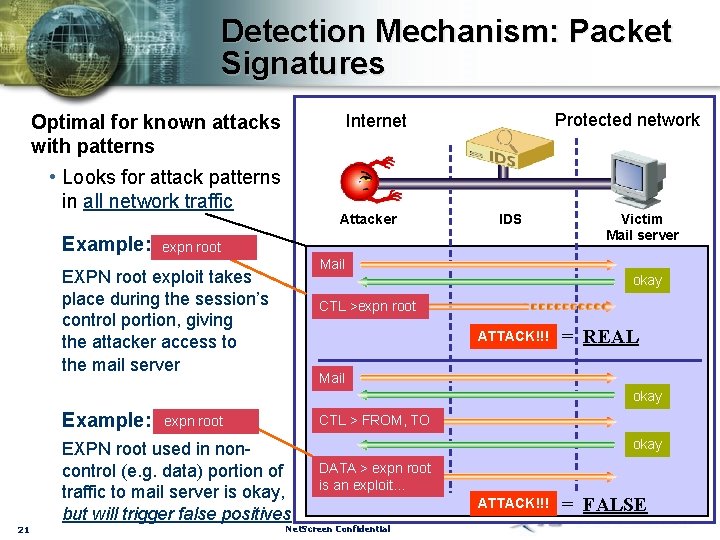
Detection Mechanism: Packet Signatures • Looks for attack patterns in all network traffic Example: Protected network Internet Optimal for known attacks with patterns Attacker IDS expn root Victim Mail server Mail EXPN root exploit takes place during the session’s control portion, giving the attacker access to the mail server okay CTL >expn root ATTACK!!! = REAL Mail okay Example: 21 CTL > FROM, TO expn root EXPN root used in noncontrol (e. g. data) portion of traffic to mail server is okay, but will trigger false positives okay DATA > expn root is an exploit… Net. Screen Confidential ATTACK!!! = FALSE

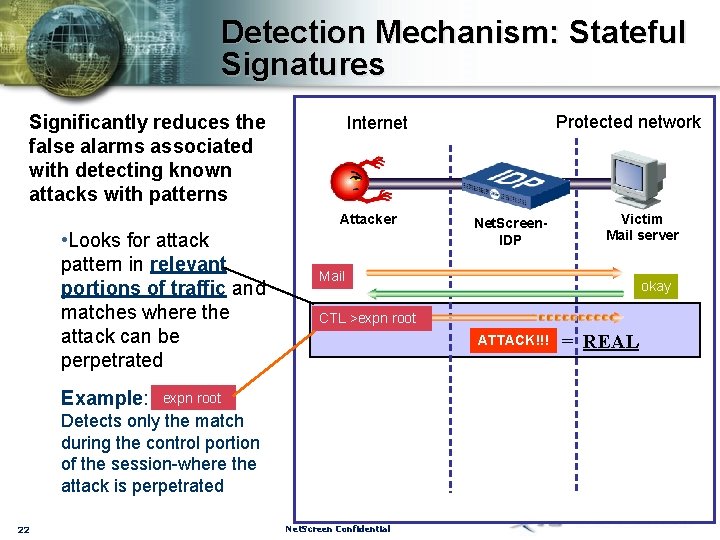
Detection Mechanism: Stateful Signatures Significantly reduces the false alarms associated with detecting known attacks with patterns Attacker • Looks for attack pattern in relevant portions of traffic and matches where the attack can be perpetrated Example: Net. Screen. IDP Victim Mail server Mail okay CTL >expn root ATTACK!!! expn root Detects only the match during the control portion of the session-where the attack is perpetrated 22 Protected network Internet Net. Screen Confidential = REAL

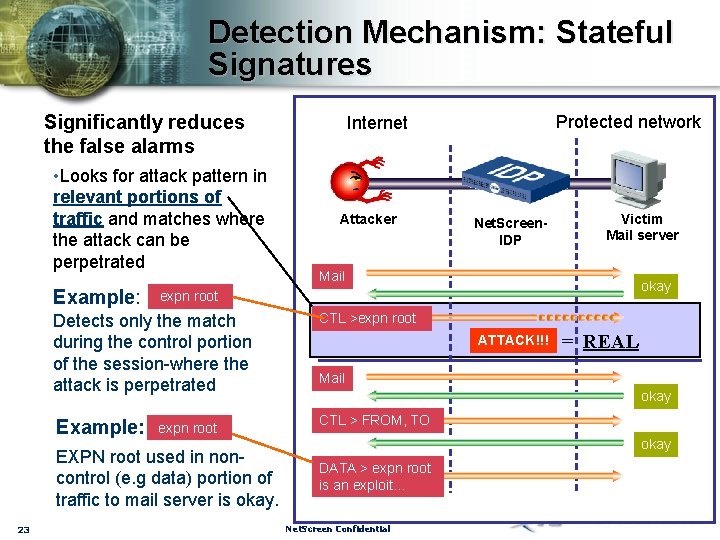
Detection Mechanism: Stateful Signatures Significantly reduces the false alarms • Looks for attack pattern in relevant portions of traffic and matches where the attack can be perpetrated Example: Attacker Net. Screen. IDP Victim Mail server Mail okay expn root Detects only the match during the control portion of the session-where the attack is perpetrated CTL >expn root Example: CTL > FROM, TO expn root EXPN root used in noncontrol (e. g data) portion of traffic to mail server is okay. 23 Protected network Internet ATTACK!!! = REAL Mail okay DATA > expn root is an exploit… Net. Screen Confidential

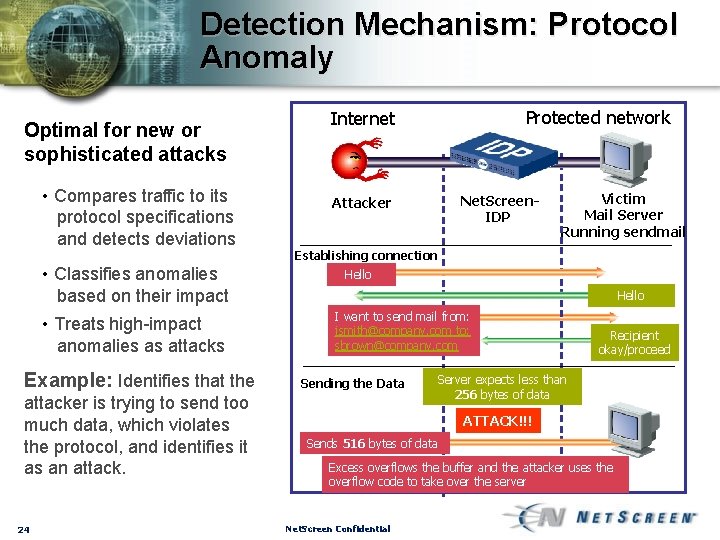
Detection Mechanism: Protocol Anomaly Optimal for new or sophisticated attacks • Compares traffic to its protocol specifications and detects deviations • Classifies anomalies based on their impact • Treats high-impact anomalies as attacks Example: Identifies that the attacker is trying to send too much data, which violates the protocol, and identifies it as an attack. 24 Protected network Internet Net. Screen. IDP Attacker Victim Mail Server Running sendmail Establishing connection Hello I want to send mail from: jsmith@company. com to: sbrown@company. com Sending the Data Recipient okay/proceed Server expects less than 256 bytes of data ATTACK!!! Sends 516 bytes of data Excess overflows the buffer and the attacker uses the overflow code to take over the server Net. Screen Confidential

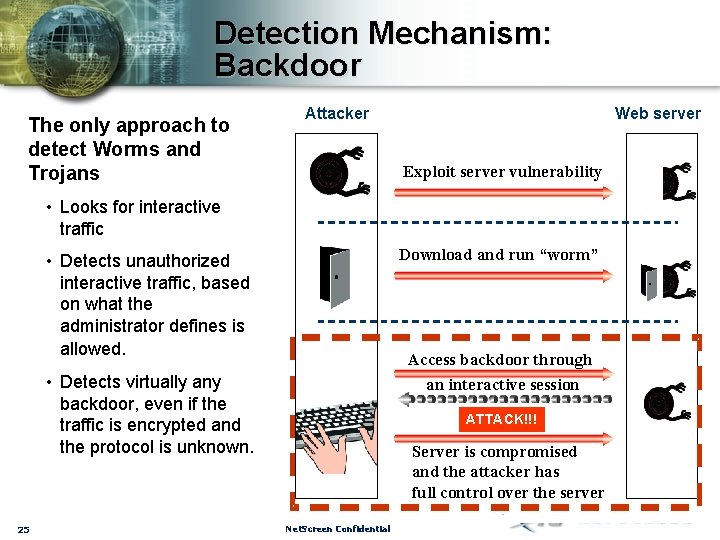
Detection Mechanism: Backdoor The only approach to detect Worms and Trojans Attacker Web server Exploit server vulnerability • Looks for interactive traffic Download and run “worm” • Detects unauthorized interactive traffic, based on what the administrator defines is allowed. Access backdoor through an interactive session • Detects virtually any backdoor, even if the traffic is encrypted and the protocol is unknown. 25 ATTACK!!! Server is compromised and the attacker has full control over the server Net. Screen Confidential

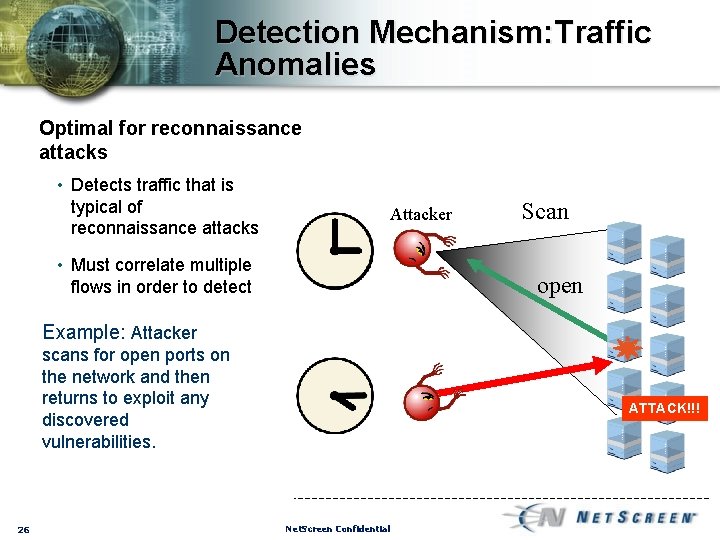
Detection Mechanism: Traffic Anomalies Optimal for reconnaissance attacks • Detects traffic that is typical of reconnaissance attacks Attacker • Must correlate multiple flows in order to detect Scan open Example: Attacker scans for open ports on the network and then returns to exploit any discovered vulnerabilities. 26 ATTACK!!! Net. Screen Confidential

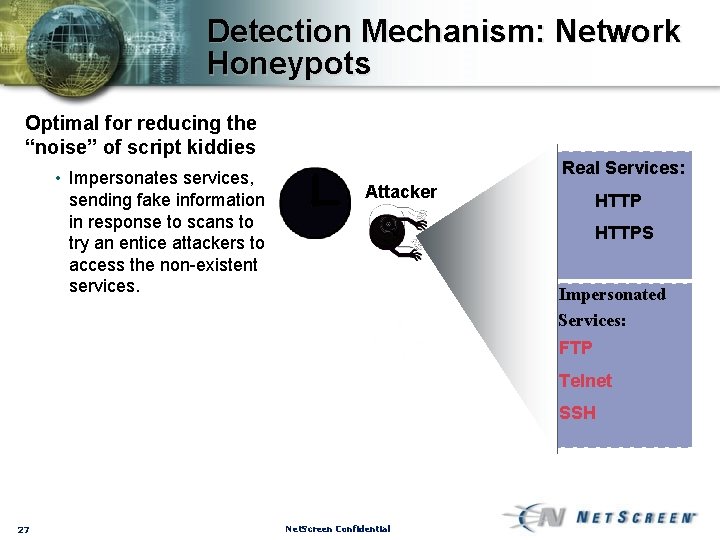
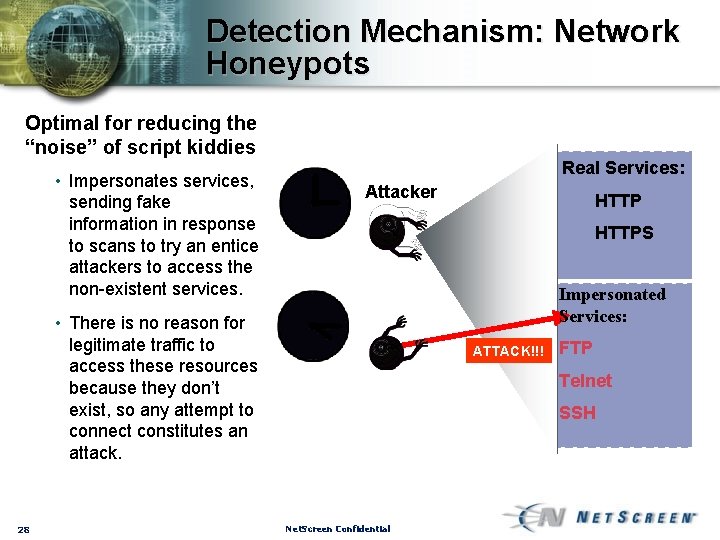
Detection Mechanism: Network Honeypots Optimal for reducing the “noise” of script kiddies • Impersonates services, sending fake information in response to scans to try an entice attackers to access the non-existent services. Real Services: Attacker HTTPS Impersonated Services: FTP Telnet SSH 27 Net. Screen Confidential

Detection Mechanism: Network Honeypots Optimal for reducing the “noise” of script kiddies • Impersonates services, sending fake information in response to scans to try an entice attackers to access the non-existent services. Real Services: Attacker HTTPS Impersonated Services: • There is no reason for legitimate traffic to access these resources because they don’t exist, so any attempt to connect constitutes an attack. 28 HTTP ATTACK!!! FTP Telnet SSH Net. Screen Confidential

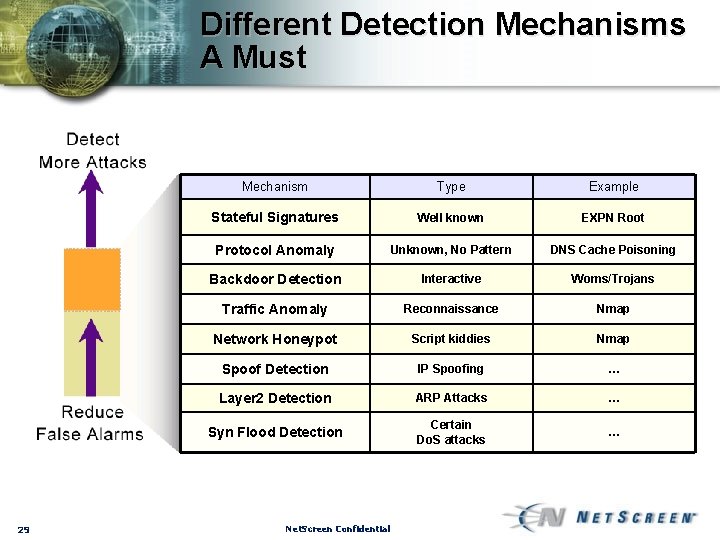
Different Detection Mechanisms A Must 29 Mechanism Type Example Stateful Signatures Well known EXPN Root Protocol Anomaly Unknown, No Pattern DNS Cache Poisoning Backdoor Detection Interactive Woms/Trojans Traffic Anomaly Reconnaissance Nmap Network Honeypot Script kiddies Nmap Spoof Detection IP Spoofing … Layer 2 Detection ARP Attacks … Syn Flood Detection Certain Do. S attacks … Net. Screen Confidential

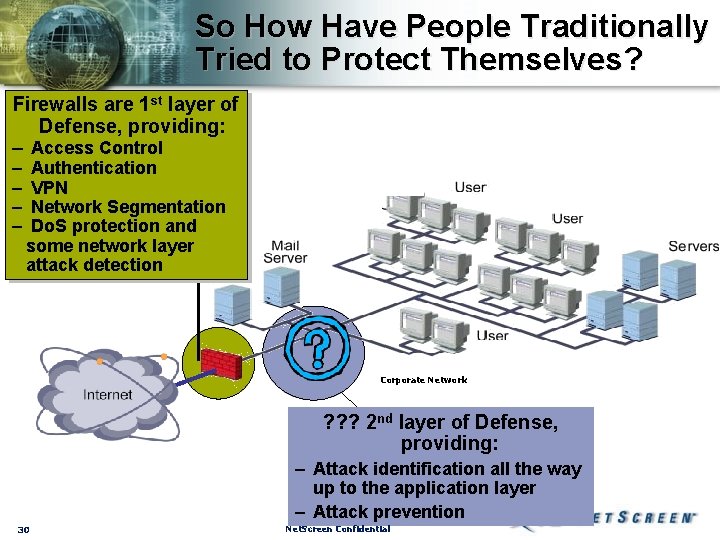
So How Have People Traditionally Tried to Protect Themselves? Firewalls are 1 st layer of Defense, providing: – Access Control – – Authentication VPN Network Segmentation Do. S protection and some network layer attack detection Corporate Network ? ? ? 2 nd layer of Defense, providing: – Attack identification all the way up to the application layer – Attack prevention 30 Net. Screen Confidential

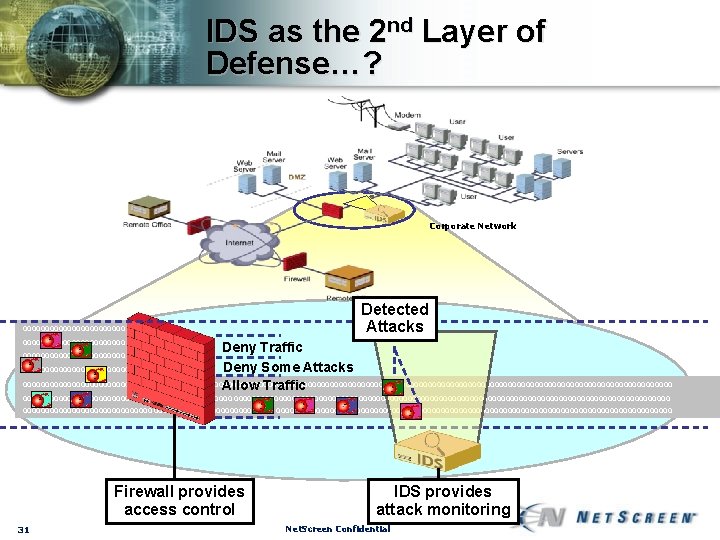
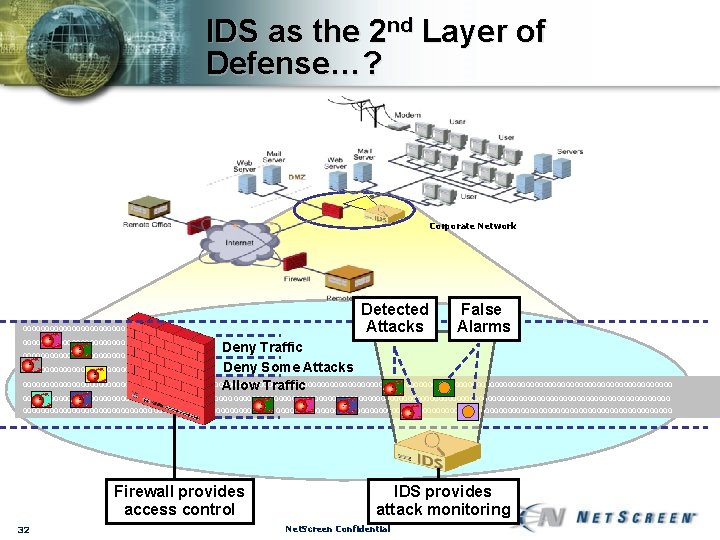
IDS as the 2 nd Layer of Defense…? Corporate Network 00000000000000000000000 000000000000000 Detected Attacks Deny Traffic Deny Some Attacks 0000000000000000000000000000000000000000000000000000000000000000000000000 Allow Traffic 0000000000000000000000000000000000000000000000000000000000000000000000000 0000000000000000000000000000000000000000000000000000000000 Firewall provides access control 31 IDS provides attack monitoring Net. Screen Confidential

IDS as the 2 nd Layer of Defense…? Corporate Network 00000000000000000000000 000000000000000 Detected Attacks False Alarms Deny Traffic Deny Some Attacks 0000000000000000000000000000000000000000000000000000000000000000000000000 Allow Traffic 0000000000000000000000000000000000000000000000000000000000000000000000000 0000000000000000000000000000000000000000000000000000000000 Firewall provides access control 32 IDS provides attack monitoring Net. Screen Confidential

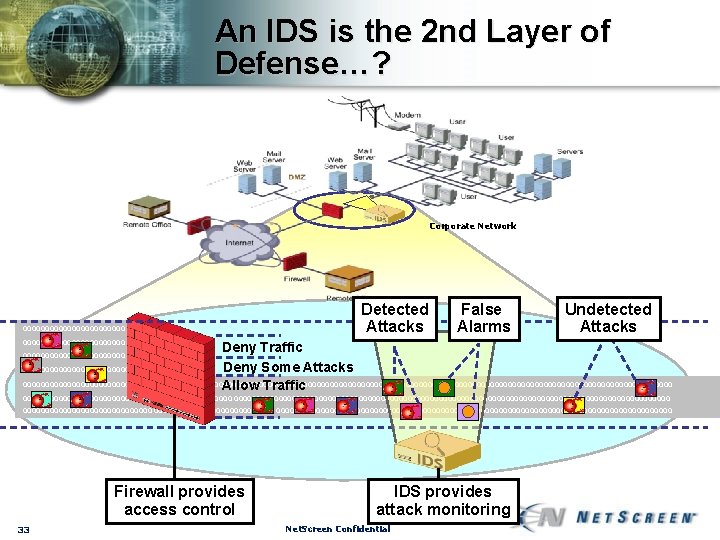
An IDS is the 2 nd Layer of Defense…? Corporate Network 00000000000000000000000 000000000000000 Detected Attacks False Alarms Undetected Attacks Deny Traffic Deny Some Attacks 0000000000000000000000000000000000000000000000000000000000000000000000000 Allow Traffic 0000000000000000000000000000000000000000000000000000000000000000000000000 0000000000000000000000000000000000000000000000000000000000 Firewall provides access control 33 IDS provides attack monitoring Net. Screen Confidential

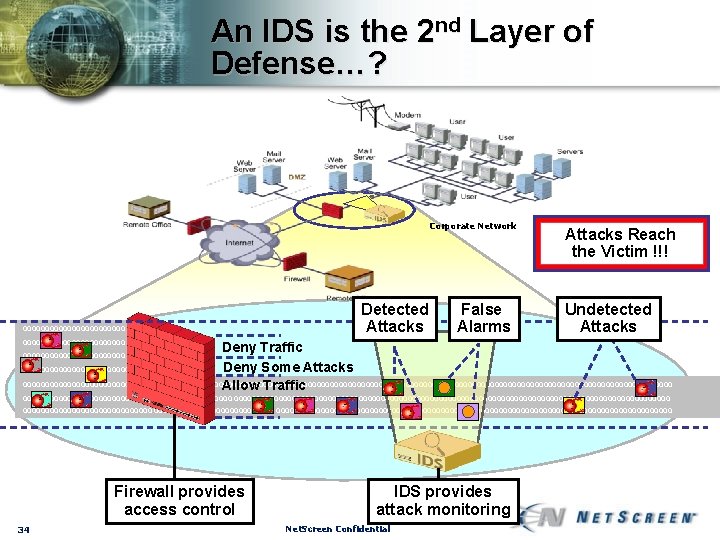
An IDS is the 2 nd Layer of Defense…? Corporate Network 00000000000000000000000 000000000000000 Detected Attacks False Alarms Attacks Reach the Victim !!! Undetected Attacks Deny Traffic Deny Some Attacks 0000000000000000000000000000000000000000000000000000000000000000000000000 Allow Traffic 0000000000000000000000000000000000000000000000000000000000000000000000000 0000000000000000000000000000000000000000000000000000000000 Firewall provides access control 34 IDS provides attack monitoring Net. Screen Confidential

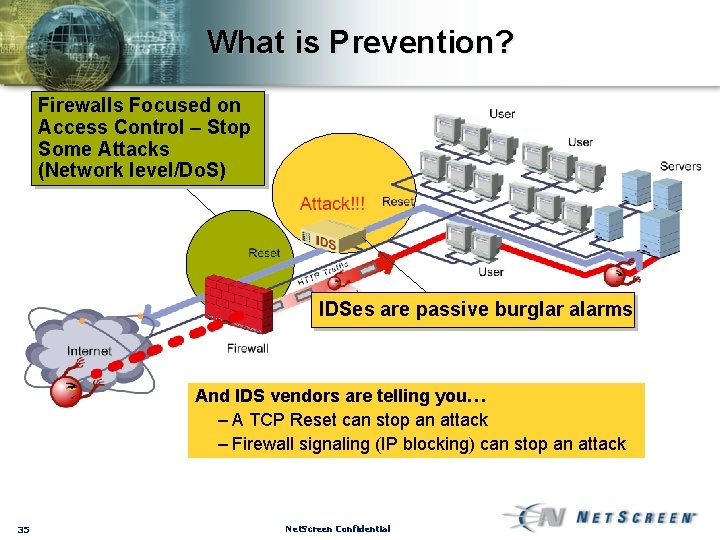
What is Prevention? Firewalls Focused on Access Control – Stop Some Attacks (Network level/Do. S) IDSes are passive burglar alarms And IDS vendors are telling you… – A TCP Reset can stop an attack – Firewall signaling (IP blocking) can stop an attack 35 Net. Screen Confidential

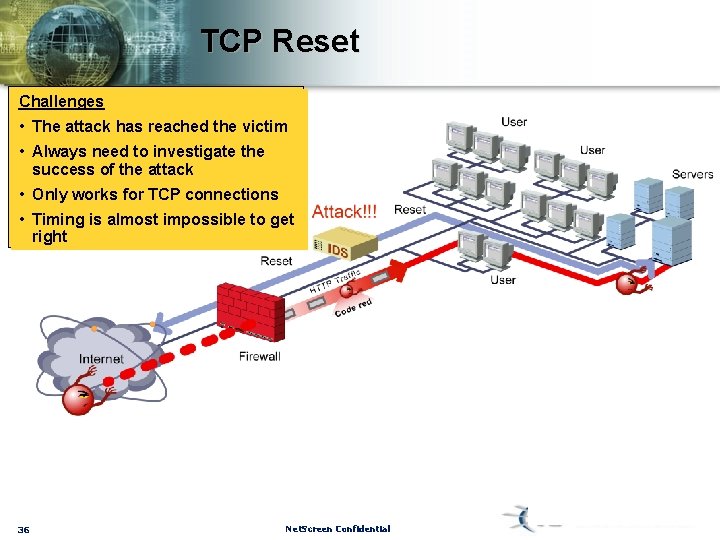
TCP Reset Challenges • The attack has reached the victim • Always need to investigate the success of the attack • Only works for TCP connections • Timing is almost impossible to get right 36 Net. Screen Confidential

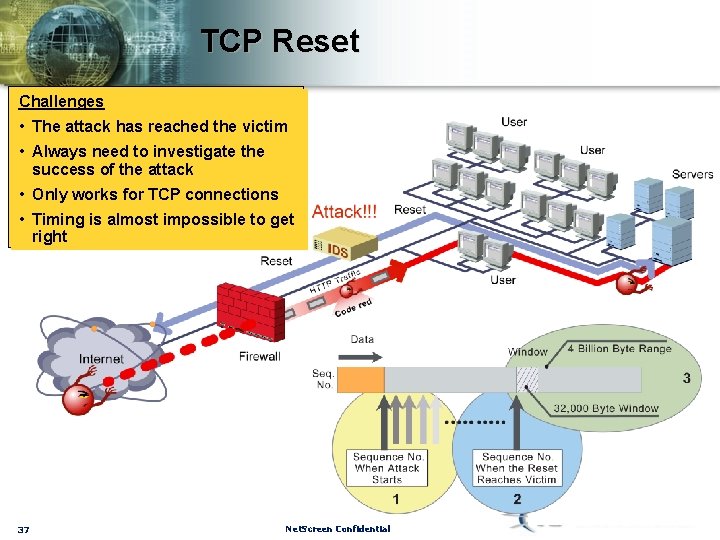
TCP Reset Challenges • The attack has reached the victim • Always need to investigate the success of the attack • Only works for TCP connections • Timing is almost impossible to get right 37 Net. Screen Confidential

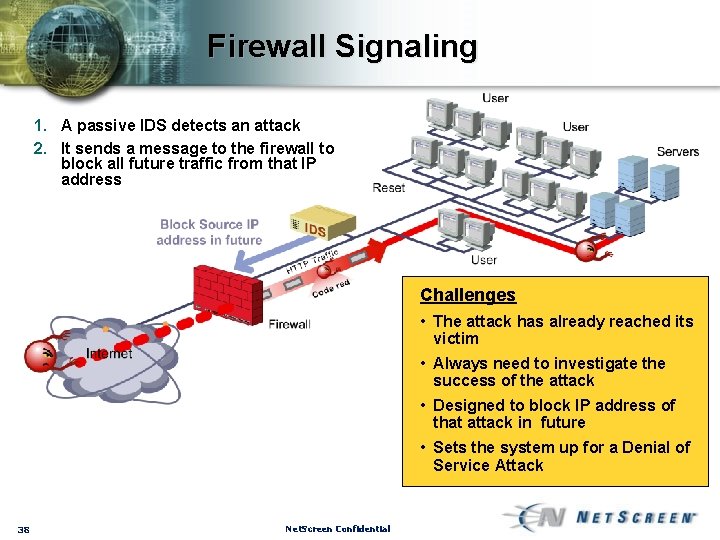
Firewall Signaling 1. A passive IDS detects an attack 2. It sends a message to the firewall to block all future traffic from that IP address Challenges • The attack has already reached its victim • Always need to investigate the success of the attack • Designed to block IP address of that attack in future • Sets the system up for a Denial of Service Attack 38 Net. Screen Confidential

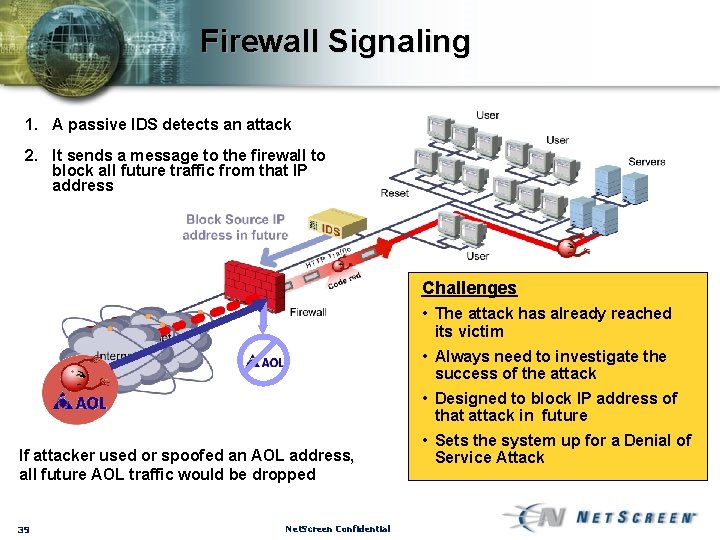
Firewall Signaling 1. A passive IDS detects an attack 2. It sends a message to the firewall to block all future traffic from that IP address Challenges • The attack has already reached its victim • Always need to investigate the success of the attack • Designed to block IP address of that attack in future If attacker used or spoofed an AOL address, all future AOL traffic would be dropped 39 Net. Screen Confidential • Sets the system up for a Denial of Service Attack

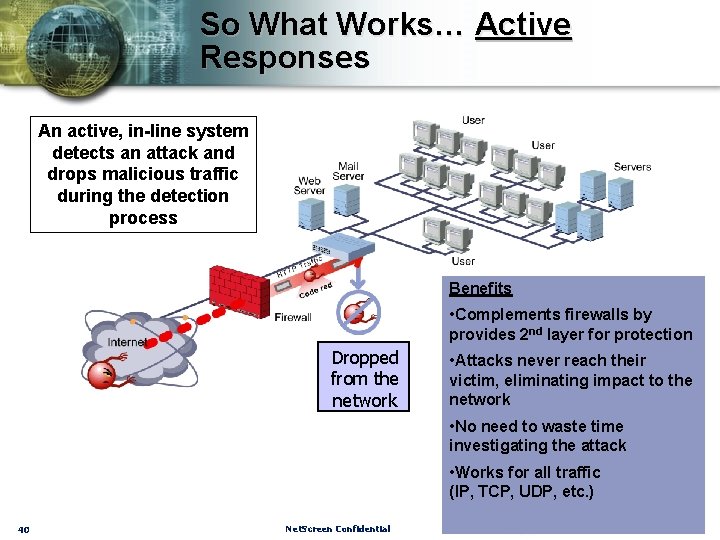
So What Works… Active Responses An active, in-line system detects an attack and drops malicious traffic during the detection process Benefits • Complements firewalls by provides 2 nd layer for protection Dropped from the network • Attacks never reach their victim, eliminating impact to the network • No need to waste time investigating the attack • Works for all traffic (IP, TCP, UDP, etc. ) 40 Net. Screen Confidential

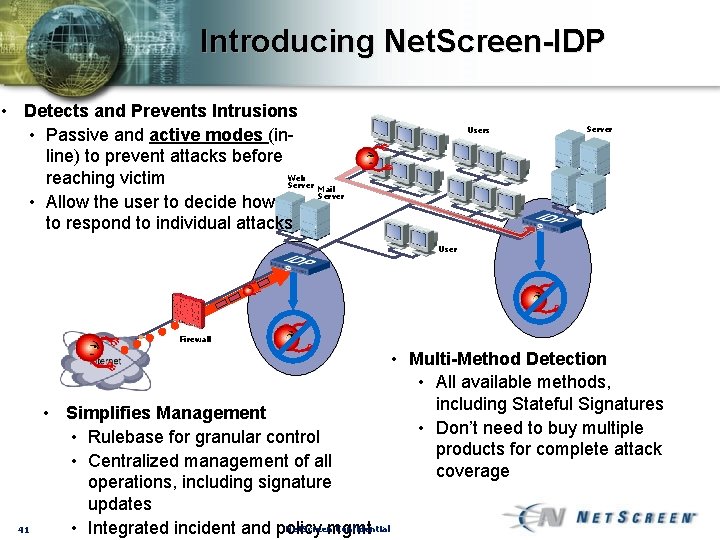
Introducing Net. Screen-IDP • Detects and Prevents Intrusions • Passive and active modes (inline) to prevent attacks before Web reaching victim Server Mail Server • Allow the user to decide how to respond to individual attacks Users Server User Firewall 41 • Simplifies Management • Rulebase for granular control • Centralized management of all operations, including signature updates Net. Screen Confidential • Integrated incident and policy mgmt • Multi-Method Detection • All available methods, including Stateful Signatures • Don’t need to buy multiple products for complete attack coverage

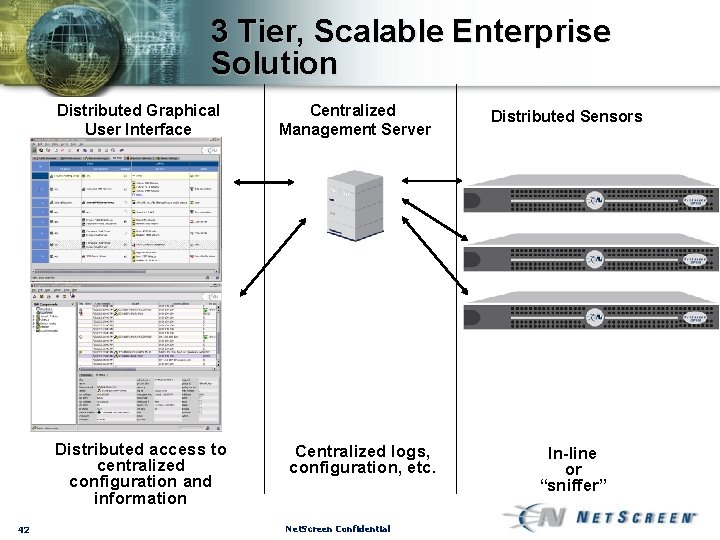
3 Tier, Scalable Enterprise Solution Distributed Graphical User Interface Distributed access to centralized configuration and information 42 Centralized Management Server Centralized logs, configuration, etc. Net. Screen Confidential Distributed Sensors In-line or “sniffer”

Simplified Management • Centralized Management –Distributed access to all configuration, log and incident information –Three-Tier Architecture for scalability • Rule-based management –Define single policy to configure all sensors. Simple, logical method of looking at all configuration information. • Granular control –Dictate exactly what traffic to analyze, what to look for in that traffic and how to respond. • Simplified signature management –Open signature format provides flexibility and scalability –Signatures are updated on sensors every time policy is downloaded • Integrated Incident Management 43 –Integrated Policy Editor, Log Viewer, Packet Viewer and Report Manager for streamlined Net. Screen Confidential operation

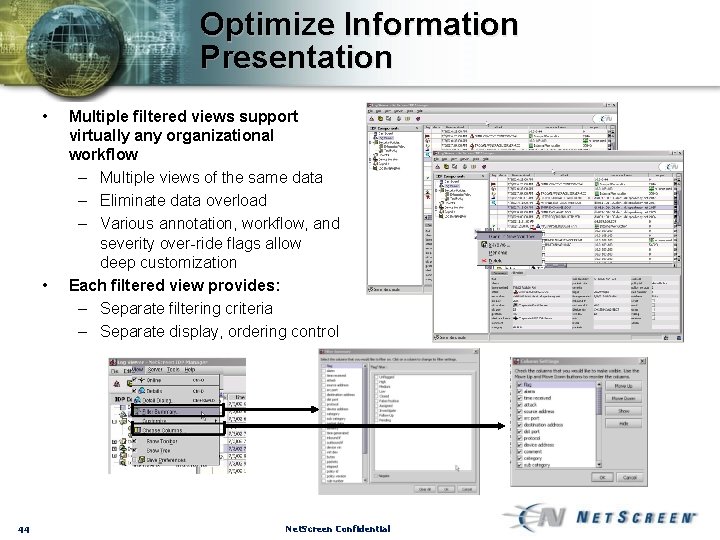
Optimize Information Presentation • • 44 Multiple filtered views support virtually any organizational workflow – Multiple views of the same data – Eliminate data overload – Various annotation, workflow, and severity over-ride flags allow deep customization Each filtered view provides: – Separate filtering criteria – Separate display, ordering control Net. Screen Confidential

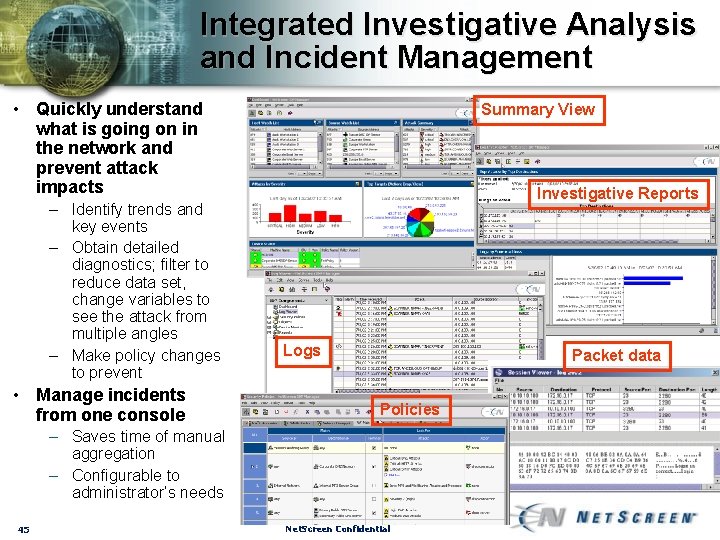
Integrated Investigative Analysis and Incident Management • Quickly understand what is going on in the network and prevent attack impacts – Identify trends and key events – Obtain detailed diagnostics; filter to reduce data set, change variables to see the attack from multiple angles – Make policy changes to prevent • Manage incidents from one console Summary View Investigative Reports Logs Packet data Policies – Saves time of manual aggregation – Configurable to administrator’s needs 45 Net. Screen Confidential

For more information 1 -877 -638 -8296 info@netscreen. com Thanks for Your Time